6
Examining Security Aspects in Industrial-Based Internet of Things
Rohini Jha
BIT Mesra, Ranchi, India
Abstract
Nowadays, the internet of things (IoT) is widely utilized as a digital application. It’s quite evident that IoT will contribute to unmatched growth and productivity as business leaders are collaborating together to reap the advantages of this potential. Primarily it’ll impact the success of most sectors like agriculture, energy, transportation, and logistics to call a couple of. Industries already had sensors and devices collaboration for digital communication called machine to machine to machine (M2M) architecture. The web of Things has led to the development of intelligent devices which allows transfer of knowledge from physical devices to the web. Therefore, huge risk and opportunity lies in this technology. The economic Internet of Things (IIoT) is employed for an industrial purpose, so it’s named as Industrial Internet of Things (IIoT). Moreover, it’s utilized altogether smart real time application to strengthen the performance of a specific system. It also progresses the dependability, maintainability, and fitness of the measured industrial procedures by sensor systems to watch the gadgets failure in the early stage. Securing the information by the crypto model is an extremely easy task but in some cases efficient malicious events might break the crypto procedures by their harmfulness. Moreover, the key issues in IIoT are controlling the administration access. Additionally, for the automated function process of IIoT, industry 4.0 procedures were used efficiently. Thus, to acknowledge this attack in IIoT frame several mathematical models and optimization frameworks must be implemented. Therein Industrial IoT (IIoT) is the foremost trending topic in the digital industrial world. Moreover, the IoT is employed in various ways to know its target. Additionally, the automation function of IIOT is defined as industry 4.0. Henceforth, this chapter is an endeavour to reveal the necessity of security in IoT platforms and applications of IIoT intimately. In past decade, they have mostly attacked the IoT gadget, for that cyber security is introduced to deal with the cyber-attack. Furthermore, one of the chief attack models in IIoT is Botnets and denial-of-service attacks. These attacks happen in several ways, once it’s occur then it is hard to predict and stop them. Chapter highlights many suggestions described by diverse authors detailed in a tabulated form.
Keywords: Cyber security, cyber-attack, information security, malicious events, digital applications
6.1 Introduction
The latest rapid climb of IoT and its capability offer various kinds of functions to strengthen the digital application [1]. Moreover, the advancement of IoT has offered a versatile and straightforward life by reducing the technical risk for a scientist and a business person [2]. Especially, marketing and finance have received many benefits with the utilization of the IoT device. It regularly meets different security threats because of its flexibility [3] in other side. Whenever the IoT network is expanded in a large frame, the potential malicious event also grows as twice [4].
The process protection is described as a function or module that secures the knowledge against malicious acts [5]. Thus maintaining the knowledge integrity could even be an enormous concern to strengthen the IoT data sharing process [6]. So, within the IoT the info is secured under several conditions with the maximum threshold [7]. This whole survey contributes the rationale security model in IoT and different quite present security for the IoT device [8]. Additionally, the IoT based cloud paradigm is concentrated to supply the safety wall for the entire global data analytics, storage and knowledge diffusion [9]. The fundamental process of IoT frame is drawn in Figure 6.1.
The ocean of digital application is cloud applications and its service [10]. Nowadays, the medical field has also grown up with the support of IoT as IoT based healthcare applications. Thus the chief area of IoT is monitoring the assigned target with the assistance of sensor nodes. Also, the intruders present in wire free frame can damage the transferred data [11]. Thus, the intruders have diverse objectives and motives to injure the target system. Moreover, the intruders have various resources like access, risk and skill and portability of risk severity stage for occurring malicious events [12]. The individual attackers are technical professionals who perform the work by own with no help. In addition to this, the engineering methods are mostly utilized by individual hackers [13]. Moreover, the social institutions like, bank, financial institution are chief goal of individual hackers. Also, the OS, which is employed in PCs, mobile and laptops have the severe attack vulnerabilities of individual hackers [14]. In this current survey article, the usage of IoT and performance of IoT before introducing security is surveyed. Moreover, several security models and threat models are discussed elaborately to satisfy the goal and need of data security for IoT gadgets. Subsequently, the limitation of every security model is discussed and tabulated in a scientific manner.
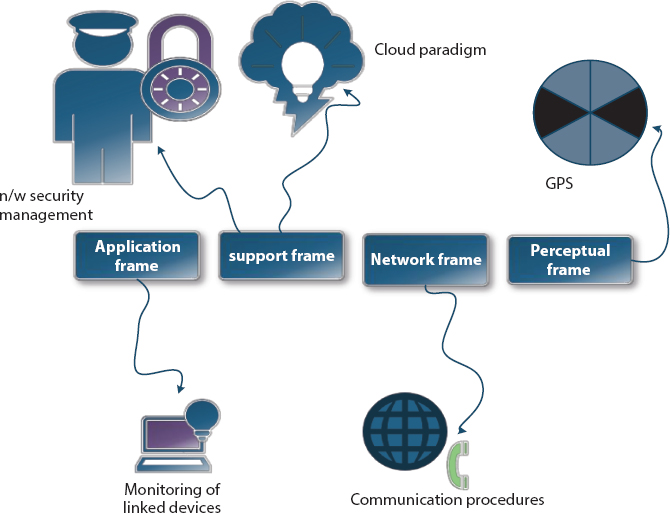
Figure 6.1 Basic model of IoT frames.
6.2 Process Frame of IoT Before Security
The frame IoT is described as a wide heterogeneous connectivity that has different pattern frames of communications. The initial stage to model security threat is cyberspace, which is described to structure the cyber security. Additionally, the need of IoT dramatically announced the cyber threat in landscape [15]. An efficient frame to initiate the security analysis is detection threats, additionally; to collapse the data delivery process in IoT several tools are introduced like worms, virus, Trojan horses, ransom ware, etc. Also, a harmful threat making tool cyber landscape is botnets [16]. he malicious events come under normal category as software or code that is secretly installed in a device without authentication [17]. The threats in transmission medium have the potential to modify the authorized data and misuse the key statistics. Furthermore, in IoT device several and different risks are rising, where the key risk in an IoT device is, it allows all connected IoT gadgets to broadcast the message [18]. In such cases, if any of the IoT gadgets became victim then the knowledge is misused by its own and controls the other connected IoT gadgets [19]. The digital assaults in linked IoT gadgets not only affected the digital area but also created the physical risks [29]. The various IoT applications are defined in Figure 6.2.
With the huge quantity of linked gadgets in an internet channel, the security became the key concern in data sharing medium. Also, the frame authentication in IoT model is insufficient in nature [20]. So, several password strategies are used to protect the information or statistics from third parties.
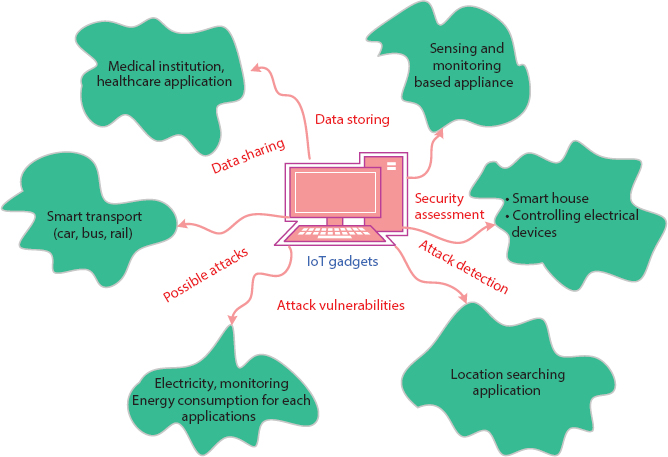
Figure 6.2 IoT application.
6.2.1 Cyber Attack
The attack as cyber isn’t within the tiniest amount of the new victim in the IoT frame, thus the cyber-attacks often disturb the digital applications. So, Abomhara and Køien [30] described the threat of IoT attack and need for security in the IoT framework [21]. Providing the protection measure in the IoT wireless environment is a varied task to secure the transfer of data. So, the authorized module is developed within the cyber security frame to verify the authenticated person and devices [22]. Additionally, the privacy target is the key degree to figure out the security range of the developed IoT frame. Moreover, the smart house based IoT models are hugely vulnerable to malicious events. Ali and Awad [31] projected the vulnerability assessment, critical threat frame model to estimate the dangerous features of smart homes. Furthermore, numerous security vulnerabilities are discussed. The operation of IoT tools for structuring the smart houses with reverence to mechanization and process of control creates new protection issues. But unlike in gadgets, IoT in house application had different requirements to understand the goal.
Moreover, the varied IoT has dramatically increased supported user suggestions. Also, the security threat in the IoT frame model can be treated with high rate flexibility and reliability.
6.2.2 Security Assessment in IoT
As the security issues in IoT become a serious threat in future IoT development, Li et al. [25] proposed one of the trust schemes in IoT paradigm to meet the security issues. Thus, the frame trust process has several trust modules like agent based, terminals based and so on. Hence, its performance is estimated by broadcasting the required pack of information. The difficulties in IoT frame is described in Figure 6.3.
The security model in network and data broadcasting frame must be functioned with the following attributes such as confidentiality, unreliability, identification and integrity. The fundamental layer of information security is perceptual level [23]; it gathers all the information about the connected system. The second layer is internet layer that functions to broadcast the data [26]. In addition, the cloud paradigm is broadly accepted by enterprises and individuals for multimedia information. In some modules, different encoding schemes are used to secure the data from theft. Thus, Sukumar et al. [27] proposed encoding based transform mechanism to secure the data from the malicious event. Also, the experimental values are analyzed for noise ration and other different parameters. The application IoT is designed with several desired signal connectivity without the use of wire [24]. The IoT frame is a heterogeneous structure, where the flexible intelligence and moving capability makes it its vast demand expertise. In addition, the IoT is worn in major applications for different processes so it met several issues and is vulnerable to get attacked. At the same time, the IoT is flexible for hardware based components also for monitoring and statistics gathering [28]. IoT is flexible to utilize in embedded applications, in addition the domain IoT is elaborated in the terms of
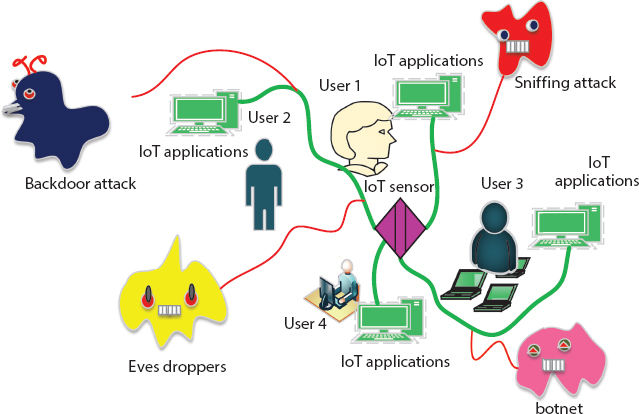
Figure 6.3 Attack difficulties in IoT environment.
- Network oriented
- Things based
- Semantic based.
Moreover, the explanation of IoT gadgets are too long that contains several elements related to physical model.
6.2.2.1 Security in Perception and Network Frame
The key process of perception frame is sensing, which is hugely worn to collect the statistics of the specific event. Moreover, to collect the data different sensors were utilized based on the particular applications. Also, it is open to utilizing in real time appliances. However, the chief issue in this frame is information leakage [58]. The information leakage tends to attain very less confidential measures. Beside this, another one main difficulty is structure because the structure topology of the IoT environment is differed dynamically. On the other hand, it met the difficulties because of attacks; the assault that happened in the wireless frame is more vigorous than in the wired network [59]. Also, the malicious hubs consumed maximum quantity of energy, thus it damaged the IoT gadgets. In addition, the node that is present in the wireless model is limited with energy and power. So, if any hubs consumed high energy, then it stops the entire data broadcasting process. Hence, the security in the IoT frame is described in Table 6.1.
Table 6.1 Security assessment in IoT network frame.
| Author and year | Frameworks | Merits | Demerits |
| Kimani et al. [50] 2019 | The framework for describing key issues in IoT gadget |
|
|
| NirKshetri [51] 2017 | Cloud blochchain |
|
|
| Sohal et al. [52] 2018 | Virtual honey pot gadget |
|
|
| Naik and Maral [53] 2017 | Attack mitigation |
|
|
| He et al. [54] 2016 | Victim handle suggestion |
|
|
| Cheng et al. [55] 2017 | Traffic aware scheme |
|
|
| Mohan [56] 2014 | Evaluation cyber threat |
|
|
| Furfaro et al. [57] 2017 | Agent based virtual investigation |
|
|
In network frames, the transportation frame is also termed as network layer. The process of this frame is gathering the previous frame outcome with the support of any communication protocols [60]. Because of different protocol usage it has met numerous issues like intrusion, hacking, etc. In addition, the transportation frame is the chief layer in an entire IoT system model [61]. Here, if any denial based attacks happens then the service of network is blocked.
- Sybil malicious event: when the malicious Sybil is present in the network medium it creates the node by its own and make it as victim. Moreover, it function like as good hub in front of entire IoT frame but during the data broadcasting it drops partial or whole data.
- Malicious sinkhole: here, the attackers cooperates with neighbouring node to divert the data delivery process by the attract function. Consequently, it collapses the network frame.
- Denial attacks: it tends to make data and routing overhead. In addition, the extreme quantity of denial attacks tends to raise botnets attacks.
6.3 Attacks and Security Assessments in IIoT
The Industrial Internet of Things (IIoT) is utilized for industrial purpose, so it is named as IIoT. Moreover, it is used in all smart real time applications to improve the performance of a specific system. It also progresses the dependability, maintainability, and fitness of the measured industrial procedures by sensor systems to monitor the gadgets failure in early stage.
Securing the data by crypto model is a very easy task but in some cases efficient malicious events might break the crypto procedures by their harmfulness. Moreover, the key issue in IIoT is controlling the administration access. In addition, for the automatic function process of IIoT, industry 4.0 procedures were used efficiently. Thus, the systematic work associated with IIoT is described in Figure 6.4 and Table 6.2.
In IIoT, the sensed statistics are generally saved in the form of unreadable text in fog nodes. The reason of storing the cipher text in cloud is that cloud based storage is vulnerable to different kinds of malicious activities. To reduce the security issues, before saving the data encryption procedure is utilized to encrypt the data to improve the confidential rate then it is stored in fog nodes. In addition, to find the solution of security threats, primarily the present malicious event should be predicted. Thus to recognize the present attack in IIoT frame several mathematical model and optimization framework must be implemented.
The chief application of IIoT is described in Figure 6.5 the significant applications in IIoT are energy, electricity, transportation, and telecommunication and so on.
6.3.1 IoT Security Techniques Analysis Based on its Merits
By the literature survey, several proposed works aim the block chain based technology to secure the data in IoT frame against malicious events. Based on different modules, the confidential rate is compared in Figure 6.7.

Figure 6.4 (a), (b), (c) Security works on IIoT.
Table 6.2 Security assessment for IIoT.
| Author and year | Models | Merits | Demerits |
| Li et al. [25] 2011 | Trust agent architecture |
|
|
| Sukumar et al. [27] 2020 | Steganography schemes |
|
|
| Weber et al. [29] 2016 | examination of legal based cyber security |
|
|
| Abomhara and Køien [30] 2015 | kind of threat in IoT frame |
|
|
| Ali and Awad [31] 2018 | Evaluation of security vulnerability in home based smart applications. |
|
|
| Boyes et al. [32] 2018 | system architecture of Industry 4.0 (IIoT) |
|
|
| Yu et al. [33] 2019 | optimized frame work for IIoT |
|
|
| Puri et al. [34] 2020 | blockchain technology |
|
|
| Petrenko et al. [35] | integrated network for IIoT applications |
|
|
| Sha et al. [36] 2016 | Sensitive data defender in IIoT |
|
|
| Karpisz and Kiełbus [37] 2019 | Machinery framework |
|
|
| Chaudhary et al. [39] 2018 | crypto models |
|
|
| Bajramovic et al. [41] 2019 | different design of security models |
|
|
| Raposo et al. [42] 2019 | sensing architecture |
|
|
| Eden et al. [43] | framework for control managing |
|
|
| Yan et al. [44] | hinge categorization frame |
|
|
In addition, various security research fields for IoT are elaborated in Figure 6.6. Also, this security flow model is the basic process of IoT security in wireless medium; it is common for both IoT and IIoT.
To secure the data in IoT environment several technique frames are utilized such as deep learning, machine learning, and optimization model, crypto procedures and so on. Usually, the optimization model is processed to optimize the frame models that are minimum or maximum. In addition, deep learning has hyper parameters comparing machine learning frame. Because of these hyper parameters, the deep neural model has attained high confidential rate and high malicious prediction rate. Moreover, the fitness of optimization procedure in deep or machine learning function can obtain good outcome than the individual machine and deep learning techniques.
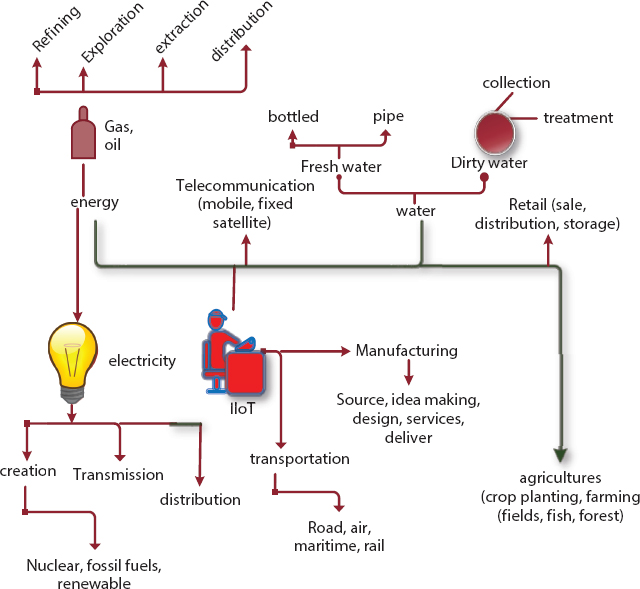
Figure 6.5 Applications of IIoT.
To ensure the security in IoT frame, numerous methods were developed, which are diagrammatically revealed in Figure 6.8. Moreover, the graph shows that in the recent year 2019 many security and IoT research works were done. Thus it verified that the research of IoT will tremendously increase in the future.
6.4 Conclusion
Numerous research works associated to IIoT and IoT are surveyed broadly, including the merits and limitation of each work which are explained in tabular content. Moreover, from the survey it is concluded that IoT has met several diverse issues to broadcast the data to the specific user. So in the modern era, numerous and efficient security paradigms are developed in the IoT frame. However, it is suffered from several new attacks because of its openness frame model. So, whenever the security model is developed similarly a hacking model is also grown in rapid manner. However, it is worn by all digital appliances because of its advancement and flexibility. Thus it is mostly utilized for location searching, monitoring, information gathering and storing.
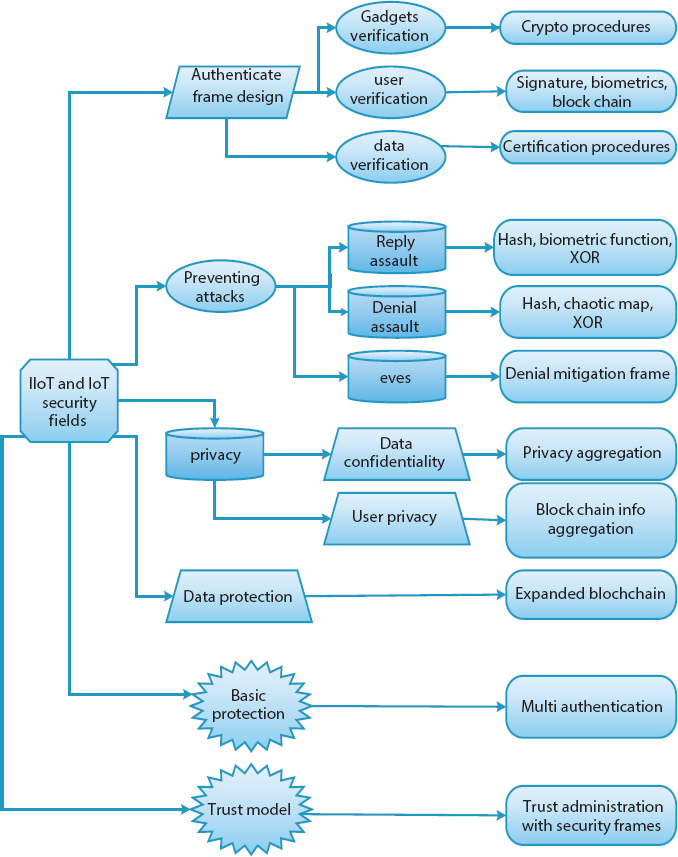
Figure 6.6 IoT security areas.

Figure 6.7 Advantages of several techniques.
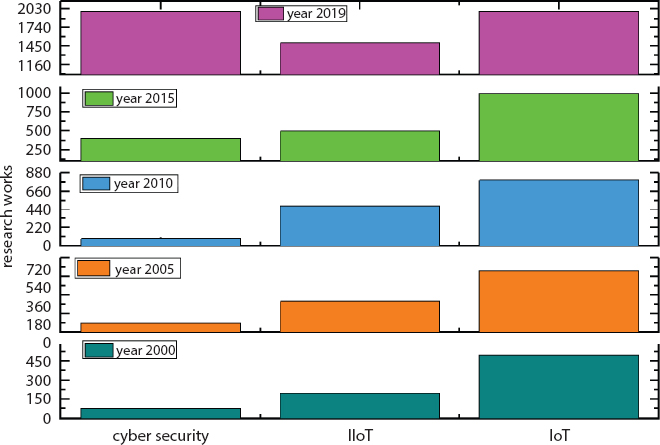
Figure 6.8 No. of research work in year wise.
References
1. Tan, L. and Wang, N., Future internet: The internet of things. 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), vol. 5, IEEE, 2010.
2. Atzori, L., Iera, A., Morabito, G., The internet of things: A survey. Comput. Netw., 54, 15, 2787–2805, 2010.
3. Xia, F. et al., Internet of things. Int. J. Commun. Syst., 25, 9, 1101, 2012.
4. Zanella, A. et al., Internet of things for smart cities. IEEE Internet Things J., 1, 1, 22–32, 2014.
5. Li, S., Xu, L.D., Zhao, S., 5G Internet of Things: A survey. J. Ind. Inf. Integr., 10, 1–9, 2018.
6. Miorandi, D. et al., Internet of things: Vision, applications and research challenges. Ad Hoc Netw., 10, 7, 1497–1516, 2012.
7. Da Xu, L., He, W., Li, S., Internet of things in industries: A survey. IEEE Trans. Industr. Inform., 10, 4, 2233–2243, 2014.
8. Stankovic, J.A., Research directions for the internet of things. IEEE Internet Things J., 1, 1, 3–9, 2014.
9. Gubbi, J. et al., Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst., 29, 7, 1645–1660, 2013.
10. Kopetz, H., Internet of things, in: Real-Time Systems, pp. 307–323, Springer, Boston, MA, 2011.
11. Roman, R., Najera, P., Lopez, J., Securing the internet of things. Computer, 44, 9, 51–58, 2011.
12. Wu, M. et al., Research on the architecture of Internet of Things. 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), vol. 5, IEEE, 2010.
13. Kortuem, G. et al., Smart objects as building blocks for the internet of things. IEEE Internet Comput., 14, 1, 44–51, 2009.
14. Mattern, F. and Floerkemeier, C., From the Internet of Computers to the Internet of Things. From Active Data Management to Event-Based Systems and More, Springer, Berlin, Heidelberg, pp. 242–259, 2010.
15. Gershenfeld, N., Krikorian, R., Cohen, D., The internet of things. Sci. Am., 291, 4, 76–81, 2004.
16. Christidis, K. and Devetsikiotis, M., Blockchains and smart contracts for the internet of things. IEEE Access, 4, 2292–2303, 2016.
17. Whitmore, A., Agarwal, A., Xu, L.D., The Internet of Things—A survey of topics and trends. Inform. Syst. Front., 17, 2, 261–274, 2015.
18. Bandyopadhyay, D. and Sen, J., Internet of things: Applications and challenges in technology and standardization. Wireless Pers. Commun., 58, 1, 49–69, 2011.
19. Al-Fuqaha, A. et al., Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tut., 17, 4, 2347–2376, 2015.
20. Lee, I. and Lee, K., The Internet of Things (IoT): Applications, investments, and challenges for enterprises. Bus. Horiz., 58, 4, 431–440, 2015.
21. Rose, K., Eldridge, S., Chapin, L., The internet of things: An overview, vol. 80, pp. 1–50, The Internet Society (ISOC), Reston, VA, 2015.
22. Vision and challenges for realising the Internet of Things, in: Cluster of European Research Projects on the Internet of Things, European Commision, vol. 3, pp. 34–36, 2010.
23. Wollschlaeger, M., Sauter, T., Jasperneite, J., The future of industrial communication: Automation networks in the era of the internet of things and industry 4.0. IEEE Ind. Electron. Mag., 11, 1, 17–27, 2017.
24. Witkowski, K., Internet of things, big data, industry 4.0—Innovative solutions in logistics and supply chains management. Proc. Eng., 182, 763–769, 2017.
25. Li, X., Xuan, Z., Wen, L., Research on the architecture of trusted security system based on the internet of things. 2011 Fourth International Conference on Intelligent Computation Technology and Automation, vol. 2, IEEE, 2011.
26. Suo, H. et al., Security in the internet of things: A review. 2012 International Conference on Computer Science and Electronics Engineering, vol. 3, IEEE, 2012.
27. Sukumar, A. et al., A secure multimedia steganography scheme using hybrid transform and support vector machine for cloud-based storage. Multimed. Tools Appl., 79, 15, 1–25, 2020.
28. Mendez Mena, D., Papapanagiotou, I., Yang, B., Internet of things: Survey on security. Inf. Secur. J.: Glob. Perspect., 27, 3, 162–182, 2018.
29. Weber, R.H. and Studer, E., Cybersecurity in the Internet of Things: Legal aspects. Comput. Law Secur. Rev., 32, 5, 715–728, 2016.
30. Abomhara, M., Cyber security and the internet of things: Vulnerabilities, threats, intruders and attacks. J. Cyber Secur. Mobil., 4, 1, 65–88, 2015.
31. Ali, B. and Awad, A.I., Cyber and physical security vulnerability assessment for IoT-based smart homes. Sensors, 18, 3, 817, 2018.
32. Boyes, H. et al., The industrial internet of things (IIoT): An analysis framework. Comput. Ind., 101, 1–12, 2018.
33. Yu, Y. et al., Toward data security in edge intelligent IIoT. IEEE Netw., 33, 5, 20–26, 2019.
34. Puri, V. et al., Blockchain meets IIoT: An architecture for privacy preservation and security in IIoT. 2020 International Conference on Computer Science, Engineering and Applications (ICCSEA), IEEE, 2020.
35. Petrenko, A.S. et al., The IIoT/IoT device control model based on narrow-band IoT (NB-IoT). 2018 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), IEEE, 2018.
36. Sha, L. et al., IIoT-SIDefender: Detecting and defense against the sensitive information leakage in industry IoT. World Wide Web, 21, 1, 59–88, 2018.
37. Karpisz, D. and Kiełbus, A., The Revitalization of Radar System as a Case of Functional and Information Security Problems, in: System Safety: Human-Technical Facility-Environment, vol. 1, pp. 692–699, 2019.
38. Lipps, C., Duque Antón, S., Dieter Schotten, H., Enabling Trust in IIoT: An PhySec Based Approach. International Conference on Cyber Warfare and Security, Academic Conferences International Limited, 2019.
39. Chaudhary, R. et al., SDN-enabled multi-attribute-based secure communication for smart grid in IIoT environment. IEEE Trans. Industr. Inform., 14, 6, 2629–2640, 2018.
40. Sengupta, J., Ruj, S., Bit, S.D., A Comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl., 149, 102481, 2020.
41. Bajramovic, E. et al., Security Challenges and Best Practices for IIoT, in: INFORMATIK 2019 50 Jahre Gesellschaft für Informatik–Informatik für Gesellschaft (Workshop-Beiträge), Gesellschaft für Informatik eV, 2019.
42. Raposo, D. et al., Security and fault detection in In-node components of IIoT constrained devices. 2019 IEEE 44th Conference on Local Computer Networks (LCN), IEEE, 2019.
43. Eden, P. et al., SCADA system forensic analysis within IIoT, in: Cybersecurity for Industry 4.0, pp. 73–101, Springer, Cham, 2017.
44. Yan, X. et al., Trustworthy network anomaly detection based on an adaptive learning rate and momentum in IIoT. IEEE Trans. Industr. Inform., 16, 9, 6182–6192, 2020.
45. Leander, B., Čaušević, A., Hansson, H., Applicability of the IEC 62443 standard in Industry 4.0/IIoT. Proceedings of the 14th International Conference on Availability, Reliability and Security, 2019.
46. Ulltveit-Moe, N. et al., Secure information sharing in an industrial Internet of Things, 2016, arXiv preprint arXiv:1601.04301. http://arxiv.org/abs/1601.04301
47. Tian, Q. et al., New security mechanisms of high-reliability IoT communication based on radio frequency fingerprint. IEEE Internet Things J., 6, 5, 7980–7987, 2019.
48. Sun, W. et al., Social-Aware Incentive Mechanisms for D2D Resource Sharing in IIoT. IEEE Trans. Industr. Inform., 16, 8, 5517–5526, 2019.
49. Malakuti, S. and Grüner, S., Architectural aspects of digital twins in IIoT systems. Proceedings of the 12th European Conference on Software Architecture: Companion Proceedings, 2018.
50. Kimani, K., Oduol, V., Langat, K., Cyber security challenges for IoT-based smart grid networks. Int. J. Crit. Infrastruct. Prot., 25, 36–49, 2019.
51. Kshetri, N., Blockchain’s roles in strengthening cybersecurity and protecting privacy. Telecomm. Policy, 41, 10, 1027–1038, 2017.
52. Sohal, A.S. et al., A cybersecurity framework to identify malicious edge device in fog computing and cloud-of-things environments. Comput. Secur., 74, 340–354, 2018.
53. Naik, S. and Maral, V., Cyber security—IoT. 2017 2nd IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), IEEE, 2017.
54. He, H., Maple, C., Watson, T., Tiwari, A., Mehnen, J., Jin, Y., Gabrys, B., The Security Challenges in the IoT Enabled Cyber-Physical Systems and Opportunities for Evolutionary Computing & Other Computational Intelligence, in: 2016 IEEE Congress on Evolutionary Computation (IEEE CEC), Vancouver, Canada, pp. 1015–1021, 24–29 July 2016.
55. Cheng, S.-M. et al., Traffic-aware patching for cyber security in mobile IoT. IEEE Commun. Mag., 55, 7, 29–35, 2017.
56. Mohan, A., Cyber security for personal medical devices internet of things. 2014 IEEE International Conference on Distributed Computing in Sensor Systems, IEEE, 2014.
57. Furfaro, A. et al., Using virtual environments for the assessment of cybersecurity issues in IoT scenarios. Simul. Model. Pract. Theory, 73, 43–54, 2017.
58. Chatfield, A.T. and Reddick, C.G., A framework for Internet of Things-enabled smart government: A case of IoTcybersecurity policies and use cases in US federal government. Gov. Inf. Q., 36, 2, 346–357, 2019.
59. Sivanathan, A., Gharakheili, H.H., Sivaraman, V., Managing IoT cyber-security using programmable telemetry and machine learning. IEEE Trans. Netw. Service Manage., 17, 1, 60–74, 2020.
60. Trappey, A.J.C. et al., A review of essential standards and patent landscapes for the Internet of Things: A key enabler for Industry 4.0. Adv. Eng. Inform., 33, 208–229, 2017.
61. Nagy, J. et al., The role and impact of Industry 4.0 and the internet of things on the business strategy of the value chain—The case of Hungary. Sustainability, 10, 10, 3491, 2018.
Email: [email protected]
Rohini Jha: ORCID: https://orcid.org/0000-0002-2865-3471
