CHAPTER TWENTY-NINE
ORGANIZATION NETWORK DYNAMICS AND ANALYSIS
Maya Townsend
People use webs of connections every day to solve problems, innovate, make decisions, and complete routine tasks. Every time they do so, they tap into networks.
OD practitioners have known that networks existed for years and called them “informal organizations,” depicted them with elementary sociograms, and encouraged people to identify their circles of influence. All of those forays into organizational network application have advanced our knowledge. Today, with research from academia and advances in technology, OD practitioners have a robust theory base supported by lab and field experiments and accessible tools for helping identify, diagnose, and leverage organization networks.
This chapter explores organization networks as a concept and a methodology. It describes the areas in which network interventions are most valuable to OD practitioners, explains the process for analyzing organization networks, and provides advice on moving forward to increase competence in network knowledge.
What Are Organization Networks?
A network is an interconnected group or system. Networks are all around us and contribute to all that people accomplish. People use networks to make decisions, increase individual and collective knowledge, solve problems, strategize, innovate, and conduct virtually every other human and organizational activity. Some types of networks are shown in Figure 29.1.

FIGURE 29.1 TYPES OF NETWORKS
All networks share the quality of connectivity: they link people together through relationship ties. The most informal networks are the ones we instinctually create every day by connecting with others in order to share information, solve problems, provide mutual support, and enjoy the experience of being in contact with other human beings we trust and enjoy. Members of these networks include friends, family members, and co-workers. Other informal networks are those in which people come together around a topic of shared interest. A neighborhood gardening club, in which people share knowledge about plants; a book group, in which people read Victorian novels or bestsellers together; and soccer groups that meet for informal games every Saturday in the park are all examples of informal networks. On the opposite pole are formal, inter-organizational partnerships and alliances. One example is the UN Global Compact, which consists of organizations that have committed to shared principles around human rights, labor, environment, and anti-corruption.
Other networks have goals that go beyond connecting. Action networks seek to produce outcomes. For example, the grassroots, informal American Riot Girls group of the 1990s brought together young women to advocate, often in punk and/or radical ways, for feminist causes. Al Qaida has no formal structure—no president or executive director—yet it consists of members who work toward shared terrorist goals. On the other end of the spectrum are formal action groups, such as Move On, which was developed to promote progressive political candidates in the United States, and the Alliance to End Hunger. In between are loose, semi-formal networks like the Austin Healthy Adolescent Initiative, which consists of no dedicated staff members, but is sponsored by the City of Austin and convenes organizations regularly to improve the health of young people in Travis County, Texas.
Finally, other networks concentrate on alignment: helping people to “develop and spread an identity or collective value proposition” (Plastrik & Taylor, 2006, p. 33). The clearest examples of alignment networks are those that form around a shared heritage or profession. One purpose of the Organization Development Network is to help the world realize the value of OD. Women in Technology International brings together women working in technological fields. Angle is an affinity network for lesbian, gay, bisexual, and transgender employees within CBS (the American television network). On the more informal end are loose networks like neighborhood citizens groups that rally around their shared identity as neighbors and the Latina employees who attend ad hoc lunches within a company.
Regardless of their type—connective, action, or alignment—all networks have specific qualities that make them valuable to organizations (Plastrik & Taylor, 2006). First, networks diffuse information rapidly. People often know what is happening before the company formally releases the news. That is because networks are adept at sending information rapidly through the system. Information is irresistible in a network; it functions much as the fuel that keeps the network vibrant and healthy. This quality of rapid information diffusion can be a boon to OD practitioners. Using networks to disseminate messages about an upcoming organizational change, for example, is a viable and effective complement to traditional communication techniques.
Second, networks are resilient and adaptable. Networks can withstand more stress than other types of organizational structures. Networks add, remove, and reconfigure links continuously according to who joins, leaves, and interacts with whom. As a result, constant shifting is the norm in a network. This quality helps networks survive when faced with internal or external change. Already accustomed to refiguration, networks can adapt and rebound faster than other structures can.
Third, networks provide easier access to expertise and information than other structures do. In a formal hierarchy, for example, someone seeking a Java developer might have to wait for an expertise request to travel up the line, across the organization, and then back. In a network, people tap into the resources they need through their connections. Often, referrals can occur very quickly. To facilitate rapid connections, many organizations now use networking apps that help people search for contacts by criteria such as expertise or experience.
Critical Connectors
Networks have one additional quality that makes them especially interesting to OD practitioners: critical connectors. Stephenson (2005) patented specific mathematical algorithms that identify three types of critical connectors. According to Stephenson, these critical connectors comprise 5 to 10 percent of all nodes in a network and are disproportionately influential over the whole. By tapping into critical connectors and using them as conduits for change, OD practitioners can more effectively and rapidly generate change. The three roles are hubs, gatekeepers, and pulsetakers.
Hubs
In Figure 29.2, Karen is a hub because she connects with more people than anyone else. Stephenson describes hubs as having a hearty appetite for information, which can be gossip, technical expertise, product knowledge, or any other kind of information (2005). They tend to be multi-taskers who enjoy juggling activities and relationships. Hubs have great value in the network since they are compulsive sharers who spread information continually. OD practitioners can leverage hubs during change by sharing important messages with them. Because of their deep connectedness, hubs have the power to disseminate that information quickly throughout the network.

FIGURE 29.2 KITE DIAGRAM
The hub also has what is called high degree centrality. Degree centrality measures nodes’ number of connections. With more contacts than anyone else, Karen has the highest degree centrality: 72 percent. In comparison, Aisha has only one connection. Her degree centrality is 9 percent. High degree centrality is not always positive. According to Krebs (2000), “What really matters is where those connections lead to—and how they connect the otherwise unconnected.” Karen has connections within her immediate cluster: people who are already connected. She might have too many redundant links and spend her time with people who cannot add information to her network, only duplicate it.
Gatekeepers
Bian is a gatekeeper since he serves as a barrier between one group and the rest of the organization. Gatekeepers do not always hold the gate between groups; they sometimes manage the flow of information or access to expertise, customers, or systems. Writes Stephenson; “Gatekeepers serve as important links or bridges within an organization, functioning as human way stations on critical pathways between parts of an organization or between Hubs” (2005, p.247).
Gatekeepers have high betweenness centrality, a measure of the extent to which people serve as boundary spanners (Krebs, 2000). Bian has a higher betweenness centrality because three people—Harry, Kwame, and Aisha—are connected to the rest of the group only through him. In comparison to Aisha, who is in between Kwame and no one, has a betweenness centrality of 0 percent.
Individuals with high betweenness centrality serve important brokering roles in the organization and help information flow between areas. However, those high in betweenness are also risks: they represent potential bottlenecks and potential vulnerability points in the system since they are the sole conduit between two areas.
Pulsetakers
Pulsetakers like Fiona and Archana have fewer paths to travel in order to access any other person in the network. They are strategically placed and can gain access to what they need more easily than most. Stephenson says, “They are almost the opposites of Hubs, unseen but all-seeing. Such people carry a lot of influence, much of it subtle. They are well versed in the culture, and a good proportion of them evolve into great leaders. They are key to knowledge succession and, at the very least, should serve as mentors and coaches for the newly hired and uninitiated” (2005, p. 248).
Pulsetakers are associated with high closeness centrality. Closeness centrality looks at the ability to access all actors in the network more quickly than anyone else (Krebs, 2000). Even though Fiona and Archana do not have the most connections, as Karen does, they have high closeness centrality because they can most easily access anyone they need within the network. In addition, they have fewer redundant connections—links within a clique or social circle—and more unique connection patterns.
Some ask whether critical connectors can be recruited to fill network gaps. Others wonder whether personality determines critical connector status. Although more research on the interplay between personality and network position is needed, the short answer to both questions is no. People become critical connectors for a combination of three reasons. First, they play roles that are well suited to connectivity. An HR generalist, for example, will contact many more people than a software developer due to the nature of his role. Second, they have personalities that help them become critical connectors. Third, others in the organization trust them. That trust develops for complex reasons—history, personality, position, affiliations—and cannot be easily predicted. Therefore, hiring someone to be a critical connector does not easily succeed since that person’s ability to form trusting connections with others is based not only on her abilities but also on others’ willingness to accept her.
Networks and Organization Development
The dynamic structure of networks is ideally suited to today’s rapidly changing business environment. Network knowledge supports OD practitioners in many activities, including:
- Change management
- Knowledge and innovation
- Talent management
- On-boarding
- Process improvement
- Fundraising
- Team building
- Alliance building
- Restructuring
- Nonprofit management, including fundraising, program implementation, and volunteer management
In this section, we look at some of the specific ways in which networks add value to initiatives related to change, teams, and leadership.
Organization Change
How many times do companies undertake a costly reorganization only to find that it fails to achieve the desired results? In these cases, the challenge often is that the informal system—the networks—has not changed along with the organization structure. People continue to draw on the connections they have in order to get work done. In essence, they draw on a shadow organization that maintains the status quo and undermines the desired relationships dictated by the new structure.
OD practitioners can use network analysis to help rewire the organization to support restructuring. By understanding internal networks, OD practitioners first deepen their understanding of how people operate in the organization and identify, for example, the constellations of connections that should not be interrupted by the reorganization since they work so well. Then OD practitioners have options: they can design the new structure to capitalize on the strongest and most productive network patterns. They can encourage new network patterns by shifting influential players in the networks to different positions. They can interrupt dysfunctional patterns by engaging critical connectors in new activities. These approaches can help minimize the time needed to realize the expected benefits of change by building alignment between the formal and informal organizations.
Network knowledge can also improve speed of integration after a merger or acquisition. By engaging critical connectors from both entities in joint activities, OD practitioners can accelerate integration. The theory proposes—and research supports—the idea that peers intuitively follow critical connectors, who are both highly trusted and adept at sharing information (Stephenson, 2005). As a result, rather than having to engage an entire workforce deeply, OD practitioners can focus attention on the critical connectors, who then naturally ease the communication and integration process due to their influence in the network.
Diversity and networks is explored in Exhibit 29.1.
Network analysis also provides insights into the nuances of successful team composition. For example, successful R&D teams share specific network qualities that, when planned into their structure, can improve the likelihood of success. Teams use technical-advice networks to access expert information on technical issues and organizational concerns, such as project scheduling and coordination (Rizova, 2006). They use organizational-advice networks to support them when they need “organizational competence and skills” (p. 50). By setting up teams with access to technical-advice and organizational-advice networks, members have access to both types of expertise needed to be successful.
Another important cause for success is a team’s ability to draw on their personal networks to support the team’s work. These teams take advantage of contacts from the members’ personal networks and integrate their own knowledge with capabilities from their networks (Cummings & Pletcher, 2011). A study performed by Cummings and Pletcher of 177 project teams involved in an organization team recognition program showed that finalists—teams that achieved product innovations, demonstrated superior customer service, and/or improved operational effectiveness—had stronger project networks than did non-finalists. A product innovation finalist, in comparison to a non-finalist, was able to draw on significant technical and marketing experts and engage more suppliers and customers. Their broader and deeper knowledge allowed them to create innovations that eluded other teams.
Networks and Leadership
Today’s leaders live in a different world than in the past. Rather than simply managing a vertical domain or a functional area, leaders are embedded in complex ecosystems: a type of macro network formed by the dynamic interplay between interconnected organizations that depend on each other for mutual survival (Moore, 1997). In these business ecosystems, building connections and managing relationships are critically important.
Effective leaders mobilize networks in specific ways (Cross, 2010):
- They manage the center: Leaders minimize bottlenecks, develop high performers, and acknowledge those who, while not individual stars, help their colleagues succeed.
- They leverage the periphery: Leaders bring in newcomers to the group and reengage high performers who have neglected or lost connections.
- They bridge silos: Leaders weave connections in order to improve collaboration at key intersections between groups or geographies.
- They encourage awareness of expertise: Leaders help those within the system identify and access people with expertise relevant to new problems and opportunities.
- They minimize insularity: Leaders bring in connections to external resources in order to prevent groups from developing tunnel vision and becoming isolated.
These five activities help individual leaders encourage success within their systems.
Leaders need to nurture different types of networks. Ibarra and Hunter (2007) outline three networks that require active attention. The first, the operational network, consists of those needed in order to get work done efficiently, provide the functions required of their group, and maintain capabilities. These contacts include direct reports; supervisors; internal partners; internal players who can block or enable a project; and outside supply chain members, distributors, partners, and customers.
The personal network focuses on those who can help a leader grow personally and professionally. They can provide referrals to useful information, contacts, feedback on performance, and coaching. Personal networks support leaders during times of stress and uncertainty by giving them trusted resources and advice.
The strategic network includes people who can help address future priorities and challenges and help secure support for new directions. These contacts are future-oriented; they may be inside or outside the organization. The strategic network often needs the most attention by new leaders. Focused on building their operational and personal networks, many find themselves without the connections they need in order to achieve a future vision.
Even simply having some network knowledge can improve leadership performance. One well-documented case at Raytheon taught participants about network dynamics in a leadership program (Burt & Ronchi, 2006). In comparison to a control group, executives active in the business leadership program were more than twice as likely as the control group to far exceed expectations on performance reviews. They were three times more likely to be promoted to a higher rank and less likely to leave the company (pp. 1, 174).
Succession Planning
Network thinking increases the likelihood of succession planning success by concentrating not just on candidates’ content knowledge but also their relational knowledge. A complement to traditional succession planning tools, organization networks can identify where the incumbent is strong and where there are gaps that could hinder performance.
One R&D subsidiary suffered from an ineffective succession planning process that did not take into account network dynamics (Kleiner, 2003). The CEO chose his golf-playing buddy to be his successor. The successor had a strong social bond with the CEO, but lacked the respect of others in the organization and knowledge about the company’s business. When he was promoted, a peer left the company. She had been deeply trusted by colleagues, held exceptional knowledge about the business and its technology, and believed she should have been promoted. Her departure caused a large gap in operations. The successor was unable to fix the damage caused by her departure or build the relationships he needed to succeed. After three months of dismal performance, the board dismissed him.
Network Analysis
To understand and leverage networks, ONA practitioners rely on network analysis. Network analysis uses complex mathematical algorithms that have been developed over decades in the academic realm. Toward the end of the 20th century, these academic advances began to be adopted within corporate, nonprofit, and government realms. Today OD practitioners have the option to work with software that embeds the mathematics within the program, so little statistical expertise is necessary. Other software requires the OD practitioner to understand and analyze mathematical information. Simple network analysis can be conducted without software. The process is the same regardless of the analytical tool chosen. It begins with project scope and then proceeds through data collection, network visualization, and data presentation and action.
Project Scope
The first step in performing a successful network analysis is to define the guiding question and population for the project. Typical network projects seek to answer questions about how people interact in order to get things done. Projects can focus on specific organization processes (like how the purchasing process functions), organization effectiveness (how people solve problems or collaborate), inter-organization relationships (how people cross organizational boundaries to complete work), or specific issues (how childhood nutrition programs are funded in a specific city).
The guiding question helps practitioners clarify the scope and boundaries for the project. Some guiding questions focus on a bounded population: a group that has clear boundaries about who is in and who is out of the group. A purchasing department, all project managers in an organization, and volunteer tutors are all examples of populations that are bounded. Of course, there are exceptions. The purchasing department may or may not include the administrative assistants who sit in satellite offices and who submit purchase orders, for example. However, the population has boundaries that can be fairly easily defined.
Bounded populations are ideal candidates for organization network analysis. A survey, usually web-based, is sent to all members of the population. A high response rate is needed in order to run analytics with any degree of confidence. Since practitioners know who has received a survey, it is relatively easy to encourage participation by following up with all respondents.
Other guiding questions focus on an unbounded population. In these cases, it is difficult to determine who is in and who is out of scope. For example, a project that focuses on relationships between funders of childhood nutrition programs includes so many different entities—government agencies, schools, private funders, hospitals, and so on—that it is difficult to place boundaries around the population. In these situations, a practitioner has a few choices:
- The OD practitioner can employ a modified snowball sampling technique. In this practice, an initial set of participants is identified. They are invited to submit names of others they believe should be part of the project. This process continues—contacting participants and asking for nominations for additional participants—through several iterations. Once the project sponsors and OD practitioners have determined that the sample size is sufficient, they can launch the survey to all within the sample.
- The OD practitioner can include in a network survey open-ended questions that ask people to identify who else should be included in the list of players relevant to the central question to be answered through the project. While those new additions can be invited to participate, those who have taken the survey prior to their inclusion will not be able to assess their relationships with the new group. Therefore, the analysis will be limited and unreliable. However, this approach can be used to expand an initial understanding of a core population and prepare for a more thorough, later investigation.
- The OD practitioner can use a specific network mapping methodology that does not depend on identifying all members of a population. (See “Value Network Analysis.”)
Data Collection
Organization network data is usually gathered through a survey using a specialized network data collection tool like Network Genie (Hansen, Reese, Kelvin, Bryant, Bishop, Wynick & Dyreng, 2008) or ONA Surveys (Lee, 2011). The survey asks respondents to identify their contacts (Exhibit 29.2), indicate why they interact with their contacts, and estimate the frequency with which they interact with their contacts. Exhibit 29.3 shows a simplified version of the first step in a network analysis data collection: contact identification.
After completing this first step, respondents are asked why they interact with these contacts and how frequently they interact. Exhibit 29.4 shows a sample question screen. Note that the exhibit shows only those who were chosen as contacts by the participant in the first step, not all of the contacts on the master list in Exhibit 29.2.
After all participants complete the survey, the results are analyzed using mathematical algorithms. To conduct this analysis, many use software such as InFlow (Krebs, 2012), UCINET (Borgatti, Everett, & Freeman, 2002), NetForm (Stephenson, 2002), or NetMiner (Cyram, 2009). Information about various software tools can be found in “Overview of Common Social Network Analysis Software Platforms” (Monitor Group and the David and Lucile Packard Foundation, 2009).
Network Visualization
Networks are usually depicted visually. There are two common symbols on every network map: the node and the link. Circles or squares represent nodes or actors in the network. These nodes can be individuals, departments, organizations, websites, issues, or roles. Lines show links or interactions between nodes.
Figure 29.3 shows a sample network map of a small nonprofit organization. The guiding question that generated this map was: With whom do you exchange information in order to get your job done? The boxes designate departments, which are, starting from the box at the top center of the image and going clockwise: Admin, Development, Ed Sales, Production, Pub Services, and Systems. Within the boxes, each point represents a person. The lines show significant information exchange within departments. For example, within Production, the large box at the bottom, there are many lines between employees. This suggests that Production employees exchange information frequently; their work seems to require interaction, rather than isolated individual action only. There are also lines between departments, indicating that people work cross-functionally in order to complete daily work.
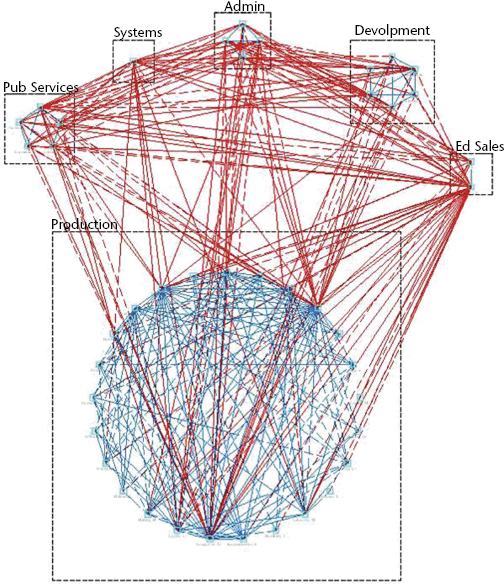
FIGURE 29.3 ORGANIZATION NETWORK MAP
Network maps arranged by department, such as Figure 29.3, are easiest to interpret since they mimic the organization’s structure, which is already familiar to most viewers. Much value comes from also depicting connections in a spider map format. This format arranges people using mathematical algorithms. Nodes with higher centrality are moved towards the center of the map. Nodes with lower centrality are placed around the periphery. By using this format, we can discern patterns that do not show up easily in a map formatted by department.
The spider map in Figure 29.4 shows expertise interactions in a technology organization. The map is color coded by department; all the black dots, for example, work in the same area. The four departments depicted are largely self-contained. The largest cluster consists of mostly one department with one person (Number 12) serving as the gatekeeper to another department. The small cluster on the top left includes members of two different departments. However, Number 55 and Number 59 are not connected to the other members of their own department, shown in the cluster at the lower left.
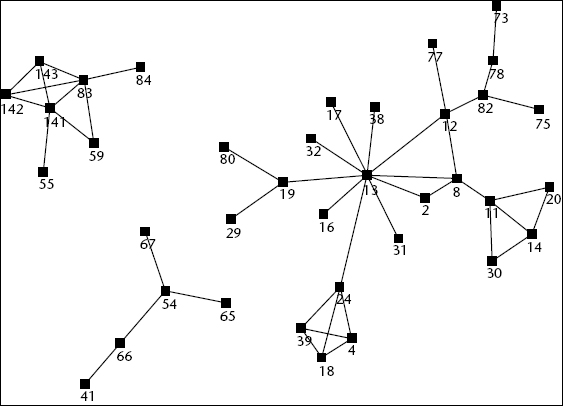
FIGURE 29.4 SPIDER MAP
Another interesting pattern that can be seen easily in a spider diagram is the centrality of specific individuals within the network. For example, Number 13, a hub, has direct connections to ten people. Many of these people have no other connections. If Number 13 were to leave the organization, it would flounder until another person filled the function performed by the critical connector. To mitigate this risk, an organization can create a mentoring relationship so that Number 13 shares responsibilities with another and, thereby, prevents the possibility of work slowdown in the case of his departure.
Data Presentation and Action
After collecting data, just as in any other action research process, the data is shared and collectively interpreted. There are specific choices to be made around how to share the data in order to maximize the value of the network analysis.
One option is to share all data, with name labels, with the entire organization. In this case, everyone can see how everyone else connects. This option can be risky: people can misinterpret data and draw harmful conclusions, such as George has no connections, therefore no one likes him and he will probably be fired soon. All participants need network education in order to successfully interpret network data. Organizations that share data with name labels tend to be new organizations or mature organizations in which there is high trust.
A safer option is to share all data without identifying labels with the entire organization. In this case, everyone can see the flows between individuals. However, since individuals are not named, the focus is on macro-level patterns across departments or groups. This is the preferred option in many network studies since it allows collective data interpretation without the dangers inherent in sharing all information. That said, people are usually clever enough to identify some of the names on the chart. Care is taken to educate individuals about networks so they can be responsible and accurate with the information.
A third option is to share a summary of findings and no maps with the entire organization. In this case, a small working group and the ONA consultant analyze the data and identify a short list of learning based on their interpretations. This list is shared with the organization and used as a springboard for collective discussion of the learning, including conversation about the validity of the interpretations and alternative interpretations.
After the presentation, discussion, and collective interpretation of network data results, the process follows a standard action research model. Specific interventions are chosen based on the findings and implemented. Many organizations choose to conduct a follow-up network analysis six months or a year after the initial analysis in order to gauge how well the interventions have addressed priority network issues.
Value Network Analysis
Value network analysis (VNA) is a specialized method of network data collection and analysis that is especially well suited to complex issues and unbounded populations. VNA was developed by Verna Allee in the 1990s. She defines a value network is “any web of relationships that generates . . . value through complex, dynamic exchanges between two or more individuals, groups, or organizations” (Allee, 2003). For example, public education adds value in the form of learning through the actions of a conglomeration of entities: schools, counselors, nutritionists, after-school programs, parents, students, and so on. A company’s procurement process acquires products and services through trusted relationships and savvy negotiations that are valued by the corporation when done well.
Figure 29.5 shows an example of a value network for the online auction giant eBay (Allee, 2003). The nodes—eBay, Buyers, Sellers, Volunteer User Groups, and Escrow and Logistics Services—represent roles played in the network. VNA is unique in its focus on roles. According to Allee, the emphasis on roles is significant because, although individuals can change in organization, roles remain fairly constant. Focusing on roles allows organizations to concentrate on what provides value most effectively, rather than on tailoring a process or system to individual strengths and preferences.
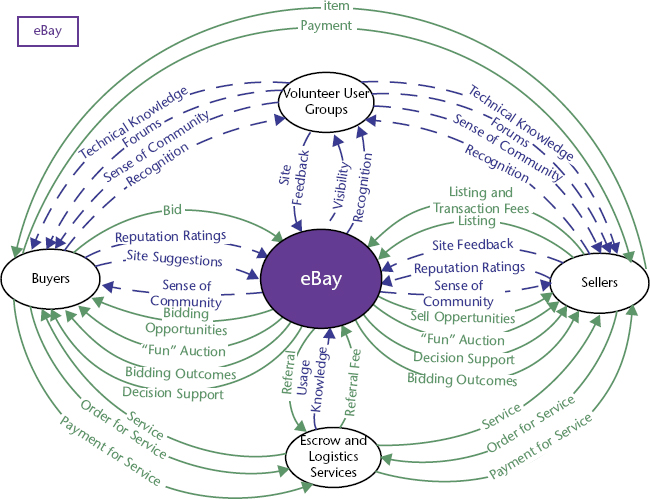
FIGURE 29.5 eBay VALUE NETWORK
Permission granted by Verna Allee to reprint. Originally published in V. Allee, The Future of Knowledge: Increasing Prosperity Through Value Networks, Butterworth-Heinemman, 2003, and updated for V. Allee and O. Schwabe, Value Networks and the True Nature of Collaboration, 2011.
The links in the value network represent transactions: activities “generated by a person that involve conveying a . . . product, service, or benefit to another person” (Allee, 2003, p. 268). There are two types of transactions in a VNA. Tangible deliverables, represented by solid lines, “directly support production and delivery of goods, services, and revenue or funding” (Allee & Schwabe, 2011). These deliverables are contractually obligated activities that are expected as part of the product or service that is paid for by a customer or requested by a partner. eBay’s tangible deliverables here include the item and payment, as well as selling opportunities, decision support for accepting bids, and bidding outcomes.
The second type of transaction is the intangible deliverable, represented by dotted lines. Intangible deliverables are the little “extras” that are rarely formalized or contractual but that are critical supports to the process or system. eBay’s intangible deliverables include a sense of community, which cannot be formalized, but is a valuable byproduct of the eBay experience.
VNA Applications
VNA has been applied successfully in many contexts and for many purposes. Sometimes considered the ideal process-mapping tool for the complexity era, VNA excels at identifying and analyzing non-linear, dynamic processes. VNA also effectively maps business ecosystems: a dynamic structure of interconnected organizations that depend on each other for mutual survival. Other applications of VNA include:
- Project management. VNA helps clarify roles and expectations; clarify monitoring and quality control techniques; and improve quality and collaboration.
- Organizational restructuring. VNA helps identify current and ideal future relationships, workflows, relationships, and value production systems.
- Knowledge networks and communities of practice. VNA helps demonstrate the value provided by knowledge networks and communities of practice.
- Talent management. VNA helps shift companies from managing individuals to managing roles and pinpointing core competencies needed by mission-critical value production processes.
- Intangible asset management. VNA helps identify and quantify intangible organizational assets, such as reputation, brand image, customer and employee loyalty, and workforce competence.
- Workspace design. VNA helps companies design workspaces that are congruent with their workflows and align with their collaboration goals. (Allee & Schwabe, 2011)
Conducting a Value Network Analysis
Value network analysis follows less of an action research model and more of a dialogic systems model (Bushe & Marshak, 2013) in that it engages people in articulating reality as they experience it, forming a shared vision of the future state, and analyzing the system in the moment based on their collective picture. VNA is typically conducted in a facilitated meeting in which, in the course of three to eight hours, a group develops their network map. After creating the map, they ask specific questions designed to test the resiliency, effectiveness, and use value of the system. Typical questions asked during this stage include:
- How much reciprocity is there between roles? Are some roles giving much more than receiving? Are others receiving more than giving?
- Is there an appropriate balance of tangible and intangible inputs and outputs between roles and within the network as a whole?
- Are there particular roles that are carrying the burden of network interactions and, as a result, pose a risk to the network?
- Are there patterns of intangible transactions that might be supplementing the existing process in inefficient or ineffective ways?
- Where are the missing or dead links?
- Where does a value flow get stuck or break down?
- Where does a role fail to transform inputs to appropriate outputs?
After analyzing the value network map, two things typically happen. First, groups create desired future maps that show how they would like the system to operate. Second, groups make changes to the mapped system based on what they have learned.
Moving Forward with Networks
OD practitioners who wish to incorporate network thinking or network analysis into their practices have several options. Each is listed beginning with the easiest, least time-consuming, and least expensive.
Incorporate Network Knowledge
OD practitioners can use simple network thinking to inform their decisions about how to intervene in organizations. Minimal formal education is needed to proceed down this path. Instead, OD practitioners need to ask several questions as they work:
- Where are the critical connectors who can help us accelerate this initiative?
- How can we engage critical connectors in our work?
- Where are the holes in the network? Where are areas not as connected as they should be?
- How can we build redundancy into the working networks of this organization so they are more resilient?
To proceed down this path, OD practitioners should expand their knowledge through reading, classes, webinars, and study groups. Hanneman & Riddle (2005) and Anklam (2007) offer helpful resources on networks and network analysis.
Facilitate Value Network Analysis
OD practitioners can integrate value network analysis into their practice. VNA is ideal for helping groups map current and desired business processes, analyze business ecosystems, and demonstrate the value provided by knowledge networks. It is simple and easy for OD practitioners to learn how to facilitate VNA sessions since VNA is dependent on advanced facilitation skill—which most OD practitioners already have—and understanding of networks. To pursue this option, start by reading Value Networks and Collaboration (Allee & Schwabe, 2011) and then take the VNA qualifying exam.
Use Outsourced ONA Services
OD practitioners can incorporate network analysis into their practice by using outsourced ONA services. OD practitioners can contract with a qualified, experienced ONA provider who performs “back office” network data collection, analysis, and visualization services. The provider can also provide guidance on data collection methodology, scope, and process and help the OD practitioner identify recommendations, themes, and opportunities. The advantage of this approach is that the OD practitioner can quickly and easily incorporate advanced ONA services into his or her existing portfolio. While more costly than other options, it dramatically reduces the long learning curve associated with developing an ONA practice.
Become an ONA Practitioner
OD practitioners can build competence in organization network analysis. Learning how to perform reliable, statistically sound, competent ONA takes time and study. The best way to proceed is through an intensive learning process supplemented by mentoring by an experienced practitioner. This method takes time and monetary investment. However, the benefit is that OD practitioners can be solely responsible for and competently provide ONA services.
Whatever path is chosen, all OD practitioners should deepen their understanding of networks and how they operate. As technology integrates more deeply into our lives, networks will become the primary conduit through which we operate both on the job and off. They will increasingly affect how we think about organizations: what they are, where they begin and end, and what they can do. They will allow diverse people to join skills and passions to address the most challenging social issues. Networks are not going away. Quite the contrary: they are here and they are going to become more prominent in years to come.
References
Allee, V. (2003). The future of knowledge: Increasing prosperity through value networks. Burlington, MA: Butterworth-Heinemann.
Allee, V., & Schwabe, O. (2011). Value networks and the true nature of collaboration. Retrieved from www.valuenetworksandcollaboration.com/.
Anklam, P. (2007). Net work: A practical guide to creating and sustaining networks at work and in the world. Burlington, MA: Butterworth-Heinemann.
Borgatti, S. P., Everett, M. G., & Freeman, L. C. (2002). UCINET for Windows: Software for social network analysis. Harvard, MA: Analytic Technologies.
Burt, R. S., & Ronchi, D. (2006). Teaching executives to see social capital: Results from a field experiment. Social Science Research, 36, 1156–1183.
Bushe, G. R., & Marshak, R. J. (2013). Advances in dialogic organization development. OD Practitioner, 45(1).
Cross, R. (2010). Improving leadership effectiveness through personal network analysis and development. In R. Cross (Ed.), The organizational network fieldbook: Best practices, techniques, and exercises to drive organizational innovation and performance. San Francisco, CA: Jossey-Bass.
Cummings, J., & Pletcher, C. (2011, Spring). Why project networks beat project teams. Sloan Management Review, 52(3).
Cyram. (2009). NetMiner 4.0.0. Seoul, Korea: Author.
Hanneman, R. A., & Riddle, M. (2005). Introduction to social network methods. Riverside, CA: University of California, Riverside. Retrieved from http://faculty.ucr.edu/~hanneman/
Hansen, W. B., Reese, E., Kelwin, B. S., Bryant, S. Bishop, D., Wynick, C. H., & Dyreng, D. I. (2008, August). Network Genie user’s manual. Retrieved from https://secure.networkgenie.com/admin/documentation/Network_Genie_Manual.pdf.
Ibarra, H., & Hunter, M. (2007, January). How leaders create and use networks. Harvard Business Review.
Kleiner, A. (2003). Karen Stephenson’s quantum theory of trust. Strategy + Business, 29.
Krebs, V. (2000). The social life of routers. Internet Protocol Journal, 3, 14–25.
Krebs, V. (2012). Software for social network analysis & organizational network analysis. Retrieved from www.orgnet.com/inflow3.html.
Lee, L. L. (2011, September). Accelerating the business of networking. Paper presented at the Open Knowledge conference. Retrieved from www.optimice.com.au/documents/Optimice-KIN2011Presentation.pdf.
Monitor Institute and the David and Lucile Packard Foundation. (2009). Overview of common social network analysis software platforms. Retrieved from www.slideshare.net/noahflower/overview-of-network-analysis-platforms.
Moore, J. F. (1997). The death of competition: Leadership and strategy in the age of business ecosystems. New York: Harper Paperbacks.
Plastrik, P., & Taylor, M. (2006). Net gains: A handbook for network builders seeking social change. http://networkimpact.org/downloads/NetGainsHandbookVersion1.pdf.
Rizova, P. (2006, Summer). Are you networked for successful innovation? MIT Sloan Management Review.
Stephenson, K. (2002). NetForm: The software. Retrieved from www.netform.com/html/software.html.
Stephenson, K. (2005). Trafficking in trust. In L. Coughlin, E. Wingard, & K. Hollihan (Eds.), Enlightened power: How women are transforming the practice of leadership. San Francisco, CA: Jossey-Bass.
