Microsoft Windows Security Protocols and Services
Every computer or device connected to a network is called a node. Nodes communicate with one another by agreeing on a set of communication rules called a protocol. A communication protocol sets the rules for how nodes construct, send, receive, and interpret messages. Each protocol serves a specific purpose and has its own structure for constructing and addressing messages. In fact, several protocols are necessary to transport a message from one application to an application running on a remote computer. The physical media has one way of handling data, the network addressing software uses a different protocol, and applications use yet another set of rules to communicate.
Most discussions of network protocols include a discussion of the Open Systems Interconnection (OSI) Reference Model. The OSI Reference Model is a generic description for how computers use multiple layers of protocol rules to communicate across a network. The OSI Reference Model defines seven different layers of communication rules. You’ll also likely encounter another popular reference model, the Transmission Control Protocol/Internet Protocol (TCP/IP) Reference Model, when discussing network protocols. The TCP/IP Reference Model defines four different layers of communication rules. Both models are useful to describe how protocols work and how to implement them in network communications. FIGURE 9-5 shows the TCP/IP Reference Model and the OSI Reference Model.
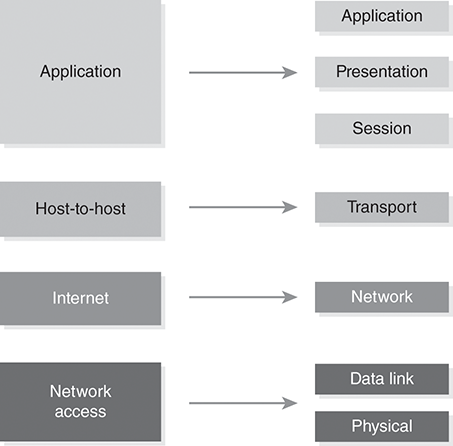
FIGURE 9-5
TCP/IP and OSI Reference Models.
© Jones & Bartlett Learning.
Protocols provide the ability for applications to exchange information with other applications on other computers. For example, most web browser applications communicate with a web server application using the Hypertext Transfer Protocol (HTTP). Web browsers can use other protocols, but HTTP is the most common protocol for regular webpages. The web browser passes the message to the networking software layer. That layer handles the details of breaking the message into smaller packets suitable for networks, addressing the target machine, and routing the request across the network to ensure it arrives.
A common networking protocol is TCP/IP. TCP/IP is actually a combination of two separate protocols, but they work together in so many environments that they are often referenced as a single protocol.
Finally, the networking software passes the messages off to the software that physically controls the hardware that sends the data using physical media. This is the software and hardware that create the radio transmission for wireless networks or electrical signals for Ethernet.
It is important to know the protocols your systems and applications use. You can change many protocol settings to make your systems more secure. You’ll want to learn more eventually about the specific protocol settings to use in hardening systems. For now, you should be aware of the most common protocols and the ones that relate most directly to security. TABLE 9-4 shows a list of common protocols and how each one relates to your environment’s security.
TABLE 9-4 Common Network Communication Protocols |
||
|---|---|---|
| PROTOCOL | DESCRIPTION | SECURITY NOTES |
| Telnet | Legacy protocol used for connecting terminals to servers. Sends text to and from the server. Historically used for remote administration accessing command-line utilities. | Telnet sends all information, including usernames and passwords, in readable text. Telnet should always be considered insecure and should not be used. |
| Secure Shell (SSH) | Similar to Telnet, except messages are encrypted. Useful for secure remote system administration using command-line utilities. | Older versions, such as 1.X, contain documented vulnerabilities. Newer versions are secure for most uses. |
| HTTP (Hypertext Transfer Protocol) | Used for most web browser/web server communication. | All data are sent in the clear. HTTP is not appropriate for confidential data. |
| HTTPS (Hypertext Transfer Protocol Secure) | Secure HTTP. Useful for exchanging confidential information between web browsers and web servers. | HTTPS uses SSL/TLS to provide encryption services. Ensure your web server is using SSL version 3.X or TLS. |
| SSL/TLS (Secure Sockets Layer/Transport Layer Security) | SSL is the predecessor of TLS. Both protocols provide encryption for Application Layer protocols, such as HTTPS. | TLS is the most secure. Do not use versions 1.X or 2.X of SSL. Use only SSL 3.X or TLS unless your application does not support newer versions. |
| TCP/IP (Transmission Control Protocol/Internet Protocol) | The most common protocol pair for Internet communication. | TCP/IP is a frequent target for attackers since it is used in so many applications. Use helper protocols, such as TLS, to secure TCP/IP communications and filters to detect malicious traffic. |
| UDP (User Datagram Protocol) | Another common protocol used in place of IP when persistent connections are not necessary or desirable. | Use the same precautions as TCP/IP. Use UDP with other protocols and filters. |
| IPSec (Internet Protocol Security) | A protocol suite used to secure IP communication by encrypting each IP packet. | IPSec secures any messages that use IP to communicate. IPSec is transparent to applications that use it. |
| IKEv2 (Internet Key Exchange) | Tunneling protocol developed by Microsoft and Cisco. | When paired with IPSec, or other protocol that provides authentication, IKEv2 is a very secure and capable VPN. |
| PPTP (Point-to-Point Tunneling Protocol) | One of three common protocols used for virtual private networks (VPNs). | PPTP relies on PPP’s encryption and authentication features to provide a VPN for applications that use TCP. |
| Layer 2 Tunneling Protocol (L2TP) | Another common protocol used for VPNs. | L2TP operates at a lower level than PPTP and must rely on a higher-level protocol, such as IPSec, to provide encryption. L2TP relies on UDP to transport messages. |
| SSTP (Secure Socket Tunneling Protocol) | New VPN protocol that uses SSL/TLS to encrypt HTTP traffic in a tunnel. | SSTP overcomes limitations that PPTP and L2TP messages have with firewalls and NAT devices. SSTP has no conflicts with NAT. |
| WEP (Wired Equivalent Privacy) | Older protocol for securing wireless network traffic. | WEP is a legacy protocol to encrypt wireless network traffic. It is better than nothing, but not sufficient to secure confidential information. |
| WPA (Wi-Fi Protected Access) | WPA and WPA2 are more secure protocols than WEP with stronger encryption for wireless network traffic. | The latest version of WPA, WPA2, is based on Advanced Encryption Standard (AES) and supports several modes for varying needs of encryption security. |
| Kerberos | Protocol network nodes can use it to authenticate themselves to one another using an insecure network. | Windows uses Kerberos as a default authentication protocol. |
© Jones & Bartlett Learning. |
||
Windows uses protocols to communicate with other nodes across a network. This allows a program running on one computer to communicate with a program on another computer. It is common that the program on at least one end of a communication channel is a Windows service. A Windows service is a long-running program that performs a specific set of functions, such as a firewall, database server, or a web server. Services generally run without requiring user intervention and commonly run on server computers. Most services that provide network-related functions monitor one or more ports. A port is a numeric identifier that programs use to classify network messages.

FIGURE 9-6
Message flow in the U.N. example.
© Jones & Bartlett Learning.
