
Wireless Security and Mobile Devices
App stores and mobile apps are the greatest hostile code and malware delivery mechanism ever created.
—WINN SCHWARTAU

In this chapter, you will learn how to
![]() Describe the different wireless systems in use today
Describe the different wireless systems in use today
![]() Detail WAP and its security implications
Detail WAP and its security implications
![]() Identify 802.11’s security issues and possible solutions
Identify 802.11’s security issues and possible solutions
![]() Learn about the different types of wireless attacks
Learn about the different types of wireless attacks
![]() Examine the elements needed for enterprise wireless deployment
Examine the elements needed for enterprise wireless deployment
![]() Examine the security of mobile systems
Examine the security of mobile systems
Wireless is increasingly the way people access the Internet. Because wireless access is considered a consumer benefit, many businesses have added wireless access points to lure customers into their shops. With the rollout of fourth-generation (4G) high-speed cellular networks, people are also increasingly accessing the Internet from their mobile phones. The massive growth in popularity of nontraditional computers such as netbooks, e-readers, and tablets has also driven the popularity of wireless access.
As wireless use increases, the security of the wireless protocols has become a more important factor in the security of the entire network. As a security professional, you need to understand wireless network applications because of the risks inherent in broadcasting a network signal where anyone can intercept it. Sending unsecured information across public airwaves is tantamount to posting your company’s passwords by the front door of the building. This chapter opens with looks at several current wireless protocols and their security features. The chapter finishes with an examination of mobile systems and their security concerns.
 Introduction to Wireless Networking
Introduction to Wireless Networking
Wireless networking is the transmission of packetized data by means of a physical topology that does not use direct physical links. This definition can be narrowed to apply to networks that use radio waves to carry the signals over either public or private bands, instead of using standard network cabling. Some proprietary applications like long-distance microwave links use point-to-point technology with narrowband radios and highly directional antennas. However, this technology is not common enough to produce any significant research into its vulnerabilities, and anything that was developed would have limited usefulness. So this chapter focuses on point-to-multipoint systems, the two most common of which are the family of cellular protocols and IEEE 802.11.
Wireless Systems
Several different wireless bands are in common use today, the most common of which is the Wi-Fi series, referring to the 802.11 Wireless LAN standards certified by the Wi-Fi Alliance. Another set of bands is WiMAX, which refers to the set of 802.16 wireless network standards ratified by the WiMAX Forum. Lastly, there is ZigBee1, a low-power, personal area networking technology described by the IEEE 802.15.4 series.
Bluetooth is a short-range wireless protocol typically used on small devices such as mobile phones. Early versions of these phones also had Bluetooth on and discoverable by default, making the compromise of a nearby phone easy. Security research has focused on finding problems with these devices simply because they are so common.
The security world ignored wireless for a long time, and then within the space of a few months, it seemed like everyone was attempting to breach the security of wireless networks and transmissions. One reason wireless suddenly found itself to be such a target is that wireless networks are so abundant and so unsecured. The dramatic proliferation of these inexpensive products has made the security ramifications of the protocol astonishing.
No matter what the system, wireless security is a very important topic as more and more applications are designed to use wireless to send data. Wireless is particularly problematic from a security standpoint, because there is no control over the physical layer of the traffic. In most wired LANs, the administrators have physical control over the network and can control to some degree who can actually connect to the physical medium. This prevents large amounts of unauthorized traffic and makes snooping around and listening to the traffic difficult. Wireless does away with the physical limitations. If an attacker can get close enough to the signal’s source as it is being broadcast, they can at the very least listen to the access point and clients talking in order to capture all the packets for examination, as depicted in Figure 12.1.

• Figure 12.1 Wireless transmission extending beyond the facility’s walls
Attackers can also try to modify the traffic being sent or try to send their own traffic to disrupt the system. In this chapter, you will learn about the different types of attacks that wireless networks face.
 Mobile Phones
Mobile Phones
When cellular phones first hit the market, security wasn’t an issue—if you wanted to keep your phone safe, you’d simply keep it physically secure and not loan it to people you didn’t want making calls. Its only function was that of a telephone.
Cellular connections refer to the use of mobile telephony circuits, today typically fourth generation or LTE in nature, although some 3G services still exist. One of the strengths of cellular is the robust nationwide networks that have been deployed, making strong signals available virtually anywhere with reasonable population density. The corresponding weakness is that for some systems in remote areas, this medium is not available.

The advance of digital circuitry has added amazing power in smaller and smaller devices, causing security to be an issue as the software becomes more and more complicated. Today’s small and inexpensive products have made the wireless market grow by leaps and bounds, as traditional wireless devices such as cellular phones and pagers have been replaced by tablets and smartphones.

Today’s smartphones support multiple wireless data-access methods, including 802.11, Bluetooth, and cellular. These mobile phones and tablet devices have caused consumers to demand access to the Internet, anytime and anywhere. This has generated a demand for additional data services. The Wireless Application Protocol (WAP) attempted to satisfy the needs for more data on mobile devices, but it is falling by the wayside as the mobile networks’ capabilities increase. The need for more and more bandwidth has pushed carriers to adopt a more IP-centric routing methodology with technologies such as High Speed Packet Access (HSPA) and Evolution Data Optimized (EVDO). Mobile phones have ruthlessly advanced with new technologies and services, causing phones and the carrier networks that support them to be described in generations—1G, 2G, 3G, and 4G. 1G refers to the original analog cellular standard, Advanced Mobile Phone System (AMPS). 2G refers to the digital network that superseded it. 3G is the system of mobile networks that followed, with many different implementations carrying data at up to 400 Kbps. 4G represents the current state of mobile phones, with LTE being the primary method. 4G allows carriers to offer a wider array of services to the consumer, including broadband data service up to 14.4 Mbps and video calling. 4G is also a move to an entirely IP-based network for all services, running voice over IP (VoIP) on your mobile phone and speeds up to 1 Gbps.
All of these “gee-whiz” features are nice, but how secure are your bits and bytes going to be when they’re traveling across a mobile carrier’s network? All the protocols mentioned have their own security implementations—WAP applies its own Wireless Transport Layer Security (WTLS) to attempt to secure data transmissions, but WAP still has issues such as the “WAP gap” (as discussed next). 3G networks have attempted to push a large amount of security down the stack and rely on the encryption designed into the wireless protocol.
Relationship of WAP and WTLS
Wireless Application Protocol is a lightweight protocol designed for mobile devices. Wireless Transport Layer Security is a lightweight security protocol designed for WAP.
Wireless Application Protocol
WAP was introduced to compensate for the relatively low amount of computing power on handheld devices as well as the generally poor network throughput of cellular networks. It uses the Wireless Transport Layer Security (WTLS) encryption scheme, which encrypts the plaintext data and then sends it over the airwaves as ciphertext. The originator and the recipient both have keys to decrypt the data and reproduce the plaintext. WTLS uses a modified version of the Transport Layer Security (TLS) protocol, which is the replacement for Secure Sockets Layer (SSL). The WTLS protocol supports several popular bulk encryption algorithms, including Data Encryption Standard (DES), Triple DES (3DES), RC5, and International Data Encryption Algorithm (IDEA).
Symmetric Encryption
In Chapter 5 you learned about symmetric encryption, including DES, 3DES, RC5, and IDEA. In the context of wireless communication, what algorithm would protect your data the best? What are some possible problems with these algorithms?
WTLS implements integrity through the use of message authentication codes (MACs). A MAC algorithm generates a one-way hash of the compressed WTLS data. WTLS supports the MD5 and SHA MAC algorithms. The MAC algorithm is also decided during the WTLS handshake. The TLS protocol that WTLS is based on is designed around Internet-based computers—machines that have relatively high processing power, large amounts of memory, and sufficient bandwidth available for Internet applications. Devices that WTLS must accommodate are limited in all these respects. Thus, WTLS has to be able to cope with small amounts of memory and limited processor capacity, as well as long round-trip times that TLS could not handle well. These requirements are the primary reasons that WTLS has security issues.
Because the protocol is designed around more capable servers than devices, the WTLS specification can allow connections with little to no security. Clients with low memory or CPU capabilities cannot support encryption, and choosing null or weak encryption greatly reduces confidentiality. Authentication is also optional in the protocol, and omitting authentication reduces security by leaving the connection vulnerable to a man-in-the-middle–type attack. In addition to the general flaws in the protocol’s implementation, several known security vulnerabilities exist, including those to the chosen-plaintext attack, the PKCS #1 attack, and the alert message truncation attack.
The chosen-plaintext attack works on the principle of a predictable initialization vector (IV). By the nature of the transport medium that it is using, WAP, WTLS needs to support unreliable transport. This forces the IV to be based on data already known to the client, and WTLS uses a linear IV computation. Because the IV is based on the sequence number of the packet, and several packets are sent unencrypted, entropy is severely decreased. This lack of entropy in the encrypted data reduces confidentiality.
Weakness in WAP Aggregation
WAP is a point-to-multipoint protocol, but it can face disruptions or attacks because it aggregates at well-known points: the cellular antenna towers.
Now consider the PKCS #1 attack. Public Key Cryptography Standards (PKCS), used in conjunction with RSA encryption, provide standards for formatting the padding used to generate a correctly formatted block size. When the client receives the block, it will reply to the sender as to the validity of the block. An attacker takes advantage of this by attempting to send multiple guesses at the padding to force a padding error. In vulnerable implementations, when RSA signatures and encryption are performed per PKCS #1, the RSA messages can be decrypted with approximately 220 chosen ciphertext queries. Alert messages in WTLS are sometimes sent in plaintext and are not authenticated. This fact could allow an attacker to overwrite an encrypted packet from the actual sender with a plaintext alert message, leading to possible disruption of the connection through, for instance, a truncation attack.
Some concern over the so-called WAP gap involves confidentiality of information where the two different networks meet, the WAP gateway, as shown in Figure 12.2.

• Figure 12.2 The WAP gap shows an unencrypted space between two enciphered connections.
WTLS acts as the security protocol for the WAP network, and TLS is the standard for the Internet, so the WAP gateway has to perform translation from one encryption standard to the other. This translation forces all messages to be seen by the WAP gateway in plaintext. This is a weak point in the network design, but from an attacker’s perspective, it’s a much more difficult target than the WTLS protocol itself. Threats to the WAP gateway can be minimized through careful infrastructure design, such as selecting a secure physical location and allowing only outbound traffic from the gateway. A risk of compromise still exists, however, and an attacker would find a WAP gateway an especially appealing target, as plaintext messages are processed through it from all wireless devices, not just a single user. The solution for this is to have end-to-end security layered over anything underlying, in effect creating a VPN from the endpoint to the mobile device, or to standardize on a full implementation of TLS for end-to-end encryption and strong authentication. The limited nature of the devices hampers the ability of the security protocols to operate as intended, compromising any real security to be implemented on WAP networks.
3G Mobile Networks
Our cell phones are one of the most visible indicators of advancing technology. Within recent memory, we were forced to switch from old analog phones to digital models. The networks have been upgraded to 3G, greatly enhancing speed and lowering latency. This has reduced the need for lightweight protocols to handle data transmission, and more standard protocols such as IP can be used. The increased power and memory of the handheld devices also reduce the need for lighter-weight encryption protocols. This has caused the protocols used for 3G mobile devices to build in their own encryption protocols. Security will rely on these lower-level protocols or standard application-level security protocols used in normal IP traffic.
3G, 4G, LTE… What’s the Difference?
In today’s mobile marketing campaigns, we hear of 3G, 4G, and LTE. What do these terms mean? 3G is the “old” network today, but it is still very capable for a variety of purposes. 4G phones are supposed to be even faster, but that’s not always the case. A lot depends on what you use the phone for. There are several technologies called “4G,” each with multiple implementations. This makes the term almost meaningless from a technical point of view. The International Telecommunication Union (ITU), a standards body, issued requirements that a network needed to meet to be called “4G,” but those requirements were ignored by carriers. Now the move is to LTE, which stands for Long Term Evolution of the Universal Mobile Telecommunications System (UMTS). UMTS is the group of standards that defines 3G for GSM networks across the world, and now LTE. There are numerous technical implementations of LTE, but one of the key elements is the use of two different types of air interfaces (radio links): one for downlink (from tower to device) and one for uplink (from device to tower). This is one of the reasons LTE is much faster when uploading information from the phone to the Internet. LTE offers high speed (up to 30 Mbps) and low latency. But not all LTE is equal. Recent tests indicate as much as an order of magnitude difference in speeds between carriers.
As LTE expands, newer versions, each with its own set of characteristics picked from the overall “standard,” are deployed by carriers. While the LTE-A standard has been approved, no carriers currently meet the entire standard. Each carrier has picked the elements of the standard they feel meet their needs.
Bottom line: 4G has become a marketing term, and the only guide one has is to use actual survey results in the area of your service to determine the best solution for your use requirements.
Several competing data transmission standards exist for 3G networks, such as HSPA and EVDO. However, all the standards include transport layer encryption protocols to secure the voice traffic traveling across the wireless signal as well as the data sent by the device. The cryptographic standard proposed for 3G is known as KASUMI. This modified version of the MISTY1 algorithm uses 64-bit blocks and 128-bit keys. Multiple attacks have been launched against this cipher. While the attacks tend to be impractical, this shows that application layer security is needed for secure transmission of data on mobile devices. WAP and WTLS can be used over the lower-level protocols, but traditional TLS can also be used.
4G Mobile Networks
Just as the mobile network carriers were finishing the rollout of 3G services, 4G networks appeared on the horizon. The desire for anywhere, anytime Internet connectivity at speeds near that of a wired connection drives deployment of these next-generation services. 4G can support high-quality VoIP connections, video calls, and real-time video streaming. Just as 3G had some intermediaries that were considered 2.9G, LTE and WiMAX networks are sometimes referred to as 3.5G, 3.75G, or 3.9G. The carriers are marketing these new networks as 4G, although they do not adhere to the ITU standards for 4G speeds.
True 4G would require a firm to meet all of the technical standards issued by the ITU, including specifications that apply to the tower side of the system. Some of the 4G requirements are as follows:
![]() Be based on an all-IP packet switched network
Be based on an all-IP packet switched network
![]() Offer high quality of service for next-generation multimedia support
Offer high quality of service for next-generation multimedia support
![]() Smooth handovers across heterogeneous networks
Smooth handovers across heterogeneous networks
![]() Peak data rates of up to approximately 100 Mbps for high mobility (mobile access)
Peak data rates of up to approximately 100 Mbps for high mobility (mobile access)
![]() Peak data rates of up to approximately 1 Gbps for low mobility such as nomadic/local wireless access
Peak data rates of up to approximately 1 Gbps for low mobility such as nomadic/local wireless access
![]() Dynamically share and use the network resources to support more simultaneous users per cell
Dynamically share and use the network resources to support more simultaneous users per cell
![]() Use scalable channel bandwidths of 5–20 MHz, optionally up to 40 MHz
Use scalable channel bandwidths of 5–20 MHz, optionally up to 40 MHz
![]() Peak link spectral efficiency of 15-bps/Hz in the downlink, and 6.75-bps/Hz in the uplink
Peak link spectral efficiency of 15-bps/Hz in the downlink, and 6.75-bps/Hz in the uplink
To achieve these and other technical elements requires specific tower-side equipment as well as handset specifications. Different carriers have chosen different sets of these to include in their offerings, each building on their existing networks and existing technologies.
Most 4G deployments are continuations of technologies already deployed—just newer evolutions of standards. This is how LTE, LTE Advanced, WiMAX, and WiMAX 2 were born. LTE and WiMAX series come from separate roots, and they are not interchangeable. Within the families, interoperability is possible and is dependent on carrier implementation.
SATCOM
SATCOM (Satellite Communications) is the use of terrestrial transmitters and receivers and satellites in orbit to transfer the signals. SATCOM can be one-way, as in satellite radio, but for most communications two-way signals are needed. Satellites are expensive, and for high-density urban areas, both cost and line-of-sight issues make SATCOM a more costly option. But in rural areas or remote areas, or mobile areas such as at sea, SATCOM is one of the only options for communications.
 Bluetooth
Bluetooth
Bluetooth was originally developed by Ericsson and known as multi-communicator link; in 1998, Nokia, IBM, Intel, and Toshiba joined Ericsson and adopted the Bluetooth name. This consortium became known as the Bluetooth Special Interest Group (SIG). The SIG now has more than 24,000 members and drives the development of the technology and controls the specification to ensure interoperability.

Most people are familiar with Bluetooth because it is part of many mobile phones and headsets, such as those shown in Figure 12.3. This short-range, low-power wireless protocol transmits in the 2.4-GHz band, the same band used for 802.11. The concept for the short-range (approx. 32 feet) wireless protocol is to transmit data in personal area networks (PANs).

• Figure 12.3 Headsets and cell phones are two of the most popular types of Bluetooth-capable devices.
Bluetooth transmits and receives data from a variety of devices, the most common being mobile phones, laptops, printers, and audio devices. The mobile phone has driven a lot of Bluetooth growth and has even spread Bluetooth into new cars as a mobile phone hands-free kit.
Bluetooth has gone through a few releases. Version 1.1 was the first commercially successful version, with version 1.2 released in 2007 and correcting some of the problems found in 1.1. Version 1.2 allows speeds up to 721 Kbps and improves resistance to interference. Version 1.2 is backward-compatible with version 1.1. With the rate of advancement and the life of most tech items, Bluetooth 1 series is basically extinct. Bluetooth 2.0 introduced Enhanced Data Rate (EDR), which allows the transmission of up to 3.0 Mbps. Bluetooth 3.0 has the capability to use an 802.11 channel to achieve speeds up to 24 Mbps. The current version is the Bluetooth 4.0 standard with support for three modes: classic, high speed, and low energy.
Bluetooth 4 introduces a new method to support collecting data from devices that generate data at a very low rate. Some devices, such as medical devices, may only collect and transmit data at low rates. This feature, called Low Energy (LE), was designed to aggregate data from various sensors, like heart rate monitors, thermometers, and so forth, and carries the commercial name Bluetooth Smart.
Bluetooth Security
Bluetooth should always have discoverable mode turned off unless you’re deliberately pairing a device.
As Bluetooth became popular, people started trying to find holes in it. Bluetooth features easy configuration of devices to allow communication, with no need for network addresses or ports. Bluetooth uses pairing to establish a trust relationship between devices. To establish that trust, the devices advertise capabilities and require a passkey. To help maintain security, most devices require the passkey to be entered into both devices; this prevents a default passkey–type attack. The Bluetooth’s protocol advertisement of services and pairing properties is where some of the security issues start.
Bluetooth Data Rates
Different versions of Bluetooth have differing maximum data transfer rates, as detailed in the following table:
Bluetooth Version |
Speed |
Bluetooth v1.0 and v1.0B |
768 Kbps |
Bluetooth v1.1 |
768 Kbps |
Bluetooth v1.2 |
1 Mbps |
Bluetooth v2.0 and v2.1 + EDR (Enhanced Data Rate) |
3 Mbps |
Bluetooth v3.0 + HS (High Speed) |
24 Mbps |
Bluetooth Smart (v4.0, 4.1, and 4.2) |
24 Mbps |
Bluetooth Attacks
As a wireless method of communication, Bluetooth is open to connection and attack from outside the intended sender and receiver. Several different attack modes have been discovered that can be used against Bluetooth systems. These are discussed later in the chapter.
Bluetooth technology is likely to grow due to the popularity of mobile phones. Software and protocol updates have helped to improve the security of the protocol. Almost all phones now keep Bluetooth turned off by default, and they allow you to make the phone discoverable for only a limited amount of time. User education about security risks is also a large factor in avoiding security breaches.
 Near Field Communication
Near Field Communication
Near field communication (NFC) is a set of wireless technologies that enables smartphones and other devices to establish radio communication over a short proximity, typically a distance of 10 cm (3.9 in) or less. This technology did not see much use until recently when it started being employed to move data between cell phones and in mobile payment systems. NFC has become a high-use technology in the past few years, as multiple uses exist for the technology, and the latest generation of smartphones includes this technology as a standard function.
 Other Forms of Connection
Other Forms of Connection
Mobile devices have numerous means of connecting to other devices. A few remaining ones are detailed in this section.
ANT
ANT is a multicast wireless sensor network technology that operates in the 2.4-GHz ISM band. ANT is a proprietary method but has open access and a protocol stack to facilitate communication by establishing standard rules for coexistence, data representation, signaling, authentication, and error detection within a personal area network (PAN). ANT is conceptually similar to Bluetooth LE, but is oriented toward usage with sensors, such as heart rate monitors, fitness devices, and personal devices. ANT uses a unique isosynchronous network technology that allows it to manage communications in a crowded 2.4-GHz spectrum and to work well with multiple devices without interference.
Infrared
Infrared (IR) is a band of electromagnetic energy just beyond the red end of the visible color spectrum. IR has been used in remote-control devices for years. IR made its debut in computer networking as a wireless method to connect to printers. Now that wireless keyboards, wireless mice, and mobile devices exchange data via IR, it seems to be everywhere. IR can also be used to connect devices in a network configuration, but it is slow compared to other wireless technologies. IR cannot penetrate walls but instead bounces off them. Nor can it penetrate other solid objects. Therefore, if you stack a few items in front of the transceiver, the signal is lost.
USB
Universal Serial Bus (USB) is still the ubiquitous standard for connecting devices with cables. Mobile phones can transfer data and charge their battery via USB. Laptops, desktops, and even servers have USB ports for a variety of data-connection needs. USB ports have greatly expanded users’ ability to connect devices to their computers. USB ports automatically recognize a device being plugged into the system and usually work without the user needing to add drivers or configure software. This has spawned a legion of USB devices, from music players to peripherals, to storage devices; virtually anything that can consume or deliver data connects via USB.
The most interesting of these, for security purposes, are the USB flash memory–based storage devices. USB drive keys, which are basically flash memory with a USB interface in a device typically about the size of your thumb, provide a way to move files easily from computer to computer. When plugged into a USB port, these devices automount and behave like any other drive attached to the computer. Their small size and relatively large capacity, coupled with instant read-write ability, present security problems. They can easily be used by an individual with malicious intent to conceal the removal of files or data from the building or to bring malicious files into the building and onto the company network.
 IEEE 802.11 Series
IEEE 802.11 Series
IEEE 802.11 is a family of protocols instead of a single specification. Table 12.1 is a summary table of the 802.11 family. The standard launched a range of products (such as wireless routers, an example of which is shown in Figure 12.4) that would open the way to a whole new genre of possibilities for attackers and a new series of headaches for security administrators everywhere. 802.11 was a new standard for sending packetized data traffic over radio waves in the unlicensed 2.4-GHz band.
Table 12.1 The IEEE 802.11 Family


• Figure 12.4 A common wireless router
This group of IEEE standards is also called Wi-Fi, which is a certification owned by an industry group, the Wi-Fi Alliance. A device marked as Wi-Fi Certified adheres to the standards of the alliance. As the products matured and became easy to use and affordable, security experts began to deconstruct the limited security that had been built into the standard.
Direct-sequence spread spectrum (DSSS) is a modulation type that spreads the traffic sent over the entire bandwidth. It does this by injecting a noise-like signal into the information stream and transmitting the normally narrowband information over the wider band available. The primary reason that spread-spectrum technology is used in 802.11 protocols is to avoid interference on the public 2.4-GHz and 5-GHz bands. Orthogonal frequency division multiplexing (OFDM) multiplexes, or separates, the data to be transmitted into smaller chunks and then transmits the chunks on several subchannels. This use of subchannels is what the “frequency division” portion of the name refers to. Both of these techniques, multiplexing and frequency division, are used to avoid interference. Orthogonal refers to the manner in which the subchannels are assigned, principally to avoid crosstalk, or interference with your own channels.
802.11: Individual Standards
The 802.11b protocol provides for multiple-rate Ethernet over 2.4-GHz spread-spectrum wireless. The most common layout is a point-to-multipoint environment, with the available bandwidth being shared by all users. The typical range is roughly 100 yards indoors and 300 yards outdoors, line of sight. 802.11a uses a higher band and has a higher bandwidth. It operates in the 5-GHz spectrum using OFDM. Supporting rates of up to 54 Mbps, it is the faster brother of 802.11b; however, the higher frequency used by 802.11a shortens the usable range of the devices and makes it incompatible with 802.11b. The 802.11g standard uses portions of both of the other standards: it uses the 2.4-GHz band for greater range but uses the OFDM transmission method to achieve the faster 54-Mbps data rates. Because it uses the 2.4-GHz band, this standard interoperates with the older 802.11b standard. This allows older 802.11g access points (AP) to give access to both “g” and “b” clients.

The 2.4-GHz band is commonly used by many household devices that are constantly on, such as cordless phones. It is also the frequency used by microwave ovens to heat food. So if you are having intermittent interference on your Wi-Fi LAN, check to see if the microwave is on.
The 802.11n version improves on the older standards by greatly increasing speed. It has a functional data rate of up to 600 Mbps, gained through the use of wider bands and multiple-input multiple-output (MIMO) processing. MIMO uses multiple antennas and can bond separate channels together to increase data throughput. 802.11ac is the latest in the 5-GHz band, with functional data rates up to a theoretical 6+ Gbps using multiple antennas. The 802.11ac standard was ratified in 2014, and chipsets have been available since late 2011. Designed for multimedia streaming and other high-bandwidth operations, the individual channels are twice the width of 802.11n channels, and as many as eight antennas can be deployed in a Mu-MIMO form.
All these protocols operate in bands that are “unlicensed” by the FCC. This means that people operating this equipment do not have to be certified by the FCC, but it also means that the devices could possibly share the band with other devices, such as cordless phones, closed-circuit TV (CCTV) wireless transceivers, and other similar equipment. This other equipment can cause interference with the 802.11 equipment, possibly causing speed degradation.
The 802.11 protocol designers expected some security concerns and attempted to build provisions into the 802.11 protocol that would ensure adequate security. The 802.11 standard includes attempts at rudimentary authentication and confidentiality controls. Authentication is handled in its most basic form by the 802.11 access point (AP), forcing the clients to perform a handshake when attempting to “associate” to the AP.

SSIDs can be set to anything by the person setting up an access point. So, while “FBI Surveillance Van #14” may seem humorous, what about SSIDs with the name of an airport, Starbucks, or a hotel? Can you trust them? Because anyone can use any name, the answer is no. So, if you need a secure connection, you should use some form of secure channel such as a VPN for communication security. For even more security, you can carry your own access point and create a wireless channel that you control.
Association is the process required before the AP will allow the client to talk across the AP to the network. Association occurs only if the client has all the correct parameters needed in the handshake, among them the service set identifier (SSID). This SSID setting should limit access only to the authorized users of the wireless network. The SSID is a phrase-based mechanism that helps ensure that you are connecting to the correct AP. This SSID phrase is transmitted in all the access point’s beacon frames. The beacon frame is an 802.11 management frame for the network and contains several different fields, such as the time stamp and beacon interval, but most importantly the SSID. This allows attackers to scan for the beacon frame and retrieve the SSID.
Typically, access to actual Ethernet segments is protected by physical security measures. This structure allows security administrators to plan for only internal threats to the network and gives them a clear idea of the types and number of machines connected to it. Wireless networking takes the keys to the kingdom and tosses them out the window and into the parking lot. A typical wireless installation broadcasts the network right through the physical controls that are in place. An attacker can drive up and have the same access as if he plugged into an Ethernet jack inside the building—in fact, better access, because 802.11 is a shared medium, allowing sniffers to view all packets being sent to or from the AP and all clients. These APs are also typically behind any security measures the companies have in place, such as firewalls and intrusion detection systems (IDSs). This kind of access into the internal network has caused a large stir among computer security professionals and eventually the media. War-driving, war-flying, war-walking, war-chalking—all of these terms have been used in security article after security article to describe attacks on wireless networks.
Attacking 802.11
Wireless is a popular target for several reasons: the access gained from wireless, the lack of default security, and the wide proliferation of devices. However, other reasons also make it attackable. The first of these is anonymity: An attacker can probe your building for wireless access from the street. Then they can log packets to and from the AP without giving any indication that an attempted intrusion is taking place. The attacker will announce their presence only if they attempt to associate to the AP. Even then, an attempted association is recorded only by the MAC address of the wireless card associating to it, and most APs do not have alerting functionality to indicate when users associate to it. This fact gives administrators a very limited view of who is gaining access to the network, if they are even paying attention at all. It gives attackers the ability to seek out and compromise wireless networks with relative impunity.

Anonymity also works in another way; once an attacker finds an unsecured AP with wireless access, they can use an essentially untraceable IP address to attempt attacks on other Internet hosts.
The second reason is the low cost of the equipment needed. A single wireless access card costing less than $100 can give access to any unsecured AP within driving range. Finally, attacking a wireless network is relatively easy compared to attacking other target hosts. Windows-based tools for locating and sniffing wireless-based networks have turned anyone who can download files from the Internet and has a wireless card into a potential attacker.
Locating wireless networks was originally termed war-driving, an adaptation of the term war-dialing. War-dialing comes from the 1983 movie WarGames; it is the process of dialing a list of phone numbers looking for modem-connected computers. War-drivers drive around with a wireless locater program recording the number of networks found and their locations. This term has evolved along with war-flying and war-walking, which mean exactly what you expect. War-chalking started with people using chalk on sidewalks to mark some of the wireless networks they found.

Because wireless antennas can transmit outside a facility, the proper tuning and placement of these antennas can be crucial for security. Adjusting radiated power through these power-level controls will assist in keeping wireless signals from being broadcast outside areas under physical access control.
The most common tools for an attacker to use are reception-based programs that listen to the beacon frames output by other wireless devices, and programs that promiscuously capture all traffic. A wide variety of programs can assist in troubleshooting wireless networks, and these all work in the same manner, by listening for the beacon frames of APs that are within range of the network interface card (NIC) attached to the computer. When the program receives the frames, it logs all available information about the AP for later analysis. If the computer has a GPS unit attached to it, the program also logs the AP’s coordinates. This information can be used to return to the AP or to plot maps of APs in a city. One of the more commonly used tools is Wireshark. Other common tools include Aircrack-ng suite, Kismet, NetSurveyor, Vistumbler, and NetSpot. Different tools have different specializations; some are better for troubleshooting some issues such as congestion, while others can map signal strengths and assist in site surveys.
Once an attacker has located a network, and assuming they cannot directly connect and start active scanning and penetration of the network, the attacker will use the best attack tool there is: a network sniffer. The network sniffer, when combined with a wireless network card it can support, is a powerful attack tool because the shared medium of a wireless network exposes all packets to interception and logging. Popular wireless sniffers are Wireshark and Kismet. Regular sniffers used on wired Ethernet have also been updated to include support for wireless. Sniffers are also important because they allow you to retrieve the MAC addresses of the nodes of the network. APs can be configured to allow access only to pre-specified MAC addresses, and an attacker spoofing the MAC can bypass this feature. More details on attacking wireless networks is provided in a separate section, Wireless Attacks, later in the chapter.
After the limited security functions of a wireless network are broken, the network behaves exactly like a regular Ethernet network and is subject to the exact same vulnerabilities. The host machines that are on or attached to the wireless network are as vulnerable as if they and the attacker were physically connected. Being on the network opens up all machines to vulnerability scanners, Trojan horse programs, virus and worm programs, and traffic interception via sniffer programs. Any unpatched vulnerability on any machine accessible from the wireless segment is now open to compromise.
WEP
The designers of the 802.11 protocol also attempted to maintain confidentiality by introducing Wired Equivalent Privacy (WEP), which uses a cipher to encrypt the data as it is transmitted through the air. WEP has been shown to have an implementation problem that can be exploited to break security. WEP encrypts the data traveling across the network with an RC4 stream cipher, attempting to ensure confidentiality. (The details of the RC4 cipher are covered in Chapter 5.) This synchronous method of encryption ensures some method of authentication. The system depends on the client and the AP having a shared secret key, ensuring that only authorized people with the proper key have access to the wireless network. WEP supports two key lengths, 40 and 104 bits, though these are more typically referred to as 64 and 128 bits. In 802.11a and 802.11g, manufacturers extended this to 152-bit WEP keys. This is because in all cases, 24 bits of the overall key length are used for the initialization vector (IV).
WEP Isn’t Equivalent
Wired Equivalent Privacy (WEP) should not be trusted alone to provide confidentiality. If WEP is the only protocol supported by your AP, place your AP outside the corporate firewall and VPN to add more protection.
The biggest weakness of WEP is that the IV problem exists, regardless of key length, because the IV always remains at 24 bits, and IVs can frequently be repeated due to the limited size. Most APs also have the ability to lock in access only to known MAC addresses, providing a limited authentication capability. Given sniffers’ capacity to grab all active MAC addresses on the network, this capability is not very effective. An attacker simply configures their wireless cards to a known-good MAC address.
Current Security Methods
WEP was designed to provide some measure of confidentiality on an 802.11 network similar to what is found on a wired network, but that has not been the case. Accordingly, the Wi-Fi Alliance developed Wi-Fi Protected Access (WPA) to improve upon WEP. The 802.11i standard is the IEEE standard for security in wireless networks, also known as Wi-Fi Protected Access 2 (WPA2). The 802.11i standard specifies the use of the Temporal Key Integrity Protocol (TKIP) and uses AES with the Counter Mode with CBC-MAC Protocol (in full, the Counter Mode with Cipher Block Chaining–Message Authentication Codes Protocol, or simply CCMP). These two protocols have different functions, but they both serve to enhance security.
TKIP is used for backward compatibility with draft 802.11i implementation and WPA standards, and it works by using a shared secret combined with the card’s MAC address to generate a new key, which is mixed with the IV to make per-packet keys that encrypt a single packet using the same RC4 cipher used by traditional WEP. This overcomes the WEP key weakness, as a key is used on only one packet. The other advantage to this method is that it can be retrofitted to current hardware with only a software change, unlike AES and 802.1X. CCMP is actually the mode in which the AES cipher is used to provide message integrity. Unlike TKIP, CCMP requires new hardware to perform the AES encryption. The advances of 802.11i have corrected the weaknesses of WEP.
WPA
The first standard to be used in the market to replace WEP was Wi-Fi Protected Access (WPA). This standard uses the flawed WEP algorithm with the Temporal Key Integrity Protocol (TKIP). WPA also introduced a message integrity check (MIC) that is known by the name Michael.
Whereas WEP uses a 40-bit or 104-bit encryption key that must be manually entered on wireless access points and devices and does not change, TKIP employs a per-packet key, generating a new 128-bit key for each packet. This can generally be accomplished with only a firmware update, enabling a simple solution to the types of attacks that compromise WEP.
WPA also suffers from a lack of forward secrecy protection. If the WPA key is known, as in a public Wi-Fi password, then an attacker can collect all the packets from all of the connections and decrypt those packets later. This is why, when using public Wi-Fi, one should always use a secondary means of protection—either a VPN or a TLS-based solution to protect their content.
TKIP
Temporal Key Integrity Protocol (TKIP) was created as a stopgap security measure to replace the WEP protocol without requiring the replacement of legacy hardware. The breaking of WEP had left Wi-Fi networks without viable link-layer security, and a solution was required for already deployed hardware. TKIP works by mixing a secret root key with the IV before the RC4 encryption. WPA/TKIP uses the same underlying mechanism as WEP, and consequently is vulnerable to a number of similar attacks. TKIP is no longer considered secure and has been deprecated with the release of WPA2.

TKIP is an integrity check; AES is an encryption algorithm.
WPA2
IEEE 802.11i is the standard for security in wireless networks and is also known as Wi-Fi Protected Access 2 (WPA2). WPA2 Enterprise mode uses 802.1x to provide authentication and uses the Advanced Encryption Standard (AES) as the encryption protocol. WPA2 uses the AES block cipher, a significant improvement over WEP and WPA’s use of the RC4 stream cipher. The 802.11i standard specifies the use of the Counter Mode with CBC-MAC Protocol (in full, the Counter Mode with Cipher Block Chaining–Message Authentication Codes Protocol, or simply CCMP).
WPS
Wi-Fi Protected Setup (WPS) is a network security standard that was created to provide users with an easy method of configuring wireless networks. Designed for home networks and small business networks, this standard involves the use of an eight-digit PIN to configure wireless devices. WPS consists of a series of Extensible Authentication Protocol (EAP) messages and has been shown to be susceptible to a brute-force attack. A successful attack can reveal the PIN and subsequently the WPA/WPA2 passphrase and allow unauthorized parties to gain access to the network. Currently, the only effective mitigation is to disable WPS.
Setting Up WPA2
If WPS is not safe for use, how does one set up WPA2? To set up WPA2, you need to have several parameters. Figure 12.5 shows the screens for a WPA2 setup in Windows.
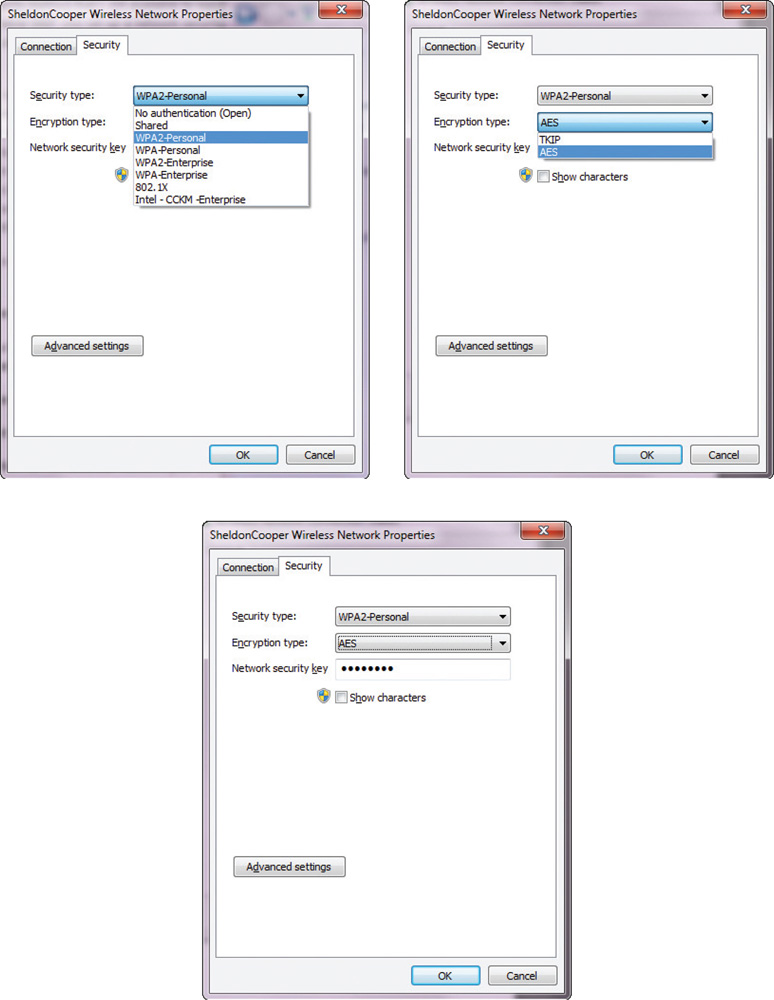
• Figure 12.5 WPA2 setup options in Windows
The first element is to choose a security framework. When configuring an adapter to connect to an existing network, you need to match the choice of the network. When setting up your own network, you can choose whichever option you prefer. There are many selections, but for security purposes, you should choose WPA2-Personal or WPA2-Enterprise. Both of these require the choice of an encryption type, either TKIP or AES. TKIP has been deprecated, so choose AES. The last element is the choice of the network security key—the secret that is shared by all users. WPA2-Enterprise, which is designed to be used with an 802.1x authentication server that distributes different keys to each user, is typically used in business environments.
PSK vs. Enterprise vs. Open System
When building out a wireless network, you must decide how you are going to employ security on the network. Specifically, the questions need to be addressed with respect to who will be allowed to connect, and what level of protection will be provided in the transmission of data between mobile devices and the access point.
Both WPA and WPA2, discussed in detail earlier in the chapter, have two methods to establish a connection: PSK and Enterprise. PSK stands for pre-shared key, which is exactly what it sounds like—a secret that has to be shared between users. A PSK is typically entered as a passphrase of up to 63 characters. This key must be securely shared between users, as it is the basis of the security provided by the protocol. The PSK is converted to a 256-bit key that is then used to secure all communications between the device and access point. PSK has one particular vulnerability: simple and short PSKs are at risk of brute-force attempts. Keeping them at least 20 random characters long should mitigate this attack vector.
Table 12.2 illustrates the differences between WAP and WPA2. In Enterprise mode, the devices use IEEE 802.1X and a RADIUS authentication server to enable a connection. This method allows the use of usernames and passwords and provides enterprise-class options such as NAC integration, multiple random keys, and the same PSK for everyone.
Table 12.2 WPA and WPA2 compared

In WEP-based systems, there are two options: Open System authentication and shared key authentication. Open System authentication is not truly authentication—it is merely a sharing of a secret key based on the SSID. The process is simple: First, the mobile client matches the SSID with the access point and requests a key (called authentication) to the access point. Then the access point generates an authentication code (the key, as there is no specific authentication of the client), which is a random number intended for use only during that session. The mobile client uses the authentication code and joins the network. The session continues until disassociation either by request or loss of signal.

Understand the differences between PSK, Enterprise, and Open System authentication. The question’s scenario will provide you with facts that make one of these options the best selection.
Authentication Protocols
Wireless networks have a need for secure authentication protocols. The following authentication protocols should be understood for the Security+ exam: EAP, PEAP, EAP-FAST, EAP-TLS, EAP-TTLS, IEEE 802.1x, and RADIUS from the RADIUS Federation.
EAP
Extensible Authentication Protocol (EAP) is defined in RFC 2284 (obsoleted by 3748). EAP-TLS relies on Transport Layer Security (TLS), an attempt to standardize the SSL structure to pass credentials. EAP-TTLS (the acronym stands for EAP–Tunneled TLS protocol) is a variant of the EAP-TLS protocol. EAP-TTLS works much the same way as EAP-TLS, with the server authenticating to the client with a certificate, but the protocol tunnels the client side of the authentication, allowing the use of legacy authentication protocols such as Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), MS-CHAP, or MS-CHAP v2.
LEAP
Cisco designed a proprietary version of EAP known as Lightweight Extensible Authentication Protocol (LEAP); however, this is being phased out for newer protocols such as PEAP and EAP-TLS. Because it is susceptible to offline password guessing, and because tools are available that actively break LEAP security, this protocol has been deprecated in favor of stronger methods of EAP.
PEAP
PEAP, or Protected EAP, was developed to protect the EAP communication by encapsulating it with TLS. This is an open standard developed jointly by Cisco, Microsoft, and RSA. EAP was designed assuming a secure communication channel. PEAP provides that protection as part of the protocol via a TLS tunnel. PEAP is widely supported by vendors for use over wireless networks.
EAP-FAST
The Wi-Fi Alliance added EAP-FAST to its list of supported protocols for WPA/WPA2 in 2010. EAP-FAST is EAP–Flexible Authentication via Secure Tunneling, which is described in RFC-4851 and proposed by Cisco to be a replacement for LEAP, a previous Cisco version of EAP. It offers a lightweight, tunneling protocol to enable authentication. The distinguishing characteristic is the passing of a Protected Access Credential (PAC) that’s used to establish a TLS tunnel through which client credentials are verified.
EAP-TLS
The Wi-Fi Alliance also added EAP-TLS to its list of supported protocols for WPA/WPA2 in 2010. EAP-TLS is an IETF open standard (RFC 5216) that uses the Transport Layer Security (TLS) protocol to secure the authentication process. This is still considered one of the most secure implementations, primarily because common implementations employ client-side certificates. This means that an attacker must also possess the key for the client-side certificate to break the TLS channel.
EAP-TTLS
The Wi-Fi Alliance also added EAP-TTLS to its list of supported protocols for WPA/WPA2 in 2010. EAP-TTLS is an extension of TLS called Tunneled TLS. In EAP-TTLS, the authentication process is protected by the tunnel from man-in-the-middle attacks, and although client certificates can be used, they are not required, making this easier to set up than EAP-TLS for clients without certificates.

You need to know two key elements concerning EAP. First, it is only a framework to secure the authentication process, not an actual encryption method. Second, many variants exist, and understanding the differences between EAP, EAP-FAST, EAP-TLS, and EAP-TTLS, and how to recognize them in practice, is important for the exam.
Implementing 802.1X
The IEEE 802.1X protocol can support a wide variety of authentication methods and also fits well into existing authentication systems such as RADIUS and LDAP. This allows 802.1X to interoperate well with other systems such as VPNs and dial-up RAS. Unlike other authentication methods, such as the Point-to-Point Protocol over Ethernet (PPPoE), 802.1X does not use encapsulation, so the network overhead is much lower. Unfortunately, the protocol is just a framework for providing implementation, so no specifics guarantee strong authentication or key management. Implementations of the protocol vary from vendor to vendor in method of implementation and strength of security, especially when it comes to the difficult test of wireless security.
Three common methods are used to implement 802.1X: EAP-TLS, EAP-TTLS, and EAP-MD5. EAP-TLS relies on TLS, an attempt to standardize the SSL structure to pass credentials. The standard, developed by Microsoft, uses X.509 certificates and offers dynamic WEP key generation. This means that the organization must have the ability to support the public key infrastructure (PKI) in the form of X.509 digital certificates. Also, per-user, per-session dynamically generated WEP keys help prevent anyone from cracking the WEP keys in use, as each user individually has their own WEP key. Even if a user were logged onto the AP and transmitted enough traffic to allow cracking of the WEP key, access would be gained only to that user’s traffic. No other user’s data would be compromised, and the attacker could not use the WEP key to connect to the AP. This standard authenticates the client to the AP, but it also authenticates the AP to the client, helping to avoid man-in-the-middle attacks. The main problem with the EAP-TLS protocol is that it is designed to work only with Microsoft’s Active Directory and Certificate Services; it will not take certificates from other certificate issuers. Thus, a mixed environment would have implementation problems.
As discussed earlier, EAP-TTLS works much the same way as EAP-TLS, with the server authenticating to the client with a certificate, but the protocol tunnels the client side of the authentication, allowing the use of legacy authentication protocols such as Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), MS-CHAP, or MS-CHAP v2. This makes the protocol more versatile while still supporting the enhanced security features, such as dynamic WEP key assignment.
RADIUS Federation
Using a series of RADIUS servers in a federated connection has been employed in several worldwide RADIUS Federation networks. One example is the EDUROAM project that connects users of education institutions worldwide. The process is relatively simple in concept, although the technical details to maintain the hierarchy of RADIUS servers and routing tables is daunting at worldwide scale. A user packages their credentials at a local access point using a certificate-based tunneling protocol method. The first RADIUS server determines which RADIUS server to send the request to, and from there the user is authenticated via their home RADIUS server and the results passed back, permitting a joining to the network.
Because the credentials must pass multiple different networks, the EAP methods are limited to those with certificates and credentials to prevent loss of credentials during transit. This type of federated identity at global scale demonstrates the power of RADIUS and EAP methods.
CCMP
As previously mentioned in the discussion of WPA2, CCMP stands for Counter Mode with Cipher Block Chaining–Message Authentication Codes Protocol (or Counter Mode with CBC-MAC Protocol). CCMP is a data encapsulation encryption mechanism designed for wireless use. CCMP is actually the mode in which the AES cipher is used to provide message integrity. Unlike WPA, CCMP requires new hardware to perform the AES encryption.
 Wireless Systems Configuration
Wireless Systems Configuration
Wireless systems are more than just protocols. Putting up a functional wireless system in a house is as easy as plugging in a wireless access point and connecting. But in an enterprise, where multiple access points will be needed, the configuration takes significantly more work. Site surveys are needed to determine proper access point and antenna placement, as well as channels and power levels.
Access Point
Wi-Fi access points are the point of entry for radio-based network signals into and out of a network. As wireless has become more capable in all aspects of networking, wireless-based networks are replacing cabled or wired solutions. In this scenario, one could consider the access point to be one half of a NIC, with the other half being the wireless card in a host.
Wireless access points can operate in several different modes, depending upon the unit capability and the need of the network. The most common mode, and the one all access points support is Normal mode. This is where the access point provides a point of connection from the wireless network to the wired network. A separate mode, bridged mode, allows an access point to communicate directly with another access point. This allows the extension of a wireless LAN over greater distance. A repeater mode is similar in that it extends the range by working between access points. A bridge mode device allows connections, while a repeater merely acts to extend range.
Fat vs. Thin
Fat (or thick) access points refer to standalone access points, whereas thin access points refer to controller-based access points. Each of these solutions differ in their handling of common functions such as configuration, encryption, updates, and policy settings. Determining which is more effective requires a closer examination of the differences, as presented in the next section, compared to a site’s needs and budget.
Controller Based vs. Standalone
Small standalone Wi-Fi access points can have substantial capabilities with respect to authentication, encryption, and even to a degree channel management. As the wireless deployment grows in size and complexity, there are some advantages to a controller-based access point solution. Controller-based solutions allow for centralized management and control, which can facilitate better channel management for adjacent access points, better load balancing, and easier deployment of patches and firmware updates. From a security standpoint, controller-based solutions offer large advantages in overall network monitoring and security controls. In large-scale environments, controller-based access points can enable network access control based on user identity, thus managing large sets of users in subgroups. Internet access can be blocked for some users (clerks), while internal access can be blocked for others (guests).
SSID
The 802.11 protocol designers expected some security concerns and attempted to build provisions into the 802.11 protocol that would ensure adequate security. The 802.11 standard includes attempts at rudimentary authentication and confidentiality controls. Authentication is handled in its most basic form by the 802.11 access point (AP), forcing clients to perform a handshake when attempting to “associate” to the AP. Association is the process required before the AP will allow the client to talk across the AP to the network.
The authentication function is known as the service set identifier (SSID). This unique 32-character identifier is attached to the header of the packet. Association occurs only if the client has all the correct parameters needed in the handshake, among them the SSID. This SSID setting should limit access to only authorized users of the wireless network. The SSID is broadcast by default as a network name, but broadcasting this beacon frame can be disabled. Many APs also use a default SSID; for example, for many versions of Cisco APs, this default is tsunami, which can indicate an AP that has not been configured for any security. Renaming the SSID and disabling SSID broadcast are both good ideas; however, because the SSID is part of every frame, these measures should not be considered “securing the network.” As the SSID is, hopefully, a unique identifier, only people who know the identifier will be able to complete association to the AP.
While the SSID is a good idea in theory, it is sent in plaintext in the packets, so in practice SSID offers little security significance—any sniffer can determine the SSID, and many operating systems (Windows XP and later, for instance) will display a list of SSIDs active in the area and prompt the user to choose one to connect to. This weakness is magnified by most APs’ default setting is to transmit beacon frames. The beacon frame’s purpose is to announce the wireless network’s presence and capabilities so that WLAN cards can attempt to associate to it. This can be disabled in software for many APs, especially the more sophisticated ones. From a security perspective, the beacon frame is damaging because it contains the SSID, and this beacon frame is transmitted at a set interval (ten times per second by default). Because a default AP without any other traffic is sending out its SSID in plaintext ten times a second, you can see why the SSID does not provide true authentication. Wireless scanning programs work by capturing the beacon frames, and thereby the SSIDs, of all APs.

Although not considered the strongest security measures, renaming the SSID and disabling SSID broadcast are important concepts to know for the exam.
Signal Strength
The usability of a wireless signal is directly related to its signal strength. Too weak of a signal, and the connection can drop out or lose data. Signal strength can be influenced by a couple of factors: the transmitting power level and the environment across which the signal is transmitted. In buildings with significant metal in the walls and roofs, additional power may be needed to have sufficient signal strength at the receivers. Wi-Fi power levels can be controlled by the hardware for a variety of reasons. The lower the power used, the less the opportunity for interference. But if the power levels are too low, then signal strength limits range. Access points can have the power level set either manually or via programmatic control. For most users, power level controls are not very useful, and leaving the unit in default mode is the best option. In complex enterprise setups, with site surveys and planned overlapping zones, this aspect of signal control can be used to increase capacity and control on the network.
Band Selection/Width
Today’s wireless environments employ multiple different bands, each with different bandwidths. Band selection may seem trivial, but with 802.11a, b/g, n, and ac radios, the deployment of access points should support the desired bands based on client needs. Multi-band radio access points exist and are commonly employed to resolve these issues. Wi-Fi operates over two different frequencies: 2.4 GHz for b/g and n, and 5 GHz for a, n, and ac.
Antenna Types and Placement
The standard access point is equipped with an omnidirectional antenna. Omnidirectional antennas operate in all directions, making the relative orientation between devices less important. Omnidirectional antennas cover the greatest area per antenna. The weakness occurs in corners and hard-to-reach areas, as well as boundaries of a facility where directional antennas are needed to complete coverage. Figure 12.6 shows a sampling of common Wi-Fi antennas: (a) is a common home wireless router, (b) is a commercial indoor wireless access point, and (c) is an outdoor directional antenna. These can be visible, as shown, or hidden above ceiling tiles.

Because wireless antennas can transmit outside a facility, tuning and placement of antennas can be crucial for security. Adjusting radiated power through the power level controls will assist in keeping wireless signals from being broadcast outside areas under physical access control.

• Figure 12.6 Wireless access point antennas
Wireless networking problems caused by weak signal strength can sometimes be solved by installing upgraded Wi-Fi radio antennas on the access points. On business networks, the complexity of multiple access points typically requires a comprehensive site survey to map the Wi-Fi signal strength in and around office buildings. Additional wireless access points can then be strategically placed where needed to resolve dead spots in coverage. For small businesses and homes, where a single access point may be all that is needed, an antenna upgrade may be a simpler and more cost-effective option to fix Wi-Fi signal problems.
Two common forms of upgraded antennas are the Yagi antenna and the panel antenna. An example of a Yagi antenna is shown in Figure 12.6(c). Both Yagi and panel antennas are directional in nature, spreading the RF energy in a more limited field, increasing effective range in one direction while limiting it in others. Panel antennas can provide solid room performance while preventing signal bleed behind the antennas. This works well on the edge of a site, limiting the stray emissions that could be captured offsite. Yagi antennas act more like a rifle, funneling the energy along a beam. This allows much longer communication distances using standard power. This also enables eavesdroppers to capture signals from much greater distances because of the gain provided by the antenna itself.
MIMO
MIMO is a set of multiple-input and multiple-output antenna technologies where the available antennas are spread over a multitude of independent access points, each having one or multiple antennas. This can enhance the usable bandwidth and data transmission capacity between the access point and user. There are a wide variety of MIMO methods, and this technology, once considered cutting edge or advanced, is becoming mainstream.
Power Level Controls
Wi-Fi power levels can be controlled by the hardware for a variety of reasons. The lower the power used, the less the opportunity for interference. But if the power levels are too low, then signal strength limits range. Access points can have the power level set either manually or via programmatic control. For most users, power level controls are not very useful, and leaving the unit in default mode is the best option. In complex enterprise setups, with site surveys and planned overlapping zones, this aspect of signal control can be used to increase capacity and control on the network.
Site Surveys
When developing a coverage map for a complex building site, you need to take into account a wide variety of factors, particularly walls, interfering sources, and floor plans. A site survey involves several steps: mapping the floor plan, testing for RF interference, testing for RF coverage, and analysis of material via software. The software can suggest placement of access points. After deploying the APs, you survey the site again, mapping the results versus the predicted, watching signal strength and signal-to-noise ratios. Figure 12.7 illustrates what a site survey looks like. The different shades indicate signal strength, showing where reception is strong and where it is weak. Site surveys can be used to ensure availability of wireless, especially when it’s critical for users to have connections.

Wireless networks are dependent on radio signals to function. It is important to understand that antenna type, placement, and site surveys are used to ensure proper coverage of a site, including areas blocked by walls, interfering signals, and echoes.
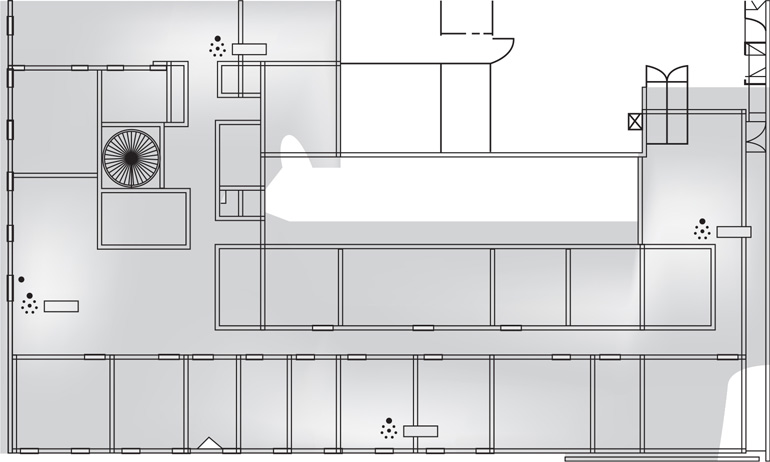
• Figure 12.7 Example site survey
MAC Filtering
MAC filtering is the selective admission of packets based on a list of approved Media Access Control (MAC) addresses. Employed on switches, this method is used to provide a means of machine authentication. In wired networks, this enjoys the protection afforded by the wires, making interception of signals to determine their MAC addresses difficult. In wireless networks, this same mechanism suffers from the fact that an attacker can see the MAC addresses of all traffic to and from the access point, and then can spoof the MAC addresses that are permitted to communicate via the access point.

MAC filtering can be employed on wireless access points, but it can be bypassed by attackers observing allowed MAC addresses and spoofing the allowed MAC address for the wireless card.
Captive Portals
Captive portal refers to a specific technique of using an HTTP client to handle authentication on a wireless network. Frequently employed in public hotspots, a captive portal opens a web browser to an authentication page. This occurs before the user is granted admission to the network. The access point uses this simple mechanism by intercepting all packets and returning the web page for login. The actual web server that serves up the authentication page can be in a walled-off section of the network, blocking access to the Internet until the user successfully authenticates.
Securing Public Wi-Fi
Public Wi-Fi is a common perk that some firms provide for their customers and visitors. When providing a Wi-Fi hotspot, even free open-to-the-public Wi-Fi, the firm should make security a concern. One of the issues associated with wireless transmissions is that they are subject to interception by anyone within range of the hotspot. This makes it possible for others to intercept and read the traffic of anyone using the hotspot, unless encryption is used. For this reason, it has become common practice to use wireless security, even when the intent is to open the channel for everyone. Having a default password, even one that everyone knows, will make it so that people cannot observe other traffic.
There is an entire open wireless movement designed around a sharing concept that promotes sharing of the Internet to all. For information, check out https://openwireless.org.
 Wireless Attacks
Wireless Attacks
Wireless is a common networking technology that has a substantial number of standards and processes to connect users to networks via a radio signal, freeing machines from wires. As in all software systems, wireless networking is a target for hackers. This is partly because of the simple fact that wireless removes the physical barrier.
Replay
A replay attack occurs when the attacker captures a portion of a communication between two parties and retransmits it at a later time. For example, an attacker might replay a series of commands and codes used in a financial transaction to cause the transaction to be conducted multiple times. Generally, replay attacks are associated with attempts to circumvent authentication mechanisms, such as the capturing and reuse of a certificate or ticket.
The best way to prevent replay attacks is with encryption, cryptographic authentication, and time stamps. If a portion of the certificate or ticket includes a date/time stamp or an expiration date/time, and this portion is also encrypted as part of the ticket or certificate, replaying it at a later time will prove useless because it will be rejected as having expired.

The best method for defending against replay attacks is through the use of encryption and short time frames for legal transactions. Encryption can protect the contents from being understood, and a short time frame for a transaction prevents subsequent use.
IV
The initialization vector (IV) is used in wireless systems as the randomization element at the beginning of a connection. Attacks against the IV aim to determine it, thus finding the repeating key sequence. This was the weakness that led to the fall of WEP, and WPA. It is not that the IV is bad; its length was short enough that it could be cycled through all the values, forcing a repeat.
The IV is the primary reason for the weaknesses in WEP. The IV is sent in the plaintext part of the message, and because the total keyspace is approximately 16 million keys, the same key will be reused. Once the key has been repeated, an attacker has two ciphertexts encrypted with the same key stream. This allows the attacker to examine the ciphertext and retrieve the key. This attack can be improved by examining only packets that have weak IVs, reducing the number of packets needed to crack the key. Using only weak IV packets, the number of required captured packets is reduced to around four or five million, which can take only a few hours to capture on a fairly busy AP. For a point of reference, this means that equipment with an advertised WEP key of 128 bits can be cracked in less than a day, whereas to crack a normal 128-bit key would take roughly 2,000,000,000,000,000,000 years on a computer able to attempt one trillion keys a second. AirSnort is a modified sniffing program that takes advantage of this weakness to retrieve the WEP keys. The biggest weakness of WEP is that the IV problem exists regardless of key length, because the IV always remains at 24 bits.
Evil Twin
The evil twin attack is in essence an attack against the wireless protocol via substitute hardware. This attack uses an access point owned by an attacker that usually has been enhanced with higher-power and higher-gain antennas to look like a better connection to the users and computers attaching to it. By getting users to connect through the evil access point, attackers can more easily analyze traffic and perform man-in-the-middle types of attacks. For simple denial of service (DoS), an attacker could use interference to jam the wireless signal, not allowing any computer to connect to the access point successfully.
Rogue AP
By setting up a rogue access point (AP), or rogue AP, an attacker can attempt to get clients to connect to it as if it were authorized and then simply authenticate to the real AP—a simple way to have access to the network and the client’s credentials. Rogue APs can act as a man in the middle and easily steal the user’s credentials. Enterprises with wireless APs should routinely scan for and remove rogue APs, because users have difficulty avoiding them.
Jamming
Jamming is a form of denial of service, specifically against the radio spectrum aspect of wireless. Just as other DoS attacks can manipulate things behind the scenes, so can jamming on a wireless AP, enabling things such as attachment to a rogue AP.
Bluejacking
Bluejacking is the term used for the sending of unauthorized messages to another Bluetooth device. This involves sending a message as a phonebook contact, as shown to the left.

Then the attacker sends the message to the possible recipient via Bluetooth. Originally, this involved sending text messages, but more recent phones can send images or audio as well. A popular variant of this is the transmission of “shock” images, featuring disturbing or crude photos. Because Bluetooth is a short-range protocol, the attack and victim must be within roughly 10 yards of each other. The victim’s phone must also have Bluetooth enabled and must be in discoverable mode. On some early phones, this was the default configuration, and while it makes connecting external devices easier, it also allows attacks against the phone. If Bluetooth is turned off, or if the device is set to nondiscoverable, bluejacking can be avoided.
Bluesnarfing
Bluesnarfing is similar to bluejacking in that it uses the same contact transmission protocol. The difference is that instead of sending an unsolicited message to the victim’s phone, the attacker copies off the victim’s information, which can include e-mails, contact lists, calendar, and anything else that exists on that device. More recent phones with media capabilities can be snarfed for private photos and videos. Bluesnarfing used to require a laptop with a Bluetooth adapter, making it relatively easy to identify a possible attacker, but bluesnarfing applications are now available for mobile devices. Bloover, a combination of Bluetooth and Hoover, is one such application that runs as a Java applet. The majority of Bluetooth phones need to be discoverable for the bluesnarf attack to work, but it does not necessarily need to be paired. In theory, an attacker can also brute-force the device’s unique 48-bit name. A program called RedFang attempts to perform this brute-force attack by sending all possible names and seeing what gets a response. This approach was addressed in Bluetooth 1.2 with an anonymity mode.

The Security+ objective is to compare and contrast attacks, and in the case of bluejacking and bluesnarfing, these are both attacks against Bluetooth. They differ in that bluejacking is the sending of unauthorized data via Bluetooth, whereas bluesnarfing is the unauthorized taking of data over a Bluetooth channel. Understanding this difference is important.
Bluebugging
Bluebugging is a far more serious attack than either bluejacking or bluesnarfing. In bluebugging, the attacker uses Bluetooth to establish a serial connection to the device. This allows access to the full AT command set—GSM phones use AT commands similar to Hayes-compatible modems.
This connection allows full control over the phone, including the placing of calls to any number without the phone owner’s knowledge. Fortunately, this attack requires pairing of the devices to complete, and phones initially vulnerable to the attack have updated firmware to correct the problem. To accomplish the attack now, the phone owner would need to surrender their phone and allow an attacker to physically establish the connection.
Bluetooth DoS is the use of Bluetooth technology to perform a denial-of-service attack against another device. In this attack, an attacker repeatedly requests pairing with the victim device. This type of attack does not divulge information or permit access, but is a nuisance. And, more importantly, if done repeatedly it can drain a device’s battery, or prevent other operations from occurring on the victim’s device. As with all Bluetooth attacks, because of the short range involved, all one has to do is leave the area and the attack will cease.
RFID
Radio Frequency Identification (RFID) tags are used in a wide range of use cases. From tracking devices to tracking keys, the unique serialization of these remotely sensible devices has made them useful in a wide range of applications. RFID tags come in several different forms and can be classified as either active or passive. Active tags have a power source, whereas passive tags utilize the RF energy transmitted to them for power. RFID tags are used as a means of identification and have the advantage over bar codes that they do not have to be visible, just within radio wave range—typically centimeters to 200 meters, depending on tag type. RFID tags are used in a range of security situations, including contactless identification systems such as smart cards.
RFID tags have multiple security concerns; first and foremost, because they are connected via RF energy, physical security is a challenge. Security was recognized as an important issue for RFID tag systems because they form a means of identification and there is a need for authentication and confidentiality of the data transfers. Several standards are associated with securing the RFID data flow, including ISO/IEC 18000 and ISO/IEC 29167 for cryptography methods to support confidentiality, untraceability, tag and reader authentication, and over-the-air privacy, whereas ISO/IEC 20248 specifies a digital signature data structure for use in RFID systems.
Several different attack types can be performed against RFID systems. The first is against the RFID devices themselves—the chips and readers. A second form of attack goes against the communication channel between the device and the reader. The third category of attack is against the reader and back-end system. This last type is more of a standard IT/IS attack, depending on the interfaces used (web, database, and so on) and therefore is not covered any further. Attacks against the communication channel are relatively easy because the radio frequencies are known and devices exist to interface with tags. Two main attacks are replay and eavesdropping. In a replay attack, the RFID information is recorded and then replayed later; in the case of an RFID-based access badge, it could be read in a restaurant from a distance and then replayed at the appropriate entry point to gain entry. In the case of eavesdropping, the data can be collected, monitoring the movement of tags for whatever purpose needed by an unauthorized party. Both of these attacks are easily defeated using the aforementioned security standards.
If eavesdropping is possible, then what about man-in-the-middle attacks? These are certainly possible because they would be a combination of a sniffing (eavesdropping) action, followed by replay (spoofing) attack. This leads to the question as to whether an RFID can be cloned. And again, the answer is yes, if the RFID information is not protected via a cryptographic component.
Disassociation
Disassociation attacks against a wireless system are those attacks designed to disassociate a host from the wireless access point, and from the wireless network. Disassociation attacks stem from the deauthentication frame that is in the IEEE 802.11 (Wi-Fi) standard. The deauthentication frame is designed as a tool to remove unauthorized stations from a Wi-Fi access point, but because of the design of the protocol, they can be implemented by virtually anyone. An attacker only needs to have the MAC address of the intended victim, and then they can send a spoofed message to the access point, specifically spoofing the MAC address of the victim machine. This results in the disconnection of the victim machine, making this attack a form of denial of service.
Disassociation attacks are not typically used alone, but rather in concert with another attack objective. For instance, if you disassociate a connection and then sniff the reconnect, you can steal passwords. After disassociating a machine, the user attempting to reestablish a WPA or WPA2 session will need to repeat the WPA 4-way handshake. This gives the hacker a chance to sniff this event, the first step in gathering needed information for a brute-force or dictionary-based WPA password-cracking attack. Forcing users to reconnect gives the attacker a chance to mount a man-in-the-middle attack against content provided during a connection. This has been used by the Wifiphisher tool to collect passwords.
 Mobile Device Management Concepts
Mobile Device Management Concepts
The concepts of mobile device management (MDM) are essential knowledge in today’s environment of connected devices. MDM began as a marketing term for a collective set of commonly employed protection elements associated with mobile devices. When viewed as a comprehensive set of security options for mobile devices, an MDM policy should be created and enforced by every corporation. The policy should require the following:
![]() Device locking with a strong password
Device locking with a strong password
![]() Encryption of data on the device
Encryption of data on the device
![]() Device locking automatically after a certain period of inactivity
Device locking automatically after a certain period of inactivity
![]() The capability to remotely lock the device if it is lost or stolen
The capability to remotely lock the device if it is lost or stolen
![]() The capability to wipe the device automatically after a certain number of failed login attempts
The capability to wipe the device automatically after a certain number of failed login attempts
![]() The capability to remotely wipe the device if it is lost or stolen
The capability to remotely wipe the device if it is lost or stolen
Password policies should extend to mobile devices, including lockout and, if possible, the automatic wiping of data. Corporate policy for data encryption on mobile devices should be consistent with the policy for data encryption on laptop computers. In other words, if you don’t require encryption of portable computers, then should you require it for mobile devices? There is not a uniform answer to this question. Mobile devices are much more mobile in practice than laptops, and more prone to loss. This is ultimately a risk question that management must address: what is the risk and what are the costs of the options employed? This also raises bigger question: Which devices should have encryption as a basic security protection mechanism? Is it by device type or by user based on what data would be exposed to risk? Fortunately, MDM solutions exist that make the choices manageable.

Mobile device management (MDM) is a marketing term for a collective set of commonly employed protection elements associated with mobile devices.
Application Management
Most mobile device vendors provide some kind of application store for finding and purchasing applications for their mobile devices. The vendors do a reasonable job of making sure that offered applications are approved and don’t create an overt security risk. Yet many applications request access to various information stores on the mobile device as part of their business model. Understanding what access is requested and approved upon installation of an app is an important security precaution. These are all potential problems for mobile users concerned over data security and drive the need for a mobile application management solution. Your company may have to restrict the types of applications that can be downloaded and used on mobile devices. If you need very strong protection, your company can be very proactive and provide an enterprise application store where only company-approved applications are available, with a corresponding policy that apps cannot be obtained from any other source. Another method involves the use of an MDM solution, as discussed in the previous section.
Full Device Encryption (FDE)
Just as laptop computers should employ whole disk encryption to protect the laptop in case of loss or theft, you may need to consider encryption for mobile devices used by your company’s employees. Mobile devices are much more likely to be lost or stolen, so you should consider encrypting data on your devices. More and more, mobile devices are used for accessing and storing business-critical data or other sensitive information. Protecting the information on mobile devices is becoming a business imperative. This is an emerging technology, so you’ll need to complete some rigorous market analysis to determine what commercial product meets your needs.
Content Management
Applications are not the only information moving to mobile devices. Content is moving as well, and organizations need a means of content management for mobile devices. For instance, it might be fine to have, and edit, some types of information on mobile devices, whereas other more sensitive information would be best suited not to be shared to this extent. Content management is the set of actions used to control content issues on mobile devices. Most organizations have a data ownership policy that clearly establishes the company ownership rights over data, regardless of the device on which it is shared. But content management goes a step further, examining what content belongs on what devices and then establishing mechanisms to enforce these rules. Again, MDM solutions exist to assist in this security issue with respect to mobile devices.
Remote Wipe
Today’s mobile devices are almost innumerable and are very susceptible to loss and theft. Further, it is unlikely that a lost or stolen device will be recovered, thus making even encrypted data stored on a device more vulnerable to decryption. If the thief can have your device for a long time, they can take all the time they want to try to decrypt your data. Therefore, many companies prefer to just remotely wipe a lost or stolen device. Remote wiping a mobile device typically removes data stored on the device and resets the device to factory settings.
Location Services
Mobile devices by their specific nature are on move, and hence the location of a device can have significant ramifications with respect to its use. Mobile devices can connect to multiple public Wi-Fi locations, and they can provide users with navigation and other location context-sensitive information, such as a local sale. To enable this functionality, location services are a set of functions to enable, yet control, the location information possessed by the device.
Geofencing
Geofencing is the use of GPS and/or RFID technology to create a virtual fence around a particular location, and to detect when devices cross the fence. This enables devices to be recognized by location and have actions taken. Geofencing is used in marketing to send messages to devices that are in a specific area—near a point of sale, or just to count potential customers. Geofencing has been used for remote workers, notifying management when they have arrived at remote work sites. This allows network connections to be enabled for them, for example. The uses of geofencing are truly only limited by one’s imagination.
Geolocation
Most mobile devices are now capable of using the Global Positioning System (GPS) for tracking device location. Many apps rely heavily on GPS location, such as device-locating services, mapping applications, traffic-monitoring apps, and apps that locate nearby businesses such as gas stations and restaurants. Such technology can be exploited to track movement and the location of the mobile device, which is referred to as geolocation. This tracking can be used to assist in the recovery of lost devices.

Know the difference between geofencing and geolocation. These make great distractors on the exam.
Geo-Tagging
Geo-tagging is the posting of location information into a data stream, signifying where the device was when the stream was created. Because many mobile devices include on-board cameras, and the photos/videos they take can divulge information, geo-tagging can make location part of any picture or video, and this information can be associated with anything the camera can image—whiteboards, documents, and even the location of the device when the photo/video was taken.
Posting photos with geo-tags embedded in them has its use, but it can also unexpectedly divulge information users might not want to share. For example, if you use your smartphone to take a photo of your car in the driveway and then post the photo on the Internet in an attempt to sell your car, if geo-tagging is enabled on the smartphone, the location of where the photo was taken is embedded as metadata in the digital photo. Such a posting could inadvertently expose where your home is located. Some social media applications strip out the metadata on a photo before posting, but then they indicate where you posted the photo within the posting itself. There has been much public discussion on this topic, and geo-tagging can be disabled on most mobile devices. It is recommended that it be disabled unless you have a specific reason for having the location information embedded in a photo.
Screen Locks
Most corporate policies regarding mobile devices require the use of the mobile device’s screen-locking capability. This usually consists of entering a passcode or PIN to unlock the device. It is highly recommended that screen locks be enforced for all mobile devices. Your policy regarding the quality of the passcode should be consistent with your corporate password policy. However, many companies merely enforce the use of screen locking. Thus, users tend to use convenient or easy-to-remember passcodes. Some devices allow complex passcodes. As shown in Figure 12.8, the device screen on the left supports only a simple iOS passcode, limited to four numbers, whereas the device screen on the right supports a passcode of indeterminate length and can contain alphanumeric characters.
• Figure 12.8 iOS lock screens
Some more advanced forms of screen locks work in conjunction with device wiping. If the passcode is entered incorrectly a specified number of times, the device is automatically wiped. This is one of the security features of BlackBerry that has traditionally made it of interest to security-conscious users. Apple has made this an option on newer iOS devices. Apple also allows remote locking of a device from the user’s iCloud account.
Mobile Device Security
Mobile devices require basic security mechanisms of screen locks, lockouts, device wiping, and encryption to protect sensitive information contained on them.
Lockout
If a user discovers that they’ve lost their device, a quick way to protect it is to remotely lock the device as soon as they recognize it has been lost or stolen. Several products are available on the market today to help enterprises manage their devices. Remote lockout is usually the first step taken in securing a mobile device.
Push Notification Services
Push notification services are services that deliver information to mobile devices without a specific request from the device. Push notifications are used a lot in mobile devices to indicate that content has been updated. Push notification methods are typically unique to the platform, with Apple Push Notification service for Apple devices and Android Cloud to Device Messaging as examples. Many other back-end server services have similar methods for updating their content.
Passwords and Pins
Passwords and pins are common security measures used to protect mobile devices from unauthorized use. These are essential tools and should be used in all cases, and mandated by company policy.
Biometrics
Biometrics are used across a wide range of mobile phones as a means of access control. Many of these devices have less-than-perfect recognition, however, and many security presentations on hacking past the biometric sensor have been shown at conferences. The newest biometric method, facial recognition, based on a camera image of the user holding their phone, offers some promise but has similar concerns. Because it has been shown that these devices can be bypassed, one should consider them to be convenience features, not security features. Hence, it is important for management policies to reflect this and not rely on these methods for securing important data.
Context-Aware Authentication
Context-aware authentication is the use of information such as who is the user, what are they requesting, what machine are they using, how are they connected, and so on, to make the authentication decision as to whether to permit the requested resource. The goal is to prevent unauthorized end users, devices, or network connections from being able to access corporate data. This approach can be used to allow an authorized user to access network-based resources from inside the office, but deny access if they are connecting via a public Wi-Fi network.
Containerization
Containerization on mobile devices is just that: dividing the device into a series of containers, with one container holding work-related materials and the other personal materials. The containers can separate apps, data, and virtually everything on the device. Depending on the mobile device management solution employed, remote control over the work container can be possible. This enables a much stronger use case for mixing business and personal data on a single device.
Storage Segmentation
On mobile devices, it can be very difficult to keep personal data separate from corporate data. Storage segmentation is similar to containerization in that it represents a logical separation of the storage in the unit. Some companies have developed capabilities to create distinct virtual containers to keep personal data separate from corporate data and applications. For devices that are used to handle highly sensitive corporate data, this form of protection is highly recommended.
Asset Control
Because each user can have multiple devices connecting to the corporate network, it is important to implement a viable asset-tracking and inventory-control mechanism. For security and liability reasons, the company needs to know what devices are connecting to its systems and what access has been granted. Just as in IT systems, maintaining a list of approved devices is a critical control.
Device Access Control
The principles of access control for mobile devices need to be managed just like access control from wired or wireless desktops and laptops. This will become more critical as storage in the cloud and Software as a Service (SaaS) become more prevalent. Emerging tablet/mobile device sharing intends to provide the user with a seamless data access experience across many devices. Data access capabilities will continue to evolve to meet this need. Rigorous data access principles need to be applied, and they become even more important with the inclusion of mobile devices as fully functional computing devices. When reviewing possible solutions, it is important that you consider seeking proof of security and procedures rather than relying on marketing brochures.
Removable Storage
Because removable devices can move data outside of the corporate-controlled environment, their security needs must be addressed. Removable devices can bring unprotected or corrupted data into the corporate environment. All removable devices should be scanned by antivirus software upon connection to the corporate environment. Corporate policies should address the copying of data to removable devices. Many mobile devices can be connected via USB to a system and used to store data—and in some cases vast quantities of data. This capability can be used to avoid some implementations of data loss prevention (DLP) mechanisms.
Disabling Unused Features
As with all computing devices, features that are not used or that present a security risk should be disabled. Bluetooth access is particularly problematic. It is best to make Bluetooth connections undiscoverable. But, users will need to enable it to pair with a new headset or car connection, for example. Requiring Bluetooth connections to be undiscoverable is very hard to enforce but should be encouraged as a best practice. Users should receive training as to the risks of Bluetooth—not so they avoid Bluetooth, but so they understand when they should turn it off. Having a mobile device with access to sensitive information carries with it a level of responsibility. Helping users understand this and act accordingly can go a long way toward securing mobile devices.
 Mobile Application Security
Mobile Application Security
Devices are not the only concern in the mobile world. Applications that run on the devices also represent security threats to the information that is stored on and processed by the device. Applications are the software elements that can be used to violate security, even when the user is not aware. Many games and utilities offer value to the user, but at the same time they scrape information stores on the device for information.
Application Control
Mobile devices are typically updated through the use of an app store. This store provides the apps and their updates in one convenient location. In devices used on enterprise networks, the security provided by the app store may not meet the requirements of the business. In these circumstances, a separate application, known typically as the Mobile Device Manager (MDM), can handle device configuration as well as security. The configuration of the MDM solution provides the company with a method of controlling what applications are loaded on the device and thus would potentially become connected to the network and other sensitive systems.
Key and Credential Management
The MDM marketplace is maturing quickly. Key and credential management services are being integrated into most MDM services to ensure that existing strong policies and procedures can be extended to mobile platforms securely. These services include protection of keys for digital signatures and S/MIME encryption and decryption. Keys and credentials are among the highest-value items that can be found on mobile devices, so ensuring protection for them is a key element in mobile device security. The keys and credentials stored on the device can be used by multiple applications. Providing protection of these keys while still maintaining usability of them is an essential element of modern mobile application security.
Authentication
When mobile devices are used to access business networks, authentication becomes an issue. Is the device allowed to access the network? Is the user of the device a network user? If so, how do you authenticate the user? Mobile devices have some advantages in that they can store certificates, which by their very nature are more secure than passwords. This moves the authentication problem to the endpoint, where it relies on passcodes, screen locks, and other mobile device protections. These can be relatively weak unless structured together, including wiping after a limited number of failures. The risk in mobile authentication is that strong credentials stored in the device are protected by the less rigorous passcode and the end user. End users can share their mobile devices, and by proxy unwittingly share their strong corporate authentication codes.
Application Whitelisting
As discussed in the “Application Control” section earlier in the chapter, controlling what applications a device can access may be an important element of your company’s mobile device policy. The use of application whitelisting and blacklisting enables you to control and block applications available on the mobile device. Whitelisting is the use of a preapproved list of behaviors – only those on the whitelist are allowed. Blacklisting is the list of behaviors that are specifically blocked. Blacklisting is great against specific known threats. Whitelisting, when possible, restricts use to only approved functions. The challenge in whitelisting is in the definition of allowed activities. This is usually administered through some type of MDM capability. Application whitelisting can improve security by preventing unapproved applications from being installed and run on the device.
Encryption
Just as the device should be encrypted, thereby protecting all information on the device, applications should be encrypted as well. Just employing encryption for the data store is not sufficient. If the device is fully encrypted, then all apps would have to have access to the data, in essence bypassing the encryption from an app point of view. Apps with sensitive information should control access via their own set of protections. The only way to segregate data within the device is for apps to manage their own data stores through app-specific encryption. This will allow sensitive data to be protected from rogue applications that would leak data if uniform access was allowed.
Transitive Trust/Authentication
Security across multiple domains/platforms is provided through trust relationships. When trust relationships between domains or platforms exist, authentication for each domain trusts the authentication for all other trusted domains. Thus, when an application is authenticated, its authentication is accepted by all other domains/platforms that trust the authenticating domain or platform. Trust relationships can be very complex in mobile devices, and often security aspects aren’t properly implemented. Mobile devices tend to be used across numerous systems, including business, personal, public, and private. This greatly expands the risk profile and opportunity for transitive trust–based attacks. As with all other applications, mobile applications should be carefully reviewed to ensure that trust relationships are secure.
 Policies for Enforcement and Monitoring
Policies for Enforcement and Monitoring
This section covers the topics of corporate policies and mobile device usage in a corporate environment. Your corporate policies regarding mobile devices should be consistent with your existing computer security policies. Your training programs should include instruction on mobile device security. Disciplinary actions should be consistent. Your monitoring programs should be enhanced to include monitoring and control of mobile devices.
Third-Party App Stores
Many mobile devices have manufacturer-associated application stores, where applications can be downloaded to the device. From a corporate enterprise point of view, these application stores are third-party app stores, as they represent neither the user nor the enterprise in the nature and quantity of their offerings. Currently there are two main app stores: one from Apple and one from Google. The Apple store is built on a principle of exclusivity, and security is highly enforced on apps. The Google store has less restrictions, which has translated into some security issues from apps. Managing what applications a user can add to the device is essential because many of these applications can create security risks for the enterprise. This issue becomes significantly more complex with employee-owned devices and access to corporate data stores. There are very few segmentation options for most devices to separate work and personal spaces, so the ability to control this access becomes problematic. For devices with access to sensitive corporate information, a company-owned device is recommended, thus allowing for more stringent control.
Rooting/Jailbreaking
A common hack associated with mobile devices is the jailbreak. Jailbreaking is a process by which the user escalates their privilege level, bypassing the operating system’s controls and limitations. The user still has the complete functionality of the device, but also has additional capabilities that bypass the OS-imposed user restrictions. There are several schools of thought concerning the utility of jailbreaking, but the important issue from a security point of view is that running any device with enhanced privileges can result in errors that cause more damage, because normal security controls are typically bypassed.
Rooting a device is a process whereby OS controls are bypassed on Android devices. The effect is the same whether the device is rooted or jailbroken: the OS controls designed to constrain operations are no longer in play and the device can do things it was never intended to do, good or bad.

Rooting is used to bypass OS controls on Android, and jailbreaking is used to escalate privileges and do the same on iOS devices. Both processes stop OS controls from inhibiting user behaviors.
Sideloading
Sideloading is the process of adding apps to a mobile device without using the authorized store associated with the device. Currently, sideloading only works on Android devices because Apple has not enabled any application execution except of those coming through the app store. Sideloading is an alternative means of instantiating an app on the device without having to have it hosted on the app store. The downside, simply put, is that without the app store screening, one is at greater risk of installing malicious software in the guise of a desired app.
Custom Firmware
Custom firmware is firmware for a device that has been altered from the original factory settings. This firmware can bring added functionality, but it can also result in security holes. The use of custom firmware should only be done on devices without access to critical information.
Carrier Unlocking
Most mobile devices in the U.S. come locked to a carrier, while in other parts of the world they are unlocked, relying on a SIM card for connection and billing information. This is a byproduct of the business market decisions made early in the mobile phone market lifecycle and has remained fairly true to date. If you have a carrier-locked device and you attempt to use a SIM card from another carrier, the phone will not accept it unless you unlock the device. Carrier unlocking is the process of telling the device to sever itself from the carrier. This is usually done through the inputting of a special key sequence that unlocks the device.
Firmware OTA Updates
Firmware is, at the end of the day, software. It may be stored in a chip, but like all software, it sometimes requires updating. With mobile devices being literarily everywhere, the scale does not support bringing the device to a central location or connection for updating. Firmware OTA (over the air) updates are a solution to this problem. Just as one can add an app, or update an app from the store, it is possible to have a menu option that permits the device firmware to be updated. All major device manufacturers support this model because it is the only real workable solution.
Camera Use
Many mobile devices include on-board cameras, and the photos/videos they take can divulge information. This information can be associated with anything the camera can image—whiteboards, documents, and even the location of the device when the photo/video was taken via geo-tagging. Another challenge presented by mobile devices is the possibility that they will be used for illegal purposes. This can create liability for the company if it is a company-owned device. Despite all the potential legal concerns, possibly the greatest concern of mobile device users is that their personal photos will be lost during a device wipe originated by the company.
SMS/MMS
Short Message Service (SMS) and Multimedia Messaging Service (MMS) are standard protocols used to send messages, including multimedia content in the case of MMS, to and from mobile devices over a cellular network. SMS is limited to short text-only messages of less than 160 characters and is carried over the signaling path of the cellular network when signaling data is not being sent. SMS dates back to the early days of mobile telephony in the 1980s, whereas MMS is a more recent development designed to support multimedia content to and from mobile devices. Because of the content connections that can be sent via MMS in particular, and SMS in certain cases, it is important to at least address these communication channels in relevant policies.
External Media
External media refers to any item or device that can store data. From flash drives to hard drives, music players, smartphones, and even smart watches, if it can store data, it is a pathway for data exfiltration. External media can also deliver malware into the enterprise. The risk is evident: these devices can carry data in and out of the enterprise, yet they have become synonymous with today’s tech worker. The key is to develop a policy that determines where these devices can exist and where they should be banned, and then follow the plan with monitoring and enforcement.
USB OTG
Universal Serial Bus is a common method of connecting mobile devices to computers and other host-based platforms. Connecting mobile devices directly to each other required changes to USB connections. Enter USB OTG (USB On-The-Go), an extension of USB technology that facilitates direct connection between USB OTG–enabled mobile devices. USB OTG allows those devices to switch back and forth between the roles of host and device, including deciding who provides power (host) and who consumes power across the interface. USB OTG also allows the connection of USB-based peripherals, such as keyboards, mice, and storage, to mobile devices. Although USB OTG is relatively new, most mobile devices made since 2015 are USB OTG compatible.
Recording Microphone
Many of today’s electronic devices—from smartphones to watches, to devices such as the online assistants from Amazon and Google, and even toys—have the ability to record audio information. Recording microphones can be used to record conversations and collect sensitive data, and the parties under observation are not even aware of the incident. As with other high-tech gadgets, the key is to determine the policy of where they can be used and the rules for their use.
GPS Tagging
GPS tagging is the addition of GPS information to a file or folder, or other digital item. Adding GPS information to the metadata of a file can add value in that it enables site specific information to be associated with the digital item. This can be a location where a picture was taken, or map coordinates when linking to mapping software. A more extensive coverage of this type of tagging was covered earlier in the chapter under the section heading “Geo-tagging.”
Wi-Fi Direct/Ad Hoc
Wi-Fi typically connects a Wi-Fi device to a network via a wireless access point. Other methods exist—namely, Wi-Fi direct and Wi-Fi ad hoc. In Wi-Fi direct, two Wi-Fi devices connect to each other in a single-hop connection. In essence, one of the two devices acts as an access point for the other device. The key element is the single-hop nature of a Wi-Fi direct connection. In the end, Wi-Fi direct connects only two devices. These two devices can be connected with all of the bells and whistles of modern wireless networking, including WPA2.
Wi-Fi direct uses a couple of services to establish secure connections between devices. The first is Wi-Fi Direct Device and Service Discovery. This protocol provides a way for devices to discover each other based on the services they support before connecting. A device can see all compatible devices in the area and then narrow down the list to only devices that allow a specific service (say, printing) before displaying to the user a list of available printers for pairing. The second protocol used is WPA2. This protocol is used to protect the connections and prevent unauthorized parties from pairing to Wi-Fi Direct devices, or intercepting communications from paired devices.
For Wi-Fi ad-hoc, the primary difference is that in the ad hoc network, multiple devices can communicate with each other, with each device capable of communicating with all other devices.
Tethering
Tethering is the connection of a device to a mobile device that has a means of accessing a network for the purpose of sharing network access. Connecting a mobile phone to a laptop to charge the phone’s battery is not tethering. Connecting it so that the laptop can use the phone to connect to the Internet is tethering. Tethering introduces new outside-of-the-enterprise, span-of-control network connections; it can act to bridge your enterprise network with the outside network.
Payment Methods
Twenty years ago, payment methods were cash, check, and charge. Today, we have new intermediaries; for example, smart devices with NFC linked to credit cards offer a convenience alternative for payments. Although the actual payment is still a credit/debit card charge, the payment pathway is through the digital device. Utilizing the security features of the device, NFC, and biometrics/PIN, this form of payment has some advantages over the other methods because it allows for the addition of specific security measures before the payment method is accessed.
 Deployment Models
Deployment Models
When determining how to incorporate mobile devices securely within the enterprise, you have a wide range of considerations. How will security be enforced? How will all the policies be enforced? And, ultimately, what devices will be supported in the enterprise? There are a variety of deployment models—from employee-owned devices to corporate-owned devices, with mixtures of the two in between. Each of these models has advantages and disadvantages.
CYOD
CYOD (choose your own device) is very similar to BYOD (bring your own device) in concept: users have a choice in the type of device. In most cases, this choice is constrained to a list of acceptable devices that can be supported in the enterprise. Because the device is corporate owned, CYOD provides greater flexibility in corporate restrictions on device use, in terms of apps, data, updates, and so on.
COPE
COPE (company-issued, personally enabled) is a model where employees are supplied a phone chosen and paid for by the company, but they are given permission to use it for personal activities. The company can decide how much choice and freedom employees get with the personal use of the device. This allows the enterprise to control security functionality while dealing with the employee dissatisfaction associated with the traditional method of supplying devices: corporate-owned business-only (COBO).
Corporate Owned
Corporate-owned business-only (COBO) is a model in which the business supplies a mobile device for company-only use on the part of the employee. This has the disadvantage of the employee having to carry two devices—one personal and one for work—and then separate functions between the devices based on the purpose of use in each instance. The advantage is that the corporation has complete control over the device and can apply any security controls desired without interference from other device functionality.
BYOD
BYOD (bring your own device) has many advantages in business, and not just from the perspective of device cost. Users tend to prefer having a single device rather than carrying multiple devices. Users have less of a learning curve on devices they already have an interest in learning. This model is popular in small firms and those employing a lot of temporary workers. The big disadvantage is that employees will not be eager to limit the use of their personal device based on corporate policies, so corporate control will be limited.
Data Ownership
BYOD blurs the lines of data ownership because it blurs the lines of device management. If a company owns a smartphone issued to an employee, the company can repossess the phone upon employee termination. This practice may protect company data by keeping the company-issued devices in the hands of employees only. However, a company cannot rely on a simple factory reset before reissuing a device, because factory resetting might not remove all the data on the device. If a device is reissued, it is possible that some of the previous owner’s personal information, such as private contacts, still remains on the device. On the other hand, if the employee’s device is a personal device that has been used for business purposes, upon termination of the employee, it is likely that some company data remains on the phone despite the company’s best efforts to remove its data from the device. If that device is resold or recycled, the company’s data might remain on the device and be passed on to the subsequent owner. Keeping business data in separate, MDM-managed containers is one method of dealing with this issue.
BYOD Concerns
There is a dilemma in the use of BYOD devices that store both personal and enterprise data. Wiping the device usually removes all data, both personal and enterprise. Therefore, if corporate policy requires wiping a lost device, that policy may mean the device’s user loses personal photos and data. The software controls for separate data containers—one for business and one for personal—have been proposed but are not a mainstream option yet.
Storage Segmentation
Storage segmentation methods are needed whenever a device has multilevel data security types, as in personal and corporate, or corporate and highly sensitive corporate. Having the ability to manage the separate data streams based on their sensitivity is important because of the highly mobile nature of the device.
Support Ownership
Support costs for mobile devices are an important consideration for corporations. Each device has its own implementation of various functions. While those functions typically are implemented against a specification, software implementations might not fully or properly implement the specification. This can result in increased support calls to your help desk or support organization. It is very difficult for a corporate help desk to be knowledgeable on all aspects of all possible devices that access a corporate network. For example, your support organization must be able to troubleshoot iPhones, Android devices, tablets, and so forth. These devices are updated frequently, new devices are released, and new capabilities are added on a regular basis. Your support organization will need viable knowledge base articles and job aids in order to provide sufficient support for the wide variety of ever-changing devices.
Patch Management
Just as your corporate policy should enforce the prompt update of desktop and laptop computers to help eliminate security vulnerabilities on those platforms, it should also require mobile devices to be kept current with respect to patches. Having the latest applications, operating system, and so on is an important best defense against viruses, malware, and other threats. It is important to recognize that “jailbreaking” or “rooting” your device can remove the manufacturer’s security mechanisms and protection against malware and other threats. These devices might also no longer be able to update their applications or OS against known issues. Jailbreaking or rooting is also a method used to bypass security measures associated with the device manufacturer control, and in some locations, this can be illegal. Mobile devices that are jailbroken or rooted should not be trusted on your enterprise network or allowed to access sensitive data.
Antivirus Management
Just like desktop and laptop computers need protection against viruses and malware, so too do, smartphones, tablets, and other mobile devices. It is important that corporate policy and personal usage keep operating systems and applications current. Antivirus and malware protection should be employed as widely as possible and kept up to date against current threats.
Forensics
Mobile device forensics is a rapidly evolving and fast-changing field. Because devices are evolving so quickly, it is difficult to stay current in this field. Solid forensics principles should always be followed. Devices should be properly handled by using RF-shielded bags or containers. Because of the rapid changes in this area, it’s best to engage the help of trained forensic specialists to ensure that data isn’t contaminated and that the device state and memory are unaltered. If forensics are needed on a device that has both personal and business data, then policies need to be in place to cover the appropriate privacy protections on the personal side of the device.
Privacy
When an employee uses their personal device to perform their work for the company, they may have strong expectations that privacy will be protected by the company. The company policy needs to consider this and address it explicitly. On company-owned devices, it’s quite acceptable for the company to reserve the right to access and wipe any company data on the device. The company can thus state that the user can have no expectation of privacy when using a company device. But when the device is a personal device, the user may feel stronger ownership. Expectations of privacy and data access on personal devices should be included in your company policy.
Onboarding/Offboarding
Most companies and individuals find it relatively easy to connect mobile devices to the corporate network. Often there are no controls around for connecting a device other than having a Microsoft Exchange account. When new employees join a company, the onboarding processes need to include provisions for mobile device responsibilities. It is easy for new employees to bypass security measures if they are not part of the business process of onboarding.
Employee termination needs to be modified to include termination of accounts on mobile devices. It’s not uncommon to find terminated employees with accounts or even company devices still connecting to the corporate network months after being terminated. E-mail accounts should be removed promptly as part of the employee termination policy and process. Mobile devices supplied by the company should be collected upon termination. BYOD equipment should have its access to corporate resources terminated as part of the offboarding process. Regular audits for old or unterminated accounts should be performed to ensure prompt deletion of accounts for terminated employees.
Adherence to Corporate Policies
Your corporate policies regarding BYOD devices should be consistent with your existing computer security policies. Your training programs should include instruction on mobile device security. Disciplinary actions should be consistent. Your monitoring programs should be enhanced to include monitoring and control of mobile devices.
BYOD User Acceptance
BYOD inherently creates a conflict between personal and corporate interests. An employee who uses their own device to conduct corporate business inherently feels strong ownership over the device and may resent corporate demands to control corporate information downloaded to the device. On the other hand, the corporation expects that corporate data be properly controlled and protected and thus desires to impose remote wiping or lockout requirements in order to protect corporate data. An individual who loses their personal photos from a special event will likely harbor ill feelings toward the corporation if it wipes their device, including those irreplaceable photos. Your corporate BYOD policy needs to be well defined, approved by the corporate legal department, and clearly communicated to all employees through training.
Architecture/Infrastructure Considerations
Mobile devices consume connections to your corporate IT infrastructure. It is not unusual now for a single individual to be connected to the corporate infrastructure with one or more smartphones, tablets, and laptop or desktop computers. Some infrastructure implementations in the past have not been efficient in their design, sometimes consuming multiple connections for a single device. This can reduce the number of available connections for other end users. It is recommended that load testing be performed to ensure that your design or existing infrastructure can support the potentially large number of connections from multiple devices.
Multiple connections can also create security issues when the system tracks user accounts against multiple connections. Users will need to be aware of this, so that they don’t inadvertently create incident response situations or find themselves locked out by their own actions. This can be a tricky issue and requires a bit more intelligent design than the traditional philosophy of “one user ID equals one current connection.”
Legal Concerns
It should be apparent from the various topics discussed in this chapter that there are many security challenges presented by mobile devices used for corporate business. Because the technology is rapidly changing, it’s best to make sure you have a solid legal review of policies. There are both legal and public relation concerns when it comes to mobile devices. Employees who use both company-owned and personal devices have responsibilities when company data is involved. Policies and procedures should be reviewed on a regular basis to stay current with technology.
Another challenge presented by mobile devices is the possibility that they will be used for illegal purposes. This can create liability for the company if it is a company-owned device.
Acceptable Use Policy
Similar to your acceptable use policies for laptops and desktops, your mobile device policies should address acceptable use of mobile or BYOD devices. Authorized usage of corporate devices for personal purposes should be addressed. Disciplinary actions for violation of mobile device policies should be defined. BYOD offers both the company and the user advantages; ramifications should be specifically spelled out, along with the specific user responsibilities.

Mobile devices offer many usability advantages across the enterprise, and they can be managed securely with the help of security-conscious users. Security policies can go a long way toward assisting users in understanding their responsibilities associated with mobile devices and sensitive data.
VDI
Although it seems that deployment models are only associated with phones, this is really not the case—at times, personal computers can also be external mobile devices requiring connections. In the case of laptops, a virtual desktop infrastructure (VDI) solution can bring control to the mobile environment associated with non-corporate-owned equipment. The enterprise can set up virtual desktop machines that are fully security compliant and contain all the necessary applications needed by the employee, and then let the employee access the virtual machine via either a virtual connection or a remote desktop connection. This can solve most if not all of the security and application functionality questions associated with mobile devices. It does require an IT organization capable of setting up, maintaining, and managing the VDI in the enterprise, which is not necessarily a small task depending on the number of instances needed.
Chapter 12 Review
 Chapter Summary
Chapter Summary
After reading this chapter and completing the exercises, you should understand the following about wireless security and mobile devices.
Describe the different wireless systems in use today
![]() Wireless Application Protocol (WAP) is used on small, handheld devices like cell phones for out-of-the-office connectivity.
Wireless Application Protocol (WAP) is used on small, handheld devices like cell phones for out-of-the-office connectivity.
![]() 802.11 is the IEEE standard for wireless local area networks. The standard includes several different specifications of 802.11 networks, such as 802.11b, 802.11a, 802.11g, and 802.11n.
802.11 is the IEEE standard for wireless local area networks. The standard includes several different specifications of 802.11 networks, such as 802.11b, 802.11a, 802.11g, and 802.11n.
Detail WAP and its security implications
![]() WAP is the data protocol used by many cellular phones to deliver e-mail and lightweight web services.
WAP is the data protocol used by many cellular phones to deliver e-mail and lightweight web services.
![]() Designers created WTLS as a method to ensure privacy of data being broadcast over WAP.
Designers created WTLS as a method to ensure privacy of data being broadcast over WAP.
![]() WTLS has a number of inherent security problems, such as weak encryption necessitated by the low computing power of the devices and the network transition that must occur at the cellular provider’s network, or the WAP gap.
WTLS has a number of inherent security problems, such as weak encryption necessitated by the low computing power of the devices and the network transition that must occur at the cellular provider’s network, or the WAP gap.
Identify 802.11’s security issues and possible solutions
![]() 802.11 does not allow physical control of the transport mechanism.
802.11 does not allow physical control of the transport mechanism.
![]() Transmission of all network data wirelessly transmits frames to all wireless machines, not just a single client, similar to Ethernet hub devices.
Transmission of all network data wirelessly transmits frames to all wireless machines, not just a single client, similar to Ethernet hub devices.
![]() Poor authentication is caused by the SSID being broadcast to anyone listening.
Poor authentication is caused by the SSID being broadcast to anyone listening.
![]() Flawed implementation of the RC4 encryption algorithm makes even encrypted traffic subject to interception and decryption.
Flawed implementation of the RC4 encryption algorithm makes even encrypted traffic subject to interception and decryption.
Learn about the different types of wireless attacks
![]() Attacks against protocols include bluejacking, blusnarfing, and IV attacks.
Attacks against protocols include bluejacking, blusnarfing, and IV attacks.
![]() Attacks against the wireless system include evil twin and rogue AP attacks.
Attacks against the wireless system include evil twin and rogue AP attacks.
Examine the elements needed for enterprise wireless deployment
![]() Wireless coverage can be a function of antenna type, placement, and power levels.
Wireless coverage can be a function of antenna type, placement, and power levels.
![]() Captive portals can be used to control access to wireless systems.
Captive portals can be used to control access to wireless systems.
Examine the security of mobile systems
![]() Mobile devices have specific security concerns and specific controls to assist in securing them.
Mobile devices have specific security concerns and specific controls to assist in securing them.
![]() BYOD has its own concerns as well as policies and procedures to manage mobile devices in the enterprise.
BYOD has its own concerns as well as policies and procedures to manage mobile devices in the enterprise.
![]() Mobile applications require security, and the issues associated with mobile, apps, and security need to be addressed.
Mobile applications require security, and the issues associated with mobile, apps, and security need to be addressed.
 Key Terms
Key Terms
beacon frames (385)
bluebugging (401)
bluejacking (400)
bluesnarfing (400)
Bluetooth (381)
Bluetooth DoS (401)
captive portal (398)
containerization (406)
custom firmware (411)
direct-sequence spread spectrum (DSSS) (384)
disassociation (402)
Extensible Authentication Protocol (EAP) (391)
EAP-FAST (392)
EAP-TLS (392)
EAP-TTLS (392)
evil twin (399)
firmware OTA updates (411)
geo-tagging (405)
IEEE 802.1X (392)
infrared (IR) (383)
initialization vector (IV) (399)
jailbreaking (410)
jamming (400)
MAC filtering (398)
MIMO (396)
mobile device management (MDM) (402)
multimedia Messaging Service (MMS) (412)
near field communication (NFC) (382)
orthogonal frequency division multiplexing (OFDM) (384)
PEAP (392)
Radio Frequency Identification (RFID) (401)
RC4 stream cipher (387)
remote wiping (404)
replay attack (399)
rogue access point (400)
rooting (411)
screen locking (405)
service set identifier (SSID) (385)
Short Message Service (SMS) (412)
sideloading (411)
site survey (397)
storage segmentation (407)
Temporal Key Integrity Protocol (TKIP) (388)
USB OTG (USB On-The-Go) (412)
WAP gap (378)
war-chalking (386)
war dialing (386)
war driving (386)
Wi-Fi Protected Access 2 (WPA2) (389)
WiMAX (375)
Wired Equivalent Privacy (WEP) (387)
Wireless Application Protocol (WAP) (376)
Wireless Transport Layer Security (WTLS) (377)
ZigBee (375)
 Key Terms Quiz
Key Terms Quiz
Use terms from the Key Terms list to complete the sentences that follow. Don’t use the same term more than once. Not all terms will be used.
1. An AP uses _______________ to advertise its existence to potential wireless clients.
2. The _______________ is the part of the RC4 cipher that has a weak implementation in WEP.
3. Two common mobile device security measures are _______________ and _______________.
4. WAP uses the _______________ protocol to attempt to ensure confidentiality of data.
5. The 32-character identifier attached to the header of a packet used for authentication to an 802.11 access point is the _______________.
6. _______________ is a feature that can disclose a user’s position when sharing photos.
7. 802.11i updates the flawed security deployed in _______________.
8. The standard for wireless local area networks is called _______________.
9. The type of application used to control security across multiple mobile devices in an enterprise is called _______________.
10. 802.11a uses frequencies in the _______________.
 Multiple-Choice Quiz
Multiple-Choice Quiz
1. Bluebugging can give an attacker what?
A. All of your contacts
B. The ability to send “shock” photos
C. Total control over a mobile phone
D. A virus
2. How does 802.11n improve network speed?
A. Wider bandwidth
B. Higher frequency
C. Multiple-input multiple-output (MIMO)
D. Both A and C
3. WTLS ensures integrity through what device?
A. Public key encryption
B. Message authentication codes
C. Source IP
D. Digital signatures
4. WEP has used an implementation of which of the following encryption algorithms?
A. SHA
B. ElGamal
C. RC4
D. Triple-DES
5. What element does not belong in a mobile device security policy in an enterprise employing BYOD?
A. Separation of personal and business-related information
B. Remote wiping
C. Passwords and screen locking
D. Mobile device carrier selection
6. What is bluejacking?
A. Stealing a person’s mobile phone
B. Sending an unsolicited message via Bluetooth
C. Breaking a WEP key
D. Leaving your Bluetooth in discoverable mode
7. While the SSID provides some measure of authentication, why is it not very effective?
A. It is dictated by the manufacturer of the access point.
B. It is encrypted.
C. It is broadcast in every beacon frame.
D. SSID is not an authentication function.
8. The 802.1X protocol is a protocol for Ethernet:
A. Authentication
B. Speed
C. Wireless
D. Cabling
9. What is the best way to avoid problems with Bluetooth?
A. Keep personal info off your phone
B. Keep Bluetooth discoverability off
C. Buy a new phone often
D. Encryption
10. Why is attacking wireless networks so popular?
A. There are more wireless networks than wired.
B. They all run Windows.
C. It’s easy.
D. It’s more difficult and more prestigious than other network attacks.
 Essay Quiz
Essay Quiz
1. Produce a report on why sensitive information should not be sent over the Wireless Application Protocol.
2. When you want to start scanning for rogue wireless networks, your supervisor asks you to write a memo detailing the threats of rogue wireless access points. What information would you include in the memo?
3. Write a security policy for company-owned cell phones that use the Bluetooth protocol.
4. Write a memo recommending upgrading your organization’s old 802.11b infrastructure to an 802.11i-compliant network, and detail the security enhancements.
Lab Projects
• Lab Project 12.1
Set up a wireless scanner on a computer and then use it to find wireless access points. You will need the following:
![]() A laptop with Windows or Linux installed
A laptop with Windows or Linux installed
![]() A compatible wireless 802.11 network adapter
A compatible wireless 802.11 network adapter
Then do the following:
1. Pick an appropriate scanner software package.
2. Install and configure package.
3. Start the program and make sure it sees your wireless adapter.
4. Take the laptop on your normal commute (or drive around your neighborhood) with the software running.
5. Log any access points you detect.
• Lab Project 12.2
Attempt to scan the area for Bluetooth devices. You will need a cell phone with Bluetooth installed or a computer with a Bluetooth adapter. Then do the following:
1. If you’re using a PC, download BlueScanner from SourceForge at http://sourceforge.net/projects/bluescanner/.
2. Take your phone or computer to a place with many people, such as a café.
3. Start the program and make sure it sees your Bluetooth adapter.
4. Attempt to scan for vulnerable Bluetooth devices.
5. If you’re using your phone, tell it to scan for Bluetooth devices. Any devices that you find are running in “discoverable” mode and are potentially exploitable.

 Tech Tip
Tech Tip