BizTalk RFID and BizTalk Server are applications completely separate from one another. Because of this, integrating with the core BizTalk Server engine (including the MessageBox, ports, orchestrations, and other components) from BizTalk RFID is similar to integrating with any other external system or application. There is generally a handoff that must occur between the two—due to BizTalk Server’s adapter framework, there are a large variety of messaging protocols available, including File, FTP, SQL, and WCF. Though similar to other integration efforts, there are a number of aspects to integrating between BizTalk Server and BizTalk RFID that are extremely easy to implement, especially when it comes to formatting data in XML and working with the Business Rules Engine (BRE). The primary topics covered in this chapter are as follows:
- Publishing data to BizTalk Server using MSMQ
- Publishing data to BizTalk Server using SQL Server
- Calling the BRE
- Calling a BizTalk RFID Web Service Proxy
The first two sections in this chapter will outline how to publish events to BizTalk Server using different event handlers; the first describes a custom approach and the second uses components that ship with the BizTalk RFID installation. The third section introduces the basics of working with the BRE, while the last section explains how certain web proxies are available for integration back to BizTalk RFID from BizTalk Server orchestrations. After reading these sections, you will have the building blocks necessary to be able to implement your own custom publishing scenarios.
Publishing Events to BizTalk Server
The intent of this discussion is to walk through the steps needed in publishing an event from BizTalk RFID to an orchestration in BizTalk Server using an MSMQ as the delivery mechanism. By walking through a full demonstration of the entire cycle, from the creation of an event handler and the configuration of a process, through the reception of the event in the BizTalk MessageBox and beyond, you will have a complete picture of how all of the pieces interact with one another. Where knowledge is lacking, you will be able to turn to other chapters in this book to get more information.
Publishing to BizTalk Server Using MSMQ
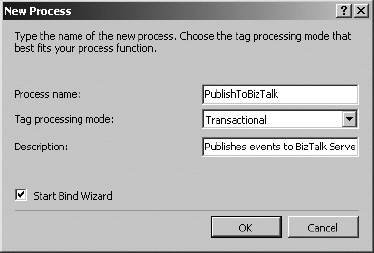
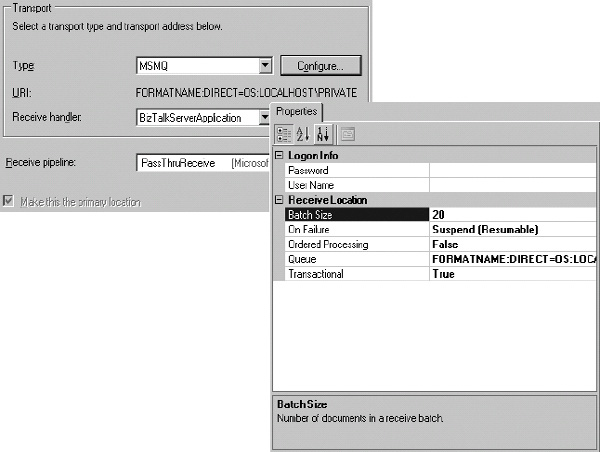
To introduce the process of publishing RFID information to BizTalk Server, a detailed example of working with MSMQ will be outlined. Using MSMQ as the publishing mechanism requires that a custom event handler be used. By working with a custom event handler, all aspects of configuring and developing the full process can be introduced. The full life cycle of the publication of the data using this approach is shown in Figure 8-1.
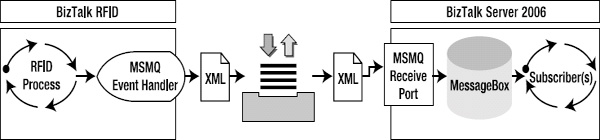
Figure 8-1. Publishing an event to BizTalk Server using MSMQ
The key ideas that will be discussed are
- How to create and deploy a custom event handler that posts to MSMQ
- How to configure and create all components needed in publishing events from BizTalk RFID to an MSMQ
- How to subscribe to the published event using an MSMQ adapter and orchestration
The MSMQ Event Handler
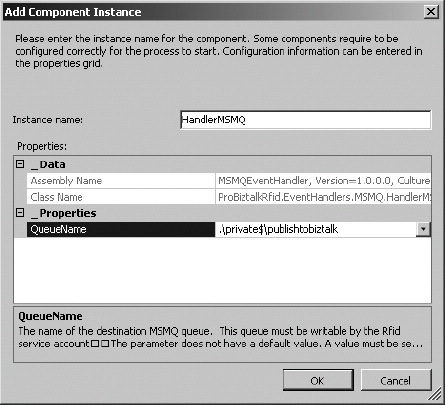
Event handlers were introduced and discussed in detail in Chapter 5. Here, we’ll discuss the specifics of how to create and use an MSMQ event handler. An MSMQ event handler must receive an event, transform it to XML, and post it to a queue. Using the MSMQ event handler that accompanies this book, the key factors of importance in the code are referencing the RFID libraries and serializing and posting the tag read event. It is also worth outlining how to debug an event handler in code.
![]() Note The full code for the MSMQ event handler can be found in the code download for the book, available from the Source Code section of the Apress web site (
Note The full code for the MSMQ event handler can be found in the code download for the book, available from the Source Code section of the Apress web site (www.apress.com/). The event handler code is located in the files associated with Chapter 8.
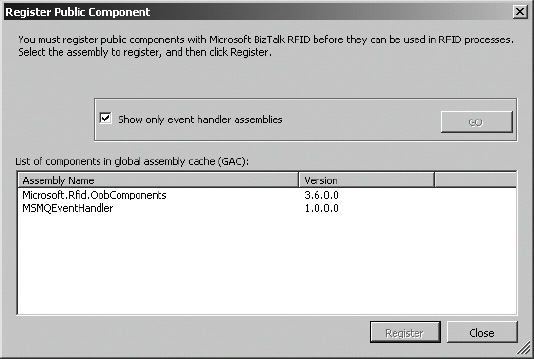
From a code perspective, event handlers are nothing more than class libraries that are deployed to the global assembly cache (GAC) (or local to the process via the privateprobing path) and called by BizTalk RFID processes. The steps in Exercise 8-1 outline how to use the MSMQ event handler to publish data to BizTalk Server. Before the exercise can be completed, the event handler must be deployed. Using the MSMQ event handler code that accompanies this book, take the following steps to enable it to be referenced by a BizTalk RFID process:
- Using Visual Studio, build the event handler assembly.
- Deploy the event handler assembly to the GAC. This can be done by opening the Microsoft .NET Configuration Framework console from Administrative Tools.
- If the assembly is being redeployed, restart the Microsoft BizTalk RFID service. This will ensure that the most recent assembly is executed when a process runs.
Referencing the BizTalk RFID Libraries
The MSMQ event handler, like all event handlers, inherits from the RfidEventHandlerBase class and requires several BizTalk RFID–specific assemblies to be referenced. These required assemblies are Microsoft.RFID.Design, Microsoft.RFID.SpiSDK, and Microsoft.RFID.Util, all of which are in the bin folder of the installation directory of Program FilesMicrosoft BizTalk RFID. Once these assemblies have been referenced, the using directive in the event handler should appear as shown in Listing 8-1.
Listing 8-1. Event Handler using Directive
using System;
using System.Collections.Generic;
using System.Text;
using Microsoft.SensorServices.Rfid;
using Microsoft.SensorServices.Rfid.Utilities;
using Microsoft.SensorServices.Rfid.Dspi;
using System.Messaging;
using System.Globalization;
using System.Xml;
using System.Runtime.Serialization;
Serializing and Posting the Event to MSMQ
At the heart of the MSMQ event handler is the conversion from an RFID event to an XML document, and the posting of that XML to MSMQ. The conversion is very simple, taking the data within the RFIDEventBase evt handler and placing it into an XML document, as shown in Listing 8-2.
Listing 8-2. Posting the Serialized Event
// the call to post to the transactional queue
destQ.Send(SerializeEvent(evt), MessageQueueTransactionType.Single);
// the conversion of the event to XML
private object SerializeEvent(RfidEventBase evt)
{
if (evt == null)
return null;
XmlDocument xml = new XmlDocument();
xml.LoadXml(evt.ToString());
return xml;
}
![]() Note Remember that an event handler can be debugged in Visual Studio by attaching it to the
Note Remember that an event handler can be debugged in Visual Studio by attaching it to the RfidService.exe service.
Exercise 8-1. Publishing to an MSMQ Using BizTalk RFID
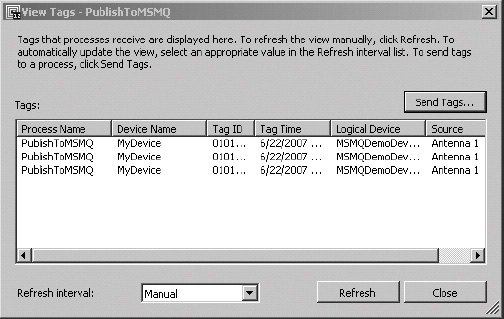
Once an event has been published to the queue, it can be consumed by BizTalk Server using an MSMQ adapter. The configuration of the adapter and the receive port is very simple, and is outlined in Exercise 8-2. The pipeline that is used is the PassThruReceive pipeline, which does no document validation on the incoming XML. This is fine for illustration, but it is important to note that BizTalk Server requires the use of schemas if any type of content-based routing is required. For example, if a field in the RFID event needs to be used in the logic within an orchestration, that field must be promoted. To promote the field, the schema must be defined and the XMLReceive pipeline must be used.
![]() Note There are several ways to create a schema (XSD) for use with the RFID event’s XML. The easiest approach would be to follow the steps in Exercise 8-2 and write out an instance of the XML to a file drop using the
Note There are several ways to create a schema (XSD) for use with the RFID event’s XML. The easiest approach would be to follow the steps in Exercise 8-2 and write out an instance of the XML to a file drop using the PassThru pipeline. Once a sample instance is available, a schema can be created using either the XSD.exe command-line tool or the Add Generated Items option from the Visual Studio BizTalk project.
Exercise 8-2. Subscribing to an MSMQ in BizTalk Server
Publishing to BizTalk Server Using SqlServerSink
The SqlServerSink event handler is deployed with the base installation of BizTalk RFID, and provides an interface to push RFID events to a SQL Server database. The event handler saves data to tables within the rfidsink database. This section will outline how to use the prepack-aged SqlServerSink event handler, and how to process messages from the rfidsink database using a SQL adapter in BizTalk Server.
![]() Note If the rfidsink database does not exist, the
Note If the rfidsink database does not exist, the SqlServerSink event handler will create it when an event is received. All connection information to the database is configured during the binding of the RFID process.
In the previous section, a process was created that published events to an MSMQ. In Exercise 8-3, the process will be extended to also publish events to SQL Server. The flow of this exercise is shown in Figure 8-11.
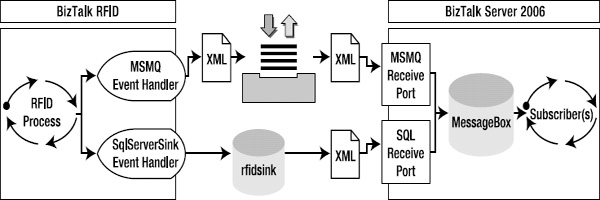
Figure 8-11. Extending the PublishToBizTalk RFID process with SQLServerSink
Exercise 8-3. Publishing an Event Using the SqlServerSink Event Handler
The GetAndDeleteEventsForBizTalk Stored Procedure
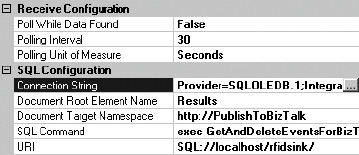
Included with the rfidsink database are a number of stored procedures. One of these stored procedures is designed to be used by a SQL adapter in BizTalk Server to retrieve the data from the TagEvents table and delete it once it has been successfully accessed. It is a very simple stored procedure, with two basic statements. The first statement is the selection of data based on the name of the RFID process, and the second statement is the deletion of all the records retrieved. The selection of data is retrieved in XML. The pertinent code for this stored procedure is shown in Listing 8-3.
Listing 8-3. Original GetAndDeleteEventsForBizTalk Query
select * from TagEvents WITH (UPDLOCK) where ProcessName = @ProcessName for xml auto
delete from TagEvents where ProcessName = @ProcessName
The use of this stored procedure in the retrieval of RFID data is outlined in Exercise 8-4. This exercise will demonstrate how to configure the SQL adapter to call the GetAndDeleteEventsForBizTalk stored procedure that is installed with the rfidsink database.
Exercise 8-4. Subscribing to the SqlServerSink Database Using a SQL Adapter
Extending the Flexibility of Event Retrieval
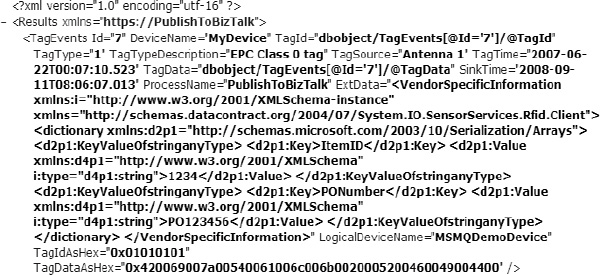
There are some obvious limitations to the out-of-the-box functionality of the GetAndDeleteEventsForBizTalk stored procedure, and no developer should feel forced to use this (or any other prepackaged component) if it does not fit the need. One of the limitations is in how the XML is structured when returned by the stored procedure. By using the For Xml Auto directive, SQL Server automatically structures the result set in a specific format. Notice how some of the attribute data contains information that is irrelevant or unusable. Especially prominent is the ExtData attribute (shown in Listing 8-4), which contains a string representation of the XML data that is stored in the database. All of the XML characters have been escaped, and the string is virtually worthless to components in BizTalk Server.
Listing 8-4. The Default ExtData Attribute with String Representation of XML
ExtData="<VendorSpecificInformation
xmlns:i="http://www.w3.org/2001/XMLSchema-instance"
xmlns="http://schemas.datacontract.org/2004/07/
System.IO.SensorServices.Rfid.Client">
<dictionary xmlns:d2p1="http://schemas.microsoft.com/2003/10/
Serialization/Arr
ays">
<d2p1:KeyValueOfstringanyType>
<d2p1:Key>ItemID</d2p1:Key>
<d2p1:Value
xmlns:d4p1="http://www.w3.org/2001/XMLSchema"
i:type="d4p1:string">1234</d2p1:Value>
</d2p1:KeyValueOfstringanyType>
<d2p1:KeyValueOfstringanyType>
<d2p1:Key>PONumber</d2p1:Key>
<d2p1:Value xmlns:d4p1="http://www.w3.org/2001/XMLSchema"
i:type="d4p1:string">PO123456</d2p1:Value>
</d2p1:KeyValueOfstringanyType>
</dictionary>
</VendorSpecificInformation>"
Far more useful than a string representation of the vendor information would be to enable BizTalk to receive this data in true XML, so that once it has been received, the information can be promoted, used in content-based routing, or used in orchestration and business rule logic. This can be done in several ways, but one approach is to alter how the XML is formed when it is first queried. Rather than the simplistic directive of For Xml Auto, a developer can give explicit instructions on how the data should be formatted.
To illustrate this, the GetAndDeleteEventsForBizTalk stored procedure will be modified. Modifying the SELECT statement with For Xml Explicit and ordering the results allows for much greater flexibility in the result set. The code shown in Listing 8-5 will produce the results shown in Figure 8-15. The output of the ExtData field is now formatted in true XML, and can be used in field promotion, content-based routing, and other core BizTalk Server activities.
Listing 8-5. Revised GetAndDeleteEventsForBizTalk Query
-- This is only a partial retrieval of all available fields in table
SELECT Id AS "Id"
,DeviceName AS "DeviceName"
,TagId AS "TagId"
,CAST(CAST(ExtData as nvarchar(max)) AS xml) As "ExtData"
FROM TagEvents
WITH (UPDLOCK)
WHERE ProcessName = @ProcessName
FOR XML PATH('TagEvent'), BINARY BASE64, TYPE
delete from TagEvents where ProcessName = @ProcessName
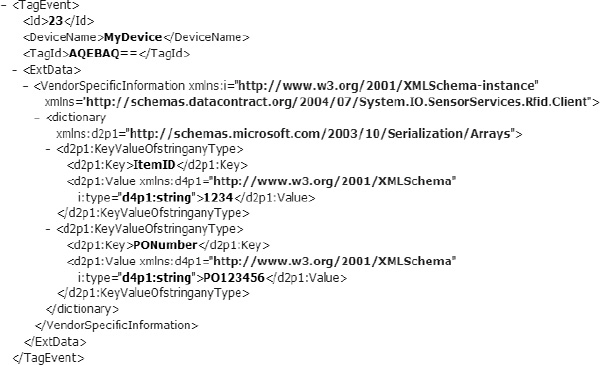
Figure 8-15. The revised results of GetAndDeleteEventsForBizTalk using explicit XML
Calling the BizTalk BRE
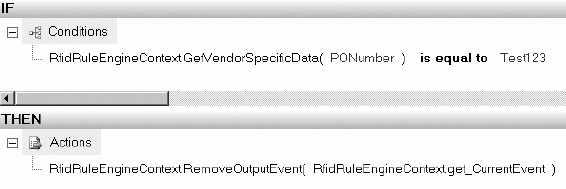
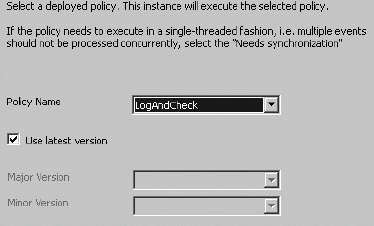
BizTalk RFID is designed to be able to interact directly with the BizTalk BRE through the use of an event handler. This event handler is fairly robust, in that it allows not only for the calling of policies, but for the creation of facts used in policy instantiation. This section will give a general overview of how to call a set of rules from the RulesEnginePolicyExecutor event handler.
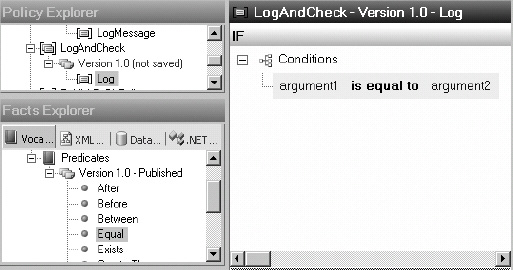
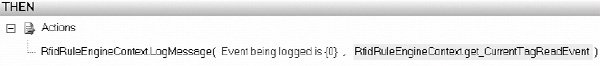
Logging Using the BRE
One of the methods on the RFIDRuleEngineContext class available within the BRE is LogMessage. This method allows for information to be logged. Log files are written for each device or process that is being logged from. For example, if the LogMessage method in a business rule policy is called from the PublishToBizTalk RFID process, information will be logged to %Program FilesMicrosoft BizTalk RFIDProcessesPublishToBizTalkPublishToBizTalk.log. Figure 8-16 illustrates the full architecture for logging, as demonstrated in Exercise 8-5.
![]() Note The last modified date does not always get updated when writing to log files. Make sure to open the file and look for the entries based on a timestamp.
Note The last modified date does not always get updated when writing to log files. Make sure to open the file and look for the entries based on a timestamp.
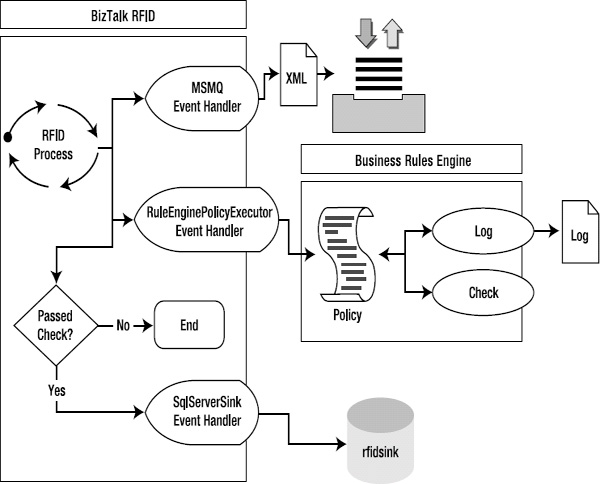
Figure 8-16. Extending the PublishToBizTalk RFID process with business rules
Calling a BizTalk RFID Web Service Proxy from an Orchestration
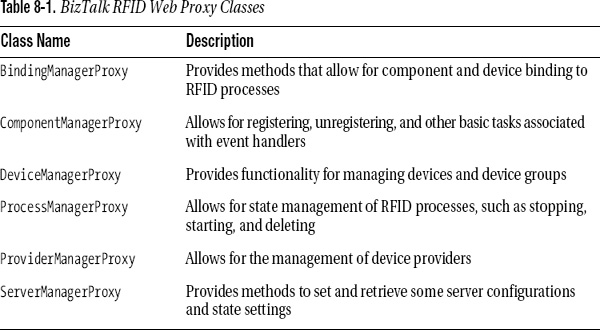
Packaged with BizTalk RFID is an assembly that allows for communication with the RFID server components. The assembly has a number of methods in it that allow for external applications to perform a wide variety of server-side functions, such as managing RFID processes, performing binding functions, setting the state of devices, and deploying event handlers. These methods can be called from any .NET application, and form the basis for the functionality behind BizTalk RFID Manager. Table 8-1 shows the proxy classes that are available, with a brief description of each.
Calling the majority of the classes and methods shown in Table 8-1 from an orchestration in BizTalk Server has limited real-world applicability. There is rarely a time that the deployment of an event handler, for example, will need to be automated. So, too, it is unlikely that the server will need to be configured in a workflow or devices will need to be bound or unbound. The ProcessManagerProxy class, however, has a number of methods that may be useful in workflow automation and orchestration development. The methods in this class allow for such functionality as starting, stopping, and instantiating BizTalk RFID processes. Several of the most important methods are described in Table 8-2. All of these should look extremely familiar to anyone who has used RFID Manager to work with processes.
One example of the use of the ProcessManagerProxy methods in an orchestration would be the automation of the state of RFID processes. For example, assume that it was discovered that processes were stopping unexpectedly due to connectivity issues or faulty components, and that the desired solution was to ensure that the processes were always restarted. To solve this, an orchestration could be built and deployed that would execute on a timed basis and call a .NET assembly to check the status of one or more processes. If it was found that a process was not started, the StartProcess method could be called. This would eliminate the need for manual actions to be taken by an administrator and ensure that the processes were constantly restarted. The orchestration would look similar to that shown in Figure 8-22.
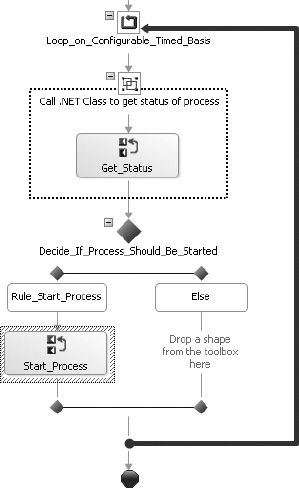
Figure 8-22. An orchestration loop to automate process state
To illustrate how a proxy method is called from an orchestration, refer to Exercise 8-6. Since the proxies are all in .NET assemblies, all that is required is to create a variable of the proxy class type and to call the method from an expression shape. Remember you can most easily call complex types associated with these proxy methods (such as arrays) through the use of a referenced .NET helper class, rather than directly from an orchestration. The .NET helper assembly can then be referenced by the orchestration.
Exercise 8-6. Calling a BizTalk RFID Web Service Proxy
Conclusion
Using BizTalk Server to process and route information from BizTalk RFID to external systems and applications has a number of benefits. These include prebuilt transmission protocols (in the form of adapters); robust functionality for workflow process (in the form of orchestrations); a configurable BRE; and extensive error handling, tracking, and reporting (through the BizTalk Administration Console and other tools). Rather than having to write complex code into RFID components or middle-tier objects, BizTalk Server enables developers to rapidly develop and deploy architectures to support data transmission and mapping. Given the variety of uses and advantages of BizTalk Server, it is important that you be familiar with a number of aspects of incorporating it into your BizTalk RFID solutions.
CASE STUDY: REDUCING THEFT AND CARELESSNESS
BY TRACKING STORAGE COMPONENTS
Industry: Financial.
Overview: A solution using both BizTalk RFID and BizTalk Server has been implemented within the banking industry to reduce the theft and misplacement of hardware. An RFID tag is affixed to each hard drive within an organization. An RFID reader is placed at all entrances and exits of the building. As hard drives pass by the readers, they are tracked, with information posted to orchestrations that perform business rules. Rules include whether or not a drive is allowed to be transported (such as within an employee’s laptop) and whether drives have been absent too long (e.g., a drive may have been out of the office for several weeks). If a business rule has been violated, the orchestration notifies the appropriate administrative party. Administrators can monitor reports that show all movement and rule violations of all tracked components.
Results: There is a sizeable decrease in the number of lost or stolen drives. While RFID tags could be removed, the knowledge that components are being tracked reduces instances of carelessness and theft.