The Fiber Data Distributed Interface (FDDI) network is a fault-redundant, point-to-point, high-speed LAN topology design. The FDDI network is based on a 100Mbps data-rate standard, although higher data rates can be achieved and are discussed later in this chapter. The design of a FDDI network is physically based on an infrastructure design that utilizes two physical rings. One ring is utilized as a primary ring; the second ring is utilized as a backup ring connection electrical link.
The nodes or stations that interconnect to a FDDI network can connect to either the primary or the backup ring at the same time, or just to the primary ring. The FDDI specification allows for approximately 500 stations to be interconnected to the FDDI network. The cabling distance of a FDDI network in a standard configuration should be no more than 200 kilometers. The maximum distance between two respective FDDI nodes on a FDDI ring can be no more than two kilometers. The FDDI internetworking protocol model design is based on a layering scheme that mainly relates to the Open System Interconnection(OSI) model at the physical and data link layer. Four layers operate as compared to the two layers of the OSI model.
The four layers are as follows:
FDDI Physical Independent layer (PHY)
FDDI Physical Media Dependent layer (PMD)
FDDI Medium Access Control layer (MAC)
FDDI Station Management layer (SMT)
Three companies developed FDDI's overall architecture: Sperry, Burroughs, and Advanced Micro Devices. These three companies formed a consortium to introduce the technology that was developed between 1983 and 1998 when the standard was approved. The American National Standards Institute (ANSI) formally certified FDDI after review by its X3T9.5 Committee.
The FDDI topology is a LAN design based on a dual-ring fault-redundant approach. FDDI has a star layout design with a point-to-point network con- figuration, in which each device connected to the network is attached to the main FDDI ring in a counter-attached dual-ring topology design. The dual ring that interconnects to each one of the specific devices on the FDDI is called the trunk ring. The primary and the secondary ring (the dual-ring technology) work together in a counter-rotating mode. The counter-rotating rings enable a support analyst to easily reconfigure a FDDI ring when a problem occurs.
FDDI actually works through an electrical ring design, but is laid out as a logical star. This is somewhat similar to the Token Ring LAN configuration. The following section further describes the architecture details.
The FDDI ring cables that interconnect FDDI devices actually move through an infrastructure, such as a building, in a star topology design. The main FDDI network is still an electrical ring. A FDDI network is mainly used as a backbone technology. Because of its use as such, FDDI rings are usually designed and implemented within one main computer room. FDDI has all the technology necessary to be fully configured as a local area network (LAN). Therefore, a FDDI network in a large corporate infrastructure can serve as a backbone technology and can also provide direct LAN connections to the desktop. Most companies have thus far limited their implementation of FDDI to its backbone role because of the physical wiring restrictions and costs. Even so, they can still interconnect other LAN topologies with a FDDI ring via modules in internetworking technology–based hubs. Most of the backbone technology for FDDI networks is used to interconnect to main file servers or key hosts within main computer rooms. Quite often, the main FDDI backbone ring interconnects to other LAN technologies so that users can access a FDDI host via other LAN technology end routes, such as Ethernet.
An end user might connect to an Ethernet LAN or a Token Ring LAN (in most cases), for example, and then route, switch, or bridge over to a FDDI backbone within a main computer room. This is a common implementation of the FDDI network because of the high-cost structures and implementation issues involved with using the FDDI topology for direct end-user connectivity.
One of the key characteristics of the FDDI architecture is that certain nodes that interconnect to the FDDI network can change the ring length of the FDDI network in terms of its complete operational configuration.
As stated previously, one of the main rings on a FDDI network is considered a primary ring and usually handles all data transfer. The secondary ring is mainly used for fault redundancy and normally handles only data-intensive transfers during high-speed transfer cycles.
All the nodes interconnected to the FDDI network are active nodes. A device is a node if it has at least one connection to either the primary or the secondary ring on the FDDI network. For a device to be an active node, it should have a FDDI MAC agent on the FDDI NIC. Further discussion of the FDDI MAC agent appears later in this chapter. If the MAC agent is processing and active, a device is considered an active node on a FDDI network.
Two types of nodes are considered active for configuration and connection to a FDDI ring structure: single attachment stations (SAS), and dual attachment stations (DAS). A SAS connects to one ring, and a DAS connects to both the primary and the secondary ring.
The FDDI architecture allows other devices to interconnect with FDDI network in extension and fault-redundancy configurations. An optical bypass device for a FDDI network is one common implementation of such. This type of device maintains an emergency connection in the event of a node fault. Certain devices can inherently have an optical bypass design connected within their node in case certain processes fail. In such a case, the FDDI ring can continue to operate through the node connection, even if the device fails.
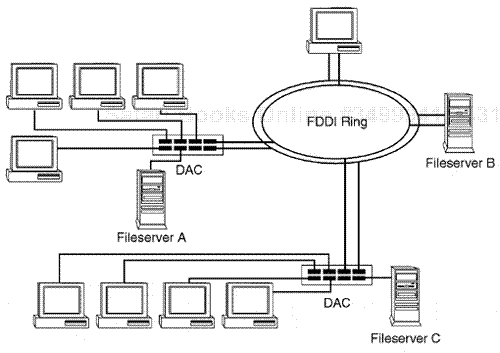
When multiple devices have to connect to the FDDI internetwork, a FDDI concentrator is used. The FDDI concentrator can connect to the dual-ring configuration or to a single-ring configuration. A single attached concentrator(SAC) connects to the single ring; a dual attached concentrator (DAC) connects to the dual-ring architecture.
Four main interconnection schemes apply to FDDI port configurations on a FDDI device or design. Port A is considered a ring port for interconnection to the backup ring. If a SAC or a DAS connects directly to the backup ring, it connects through Port A. If a device, such as a SAS or a DAS, is going to connect to a primary ring, it uses Port B. If a device, such as a concentrator, is going to connect to the ring on the primary ring, it uses Port B. In most cases, DASs and DACs connect to both rings, which is the most common configuration; and in such cases, Ports A and B are both used. The dual- redundancy technology offers the advantage of the counter-rotating fault-redundancy inherent in the architecture.
Most DAC and SAC concentrators have a Port M. This is the connection port on a concentrator for an end-node device to actually connect to the FDDI topology (as noted before, through a concentrator link). If a device is going to a concentrator, the device will have a Port S, which connects to Port M on the concentrator.
Specifically, the normal link process for an endpoint device to interconnect to a FDDI ring is for the device's Port S connector to link and interconnect to Port M on a SAC or DAC concentrator. Then the concentrator will have interconnection ports, such as Ports A and B, which provide the final connection directly to the main FDDI ring (see Figure 10.1).
All active SAS and DAS devices have a MAC agent operating. The FDDI MAC agent enables interconnection processes, address verification, fault-redundancy verification, and interconnection and cross-communication operations with Station Management layer (SMT) agents inherent in a FDDI device. (More details on this subject appear later in this chapter.) Note that connecting a specific single device to just one of the FDDI ring paths is normally not recommended. An SAS should connect through a concentrator link, for example. This type of interconnection scheme can be used, but might cause faults and failures on the FDDI ring.
You should actually use DAS or DAC devices to connect to both rings. When this setup is used, multiple end ports interconnect to the main ring, ensuring a clean A and B connection to both the primary and the backup secondary ring (see Figure 10.2).
Another advantage of DAS-based stations is that they usually have both a MAC agent active as well as a SMT layer operation active, which allows for a full set of physical management operations to be active (as is inherent in the FDDI design). This is not to say that some SAS-based designs will not also have an active SMT layer that can also be an active component of the SAS device architecture (see Figure 10.3).
The DAC type concentrators usually fully comply with all the FDDI specifi-cations and allow for the cleanest connection to the FDDI ring. Also, dual attachment stations inherently enable you to configure and lay out a fault-redundant architecture within a specific site. DACs normally support a fully physical media-dependent operation that allows for a full A and B port interconnection and uses both media interface connections (MIC) and the standard FDDI (ST) and (SC) connectors for physical media fiber links.
SACs are usually less intelligent than DACs, but will allow for the intercon- nection of a device to the ring. A SAC is generally implemented on config- urations when budget resources are limited. As stated earlier, the preferred approach when designing a FDDI LAN is to use DACs that allow for a fully redundant A and B port connection to the main FDDI ring. The DACs then can provide multiple access end ports for SASs and DASs to interconnect to the concentrator, and can then link directly into the main FDDI ring.
The following items are some of the key FDDI architecture technical specifications:
FDDI data rate. . 100Mbps.
Signal encoding process. . NRZI with 4B/5B block coding.
FDDI media type interconnection scheme. . Fiber MMF and SMF. Shielded twisted-pair/data grade unshielded twisted-pair.
Clocking scheme. . Distributed and cross-linked transmit and receive clocks operating in direct parallel.
Maximum frame size. . 4500 bytes or 9000 symbols.
Frame format. . MAC frame format: Preamble, Starting Delimiter, Frame Control, Destination Address, Source Address, Information field, Frame Check Sequence, Ending Delimiter, Frame Status field.
Priority levels for operation as assigned with access. . Eight levels of asynchronous deterministic operation, which is considered standard, along with synchronous if required.
Priority handling. . Station priority can be considered active.
Access protocol. . Timed Token Rotation Time(TTRT) protocol and token passing methodology.
Network transmission. . The token is captured by extracting it from the ring and stripping it from the network into the station. The station transmits data frames as required, and then releases the token. A token release is normally provided immediately after data transmission is completed or after timer THT expires.
Maximum length of standard configurations. . 200 kilometers. In certain cases, a unique configuration may apply in accordance with vendor's specification.
Maximum node count. . 500 nodes.
Physical topology. . Logical star hierarchical ring.
When the FDDI ring is operating, the ring can be configured in different states (from a layout and design perspective). The FDDI operational state changes based on occurrence. The following is a brief description of the primary ring layout and design possibilities, along with certain descriptions of FDDI operational states.
The main FDDI network operational states are as follows:
FDDI single ring with trees
FDDI dual rings with trees
FDDI dual rings without trees
FDDI dual homing ring configuration
FDDI wrapped ring
This implementation is configured in a design where a FDDI network is using a single ring. Multiple devices can be interconnected via M ports on a concentrator. This is not the most popular design, because fault redundancy is not inherent to the operation within a single ring architecture.
In this type of configuration, both the primary and the secondary rings are used. A DAC design is normally directly connected to the main primary and secondary ring via the A and B port connection method. Any specific devices that are going to interconnect to the main FDDI ring will usually only be DAS-type devices. Specifically, any devices that are going to directly connect to the ring and not use a concentrator import normally use a DAC configuration rather than an SAS-type connection to ensure a fault-redundant implementation. Any SAS devices that are going to connect are linked to the main FDDI dual ring through a DAC connection. With this type of configuration, it is important to ensure that a pure dual ring is maintained; devices can have both SAS and DAS connections via a DAC concentrator, however, to form the tree off the dual ring (see Figure 10.4).
In this configuration, a main FDDI ring is designed and engaged primarily as a pure backbone architecture. This type of configuration is based on a dual ring without any trees linked to the configuration. In this configuration, only DACs and DAS devices that are considered critical are interconnected to the both the FDDI primary and secondary ring configuration.
This setup would be based on a configuration where a FDDI layout is in a main computer room. In this case, the main servers or hosts would have primary Port B and secondary Port A connections directly to the ring. Generally, no trees are configured as a concentrator link between the main server or host even though a DAC connection is valid. This would allow for a pure DAS to dual ring full loop interconnection operation.
The FDDI design can also allow a critical server, such as a host or a main file server, to have direct resource interconnections via two different connection links to the FDDI ring.
One specific design could allow for two DAC concentrators to be connected to both the primary and the secondary rings of the main FDDI full loop ring, for example. A main file server could also have two FDDI NICs, which would then interconnect to the two different DACs via M ports. This layout would then allow two different points of presence through two different concentrators for the main server to link into the FDDI ring. In this type of situation, one link from the server would be maintained in a constant operational state; the other one would be maintained in a withheld or quiet link state. In this case, the main active link state that is operating would be the primary link. In case of any failure of operation in that particular device or FDDI NIC, the dual homing link would take over and become the active link, and would move from a quiet or withheld state to an active link state. This is a popular configuration for fault redundancy (see Figure 10.5).
In the case of a failure of a FDDI node or device connected to the main ring, it is possible for devices, such as DACs or DASs, to allow for immediate reconfiguration and for the main FDDI ring to be wrapped. When a FDDI ring wraps, a loop occurs where the main and primary ring connect at a failure point to effect a wrapped condition.
In such a case, the FDDI node technology in the DAC or DAS invokes an operation where an electrical trigger signal is sent to the FDDI network connection. Certain dual-ring technology components allow an actual bypass process to take place where the concentrator or station will allow light to stream through the bypass optical break and actually move the ring into a wrapped state process. In certain types of device configurations, this might require manual reconfiguration; in other cases, true inherent automatic reconfiguration can take place. This depends on the specific type of FDDI device and technology as implemented for wrapped state configurations (see Figures 10.6 and 10.7).
The following is a description of the main FDDI layer operational modes and processes that can take effect when a device is connected and active on a FDDI network. The following descriptions apply to both directly connected station configuration NICs, such as a SAS or DAS, and to concentrator connections, such as SACs and DACs, as they interconnect to a main FDDI single- or full-loop ring.
All FDDI NIC connections can have certain layer operations that are active. The following descriptions relate to these layer interconnection schemes.
The following four operational layers operate within the FDDI physical connection area:
FDDI Physical Media Dependent layer (PMD)
FDDI Physical layer (PHY)
FDDI Medium Access Control layer (MAC)
FDDI Station Management layer (SMT)
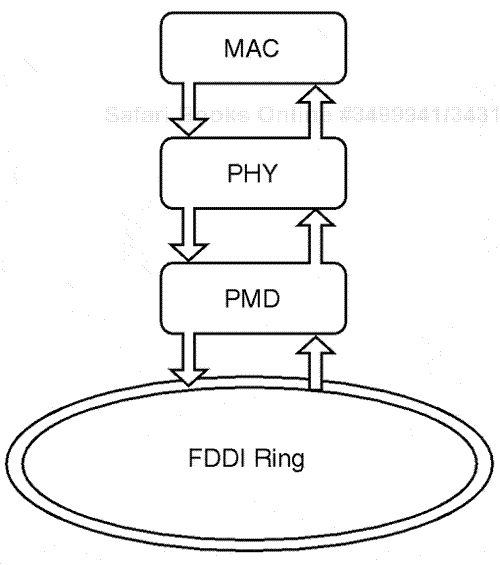
This example represents the processing chain that engages when a FDDI NIC receives a FDDI packet from the medium for handling: The main interconnection of the FDDI NIC operation scheme from the physical medium up through the protocol chain includes a process where signals are either transmitted or received through a PMD layer. The optical signals are then converted into electrical signals that are passed on to the PHY layer for operation. The FDDI PHY layer then processes the physical signals, which are based on FDDI symbols, and translates these into the final FDDI frame or packet format. The FDDI MAC layer processes the FDDI packet and frame field to extract the actual data transferred, which is either passed to the SMT if the data is based on physical operations or to the upper-layer protocol sockets if pure data is being transmitted. Figure 10.8 shows how the internal FDDI NIC internal operational areas relate to the OSI standard model.
The PMD layer is the closest connection point of the FDDI NIC from a station or concentrator as it interconnects to the FDDI main ring fiber loop connection. This is the actual physical media-dependent area of the physical network operation. Key operations are required for the FDDI NIC to convert optical signals brought from the medium or being sent onto the medium to and from the physical electrical format as related to media transmission. An optical signal is used for final transmission on the FDDI medium for overall transfer of data.
Specific technology allows a FDDI NIC to connect to the actual media. The PMD layer includes internal operations that allow for optical signal processing.
These areas include the optical transmitter, which processes the FDDI-applied waveform in a spectral-width format, and also has internal capabilities to operate with a center wavelength operational power meter through a light emitting diode(LED) operation to process through a final laser diode for transmission. Figure 10.9 shows the FDDI PMD operational areas.
The optical receiver circuit provides the same type of circuitry operations as the receiver circuit. Optical bypass switches can also be involved in the interconnection of this type of configuration. The main media type of con- nections normally utilized in a PMD layer can include both fiber and cabling specifications. A standard media interface connection(MIC) can be used, or the standard FDDI (ST) and (SC) fiber connectors can be used (see Figures 10.10, 10.11, and 10.12).
The FDDI PHY layer is the area that provides the internal operations of the circuitry to allow for the optical signals from the FDDI medium to be processed through the FDDI NIC channel up to the protocol-processing layer. In the PHY layer, the primary FDDI operations occur on the FDDI NIC and relate to the interconnection between the PMD layer and the uplinked FDDI MAC layer. Specifically, the FDDI PHY layer is the area where technology operations occur that link the PMD fiber link operations to the FDDI MAC layer frame processing area operations. Figure 10.13 shows the internal operations of the FDDI NIC physical operational area circuits.
The PHY layer allows for the encoding and decoding of the actual physical symbols on the FDDI medium to be processed on reception from the fiber medium and upon transmission from the MAC layer. Having said that, both transmit and receive circuits are active in the PHY layer. On the FDDI PHY layer receive circuit, optical signals are received from the FDDI medium via the FDDI PMD layer on the receive function and then processed through a PHY receive circuit, which then simultaneously processes signals through a 4/5 B signal decoder circuit and through a line state detector. The line state detector interfaces in a parallel operation with the FDDI SMT layer interface. The PHY 4/5 B decoder circuit then processes the signals through an elasticity buffer and into a smoother circuit. The data is then passed up to the FDDI MAC layer.
On the FDDI PHY transmit circuit, FDDI frames assembled within the FDDI MAC layer are set for transmit and are passed to the FDDI PHY layer. The FDDI PHY layer performs an operation to break the frame down into electrical signals and then composes actual FDDI symbols for transmission on the medium. The signals are sent from the FDDI MAC layer to a FDDI PHY layer repeat filter. Next, the signals are processed by a 4/5 B line encoder, which associates the signal with a clocking signal, and then the final signal is passed to the PMD layer for transmission onto the FDDI medium.
In this case of signal transmission and reception, a FDDI NIC will utilize a certain coding on the medium. The encoding for the signal is nonreturn to zero inverted (NRZI) on ones. In this coding scheme, a logical one (1) is represented by a transition from the signal's current operation state to its next state in an interval mode. In the next case, a logical zero (0) is represented when there is no transition for the overall signal for process on the medium. These signals are interleaved through a local clocking signal, and the final signal is processed.
The FDDI MAC Layer is one of the more important areas on the FDDI NIC. This importance results because the FDDI NIC MAC layer is responsible for assembling a packet for transmission and from reception to the upper-layer protocol area chain within a particular FDDI device.
The FDDI MAC layer interacts heavily with the PHY layer and also operates in direct correlation with the FDDI SMT layer. The physical FDDI MAC layer provides four main high-level functions when transferring FDDI frame information to signals on a reverse receive and transmit cycle in and out of the FDDI NIC to the upper-layer protocols, as required.
The following four functions are invoked:
Error checking processes
Address recognition review
Data interpretation of the FDDI frame and packet internal data
Access of the FDDI NIC to the medium
Figure 10.14 shows the internals of the FDDI MAC agent.
The FDDI signals, when being interpreted on a receive process, come from the FDDI PMD and PHY layers and then are passed through the FDDI MAC layer before moving to the upper-layer protocols. When the signals are received on an inbound MAC receiving cycle, error-checking processes activate and compilation starts, where a FDDI frame and packet are assembled for processing. The FDDI MAC layer engages address recognition to verify the source and destination FDDI node addresses. Next, the FDDI layer starts the interpretation of the type of data being presented for processing. The valid data types can include SMT layer data associated with control of the FDDI physical ring or upper-layer protocol data. The FDDI layer starts the interpretation of the class of traffic as the FDDI frame is processed. Any data that needs to be extracted for the SMT layer or for the upper-layer protocols is then separated by the FDDI MAC functional operations.
On an outbound transmit cycle, the FDDI MAC layer receives data from the upper-layer protocol chain processing layer or the FDDI SMT layer. In this case, the FDDI MAC layer then must perform an immediate data-type inter-pretation to assign a class of traffic and to assign the proper addresses and formulate the FDDI frame formatting that will surround the upper-layer protocol data unit or the SMT layer internal frame data. Certain error-checking fields are assigned as active, and the FDDI packet is formed for transmission and processing down through the FDDI PHY layer for signaling transfer to FDDI symbols, and then for final processing through the FDDI PMD layer for the optical signal to be formed for transmission. In the transmission operation, the FDDI MAC layer engages the operational steps for the FDDI node to gain access to the FDDI medium. In this operation, the FDDI MAC layer invokes certain timers required for access. The FDDI access method is presented in detail later in this chapter.
The FDDI SMT layer is an important operational layer that runs in direct parallel with the FDDI MAC and PHY layer operational areas. The SMT layer utilizes certain operations to effect a fault-redundant cross-management of the device nodes as part of the complete FDDI network. Later in this chapter, a full detailed section is presented on the FDDI SMT layer and the effects on FDDI NIC operations.
The FDDI MAC layer actually assigns access methods. When this process occurs, the operation may affect certain FDDI frame operations. The FDDI internetwork architecture is based on the deterministic access that is somewhat comparable to the Token Ring access methodology. For a FDDI device or node to connect to the FDDI ring, the FDDI TTRT must be active and operating.
The FDDI technology allows for the following three types of access to the overall available bandwidth:
Synchronous bandwidth
Asynchronous shared bandwidth
Batch bandwidth
The first class of bandwidth, noted as synchronous bandwidth, is not normally invoked in a common FDDI configuration. If invoked, this would be a case where a device could have complete operation and control over the FDDI ring in a continuous synchronous format. The second class of service, noted as asynchronous shared bandwidth, is a process where the deterministic access method does not engage any priority and all devices with FDDI NIC connections have equal access based on the TTRT.
The third class of service is only applied in the case of a condition where there is leftover bandwidth. In this condition, a specific device will have already transmitted its normal data sequence and then can utilize any leftover bandwidth for engaging batch transfers. This is another mode that is not commonly engaged for general data transfer in most FDDI configurations.
To access the FDDI network, a FDDI NIC card for a device must gain control of the FDDI token. For a FDDI device to transmit data, the device's NIC must capture the token by using extraction stripping process. After the FDDI NIC has captured the token, it performs a combination process where a set unit of data is formed into a frame and processed from the FDDI MAC layer and is then processed through the PHY layer and sent to the PMD layer; a FDDI packet is next transmitted out onto the main FDDI ring. When a FDDI device transmits a data frame out onto the ring, it has control of the asynchronous bandwidth for a short period of time. It cannot hold the bandwidth in an asynchronous mode for a continuous cycle; otherwise it would be considered as operating in a synchronous operation. In the asynchronous process, the FDDI MAC timers associated with TTRT protocol sequencing determine the amount of time that the device can transmit on the FDDI ring before it must release the token back onto the main FDDI loop for other FDDI nodes to utilize the ring for data transfer.
After the source station has completed the process of transmitting data out onto the ring, in most cases it then must release the token out onto the ring so that other devices can transmit data. Certain protocol timers are associated with this type of transmission cycle. A timer called the Token Rotation Timer (TRT) of a device normally monitors the amount of time that a device can actually transmit on the ring as related to when it must finally release the token for other nodes to gain access to the medium.
During most cycles, a device connecting to the FDDI ring just grabs the token and performs a source data transmission on the ring, and then releases the token when it has finished transmitting. In certain other cases, a FDDI- connected device can activate a timer called the Token Holding Timer (THT), which allows a device after completing an initial transmission cycle to again transmit for an additional period of time. In this case, after the THT has expired, the source device must finally release the token to ensure an asyn-chronous operation on the main FDDI ring.
The following example describes a typical FDDI MAC timer interaction. A FDDI station, when interconnected to the ring, invokes a FDDI NIC operation when an upper-layer protocol transmission is required for packet transmission. This also can be invoked by the FDDI SMT layer for physical node ring management processes. The FDDI NIC loads an immediate T_Request (T_REQ) timer value that activates the TTRT process, which then engages the TRT time cycle that the device attempts to use for transmission. The FDDI NIC after loading the T_REQ time value in a register, and completing a process called token bidding,next loads the time value determined by TTRT into the T_Operational (T_OPR) timer register. The T_OPR register actually becomes the individual FDDI station NIC's TRT value. In this case, the NIC now has been assigned a TRT timer value that it will utilize for its transmission time cycle. After the TRT has been activated, the station attempts data transmission. Note that each station performs transmission out onto the ring through the process of utilizing the loaded TRT timer value to engage an assigned data transmission cycle. If the station's data transmission cycles are completed, the station can then utilize any extra time that may be available as based on the original TRT time cycle. Additional time would be assigned to a THT timer, which would be activated and allow for an additional transmission cycle. At this point, other timers would interrelate to the final transmission time cycle, such as the T_MAX and T_MIN timers, which may invoke a station to imme-diately release a token, if required.
Assume, for example, that one station (B1) FDDI NIC is set at a TRT of 10ms and three other stations are bidding with the station to determine the final TTRT of the ring. If the first station is labeled as B1, after the token has been received by station B1 and a data frame has been composed, the B1 station would start the transmission. It would transmit onto the ring and send one FDDI frame for a complete cycle. After its THT timer has expired, it would then release the token out onto the ring so that another station could transmit.
If only eight months of time were utilized for transmit, that would mean that its token holding timer would hold an additional two months for transmission. Depending on protocol operation, the station could release the token immediately or transmit for another two months. If for some reason it attempts to transmit and eventually the token holding timer expires, other timers can be activated, such as T_MIN and T_MAX, and the final Timer Valid Transmission (TVX) will activate an immediate release of the token out onto the ring so that stations B1 and B2 can to transmit.
Various contention processes occur on the FDDI token passing scheme when required. These contention processes are involved with the final TTRT as determined by all the devices as they are configured on the FDDI ring for communication. All the FDDI device NICs interconnected to the ring must participate in a process called token bidding, which determines the final TTRT utilized across the ring.
The various manufacturers of FDDI NICs might have specific preset values designed into the FDDI NIC card hardware and software structure that allow for a different T_REQ and T_OPR values to be set. These values can affect the final timer for bidding, which is called T_BID, and the final TRT of a device's particular NIC. The values for T_REQ timer and the loaded T_OPR timer can vary from manufacturer to manufacturer. Specifically, certain FDDI NICs can attempt to transmit faster than others and will have certain targets in design for how long they will hold the token when transmitting on the ring before they release the token as compared to other FDDI NICs. Due to this possible variance in FDDI NIC technology, it is important that a common time be assigned for the main FDDI ring TTRT value. To ensure that the process is equal for asynchronous bandwidth control, the token bidding process is engaged.
The following is a description of a typical token bidding scheme and data- passing process as it would occur on a FDDI medium in a real network configuration. All stations on a FDDI ring normally must go through a bidding process and a claim process to connect and become an active station on the FDDI network. When a station is powered up and is the first station on a ring, its T_REQ loads the T_OPR operational value register, which determines its TRT. The T_REQ value is also loaded in the T_BID register for each station when a device is connecting to the ring that must go through a bidding process.
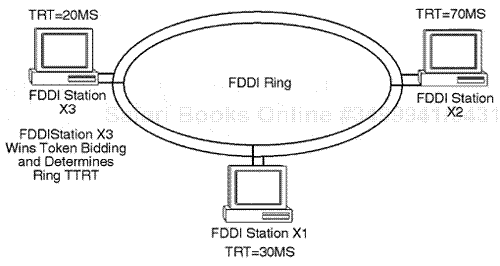
Consider this example: Station X1 activates and connects to a FDDI network and becomes the first station connected on the network. Immediately after this process, stations X2 and X3 can become active as related to connection for the FDDI medium. Assume that station X1 transmits an initial FDDI MAC Claim frame on the ring based on a T_REQ and T_BID value set that determines the a final TRT of 30ms. If station X2 receives the Claim frame from station X1, it activates an immediate bidding contention. Station X2 compares its address to the incoming station from X1.
If the destination address of the frame does not match the station of X2, it next compares the source address to the incoming frame. If the address of the inbound source frame from station X2 has a high or low address, this may then activate other timers. The actual timing values are compared also in the frame structure, and the T_REQ values are compared. Station X2 checks the frame control field and examine the Frame Control field for the address state to identify whether the X1 station is using a long or short address identification for a 16- or 48-bit address setting.
Station X2 next compares its Destination Address field to the incoming frame from station X1. If the destination address of the frame does not match the station X2, it next compares the source address of the incoming frame to its own address, and then it sets the higher flag if the address of the Claim frame is higher than the address of the station; otherwise, it sets the lower flag. A higher flag setting indicates to the MAC state machine that the Claim frame with the higher address was received, and the lower flag indicates a lower address. The first four bytes of the received frame contain the T_BID value of station X1, which is examined next. It compares stations X1 T_BID value at 30ms with its own T_BID of 70ms.
Its own value is higher and it sets the higher flag indicating the higher value. Station X2 validates that the frame from station X1 is legal in size. This frame-check sequence operation is verified. In this case, because a higher claim comparison has been made, the receiver process in station X2 indicates that its transmitter is set to repeat the frame and it does so by setting a unique flag called higher claim. Station X2 then sets its T_NEG = T_BID received and repeats the station X1 Claim frame on the main FDDI ring. In this case, station X2 is not bidding or is in contention. Station X1's Claim frame next reaches station X3, which is in a quite flat state. Station X3's NIC state machine operation applies the same operation as X2 did in the preceding process. Specifically, station X3 compares the T-BID received from station X1 at 30ms with its own T_BID at 20ms and finds it has received a lower-claim complement number. Then it sets the lower-claim flag, indicating to the transmit state machine to strip the station X1 Claim frame from the ring and transmit its own Claim frame.
At this point, station X1 is losing to station X3 and station X3 is starting to win the bid process in determining the ring final TTRT time. Station X1, which was transmitting its own Claim frame, receives the Claim frame from station X3. After the station X3's Claim frame is received and checked for validity, station X1 defers the bid process and drops out as a bidder and repeats X3's Claim frame. Station X1 sets its T_NEG timer to equal 20ms, as noted from station X3's T_BID as received, and sets its higher-Claim frame, and its NIC state machine stops transmitting its own Claim frame and repeats the Claim frame from station X3. At station X2, a similar situation occurs and it changes its T_NEG timer, which was noted at 30ms from a previous contention with station X1 to a resolved T_NEG timer of 20ms, acknowledging that X3 is the lowest value and is determining the final FDDI ring TTRT.
When Station X3 receives back its own Claim frame, it knows that it has won the claim process. At that point, station X3 sets a receive state machine of "My Claim Flag Indicator" for the transmitters to stop transmitting any Claim frame and notes that it has won the claim process. The station X3 transmitter then sets its T_OPR timer to T_NEG and resets its TRT to T_OPR. Station X3 clears its late counter of any value and then issues a nonrestricted token. At this time, station X3 has won the claim process and it may not immediately begin transmitting data before issuing the token. The first token rotation is usually engaged just to synchronize the various timers and flags in the different FDDI stations and to notify all active FDDI stations that the claim process has been successfully terminated (see Figure 10.15).
Note that at times it is possible that the FDDI cross-ring claim resolution may occur where certain stations may bid with the same T_BID. If equal T_REQ bids are present from two or more stations, the longer address configuration usually takes precedence over the final transmission. A 48-bit address FDDI Claim frame with a T_REQ bid of 60ms usually wins the bid against a 16-bit address in FDDI with a 60ms T_BID and T_REQ bid set.
All FDDI stations when transmitting and receiving data perform an extensive data- and error-analysis process. All FDDI NIC MAC agents verify destination and source addresses, and examine a FDDI frame transfer process for proper structures as to CRC alignment and FDDI frame integrity (see Figure 10.16).
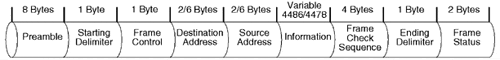
The following is a brief description of the FDDI MAC frame format specifications. The FDDI token format engages a starting delimiter with a Frame Class field with an additional ending delimiter. A FDDI frame is composed of a a maximum of 4500 bytes, which includes 8 bytes of preamble. The Preamble field is engaged for clock recovery purposes and for the synchronization of the incoming and outgoing symbols as processed through the FDDI PHY receiver and transmission circuits. The Source and Destination Address fields in a FDDI frame normally take up 2 to 6 bytes each, depending on whether the station is engaging a 16-bit addressing scheme or a 48-bit addressing scheme, which in turn affects the final Information field size (which varies between 4478 to 4486 bytes). Figure 10.17 shows the data frame format.
The configuration fields in a FDDI frame are set as follows:
Preamble (PA). . 8 bytes in length.
Starting Delimiter (D). . 1 byte in length.
Frame Control (FC). . 1 byte in length.
Destination Address (DA). . 2 to 6 bytes, depending on 16- or 48-bit addressing.
Source Address (SA). . 2 to 6 bytes, depending on 16- or 48-bit addressing.
Information (PDU). . Variable 4478 bytes to 4486 bytes in length.
Frame Check Sequence (FCS). . 4 bytes in length.
Ending Delimiter (ED). . 1 byte in length.
Frame Status (FS). . 2 bytes or more. This field includes a frame error indicator, address recognized indicator, and a frame copied indicator.
As discussed earlier, a FDDI NIC layer allows for control of the FDDI MAC processes. That layer is somewhat similar to the Token Ring MAC layer. The FDDI Station Management (SMT) layer is a higher-layer type of operation that intercommunicates with the FDDI MAC and PHY layers. The SMT layer also has extensive capabilities for cross-device management of the FDDI network as a whole. The FDDI SMT interconnects with a PHY layer by engaging certain physical connection management processes. These processes involve operations, such as link junction–level management, that further invoke operations such as "station initial state open," "single active to form connection," "network response to exchange," "synchronize link," and "station link active." In other words, the FDDI SMT layer can invoke functions that operate on interaction with the PHY layer but affect the PMD layer. These SMT-to-PHY processes are invoked by the physical connection management operations that reside in the SMT layer operational cycles (see Figure 10.18).
The physical connection management process can also monitor the state of the FDDI ring by invoking link confidence tests and link error monitoring tests. These special operations allow for monitoring of the FDDI NIC insertion cycle, the FDDI station configuration mode, and also are used for the monitoring of the FDDI NIC as it is interconnected to the network. Actual line states can be monitored by a device's SMT layer, which can invoke certain signals through the PHY layer to generate operations on the PMD layer. The line states that can be monitored by the SMT layer are operational states such as active line state or unknown line state and other states related to the FDDI medium connection process (see Figure 10.19).
The SMT layer can also perform management on the FDDI ring with the ring node management sublayer operations. In this case, the SMT layer interacts with the MAC layer on the FDDI NIC. The SMT layer is communicating mainly to the MAC layer. This is a functional area of the SMT processes that ensures that a FDDI NIC station is inserted into the FDDI ring and is properly configured. Certain operations are performed to ensure that device key statistics are communicated through SMT channel circuit operation functions such as configuration management, path functions operations, entity coordination management processes, and ring management processes. In this particular area, important functions are monitored such as the state of the FDDI NIC as related to FDDI MAC operations for stability. Directed beacons and subbeacon isolation operations are monitored, along with trace operations and duplicate address isolations. These operations are described in detail in the section titled "Methods for Analyzing and Troubleshooting FDDI Networks," later in this chapter.
At the network level, the SMT layer can monitor the node-to-node communications on the FDDI ring as a whole. Certain types of communication related to operations are performed; these are somewhat similar to the Token Ring MAC layer operations on a Token Ring network.
On a FDDI network, the SMT layer can invoke key processes, including the following:
Station Management Neighbor Information Frame (NIF)
Station Information Frame (SIF)
Station Management Layer Echo Frame (ECF)
Station Management Layer Resource Allocation Frame (RAF)
Station Management Request Denied Frame (RDF)
Station Management Layer Report Frame (SRF)
Station Management Parameter Management Frame (PMF)
Station Management Extended Services Frame (ESF)
The following sections describe how the SMT layer can engage functions that affect the complete FDDI ring operation (see Figure 10.20).
In this case, the SMT layer engages operations through the FDDI MAC layer to form certain frames that invoke cycles for Neighbor Notification. The Neighbor Notification protocol is engaged when a new station enters the FDDI NIC ring. The new station should participate in Neighbor Notification by sending an SMT Neighbor Information frame (NIF) to request that it can become part of the operational FDDI ring. A FDDI NIF frame request can include information about the upstream and downstream neighbors (UNA and DNA).
Certain cycles occur in a FDDI NIF operation: Normally, a station such as H1 transmits a request that includes a NIF identification onto the ring. Station H2 receives the NIF request and transmits a NIF response onto the ring identifying its own address. Station H3 also receives the NIF request and responds with its address. This process continues around the ring. This cycle allows for the new device inserting on the ring to be aware of the other devices. The process also allows the complete FDDI ring addressing scheme to be recycled so that all active stations are aware of the upstream and downstream neighbor addresses associated as to interconnection on the FDDI loop. This process is engaged by the FDDI SMT layer, which forces the FDDI MAC layer to transmit the necessary NIF frames, as required.
The FDDI SMT layer can also perform a process known as generating Status Reporting frames (SRF) by engaging the Status Reporting Protocol. When unexpected or dynamic changes on the ring are encountered, the changes can be communicated back and forth to different nodes via the SRF protocol sequence. These are very important frames from a protocol analysis perspective.
The FDDI SMT layer can engage a process called Parameter Management Protocol. In this operation, an SMT Parameter Management frame (PMF) can be sent out for ring management purposes. In such a case, the FDDI SMT engages a PMF cycle through the FDDI MAC layer. The FDDI MAC layer transmits an SMT PMF with "get request" subvector on the main ring to a specific device. In this type of operation, another station can respond with a PMF with a "get response" subvector to the source querying station. This inherent SMT operation engages a management cycle based on a query-and-response cycle utilizing the Parameter Management Protocol process.
SMT Echo frames are engaged to perform an operation similar to an ICMP ping. The FDDI SMT layer can invoke a FDDI devices's NIC MAC layer agent to transmit an Echo request frame to a certain device. The device receiving the SMT Echo request frame normally then responds with an SMT Echo reply frame.
SMT frames can be generated for advertising SMT resources as available between nodes. In such a case. the FDDI SMT layer can generate SMT Resource Allocation Frames (RAF). The SMT RAF can be engaged to cause a FDDI NIC to process communications as to the resources available on the network to determine the capability for asynchronous or synchronous transfer.
SMT frames can be generated for engaging an advertisement of extended services available in communication between FDDI nodes. In such a case. the FDDI SMT layer can generate SMT Extended Services frames (ESF).
In certain cases, when a FDDI device cannot respond to a certain type of SMT frame, it can transmit an SMT Request Denied frame (RDF) and ignore the requested SMT operation. When a RDF frame is captured with a FDDI protocol analyzer, it may indicate an operational incompatibility with an SMT operation between multiple FDDI active devices or NICs.
Within the SMT layer operations, there is also the capability for the status of a FDDI NIC as related to its operational mode and general configuration on the FDDI network to communicate certain key information through SMT Status Information frames (SIF). The FDDI SMT layer on one NIC can communicate to the SMT layer on another NIC to determine certain communication cycles on the ring through SIF frame formats. This is a communication layer capability unique in the FDDI operations and allows for unique inherent management capability through the FDDI SMT layer.
The FDDI Frame Information field can encapsulate an internal field that carries the Station Management layer Information frame data and the applied header. The FDDI SMT layer assembles a unique protocol data unit for the SMT process and inserts it within the data field of an SMT layer frame format (see Figure 10.21).

Figure 10.21. The main FDDI frame format can carry the required SMT information to effect an SMT process on the FDDI network.
The following SMT fields are engaged:
SMT Frame Header. . Total normal standard length, 20 bytes (7 fields engaged).
Field 1. . SMT frame class, 1 byte. This field identifies the SMT frame-based operation ( NIF, SIF, ECF, RAF, RDF, SRF, PMF, or ESF).
Field 2. . SMT frame type, 1 byte. This field identifies whether the SMT frame is an announcement, a request, or a response.
Field 3. . SMT version ID, 2 bytes. This field indicates current SMT version. This varies from time to time accordingly to industry releases.
Field 4. . SMT transaction ID, 4 bytes. This field displays an SMT request/response sequence.
Field 5. . SMT station ID, 8 bytes. This field identifies a FDDI station ID.
Field 6. . SMT PAD, 2 bytes. This field marks the alignment of the SMT frame.
Field 7. . SMT data length, 2 bytes. This field identifies the SMT data field length.
The FDDI SMT layer is extremely important from a protocol analysis standpoint. If an analyst is monitoring a FDDI backbone ring or a LAN ring that is utilizing SMT operations, the SMT layer may inherently communicate some of the key configuration and operational issues that may be taking place on the FDDI medium. It is important during a network baseline study for an analyst to filter the SMT layer by utilizing a protocol analysis approach described later in this chapter. It is also important to finally note that there is a heavy interaction between the FDDI SMT layer and FDDI MAC layer.
When analyzing and troubleshooting a FDDI network, it is important to first ensure that the analyzer that is going to be utilized is completely FDDI compliant. Because both a primary and backup ring connection is possible in configuration, based on the FDDI ring specifications, it is important to ensure that an analyzer can connect to both rings. Specifically, because variances in the FDDI connection types can exist—as related to the options of MIC, ST, and SC connections—it is important to ensure that the physical medium-dependent connectors are available along with the analyzer tool connection cables.
When analyzing a FDDI LAN, it is important to ensure that the network is monitored for high efficiency throughput, low delay, and latency. This is necessary because, in most cases, a FDDI network is providing backbone technology capability. It is important that the network delay be minimal when devices communicate across the FDDI medium. The queuing delays must be minimal and the final transmission time must be executed in a mode that allows each device an equal asynchronous time cycle. The final endpoint-to-endpoint transfers must be achieved at a high effective throughput level.
As mentioned previously, various timing factors are important in each FDDI NIC, such as a queuing delay, because they affect final transmission capability. It is important to ensure that FDDI NICs receive frames properly in a rapid fashion, process all frames through upper-layer protocol cycles, and then the NIC must transmit all responses back rapidly. Usually standard transmission times apply, based on the TTRT, finally determined through token bidding and associated with the T_BID and T_OPR timers and variable registers of each specific FDDI NIC interconnected to the ring. As noted earlier, heavy interactions may occur, associated with different FDDI NICs as they activate a connection to a main FDDI ring. If a FDDI NIC has an extremely low or high T_BID and T_OPR value finally loaded into the TRT, this may affect the overall operation of the complete FDDI ring. It is important that an analyst understand that each device on a FDDI ring must be closely monitored during events such as token bidding, claiming, and neighbor notification via protocol analysis. A standard transmission time normally takes place when a FDDI NIC is transmitting on a ring. A FDDI NIC can normally transmit within 80 nanoseconds-per-byte range. This translates to approximately a 32 to 38 milliseconds time period to transmit a 4500-byte- or 9000- symbol-based frame. Although this is not considered a standard, it is considered a common goal when a vendor designs a FDDI NIC. This range for transmission ensures low latency and low propagation delay on the internetwork.
The minimum ring latency should always be no more than 100 microseconds. In most cases, a FDDI ring complete with all devices active should provide a much lower ring latency level than 100 milliseconds; and in most cases, the ring latency should be no more than approximately 3.4 to 10 milliseconds. This is the normal ceiling level for ring latency.
The following section presents the key steps required to properly perform a network baseline on a FDDI network.
When analyzing a FDDI network, it is important to understand that the network is based on a high data rate, at 100Mbps minimum, and has the capability to perform at a high throughput level. The main focus of a FDDI baseline is to perform the network statistical measurements that will enable the analyst to identify any performance-inhibiting factors present within a FDDI network layout or design. The FDDI network topology should provide the highest throughput and performance foundation so that upper-layer protocols have a strong foundation for throughput and performance for general data transfer. With this in mind, certain measurements apply to a FDDI network baseline.
The following is a brief review of the workload characterization measurements that an analyst should use in a FDDI analysis study.
When performing bandwidth utilization measurements in a FDDI network, keep in mind that it is a deterministic medium. Because it is deterministic and operates somewhat similar to the Token Ring environment, it is important to understand that utilization levels must be monitored in a specific manner. Utilization levels can be achieved at a higher level and the network will still sustain operations because of inherent fault-redundant operations and sequencing processing that occur at the FDDI MAC layer and the SMT layer. These layers assist in allowing the FDDI network to continue to operate in a stable fashion even when high utilization loads impact the medium. The key factor is that if there are high number of nodes on a FDDI network and utilization is showing high peak utilization saturation, it may be beneficial to consider whether there would be any options as to segmentation. There may be possible advantages in breaking up a FDDI network into more separate networks by implementing a FDDI router, switch, or bridge between the networks. The segmentation process may allow each device node on the FDDI rings to receive a more even distribution of the token from the deterministic process. This would only be required on extremely high saturation levels above 80% to 90%. Keep this in mind that all standard utilization measurements apply in a FDDI baseline study, such as average utilization, peak utilization, and historical measurements.
It is important to closely monitor node-to-node by utilization when examining a FDDI network. This is necessary because on a FDDI network there may be concerns as to the overall token passing scheme if certain devices have any problem circumstances in the FDDI NIC that might cause a high token rotation time or a negative effect on the TTRP of the complete ring. By closely examining node-to-node by utilization, an analyst might quickly determine whether any node is absorbing a high amount of bandwidth. It is possible that the physical FDDI NIC operation and design of the NIC is causing this occurrence. When analyzing the physical FDDI medium, an analyst might further isolate the problem to a specific node that exhibits an extremely high bandwidth level, leading the analyst to the exact cause of a problem (in this case, related to FDDI cross-ring performance on the deterministic medium).
When performing protocol percentage measurements in the FDDI network, it is important to extract any high levels of FDDI protocol percentages in the MAC or SMT layers. If percentages above the 4% to 5% level are seen in the MAC protocol, or above 6% to 7% in the SMT protocol, the composition of these protocol types should be further investigated. Specifically, a detailed analysis of the MAC processes and the SMT management processes should be performed. If extremely high levels of the MAC or SMT layers are noted, this may indicate a FDDI ring that is moving through states considered nonoperational or recovery states that require further physical layer analysis.
The next area to focus on during analysis of a FDDI ring is related to a basic monitoring process of the physical layer. Monitoring the physical layer on a FDDI ring requires a close understanding of the FDDI MAC operational timer processes and the FDDI SMT layer processes.
To closely examine the FDDI physical layer, an analyst should engage a FDDI protocol analyzer and activate a filter in a capture mode for both the FDDI MAC layer and the SMT layer. Some protocol analyzers may require the activation of the FDDI Void and Claim capture filter along with the general FDDI MAC and SMT filters, because these are sometimes considered separate on certain analysis platforms.
An analyst should examine any MAC communication from the FDDI NICs to other FDDI NICs, along with any SMT layer communication between NICs. This examination enables an analyst to understand how the FDDI NICs are connecting to the FDDI medium and also how devices are participating within the FDDI main ring standard TTRT. Any FDDI NICs that have high effected TRT or high T_OPR timers may be able to be identified as devices they are causing performance problems on the ring. Any FDDI NICs or FDDI concentrators having hardware problems may be able to be identified by excessive levels of the FDDI claim processes.
High void frame rates may indicate delays in translational frame transfer from one topology to another, such as FDDI to Ethernet. Any high-traffic occurrences in the SMT layer usually shows the subframe type for SMT sublayer types, such as SRF frames that can be further decoded to analyze the problem encountered. Based on the analysis performed in these areas, an analyst may be able to identify a physical FDDI problem and address the issue either by replacing or reconfiguring a device, and then by re-analyzing the LAN.
Other key technical notes are important when examining the FDDI physical layer operations and processes.
An analyst must closely monitor the standard FDDI token rotation processes. When analyzing the physical layer of a FDDI network, an analyst should closely monitor the actual ring latency. As noted, in most cases the FDDI ring latency should be less than 3.5 microseconds for general operations. The ring latency should be no more than 100 microseconds. This allows for a proper asynchronous spread of transmission. Also, each device should not have to transmit and hold the token for any more than 80 milliseconds for normal transmissions. Any level higher than this would be extremely high. The low timing value for a device that is going to be transmitting on a FDDI ring should not typically be lower than 8 milliseconds. The spread between 8 and 80 milliseconds is key, because variances do exist between the various FDDI NIC cards available. When monitoring a FDDI ring with a protocol analyzer that can engage a latency timer that will monitor token rotation time across the ring, it is important to note that the token rotation time should be no higher than 100 microseconds between FDDI NICs. When a FDDI NIC is attempting transmission, the time for transmission including the transmission and the token holding timer operation and final release of the token should be no more than 8 to 80 milliseconds. Typically, these timing levels are at the lower end of the spectrum.
After the transmission areas have been monitored via network analysis, an analyst should take a step back and take a bird's-eye view of the timing situation. Again, the key is low latency and high performance and high throughput on a FDDI technology. If problems are seen in the TRT or the amount of transmission timing, it is possible that such occurrences affect the overall performance levels of the complete ring. If higher timing levels and values are identified, the analyst may need to review further a FDDI NIC or the NIC software drivers.
After these areas have been reviewed, the analyst must next use a protocol analyzer on the FDDI medium and invoke a general FDDI MAC capture or display filter, depending on the mode of analysis. If the data has already been captured in one large trace file, the analyst can invoke a display filter to view the MAC layer. Certain FDDI MAC operations are key when reviewing the FDDI ring.
The following types of processes should be closely reviewed with a FDDI protocol analyzer when analyzing a FDDI ring for physical layer analysis of the MAC and SMT layer process cycles.
After a MAC layer is operating in a FDDI beacon state, a directed beacon may be active. When a directed beacon continues to occur, it can be considered a stuck beacon operation. After a stuck beacon operation occurs, the NIC itself may remove a fault within the node from the FDDI ring. This could cause the FDDI device to move into a FDDI trace function, which performs a testing of the device NIC.
In a trace function, the device encountering a stuck beacon operation performs a loopback path test. If the device passes that test, the device reenters the ring. The trace operation usually isolates the problem to a fault domain.
On duplicate address concerns, the SMT functions activate to assist in detecting situations related to duplicate addresses. Such situations can prevent a ring from becoming fully operational during MAC claim and beacon processes. When situations arise in which duplicate stations are present on a FDDI network, it is possible that more than one station might win the claim process and issue a token. This is more likely to occur if stations are utilizing 16-bit addresses, which are locally administered. With 48-bit addresses, this normally does not occur. If a duplicate address occurrence takes place, a jam beacon may be present in the analysis data of the FDDI ring.
After the FDDI MAC layer analysis has been completed, the final focus before moving to the upper-layer protocols is to analyze any SMT layer operations taking place on the ring. These types of operations include key areas that require further analysis in the SMT layer.
An analyst should always perform analysis of the Neighbor Notification Protocol(NNP). This may show conditions where certain devices may not be participating in the neighbor information process. If a certain device is not transmitting NIF frames, that may indicate a problem with the FDDI NIC.
The SMT SRF-type frames may carry unique data about a node's operations and are a key factor in FDDI physical layer analysis. The SMT layer SRF Link Confidence Test errors may indicate that a FDDI NIC cannot insert upon the ring. Through analyzing SRF frame via network analysis, the device that cannot insert can be identified. The SMT layer SRF Link Error Reporting Errors frames may indicate a problem with the flow of traffic through a port in a FDDI station NIC or concentrator. The SMT layer SRF MAC Errors frames may indicate a FDDI NIC cannot process a frame through copy functions or a frame is invalid and in error, or a duplicate address found. These conditions can identify possible misconfigured FDDI station NICs or concentrators. The SMT layer SRF Trace frames may indicate that a certain FDDI NIC or concentrator is operating in a fault mode.
The SMT layer assists in reporting on high FDDI MAC claim rates. High FDDI MAC claim rates indicate a constant change in the overall token bidding scheme and the ring order. The SMT layer can also assist in reporting on the frequent occurrence of stuck beacon and directed MAC frames. If a directed or stuck beacon frame is captured, the source device should be isolated and the analyst should replace the FDDI NIC or concentrator and the ring should be re-analyzed. The SMT layer may also assist in the reporting of trace occurrences. If the trace function is active on a FDDI ring, there may be conditions where a device is isolating a fault domain. An analyst should note the source and destination addresses to mark the fault domain.
The processes previously noted are the most important areas to analyze during a standard FDDI network baseline process. The analyst should also apply a ring performance analysis approach as required. Chapter 4, "Quantitative Measurements in Network Baselining," and Chapter 5, "Network Analysis and Optimization Techniques," discussed this process when the concepts for measuring effective throughput and timing were introduced. Based on a full stability review of the FDDI physical layer showing a positive output, an analyst can then move to the upper-layer protocol analysis step, which is described next.
Based on initial workload characterization steps being performed in a positive manner, an analyst can then move to analyzing the upper-layer protocols. This is where an analyst closely focuses on the FDDI medium from a full analysis perspective and examines the upper-layer protocol areas. In this case, the analyst should examine the protocol data unit carried by the FDDI frame by utilizing the methodologies presented earlier in this book to perform a full workload characterization review of the FDDI packets. This completes the approach necessary to analyze a FDDI medium in a positive network baseline process (see Figure 10.22).
The FDDI LAN topology is extremely fault redundant. When applying a proper network baseline approach, an analyst can perform the required methodology and extract the relevant workload characterizations such as utilization, protocol percentages, and associated physical analysis techniques to ensure that the ring is stable. If problems still exist after the ring has been verified stable, these problems most likely reside in the upper-layer protocol area.
If problems are located on the FDDI physical ring, they most likely will show in the physical layer MAC analysis or in the physical layer SMT layer analysis reviews at the network baseline stage. Further analysis of any other FDDI specifications may be required, as related to the variances possible because of manufacturer-specific designs and layout configurations.
The most important point to be made in this chapter is that most FDDI issues can be resolved by analyzing the MAC and the SMT layers, and the upper layers can be focused on from a main network baseline perspective.
The Fiber Distributed Data Interface (FDDI) architecture allows for a network topology architecture that is extremely fault redundant, but that can also operate at an extremely high data rate. The FDDI data-rate design is much higher than standard topology ring architecture, such as the Token Ring specification. FDDI allows for a 100Mbps data rate on a single ring configuration and in custom dual configurations can allow for up to 200Mbps data-rate transmissions. Further specifications on the FDDI architecture and general topology specifications are presented later in this book. The discussion now focuses on a specific case study based on FDDI analysis.
The LAN Scope analysis team was contacted by a client who was experiencing excessive performance problems on a small FDDI backbone ring. Although the ring was small as to node-connection count, it was still a critical main ring for database access at the company's headquarters.
Upon arriving at the site, the LAN Scope analysis team immediately held an entrance briefing to review the FDDI ring configuration and specification. The ring was based on a 24-device connected configuration. The FDDI ring was operating in a normal fashion until several months prior to our engagement. The ring recently started to exhibit performance problems after two new database servers had been introduced into the facility.
The main facility internetwork was based on a split Token Ring and Ethernet shared architecture for user access through different floors of the facility for general operations. The FDDI ring in question contained the main file servers that were used for access to a custom database application for product tracking related to the site business operations. The applications that were experiencing slow performance were originally designed to operate on a digital VAX environment. The host environment for the application at this site was configured with Digital Equipment Company (DEC) mini-computers that were used for operations on this particular ring.
The NICs were all originally based on connection to a DEC host platform. Two new custom hosts of a specific server type were brought into the facility. The new host hardware platforms were designed to support a new type of the database being used at the facility. The vendor of the new database also brought the hardware configuration for the host as part of the package platform for the company.
This customer was a manufacturing company based in Detroit, Michigan, which developed a specific type of motor part having to do with infrastructure for engines used throughout automotive manufacturing plants in the United States.
Upon arriving at the site and meeting with the internal MIS team, the LAN Scope analysis team reviewed the general configuration. The internal MIS team immediately informed us that the two new database servers were the cause of the problem. Our initial focus was not to examine these servers as to the specific cause, but to generally review the FDDI ring from an initial baseline perspective, and then to closely examine the servers' operation (see Figure CS13.1).
We first connected a network protocol analyzer configured for FDDI topology analysis to the main FDDI ring. We noted the important workload characterizations such as utilization and protocol percentages as an initial focus. We observed that the average ring utilization was only 2% with a peak of 12% for 2.1 seconds as related to utilized capacity. The protocol percentages were normal, with DECnet showing at 70% and NetBIOS at 10%, and a TCP/IP showing at 20%. We immediately identified that there was a fluctuating percentage of Station Management Protocol (SMT) for FDDI at the physical layer, noted between 2% and 12%. Upon our review of the protocol statistics, this appeared abnormal.
Based on this concern, we then examined the physical layer of the FDDI from a general operation perspective. We set filters to examine physical FDDI beacon frames, Medium Access Control (MAC) beacon frames, claim frames, void frames, and general SMT types for conditions such as examining SMT neighbor information frames(NIF), SMT status reporting frames (SRF), and other conditions in the station management protocol category.
Our analysis immediately showed that the MAC layer appeared to be stable. There were no excessive beaconing conditions, claim conditions, or excessive void rates at the FDDI MAC level.
The higher percentage definitely appeared to be in the SMT frame-based layer. It appeared that the SRF count was high along with a nonstable NIF configuration sequence occurring upon operations. We also noticed that the claim rate appeared to be occurring on a more frequent basis than normal at the MAC level.
We then started to decode some of the general FDDI physical layer frames that were present. When we examined the FDDI frames for general operation information, we noted that upon NIF operation request and claim rate occurrences, all the DEC machines showed a requested Timed Token Rotation Time (TTRT) of 10.1ms, which appeared to be well within normal specifications. However, it was immediately evident that the valid transmission time and final determined bid time was as high as 41.9ms. This was excessive for general operations for FDDI claim sequencing.
We immediately decided that we should further examine the general claim process on the ring. The claim process in FDDI is a process where the stations across a FDDI ring can bid to determine the TTRT. This determines the amount of time that each station is allocated to transmit on a FDDI ring in an asynchronous process for equal communication, and also the time available for an additional transmission for a node based on the Token Holding Timer (THT), if additional time is required.
We noted that most of the stations on the ring in the original DEC configuration were using a token operational loaded timer of approximately 10ms for a Timing Bid (T_BID) operation. This T_ BID configuration is typically loaded upon the original configuration of a bid cycle.
After the two new devices had been introduced into the facility and their database server operations had become involved in the bidding process, they appeared to bid at a sequence rate that showed an intermittent change in bidding operation from 8.2 seconds. This rate rose intermittently and flagged solid at 41.9 seconds. This appeared to be an event that recurred and the nodes appeared to fluctuate with regard to their timing request on the token bidding processes. Every time this happened, it appeared that there was also an additional claim operation on the ring. This was odd. It showed that eventually what was occurring was that the new host station FDDI NICs were causing intermittent fluctuation in the complete bidding process and transmitting claim frames at an intermittent, different level and causing an abnormal operation. Other stations on the ring, such as DEC stations, would stabilize at a 10.1ms TTRT at a lower level and then eventually would increase into a higher level of 41.9ms.
Our investigation showed that because of the inconsistent claim operation of the new host environment NICs based on the database servers, their T Operational Timers (T_OPR) might be problematic. During the first rotation, we noted that they initialized at an 8ms level, but on the second rotation they changed their T_OPR and T_BID timers to approximately 41.9ms. We observed that eventually the actual physical level of FDDI was resetting at an asynchronous level across the ring at 41.9ms and continuing to operate for a period of time during which upper-layer protocols would operate on a ring that was utilizing a final negotiated TRT of 41.9ms.
We then verified our analysis of this condition and saved it in our trace analysis results. We then contacted the vendor of the new database application. They contacted their hardware vendor, and through further investigation it was determined that the particular FDDI NICs had a problem that caused this exact type of condition. Eventually, we even found conditions where a FDDI MAC Beacon Trace event was engaged and affected by the fluctuating TTRT situation. This condition, as analyzed, was abnormal and acknowledged as so by the FDDI NIC vendor. The new FDDI NICs were shipped to the facility and the LAN Scope analysis team oversaw the implementation of the new cards.
We re-analyzed the FDDI ring and found that the requested T_BID and TTRT and associated TRT of the new FDDI cards was 8ms and always consistent. This allowed the negotiated TTRT on the ring to eventually become 8ms and the valid transmission time to be much lower across the FDDI ring.
General operational performance immediately increased across the facility and appeared to show stable operation.
This type of analysis would not have been possible without discrete protocol analysis review and except through the method of reviewing the FDDI workload characterizations.
Many of the MIS support team members were concerned that periodic peak utilizations were occurring and were not being captured in the management systems. They also thought that there were perhaps too many devices on the ring.
In this case, it was a simple condition of two new FDDI NICs that were operating abnormally during the token bidding process of the claim cycle of FDDI.
In this particular case, our network baselining methodology proved to be 100% successful in verifying the site's operation and stabilizing the facility to a higher performance level.