This chapter provides an introduction to radio frequency identification (RFID), the history of the technology, and its uses. It will compare and contrast RFID technology and standards while providing a context for how RFID is used to overcome real-world business challenges.
The intention of this section is not to make you an expert on the “physics” side of RFID technology, but provide enough of a high-level overview to enable informed discussions and choices.
Tracking Stuff: Eyeballs and Lasers
From the dawn of recorded history, through paintings on cave walls, cuneiform tablets from ancient Babylon, tax records from medieval England, all the way up to modern information systems and databases, we have been obsessed with answering the question, “Where is my stuff?”
Advances in information technology (IT) have always been tied to helping us understand the physical world around us, especially those aspects in which we have some special interest or ownership. The foundation of keeping track of things in the physical world around us is identifying assets, pairing a sensor for collecting information with distinguishing features of a specific asset.
For thousands of years, the essential technology used to identify things was eyesight, coupled with a variety of visual cues. These took a variety of forms, such as pictograms1 and text. Combining these with paper ledgers to form information management systems made it feasible to manage assets at a far larger scale than ever before.
With the advent of computer-based information processing systems, the information about “stuff” started moving out of accounting books and ledgers and into their electronic counterparts. The fundamental link between these electronic records and the physical objects they tracked remained the eyeball, requiring manual data entry to synchronize the digital and physical worlds.
The challenge with the Mark 1 Mod 0 eyeball (a military colloquialism referring to unaided human eyesight) and handwriting is the human factor. The volume of seemingly identical goods began to overwhelm the human component’s ability to capture and process information. For example, take the example of a modern supermarket. How would our large markets function if each cashier had to remember the price of each and every type of product in the store, and ring it in manually?
__________
1. Such “primitive” methods of identifying objects are more common than one might think. Everything from “no parking” signs to corporate logos use pictograms to visually associate information.
In the late 1960s, the availability of relatively cheap laser technology led to the development of the now ubiquitous bar code technology, allowing assets to be automatically identified, bridging the gap between the digital and physical worlds. In less than 30 years, the technology has pervaded our lives, appearing on nearly every packaged good available for sale.
As the global supply chain came into being, and trends such as just-in-time inventory drove the need for increased efficiencies, several shortcomings in bar code technology became apparent. This is not to say that bar codes aren’t an amazing technology that will be with us for a very long time, simply that their basis on optics rules out being able to extend them to handle a number of scenarios.
The key shortcomings of bar codes that became apparent are the following:
Limitation to line of sight: As reading a bar code requires that the reader (either a laser or special camera) can actually see the bar code, there needs to be a line of sight between the scanner and the bar code. This prevents a scanner from reading items that are inside a box (such as a pallet of goods) or otherwise obscured or out of alignment. (Depending on the scanner being used, the bar code may have to be at a very specific alignment to the reader.) In addition to the line-of-sight challenges, bar code scanners can only read one item at a time. As anyone who has ever waited in line at a supermarket knows all too well, this means that every item needs to be scanned individually.
Static content: Once a bar code has been printed, the data encoded cannot be changed without replacing the label.
Data capacity for serialized items: The amount of data that can be contained within a typical one-dimensional bar code (i.e., a standard UPC code) is fairly limited—often a ten-digit number. Although it’s well suited to encoding both the manufacturer of a product and the SKU,2 it doesn’t have sufficient capacity to serialize individual assets.
![]() Note Serializing refers to the ability to assign a unique identification code to a specific item, rather than an identifying code to that type of item. With a serialized identification number, it is possible to not only identify something as a specific type of item (such as a laptop), but a specific item (such as that laptop).
Note Serializing refers to the ability to assign a unique identification code to a specific item, rather than an identifying code to that type of item. With a serialized identification number, it is possible to not only identify something as a specific type of item (such as a laptop), but a specific item (such as that laptop).
A number of new bar-coding technologies have been developed that seek to address the data size limitations, such as 2D bar codes. Commonly used in military and logistics applications, 2D bar codes allow encoding of a large amount of information. However, they still suffer from some of the limitations of optics technology (such as requiring a line of sight). In addition, the physical size of these codes often prevents them from being used in applications with space or marketing constraints.
These challenges with both manual asset identification and bar-coding have led to the rise of a new form of automated identification technology: RFID. Rather than optics, RFID utilizes radio waves to communicate identification data.
__________
2. SKU stands for stock-keeping unit, and is used to represent a type of item or packaged collection of like items (such as a box of razors).
Introducing Radio Frequency Identification
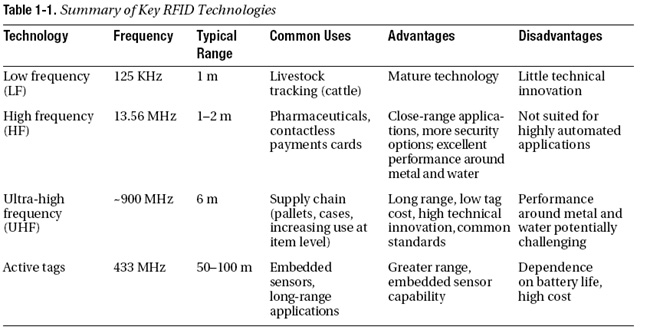
RFID is a technology that uses radio waves to pass information between a reader and a tag (analogous to how bar codes use optics to pass information between a scanner and a bar code). In general (although some active flavors of RFID work slightly differently), the sequence of events for reading an RFID tag is as follows (as illustrated in Figure 1-1):
- An interrogator (i.e., reader) generates a radio signal.
- A tag receives this signal and transmits back information.
- This information is passed back to a host computer.
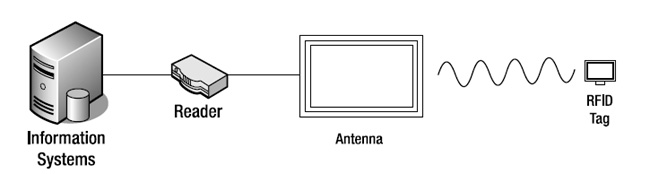
Figure 1-1. Anatomy of an RFID System
There are several different types of RFID technology that operate in different frequency bands, draw the power needed for the tags from difference sources, and store different quantities and types of information.
Using radio waves rather than optics opens up several new applications that can be used to drive solutions to business challenges:
RFID technology does not require line of sight. Tags can be read inside of boxes, and through cardboard and wood. Items on a conveyer belt do not require exact alignment with a scanner to be read.
Tags can store dynamic information. RFID tags can hold a large amount of information (from 96 bits to thousands of bytes). This information can be updated in the field. This provides enough information storage for unique, global serialization of assets. Organizations such as GS1 and EPCglobal are leading efforts to provide standard ways of encoding data on RFID tags—the RFID equivalent of UPC codes. These encodings provide standard methods of encoding company IDs, product IDs, and so on.
Tags can provide information security. Certain flavors of RFID technology provide encryption support for accessing data.
Along with its unique advantages, RFID technology also carries some key limitations that need to be taken into account when developing a solution:
The transmission and receipt of radio waves are affected by materials such as water and metal. While it is not impossible to use RFID technology with these substances, special care needs to be taken in choosing appropriate flavors of RFID and deploying the technology.
There are regulatory requirements on which radio frequencies may be used and how much power may be emitted by readers. These regulations vary by country and frequency band.
There are several different types of RFID technology, each with its own unique advantages and disadvantages. Selecting the appropriate technology in developing an asset visibility solution (be it RFID, bar codes, or eyeballs and paper) is a critical factor in the success of the overall solution.
Navigating the Technology Matrix
RFID technology is primarily categorized by its power source (active vs. passive) and frequency band. The key types of RFID technology are outlined in Table 1-1, which provides a breakdown by technology type, frequency band, key advantages/disadvantages, and primary uses.
What’s in a Tag?
RFID tags typically consist of the inlay, containing the antenna and digital circuitry, and the encapsulation (the physical packaging that surrounds and protects the digital circuitry of an RFID tag, typically a paper label or plastic shell). Many different companies take inlays and provide encapsulations, often in the form of labels, or more ruggedized form factors such as hardened plastic casings for use on reusable pallets. Figure 1-2 shows some examples of typical RFID tags.

Figure 1-2. Samples of RFID tags
Active vs. Passive
Passive RFID technology uses the energy provided by the reader to power the RFID tags. In essence, the tag uses the energy provided by the reader as a power source. This gives passive tags a virtually infinite life span, as they have no moving parts and no batteries to deplete. On the other hand, they have a shorter range than active tags, and can only operate when activated by a reader.
Active RFID technology uses an onboard battery to power the RFID tags. This allows active tags to have a longer communication range, and to perform tasks when not within range of a reader. They can also have onboard sensors that allow sampling of temperature, humidity, and physical shock (such as being dropped), in addition to providing identifying information. In contrast, they tend to be a lot bulkier and more expensive than passive tags, and require batteries to be replaced on a regular basis.
In terms of cost, the relatively simple design of passive tags means that they are an order of magnitude cheaper than active tags. While the exact price of tags depends on factors such as technology, vendor, and volume, passive RFID tags often cost on the order of cents, while active tags can cost upward of $100. Table 1-1 lists some of the key RFID technologies.
![]() Note The air protocol, also commonly referred to as the air interface, describes the communication protocol used to translate back and forth between electromagnetic waves and information. This is analogous to the Ethernet wire protocol.
Note The air protocol, also commonly referred to as the air interface, describes the communication protocol used to translate back and forth between electromagnetic waves and information. This is analogous to the Ethernet wire protocol.
Passive Readers in Action
All passive RFID systems, regardless of their frequency band and air protocol, share certain common characteristics. Passive RFID systems are composed of readers (interrogators), antennae, and tags. Tags store information, readers manage the logic and communication, and antennae shift electrical waveforms into the appropriate electromagnetic frequency (see Figure 1-3).
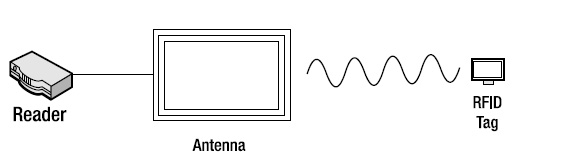
Figure 1-3. Passive RFID
The basic sequence for communicating with an RFID tag is the following:
- The reader activates (powers) the antenna. This transmits a carrier wave on the chosen frequency (see Figure 1-4).
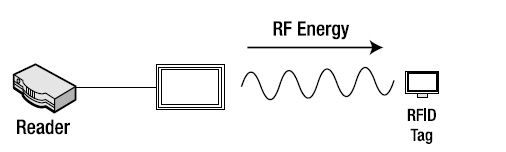
Figure 1-4. Powering (energizing) the tag
- The tag receives the signal (through its built-in antenna), which is used to power up the onboard digital logic (see Figure 1-5). Note that the tag’s antenna is tuned to receive a specific range of frequencies, similar to a car radio being dialed into a specific radio station.
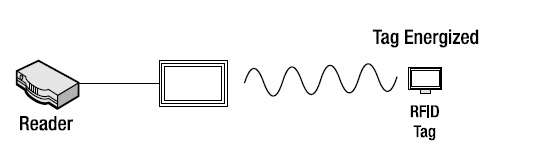
Figure 1-5. The tag has been energized by the reader.
- The reader then modulates data on top of the carrier wave (see Figure 1-6).3 The specifics depend on the air interface of the particular RFID technology being used (i.e., even within a specific type of RFID, such as HF, different air protocols can be used).
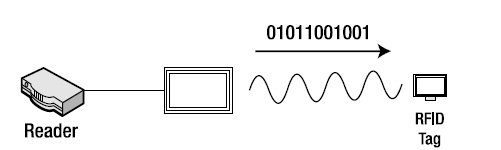
Figure 1-6. Reader transmitting data to an energized tag
- If the tag has been successfully energized, and recognizes the command transmitted from the reader (such as a request for the tag’s identifying code), the tag executes that command (see Figure 1-7).
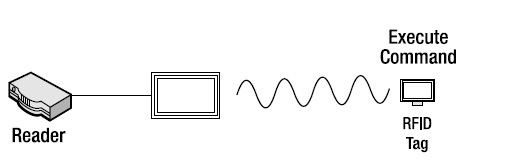
Figure 1-7. Tag executing command received from the reader
- The results of the command (such as the tag’s ID) are then sent back to the reader, as shown in Figure 1-8.
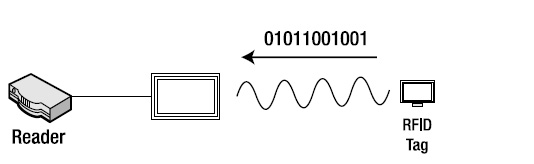
Figure 1-8. Tag transmitting response back to the reader
Successful communication between the reader and the tag depends on several factors:
- The reader and tag have to be using a compatible frequency range. If the tag is built for a different frequency than the reader is transmitting, it won’t receive any of the power (and hence will not successfully energize).
- The reader’s antenna has to deliver enough power to energize the tag. The amount of energy delivered to the tag depends on a number of factors, including the following:
- Distance from the antenna
- Orientation between the antenna and the tag
- Ambient RF noise in the frequency band
- Environmental factors such as the presence of metal or water
- Sensitivity of the tag (i.e., the more sensitive the tag is, the more efficiently it will capture energy)
- The reader needs to be speaking the same air protocol as the tag. If the tag doesn’t recognize incoming data, it will not respond.
__________
3. Modulation is a technical term that refers to layering a data signal on top of a carrier wave.
Anticollision
One of the key value propositions of RFID technology is the ability to simultaneously read a large number of tags (e.g., for reading all of the boxes on a pallet while it passes through a loading door). Anticollision algorithms are used to allow multiple tags (and sometimes multiple readers) to share the same bandwidth, in a similar manner to how Ethernet employs a backoff algorithm to allow multiple computers to share the same physical network segment.
Antenna Considerations
RFID antennae come in two primary configurations: linear and circular.4 The choice of antenna type has a dramatic effect on read range and fidelity, specifically when using UHF technology, as shown in Table 1-2.
Readers connect to antennae in three primary ways: monostatic, bistatic, and multistatic. Different types of readers support different antenna connections (note that the supported antenna configuration is typically not a configurable option—i.e., you get whatever configuration is used by the reader you buy). The differences, advantages, and disadvantages to each are outlined in the following list:
__________
4. There are other types of antennae, such as directional, but these are typically used for niche and certain mobile applications.
Monostatic: The same antenna can both transmit (TX) and receive (RX). Only one antenna is required to read tags in a monostatic configuration (see Figure 1-9).
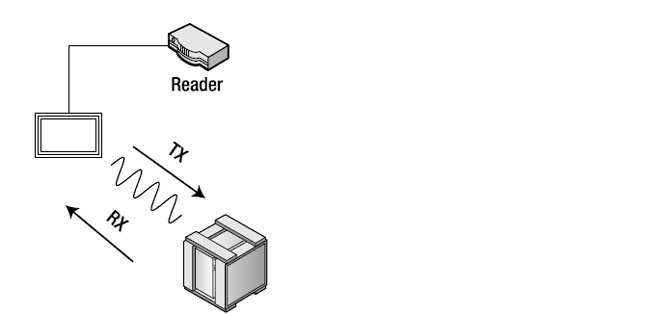
Figure 1-9. Monostatic: Single antenna for transmitting and receiving
Bistatic: The reader transmits on one antenna and receives on another. Paired antennae are required (see Figure 1-10).
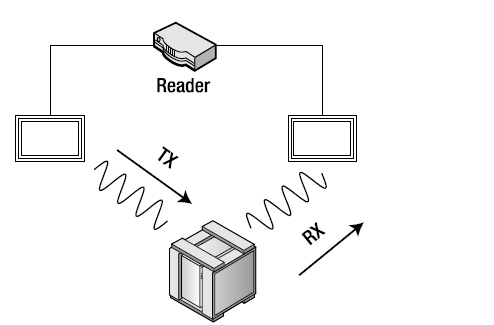
Figure 1-10. Bistatic: One antenna transmits and the other receives
Multistatic: Separate antennae are used for transmitting and receiving. The reader alternates between transmitting and receiving on each antenna (see Figure 1-11).
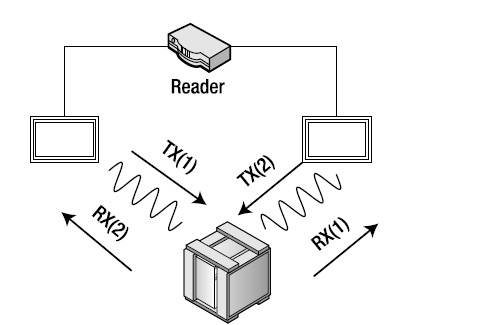
Figure 1-11. Multistatic: Paired antenna
Low-Frequency Readers
Operating at 125 KHz, LF readers and tags are the dominant technology in the livestock industry. A stable and mature technology, there is relatively little growth in this space as compared to the HF and UHF spaces. At the time of publication, there are no LF devices supported on the BizTalk RFID platform.
High-Frequency Readers
Operating at 13.56 MHz, HF readers and tags are heavily used in near-field and security-related operations, with a lot of traction in pharmacy applications. There are two primary air interface standards in HF: ISO 15693 and ISO 14443. The ISO 14443 standard has a higher data rate and implements a number of security-related features (such as requiring encryption keys to access data). Figure 1-12 shows an example of a mobile HF reader and an RFID tag.

Figure 1-12. Cathexis IDBlue HF RFID reader, PocketPC, and encapsulated HF RFID tag
Historically, HF technology has provided far superior performance in the presence of water and metal, though recent advances in UHF have closed the gap somewhat. HF tags also tend to be smaller (in some cases much smaller) than their UHF counterparts, and adapt well to hardened casings for challenging environments.
Even though defined standards exist and the technology is quite mature, there are a number of vendors who have implemented proprietary standards on top of the base ISO 15693 and ISO 14443 standards. When choosing technology in this space, it is very important to be clear about compatibility between the selected readers and tags.
When working with a reader vendor, always ask if a specific tag (model number) can be read by their reader. Compatibility is not guaranteed simply because both reader and tag are based on the ISO 15693 or ISO 14443 protocols.
Ultra–High Frequency Readers
The predominant technology in RFID, especially for supply chain applications, UHF operates around the 900 MHz frequency range (different geographic locations have different regulatory requirements for the allowable range and emitted power levels).
There have been several generations and standards around UHF, but the EPC Class 1 Generation 2 air interface and tag standard (described later in the “Electronic Product Code Class 1 Generation 2” section) has come to dominate the industry.
UHF tags are well suited for use in a supply chain scenario, with a solid combination of good read range and reasonable cost. Although earlier generations of UHF technology were somewhat unreliable in proximity to water or metal, recent advances have greatly improved performance for these scenarios. Figure 1-13 shows an example of a UHF reader.

Figure 1-13. Alien ALR-9650 UHF reader
This is not to say that these environments do not present serious deployment challenges, simply that it is no longer impossible to successfully deploy UHF for these types of applications.
Most UHF readers, in addition to the RFID and networking functionality, also include general purpose digital input/output (I/O) ports (often abbreviated GPIO or GPO/GPI). These allow the readers to directly interact with light stacks, air horns, and other I/O devices.
Active RFID Technology
The key differentiator between passive and active RFID is the power source. Whereas passive tags are powered by RF energy from readers, active tags have a built-in power source (usually a replaceable battery). Active tags are usually set to beacon; that is, at a fixed interval, they will broadcast their built-in ID code to be picked up by a series of readers. Due to the built-in power source, active tags can often be read hundreds of feet away.
Some active technology is deployed to implement a Real-Time Locating System (RTLS). In this scenario, information from several different read points is correlated to determine the physical location of a particular tag.
One other key aspect of active technology is the use of sensor tags that have built-in measurement devices. These can measure temperature, humidity, and physical shock (i.e., being dropped). Often deployed in food chain scenarios (i.e., the tag can report if the temperature in a reefer5 has risen above safe storage levels), they can be used to determine if foodstuffs have been safely transported.
Tag Memory: Reading and Writing
All RFID tags have some amount of onboard memory, varying greatly by vendor and technology type. Some tags (such as most HF tags and some newer UHF tags) ship from the factory with a hard-coded globally unique tag ID (similar to a MAC address). Other tags ship with a default value, which then has to be initialized. The process of initializing these values is commonly referred to as commissioning.
Newer tag technologies have improved the ability of vendors to place more memory storage on tags. However, these increased-memory tags carry a burden in production cost and sticker price. While high-memory tags (such as the 64 Kb UHF tag from Fujitsu) enable applications such as storing maintenance histories in aerospace applications, their price point is not suitable for supply chain scenarios.
Thus far, the primary focus of discussion has been on reading data from RFID tags. However, most readers can act as both an interrogator (reading data) and a programmer (writing data). The only key differences between them are the command set used and the amount of power and time required (writing data takes more power and time). Whereas most readers can also program tags, this function is typically performed by an RFID printer or applicator (described in the next section).
Printers and Applicators
So far, this chapter has been focused on readers, tags, and technology. However, the linchpin in any real-world RFID deployment is the commissioning of the RFID tags. This term refers to initializing the RFID tags with the appropriate identifying codes (i.e., in a UHF supply chain scenario, the EPCs), and any accompanying physical packaging (such as a printed label).
__________
5. In this context, a reefer refers to a refrigerated truck or rail container.
RFID printers combine the ability to print physical labels (usually combining textual information, logos, and bar codes) with encoding of data on the tag itself. Once the labels are printed, they are typically manually applied to the target asset.
For use in high-speed, automated scenarios, such as packaged goods rolling off of a conveyer belt in a manufacturing plant, applicators take the print engine and marry it with the ability to automatically apply labels to a given product. While carrying a high price tag, these applicators allow the deployment of RFID technology to scale up to handle high-volume scenarios.
Cutting Through the Hype
RFID technology has been the subject of intense hype, purporting that the technology could track the physical location of assets down to the centimeter in real time, read through bank vault doors, establish an Orwellian state, and allows users to perform wondrous feats of magic. Others have contended that the recent relative lack of buzz around RFID has sounded its death knell.
Neither of these extremes paints an accurate picture of the state of RFID technology. While still early in its adoption phase, RFID technology has reached a level of maturity that is quietly but surely gaining traction in the marketplace by delivering real-world return on investment.
The Science of the Feasible vs. the Art of the Possible
One product of the hype around RFID is the myth that it enables solutions that were not possible without it. This is again losing sight of the true value provided by enabling solutions with RFID. There is no feature provided by adding RFID to a solution that cannot be performed manually.
Dock workers can count boxes, maintenance personnel can fill out work orders, and destination codes can be read from luggage tags, all without the benefit of RFID. If these solutions are possible without RFID, where is the value driving the adoption of RFID?
The key value proposition for adding RFID technology is that it provides a pathway from the possible to the feasible by linking the physical world to the digital. It provides the necessary automation, speed, and accuracy required to bridge the gap between real-world assets and business systems that manage them.
Whereas manual processes provide the first step in bridging the digital divide, RFID technology offers the ability to enable a truly compelling degree of fidelity between the information systems driving your enterprise and your real-world assets. Take the example of receiving a pallet of goods in a warehouse. A dock worker can read all of the box labels and manually enter them into a database. However, the data capture is prone to errors (e.g., was that a box of blue razors or red razors?), and there is a gap between acquiring the data (looking at the boxes and writing the information down on a clipboard) and recording the information (typing it up). Bar code technology provides a first level of data fidelity (reliably identifying the type of product), but does not uniquely identify a specific box of products (which can prove vital in activities such as product recall).
Regardless of the specific technology involved, the fundamental activities remain the same—associating physical assets with digital information. However, the technology (be it eyeballs, bar codes, or RFID) plays a key role in the fidelity and availability of that association.
The Myth of the RFID Solution
Another product of the hype cycle that has surrounded RFID over the past several years has been the phrase “RFID solution,” with vendors far and wide touting their technology as a glorious panacea in the provision of such a solution. The phrase obscures the real value provided by RFID technology.
There is no such thing as an RFID problem. There are asset visibility issues, data fidelity problems, and logistical challenges, but there are no RFID problems. Wise use of RFID technology can play a critical role in overcoming these business challenges, but there is no inherent RFID problem that requires an RFID solution.
This insistence on terminology could be seen as mere semantics, but one of the key failings I have observed in the RFID industry over the past five years is the lack of focus on the challenges faced by the end user. Their problem is never “I need to improve read rates in my portal readers,” or “This particular tag doesn’t read well in proximity to my metal cylinders”— their problem is “I don’t know enough about where my assets are,” or “The information in my ERP system is out of touch with the real world.”
The most important aspect of any system is the value that it provides, not the technology used to enable it. This is why we prefer to refer to the reality of the RFID-enabled solution, rather than the myth of the RFID solution.
For example, picture yourself as a consultant working on implementing a solution at a warehouse for streamlining shipping and receiving activities. If the focus is on delivering an “RFID solution” and diving into readers, tags, and read rates, it’s easy to lose sight of the primary goal—driving efficiency in the overall business process. This process stretches all the way from the physical assets being shipped to the key performance indicators (KPIs) viewed at the annual shareholder’s meeting. The focus of any solution needs to be firmly centered around the business challenge—not aspects of the technology used to surmount those challenges.
Electronic Product Code Class 1 Generation 2
One of the most important developments in the RFID industry in recent times was the ratification and adoption of the Electronic Product Code (EPC) Class 1 Generation 2 (commonly referred to as EPC Gen 2, or just Gen 2) standard of the EPCglobal standards organization (www.epcglobalinc.org/home/). EPC Gen 2 is an air interface standard that defines how readers and tags communicate.
An industry standards body, EPCglobal has been the lead agency in defining RFID standards for the supply chain industry, based on UHF technology. EPCglobal’s mandate is to provide vendor-agnostic standards to provide a common baseline for RFID technology with a focus on industrial (as opposed to academic) requirements.
Designed to overcome some of the limitations of the first-generation EPC standard (known as EPC Gen 1), since its ratification in 2004, EPC Gen 2 has come to dominate the UHF landscape. Offering better performance, 96-bit tag IDs, increased user memory, and important security and privacy features, virtually every UHF reader and tag for sale today is based on EPC Gen 2.
EPCglobal has also led the development of several other standards, definitions, and data formats, such as the following:
Global trade identification number (GTIN): This numbering format provides globally unique identification of products (essentially a global UPC code).
Serialized GTIN (SGTIN): This is a GTIN paired with a serial number, providing unique identification of a specific asset.
Low Level Reader Protocol (LLRP): This is a wire protocol for controlling and receiving data from RFID readers. Several vendors provide native LLRP support in their readers (such as Impinj and Motorola). With BizTalk Server 2009, Microsoft has included support for LLRP readers out of the box.
Electronic Product Coding Information Services (EPCIS): This is a data interchange standard designed to enable enterprises to easily share and exchange EPC-related data both between internal systems and with external trading partners. Still in an early adoption phase, this standard has not seen widespread use.
Information about other EPCglobal standardization efforts and initiatives can be found on the EPCglobal web site (www.epcglobalinc.org/standards/).
The 96-bit EPC format contains a manufacturer code, an object type code, and a unique serial number for that object type. The manufacturer code (also known as the EPC manager number) is assigned by EPCglobal. There are several different ways of encoding data into the 96-bit field (defined by a header value), including SGTIN, Global Individual Asset Identifier (GIAI), and Serial Shipping Container Code (SSCC).
Closed-Loop vs. Open-Loop Systems
One of the common discussions in the RFID industry involves closed-loop vs. open-loop systems. A closed-loop system refers to one wherein a single organization owns the assets (i.e., no RFID-related information is shared with external partners). An example of this would be an IT department using RFID to track its laptops and servers.
In an open-loop system, the RFID infrastructure stretches across multiple organizations. An example of this would be a manufacturer of goods exchanging information and tracking goods through delivery to its distributor.
While much of the early hype focused around large-scale open-loop scenarios, closed-loop implementations (if often very large closed-loop implementations) are starting to take center stage as companies deploy RFID within their own walls to drive efficiency.
Applying RFID
So far, this chapter has been very technology-centric. However, as with any technology, the key question is why. What is the purpose of deploying this technology, what problem do we seek to address, and how is the investment justified?
While applicable across a (very) broad range of applications, all RFID technology (and bar codes) relates to correlating digital data with physical assets in an automated, reliable, scalable fashion. The following list describes some of the key industries and scenarios that are adopting RFID as a core technology:
Supply Chain: As perhaps the key industry behind the drive to adopt RFID, supply chain leverages RFID technology to automate tracking the movement of goods (at the pallet, case, and increasingly, item level) between the manufacturer, distribution centers, and retail outlets.
Retail: With increasing adoption and uptake, retail is becoming a key industry for RFID. With the increased automation provided by the technology, industry players are starting to use RFID to do the following:
- Streamline their cycle counts (i.e., counting items on the retail floor and in stock rooms).
- Manage out-of-stock events (if you don’t know you no longer have an item on the store floor, you don’t know that you need to put more out).
- Improve theft reduction. Systems such as Checkpoint have long been the dominant technology in terms of alerting stores to goods being stolen. However, that technology cannot distinguish between a single pair of jeans being waved in front of the sensor as a decoy, and someone else walking out with 20 pairs.
Manufacturing: This industry is seeing increased use of RFID to automate visibility into processes such as work-in-progress (where an item moves between different stages during manufacture).
The case studies interspersed throughout this book will dive into the innovative ways that many organizations are leveraging RFID technology to enable real-world solutions to business challenges.
Conclusion
RFID technology is the next step along the path of linking information systems with objects in the physical world. Based on radio waves rather than optics, it provides several advantages over bar codes in scenarios requiring high degrees of automation, reading without line of sight, and storage of dynamic data.
Successfully deploying RFID requires careful selection of appropriate technology from the available options (passive vs. active and HF vs. UHF). The intent of this chapter was to provide a high-level overview of some of the key aspects of RFID, and to provide context around integrating information from RFID readers and tags into software systems via Microsoft BizTalk RFID.
If you want to learn more about the physics side of RFID technology, the RFID Solutions Center in Dayton, Ohio (www.rfidsolutionscenter.com/) offers in-depth courses on understanding and implementing RFID.
CASE STUDY: WHAT RFID INFRASTRUCTURES LOOKED LIKE PRIOR TO BIZTALK RFID
Industry: Multiple.
Overview: To understand how BizTalk RFID improves processes, a quick introduction to infrastructures prior to its advent is in order. To begin with, if an organization wanted to capture event information from an RFID reader, it generally needed to work directly with the manufacturer of that device to build code to output the information. Then, once this information was made available, they would need to build “middleware” components to catch this information and route it to the appropriate destination. Manufacturers would often request their own proprietary databases to capture this information, and organizations with multiple device types would be left with a scattered and disconnected view of their data. Metrics would be across systems and databases, and would be complex and time-consuming to combine. Updates to readers and components would be difficult and splintered. Exception and error tracking were unique to each reader and each path. Essentially, a united approach to integrating RFID data into the enterprise was elusive, expensive, difficult, and rarely achieved.
Results: Organizations that have incorporated BizTalk RFID have seen a dramatic reduction in the complexity and maintenance of their RFID solutions. By its nature, BizTalk Server combined with BizTalk RFID provide for the integrated infrastructure that enables the capture of events from a multitude of readers and the publication of that information across the enterprise without extensive development of custom objects.