Microsoft Baseline Security Analyzer (MBSA)
Microsoft has provided a free tool for several versions of Windows that analyzes computers to identify insecure configurations. The MBSA is an easy-to-use legacy tool. However, MBSA isn’t the latest analysis tool available, and with each new version of Windows, it looks for fewer and fewer vulnerabilities. It evaluates part of the current security state of computers in accordance with Microsoft security recommendations. It not only identifies problems but also ranks them by severity and provides recommendations to fix each one. Although MBSA isn’t as comprehensive as it used to be, it does a good job of finding much of the “low hanging fruit.”
The latest version of MBSA, version 2.3, officially supports Windows Server 2012 R2 and Windows 8.1, as well as multiple previous Windows versions. (Note that MBSA version 2.3 is not supported on Windows 10.) If your environment includes computers running previous versions of Windows, you can consult the MBSA release notes or download page to ensure that your version of MBSA supports all your Windows computers. Since MBSA does not install with Windows, you must download and install it yourself. It is well worth the small amount of time and effort to acquire and install this tool. You can get it from Microsoft’s website.

FIGURE 7-3
SCA snap-in analysis results.
Courtesy of Microsoft Corporation.

FIGURE 7-4
SCA command-line tool.
Courtesy of Microsoft Corporation.
FIGURE 7-5
SCA command-line tool analysis results.
Courtesy of Microsoft Corporation.
MBSA Graphical User Interface
You can run the MBSA using the graphical user interface (GUI) or command-line interface. The GUI provides an intuitive way to select the types of resources MBSA will analyze. The GUI is the most common interface to use when learning about MBSA. To run MBSA, launch the program, select the scan scope and options, and then, start the scan. The scan report contains lots of information on what was found and what you should do about it. You choose to address or ignore each identified issue. It’s really that simple. The MBSA will scan your selected computers for just the types of vulnerabilities that interest you. In addition to looking for specific security vulnerabilities, MBSA will alert you if operating system or application updates exist that you haven’t installed.

FIGURE 7-6
MBSA GUI.
Courtesy of Microsoft Corporation
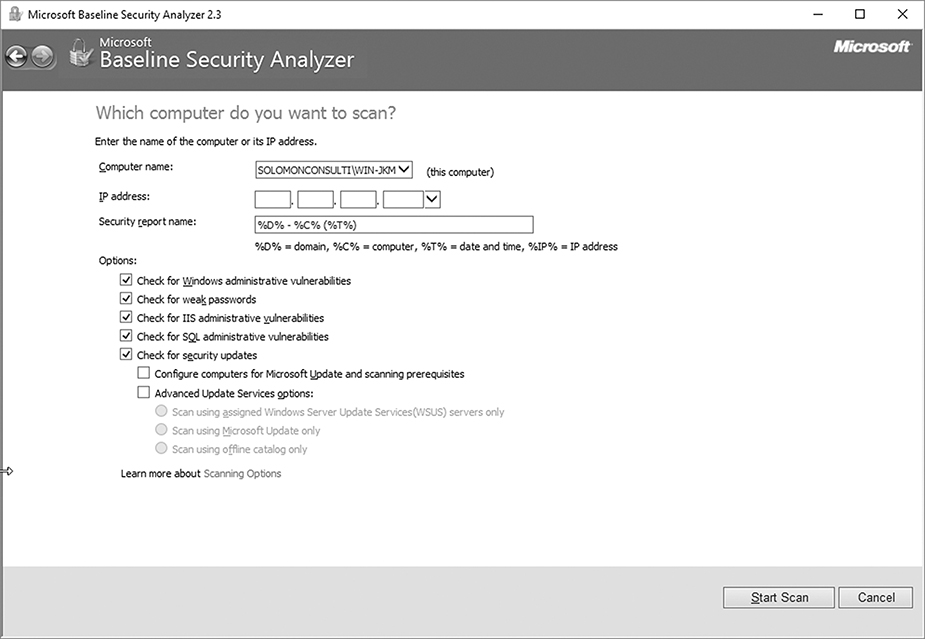
FIGURE 7-7
MBSA scan options.
Courtesy of Microsoft Corporation.

FIGURE 7-8
MBSA scan results.
Courtesy of Microsoft Corporation.
MBSA Command-Line Interface
Microsoft also provides a command-line interface for MBSA (FIGURE 7-9). The mbsacli.exe command performs the same scan as the MBSA GUI (FIGURE 7-10) but with the added flexibility of starting the scan from the command line. Calling an MBSA scan from the command line gives you the ability to use batch files to scan computers for vulnerabilities. You can schedule batch files to run scans unattended at any time.

FIGURE 7-9
MBSA command-line interface.
Courtesy of Microsoft Corporation.
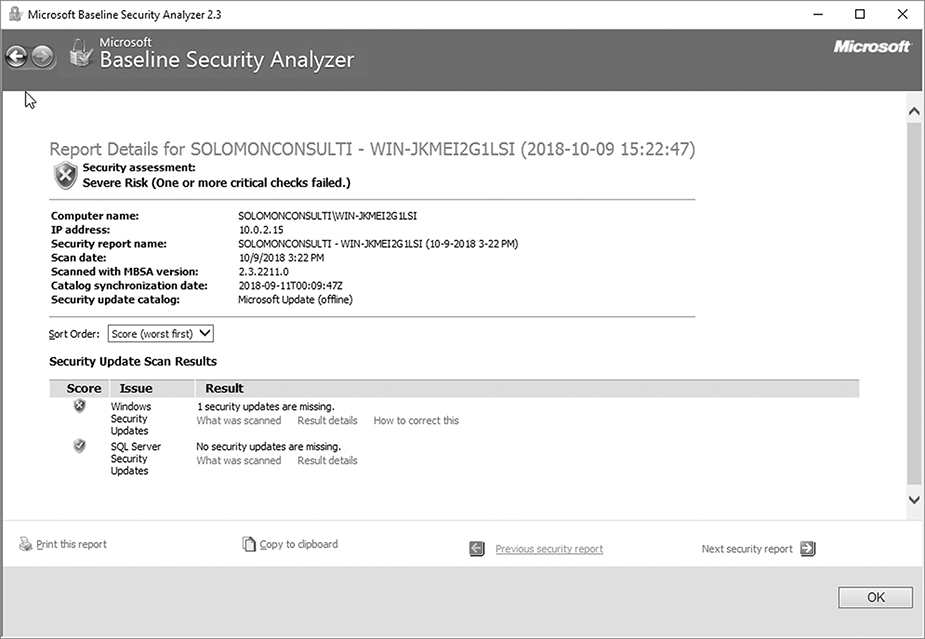
FIGURE 7-10
MBSA command-line interface scan results.
Courtesy of Microsoft Corporation.
The MBSA command-line interface supports the same functions as the GUI. In fact, there are advanced options that give you more flexibility than the GUI. TABLE 7-1 shows the most common MBSA command-line interface options.
TABLE 7-1 Common MBSA Command-Line Interface (mbsacli.exe) Options |
|
|---|---|
| OPTION | DESCRIPTION |
| /target | Computer to scan. Target can be a domain or computer name or an IP address. |
| /d | Domain to scan. Use NetBIOS-compatible domain names instead of fully qualified domain names. For example, use “CorpDomain” instead of “CorpDomain.com.” |
| /r | Range of IP addresses of computers to scan. Beginning and ending IP addresses should be separated by a hyphen. For example, use “192.168.141.130-192.168.141.254.” |
| /listfile | Filename of a text file that contains computer names or IP addresses of computers to scan. Each computer name or IP address should be on a separate line. |
| /n | Scan options that MBSA should not perform. Excluded options may consist of:OS—Windows administrative vulnerabilitiesIIS—Internet Information Services administrative vulnerabilitiesSQL—SQL Server administrative vulnerabilitiesUpdates—Missing security updatesPassword—Check for weak passwords. You can combine options with the “+” operator. For example, “/n os+iis+sql+password” would scan only for missing updates. MBSA excludes all options you supply. |
© Jones & Bartlett Learning. |
|
Microsoft SCA and MBSA aren’t the only profilers. Other products can help you identify security vulnerabilities and keep your computers as secure as possible. You’ll learn about other products that extend and complement SCA and MBSA in the next sections.
