Acquiring and Managing Incident Evidence
One of an investigation’s goals is to discover evidence that answers the who, what, when, where, why, and how questions you learned about in the previous section. The evidence you collect will further the discovery of facts. The same evidence could provide the proof necessary to result in a legal finding in your favor.
Treat every investigation as if it will end up in court. When you begin a new investigation, you don’t know how it will be resolved. Any investigation can end up as an internal matter. Alternatively, it could end up in civil or criminal court. Ensure that any evidence you collect will be useful in court if that’s where you end up.
Your investigation should produce evidence of an incident and possibly support action against an attacker. The evidence you will collect consists of files and their contents left behind after an incident. The existence of some files, such as pictures or executable files, can provide evidence of an incident. In other cases, the contents of files, such as log files, provide the necessary proof. Recognizing and identifying hardware, software, and data you can use is the first step in the evidence collection process.
Types of Evidence
The two types of evidence you’ll collect during an incident investigation are real evidence and documentary evidence. Real evidence is any physical object that you can bring into court. You can touch, hold, and directly observe real evidence. The real evidence you collect during an incident investigation could include computers and other hardware. If your incident involves criminal activity, real evidence may contain fingerprints that you can introduce in court.
The more common type of evidence you’ll collect is documentary evidence. Documentary evidence is any written evidence, such as printed reports or data in log files. Unlike real evidence, documentary evidence cannot stand on its own. Documentary evidence must be authenticated. Much of the evidence you are likely to use in proving a case will be in files, such as log files, database files, and incident-specific files and reports, that provide information indicating what occurred. Because anyone can create a data file or report with desired contents, you must prove that the evidence was collected appropriately and the data it contains prove a fact.
The majority of activities during your investigation will involve using utilities and tools to explore the contents of the computer and storage media. All files and file contents that support your case will be considered documentary evidence. This is where you’ll find most of the evidence for your investigation.
Chain of Custody
All evidence you present in court must exist in the same condition as it did when you collected it. Each device, computer, and operating system has specific procedures for preserving data. Evidence cannot change at all once you collect it; it must be in pristine condition. The court will require you to prove that the evidence did not change during the investigation. You’ll have to provide your own proof that all collected evidence exists without changes as it did when your team collected it. The documentation that supplies details of every move and access of evidence is called the chain of custody. The chain starts when you collect any piece of evidence. FIGURE 13-2 shows a sample chain of custody log.
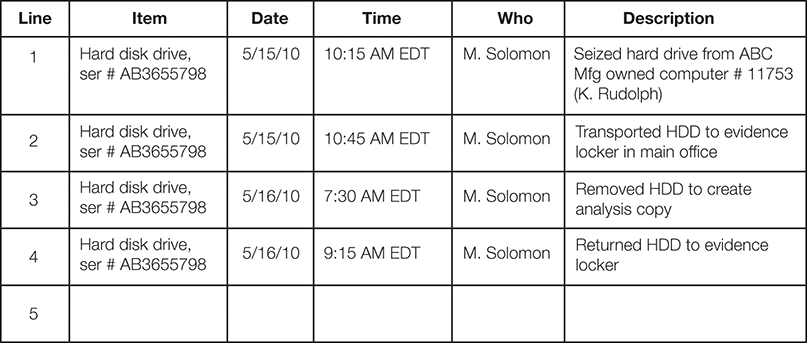
FIGURE 13-2
Sample chain of custody log.
© Jones & Bartlett Learning.
The chain of custody must be complete and without gaps. You demonstrate this by providing the evidence log that shows every access to evidence, from collection to appearance in court. A complete chain of custody log also includes procedures that describe each step. For example, an entry might read “checked out hard disk drive serial number XN629H to create a primary analysis image.” Also include a description of what “creating a primary analysis image” means. The defense will examine the chain of custody documents, looking for any gaps or inconsistencies. Any issue with the chain of custody has the real potential of causing the court to throw out the evidence in question. Once that happens, the evidence you have collected becomes useless and your credibility will probably be questioned.
Since you don’t know if you’ll have to present evidence in court, collect all evidence during an incident investigation as if you will take it to court. If you carefully preserve the chain of custody and do not go to court after all, you just have well-documented evidence. This type of information is great for analyzing incidents for the lessons learned step of incident response. If you are sloppy in the way you collect evidence and then end up going to court, your sloppiness will likely result in having your evidence rejected by the court. Without the evidence you need to prove your case, you may not be able to prevail. Always treat each investigation as if it will end up in court.
Evidence Collection Rules
It is important that you know the rules surrounding evidence collection and handling before starting any investigation. Each state and local jurisdiction may impose slightly different rules; so, familiarize yourself with local laws and policies. In addition, different rules govern different types of evidence. For example, analyzing a database that contains confidential personal medical information will have more stringent requirements than a database containing a parts inventory. Medical data falls under federal HIPAA regulations. Ask questions before engaging in evidence collection. Making incorrect assumptions when collecting evidence will likely get it thrown out of court.
A good place to start learning about local laws concerning collecting evidence is by developing a relationship with your local law enforcement agents. Call your local agency and ask for the computer forensics unit. Meet with them and take the time to learn how they approach investigations. Often, law enforcement officers will provide guidance and help you comply with their investigative requirements. Learning from them will save both of you substantial time and effort when an event occurs that requires law enforcement involvement.
Spend time with your organization’s legal representatives. Start with your CSIRT’s legal representative. He or she can provide valuable input that will guide your investigative efforts as well. The goal is to ensure your processes comply with any statutes, regulations, and policies before an investigation starts.
