
Physical Security
You can ensure the safety of your defense if you only hold positions that cannot be attacked.
—SUN TZU, THE ART OF WAR

In this chapter, you will learn how to
![]() Describe how physical security directly affects computer and network security
Describe how physical security directly affects computer and network security
![]() Discuss steps that can be taken to help mitigate risks
Discuss steps that can be taken to help mitigate risks
![]() Describe the physical security components that can protect your computers and network
Describe the physical security components that can protect your computers and network
![]() Identify environmental factors that can affect security
Identify environmental factors that can affect security
![]() Identify the different types of fires and the various fire suppression systems designed to limit the damage caused by fires
Identify the different types of fires and the various fire suppression systems designed to limit the damage caused by fires
![]() Explain electronic access controls and the principles of convergence
Explain electronic access controls and the principles of convergence
![]() Prevent disclosure through electronic emanations
Prevent disclosure through electronic emanations
Physical security consists of all mechanisms used to ensure that physical access to the computer systems and networks is restricted to only authorized users. Additional physical security mechanisms may be used to provide increased security for especially sensitive systems such as servers as well as devices such as routers, firewalls, and intrusion detection systems. When considering physical security, access from all six sides should be considered—not only should the security of obvious points of entry be examined, such as doors and windows, but the walls themselves as well as the floor and ceiling should also be considered. Questions such as the following should be addressed:
![]() Is there a false ceiling with tiles that can be easily removed?
Is there a false ceiling with tiles that can be easily removed?
![]() Do the walls extend to the actual ceiling or only to a false ceiling?
Do the walls extend to the actual ceiling or only to a false ceiling?
![]() Is there a raised floor?
Is there a raised floor?
![]() Do the walls extend to the actual floor, or do they stop at a raised floor?
Do the walls extend to the actual floor, or do they stop at a raised floor?
![]() How are important systems situated?
How are important systems situated?
![]() Do the monitors face away from windows, or could the activity of somebody at a system be monitored from outside?
Do the monitors face away from windows, or could the activity of somebody at a system be monitored from outside?
![]() Who has access to the facility?
Who has access to the facility?
![]() What type of access control is there, and are there any guards?
What type of access control is there, and are there any guards?
![]() Who is allowed unsupervised access to the facility?
Who is allowed unsupervised access to the facility?
![]() Is there an alarm system or security camera that covers the area?
Is there an alarm system or security camera that covers the area?
![]() What procedures govern the monitoring of the alarm system or security camera as well as the response should unauthorized activity be detected?
What procedures govern the monitoring of the alarm system or security camera as well as the response should unauthorized activity be detected?
These are just some of the numerous questions that need to be asked when you’re examining the physical security surrounding a system.
Physical Security Is Also Important to Computer Security
Computer security professionals recognize that they cannot rely only on computer security mechanisms to keep their systems safe. Physical security must be maintained as well, because in many cases, if an attacker gains physical access, they can steal data and destroy the system.
 The Security Problem
The Security Problem
The problem that faces professionals charged with securing a company’s network can be stated rather simply: physical access negates all other security measures. No matter how impenetrable the firewall and intrusion detection system (IDS), if an attacker can find a way to walk up to and touch a server, they can break into it.
Consider that most network security measures are, from necessity, directed at protecting a company from Internet-based threats. Consequently, a lot of companies allow any kind of traffic on the local area network (LAN). So if an attacker attempts to gain access to a server over the Internet and fails, they may be able to gain physical access to the receptionist’s machine and, by quickly compromising it, use it as a remotely controlled zombie to attack what they are really after. Figure 8.1 illustrates the use of a lower-privilege machine to obtain sensitive information. Physically securing information assets doesn’t mean just the servers; it means protecting physical access to all the organization’s computers and its entire network infrastructure.
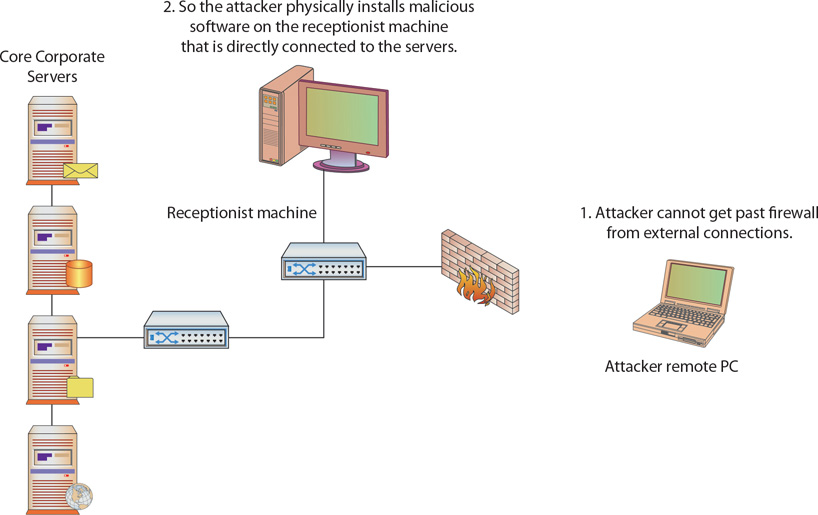
• Figure 8.1 Using a lower-privilege machine to get at sensitive information
Physical access to a corporation’s systems can allow an attacker to perform a number of interesting activities, starting with simply plugging into an open Ethernet jack. The advent of handheld devices with the ability to run operating systems with full networking support has made this attack scenario even more feasible. Prior to handheld devices, the attacker would have to work in a secluded area with dedicated access to the Ethernet for a time. The attacker would sit down with a laptop and run a variety of tools against the network, and working internally typically put the attacker inside the firewall and IDS. Today’s capable mobile devices can assist these efforts by allowing attackers to place the small device onto the network to act as a wireless bridge, as shown in Figure 8.2.
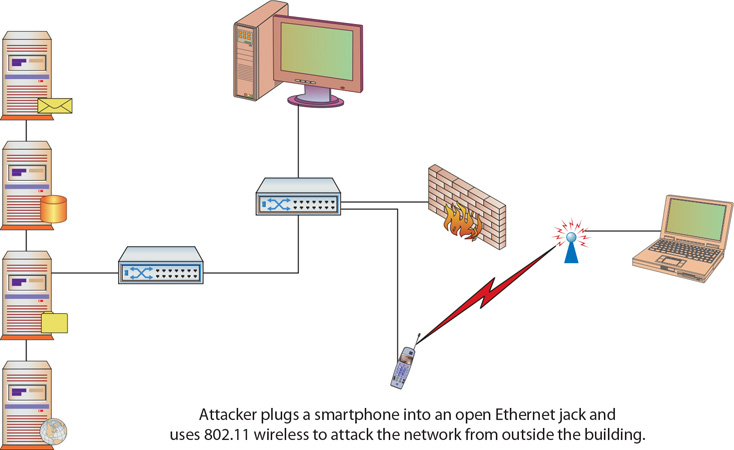
• Figure 8.2 A wireless bridge can allow remote access.
The attacker can then use a laptop to attack a network remotely via the bridge from outside the building. If power is available near the Ethernet jack, this type of attack can also be accomplished with an off-the-shelf access point. The attacker’s only challenge is finding an Ethernet jack that isn’t blocked by furniture or some other obstruction.
Another simple attack that can be used when an attacker has physical access is called a bootdisk. Any media used to boot a computer into an operating system that is not the native OS on its hard drive could be classified as a bootdisk. This can be in the form of a floppy disk, CD, DVD, or a USB flash drive. Before bootable CDs or DVDs were available, a boot floppy was used to start the system and prepare the hard drives to load the operating system. A boot source can contain a number of programs, but the most typical ones would be NTFSDOS or a floppy-based Linux distribution that can be used to perform a number of tasks, including mounting the hard drives and performing at least read operations, all done via script. Once an attacker is able to read a hard drive, the password file can be copied off the machine for offline password-cracking attacks. If write access to the drive is obtained, the attacker could alter the password file or place a remote-control program to be executed automatically upon the next boot, guaranteeing continued access to the machine. Most new machines do not include floppy drives, so this attack is rapidly being replaced by the same concept with a USB device, CD, or DVD. The most obvious mitigation is to tell the BIOS not to boot from removable media, but this too has issues.
The bootable CD-ROMs and DVD-ROMs are actually more of a threat than boot floppies, because they are frequently used to carry a variety of software for updates and can utilize the much greater storage capacity of the CD or DVD media. This capacity can store an entire operating system and a complete tool set for a variety of tasks or malware, so when you’re updating via CD/DVD, precautions must be taken to ensure the veracity of the media.
There are operating system distributions specifically designed to run the entire machine from an optical disc without using the hard drive. These are commonly referred to as LiveCDs. A LiveCD contains a bootable version of an entire operating system, typically a variant of Linux, complete with drivers for most devices. LiveCDs give an attacker a greater array of tools than could be loaded onto a floppy disk, such as scanners, sniffers, vulnerability exploits, forensic tools, drive imagers, password crackers, and so on. These sets of tools are too numerous to list here and are changing every day. The best resource is to search the Internet for popular LiveCD distributions like Kali/Backtrack, knoppix, and PHLAK. A sample collection of LiveCDs is shown in Figure 8.3.

• Figure 8.3 A collection of sample LiveCDs
Create a Bootdisk
Bootdisks allow you to boot a computer to the disk rather than the OS that is on the hard drive. Create a bootdisk for your own personal computer. The steps differ between different OSs and depending on the media you wish to make bootable. Perform a little research to determine the correct procedure for your OS and give it a try. Make a bootable CD/DVD or USB flash drive.
For example, with a LiveCD, an attacker would likely have access to the hard disk and also to an operational network interface that allows them to send the drive data over the Internet if properly connected. These bootable operating systems could also be custom built to contain any tool that runs under Linux, allowing an attacker to build a standard bootable attack image or a standard bootable forensic image, or something customized for the tools they like to use. Bootable USB flash drives emulate the function of a CD-ROM and provide a device that is both physically smaller and logically larger.

Drive imaging is a threat because all existing access controls to data can be bypassed and all the data stored on the drive can be read from the image.
These types of devices have spawned a new kind of attack in which a CD, DVD, or flash drive is left in an opportunistic place where members of a target organization may pick it up and use it. This CD/DVD or flash drive is typically loaded with malware and is referred to as a road apple. The attack relies on curious people plugging the device into their work computer to see what’s on it. Occasionally the attacker may also try to tempt the passerby with enticing descriptions like “Employee Salaries” or even something as simple as “Confidential.” Once a user loads the CD/DVD or flash drive, the malware will attempt to infect the machine.
Encryption to TPM-Based Keys
Many computers now come with a security chip that follows the Trusted Platform Module (TMP) standard. This TPM chip allows for the creation and storage of encryption keys. One of the strengths associated with this level of security is that if a copy of a drive, or even the drive itself, is stolen, the contents are unusable without the key. Having this key locked in hardware prevents hackers from stealing a copy of the key from a memory location.
Physical access is the most common way of imaging a drive, and the biggest benefit for the attacker is that drive imaging leaves absolutely no trace of the crime. Besides physically securing access to your computers, you can do very little to prevent drive imaging, but you can minimize its impact. The use of encryption even for a few important files provides protection. Full encryption of the drive protects all files stored on it. Alternatively, placing files on a centralized file server keeps them from being imaged from an individual machine, but if an attacker is able to image the file server, the data will be copied.
Forensic Images
When taking a forensic-based image, it is important to follow proper forensic procedures to ensure the evidence is properly secured. Forensic processes and procedures are covered in detail in Chapter 23.
A denial-of-service (DoS) attack can also be performed with physical access. Physical access to the computers can be much more effective than a network-based DoS attack. Stealing a computer, using a bootdisk to erase all data on the drives, or simply unplugging computers are all effective DoS attacks. Depending on the company’s frequency of backing up critical systems, as well as the quality of those backups, a DoS attack using these methods can have lasting effects.
Physical access can negate almost all the security that the network attempts to provide. Considering this, you must determine the level of physical access that attackers might obtain. Of special consideration are persons with authorized access to the building who are not authorized users of the systems. Janitorial personnel and others have authorized access to many areas, but they do not have authorized system access. An attacker could pose as one of these individuals or attempt to gain access to the facilities through them.
 Physical Security Safeguards
Physical Security Safeguards
Although it is difficult, if not impossible, to make an organization’s computer systems totally secure, many steps can be taken to mitigate the risk to information systems from a physical threat. The following sections discuss access control methods and physical security policies and procedures that should be implemented.

All entry points to server rooms and wiring closets should be closely controlled, and, if possible, access should be logged through an access control system.
Walls and Guards
The primary defense against a majority of physical attacks is the barriers between the assets and a potential attacker—walls, fences, gates, and doors. Some organizations also employ full- or part-time private security staff to attempt to protect their assets. These barriers provide the foundation upon which all other security initiatives are based, but the security must be designed carefully, as an attacker has to find only a single gap to gain access.
Walls may have been one of the first inventions of man. Once he learned to use natural obstacles such as mountains to separate him from his enemy, he next learned to build his own mountain for the same purpose. Hadrian’s Wall in England, the Great Wall of China, and the Berlin Wall are all famous examples of such basic physical defenses. The walls of any building serve the same purpose, but on a smaller scale: they provide barriers to physical access to company assets. Bollards are small and round concrete pillars that are constructed and placed around a building to protect it from being damaged by someone driving a vehicle into the side of the building, or getting close and using a car bomb.
To protect the physical servers, you must look in all directions: Doors and windows should be safeguarded, and a minimum number of each should be used in a server room. Less obvious entry points should also be considered: Is a drop ceiling used in the server room? Do the interior walls extend to the actual roof, raised floors, or crawlspaces? Access to the server room should be limited to the people who need access, not to all employees of the organization. If you are going to use a wall to protect an asset, make sure no obvious holes appear in that wall.
Lighting
Proper lighting is essential for physical security. Unlit or dimly lit areas allow intruders to lurk and conduct unauthorized activities without a significant risk of observation by guards or other personnel. External building lighting is important to ensure that unauthorized activities cannot occur without being observed and responded to. Internal lighting is equally important because it enables more people to observe activities and see conditions that are not correct. Similarly, windows can play an important role in assisting the observation of the premises. Having sensitive areas well lit and open to observation through windows prevents activities that would otherwise take place in secret. Unauthorized parties in server rooms are more likely to be detected if the servers are centrally located, surrounded in windows, and well lit.
Lighting types
Lighting not only provides a deterrent to intruders but also assists other access control systems.
Types of lighting systems:
![]() Continuous lighting A series of fixed lights arranged to flood a given area continuously
Continuous lighting A series of fixed lights arranged to flood a given area continuously
![]() Trip lighting Activated when an intruder crosses a sensor
Trip lighting Activated when an intruder crosses a sensor
![]() Standby lighting Similar to continuous lighting, except lights are not continuously lit
Standby lighting Similar to continuous lighting, except lights are not continuously lit
![]() Emergency lighting Activated in emergency events (for example, a power failure or fire)
Emergency lighting Activated in emergency events (for example, a power failure or fire)
Signs
Signs act as informational devices and can be used in a variety of ways to assist in physical security. Signs can provide information as to areas that are restricted, or they can indicate where specific precautions, such as keeping doors locked, are required. A common use of signs in high-security facilities is to delineate where visitor are allowed versus secured areas where escorts are required. Visual security clues can assist in alerting users to the need for specific security precautions. Visual clues as to the types of protection required can take the form of different color name badges that dictate the level of access, visual lanyards that indicate visitors, colored folders, and so forth.
Fences
Outside of the building’s walls, many organizations prefer to have a perimeter fence as a physical first layer of defense. Chain-link-type fencing is most commonly used, and it can be enhanced with barbed wire. Anti-scale fencing, which looks like very tall vertical poles placed close together to form a fence, is used for high-security implementations that require additional scale and tamper resistance.
To increase security against physical intrusion, higher fences can be employed. A fence that is three to four feet in height will deter casual or accidental trespassers. Six to seven feet will deter a general intruder. To deter more determined intruders, a minimum height of eight feet is recommended, with the addition of barbed wire or razor wire on top for extreme levels of deterrence.
Fence types
Fences come in a variety of types and heights. The following table assists you in choosing the correct size based on need:

Barricades/Bollards
Barricades provide the foundation upon which all other physical security initiatives are based. Barricades can also be used to control vehicular access to (or near) a building or structure. A simple post-type barricade that prevents a vehicle from passing but allows people to walk past it is called a bollard. Bollards also act to prevent some forms of physical entry but like a window do not obscure vision as a wall or fence might. Physical security elements must be designed and deployed carefully, as an attacker has to find only a single gap to gain access.
Guards
Guards provide an excellent security measure, because they are a visible presence with direct responsibility for security. Other employees expect security guards to behave a certain way with regard to securing the facility. Guards typically monitor entrances and exits and can maintain access logs of who has entered and departed the building. In many organizations, everyone who passes through security as a visitor must sign the log, which can be useful in tracing who was at what location and when.
Security personnel are helpful in physically securing the machines on which information assets reside, but for an organization to get the most benefit from their presence, they must be trained to take a holistic approach to security. The value of data typically can be many times that of the machines on which the data is stored. Security guards typically are not computer security experts, so they need to be educated about the value of the data and be trained in network security as well as physical security involving users. They are the company’s eyes and ears for suspicious activity, so the network security department needs to train them to notice suspicious network activity as well. Multiple extensions ringing in sequence during the night, computers rebooting all at once, or strange people parked in the parking lot with laptop computers are all indicators of a network attack that might be missed without proper training.
Many traditional physical security tools such as access controls and CCTV camera systems are transitioning from closed hardwired systems to Ethernet- and IP-based systems. This transition opens up the devices to network attacks traditionally performed on computers. With physical security systems being implemented using the IP network, everyone in physical security must become smarter about network security.

The bigger challenge associated with capturing surveillance activities or other attempted break-in efforts is their clandestine nature. These efforts are designed to be as low profile and nonobvious as possible to increase the chances of success. Training and awareness are necessary not just for security personnel but for all personnel. If an employee hears multiple extensions all start ringing in the middle of the night, do they know whom to notify? If a security guard notes such activity, how does this information get reported to the correct team?
Alarms
Alarms serve to alert operators to abnormal conditions. Physical security can involve numerous sensors, intrusion alarms, motion detectors, switches that alert to doors being opened, video and audio surveillance, and more. Each of these systems can gather useful information, but it is only truly useful if it is acted upon. When one of these systems has information that can be of use to operational personnel, an alarm is the easiest method of alerting personnel to the condition. Alarms are not simple; if there are too many alarm conditions, especially false alarms, then the operators will not react to these conditions as desired. Tuning alarms so that they provide useful, accurate, and actionable information is important if you want them to be effective.
There are many types of alarm systems. Local alarm systems ring only locally. A central station system is one where alarms (and CCTV) are monitored by a central station. Many alarms will have auxiliary or secondary reporting functions to local police or fire departments. Alarms work by alerting personnel to the triggering of specific monitoring controls. Typical controls include the following:
![]() Dry contact switches use metallic foil tape as a contact detector to detect whether a door or window is opened.
Dry contact switches use metallic foil tape as a contact detector to detect whether a door or window is opened.
![]() Electro-mechanical detection systems detect a change or break in a circuit. They can be used as a contact detector to detect whether a door or window is opened.
Electro-mechanical detection systems detect a change or break in a circuit. They can be used as a contact detector to detect whether a door or window is opened.
![]() Vibration detection systems detect movement on walls, ceiling, floors, and so forth, by vibration.
Vibration detection systems detect movement on walls, ceiling, floors, and so forth, by vibration.
![]() Pressure mats detect whether someone is stepping on the mat.
Pressure mats detect whether someone is stepping on the mat.
![]() Photoelectric or photometric detection systems emit a beam of light and monitor the beam to detect for motion and break-in.
Photoelectric or photometric detection systems emit a beam of light and monitor the beam to detect for motion and break-in.
![]() Wave pattern motion detectors generate microwave or ultrasonic wave and monitor the emitted waves to detect for motion.
Wave pattern motion detectors generate microwave or ultrasonic wave and monitor the emitted waves to detect for motion.
![]() Passive infrared detection systems detect changes of heat waves generated by an intruder.
Passive infrared detection systems detect changes of heat waves generated by an intruder.
![]() Audio or acoustical-seismic detection systems listen for changes in noise levels.
Audio or acoustical-seismic detection systems listen for changes in noise levels.
![]() Proximity detectors or capacitance detectors emit a magnetic field and monitor the field to detect any interruption.
Proximity detectors or capacitance detectors emit a magnetic field and monitor the field to detect any interruption.
Physical Access Controls and Monitoring
Physical access control means control of doors and entry points. The design and construction of all types of access control systems, as well as the physical barriers to which they are most complementary, are fully discussed in other texts. Here, we explore a few important points to help you safeguard the information infrastructure, especially where it meets with the physical access control system. This section talks about physical locks, layered access systems, and electronic access control systems. It also discusses closed-circuit television (CCTV) systems and the implications of different CCTV system types.
Layered Access
Layered access is an important concept in security. It is often mentioned in conversations about network security perimeters, but in this chapter it relates to the concept of physical security perimeters. To help prevent an attacker from gaining access to important assets, these assets should be placed inside multiple perimeters. Servers should be placed in a separate secure area, ideally with a separate authentication mechanism. For example, if an organization has an electronic door control system using contactless access cards (such as the example shown in Figure 8.4) as well as a keypad, a combination of the card and a separate PIN code would be required to open the door to the server room.

• Figure 8.4 Contactless access cards act as modern keys to a building.
Access to the server room should be limited to staff with a legitimate need to work on the servers. To layer the protection, the area surrounding the server room should also be limited to people who need to work in that area.
Locks
Locks have been discussed as a primary element of security. Although locks have been used for hundreds of years, their design has not changed much: a metal “token” is used to align pins in a mechanical device. As all mechanical devices have tolerances, it is possible to sneak through these tolerances by “picking” the lock. Most locks can be easily picked with simple tools, some of which are shown in Figure 8.5.

• Figure 8.5 Lockpicking tools
As we humans are always trying to build a better mousetrap, high-security locks, such as the one shown in Figure 8.6, have been designed to defeat attacks; these locks are more sophisticated than a standard home deadbolt system. Typically found in commercial applications that require high security, these locks are made to resist picking and drilling, as well as other common attacks such as simply pounding the lock through the door. Another common feature of high-security locks is key control, which refers to the restrictions placed on making a copy of the key. For most residential locks, a trip to the hardware store will allow you to make a copy of the key. Key control locks use patented keyways that can only be copied at a locksmith, who will keep records on authorized users of a particular key.

• Figure 8.6 A high-security lock and its key
High-end lock security is more important now that attacks such as “bump keys” are well known and widely available. A bump key is a key cut with all notches to the maximum depth, also known as “all nines.” This key uses a technique that has been around a long time, but has recently gained a lot of popularity. The key is inserted into the lock and then sharply struck, bouncing the lock pins up above the shear line and allowing the lock to open. High-security locks attempt to prevent this type of attack through various mechanical means such as nontraditional pin layout, sidebars, and even magnetic keys.
Other physical locks include programmable or cipher locks; locks with a keypad that require a combination of keys to open the lock; and locks with a reader that require an access card to open the lock. These may have special options such as a hostage alarm (which supports a key combination to trigger an alarm). Master-keying (which supports key combinations to change the access code and configure the functions of the lock) and key-override functions (which support key combinations to override the usual procedures) are also options on high-end programmable locks.

Layered access is a form of defense in depth, a principle component of any strong security solution.
Device locks are used to lock a device to a physical restraint, preventing its removal. Another method of securing laptops and mobile devices is a cable trap, which allows a user to affix a cable lock to a secure structure.
Doors
Doors to secured areas should have characteristics to make them less obvious. They should have similar appearance to the other doors to avoid catching the attention of intruders. Security doors should be self-closing and have no hold-open feature. They should trigger alarms if they are forcibly opened or have been held open for a long period.
Door systems, like many systems, have two design methodologies: fail-safe and fail-secure. While fail-safe is a common enough phrase to have entered the lexicon, think about what it really means—being safe when a system fails. In the case of these electronic door systems, fail-safe means that the door is unlocked should power fail. Fail-secure, on the other hand, means that the system will lock the door when power is lost. This can also apply when door systems are manually bypassed. It is important to know how each door will react to a system failure, not only for security but also for fire code compliance, as fail-secure is not allowed for certain doors in a building.

A fail-soft (or fail-safe) lock is unlocked in a power interruption, meaning the door defaults to being unlocked. A fail-secure lock is locked in a power interruption, meaning the door defaults to being locked.
Mantraps and Turnstiles
The implementation of a mantrap is one way to combat tailgating. A mantrap is composed of two doors closely spaced that require the user to card through one and then the other sequentially. Mantraps make it nearly impossible to trail through a doorway undetected—if you happen to catch the first door, you will be trapped in by the second door.
As shown here, a turnstile is a physical gated barrier that allows only one person at a time to pass. Turnstiles can also be used for exits, allowing only a single direction of traffic.


A mantrap/turnstile door arrangement can prevent unauthorized people from following authorized users through an access-controlled door, which is also known as tailgating.
Cameras
Closed-circuit television (CCTV) cameras are similar to the door control systems—they can be very effective, but how they are implemented is an important consideration. The use of CCTV cameras for surveillance purposes dates back to at least 1961, when cameras were installed in a London Transport train station. The development of smaller and more sophisticated camera components and decreasing prices for the cameras have caused a boom in the CCTV industry since then.
CCTV cameras are used to monitor a workplace for security purposes. These systems are commonplace in banks and jewelry stores, places with high-value merchandise that is attractive to thieves. As the expense of these systems dropped, they became practical for many more industry segments. Traditional cameras are analog and require a video multiplexer to combine all the signals and make multiple views appear on a monitor. IP-based cameras are changing that, as most of them are standalone units viewable through a web browser, such as the camera shown in Figure 8.7.

• Figure 8.7 IP-based cameras leverage existing IP networks instead of needing a proprietary CCTV cable.
These IP-based systems add useful functionality, such as the ability to check on the building from the Internet. This network functionality, however, makes the cameras subject to normal IP-based network attacks. A DoS attack launched at the CCTV system just as a break-in is occurring is the last thing anyone would want (other than the criminals). For this reason, IP-based CCTV cameras should be placed on their own separate network that can be accessed only by security personnel. The same physical separation applies to any IP-based camera infrastructure. Older time-lapse tape recorders are slowly being replaced with digital video recorders. While the advance in technology is significant, be careful if and when these devices become IP enabled, because they will become a security issue, just like everything else that touches the network.
PTZ Cameras
Pan-tilt-zoom (PTZ) cameras are ones that have the functionality to enable camera movement along multiple axes, as well as the ability to zoom in on an item. These cameras provide additional capability, especially in situations where the video is monitored and the monitoring station can maneuver the camera.
If you depend on the CCTV system to protect your organization’s assets, carefully consider camera placement and the type of cameras used. Different iris types, focal lengths, and color or infrared capabilities are all options that make one camera superior to another in a specific location.
Infrared Detection
Infrared (IR) radiation is not visible to the human eye, but can be used just like a light source to detect a range of things. Motion from living creatures can be seen because of the heat signatures of their bodies. Infrared detection is a technical means of looking for things that otherwise might not be noticed. At night, when it is dark, someone can hide in the shadows, but infrared light can point them out to IR-sensing cameras.
Motion Detection
When an area is being monitored for unauthorized activity, one potentially useful tool is a motion detector. In areas where there is little or no expected traffic, a motion detector can alert an operator to activity in an area. Motion detectors come in a variety of types, but most are based on infrared radiation (heat) and can detect the changes of a warm body moving. They can be tuned for size, ignoring smaller movement such as small animals in outdoor settings. Although not useful in busy office buildings during normal daily use, motion detectors can be useful during off-hours, when traffic is minimal. Motion detectors can be used to trigger video systems, so they do not record large amounts of “empty” activity. Video monitoring of the loading dock area in the back of the building can be triggered in this fashion, using the motion detector to turn on cameras whenever activity is occurring.
Safes
Safes are physical storage devices meant to increase the work factor for unauthorized personnel attempting to access the protected contents within. Safes come in a wide variety of shapes, sizes, and costs. The higher the level of protection from the physical environment, the better the level of protection against unauthorized access. Safes are not perfect; in fact, they are rated in terms of how long they can be expected to protect the contents from theft and/or fire. The better the rating, the more expensive the safe.
Secure Cabinets/Enclosures
There are times when using a safe is overkill—when it provides better levels of security than is really needed. A simpler solution is to use a secure cabinet or enclosure. Secure cabinets and enclosures provide system owners a place to park an asset until it’s needed. Most secure cabinets/enclosures do not offer all the levels of protection that one gets with a safe, but they can be useful, especially when the volume of secure storage is large.
Protected Distribution/Protected Cabling
Cable runs between systems need to be protected from physical damage to the cables and subsequent communication failures. This is accomplished by protected distribution/protected cabling during the cable installation. This may be something as simple as metal tubes, or as complex a concrete pipes to run buried cables. The objective is to prevent any physical damage to the physical layer portion of the system.
Airgap
Airgap is a term used to describe a network that is not physically connected to other networks. This separation was designed to prevent unauthorized data transfers to and from the network. The flaw in this logic is that users will move data by other means in order to get their work done. Frequently called sneakernet, this unauthorized bypassing of the airgap, although ostensibly for the purpose of mission accomplishment, increases system risk because it also bypasses checks, logging, and other processes important is development and deployment.
Faraday Cage
A Faraday cage, or Faraday shield, is an enclosure of conductive, grounded material designed to provide shielding against electromagnetic interference (EMI). These can be room-sized or built into a building’s construction; the critical element is that there is no significant gap in the enclosure material. These measures can help shield EMI, especially in high-radio-frequency environments.
EMI can plague any type of electronics, but the density of circuitry in the typical data center can make it a haven for EMI. EMI is defined as the disturbance on an electrical circuit caused by that circuit’s reception of electromagnetic radiation. Magnetic radiation enters the circuit by induction, where magnetic waves create a charge on the circuit. The amount of sensitivity to this magnetic field depends on a number of factors, including the length of the circuit, which can act like an antenna. EMI is grouped into two general types: narrowband and broadband. Narrowband is, by its nature, electromagnetic energy with a small frequency band and, therefore, is typically sourced from a device that is purposefully transmitting in the specified band. Broadband covers a wider array of frequencies and is typically caused by some type of general electrical power use such as power lines or electric motors. More information on EMI is provided in the section “Electromagnetic Environment” later in the chapter.
In the United States, the Federal Communications Commission (FCC) has responsibility for regulating products that produce EMI and has developed a program for equipment manufacturers to adhere to standards for EMI immunity. Modern circuitry is designed to resist EMI. Cabling is a good example; the twists in unshielded twisted pair (UTP)—or Category 5e, 6, 6a, and 7—cable is there to prevent EMI. EMI is also controlled by metal computer cases that are grounded; by providing an easy path to ground, the case acts as an EMI shield. Shielding can be important for network cabling. It is important not to run lengths of network cabling in parallel with power cables. Twisted pair offers some degree of protection, but in electrically noisy environments such as industrial facilities, shielded twisted pair (STP) may be necessary.
Cable Locks
Portable equipment has a principal feature of being moveable, but this can also be a problem because portable equipment, laptops, projectors and the like, can be easily removed or stolen. Cable locks provide a simple means of securing portable equipment to the furniture in the room where it resides. Cable locks can be used by road warriors to secure laptops from casual theft. They also can be used in open areas such as conference centers, or rooms where portable equipment is exposed to a wide range of visitors.
Screen Filters
Shoulder surfing is the process of looking over someone’s shoulder while they are typing, usually to read passwords or other sensitive information. Given the close physical spacing on today’s aircraft and other public conveyances, if one is going to use a laptop, others are going to have access to see the screen. Screen filters are optical filters that limit the angle of viewability to a very narrow range, making it difficult for others to visually eavesdrop. Screen filters have a wide range of uses—for road warrior laptops, kiosks, reception desks, as well as places where sensitive data is displayed, such as medical data in medical environments.

Some physical security equipment is used to secure aspects of mobile devices. Screen filters secure screens from observation, whereas cable locks prevent equipment theft. These are both preventative agents and should be matched on an exam to specific threats, such as copying information for screen filters, and theft of devices for cable locks.
Key Management
Physical locks have physical keys, and keeping track of who has what keys can be a chore. Add in master keys and maintaining a list of who has physical access to each space can quickly become a task requiring a software solution. Key management is the process of keeping track of where the keys are and who has access to what. A physical security environment that does not have a means of key management is living on borrowed time. Key management will be essential when something goes wrong and the question arises of who has keys that can give them access.
Logs
Physical security logs provide the same utility that computer logs do for a security investigation. They act as a record of what was observed at specific points in time. Having roving guards check in at various places across a shift via a log entry provides a record of the actual surveillance. Logs of visitors going in and out and equipment going in and out, as well as other types of log entries, serve as a record of the physical happenings in a facility.

Cameras, IR detection, motion detection, and logs are all methods associated with detection, and frequently after-the-fact detection at that. These devices and methods provide valuable attribution fact patterns, even after an actual event.
Electronic Access Control Systems
Access tokens are defined as “something you have.” An access token is a physical object that identifies specific access rights. Access tokens are frequently used for physical access solutions, just as your house key is a basic physical access token that allows you access into your home. Although keys have been used to unlock devices for centuries, they do have several limitations. Keys are paired exclusively with a lock or a set of locks, and they are not easily changed. It is easy to add an authorized user by giving the user a copy of the key, but it is far more difficult to give that user selective access unless that specified area is already set up as a separate key. It is also difficult to take access away from a single key or key holder, which usually requires a rekey of the whole system.
Master Keys
Mechanical keying systems with industrial-grade locks have provisions for multiple master keys. This allows individual master keys to be designated by floor, by department, for the whole building, and so forth. This provides tremendous flexibility, although if a master key is lost, significant rekeying will be required.
Tokens/Cards
Physical access to a facility can be via a door, but who keeps random visitors from using the same door? For some doors, a physical key can be used to unlock the door. For facilities with larger numbers of people coming and going, a badging system using either tokens or cards that can be tied to automated ID checks, in addition to the logging of entry/exit, can provide much greater detail in tracking who is in the facility and when they have come and gone. Tokens and cards can be enabled to provide a serialized ID for each user, thus enabling user-specific logging. Originally designed to augment payroll time cards, these electronic IDs have improved security through the logging of employees’ in and out times.
In many businesses, physical access authentication has moved to contactless radio frequency cards and proximity readers. When passed near a card reader, the card sends out a code using radio waves. The reader picks up this code and transmits it to the control panel. The control panel checks the code against the reader from which it is being read and the type of access the card has in its database. One of the advantages of this kind of token-based system is that any card can be deleted from the system without affecting any other card or the rest of the system. The RFID-based contactless entry card shown in Figure 8.8 is a common form of this token device employed for door controls and is frequently put behind an employee badge. In addition, all doors connected to the system can be segmented in any form or fashion to create multiple access areas, with different permissions for each one. The tokens themselves can also be grouped in multiple ways to provide different access levels to different groups of people. All of the access levels or segmentation of doors can be modified quickly and easily if building space is retasked. Newer technologies are adding capabilities to the standard token-based systems.

• Figure 8.8 Smart cards have an internal chip as well as multiple external contacts for interfacing with a smart card reader.
The advent of smart cards (cards that contain integrated circuits capable of generating and storing cryptographic keys) has enabled cryptographic types of authentication. Smart card technology has proven reliable enough that it is now part of a governmental standard for physical and logical authentication. Known as personal identity verification (PIV) cards, they adhere to the FIPS 201 standard. These smart cards include a cryptographic chip and connector, as well as a contactless proximity card circuit. They also have standards for a photo and name printed on the front. Biometric data can be stored on the cards, providing an additional authentication factor, and if the PIV standard is followed, several forms of identification are needed in order to get a card.
Personnel ID Badges
Having personnel wear a visible ID badge with their picture is a common form of physical security. If everyone is supposed to wear a badge visibly, then anyone who sees someone without a badge can ask them who they are, and why they are there. This greatly increases the number of eyes watching for intruders in large, publicly accessible facilities.
The primary drawback of token-based authentication is that only the token is being authenticated. Therefore, the theft of the token could grant anyone who possesses the token access to what the system protects. The risk of theft of the token can be offset by the use of multiple-factor authentication. One of the ways that people have tried to achieve multiple-factor authentication is to add a biometric factor to the system.
Biometrics
Biometrics use the measurements of certain biological factors to identify one specific person from others. These factors are based on parts of the human body that are unique. The most well-known of these unique biological factors is the fingerprint. Fingerprint readers have been available for several years in laptops—and more recently in smartphones. These come in a variety of form factors, such as the example shown in Figure 8.9, and as standalone USB devices.

• Figure 8.9 Newer laptop computers often include a fingerprint reader.
Convergence
There is a trend toward converging elements of physical and information security in order to improve identification of unauthorized activity on networks. For example, if an access control system is asked to approve access to an insider using an outside address, yet the physical security system identifies them as being inside the building, then an anomaly exists and should be investigated. This trend of convergence can significantly improve defenses against cloned credentials.
Policies and Procedures
A policy’s effectiveness depends on the culture of an organization, so all the policies mentioned here should be followed up by functional procedures that are designed to implement them. Physical security policies and procedures relate to two distinct areas: those that affect the computers themselves and those that affect users.
To mitigate the risk to computers, physical security needs to be extended to the computers themselves. To combat the threat of bootdisks, begin by removing or disabling the ability of a system to automatically play connected devices, such as USB flash drives. Other activities that typically require physical presence should be protected, such as access to a system’s BIOS at bootup.
BIOS
A safeguard that can be employed is the removal of removable media devices from the boot sequence in the computer’s BIOS (basic input/output system). The specifics of this operation depend on the BIOS software of the individual machine. A related step that must be taken is to set a BIOS password. Nearly all BIOS software will support password protection that allows you to boot the machine but requires a password to edit any BIOS settings. Although disabling the optical drive and setting a BIOS password are both good measures, do not depend on this strategy exclusively because, in some cases, BIOS manufacturers will have a default BIOS password that still works.

Depending upon BIOS passwords is also not a guaranteed security measure. For many machines, it is trivial to remove and then replace the BIOS battery, which will reset the BIOS to the “no password” or default password state.
Exploring Your BIOS Settings
Next time you boot your PC, explore the BIOS settings. Usually, pressing the F2 key immediately on power-up will allow you to enter the BIOS setup screens. Most PCs will also have a brief time when they prompt for “Setup” and give a key to press, most commonly F2 or f12. Explore elements such as the boot order for devices, options for adding passwords, and other options. For safety, do not save changes unless you are absolutely certain that you want to make those changes and are aware of the consequences. To prevent an attacker from editing the boot order, you should set BIOS passwords.

USB devices can be used to inject malicious code onto any machine to which they are attached. They can be used to transport malicious code from machine to machine without using the network.
UEFI
Unified Extensible Firmware Interface (UEFI) is a standard firmware interface for PCs, designed to replace BIOS. Supported by macOS, Linux (later versions), and Windows 8 and beyond, UEFI offers some significant security advantages. UEFI has a functionality known as secure boot, which allows only digitally signed drivers and OS loaders to be used during the boot process, preventing bootkit attacks. As UEFI is replacing BIOS, and provides additional characteristics, it is important to keep policies and procedures current with the advancement of technology.

Laptops and tablets are popular targets for thieves and should be locked inside a desk when not in use, or secured with special computer lockdown cables. If desktop towers are used, use computer desks that provide a space in which to lock the computer. All of these measures can improve the physical security of the computers themselves, but most of them can be defeated by attackers if users are not knowledgeable about the security program and do not follow it.
USB
USB ports have greatly expanded users’ ability to connect devices to their computers. USB ports automatically recognize a device being plugged into the system and usually work without the user needing to add drivers or configure software. This has spawned a legion of USB devices, from MP3 players to CD burners.
The most interesting of these, for security purposes, are the USB flash memory–based storage devices. USB drive keys, which are basically flash memory with a USB interface in a device typically about the size of your thumb, provide a way to move files easily from computer to computer. When plugged into a USB port, these devices automount and behave like any other drive attached to the computer. Their small size and relatively large capacity, coupled with instant read-write capability, present security problems. They can easily be used by an individual with malicious intent to conceal the removal of files or data from the building or to bring malicious files into the building and onto the company network.
In addition, well-intentioned users could accidentally introduce malicious code from a USB device by using it on an infected home machine and then bringing the infected device to the office, allowing the malware to bypass perimeter protections and possibly infect the organization. If USB devices are allowed, aggressive virus scanning should be implemented throughout the organization. The devices can be disallowed via Active Directory policy settings or with a Windows Registry key entry. USB can also be completely disabled, either through BIOS settings or by unloading and disabling the USB drivers from users’ machines, either of which will stop all USB devices from working. However, doing this can create more trouble if users have USB keyboards and mice. There are two common ways to disable USB support in a Windows system. On older systems, editing the Registry key is probably the most effective solution for users who are not authorized to use these devices. On newer systems, the best way is through Group Policy in a domain or through the Local Security Policy MMC on a standalone box.
Autoplay
Another boot device to consider is the CD/DVD drive. This device can probably also be removed from or disabled on a number of machines. A DVD not only can be used as a boot device, but also can be exploited via the autoplay feature that some operating systems support. Autoplay was designed as a convenience for users, so that when a CD/DVD or USB containing an application is inserted, the computer instantly prompts for input versus requiring the user to explore the device file system and find the executable file. Unfortunately, because the autoplay functionality runs an executable, it can be programmed to do anything an attacker wants. If an autoplay executable is malicious, it could allow an attacker to gain remote control of the machine. Figure 8.10 illustrates an autoplay message prompt in Windows, giving a user at least minimal control over whether to run an item or not.
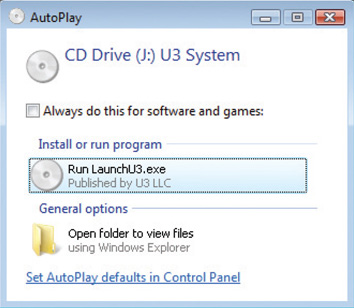
• Figure 8.10 Autoplay on a Windows system
Since the optical drive can be used as a boot device, a DVD loaded with its own operating system (called a LiveCD, introduced earlier in the chapter) could be used to boot the computer with malicious system code (see Figure 8.11). This separate operating system will bypass any passwords on the host machine and can access locally stored files.
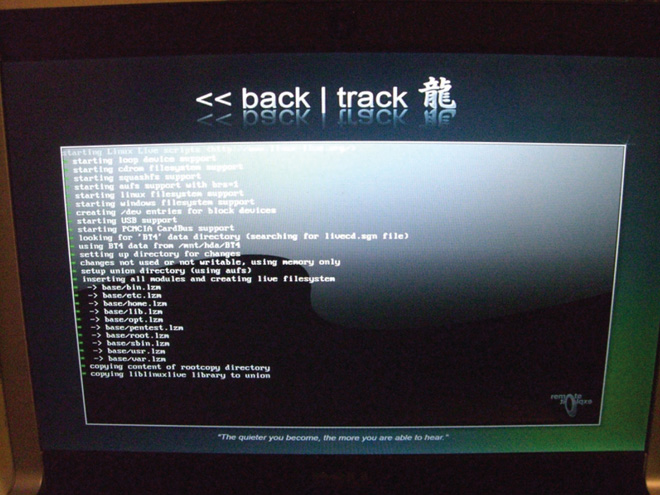
• Figure 8.11 A LiveCD boots its own OS and bypasses any built-in security of the native operating system.
Disabling the Autoplay Feature in Windows
Disabling the autoplay feature is an easy task using Local Group Policy Editor in Windows. Simply launch the Local Group Policy Editor (gpedit.msc) and navigate to this location:
Computer Configuration | Administrative Templates | Windows Components | AutoPlay Policies

Device Theft
The outright theft of a computer is a simple physical attack. This attack can be mitigated in a number of ways, but the most effective method is to lock up equipment that contains important data. Insurance can cover the loss of the physical equipment, but this can do little to get a business up and running again quickly after a theft. Therefore, implementing special access controls for server rooms and simply locking the rack cabinets when maintenance is not being performed are good ways to secure an area. From a data standpoint, mission-critical or high-value information should be stored on a server only. This can mitigate the risk of a desktop or laptop being stolen for the data it contains. Loss of laptops has been a common cause of information breaches.

Mobile device thefts from cars and other locations can occur in seconds. Thieves have been caught taking mobile devices from security screening areas at airports while the owner was distracted in screening. Snatch-and-grab attacks occur in restaurants, bars, and cafes. Tablets and smartphones have significant value, and physical precautions should be taken at all times.
Mobile Device Security
Mobile device security is covered in depth in Chapter 12. For a more detailed analysis of safeguards unique to mobile devices, refer that that chapter.
Users can perform one of the most simple, yet important, information security tasks: lock their workstation immediately before they step away from it.
Although use of a self-locking screensaver is a good policy, setting it to lock at any point less than 10 to 15 minutes after becoming idle is often considered a nuisance and counterproductive to active use of the computer on the job because the computer will often lock while the employee is still actively using it. Thus, computers typically sit idle for at least 15 minutes before automatically locking under this type of policy. Users should manually lock their workstations, as an attacker only needs to be lucky enough to catch a machine that has been left alone for five minutes.

BTU stands for British thermal unit. A single BTU is defined as the amount of energy required to raise the temperature of one pound of liquid water one degree Fahrenheit.
 Environmental Controls
Environmental Controls
While the confidentiality of information is important, so is its availability. Sophisticated environmental controls are needed for current data centers. Servers can generate large levels of heat, and managing the heat is the job of the environmental control.
Controlling a data center’s temperature and humidity is important to keeping servers running. Heating ventilating and air conditioning (HVAC) systems are critical for keeping data centers cool, because typical servers put out between 1000 and 2000 BTUs of heat. The temperature of a data center should be maintained between 70 and 74 degrees Fahrenheit (oF). If the temperature is too low, it may cause mechanisms to slow down. If the temperature is too high, it may cause equipment damage. The temperature-damaging points of different products are as follows:
![]() Magnetic media: 100oF
Magnetic media: 100oF
![]() Computer hardware: 175oF
Computer hardware: 175oF
![]() Paper products: 350oF
Paper products: 350oF
It should be noted that these are temperatures of the materials; the surrounding air is frequently cooler. Temperature measurements should be obtained on equipment itself to ensure appropriate protection.
Multiple servers in a confined area can create conditions too hot for the machines to continue to operate. This problem is made worse with the advent of blade-style computing systems and with many other devices shrinking in size. Although physically smaller, they tend to still expel the same amount of heat. This is known as increased data center density—more servers and devices per rack, putting a greater load on the cooling systems. This encourages the use of a hot aisle/cold aisle layout. A data center that is arranged into hot and cold aisles dictates that all the intake fans on all equipment face the cold aisle, and the exhaust fans all face the opposite aisle. The HVAC system is then designed to push cool air underneath the raised floor and up through perforated tiles on the cold aisle. Hot air from the hot aisle is captured by return air ducts for the HVAC system. The use of this layout is designed to control airflow, with the purpose being never to mix the hot and cold air. This requires the use of blocking plates and side plates to close open rack slots. The benefits of this arrangement are that cooling is more efficient and can handle higher density. The failure of HVAC systems for any reason is cause for concern. Rising copper prices have made HVAC systems the targets for thieves, and general vandalism can result in costly downtime. Properly securing these systems is important in helping prevent an attacker from performing a physical DoS attack on your servers.
 Fire Suppression
Fire Suppression
According to the Fire Suppression Systems Association (www.fssa.net), 43 percent of businesses that close as a result of a significant fire never reopen. An additional 29 percent fail within three years of the event. The ability to respond to a fire quickly and effectively is thus critical to the long-term success of any organization. Addressing potential fire hazards and vulnerabilities has long been a concern of organizations in their risk analysis process. The goal obviously should be never to have a fire, but in the event that one does occur, it is important that mechanisms are in place to limit the damage the fire can cause.
Environment and Fires
Although it may at first seem to the security professional that environmental controls and natural disasters such as fires don’t have anything to do with computer security, think of it in terms of availability. If the goal of the attacker is not information but rather to deny an organization the use of its resources, environmental factors and disasters such as fires can be used to deny the target the use of its own computing resources. This, then, becomes a security issue as well as an operational issue.
Water-Based Fire Suppression Systems
Water-based fire suppression systems have long been, and still are today, the primary tool to address and control structural fires. Considering the amount of electrical equipment found in today’s office environment and the fact that, for obvious reasons, this equipment does not react well to large applications of water, it is important to know what to do with equipment if it does become subjected to a water-based sprinkler system. The National Fire Protection Association’s NFPA 75, “Standard for the Protection of Information Technology Equipment,” from 2013, outlines measures that can be taken to minimize the damage to electronic equipment exposed to water. This guidance includes these suggestions:
![]() Open cabinet doors, remove side panels and covers, and pull out chassis drawers to allow water to run out of equipment.
Open cabinet doors, remove side panels and covers, and pull out chassis drawers to allow water to run out of equipment.
![]() Set up fans to move room-temperature air through the equipment for general drying. Move portable equipment to dry air-conditioned areas.
Set up fans to move room-temperature air through the equipment for general drying. Move portable equipment to dry air-conditioned areas.
![]() Use compressed air at no higher than 50 psi to blow out trapped water.
Use compressed air at no higher than 50 psi to blow out trapped water.
![]() Use handheld dryers on lowest setting to dry connectors, backplane wirewraps, and printed circuit cards.
Use handheld dryers on lowest setting to dry connectors, backplane wirewraps, and printed circuit cards.
![]() Use cotton-tipped swabs for hard-to-reach places. Lightly dab the surfaces to remove residual moisture.
Use cotton-tipped swabs for hard-to-reach places. Lightly dab the surfaces to remove residual moisture.
Even if these guidelines are followed, damage to the systems may have already occurred. Because water is so destructive to electronic equipment, not only because of the immediate problems of electronic shorts to the system but also because of longer-term corrosive damage water can cause, alternative fire suppression methods have been sought.
Drills
In the event of an emergency, people will be challenged to perform correct actions when stressed by the emergency. The use of drills, plans, and testing will ensure that escape plans and escape routes are known and effective and that people are familiar with their use. The time to practice is before the problem, and repeating practice over time builds confidence and strengthens familiarity.
Halon-Based Fire Suppression Systems
A fire needs fuel, oxygen, and high temperatures for the chemical combustion to occur. If you remove any of one these elements, the fire will not continue. Halon interferes with the chemical combustion present in a fire. Even though halon production was banned in 1994, a number of these systems still exist today. They were originally popular because halon will mix quickly with the air in a room and will not cause harm to computer systems. Halon is, however, dangerous to humans, especially when subjected to extremely hot temperatures (such as might be found during a fire), when it can degrade into other toxic chemicals. As a result of these dangers, and also because halon has been linked with the issue of ozone depletion, halon is banned in new fire suppression systems. It is important to note that under the Environmental Protection Agency (EPA) rules that mandated no further production of halon, existing systems were not required to be destroyed. Replacing the halon in a discharged system, however, will be a problem, since only existing stockpiles of halon may be used and the cost is becoming prohibitive. For this reason, many organizations are switching to alternative solutions.
Clean-Agent Fire Suppression Systems
These alternatives are known as clean-agent fire suppression systems, because they not only provide fire suppression capabilities but also protect the contents of the room, including people, documents, and electronic equipment. Examples of clean agents include carbon dioxide, argon, Inergen, and FM-200 (heptafluoropropane). Carbon dioxide (CO2) has been used as a fire suppression agent for a long time. The Bell Telephone Company used portable CO2 extinguishers in the early part of the 20th century. Carbon dioxide extinguishers attack all three necessary elements for a fire to occur. CO2 displaces oxygen so that the amount of oxygen remaining is insufficient to sustain the fire. It also provides some cooling in the fire zone and reduces the concentration of “gasified” fuel. Argon extinguishes fire by lowering the oxygen concentration below the 15 percent level required for combustible items to burn. Argon systems are designed to reduce the oxygen content to about 12.5 percent, which is below the 15 percent needed for the fire but is still above the 10 percent required by the EPA for human safety. Inergen, a product of the Ansul Corporation, is composed of three gases: 52 percent nitrogen, 40 percent argon, and 8 percent carbon dioxide. In a manner similar to pure argon systems, Inergen systems reduce the level of oxygen to about 12.5 percent, which is sufficient for human safety but not sufficient to sustain a fire. Another chemical used in the phase-out of halon is FE-13, or trifluoromethane. This chemical was originally developed as a refrigerant and works to suppress fires by inhibiting the combustion chain reaction. FE-13 is gaseous, leaves behind no residue that would harm equipment, and is considered safe to use in occupied areas. Other halocarbons are also approved for use in replacing halon systems, including FM-200 (heptafluoropropane), a chemical used as a propellant for asthma medication dispensers.
Handheld Fire Extinguishers
Automatic fire suppression systems designed to discharge when a fire is detected are not the only systems you should be aware of. If a fire can be caught and contained before the automatic systems discharge, it can mean significant savings to the organization in terms of both time and equipment costs (including the recharging of the automatic system). Handheld extinguishers are common in offices, but the correct use of them must be understood or else disaster can occur. There are four different types of fire, as shown in Table 8.1. Each type of fire has its own fuel source and method for extinguishing it. Type A systems, for example, are designed to extinguish fires with normal combustible material as the fire’s source. Water can be used in an extinguisher of this sort because it is effective against fires of this type. Water, as we’ve discussed, is not appropriate for fires involving wiring or electrical equipment. Using a type A extinguisher against an electrical fire will not only be ineffective but can result in additional damage. Some extinguishers are designed to be effective against more than one type of fire, such as the common ABC fire extinguishers. This is probably the best type of system to have in a data processing facility. All fire extinguishers should be easily accessible and should be clearly marked. Before anybody uses an extinguisher, they should know what type of extinguisher it is and what the source of the fire is. When in doubt, evacuate and let the fire department handle the situation.

The type of fire distinguishes the type of extinguisher that should be used to suppress it. Remember that the most common type is the ABC fire extinguisher, which is designed to handle all types of fires except flammable-metal fires, which are rare.
Table 8.1 Types of Fire and Suppression Methods

Handheld Fire Extinguishers
Computer security professionals typically do not have much influence over the type of fire suppression system that their office includes. It is, however, important that they are aware of what type has been installed, what they should do in case of an emergency, and what needs to be done to recover after the release of the system. One area that they can influence, however, is the type of handheld fire extinguisher located in their area. Check your facility to see what type of fire suppression system is installed. Also check to see where the fire extinguishers are in your office and what type of fires they are designed to handle.
Fire Detection Devices
An essential complement to fire suppression systems and devices are fire detection devices (fire detectors). Detectors may be able to detect a fire in its very early stages, before a fire suppression system is activated, and sound a warning that potentially enables employees to address the fire before it becomes serious enough for the fire suppression equipment to kick in.
There are several different types of fire detectors. One type, of which there are two varieties, is activated by smoke. The two varieties of smoke detector are ionization and photoelectric. A photoelectric detector is good for potentially providing advance warning of a smoldering fire. This type of device monitors an internal beam of light. If something degrades the light (for example, by obstructing it), the detector assumes it is something like smoke and the alarm sounds. An ionization style of detector uses an ionization chamber and a small radioactive source to detect fast-burning fires. Shown in Figure 8.12, the chamber consists of two plates—one with a positive charge and one with a negative charge. Oxygen and nitrogen particles in the air become “ionized” (an ion is freed from the molecule). The freed ion, which has a negative charge, is attracted to the positive plate, and the remaining part of the molecule, now with a positive charge, is attracted to the negative plate. This movement of particles creates a very small electric current that the device measures. Smoke inhibits this process, and the detector will detect the resulting drop in current and sound an alarm. Both of these devices are often referred to generically as smoke detectors, and combinations of both varieties are possible. For more information on smoke detectors, see http://home.howstuffworks.com/home-improvement/household-safety/fire/smoke2.htm.

• Figure 8.12 An ionization chamber for an ionization type of smoke detector
Testing Controls
Because of the importance of their protection, safety controls should be periodically tested for proper operation and alerting. This should be a system-level, not device-level, test to ensure the entire control system performs in the intended manner.
Another type of fire detector is activated by heat. These devices also come in two varieties. Fixed-temperature or fixed-point devices activate if the temperature in the area ever exceeds some predefined level. Rate-of-rise or rate-of-increase temperature devices activate when there is a sudden increase in local temperature that may indicate the beginning stages of a fire. Rate-of-rise sensors can provide an earlier warning but are also responsible for more false warnings.
A third type of detector is flame activated. This type of device relies on the flames from the fire to provide a change in the infrared energy that can be detected. Flame-activated devices are generally more expensive than the other two types but can frequently detect a fire sooner.
 Electromagnetic Environment
Electromagnetic Environment
In 1985, a paper by Wim van Eck of the Netherlands described what became known as the van Eck phenomenon. In the paper, van Eck described how eavesdropping on what was being displayed on monitors could be accomplished by picking up and then decoding the electromagnetic interference produced by the monitors. With the appropriate equipment, the exact image of what is being displayed can be re-created some distance away. While the original paper discussed emanations as they applied to video display units (monitors), the same phenomenon applies to other devices such as printers and computers.
This phenomenon had actually been known about for quite some time before van Eck published his paper. The U.S. Department of Defense used the term TEMPEST (referred to by some as the Transient ElectroMagnetic Pulse Emanation STandard) to describe both a program in the military to control these electronic emanations from electrical equipment and the actual process for controlling the emanations. There are three basic ways to prevent these emanations from being picked up by an attacker:
![]() Put the equipment beyond the point that the emanations can be picked up.
Put the equipment beyond the point that the emanations can be picked up.
![]() Provide shielding for the equipment itself.
Provide shielding for the equipment itself.
![]() Provide a shielded enclosure (such as a room) to put the equipment in.
Provide a shielded enclosure (such as a room) to put the equipment in.
One of the simplest ways to protect against equipment being monitored in this fashion is to put enough distance between the target and the attacker. The emanations can be picked up from only a limited distance. If the physical security for the facility is sufficient to put enough space between the equipment and publicly accessible areas that the signals cannot be picked up, then the organization doesn’t have to take any additional measures to ensure security.

One of the challenges in security is determining how much to spend on security without spending too much. Security spending should be based on likely threats to your systems and network. While electronic emanations can be monitored, the likelihood of this taking place in most situations is remote, which makes spending on items to protect against it at best a low priority.
Distance is not the only way to protect against eavesdropping on electronic emanations. Devices can be shielded so their emanations are blocked. Acquiring enough property to provide the necessary distance needed to protect against an eavesdropper may be possible if the facility is in the country with lots of available land surrounding it. Indeed, for smaller organizations that occupy only a few offices or floors in a large office building, it would be impossible to acquire enough space. In this case, the organization may resort to purchasing shielded equipment. A “TEMPEST approved” computer will cost significantly more than what a normal computer would cost. Shielding a room (e.g., using a Faraday cage) is also an extremely expensive endeavor.
A natural question to ask is, how prevalent is this form of attack? The equipment needed to perform electromagnetic eavesdropping is not readily available, but it would not cost an inordinate amount of money to produce it. The cost could certainly be afforded by any large corporation, and industrial espionage using such a device is a possibility. Although there are no public records of this sort of activity being conducted, it is reasonable to assume that it does take place in large corporations and the government, especially in foreign countries.
Modern Eavesdropping
Not just electromagnetic information can be used to carry information out of a system to an adversary. Recent advances have demonstrated the feasibility of using the webcams and microphones on systems to spy on users, recording keystrokes and other activities. There are even devices built to intercept the wireless signals between wireless keyboards and mice and transmit them over another channel to an adversary. USB-based keyloggers can be placed in the back of machines, because in many cases the back of a machine is unguarded or facing the public (watch for this the next time you see a receptionist’s machine).
 Power Protection
Power Protection
Computer systems require clean electrical power, and for critical systems, uninterrupted power can be important as well. Several elements are used to manage the power to systems, including uninterruptible power supplies and backup power systems.
UPS
An uninterruptible power supply (UPS) is used to protect against short-duration power failures. There are two types of UPS: online and standby. An online UPS is in continuous use because the primary power source goes through it to the equipment. It uses AC line voltage to charge a bank of batteries. When the primary power source fails, an inverter in the UPS will change the DC of the batteries into AC. A standby UPS has sensors to detect power failures. If there is a power failure, the load will be switched to the UPS. It stays inactive before a power failure, and takes more time than an online UPS to provide power when the primary source fails.
UPS Attributes
UPS systems have several attributes to consider:
![]() The electrical load they can support (measured in kVA)
The electrical load they can support (measured in kVA)
![]() The length of time they can support the load
The length of time they can support the load
![]() The speed of providing power when there is a power failure
The speed of providing power when there is a power failure
![]() The physical space they occupy
The physical space they occupy
Backup Power and Cable Shielding
A backup power source, such as a motor generator or another electrical substation, is used to protect against a long-duration power failure. A voltage regulator and line conditioner are used to protect against unstable power supply and spikes. Proper grounding is essential for all electrical devices to protect against short circuits and static electricity.
In more sensitive areas, cable shielding can be employed to avoid interference. Power line monitoring can be used to detect changes in frequency and voltage amplitude, warning of brownouts or spikes. An emergency power-off (EPO) switch can be installed to allow for the quick shutdown of power when required. To prevent electromagnetic interference and voltage spikes, electrical cables should be placed away from powerful electrical motors and lighting. Another source of power-induced interference can be fluorescent lighting, which can cause radio frequency interference.
Chapter 8 Review
 Chapter Summary
Chapter Summary
After reading this chapter and completing the exercises, you should understand the following facts about how physical security impacts network security.
Describe how physical security directly affects computer and network security
![]() Physical access defeats all network security protections.
Physical access defeats all network security protections.
![]() Bootdisks allow file system access.
Bootdisks allow file system access.
![]() Drive imaging is simple to accomplish with physical access.
Drive imaging is simple to accomplish with physical access.
![]() Access to the internal network is simple with physical access.
Access to the internal network is simple with physical access.
![]() Theft of hardware can be an attack in and of itself.
Theft of hardware can be an attack in and of itself.
Discuss steps that can be taken to help mitigate risks
![]() Removal of floppy drives and other media drives when they are unnecessary can help mitigate bootdisk attacks.
Removal of floppy drives and other media drives when they are unnecessary can help mitigate bootdisk attacks.
![]() Removal of CD-ROM devices also makes physical access attacks more difficult.
Removal of CD-ROM devices also makes physical access attacks more difficult.
![]() BIOS passwords should be used to protect the boot sequence.
BIOS passwords should be used to protect the boot sequence.
![]() USB devices are a threat; if possible, USB drivers should be removed.
USB devices are a threat; if possible, USB drivers should be removed.
![]() All users need security training.
All users need security training.
![]() Authentication systems should use multiple factors when feasible.
Authentication systems should use multiple factors when feasible.
Describe the physical security components that can protect your computers and network
![]() Physical security consists of all mechanisms used to ensure that physical access to the computer systems and networks is restricted to only authorized users.
Physical security consists of all mechanisms used to ensure that physical access to the computer systems and networks is restricted to only authorized users.
![]() The purpose of physical access controls is the same as that of computer and network access controls—to restrict access to only those who are authorized to have it.
The purpose of physical access controls is the same as that of computer and network access controls—to restrict access to only those who are authorized to have it.
![]() The careful placement of equipment can provide security for known security problems exhibited by wireless devices and that arise due to electronic emanations.
The careful placement of equipment can provide security for known security problems exhibited by wireless devices and that arise due to electronic emanations.
Identify environmental factors that can affect security
![]() Environmental issues are important to security because they can affect the availability of a computer system or network.
Environmental issues are important to security because they can affect the availability of a computer system or network.
![]() Loss of HVAC systems can lead to overheating problems that can affect electronic equipment, including security-related devices.
Loss of HVAC systems can lead to overheating problems that can affect electronic equipment, including security-related devices.
![]() Fires are a common problem for organizations. Two general approaches to addressing this problem are fire detection and fire suppression.
Fires are a common problem for organizations. Two general approaches to addressing this problem are fire detection and fire suppression.
Identify the different types of fires and the various fire suppression systems designed to limit the damage caused by fires
![]() Fires can be caused by and can consume a number of different materials. It is important to recognize what type of fire is occurring, because the extinguisher to use depends on the type of fire.
Fires can be caused by and can consume a number of different materials. It is important to recognize what type of fire is occurring, because the extinguisher to use depends on the type of fire.
![]() The ABC fire extinguisher is the most common type and is designed to handle most types of fires. The only type of fire it is not designed to address is one with combustible metals.
The ABC fire extinguisher is the most common type and is designed to handle most types of fires. The only type of fire it is not designed to address is one with combustible metals.
Explain electronic access controls and the principles of convergence
![]() Access controls should have layered areas and electronic access control systems.
Access controls should have layered areas and electronic access control systems.
![]() Electronic physical security systems need to be protected from network-based attacks.
Electronic physical security systems need to be protected from network-based attacks.
Prevent disclosure through electronic emanations
![]() With the appropriate equipment, the exact image of what is being displayed on a computer monitor can be re-created some distance away, allowing eavesdroppers to view what you are doing.
With the appropriate equipment, the exact image of what is being displayed on a computer monitor can be re-created some distance away, allowing eavesdroppers to view what you are doing.
![]() Providing a lot of distance between the system you wish to protect and the closest place an eavesdropper could be is one way to protect against eavesdropping on electronic emanations. Devices can also be shielded so that their emanations are blocked.
Providing a lot of distance between the system you wish to protect and the closest place an eavesdropper could be is one way to protect against eavesdropping on electronic emanations. Devices can also be shielded so that their emanations are blocked.
 Key Terms
Key Terms
access tokens (217)
autoplay (220)
biometrics (218)
BIOS passwords (219)
bootdisk (206)
closed-circuit television (CCTV) (214)
contactless access cards (212)
convergence (218)
Faraday cage (215)
layered access (211)
lighting (209)
LiveCD (207)
mantrap (213)
physical access control (211)
policies and procedures (218)
smart cards (218)
TEMPEST (227)
turnstile (213)
Unified Extensible Firmware Interface (UEFI) (219)
USB devices (219)
 Key Terms Quiz
Key Terms Quiz
Use terms from the Key Terms list to complete the sentences that follow. Don’t use the same term more than once. Not all terms will be used.
1. A door system designed to only allow a single person through is called a(n) _______________.
2. _______________ include MP3 players and flash drives.
3. _______________ is the program to control these electronic emanations from electrical equipment.
4. Removable media from which a computer can be booted is called a(n) _______________.
5. _______________ forces a user to authenticate again when entering a more secure area.
6. Items carried by the user to allow them to be authenticated are called _______________.
7. _______________ is the measurement of unique biological properties such as the fingerprint.
8. _______________ prevent an attacker from making a machine boot off its DVD drive.
9. _______________ is a system where the camera and monitor are directly linked.
10. Continuous, standby, Trip, and emergency are all types of _______________.
 Multiple-Choice Quiz
Multiple-Choice Quiz
1. What is the most common example of an access token?
A. Smart card
B. Handwriting sample
C. PDA
D. Key
2. What is used in data centers for fire extinguishers?
A. CO2 fire extinguishers
B. Water Sprinklers
C. Dry agent extinguishers
D. Special non-conductive foam agents
3. Probably the simplest physical attack on the computer system is which of the following?
A. Accessing an Ethernet jack to attack the network
B. Using an imitation to fool a biometric authenticator
C. Installing a virus on the CCTV system
D. Outright theft of a computer
4. What is a common threat to token-based access controls?
A. The key
B. Demagnetization of the strip
C. A system crash
D. Loss or theft of the token
5. Why can USB flash drives be a threat?
A. They use too much power.
B. They can bring malicious code past other security mechanisms.
C. They can be stolen.
D. They can be encrypted.
6. Why is HVAC important to computer security?
A. Sabotage of the AC unit could take out the electrical power.
B. Sabotage of the AC unit would make the computers overheat and shut down.
C. The AC units could be connected to the network.
D. HVAC is not important to security.
7. Why should security guards get cross-training in network security?
A. They are the eyes and ears of the corporation when it comes to security.
B. They are the only people in the building at night.
C. They are more qualified to know what a security threat is.
D. They have the authority to detain violators.
8. Emergency exit doors for manned security sensitive spaces should be what type of door?
A. Fail-secure
B. Fail-safe
C. Unlocked at all times
D. Locked unless monitored
9. Why is physical security so important to good network security?
A. Because encryption is not involved
B. Because physical access defeats nearly all network security measures
C. Because an attacker can steal biometric identities
D. Authentication
10. How high should a fence be to deter casual climbing?
A. Five feet if the fence is monitored visually
B. Ten feet
C. Seven feet
D. Eight feet or higher with barbed wire.
 Essay Questions
Essay Questions
1. You have been asked to report on the feasibility of installing an IP CCTV camera system at your organization. Detail the pros and cons of an IP CCTV system and how you would implement the system.
2. Write a memo justifying layered access for devices in an organization.
3. Write a memo justifying more user education about physical security.
4. Write a sample policy regarding the use of USB devices in an organization.
Lab Projects
• Lab Project 8.1
Load a LiveCD on your machine and examine the tools it provides. You will need the following materials:
![]() A computer with a version of Windows installed and a CD/DVD burner
A computer with a version of Windows installed and a CD/DVD burner
![]() A blank CD or DVD
A blank CD or DVD
Then do the following:
1. Download a copy of Kali Linux. A good site from which to obtain this is www.kali.org/downloads/.
2. Burn the ISO file to the CD/DVD.
3. Reboot the machine, allowing the LiveCD to start the machine in Linux.
4. Once Kali Linux is running, open a terminal window and type wireshark.
5. With Wireshark open as a sniffing program, record the traffic to and from this computer.
A. Open Capture | Options.
B. Select Start on your Ethernet interface (usually eth0).
C. Stop Capture by selecting Capture | Stop.
D. Click any packet listed to view the analysis.
6. View the other tools on the CD under KDE | Kali.
• Lab Project 8.2
Disable autoplay on your system for several types of media. You will need the following materials:
![]() A computer with Windows
A computer with Windows
![]() A USB flash drive that is set to be bootable
A USB flash drive that is set to be bootable
![]() A CD/DVD with an autoplay file
A CD/DVD with an autoplay file
Then do the following:
1. Insert the CD/DVD and verify that autoplay is on and working.
2. Follow this chapter’s instructions for disabling autoplay.
3. Reinsert the CD/DVD and verify that autoplay is disabled—nothing should appear when the CD/DVD is inserted now.
4. Insert the USB flash drive and see if autoplay works for it; if it does, disable it using the same method.

 Tech Tip
Tech Tip