3
Identity and Access Management for Internet of Things Cloud
Soumya Prakash Otta and Subhrakanta Panda*
Department of CSIS BITS Pilani, Hyderabad Campus, Hyderabad, India
Abstract
The Internet of Things is an emerging technical ecosystem, composed of heterogeneous technological smart objects which are seamlessly connected to the Internet. Provisioning of high-speed data and bandwidth for connectivity for growing variety of IoT services would increase their exposure for fraudulent activity as well as cyber-attacks. Since security issues are significant for the deployment of many IoT services with its amalgamation with cloud implementation, threats severity and vulnerability associated show multiplying effect. This article highlights the emerging security issues associated with IoT Cloud and specifically addresses the challenges faced due to Identity and Access Control of the IoT Cloud. Internet of Things is getting established as a technological ecosystem enabling application of computing to anything, anywhere, and at any time. For such unique versatility and openness, such interconnected devices and users are vulnerable to cyber-attacks. In such a scenario a small lapse in identity management will have exponential effects from such attacks. In this work, an effort has been done to critically examine aspects of IoT security and particularly regarding identity and access management for IoT over Cloud infrastructure. This chapter analyses the identity and access management challenges in IoT, followed by a proposal of cloud identity management model for IoT using distributed ledger technology.
Keywords: Distributed ledger, Internet of Things, IoT security, cloud IoT, identity and access management
3.1 Introduction
The concept of Internet of Things (IoT), for the first time was proposed in 1999 by Auto-ID laboratory of the Massachusetts Institute of Technology (MIT). IoT extensively uses Machine to Human (M2H) as well as Machine to Machine (M2M) communication models. Various Dedicated Short-Range Communication (DSC) techniques have enabled interconnection of sensors, receivers, actuators and associated computational nodes for IoT devices for exchanging the acquired data. Since inception, IoT has been continuously growing as a technological ecosystem. It is also noticed that IoT devices are generally constrained from high availability of resources point of view. It is observed that the interconnected systems comprise of a huge number of sensing devices which have less memory coupled with smaller processing capability as well as their firmware or driver software are seldom updated. Usually, they are also deployed at physically unsecured, even at public places and left unattended for prolonged duration. Hence there is a definite requirement to secure IoT infrastructure as well as the network. A principal factor in securing an IoT infrastructure is envisaged regarding device identity and mechanisms to authenticate them in the ecosystem. Well known and existing authentication mechanisms require sufficient computing requirement which are generally not possible by the IoT devices. Associated problems such as issues related to authentication, security, data privacy of the IoT devices are increasing with passage of time. In general, huge volume of data is acquired by various sensors and other IoT devices in the IoT system. Such data, if at all saved using a centrally controlled mechanism or under the supervision of a single Trusted Third Party (TTP) administrator, may lead to the data security and privacy issues. To securely control and manage issues of IoT, classical protection mechanisms like cryptographic means and secured communication protocols are insufficient. In order to tackle these problems, there is a requirement of efficient mechanism having distributed storage, thereby avoiding a central point of failure or control. The mechanism should also facilitate secured authentication and access control having capability of sustaining security related attacks on the system.
Similarly, another evolving area, Cloud computing, is also making its presence felt in almost all technical ecosystems. This is also emerging as a vital processing nodal system for IoT. Accordingly, an efficient and robust cloud IoT identity management framework merits its development due to its definite relevance. Due to the above mentioned concepts, systematic analysis with visualization of associated risks with various elements of IoT for identity management is of paramount importance. Visualizing its importance, some research by academia and related developments have been initiated by industries in this regard.
The organization of the rest of the chapter is as follows: Section 3.2 provides details on Internet of Things (IoT) Security. Section 3.3 discusses details on IoT Cloud and Identity related aspects. Section 3.4 elaborates related Developments for Securing IoT for better Identity and Access management. A Distributed Ledger based solution for Identity and Access Management (IAM) security of IoT Cloud is covered in Section 3.5 and Section 3.6 concludes the chapter.
3.2 Internet of Things (IoT) Security
IoT ecosystem essentially comprises of a network of enabled and smart sensing devices. Such devices drive the IoT system by means of data acquired and the purpose it is deployed for. However due to the openness as well as growing popularity and density of the IoT devices, it is generally under continuous scanning by the malicious users. These users try to gather legitimate user credentials and try for intrusion to the IoT ecosystem. Further they fraudulently take control of the devices associated, there by posing a great threat to the system as a whole. Hence there is a need to deliberate on the salient aspects which have an impact on the security of IoT system.
3.2.1 IoT Security Overview
IoT infrastructure and associated services are generally established using network enabled endpoint devices. Such devices function with integrated service platform components that work with similar technology to interact with many communication equipment, computing devices and IT services [1]. The terminal-end device of such system is primarily a TCP/IP network Protocol facilitated & internet enabled computing hardware. This could range from PCs, laptop computers, smart phones, tablet PCs, thin-client machines, network printers to some of the special hardware like IP Phone, IP Camera, smart metering systems, POS terminals, etc. In most cases, these devices are used for sensing and capturing data driving events to further enable their provisioning for various services and applications. In the event of any device of IoT ecosystem being compromised, related service could be controlled by attacker which could result in stealing of sensitive information and may be disrupting the services. For effective functioning of IoT ecosystem, undermentioned security aspects are required to be kept in mind with respect to network operators as well as service providers [2].
- (i) Availability: To ensure uninterrupted and errorfree communication between endpoint devices and their corresponding services.
- (ii) Identity: To ensure proper authentication among users, endpoints and the associated services.
- (iii) Privacy: To ensure prevention of any harm or misuse of the subscribed service-related information as well as end user’s location and data.
- (iv) Security: To ensure system’s integrity and communication confidentiality to further facilitate verification, monitoring and tracking of user’s activities and corresponding services.
3.2.2 IoT Security Requirements
IoT systems, due to their simultaneous and huge amount of data handling among many users, subsystems and devices are becoming lucrative destination for cyber-attack activities. Such attacks are mainly aimed for mischievously stealing and gaining sensitive system information by eavesdropping. Every connected device of the ecosystem could be potentially leading to some kind of sensitive and critical data of interconnected system of the IoT infrastructure. Due to their multidimensional impact, concerns related to data security are very much relevant and important. Risks associated with the IoT could be much higher as automated processing, decision making and interoperability along with security loopholes can show exponential results towards potential vulnerabilities.
A prominent and essential requirement related to IoT ecosystem is that devices are mandatorily required to be interconnected. Upon these interconnected resources various IoT activities like sensing, communicating and processing are facilitated. IoT system generally acquires information from end-nodes or devices. After acquiring, data is transmitted and processed at certain nodes designated for their processing towards accomplishment of associated complex tasks. The inherent capability of the system must provide security related protection for various applications for secured online transaction, as well as for maintaining data integrity. Accordingly, concerns for the need of a comprehensive, robust and a effectively secured mechanism merit its relevance to the constantly evolving IoT ecosystem.
From the above discussion, broadly the following three objectives for security aspects of IoT and the associated networks have been assessed. Firstly, desired mechanism to protect IoT devices and associated networking resources from attacks. Secondly necessary mechanism for protecting IoT related services and applications from unauthorized access and usage. Finally, protection of balance of the IoT resources from cascading effect attacks, as usage of compromised information. Similarly a compromised device may function like an attacking platform itself. To summarize these points, we can comfortably come to a conclusion that full proof identification establishment of devices and strict access control are principal factors for securing an IoT ecosystem.
At a broad level, security requirement aspects of IoT are classified into several categories which are discussed below:
- (i) Availability: This signifies that IoT assets of the system under consideration are made available for usage when request by entities which are authorized to do so and also by the genuine users. This factor allows desired data collection as well as prevents interruptions in the desired service. A fully functional Internet connected environment is essentially required to provide IoT availability in the true sense. Distributed Denial of Service attack (DDOS), Denial of Service (DOS) and flooding attacks generally regarded as threats to availability. However IoT service disruption can also arise from hardware and software failures which could affect service availability.
- (ii) Authentication: Things in IoT are essentially required to be made identifiable and also to be authenticated. Due to the complex nature of the IoT system, such process sometimes becomes extremely critical with respect to authentication. Since several entity types are associated like type of device, kind of services, specific service provider, corresponding unit for processing, etc., initial service session establishment is required among the IoT devices. Accordingly, desired mechanism for mutual authentication of entities in IoT system in all interactions is essentially required.
- (iii) Confidentiality: In any IoT ecosystem where there is a complex topological and logical networking of various sensors and data aquation devices, there is a need for exchanging certain enciphered data for having confidentiality. Various standardized and established key management technique are in use. In an IoT ecosystem, a specific type of key management systems requiring lesser processing loads needs to be followed for establishing trust among entities. Similarly lessor resources utilization is also a requirement for key distribution among them. Hence less processor, memory and network bandwidth requiring key management procedure is required to be adopted.
- (iv) Integrity: This implies to mechanism to ascertain that received information which is temporarily or permanently stored in IoT system has not been compromised in any way. Infrastructure of IoT ecosystem holds a number of sensitive information. Any attempt or successfully manipulated information may result in severe damage to the usage of the system. Data integrity is a critical factor for IoT ecosystem. A malicious user may use offensive means for manipulating critical information using a wrongly configured resource. Software vulnerability associated with the IoT application may even be explored for this purpose. Virus infections and other malicious programs could potentially be used for altering source of data. Hence it could adversely impact system integrity. With respect to authentication of devices, integrity aspect ensures genuineness. It also encompasses the identity of the systems. Also a non-compromised user is a vital aspect for facilitating desired service in the IoT system reliably. Certain service instances like mission critical military applications must maintain high integrity level over an IoT system.
- (v) Lightweight Protocols: This requirement is one of its kind for security. The specific requirement was visualized due to the inherent limitation regarding computing and power handling capabilities of the devices of the IoT system. Such thing is an indirect requirement, but a constraint which is required to be considered for design and implementation of various protocols for IoT networks. This is applicable both for encryption and authentication of data as well as device attached to IoT system. Underneath algorithms are essentially required to work with constraint capacities of the associated devices.
- (vi) Standardization and Policies: IoT ecosystem usually comprise of various devices of heterogenous characteristics. From the networking point of view the system may be of dynamic nature, where various IoT devices be put to active use depending on the dynamics of its utilization requirements. At the same time, it is also required for ensuring protection of acquired data, management and transmission of such data using a secured manner. Above all formalized means for enforcing desired set of regulations are required to meet the defined standards of the ecosystem. Service Level Agreements (SLAs) is required to unambiguously spell out all details of the services planned for being provided. Commonly followed network security protocols and standards may not be applicable such a system having dynamic characteristics. Implementing standardized set of regulations coupled with SLAs would be able to enhance mutual trust among users and devices leads to effective usage, remarkable growth to result in high scalability of the system.
3.2.3 Securing the IoT Infrastructure
The most commonly used public key cryptographic means are Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC). RSA calculates the product of two large prime numbers and tries to find difficulty of factoring it. However, ECC is a comparatively newer approach in the field of public key cryptography which is based on the algebraic structure of elliptic curves over finite fields. In the matter of performance, ECC is accessed to be faster than RSA. Hence it has become a default choice for the public key cryptosystem for resource constrained systems like IoT.
In the recent times Cryptographic Hash function has emerged as a new approach towards security by converting a bit string of variable length into a fixed-length hash value. Significantly the conversion function is a one way conversation function only, which cannot have any reverse function mechanism. The Hash functions maintains following four vital characteristics in terms of mathematics and algorithm: (i) Function of low computing complexity. (ii) It is an irreversible or “one-way” function. (iii) Non-feasibility for modifying input value with non-alternation of the hash (iv) As a matter of rule it must be followed by using a common and one hash, it must not be possible to have multiple corresponding inputs.
3.3 IoT Cloud
Proliferation of technological advancements in the areas of Cloud Computing as well as IoT ecosystem has shown the path for many new approaches. Amalgamation of these two technological paradigms has proven to have shown to have multiplicative advantages for their applications. In this section we will deliberate on this aspect of Cloud as well as IoT covering details of commercially available IoT Clouds as well.
3.3.1 Cloudification of IoT
Based upon the fundamental nature of cloud, it is capable to store and handle huge amounts of information from various devices of an ecosystem. At the same time where there are multiple and heterogenous devices in an ecosystem that acquire huge amounts of data, it becomes a difficult task for identifying as well as keeping track of all IoT device from where associated and corresponding data are collected. Computing capability of cloud in a virtual and unlimited processing scenario can handle such huge data processing requirements.
Considering an IoT environment, the sensing devices keep on acquiring the sensor data and temporarily store them before processing in a near real time environment. In this condition limited storage capability poses as a hindrance for data storage. At the same time processing of huge amounts of data in a near real time environment is a challenge for such resource limited IoT devices. At this point characteristics of unlimited computing power of Cloud come to play. Similarly, in a huge IoT eco system some of the sensing devices may not always be on active use. Hence malicious users may exploit them for intrusion to the system security. Hence the identity of the IoT devices is having equal importance as that of the legitimate users of the system.
For effective cloud implementation essential actors play their designated roles for IoT, as depicted in Figure 3.1. Details of their roles considered for each actor are listed below.
- (i) Things or IoT devices: This is used to collect and transmit data using various sensors for further processing.
- (ii) Processing node: This solves the purpose of processing input as well as output data acquired by things or devices.
- (iii) Trans-receiver: This sends or receives various instructions and other associated commands from the processing node or the devices.
- (iv) Actuator: This is used to initiate or trigger a thing or device for performing a specified assigned task by processing the input data.
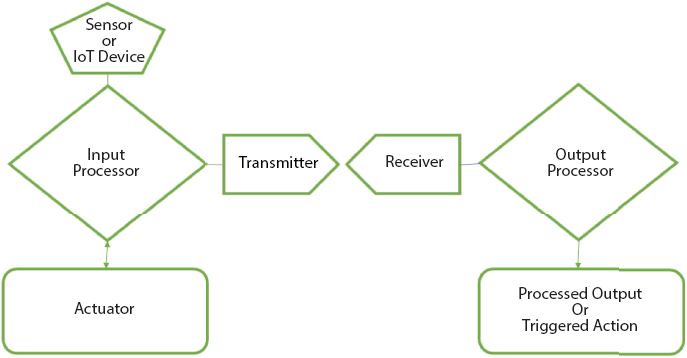
Figure 3.1 Actors of an IoT system.
The respective roles played by things or devices are generally reflected as incorporating themselves to cloud. Following such a structured approach, devices of the IoT ecosystem would be able to authenticate themselves to the cloud and also be able to process the acquired data in the desired manner with best utilization of cloud infrastructure. In the similar manner, receiver node of IoT network would also require necessary authentication method for obtaining authorization signifying as legitimate receiving entity. Considering data for being hosted in the cloud, establishing access controls as well as de-assigning users and IoT devices which might have been redundant or changed or no longer in use is a crucial thing for consideration. Figure 3.2 represents a generalized architecture of IoT Cloud. Further details on the same would be considered in the next section covering details on IAM Related Developments framework for the IoT cloud.
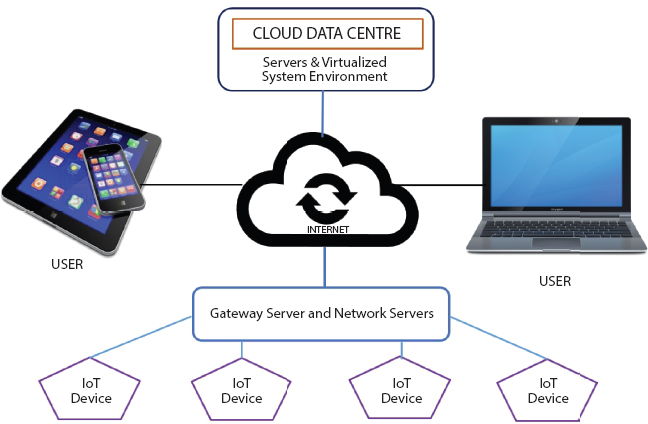
Figure 3.2 IoT Cloud system architecture.
3.3.2 Commercial IoT Clouds
Some of the commonly used and commercially available IoT Clouds are discussed below to provide desired insight for its utility and associated effects. In this chapter the broad aim is to bring out its security aspects specifically IAM and its relevance to our day to day lives.
- (i) Azure IoT Suite: This Microsoft proprietary product provides several services which facilitate users for interacting with corresponding IoT devices for data transaction and for performing various data related operation. Some of them may be aggregation of data, multidimensional data analysis, desired transformation of corresponding data for representing it suitably for day to day and usage on large scale commercially. Azure IoT platform is able to handle the challenge by presenting a complete IoT ecosystem with three varied and associated areas, specifically scaling, patterns for telemetry, and big data. Because of its applicability, this platform can be suitably utilized for different hardware devices, multiple operating systems using varied program coding languages.
- (ii) Brillo/Weave: This is an established platform of Google with a specific feature of faster implementation of applications over IoT network system. This has two numbers of specific defined backbones namely Brillo and Weave. Brillo is an Android operating based system and aims for the system development associated and embedded low power drawing devices. Weave manages the communication handler’s task facilitating interaction as well as messaging. Essentially Weave facilitates provision to register devices for cloudification. It also facilitates processing of all types of remote operative commands. The above mentioned functions are complementary to each other and also collectively form an IoT system. Brillo/Weave is most prominently intended towards smart homes and found to be user friendly for supporting general IoT devices like smart and net enabled speakers, lights, etc.
- (iii) AWS IoT Cloud: This platform is a product from Amazon Web Services (AWS) for the Internet of things. This system facilitates convenient interconnection of smart and other connected devices in secured manner with the AWS cloud. With AWS IoT, it is very easy to utilize various provided and subscribed AWS services like Amazon DynamoDB and Amazon S3. Above all AWS IoT applications significantly facilitate offline interaction among connected devices. This multi-utility nature and user-friendliness have effectively contributed for its vast acceptance and popularity.
- (iv) HomeKit: It is a popular Apple proprietary IoT framework. This IoT framework essentially aims to connect home based or domestic IoT devices. Using smart applications over Apple iOS based system, this enables management and control of connected devices and their corresponding accessories. For example, with HomeKit it is conveniently feasible to discover, configure, control, and manage HomeKit connected smart devices and their accessories in a secure way. Simultaneously, users are capable of initiating and controlling of the functioning IoT devices using Siri service of Apple. Presently, Apple iOS, its watchOS, and tvOS of Apple family are the only ones supporting the HomeKit functionalities.
- (v) Kura: This IoT project has been proposed and initiated by Eclipse. This project provides Java enabled network for IoT gateways designed for running M2M applications. Kura platform facilitates management of interaction among physical network of IoT devices and the public Internet or the cellular networks. Depending on the network type and its usage. Kura also enables abstraction and isolation of developers from underneath hardware, network subsystems. It also renews and optimizes development of prevailing software, by means of provisioning of APIs which permits and manages access to underlying hardware.
- (vi) ARM mbed IoT: This is an opensource platform planned and designed for application towards IoT devices based on ARM microcontrollers. It functions as an enabler for the ecosystem to build either an IoT standalone applications or a networked application. ARM mbed IoT platform aims for provisioning a scalable, connected, and secure environment for IoT devices by integrating mbed tools and related services, ARM mbed microcontrollers, mbed OSs, mbed Device Connectors, and mbed Cloud. ARM mbed IoT also provisions a common OS foundation for developing IoT frameworks. It is compatible with all standard communication protocols for connecting devices with each other and also with cloud. At the same time, it also supports automatic power management in order to solve the power consumption problem towards Green Cloud Computing.
3.3.3 IAM of IoT Clouds
A standardized requirement for all IoT systems is that, all the IoT devices are essentially required to know the identity of other devices of the system to interact with. For effective access management of the devices must be owned by a known owner. Here the known owner signifies a user or an entity which is uniquely distinguishable and whose identity can be established uniquely. Deployment of IoT system was initially based up on the IP address range allocated as well as the physical location of IoT devices in the specified geographical area of the system. Identity management of IoT was initially addressed by assigning object naming and IP addressing schemes. Since there are increasing efforts by research community for secured identification, authentication, as well as access management issues with IoT system, several new methods and means have emerged. A few such methods used for identity establishment and resource authorization are Ubiquitous code, ODI, short OID, EPC and RFID identifiers.
Subsequently cloud computing method was adopted to assign virtual identity to users and things. The main drawback of such method was to only handle the addressing virtual identity issues, without considering various underneath protocols for data transmission and their applications on the IoT environment. Similarly Wireless Sensor Network (WSN) protocol having identity management functionality as well as clustering of things has not been able to address the specific requirements of mobility of objects and their data transfer in the environment. Some other means were considered in IoT environment only for user identifications such as Open ID, Liberty Alliance and Shibboleth. Provisioning of identity management cycle using Cloud computing was initially based upon centralized solution model for authentication and authorization of resources. This was also used for proper resource accessibility and availability for desired application and service. However over a period of time it was realized that having a single point of failure in a centralized as well as critical system needs due attention. Alternatively desired mechanism needs to be adopted for tackle this issue.
Various ways and means to address this concern of IAM are going to be one of the prime focuses for the chapter. The following section analyzes how cloud enabled IoT solutions have attempted to handle IAM related matters in IoT ecosystem.
3.4 IoT Cloud Related Developments
Many efforts have been made by research community to efficiently handle the security related matters of IoT ecosystem. The authors of the chapter on Open Web Application Security Project (OWASP) [3] have listed and described most prominent 10 vulnerabilities associated with architecture of IoT. These features include important features like interfaces of entities related to the IoT architecture which are known as not secured, aspects like physical security of the system, inappropriately configured security configuration matters, insecure associated software and firmware.
In 2017 WAVE [4] was proposed. As best known to us, this was a novel and first approach using blockchain based and decentralized authorization in IoT environment. This made use of fine grained access control policies in conjunction with having smart contracts for event triggering functionality. However, functioning of blockchain nodes on constrained IoT devices was a troublesome matter. Hence to address this some trusted gateways were put to use for the devices in order to perform interaction to the blockchain network.
Several methods have been proposed by various researchers which require a detailed analysis for judging their efficiency and applicability along with related pros and cons. In the subsequent paras we are deliberation on prominent methods proposed since 2017 and also summarize their central ideas with a comparison among them.
Depending on the ad hoc nature of the IoT devices of the ecosystem for their access control, a requirement was felt for distributed IoT. Accordingly, capability-based access control (CBAC) proposed by Hussein et al. [5] proved to be well suited for the IoT environment compared to traditionally known access control models (Table 3.1).
Table 3.1 Comparison of access control method for IoT.
| Proposal year | Elementary method | Type of encryption | Key generation method | Access control | Mutual authentication | Anonymity of data | Integrity of data | Reference |
| 2017 | Decentralized | Symmetric | XOR Operation Based | Y | Y | N | Y | [5] [6] |
| 2018 | Centralized | Asymmetric | Random No Generation & Hash Function | Y | N | Y | Y | [7] [8] |
| 2018 | Centralized | Asymmetric | Elliptic curve cryptography | Y | Y | N | Y | [9] |
| 2018 | Centralized | Asymmetric | Fuzzy Extractor Gen Algorithm | Y | Y | N | Y | [10] |
| 2018 | Decentralized | Asymmetric | Elliptic curve cryptography | Y | Y | N | Y | [11] |
| 2019 | Centralized | Symmetric | Physical Unclonable Function And Fuzzy Extractor | Y | Y | Y | Y | [12] |
A computationally light weight authentication mechanism has been proposed by Aman et al. [6]. There is no need of any central server for storage mechanism of secret keys. This is based on Physical Unclonable Functions (PUFs) mechanism. Though it may be difficult to impersonate physical properties of the associated IoT devices but swapping of such devices with a malicious one could not be ruled out. The main drawback of the system was that, the mechanism required storing corresponding authentication credential details centrally. Accordingly, PUF based credentials kept is always a potential location for single point of failure.
In Vijaykumar et al. [7] introduced comparatively an updated authentication mechanism with respect to IoT devices. Better maintenance of privacy was achieved by using minimal information regarding used devices. This method used short group signatures and RSA algorithm. In order to have secured communication and associated generation and also distribution of encryption keys this is found to be a suitable mechanism. Anonymity feature for the signature holder’s identity is provisioned by short group signature mechanism. Prominent drawback of this mechanism is that it needed secret key to be stored in all associated devices for anonymizing identity. Limited storage availability with IoT devices was not in favor of this method. Above all this scheme needed very higher number of message exchange for authentication, thereby introducing unnecessary latency.
In Gong et al. [8] made use of remote validation mechanism for identifying node trust as well as for monitoring their behavior. This proposal consists of a model for measurement of trust where behavior of the sensing node data for transmission is considered. Hashing operation is used to prepare a threshold. Its storage was unable to address single point of failure. Observed drawback in a real time environment was pertaining to remote authentication deployment was unable to validate trust level of a node. Similarly, the mechanism could not provide tracking information regarding the associated nodes. Subsequently in order to generate trust threshold, a hash operation is performed and then the hash-value is stored at local server. The aforesaid means is found to be insecure with respect to vulnerability relating to single point of failure. High time and space complexity for processing resultantly makes it unsuitable for resource limited IoT devices.
In [9] the authors have proposed a specific mechanism which was intended for group authentication. Devices were required to be pre authenticated before being deployed in the system. This mechanism comprised of three aspects, namely the device, the group leader and subscriber server. It is mandatory for the device to be pre-registered and also pre-authenticated with the subscriber server for participating in the IoT network. The main drawback was single point of failure as the server was storing all credential and also desired authentication data regarding various groups of IoT devices.
The authors in [10] proposed blockchain technology for handling security issues in IoT. A decentralized authentication method was followed for IoT devices. It had a prominent drawback in terms of interoperability between different interconnected systems. There is a prominent drawback with this system that the devices of one could not be able to communicate with other system devices. Accordingly, this was not very useful for seamless integration between systems where there was requirement to communicate between IoT devices belonging to different systems.
In Feng et al. [11], emphasized regarding remote use of a concept of attestation mechanism for IoT as well as Cyber-Physical Systems. IoT devices being resources constraint, were not able to meet the requirements of complex computations. Accordingly basing upon physical behavior of devices a software based remote authentication method was proposed. This needed storage of hardware properties and other related details of IoT devices on a local server. Whenever a device needs an authentication, corresponding hardware signature of device is matched with the details available at the local server. Further it was observed to be less efficient involving resource constrained devices.
Authors in [12] proposed a two-factor authentication mechanism for IoT devices which was easier for processing. It incorporated authentication details of IoT device along with physical properties of the devices. Along with device identification it was found useful for eliminating any type of physical attack on the device. To name a few, it could be impersonation attack or even side channel attack. Apart from processing latency delay, prominent drawback of this mechanism was dependent on storage of a centralized server.
3.5 Proposed Method for IoT Cloud IAM
A Distributed Ledger is implemented for the establishment of a Blockchain. A blockchain essentially is a decentralized, distributed and also an immutable shared ledger which keeps resources and all transaction within a peer-topeer network. From its structural point of view, it contains interconnected blocks of data which are timestamped and also validated with consensus algorithm. Each block contains a list of all transactions and a hash to the previous block. The blockchain uses Elliptic Curve Cryptography (ECC) and Secured Hashing (SHA-256) cryptographic means to ensure data integrity and authentication. Blockchain stores entire past events of all transactions after due verification. Such verification is done with a majority consensus of miner nodes, which also are used to validate each transaction. Out of the two categories, Private or permissioned Blockchain is used for restricted access to a certain group of participants, whereas Public or permission less Blockchain is open for anyone to access. Permissioned Blockchain is a preferred choice to provide privacy solution implementation and also better access control enforcement.
3.5.1 Distributed Ledger Approach for IoT Security
Both academia and industry have conducted several researches to arrive at a conclusion that Distributed Ledger and Blockchain technology can potentially play a crucial role to manage, control and secure all networked device. Schematic diagram of Blockchain empowered IoT Cloud is depicted at Figure 3.3. Accordingly, this can be seen as a promising security solution to counter the challenges with IoT related security issues. Some vital features of blockchain which are useful for IoT in general and IoT security specifically are described below.
For Addressing: Typically, Blockchain uses 160 bit address. As a standardized cryptographic function in Blockchain, it is capable to address 20 bytes or a 160 bit hash of the public key which is the output of Elliptic Curve Digital Signature Algorithm (ECDSA). Hence it is found to be a better addressing means than IP V6 (128 bit) for provisioning of Global Unique Identifier (GUI) at the time of allocating and assigning address for an IoT device.
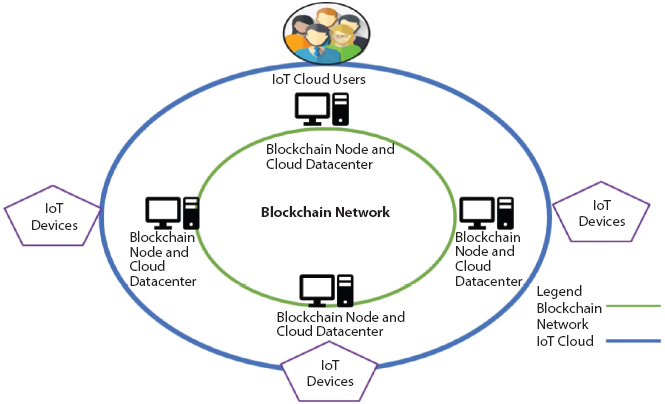
Figure 3.3 Blockchain empowered IoT Cloud.
For Authentication: Smart contracts can be deployed with Blockchain to provide authentication using decentralized means. This can also be used to provide authentication to smart devices connected to the IoT system. Inherent advantages of Blockchain can also be suitably utilized for effective authentication establishment.
For Authorization: Using Smart contracts deployed over Blockchain and also integrating multiple smart contracts, effective authorization and access control mechanism for connected IoT devices can be established. This mechanism is found to be faster and efficient compared to commonly used protocols like Oath, Open ID, etc.
For Privacy: Smart contracts are such versatile tools, whereby using this over Blockchain enables ensuring data privacy. This technique can control access by enforcing a designated set of conditions and time to allow or deny access to users or group of users to control the acquired data or even transit data for the IoT system. Smart contracts can also be programmed to decide on patch updation. Using this means, changing of ownership and provisioning of IoT devices are found to be smooth exercises.
For Data Integrity: In a Blockchain based arrangement, the connected IoT devices are cryptographically safeguarded and signed by a verified and legitimate sender who is holding a unique public key and GUID. Secure storage mechanism along with its event time stamping of the distributed ledger facilitates data integrity for the interconnected IoT devices. For example, to maintain data integrity in a distributed system TrustChain is proposed with an aim to perform trusted transactions using blockchain.
For Identity of Things: Blockchain technology can be used to identify IoT devices with a set of attributes. Attribute management for the connected smart devices of IoT system holds a key factor for the Identity and Access Management (IAM). Attributes in terms of deployment location coordinates as registered by GPS, make, model and device serial no of IoT device along with its ownership, change or renovation of ownership play a crucial role with respect to identity of things.
3.5.2 Blockchain for IoT Security Solution
Emerging technologies like IoT as well as Bockchain has presented many technological advantages. Subsequently advantages of integrating Blockchain and IoT have been studied and analyzed by many researchers. The primary aspect of IoT device level security is mainly expected to cover diversified factors like managing huge amount of data, privacy preservation of user, trust assurance, confidentiality and also integrity. It also merits its significance related to advantages associated with Blockchain and distributed ledger applications. In this subsection we will consider some of the prominent research contributions addressing security concerns of IoT using Distributed Ledger technology with Blockchain.
A Blockchain Connected Gateway has been proposed in [13] for maintaining security and adaptive users’ privacy, where the authors have made use of Bluetooth Low Energy empowered IoT devices. Crucial data of user are protected from being accessed without user’s consent by means of the Gateway. To implement authentication and also secrecy in terms of privacy preservation, a digital signature scheme is also proposed. As basic fundamental architecture of the system, blockchain networks are applied to address privacy related issues between application providers of IoT and their users by encrypting users’ applied choices and keeping them for further reference in the network.
Authors have highlighted in [14] regarding difficulty for the mobile and handheld devices for performing required computation for proof of work for reaching a consensus due to their resource limitations. Hence a concept of edge computing was introduced wherein such mobile devices are facilitated to use the resources present at the level of edge devices for computations in order to get the proof of work.
A blockchain based data storage scheme was proposed in [15] for protecting and storing huge volume of generated data by IoT devices. This secured method applied register and forward methodology. The devices located at the edge actually collect data from the IoT devices. Then this data is registered and associated with the particular IoT device in the blockchain and subsequently forwarded to a Distributed Hash Table (DHT). Blockchain based cryptographic means are used to address queries on specific data. It is registered as a transaction in the blockchain for verification of authentication. After being successfully authenticated, DHT then releases the desired data. In this approach blockchain works like a trusted third party (TTP) for storing of data and its management, provides protection to the stored data and also facilitates user authentication.
A distributed cloud architecture was proposed in [16] using blockchain utilizing Software Defined Networking (SDN) enabled controller fog nodes as edge nodes in the system. The edge nodes process data analysis, their classification for the huge volume of acquired data from the IoT devices present at the edge of the network. This system also took care of efficient data traffic management of the system using data distribution within the fog and associated edge nodes.
To improve scalability and also for eliminating the role of a TTP, in Manzoor et al. [17] have presented a blockchain based proxy controlled re-encryption scheme [18]. This is implemented with deployment of Smart Contracts. In this scheme the proxy re-encryption facilitates data transparency and mapping between the data owner and the registered user associated to the Smart Contract. In this, secure storage and sharing of the IoT acquired data’s confidentiality is maintained by first performing data encryption before their storage on cloud and then subsequently re- encrypting the stored data before their sharing among users.
In Kim et al. [19] have suggested an idea based on Blockchain of Things (BoT) model to address the corresponding hacking issues of IoT devices. A specialized method called color spectrum chain blockchain technique is used. This proposal tried to address the security vulnerabilities in the sensors. In this technique Thin Plate Spline (TPS) is used along with multiple-agreement algorithm to access required security strengths of the system.
A fingerprint verification based automatic door locking system was proposed and implemented using mobile handsets in [20] based on blockchain technology. This system implementation has been proved to be efficient about the prevention of attempt to forge, any move to tamper or leak biometric information of the users. In the system the users could authenticate themselves using a mobile handset with biometric fingerprint printing authentication coupled with blockchain based security measures.
3.5.3 Proposed Distributed Ledger-Based IoT Cloud IAM
Distributed Ledger implementation needs a basic platform namely a Blockchain. As the blockchain facilitates distributed database and essential characteristics of immutability, Distributed Ledger implementation can be done upon this platform efficiently. Blockchain as a technology can easily be integrated with access control and data sharing mechanisms. This way it may provide a new means for elimination of shortcomings of the age old traditional schemes. Blockchain provides solutions to many problems that are more effective to provide data integrity, fairness, authenticity, security, and distribution [21]. By virtue of the inherent cryptographic properties and decentralized storage and processing, as a technology Blockchain has been assessed as a suitable method for providing IAM services for IoT ecosystem as deliberated by the authors of [22, 23].
In any cryptographically secured system key management plays a vital role. In our proposed method Elliptic Curve Digital Signature Algorithm (ECDSA) may be conveniently used for generating public and private keys for the devices and the IoT clusters associated with Blockchain nodes. It provides the same level of security as with the RSA method. We have selected this approach depending upon a detailed comparison between encryption algorithms described by [24]. The ECDSA based program needs comparatively reduced power consumption from other similar methods. Hence it also suits the requirements of IoT infrastructure, keeping the constraint resources availability of the IoT devices.
Figure 3.4 above represents a schematic diagram of the proposed Blockchain based IoT Cloud model for the IAM service implementation. Vital aspects of the proposed model are as follows.
- (i) Establishment of an Ethereum-based private blockchain as a core of the distributed ledger network.
- (ii) Device address and user Ids are mapped over the nodes of the blockchain.
- (iii) Storage of the acquired data from the devices is done off the blockchain inn the cloud storage.
- (iv) Use of multiple smart contracts for ensuring ‘user’ and ‘things’ mapping for effective service management as well as identity management.
- (v) Use of blockchain consensus mechanism for verification of data access as a registered event logged in the blockchain
- (vi) Use of cloud nodes for processing and relieving the edge devices from loading of processing due to their constrained resources availability.
- (vii) Superimposing the IAM functionality of Cloud with the inherent advantages of blockchain related information security and event logging.
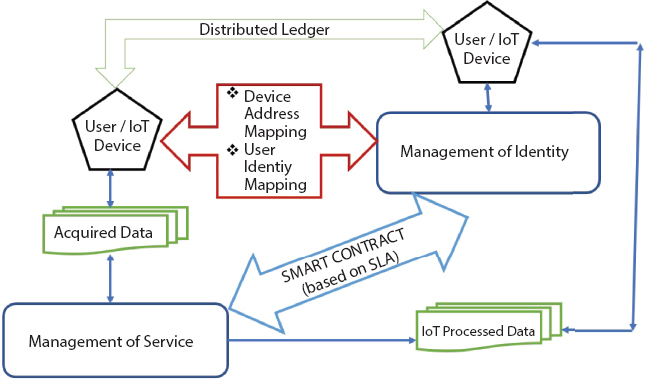
Figure 3.4 Proposed model of blockchain-based IoT Cloud for IAM.
3.6 Conclusion
Steadily the use of IoT devices is making ingress to our day to day lives affecting improvements towards our living conditions. It is quite evident to note that IoT is one of most prominent and emerging technologies in today’s scenario. The proliferation and application of IoT in all spheres of life is ever increasing for ease of life as well as efficient functioning of things. At the same time the value of sensitive data and its adverse effect to a fully functional IoT network is not hidden from anyone. It has been established in many researches that secured storage of data both in static and transit plays a vital role in the domain of information security. However as a new and emerging trend, the identity of entities of IoT as well as proper access management is emerging as a more crucial reason in the dynamics of information security matters. Accordingly, IAM is going to play a critically prominent role in future time to come.
Blockchain and distributed ledger empowered security technique have proved their significance as potential technology for tomorrow’s world. But there is a way forward for its effective application and wide acceptance as a decentralize approach based solution towards security of an IoT cloud. Gradual improvement in efficiency and the consensus algorithms used by blockchain, needs comparatively heavy computational loads to be addressed for its effective use. Thus without introducing significant overhead, the design of a less computation intensive consensus mechanism for resource constrained IoT devices cloud could be more pertinent for security solution empowered with blockchain and using distributed ledger based IoT ecosystems.
References
1. GSMA, IoT Security Guidelines for Endpoint Ecosystems, https://www.gsma.com/iot/iot-security-guidelines-for-endpoint-ecosystem/, Last accessed: 07 Nov 2020.
2. GSMA, IoT Security Guidelines for Network Operators, https://www.gsma.com/iot/iot-security-guidelines-for-network-operators/, Last accessed: 08 Nov 2020.
3. Miessler, D., Securing the internet of things: Mapping attack surface areas using the OWASP IoT top 10, in: RSA Conference, 2015.
4. Andersen, M.P., Kolb, J., Chen, K., Fierro, G., Culler, D.E., Popa, R.A., WAVE: A Decentralized Authorization System for IoT via Blockchain Smart Contracts. Tech. Rep., 2017.
5. Hussein, D., Bertin, E., Frey, V., A Community-Driven Access Control Approach in Distributed IoT Environments. IEEE Commun. Mag., 55, 3, 146–153, 2017.
6. Aman, M.N., Chua, K.C., Sikdar, B., Mutual authentication in IoT systems using physical unclonable functions. IEEE Internet Things J., 4, 5, 1327–1340, 017.
7. Vijayakumar, P., Chang, V., Deborah, L.J., Balusamy, B., Shynu, P.G., Computationally efficient privacy preserving anonymous mutual and batch authentication schemes for vehicular ad hoc networks. Future Gener. Comput. Syst., 78, 943–955, 2018.
8. Gong, B., Zhang, Y., Wang, Y., A remote attestation mechanism for the sensing layer nodes of the Internet of Things. Future Gener. Comput. Syst., 78, 867–886, 2018.
9. Roychoudhury, P., Roychoudhury, B., Saikia, D.K., Provably secure group authentication and key agreement for machine type communication using Chebyshev’s polynomial. Comput. Commun., 127, 146–157, 2018.
10. Hammi, M.T., Hammi, B., Bellot, P., Serhrouchni, A., Bubbles of trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur., 78, 126–142, 2018.
11. Feng, W., Qin, Y., Zhao, S., Feng, D., AAoT: Lightweight attestation and authentication of low-resource things in IoT and CPS. Comput. Netw., 134, 167–182, 2018.
12. Gope, P. and Sikdar, B., Lightweight and privacy-preserving two factor authentication scheme for IoT devices. IEEE Internet Things J., 6, 580–589, 2019.
13. Cha, S.C., Chen, J.F. et al., A blockchain connected gateway for BLE-based devices in the Internet of Things. IEEE Access, 6, 24639–24649, 2018.
14. Xiong, Z., Zhang, Y. et al., When mobile blockchain meets edge computing. IEEE Commun. Mag., 56, 8, 33–39, 2018.
15. Li, R., Song, T. et al., Blockchain for large-scale internet of things data storage and protection. IEEE Trans. Serv. Comput., 12, 5, 762–771, 2018.
16. Sharma, P.K., Chen, M., Park, J.H., A software defined fog node based distributed blockchain cloud architecture for IoT. IEEE Access, 6, 115–124, 2018.
17. Manzoor, A., Liyanage, M. et al., Blockchain based proxy re-encryption scheme for secure IoT data sharing, in: 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), pp. 99–103, May 2019.
18. Lu, Y. and Li, J., A pairing-free certificate-based proxy re-encryption scheme for secure data sharing in public clouds. Future Gener. Comput. Syst., 62, 140–147, 2016.
19. Kim, S.K., Kim, U.M. et al., A study on improvement of blockchain application to overcome vulnerability of IoT multiplatform security. Energies, 12, 3, 402, 2019.
20. Huh, J.H. and Seo, K., Blockchain-based mobile fingerprint verification and automatic log-in platform for future computing. J. Supercomput., 75, 6, 3123–3139, 2019.
21. Liu, H.C., Lin, Q., Wen, S., Blockchain-enabled Data Collection and Sharing for Industrial IoT with Deep Reinforcement Learning. IEEE Trans. Industr. Inform., 15, 3516–3526, 2018.
22. Hammi, B., Khatoun, R., Zeadally, S., Fayad, A., Khoukhi, L., IoT technologies for smart cities. IET Netw., 7, 1–13, 2017.
23. Baker, T., Asim, M., MacDermott, A. et al., A secure fog-based platform for SCADA-based IoT critical infrastructure. Software Pract. Exp., 2019.
24. Goyal, T.K. and Sahula, V., Lightweight security algorithm for low power IoT devices, in: 2016 International Conference on Advances in Computing, Communications and Informatics (ICACCI), pp. 1725–1729, 2016.
*Corresponding author: [email protected]
