CHAPTER 4: ACTIVE RECONNAISSANCE AND ENUMERATION
Active reconnaissance is the next critical step in the pen testing process. During this step, the pen tester will learn crucial information about the characteristics of the target system (and perhaps even about the administrators’ diligence in monitoring, patching and configuring the systems properly).
Active reconnaissance is the actual probing of the system to learn how it is configured, what possible points of entry there are for the pen tester and what services or vulnerable points may be found.
Active reconnaissance may consist of several types of tests, including port scans, operating system fingerprinting, and Transmission Control Protocol (TCP) scanning. It can be compared to knocking on every door in a hotel or apartment building to see which rooms are in use, which doors are locked, and which rooms issue a response.
Closely linked with active reconnaissance is enumeration. Enumeration is the retrieval of specific information about the target systems, user accounts and passwords that may identify vulnerabilities and attack vectors that can be used by the pen tester – or an attacker – in a subsequent attack.
Through the process of enumeration, the objective is to gather as much information as possible about network resources, usernames, passwords, active services and machine names.
Port scanning
Network communications and applications are set to transfer information over predefined ports. These ports are similar to the rooms in a hotel – some rooms are occupied and in use, while others are vacant. A thief wanting to gain access to valuables that residents of the hotel may have in their rooms will not want to waste time entering rooms that are not in use. Therefore, the thief may first listen at the door (passive reconnaissance) and then perhaps even knock on the door to see if anyone answers (active reconnaissance). The purpose of port scanning is to see which doors or ports are open on a system, so that the pen tester can target their attack to the services, ports and applications that are in use.
Applications are usually related to certain ports, such as port 25 for SMTP (e-mail), port 80 for web applications, port 443 for Secure Sockets Layer (SSL), and port 53 for DNS. Any open port is a target and opportunity for an attacker, so those that are not needed should be closed. The less attack surface area the organization has, the easier it is to defend. Every open door requires that much more work to protect and monitor.
A port scan sends a request to each port to see if it will respond. If it does, it may be possible for the tester to learn information, such as the operating system in use and the services available, and, from that information, begin to draw out a network blueprint.
It is important to note that a port scan is nothing more than a knock on a door and is not illegal in most cases – but the pen tester must know the laws and regulations for the country they are operating in. Some countries may consider a port scan to be a demonstration of intent to break in and, therefore, unlawful.
The first step in port scanning is often to use the Internet Control Message Protocol (ICMP) to ping the target network. Hosts on a network that allow pings will respond to the pings, thereby revealing their presence. Open source tools like Nmap® are frequently used for this type of test. Nmap can then also be used to do more thorough tests without using the ping feature. In this way, Nessus is used for operating system fingerprinting and patch level detection.
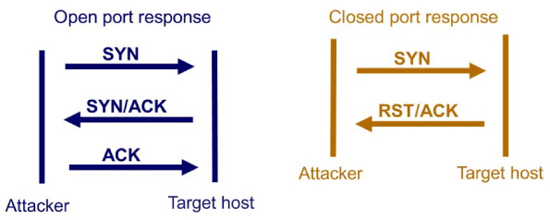
The use of the three-way handshake of TCP is also a way to determine which ports are open on a system. A TCP-connect port scan will attempt to sequentially connect to each port on a system. If a port is open, then the target port should respond to a SYN request with a SYN/ACK; otherwise, it will respond with a RST/ACK or no reply (if filtered). Many systems are filtered, which means that responses to a scan may be blocked.
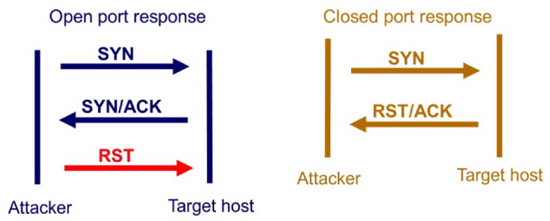
The tester may also choose to do a half-open TCP SYN port scan instead of a TCP-connect scan. In this case, the third part of the TCP three-way handshake is not completed. This method is commonly used when an attacker wants to conduct a distributed denial-of-service (DDoS) attack against a victim by sending a flood of SYN packets towards the victim and never responding to the SYN/ACK that the victim sends back.
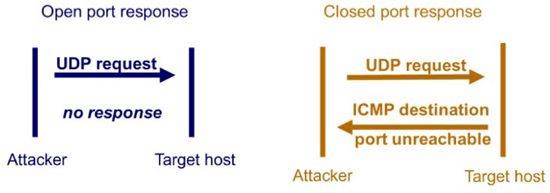
User Datagram Protocol (UDP) scans may also be used to detect open or closed ports. A UDP message is sent to the target system and the tester will note whether the system responds with a “port unreachable” reply, indicating a closed port.
Nmap can be used to do UDP scans by using the -aU argument.
Adding additional conditions to an Nmap test will provide more data about the target operating system, and allow the pen tester to adjust their attacks accordingly. However, some Nmap tests can be very noisy and are more likely to attract the attention of the target system and intrusion detection system (IDS).
Other common tools used for scanning include hping2, SuperScan® and Look@LAN.
Web server banners
Learning what type of equipment and operating systems are being used by a web server will provide a strategic advantage to the attacker. Such information is readily available from many servers through simple actions. Establishing a telnet session to the web server by typing “telnet <webserver> 80” and then the command “GET / HTTP/1.0” works on many older systems; and the use of tools, such as SuperScan and HTTPRINT, are effective against some newer systems. Establishing a telnet session to a SMTP server over port 25 can also disclose the software version that is being used by the SMTP server.
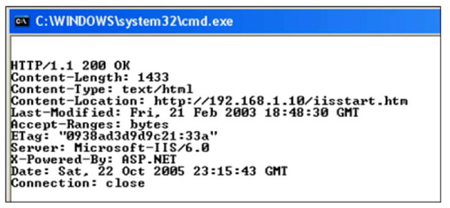
Figure 13: Web banner grabbing using telnet
SuperScan can also be used for Web Banner Grabbing, as seen below.
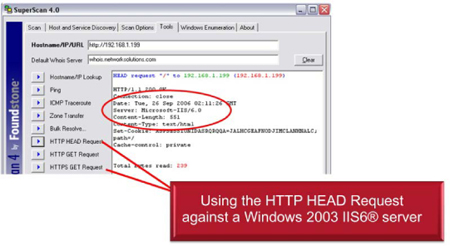
Figure 14: Banner grabbing using SuperScan
DNS vulnerabilities
The tools nslookup and BackTrack® are the attacker’s and pen tester’s friends when it comes to enumerating the characteristics of the DNS configurations. Zone transfers and data about server names and addresses can be queried from any DNS attached to the Internet. This is why it is important to always have separate internal and external DNS servers, and to ensure that they are configured correctly to prevent zone transfers.
Simple Network Management Protocol (SNMP®) insecurity
SNMP is a very useful tool for network and system administrators; however, the earlier versions – SNMPv1 and SNMPv2 – are not secure enough for use. These versions pass the community string (the password, if you will) in cleartext and the default setting of “public” is often still set. The community string should be set to a cryptic value and ports 161 and 162 should be blocked at the firewall.
Administrators should use SNMPv3 wherever possible. Where older equipment does not support this version, however, the SNMP traffic can be encrypted over Internet Protocol Security (IPsec), or all SNMP connections can be restricted to respond to predefined IP addresses only.
Active Directory® enumeration
Active Directory (AD) will contain the user names and access rights for all the users on a system. Learning user names will provide the attacker with a great advantage in targeting an attack – especially as some names may indicate job roles and obviously be set for high-level access. Lightweight Directory Access Protocol (LDAP) is used to access AD following the X.500 naming standards. LdapMiner is a tool that can be used to search AD entries. Administrators should also consider blocking ports 389 (LDAP) and 3268 (global catalog) at the firewall.
Null sessions
If an attacker/pen tester can establish a null session to a server, a whole list of new attacks and the use of many more tools – such as Cain & Abel, DumpSec and THC-Hydra – will be possible. These tools gather network and user information, allow the attacker to establish new user accounts and grab password hashes. The best countermeasures to this are to disable ports that may not be needed, such as port 135 (Remote Procedure Call (RPC) locator); 137 (Windows® Internet Name Service (WINS)); 138 (Network Basic Input/Output System (NetBIOS®)); and 445 (Common Internet File System / Server Message Block (CIFS/SMB)).
Countermeasures to active reconnaissance
Organizations should harden their systems by turning off services and ports that are not needed. Every port is a possible point of attack, and a breach at any point in the network may lead to a compromise in other locations.
The corporate firewall is the first layer of defense and should be configured to block inbound ICMP packets, detect and drop any abnormal packets and monitor all network connections.
The intrusion detection system (IDS) should also be set to detect port scans and terminate the connections.
A layered defense is the secret to true security. Just as in a hotel, where valuables are locked in a safe in the room, on a network the ports should be closed, the IDS enabled, the application level monitoring in use and proxies used to hide network information.
Perhaps the most important countermeasure to an attack is to monitor system activity and check system logs frequently. Many times, the administrator may become aware of a probing attack from a remote entity through evidence in the logs. While it may be impossible to stop an attacker from probing and attempting to break in, by knowing about the malicious activity, the administrator can take steps to block the amount of information available or to block the access ports open to the attacker.
Key learning points
Active reconnaissance is one of the most important steps in a penetration test. It enables the tester to learn about the actual configurations and potential technical weaknesses of the system, and thereby prepare test scenarios targeted specifically at those vulnerable points. Port scans, TCP-connect and TCP half-open scans are some of the most popular methods of scanning. Many attacks are enabled by administrators leaving ports open that may not be needed, or by not enforcing good password rules.
Questions
1. Which of the following would be an example of active reconnaissance?
a) Eavesdropping on a communications line
b) Capturing unencrypted wireless traffic to an authorized wireless access point
c) Scanning well-known ports on a system to determine system responses
d) Social engineering the administrators to provide unauthorized access to a system.
Answer: C
2. A TCP half-open scan will:
a) Set up a completed handshake with a target system
b) Send a series of pings over the target network
c) Respond with all ports open to a network scan
d) Send a SYN request to a target, but fail to respond to the subsequent SYN/ACK reply.
Answer: D
3. A ping scan may be illegal if it:
a) Causes a denial of service on the target network
b) Responds to a SYN request with a counterattacking RST
c) Disables the TCP-connect feature on a firewall
d) Completes a three-way handshake with an infected source system.
4. One reason to use SNMPv3 is:
a) The earlier versions are too slow to allow for productive remote maintenance
b) SNMPv1 and SNMPv2 pass the community string in cleartext
c) SNMPv3 is supported by all versions and generations of equipment
d) SNMPv1 and SNMPv2 are restricted to internal networks only.
Answer: B