CHAPTER 3: RECONNAISSANCE
The start of the test
Now that the preparatory work has been completed and the testing team knows the scope, authority and rules of engagement for the test, the real pen testing work begins. The first step in conducting a pen test is to get to know the target. The test requires knowledge of client networks, applications, physical facilities, equipment and the people that use, manage and oversee client systems. It must be remembered that a pen test is often much more than just a technical probe of a system or technology. The test may be multifaceted and also examine physical, procedural and administrative controls.
The pen tester will use several methods to gather information about the target organization. These information-gathering techniques will include the same types of steps taken by an attacker attempting to probe the systems of networks of a potential victim.
Physical information gathering
Physical information gathering includes several techniques, including gaining physical access and the various types of social engineering.
Figure 6: Data gathering sources
Physical access
The pen tester will often test the physical access controls of the organization by methods such as attempting to bypass security procedures, defeating locks, and using alternative manners of entry (including roof access, loading docks and other access points). Of course, it is important to make sure that proper authorization is obtained before attempting such tests and that there is no physical risk to the tester.
Figure 7: Physical penetration testing
It can accurately be stated that breaches of physical security can have more impact than a breach of any other security control. If an attacker can gain physical access to systems, equipment, equipment rooms, network cables and personnel, then they can successfully execute virtually any type of attack and gain nearly unlimited access to data or sensitive information.
Social engineering
Social engineering is the manipulation of people to convince them to provide information or access that should not have been granted to the attacker (the engineer). This is one of the most common methods used to gain access to an organization or to gather sensitive data, and is very often successful. Social engineering takes many forms, including intimidation, name-dropping, appealing for assistance, and technical attacks.
Intimidation: This is the coercion or threatening of a victimized employee that causes the victim to provide access or information. This may work if the culture of the organization discourages employees from challenging a person that appears to be in authority. In the past, the intimidation method has been carried out successfully to gain access to military locations – if an attacker is dressed in the uniform of a senior officer, the guards may be afraid to challenge the imposter and allow the “officer” to gain unauthorized access. Some senior managers may also use intimidating behavior to pressure subordinates or other staff to break the rules and permit co-workers, visitors or other personnel to perform tasks that they should not have been permitted to do.
Name-dropping: This is one of the most common attacks. The attacker convinces the victim that the attacker has the approval from a person in authority to perform a restricted function or have access to protected data. The attacker may learn the name of the person in authority from a public source (such as an annual report or press release) and tell the victim that “Mr Davies,” for example, has granted them permission to gain access to the data or system in question.
Appealing for assistance: This is an attack that takes advantage of the helpful and good nature of people that would like to provide assistance to a person in need. The attacker asks the victim to help them solve a problem they are having – such as having trouble gaining remote access. The helpful victim may offer to help them use their account for access or set up an alternative way for the attacker to get the access or information they need.
Technical attacks: These are very common these days and take many forms. Many technical attacks come in the form of e-mails that promise jobs, lottery winnings, loans or other incentives. The attacker convinces the victim to disclose personal information that can then be used by the attacker to exploit the victim or the victim’s organization. The attack on RSA was facilitated by an employee opening an e-mail attachment that purported to list job opportunities.
Dumpster diving
Dumpster diving – going through the trash, garbage and recycling bins of an organization – is also a form of social engineering. The method is to simply sift through the discarded papers of an organization, looking for confidential data or technical manuals that may contain information that could aid an attacker in launching an attack. Many organizations have unknowingly provided the information needed to break into their systems by discarding old manuals that may have had passwords written in the notes and details on how to configure or connect to systems.
The pen tester will often use forms of social engineering to test the defenses and controls of the organization. One test has been to leave USB sticks lying around a facility and hope that staff will find them and take them into the office with them. The USB sticks may contain a Trojan horse or other malware that can then be used to gain access to the corporate network.
These attacks show that the secret to a successful pen test may be to attack the organization via its own personnel – this is often a very successful attack angle.
As will be seen later in this book, the pen tester must report on the success of such attacks and can then recommend steps that can be taken to mitigate them – often through improved awareness training.
Publicly available information
The first step in data gathering is to research publicly available data sources for information about the target company. Most companies have vast amounts of information available via the Internet, which can disclose potential attack vectors and enable social engineering or technical attacks to succeed. There are several examples of companies that have found source code for their applications posted on the Internet in user groups or chat rooms in which the company’s developers were searching for advice on solving programming problems. It is not uncommon to find that employees have been posting articles and comments on weblogs (blogs) that may indicate the types of equipment and other practices in use at the organization. Employee e-mail addresses, user IDs and passwords may also be freely available.
Social engineering and data mining in publicly available data are the least technical of all the steps in a penetration test. Anybody can do extensive searches on an organization. Most people are familiar with the tools and search engines that can be used – search engines, such as Google, Yahoo! and Bing, provide an easy way to discover information that the organization may not realize is commonly available. It is not uncommon to find passwords, conference presentations, or information about systems, equipment or personnel readily available using search engines. Many web archives also contain information about organizations and individuals that may make the attacker’s job easier. Archived web pages may also be available on the Wayback Machine.
Wireless penetration
Wireless devices provide a great benefit to an organization due to their greater mobility and easier access, but, as is well known, they can also provide access for an attacker. Wireless devices may be easily accessible from outside the building and allow an attacker to gain access to internal networks without even stepping onto the property of the victim organization. Thinking to “hide” wireless access points by turning off the service set identifier (SSID) broadcast or using Media Access Control (MAC) filtering is an ineffective control. A pen tester should look for authorized and unauthorized wireless devices during a test. The breach of T.J.Maxx in the United States, which led to the compromise of over 49 million credit cards, was enabled through an authorized, but insecure, wireless access point. Since many laptops have Bluetooth,® IEEE 802.11 and USB mobile access, it is relatively easy to find unsecured wireless channels into the networks and systems of the target organization that are located behind firewalls.
Other data sources
There are many other sources of information that can be used in the data gathering stage of a pen test. These include social networking sites, instant messages and blogs.
Social networking sites
It may be surprising to see how much information is willingly provided every day by users of social networking sites. Employees of organizations share information about their lives, work and relationships that may give an attacker an opportunity to build relationships with them that may then be leveraged to obtain competitive information or access to the strategies of the organization. Posting organizational information may also lead to the loss of ownership of that information. This may be a risk when an organization wants to promote a marketing plan without realizing that doing this may allow another organization to use that information without penalty.
Instant messaging and blogs
Anything posted in an instant messaging (IM) system or a blog must be considered public information. Organizational policy should direct how employees use instant messaging or participate in blogs. This policy should include a directive that no corporate data or files be shared using instant messaging. In some countries, the use of IM to communicate with customers would be a matter of official record and all IM traffic must be stored for a period of seven or more years.
It has not been uncommon to find that developers and other staff have contributed to internet forums and blogs that will reveal information about their organization – including source code and equipment configurations at times.
Domain name system (DNS)
The domain name system is a crucial part of the Internet, and using fully qualified domain names (FQDNs) – instead of using IP addresses – provides an easy way for most people to reach web pages. When registering their domain name with the DNS, the organization is required to provide some publicly available information, such as phone numbers, addresses and the names of administrators when they register their domain name. This information may then be used in social engineering attacks. The pen tester will look up the DNS registration as a part of data gathering.
Banner grabbing
Banner grabbing is the act of reviewing the metadata banner that is a header in the communications channel that is set up between the two remote entities. By reviewing the banner, the pen tester can often learn information about the operating system and other services running on the target machine.
Footprinting
Through both active and passive reconnaissance, the pen tester can learn a lot about the target’s networks, system layout, configurations and patch levels.
While passive reconnaissance is the quiet method of gathering information without contacting the target systems and trying to go as unnoticed as possible, active reconnaissance is the probing and prodding of the target systems and networks. The tester learns about the target through the ways that the systems respond to queries or react to probes.
The purpose of footprinting is to gather as much information about the target as possible, so that the pen tester can design the subsequent pen tests to exactly target the discovered vulnerabilities and be successful. The footprint of the system should include a diagram of the target network and a description of system services, equipment and patch levels.
The use of products, such as Maltego and FireCAT, will help the pen tester map out the networks and the relationships between data, systems and services. Refined Google searches will also present a wealth of information to the tester.
Job postings
The pen tester may also review job postings that have been posted on public areas, since they will often describe the qualifications and experience needed by a job applicant. The posting will often disclose the types of equipment, software and methodologies used by the target organization.
Reviewing Securities and Exchange Commission (SEC) filings for publicly traded companies or other publicly available information, such as company listings, search results of executive staff in people search engines and comments in news media will often uncover extensive information that may be valuable to the pen tester.
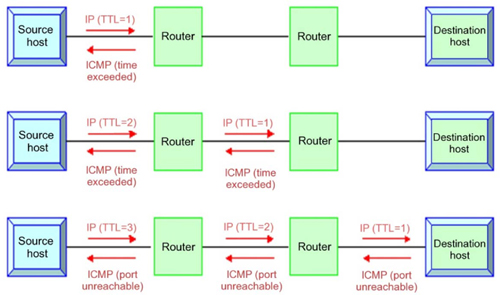
Traceroute
A very useful tool for the pen tester is traceroute. Traceroute will identify the path taken by traffic travelling to the target network. It will allow the pen tester to learn some of the behaviors of the traffic using of Time to Live (TTL) statistics and response times. This can assist the pen tester in determining the presence and layout of various network devices.
Avoiding footprinting
An organization that wants to minimize the impact of footprinting needs to be careful what information is available publicly about the company. This may require the sanitizing of DNS registries, the careful wording of job postings and clear policies for staff that review or contribute to blogs or other interactive forums. The organization should also have separate internal and external DNS servers, since an attacker may learn network configuration information from the internal DNS.
DNS zone transfers
In order to replicate the data stored on a DNS server, an administrator can perform a zone transfer. The problem is that an attacker can also copy the DNS data in the same manner. If the DNS server is on the internal network, this would allow the attacker to learn information that may assist in the execution of an attack. Attackers also can successfully poison DNS entries, so that requests to a website are diverted to an alternate location.
Key learning points
There is a wealth of information publicly available about most organizations, and the pen tester should take the time to uncover as much of it as possible. This will enable a targeted test, which is much more likely to be successful and may avoid a lot of wasted time and effort later in the pen testing process.
Footprinting is a combination of technical, social and physical tests – some of which are passive in nature and some of which are active.
Every organization should take steps to minimize the amount of information publicly available about their systems, networks, software, processes and staff.
Questions
1. The purpose of footprinting is to:
a) Test of the ability of the systems administrators to detect and respond to a penetration
b) Review and audit whether the administrators are complying with organizational procedures
c) Detect any misconfigurations of network or host equipment
d) Gather information about a target organization.
Answer: D
2. Social engineering can be described as:
a) Aggressively marketing the organization through social media
b) Managing the social perception of the organization through press releases and media manipulation
c) Influencing a person to provide access or information against the policies of the organization
d) The engineering and design of systems through a committee-based approach.
Answer: C
a) Exploiting weaknesses in the security infrastructure of Google
b) Using Google tools to hack into an organization
c) The discovery of information about an organization using Google features
d) The footprinting of the Google network layout and international server relationships.
Answer: C
4. Traceroute is used to:
a) Discover the path taken by packets across a network
b) Determine response times for database queries
c) Track the activity on a network and monitor error levels
d) Evaluate whether the Time to Live (TTL) is set properly for internal network communications.
Answer: A
5. With regards to DNS servers, the organization should:
a) Ensure they contain as much information as possible to speed up network traffic
b) Always have separate internal and external DNS servers to provide better efficiency
c) Deploy separate internal and external DNS servers to hide internal network data from external parties
d) Configure DNS servers to point to authoritative domain hosts.
Answer: C