The patterns in this chapter are fundamental to defining a service-oriented architectural model with an emphasis on service inventory architecture. The design problems solved by these patterns help structure the architecture for the sole purpose of establishing a flexible and agile environment suitable for solution logic designed in accordance with service-orientation.
This chapter is structured so that the patterns are organized into a proposed application sequence. It is important to acknowledge that you are not required to follow this recommended sequence and that these patterns exist individually as part of the master pattern language provided by the book as a whole. You can therefore consider this chapter a “mini” structured pattern language that is part of a greater open-ended pattern language. As such, these patterns can be combined with patterns from other chapters into a variety of creative sequences.
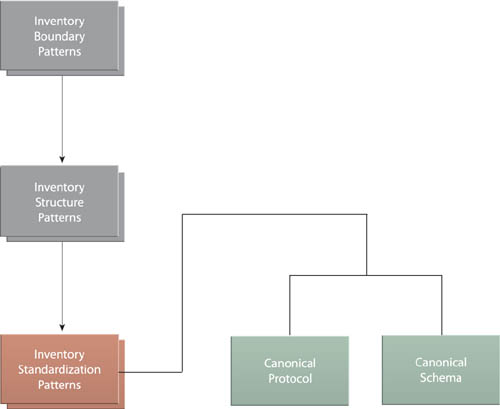
As shown in Figure 6.1, the upcoming patterns are organized into the following groups:
1. Inventory Boundary Patterns– The scope of an architecture is defined by identifying the boundary of its corresponding service inventory and related characteristics.
2. Inventory Structure Patterns– The high-level structure and the overall complexion of the inventory itself is determined, which further influences the requirements that the eventual architecture implementation will need to fulfill.
3. Inventory Standardization Patterns– Key inventory-wide design standards are established to ensure a baseline level of service interoperability.
The design patterns within a given group are explained at the beginning of each of the upcoming sections.
Note
Throughout this chapter you’ll notice references to “agnostic” services and logic. If this term is new to you, skip ahead to the Agnostic Logic and Non-Agnostic Logic section at the beginning of Chapter 7 for an explanation. Also if you are not familiar with the term “service inventory,” be sure to read the definition provided in Chapter 3.
It is interesting to note that the four fundamental design characteristics of a service-oriented architecture (established back in Chapter 4) are closely related to the application of the design patterns in this chapter, as shown in Table 6.1. The nature of these relationships will become clear when reading the pattern descriptions.
Table 6.1 How fundamental inventory design patterns (left) relate to the required base characteristics (top) of service-oriented architecture.

As mentioned earlier, this chapter provides a structured collection of patterns provided in a recommended application sequence. Chapter 11 provides a similarly organized set of patterns arranged in a suggested application sequence focused solely on service design. The fact that this chapter precedes Chapter 11 is not meant to indicate that the process established by this pattern application sequence should be completed prior to service design. Inventory design patterns are simply covered first in this book because they tend to be broader and coarser-grained in nature than those specific to service design.
In most modern SOA methodologies, iterative modeling and design processes are used to allow the design of an inventory architecture to be accomplished concurrently with service modeling and identification so that the definition of one can lead to the refinement of the other. It is completely up to you as to how these pattern groups are used in incorporated into project delivery cycles.
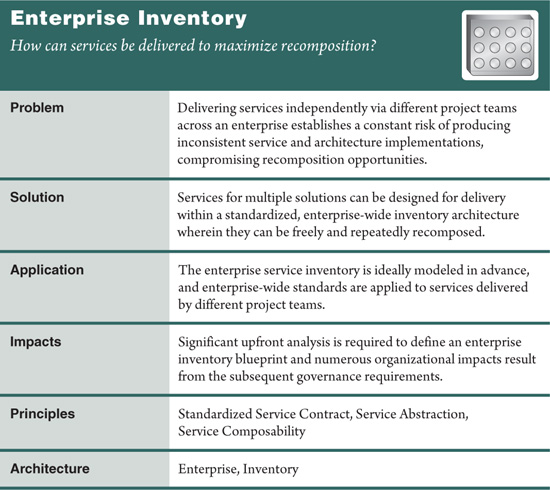
As explained in Chapters 3 and 4, a service inventory represents an independently standardized and governed collection of related services, and each such inventory is supported by its own, individual service-oriented technology architecture implementation. Therefore, a fundamental step in the creation of any service inventory is the definition of its scope in relation to the enterprise within which it resides.
The design patterns Enterprise Inventory (116) and Domain Inventory (123) shown in Figure 6.2 establish the boundary of the service inventory. Only one of these two patterns can be applied within a given IT enterprise.
Throughout an enterprise, services can be delivered as part of various on-going development projects. Because each project has its own priorities and goals, services and supporting implementation architectures can easily be designed in isolation, optimized to fulfill tactical requirements.
The result is a collection of potentially disparate service clusters and technology architectures. The differences in these implementation environments can lead to serious problems when attempting to compose services into new configurations that span the initial architectural boundaries (Figure 6.3).
Figure 6.3 All services are built with the same vendor platform, but they are delivered via separate projects without taking into account a common architectural boundary. The end-result is an environment reminiscent of a silo-based enterprise that relies on constant integration effort to enable interoperability.

A service-oriented enterprise architecture is established to form the basis for a single enterprise service inventory. Services delivered as part of any project are designed specifically for implementation within the enterprise inventory’s supporting architecture, guaranteeing wide-spread standardization and intrinsic interoperability.
If the planned enterprise service inventory is significant in scope, then the organization needs to ensure it is capable of carrying out the corresponding SOA adoption effort.
Various factors come into play, each of which may introduce the need to reduce the scope or explore an alternative approach:
• the maturity of available technology for the planned services (especially for services being positioned as highly reusable enterprise resources)
• the maturity of governance technology platforms required to manage and evolve the service inventory as it is being built and after it is in place
• the order of magnitude associated with the amount of change and disruption brought on by the adoption
• the amount of legacy environments that are expected to constrain service encapsulation
• the financial resources required to carry out the adoption
• cultural and political obstacles that may arise as a result of the proposed changes and the required standardization effort
Therefore, this pattern is recommended for the following types of environments:
• small-to-medium-sized organizations with sufficient resources
• medium-to-large-sized organizations with highly controlled IT environments, a history of enterprise-wide standardization, or with the cultural flexibility to successfully adopt the required level of standardization
• medium-to-large-sized organizations that have the resources to build an enterprise service inventory while concurrently operating and maintaining their existing legacy systems
• new organizations that have no legacy systems and no IT history (and can therefore build an IT enterprise with a clean slate)
An enterprise service inventory does not need to encompass an entire enterprise. The purpose of this pattern is to establish a single service inventory with a scope sufficiently meaningful to warrant its creation.
Furthermore, the application of this pattern does not result in the creation of physical services. It establishes the concept of a service inventory on an enterprise-wide scale, for which services are conceptually defined through a planning and analysis effort that ties into the definition of a service inventory blueprint. To accomplish all of this typically requires a top-down analysis project that is completed by iteratively carrying out the service-oriented analysis and service modeling processes.
The following steps provide a suggested process:
1. Carry out planning and analysis stages to determine a preliminary scope for the service inventory that appears to be manageable based on the previously listed factors.
2. Collect all of the necessary enterprise business specifications that document business models and requirements that fall within the scope of the planned inventory (as well as those that are enterprise-wide). These specifications can include business entity models, logical data models, ontologies, taxonomies, business process definitions, and numerous other information and business architecture documents.
3. Using the enterprise-wide business models collected in Step 2, apply Entity Abstraction (175) and Process Abstraction (182) to establish a base set of business service layers.
4. Carry out the service-oriented analysis process iteratively by decomposing business process definitions that fall within the scope of the planned inventory. This results in the definition of service candidates that are continually refined. (See SOAMethodology.com for an example of a top-down process that iterates through the service-oriented analysis stage.)
Note
Several of the previously listed steps also apply to the upcoming pattern Domain Inventory (123). The primary distinctions are scope and quantity. The ultimate goal of Enterprise Inventory is to establish a single service inventory that spans as much of the IT enterprise as possible, whereas Domain Inventory (123) allows for multiple (usually smaller) inventories to exist within an enterprise.
To achieve unity across an enterprise-wide service inventory, a large (and sometimes monumental) amount of top-down analysis may be required so that service candidates can be modeled and aligned with each other prior to their actual delivery. This can lead to an expensive and time-consuming up-front analysis project.
Alternative methodologies can be employed to phase in the delivery of services with less initial analysis. One example is the “meet-in-the-middle” approach that allows for analysis to occur on an on-going basis while services are built and implemented. There is then a commitment to “re-align” the services at a later point after the analysis produces a mature enterprise-wide inventory blueprint. Although a proven strategy that overcomes the time-burden of top-down approaches, this method can introduce additional complexities and increased expense.
Common issues that challenge the creation of an enterprise service inventory are documented in the Problem section of the pattern description for Domain Inventory (123) because this pattern provides an alternative approach that directly addresses concerns associated with Enterprise Inventory.
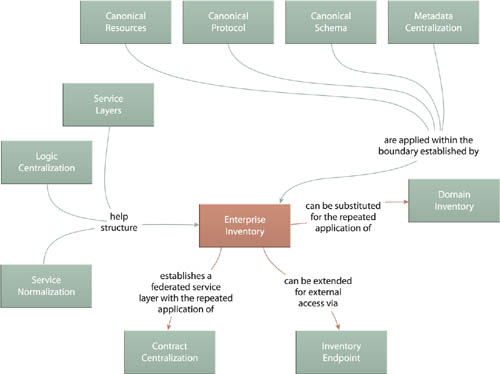
Enterprise Inventory establishes an architectural boundary with a physical structure that is further subject to the application of a series of additional inventory-related patterns. Inventory Endpoint (260) in particular can complement this pattern by providing standardized access to consumers outside the enterprise. Domain Inventory (123) provides the primary alternative to this pattern.
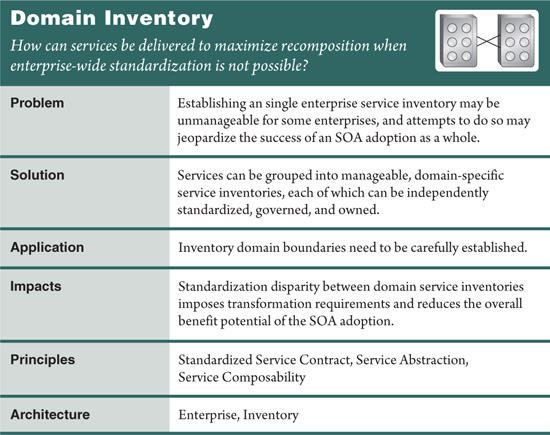
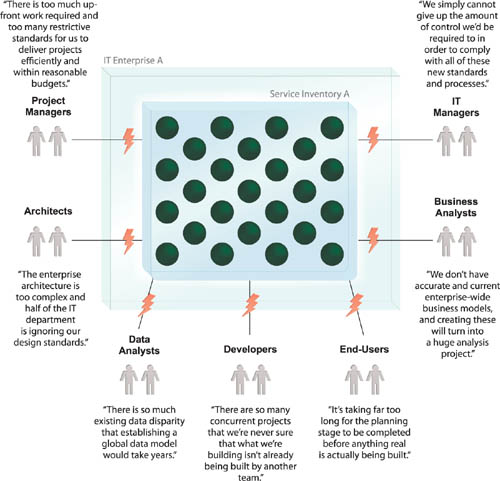
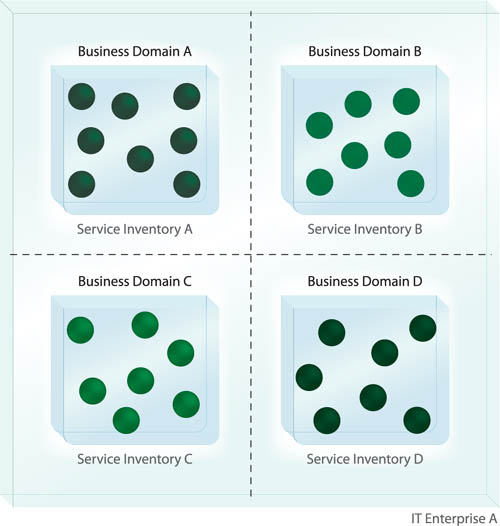
In larger environments it can be impractical or even unrealistic to define and maintain a single service inventory for an entire enterprise. Standardization and governance issues can raise numerous concerns, most of which tend to be organizational in nature (Figure 6.7).
Note
Several of the issues raised in Figure 6.7 relate to the governance of SOA projects and implementations. Organizational and technology-related governance topics (and patterns) will be covered separately in the upcoming title SOA Governance as part of this book series.
Multiple service inventories are created for one enterprise. The scope of each represents a well-defined enterprise domain. Within domains, service inventories are standardized and governed independently (Figure 6.8).
Whether or not to apply this pattern is tied to the question of whether an enterprise service inventory is feasible within a given environment. Many factors (most of which are specific to the organization) weigh in on this decision point. However, some general guidelines are available.
For example, domain service inventories are an appropriate alternative when any of the following supporting factors exist:
• The implementation environment is a large enterprise without strong executive sponsorship and wide-spread support for the SOA initiative.
• The enterprise does not have an established, global data models and creating them is considered unrealistic.
• The organization is incapable of changing the complexion of its IT departments in support of a more centralized governance model.
The application of this pattern can bypass these obstacles and accelerate the transition toward service-orientation in that an enterprise-level migration can be delivered in phases that each result in the creation of a manageable collection of services. For many organizations, this pattern provides the only realistic option for adopting SOA.
The key to creating effective domain inventories is to clearly define the domains in advance, thereby establishing a sub-divided view of an enterprise prior to building any one inventory.
Organizations will often have options as to how the domains are defined. Here are some common examples:
• Organizational business areas represented by specific IT departments or groups. These business areas would then establish the basis for business domains.
• Organizational business domains not represented by separate IT departments or groups. These domains can still form the basis of service inventory boundaries but require cooperation across IT departments.
• Remote offices, each with its own IT department and development center. This can result in geographical-based domains.
Ideally, domain inventories correspond to enterprise business domains, such as those based on an organization’s lines of business. This allows each inventory to be tuned to and evolve with its corresponding set of business models in full support of establishing the business-driven architecture characteristic.
Multi-domain service inventory implementations make some impositions, in that they allow for individual inventories to be standardized differently. This generally results in the need to introduce targeted transformation for cross-domain interoperability as part of the overall enterprise architecture.
The ultimate benefits associated with achieving a unified and federated enterprise service-oriented architecture are scaled back to whatever extent domain inventories are created.
Transformation requirements that emerge to enable cross-domain data exchange impact the development and design effort of corresponding service compositions and also add performance overhead to their runtime execution. Furthermore, the independence by which each inventory can be built and evolved will often lead to the creation of redundant services across domains.
The same design patterns that structure an enterprise inventory will end up structuring an inventory defined via Domain Inventory (only the scope will be smaller). However, unlike Enterprise Inventory (116), the application of this pattern will generally result in the need for transformation patterns, such as Protocol Bridging (687) and Data Model Transformation (671). Inventory Endpoint (260) will also play a more prominent role to facilitate cross-inventory communication.
Figure 6.9 Domain Inventory shares many of the same relationships as Enterprise Inventory (116) but introduces new requirements that can be fulfilled by additional patterns more specific to a domain-based environment.

Once the inventory boundary is determined, the complexion and organization of the inventory itself needs to be determined on a fundamental level. The next set of patterns helps define the underlying inventory structure by establishing basic service boundaries and classifications.
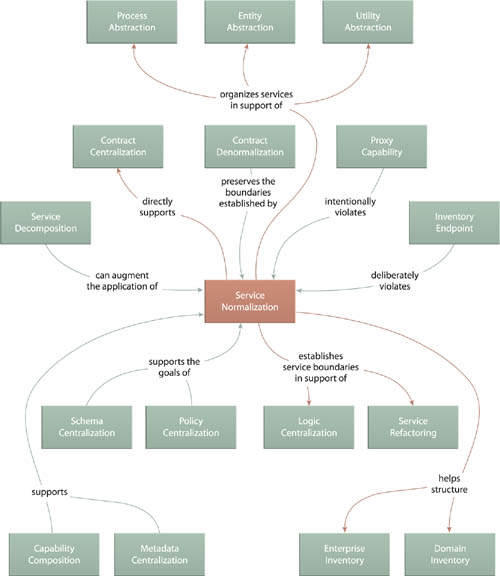
As shown in Figure 6.11, Service Normalization (131) and Logic Centralization (136) influence the inventory structure by requiring that future services be in alignment with each other and that future agnostic services in particular be positioned as the sole endpoint for the logic they represent.
There is no proposed sequence within this pattern group. These patterns simply establish modeling and design parameters on an inventory-wide basis.
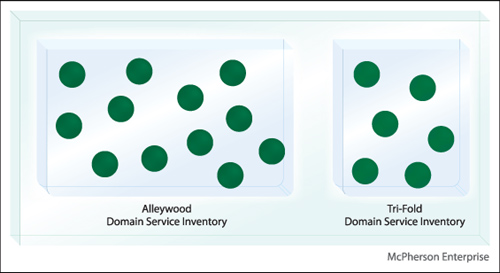
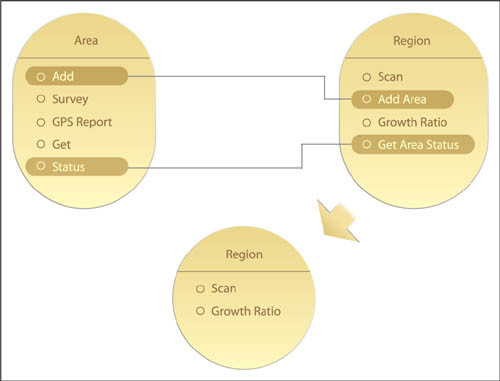
The boundary of a service is defined by its functional context and the collective boundaries of its capabilities. Even within a pre-defined inventory boundary, when services are delivered by multiple project teams there is a risk that some will provide functionality that will overlap with others.
This leads to a denormalization of the inventory (Figure 6.12), which can cause several problems, such as:
• an inability to establish service capabilities as the official endpoints for bodies of agnostic logic
• a more convoluted architecture wherein services with overlapping functionality can become out of synch, providing the same functions in different ways
Services are collectively modeled before their individual physical contracts are created. This provides the opportunity for each service boundary to be planned out so as to ensure that it does not overlap with other services. The result is a service inventory with a higher degree of functional normalization (Figure 6.13).
The goals of this pattern are best realized by pursuing service-level autonomy (as associated with the Service Autonomy design principle) during the service modeling stage.
Common steps include:
1. Identifying and decomposing a business process definition that pertains to the inventory boundary.
2. Allocating the individual parts of the process into appropriate new or existing conceptual service candidates.
3. Validating that no two service boundaries overlap.
These steps are part of a greater service modeling process that takes other modeling considerations into account. To fully apply Service Normalization requires that this process be carried out iteratively, once for every business process that is associated with the scope of the service inventory. Through these iterations, the functional contexts and boundaries of service candidates are repeatedly refined and validated.
The end-result is a service inventory blueprint that provides a normalized view of all services within the inventory. This approach is typically part of a top-down delivery effort.
Note
The service modeling process explained in Service-Oriented Architecture: Concepts, Technology, and Design contains steps that address normalization issues. However, because larger modeling efforts may result in this process being carried out concurrently by different teams, a subsequent inventory blueprint-wide review is always recommended. Other approaches for achieving the goals of Service Normalization may also exist as part of different methodologies.
The guarantee of inventory-wide normalization requires that all services be conceptually modeled prior to delivery, as part of an inventory service blueprint specification. Depending on the scope of the planned inventory, this can result in a separate analysis project that needs to be completed before any service can actually be built.
Continual governance effort is further required to ensure that services maintain normalization throughout the inventory as they are revised and evolved over time.
Service Normalization lays the foundation for Contract Centralization (409) by ensuring that no two services share the same functionality. This allows contracts to be positioned as the sole entry point into service logic and further enables those services to be independently evolved, as per Service Refactoring (484). Schema Centralization (200) and Policy Centralization (207) further support this pattern by avoiding contract-related redundancy.
To successfully preserve a normalized inventory requires the consistent enforcement of Logic Centralization (136), making these two patterns very closely related.
Contract Denormalization (414) is referred to in Figure 6.14 only to indicate that, despite its name, it does not interfere with the goals of this pattern. As explained in Chapter 16, Proxy Capability (497) must violate this pattern out of necessity when services require post implementation decomposition.
As we established in earlier chapters, reuse represents a key characteristic that typically needs to be realized on a broad scale for some of the more strategic goals associated with service-orientation to be attained. However, even if well-designed agnostic services are consistently delivered into a service inventory, it does not guarantee that project teams building new solutions will use them.
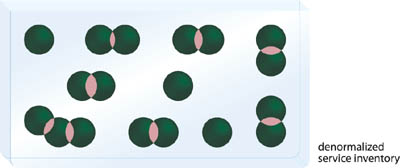
For various reasons, it may be easier, simpler, or just more practical to avoid involving reusable services in order to concentrate on the fulfillment of short-term, tactical delivery goals. This approach may be convenient, but it eventually results in a denormalized service inventory where functional redundancy is common (Figure 6.16).
To pursue the strategic goals associated with service reuse, the characteristic of reuse itself must form the basis of supporting internal design standards. The foremost of these standards needs to dictate that services classified as agnostic must become a primary (or even sole) means by which the logic they represent is accessed. This forms the basis for Logic Centralization, as depicted in Figure 6.17. The level to which the centralization of logic succeeds as an enterprise-wide standard determines the extent to which the repeated ROI of services can be realized.
When services are built by different project teams, there is always the risk that one team will develop a service with new logic that exists as part of an already-implemented agnostic service.
Common reasons for this are:
• The project team is not aware of the agnostic service’s existence or capabilities because the service is not sufficiently discoverable or descriptive.
• The project team refuses to use the existing agnostic service because it is considered burdensome to do so.
While the former scenario can be avoided through the application of Metadata Centralization (280), the latter is where an inventory-wide design standard is required. In fact, the manner in which this pattern is applied is through the creation and enforcement of a standard that requires that services act as the sole entry point for the functional boundaries they represent within a given inventory.
This type of standard essentially dictates that agnostic services must always be used as intended, even if they do not yet possess all required functions. For example, if a new capability needed by a project team clearly falls within the boundary of an existing service, the corresponding functionality needs to be added to that service instead of ending up elsewhere (Figure 6.18).
As straightforward as Logic Centralization may sound, it can be difficult to achieve, especially with broadly scoped service inventories. For larger organizations working toward an enterprise service inventory attaining a state where all development project teams agree to not build redundant logic and instead use existing services may seem like an unattainable ideal.
Introducing Logic Centralization into an organization that does not have a history of fostering reuse or using design standards in general will almost always raise cultural issues with people and IT departments affected by service delivery projects.
For example:
• Existing project plans and processes are impacted by requiring the involvement of reusable services as part of their development projects.
• There may be resistance to giving up control of solution designs if teams are forced to include existing agnostic services or produce new services that need to be reusable.
These concerns need to be addressed prior to the delivery of agnostic services to avoid compromising the strategic value of a service inventory. If only partial support for the delivery and usage of reusable services is received within an IT division, the risk of ending up with a denormalized and potentially convoluted inventory architecture is significant.
Logic Centralization is a core design pattern very much focused on centralizing agnostic logic, which is why it is commonly associated with Entity Abstraction (175) and Utility Abstraction (168) and also why its application is influenced by Agnostic Context (312) and Agnostic Capability (324).
Whereas Service Normalization (131) primarily solves a service modeling problem, Logic Centralization addresses service usage concerns. In a way, Logic Centralization helps attain the goals of Service Normalization (131).
Contract Centralization (409) also has a very close relationship with Logic Centralization because together they position official services that can only be accessed via official entry points (contracts), which is fundamental to establishing a healthy federated endpoint layer.
There are also numerous peripheral relationships with additional specialized patterns, such as Metadata Centralization (280), which supports the discovery of services to which Logic Centralization has been applied, and Redundant Implementation (345), which supports the scalability demands that tend to fall upon centralized services. Additional examples are shown at the top and bottom of Figure 6.19.
Perhaps its most important relationship is with Capability Composition (521), a pattern that introduces the fundamental rule that logic outside of a service’s boundary must be composed.
Note
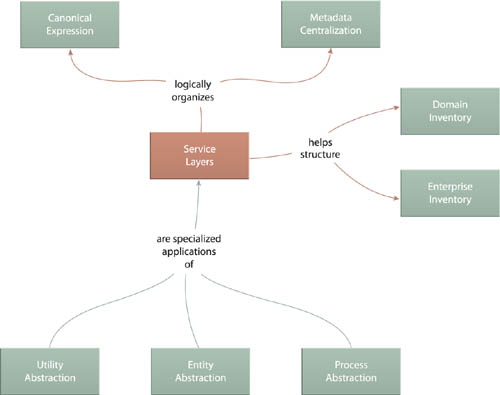
This pattern should not be confused with Service Layer (Fowler, Stafford). Whereas the goal of Service Layers is to establish logical domains represented by collections of related services, the application of Service Layer results in an externally facing interface layer for a specific application.
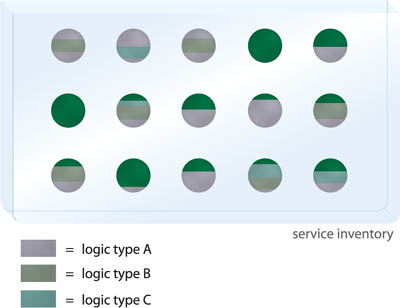
Within a typical service inventory there will tend to be services that have similar functional contexts. However, these services may be designed and implemented differently, depending on the nature of the delivery project. This leads to a missed opportunity to establish consistency in how service boundaries are defined and in the nature of the logic they encapsulate. The result is an inventory of services that cannot easily (or cleanly) be partitioned into groups for the purpose of sub-domain based abstraction and governance (Figure 6.20).
A service inventory architecture can formally establish classification profiles to represent common types of services within a given inventory. These profiles are referred to as service models, each of which represents a unique set of design characteristics associated with a well defined service category. Service models form the basis for this pattern in that a collection of services that conform to one model establish a logical architectural layer of related functionality (Figure 6.21).
Figure 6.21 Related services are designed according to service models, thereby establishing logical service layers. In this case, the service inventory is structured with three service layers that correspond to the three abstraction patterns described in Chapter 7. (Note the pipe symbol is used to represent a service layer in this book.)

Applying Service Layers ensures that services matching common types are designed with the same fundamental characteristics, as derived from common service models. These services can form logical domains within the inventory, which can be evolved and governed as groups (Figure 6.22).
Note
Because service layers are closely related to service models, this pattern could have easily been called Service Models instead. The term “Service Layers” was chosen because it represents the end-result of repeatedly applying service models to service inventories.
Layers of services are generally defined prior to the implementation of a service inventory. During the modeling of a service inventory blueprint, the functional nature of planned service candidates helps determine what layers are most suitable. Therefore, any given service inventory can have different layers. The only rule is that there be a minimum of two.
The most fundamental layers are:
• a layer that represents single-purpose (non-agnostic) logic
• a layer that represents multi-purpose (agnostic) logic
By abstracting non-agnostic logic into one part of an inventory, agnostic logic can be defined and evolved in support of fostering reusability.
While there is always the option of customizing service layers, the safest starting point is to base them on common industry service models. These fundamental models have been proven to solve known design problems and are further explored in Chapter 7 as part of the descriptions for Process Abstraction (182), Entity Abstraction (175), and Utility Abstraction (168). As illustrated in Figure 6.23, service compositions tend to naturally span service layers established by common service models.
Determining what service models should or shouldn’t be used within a service inventory requires a familiarity with the types of logic that reside within the inventory’s boundary. Therefore, service layers often evolve out of repeated iterations of the service-oriented analysis phase and sometimes even require revisions to previously modeled service candidates. As a result, their use can increase the time and effort required to define a service inventory blueprint.
An exception to this is when service models have already been established as enterprise design standards, in which case they can be used as the basis for planned service layers right from the start.
Furthermore, once layers have been chosen, they become inventory-wide design standards in that every subsequently defined service needs to fit into one of the established service layers. After services have been built according to the underlying service models, it can be very difficult to change the structure of the established layers without disrupting the service inventory.
Service Layers introduces logical separation into inventory boundaries and therefore naturally builds upon Enterprise Inventory (116) and Domain Inventory (123). Both Service Normalization (131) and Logic Centralization (136) help establish firm boundaries for individual services that allow for them to be organized into layers in support of this pattern.
As shown in Figure 6.24 and explored throughout Chapter 7, this pattern forms the basis of Utility Abstraction (168), Entity Abstraction (175), and Process Abstraction (182).
Note
Service Layers is at the root of the abstraction patterns that are core to the compound pattern Three-Layer Inventory (715).
Design patterns and design standards were defined as two separate but related parts of a typical design framework back in Chapter 4. A design pattern provides a proven solution to a common design problem, and a design standard is a mandatory convention applied across multiple systems. Whereas a design pattern is industry-recognized, a design standard is internal and specific to an IT enterprise.
Even though they are distinct, design standards are a lot like design patterns. In fact, design standards can be seen as “pre-solving” specific design issues in order to ensure consistent system designs. It is therefore not uncommon for a design pattern to become the basis of design standard, which is essentially what this group of patterns is all about.
These next patterns (Figure 6.25) do not just propose possible solutions to common problems, but they propose that to solve this set of specific problems, the solutions themselves must become actual design standards.
Though there is no particular order in which these patterns need to be applied, it is sometimes necessary for Canonical Protocol to be established prior to the Canonical Schema because the communications technology represents the fundamental medium by which data (and associated data models) are delivered and processed.
Each service exists as a standalone software program. When these programs need to exchange information, they have to form a connection using a communications technology. When programs are designed to use different communications technologies, they are incompatible and cannot exchange information without involving a separate program that can translate one communications technology to another, as per Protocol Bridging (687).
Building services with different implementation technologies is not uncommon, but allowing services based on different communication technologies to exist within the same architecture can result in limitations. For example, groups of services based on the same communication framework are likely to be delivered as part of the same project. The day any of these services needs to be pulled into a new composition consisting of services delivered by a different project (and using different communication protocols), incompatibility issues could make their connectivity and reuse challenging and perhaps impossible (Figure 6.26).
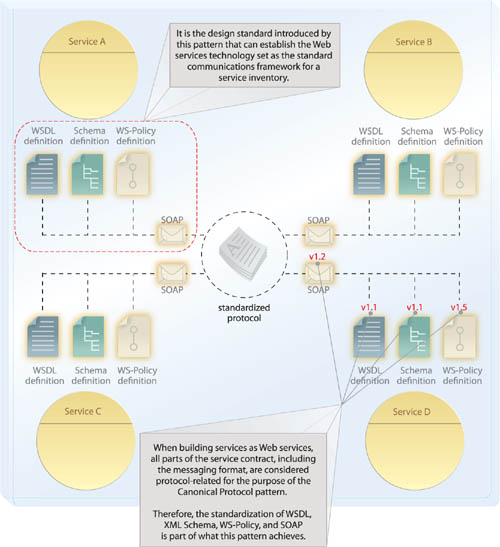
The technology architecture is designed to limit enablement of cross-service interaction to a single or primary communications protocol or protocol version. All other technologies associated with supporting the protocol’s underlying communications framework are also standardized. This guarantees baseline technological compatibility across services (Figure 6.27).
Note
This design pattern advocates the standardization of protocols used for inter-service communication only. Traditional protocols, such as those used to communicate with proprietary components or databases, are not affected by this pattern as long as they remain part of the logic encapsulated by services.
To ensure that all services an inventory architecture is intended to support can effectively interact and be repeatedly recomposed requires that a centralized communications technology be carefully chosen.
A common framework that fulfills this role is the Web services platform because it leverages industry-standard transport and messaging protocols (e.g., HTTP and SOAP) that are widely supported yet still vendor-neutral. However, even when using Web services, this design standardization pattern must still be applied to overcome possible disparity resulting from the mismatch of protocol-related versions (as illustrated in Figure 6.28). The WS-I Basic Profile is therefore likely a key part of applying this pattern as a means of ensuring technological compatibility among the various versions of Web service technology standards.
Alternative communication options can also be explored within controlled environments. For example, a proprietary vendor protocol can be chosen, as long as all services within its inventory are standardized to conform to its use.
Note
When applying this design pattern to Web services, any Web services-related industry standards and technologies associated with inter-service communication are affected. This can include WSDL, XML Schema, SOAP, WS-Policy, and various WS-* standards. This pattern does not dictate how these technologies are applied, only that their use—and, in particular, their version—are standardized.
Some key considerations when standardizing on one communication protocol are:
• Maturity and Reliability– Whichever protocol is chosen, service interaction throughout the resulting technology architecture will be constrained by whatever limitations this framework imposes. Therefore, the maturity and overall adequacy of the communications technology must be carefully assessed.
• Longevity– If there are any concerns that vendors may discontinue or abandon the technology, the associated risks would need to be taken into account.
• Cost– Building services to support a primary communication protocol can bring with it a series of hidden expenses. Some may be related to accommodating deficiencies in the protocol (as per the maturity, reliability, and longevity considerations just raised), while other costs can be incurred if the protocol is part of a proprietary platform that requires licensing fees.
When the preferred protocol imposes constraints in any of these areas, Dual Protocols (227) can be viewed as a viable alternative to (or even a first step toward) this pattern.
Note
This design pattern could be considered a specialized implementation of Canonical Resources (237) in that it is very much about standardizing technology across an inventory. However, it is singled out here because a communication protocol is more than just an architectural extension. It represents the fundamental means by which all parts of a distributed solution work together.
Canonical Protocol’s architectural focus naturally results in relationships with other architecture-centric design patterns, such as Canonical Resources (237), Enterprise Inventory (116), and Domain Inventory (123).
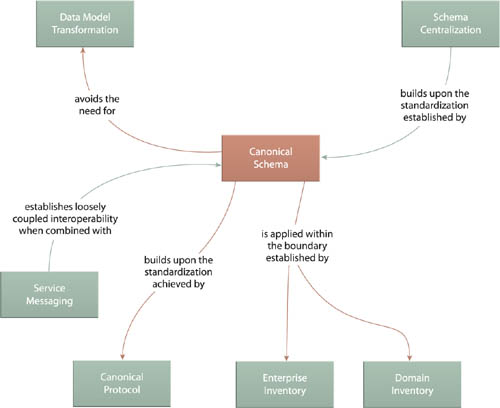
By standardizing the medium by which services exchange business and activity data, a foundation for service interoperability is established. Therefore, this pattern is closely related to Service Messaging (533), Messaging Metadata (538), and also Schema Centralization (200).
Note
Canonical Schema should not be confused with Canonical Data Model (Hohpe, Woolf). With Canonical Schema, services and consumers utilize and conform to an already-developed data model, avoiding the need for transformation. The classic Canonical Data Model pattern assumes that data model transformations are necessary and recommends that they be designed in such a manner that they adhere to a standard data model instead of resulting in pair-wise permutations.
For a service to send or receive data, it needs to know in advance exactly how that data will be organized and structured. For example, a business document such as an invoice can have its own data model structure that determines how invoice information is organized, what the different parts of an invoice document are called, and what data types and validation constraints should be associated with these parts.
When different services are delivered by different project teams, each team may decide to structure an invoice data model in a different way. When those services need to exchange invoice data at a later point in time, they will not be compatible and will require Data Model Transformation (671) to convert one invoice document structure into another.
This generally introduces the need to design and develop a custom transformation layer consisting of mapping logic and rules that resolve differences between disparate schemas. This logic can be implemented as part of the service hosting environment and carries out its transformation every time data needs to be exchanged via the affected service capabilities (and is therefore considered undesirable).
The need for Data Model Transformation (671) can be avoided by ensuring that service contracts are designed with compatible schemas from the beginning. This is achieved by applying data design standards to the data models within service contracts (see Figure 6.31).
Canonical Schema is commonly applied to services implemented as Web services because this allows for data models to be defined using the industry standard XML Schema expression language. In this case, XML Schema definitions representing the same type of documents or information sets need to be kept in alignment so that complex and simple data types remain in synch across different service contracts.
Once standardized schemas are in place, this pattern is realized via a formal process through which service contracts are designed, which ensures consistent application of the Standardized Service Contract design principle.
In larger enterprises, the scope of data model standardization may need to be limited to individual domains so as to make the standardization effort and the subsequent governance responsibilities more manageable. In fact, it is the considerations raised by this pattern that often motivates organizations to apply Domain Inventory (123) over Enterprise Inventory (116).
Data models are typically standardized within the boundaries of inventories defined by Enterprise Inventory (116) or Domain Inventory (123), resulting in a healthy inventory architecture with a reduced need for Data Model Transformation (671).
Also, by establishing a key design standard in support of service interoperability, Canonical Schema forms several close relationships with other patterns, such as Schema Centralization (200) and Canonical Protocol (150).