Chapter 1. Evolution of the Internet of Things (IoT)
Topics covered in this chapter include
■ Defining the Internet of Things
Barely a week passes without another fear-inducing news headline painting a picture of an inherently insecure Internet of Things (IoT). Whether you love, hate, or even fear IoT, it is becoming an inescapable reality and is changing how we behave and interact with the world around us. IoT expansion continues, with Gartner predicting 26 billion and Cisco predicting 50 billion “things” connected to the Internet by 2020, although whether these numbers will be achieved is a hotly debated topic. This is in addition to the estimated 7–10 billion smartphones, tablets, and PCs we use in our daily lives. The main driver for this is not human population growth; it is the fact that devices we use every day, including cars, appliances and lights, and operational technologies such as those in manufacturing facilities or power utility substations, are becoming connected entities around the world. This world of interconnected things, machines, and people has arrived—and is here to stay.
As technology becomes an integrated part of life, we inevitably become more dependent on it. This dependence makes us vulnerable if technology fails. Technology thus needs to be as reliable, safe, and secure as possible.
Despite the potential benefits of new technology for businesses, economies, the environment, and our health, popular focus firmly remains on keeping the “bad guys” from gaining easy access to our devices and data. The media continue to suggest that the prevalence of connected gadgets, appliances, homes, and cars makes us vulnerable to cyber attack, eventually catapulting us toward a dystopian world in which we will inevitably succumb to security breaches no matter what prevention measures we take.
IoT is an incredibly broad and often generalized term that can be applied across businesses, industrial verticals, transportation, and the home. To manage IoT deployments, IoT platforms exist across all these areas and range from simple to highly complex. Although many of the technologies themselves are consistent, the use cases, architectures, and standards used to secure them vary greatly. Of course, no system can ever truly be secure. Despite significant levels of hype, IoT technologies, best practices, and architectures are not well established, which makes securing them an even more difficult task.
The good news is that security is not a new topic—nor are many of the technologies used to build today’s IoT platforms. This book focuses on the practical steps you can take, using the best technology, security, and architectural components, to evaluate the potential risks for large-scale IoT systems and then deploy the appropriate mitigation and management mechanisms to protect them as much as possible. This is demonstrated through practical, real-world use cases.
Defining the Internet of Things
As in many technology lifecycles, IoT has no single definition. Like technology itself, it is not a static phenomenon and continues to evolve. The term first appeared in Internet searches in 1999, but it did not become widely adopted until 2011, when it was included in the Gartner Hype Cycle for Emerging Technologies. This coincided with mass marketing campaigns from Cisco and IBM, among others. Since 2013, adoption has accelerated rapidly and will continue to grow for the foreseeable future (see Figure 1-1).
Early definitions focused on technology, based on the fundamental scope of connecting endpoints and devices and producing data. In 2012, the International Telecommunications Union (ITU) defined IoT as the network of physical objects (de-vices, vehicles, buildings, and so on) that are embedded with electronics, software, sensors, and network connectivity, enabling them to collect and exchange data.
The terms Machine-to-Machine (M2M) and the Future Internet have been used interchangeably to describe IoT; and related, more verticalized movements include Manufacturing 4.0 and the Industrial Internet of Things (IIoT). However, these should be considered subsets under the encompassing IoT umbrella. With the primary driver of device connectivity coming from industrial environments more than the consumer space, individual industries have used IoT components to create vertical-specific applications such as Smart Manufacturing, Smart Cities, Smart Grid, Smart Buildings, Connected Transportation, and Connected Healthcare. Although these verticals have different use cases and requirements, the technologies and platforms deployed are often similar; you can see this with cross-vertical compound applications such as Smart Cities delivering Smart Transportation solutions to ease parking. It is also important to mention that many industrial environments, such as manufacturing and power utilities, were deploying automation networks before the concept of IoT emerged. These automation networks (for example, substations or manufacturing assembly lines) are not considered IoT. As these same environments continue to evolve, the lines between IoT and traditional industrial control systems and automation are blurring. However, this does not mean that the terms should be used interchangeably.
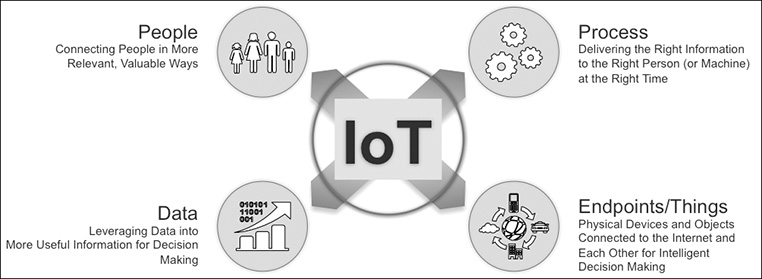
More recent definitions have moved beyond device connectivity and data production to include people and processes. Merely connecting devices and producing data is not enough, though: The data needs to be consumed in the right way; at the right time; by the correct device, system, or human; and in a way that is meaningful and can be acted upon appropriately (see Figure 1-2).
The current view is that IoT is a combination of endpoints or things, connectivity, and people and processes, with interactions (data and decisions) between these entities creating smart systems and services that deliver business value (see Figure 1-3).
■ Endpoints/things: Sensors provide binary or analog detection of changes or events of monitored parameters and send this information for computational decisions. Parameters include temperature, flow, pressure, location, proximity, presence, position, visuals, sound, and vibration. Actuators are responsible for movement or control of a device or system based on computational analysis, and include pneumatic, hydraulic, mechanical, magnetic, electrical, and rotary versions. These can be static, as with a water meter, or mobile, as with a car.
■ Connectivity: This refers to any kind of networking that provides connection and data exchange among endpoints, people, and processes. This can include protocols such as IPv4, IPv6, or even serial. Media can span from edge sensor to cloud across personal, local, and wide area networks, leveraging wired or wireless technology.
■ Data: Data is produced from endpoints and exchanged via networking to computers, systems, people, or other endpoints. The data can be at rest or on the move.
■ People and processes: Two-way systems that create information from the exchanged data to make an actionable business decision. Examples include Customer Relationship Management (CRM) and support systems, logistics, supply chain management and location tracking systems, automation, management and control systems, and monitoring and maintenance systems.
An important point here is that systems and organizations have been creating, collecting, and using data for years. Big Data is not a new term. Importantly, however, a Digital Universe study estimated that around 97 percent of data collected is not actually used. Approximately 3 percent is tagged and ready for manipulation, and less than 1 percent is actually analyzed. A platform should be implemented across an IoT deployment to manage the endpoints, connectivity, people and processes, and smart systems and services to effectively manage the data. An IoT platform must ensure that only the correct data is generated, collected, analyzed, and used in a way that is actionable toward a business decision. Otherwise, the data provides little or no value. Incredibly, the same study found that only 80 percent of data produced was actually secured and protected.
Making Technology and Architectural Decisions
So what should an IoT platform do? At a high level, an IoT platform, whether public or private, should deliver the fundamental capabilities of connectivity and data exchange. Most users of a system require additional capabilities to generate business value:
■ Data management and analytics: Collecting, transforming, managing, and analyzing data streams throughout the IoT deployment
■ Security compliance and governance: Managing security, compliance, and risk throughout the IoT deployment, including privacy where customer data is involved
■ Orchestration and automation: Deploying, monitoring, and managing devices, infrastructure, and systems throughout the IoT deployment
■ Presentation and system interaction: Using dashboards, reports, and human interfaces to interact at various levels throughout the IoT deployment
Chapter 3, “IoT Security Fundamentals,” discusses the actual components of an IoT platform. Chapter 5, “Current IoT Architecture Design and Challenges,” covers approaches to architecting an IoT platform. Alongside the technical and architectural components and requirements, a platform solution is influenced by vertical best practice and standards bodies. These generate and recommend specific architectures, views on information technology (IT) and operational technology (OT) divides and physical versus logical separation, and shared infrastructure, among other considerations. A good example is that many industrial environment systems are deployed following the Purdue Model of Control Hierarchy framework. This separates the IT and OT domains, including no shared infrastructure for data transport, even though many different types of data need to be exchanged to best benefit the overall organization and despite the fact that separation typically increases operational and capital costs. Chapter 4, “IoT and Security Standards and Best Practices,” details IoT standards. Understanding how these factors influence a specific IoT deployment is essential because it often determines how an IoT platform will be architected, deployed, managed, governed, and secured.
As organizations have come to realize the business value of IoT and seek more connections, a key challenge that IoT platforms face is increasing scalability. This is accelerating due to technology drivers. Computing architectures are evolving, with compute and storage capabilities occurring locally throughout an IoT system. Fog and edge compute (particularly in processing devices that continue to decrease in size and cost) have changed the traditional centralized cloud or data center model and extended capabilities to the edge. Processes, decisions, and control now occur at or near the source. IP, particularly IPv6, has also been widely adopted, allowing standardized transport of multiple use cases across a common infrastructure.
Essentially, the enhancements and progress in these technologies have facilitated the development of IoT devices that have compute, storage, and network capabilities built into extremely small form factors with low energy requirements, at a reduced cost. This has lowered the barriers to deploying IoT solutions. Adoption in both industrial verticals and the enterprise is increasing at an unprecedented scale.
However, although this provides new opportunities for businesses to deliver new value, it also introduces key operational challenges. Humans simply are not able to manage networks of this scale. To see this, let’s take a look at some examples of scale today.
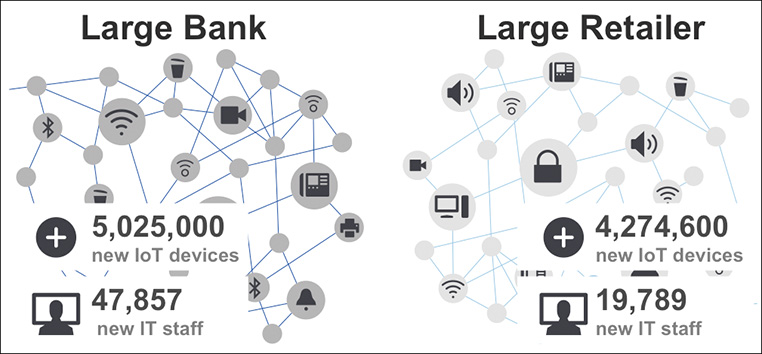
The traditional approach to determining IT staff levels uses IT staff–to–user ratios. A good benchmark in the past recommended 1 IT staff member per 50 employees. Today, organizations have been striving for 1 IT staff member per 100 employees. As businesses implement IoT solutions, the requirements for this ratio should be rethought. Instead of considering the number of IT staff per supported employees, a better benchmark is to allocate IT staff based on the number of supported devices. Using this approach, we would typically see a ratio of around 1:100 for highly regulated industries today and around 1:200 for less regulated industries (see Figure 1-4).
Thinking about the practical requirements of deploying IoT systems, especially at this scale, these numbers might seem very low. The complexities of configuring, managing, and securing large communication systems are challenging. Properly deploying and maintaining routing, switching, security, storage, collaboration, service assurance, and applications is not an easy task. This ratio might work today, but if we follow the predicted trend of increasing IoT device deployment through to 2020, will it still work?
Using a linear scale (see Figure 1-5), it is clear that we need to change the way our IoT platforms operate. The current model is not financially viable for employing such an increase in staff. Imagine deploying an IoT platform for a city such as Barcelona with a plan to connect and digitize every traffic signal, parking space, streetlight, parking meter, power distribution device, and vehicle. Now imagine securing and managing security for these tens of millions of devices. Clearly, a new approach is required.
The mindset needs to drastically change, with a single IT person managing tens or hundreds of thousands of devices. This is why orchestration and automation of IoT platforms is an essential approach, removing the time-consuming and repetitive tasks for IT staff and allowing them to focus on essential activities. Orchestration and automation must be designed and implemented end to end, not only for connectivity, but also for virtualization, applications, services, and, of course, security.
Research from IHS Markit, Technavia, and Gartner point to five main conclusions:
■ By 2020, the demands of IoT solutions will transform IoT platforms into comprehensive platforms as a service (PaaS).
■ Through 2020, the design of custom IoT solutions will be too complex for most organizations, and more than 80 percent of spending will move toward IoT software as a service (SaaS).
■ No single solution for IoT will exist: Platforms will incorporate hardware, software, and functionality from multiple vendors.
■ IoT platforms will move away from proprietary single-vendor solutions to open standard and open architecture systems based on network function virtualization (NFV) and software-defined networking (SDN). NFV alone is set to grow 33 percent per year up to 2020, driven solely by IoT.
■ Security must be inherent to a solution, not point products, and must be implemented and managed end to end to provide maximum protection.
For more on NFV and SDN, see Chapter 6, “Evolution and Benefits of SDX and NFV Technologies and Their Impact on IoT,” Chapter 7, “Securing SDN and NFV Environments,” and Chapter 8, “The Advanced IoT Platform and MANO.”
Unfortunately, security has not kept pace with technology advancements. No consensus exists on how to implement end-to-end IoT security for the platform of today, never mind the platforms predicted for 2020. However, adopting standards-based architectures encourages the potential to drive consistent security measures for IoT implementations. This is a key theme throughout this book.
Is the Internet of Things Really So Vulnerable?
The simple and honest answer is, yes! In the quest for new business opportunities, the current IoT allows for potentially billions of endpoints to be connected. The future IoT offers many additional possibilities we have not even considered, making connectivity virtually boundless. How do you fully secure systems consisting of both hardware and software, with billions of devices connected together, from multiple vendors? Add to this the issues of data privacy and data sharing, the integration of new IoT technology to legacy systems, and the requirement for a new skill set for those designing and operating the IoT platforms, and you can see a potential wealth of attack possibilities.
Historically, attackers have been skilled individuals with a deep knowledge of both technology and the systems they were attacking. However, as technology has advanced, widely available tools have been created to make attack methods easy to use. This means attackers with limited or no technical capability have the potential to launch a cyber attack, greatly increasing the overall threat to IoT systems.
Not everything spells doom and gloom, though. We can take measures to protect IoT deployments, and many best practice examples are available today. It is also a common misconception that attackers always have the advantage and end operators lack effective defenses. Operators know their environment and processes and can leverage multiple technologies and capabilities to defend their information networks against attack. Of course, attack methods also evolve over time, making defense more challenging for operators.
Add to this ongoing vigilance the potential disruption to traditional architectures, and it is clear that IoT brings a new set of challenges. When designing IoT platforms or IoT devices, a number of security considerations must be addressed:
■ Platforms must consider scalability and reliability, with the capability to manage and govern potentially tens of millions of devices and endpoints. All devices connected into a system require secure remote management before, during, and after onboarding.
■ Platforms must consider how to identify and trust entities before onboarding endpoints. Once connected, they must ensure that performance is as intended by the manufacturer. For example, a light bulb in a building should communicate only to a local lighting controller. If traffic patterns change, the system should automatically recognize this unusual behavior pattern and enforce policy to stop it happening—and prevent it from happening again.
■ Platforms need to manage multivendor deployments and multitenant environments, ensuring strict separation and protection of data. These scenarios create challenges in determining responsibility and liability.
■ In these multitenant deployments, data sharing and protection are often necessary. A device might support multiple tenants in a virtualized way, sharing resources and ensuring equal access to shared resources. Data produced might need to be shared between multiple tenants—not only on the device, but also between devices and throughout the system. Secure availability of data among systemwide chains of trust must be implemented to protect data throughout an IoT platform.
■ Many IoT devices are small, cost little, and have limited physical or cybersecurity capability. Existing and new computing devices might have constrained resources that cannot support robust or evolving security capabilities for confidentiality, data integrity, and identity management.
■ Many devices are designed to operate autonomously in the field, with no backup capability. If the primary connection is lost, monitoring or enforcing security is difficult while the device is offline. Additionally, many devices, particularly legacy ones, have no mechanism to identify themselves securely to an IoT platform. Insecure devices thus need to be connected or a proxy mechanism needs to be developed, typically based on gateway devices.
■ Endpoints such as phones, tablets, laptops, vehicles, and even robots on a factory floor are mobile by design. They might move geographically or be connected to different parts of the platform on a regular basis. How can these be secured across a system and protected from physical threats such as theft?
■ Technology lifecycle is another consideration. Many devices built for industrial environments, such as meters, are designed with a lifespan of 30 to 40 years. How can initially implemented security measures be maintained through the device lifecycle as security techniques change to combat new threats?
The way in which the IoT platform fundamentally behaves is not always consistent. In the IT space, the focus is on confidentiality, integrity, and then availability. In OT environments, where the priority is to ensure that systems continue to operate, the focus is on availability, then integrity, and finally confidentiality. As an example, it is more important for a power grid to continue to provide power, even if it is subject to a security breach.
Summary
This chapter looked at just a few of the security considerations that an IoT platform must address. Its four main areas of focus include maintaining a cohesive set of standards to foster IoT adoption, providing interoperability at all levels and layers, complying with regulations, and establishing strong cybersecurity, privacy, and safety controls. Chapter 2, “Planning for IoT Security,” provides a comprehensive and structured list of techniques to mitigate and secure against these threats.
With this volume of possible security challenges and a potentially inadequate security staff-to-device ratio, organizations must strive to deploy security implementations in a way that is easy to manage, readily orchestrated, and automated wherever possible. This is the best way to prevent more fear-inducing news stories.
References
http://telecoms.com/476945/nfv-market-forecast-to-grow-33-per-year-until-2020-driven-by-iot/