7
SWu Tunnel Establishment
7.1. IPSec mechanism
The IPSec (Internet Protocol Security) mechanism offers security services (authentication, integrity and confidentiality) in an identical way in IPv4 and IPv6. Their implementation is optional in IPv4 but mandatory in IPv6. Their use is optional.
Security services are offered through the use of AH (Authentication Header) or ESP (Encapsulating Security Payload) extensions of the IPv4 or IPv6 header.
To secure a two-directional communication between two end points, a security association (SA) pair is required. The IKEv2 (Internet Key Exchange version 2) protocol dynamically ensures the creation of the security association.
A security association contains the following parameters:
- – the authentication algorithm and the key in order to generate the AH extension;
- – the encryption algorithm and the key in order to generate the ESP extension;
- – the authentication algorithm and the key in order to generate the ESP extension, if this service is used;
- – the lifetime of the security association;
- – the encapsulation mode (tunnel or transport).
The IPSec mechanism defines the following three databases:
- – security policy database (SPD): this defines the security policy to be applied to input and output traffic for a host or a security gateway;
- – security association database (SAD): this contains the parameters applied to a security association;
- – peer authorization database (PAD): this provides a link between the IKEv2 protocol and the SPD.
The selector is the mechanism enabling identification at the source of the security association to be applied to traffic. The selector uses the following fields:
- – Protocol (IPv4) or Next Header (IPv6) and source or destination address of the IP headers;
- – source or destination port of the TCP (Transmission Control Protocol) or UDP (User Datagram Protocol) headers.
For an outgoing packet, the selector consults the SPD that defines the process to be applied to the packet:
- – BYPASS: the packet is transmitted without a security service;
- – DISCARD: the packet is discarded;
- – PROTECT: the security service is applied to the packet. If the security association is not established, then the IKE protocol is invoked. If the security association exists, then the database returns a pointer to the SAD.
The deletion of a packet causes the generation from the security gateway toward the source of an ICMP message with the following characteristics:
- – in the IPv4 environment, Type = 3 (destination unreachable) and Code = 13 (Communication Administratively Prohibited);
- – in the IPv6 environment, Type = 1 (destination unreachable) and Code = 1 (Communication with Destination Administratively Prohibited).
The security parameter index (SPI) is a field in the AH or ESP header used by the destination to identify the security association in a unique way. The destination uses this index to extract the security association parameters from the SAD.
For an incoming packet, the SPD is consulted if the packet is not protected, and the instruction (BYPASS or DISCARD) is applied. If the IP packet is protected, then the SPI field is used to recover the parameter of the security association.
7.1.1. Header extensions
The IPSec mechanism introduces two IPv4 or IPv6 header extensions:
- – authentication header (AH) is designed to ensure the integrity and authentication of IP packets without data encryption (no confidentiality);
- – encapsulating security payload (ESP) ensures the integrity, authentication and confidentiality of IP packets.
7.1.1.1. AH extension
The presence of the AH extension is indicated by the Next Header (in IPv6) or Protocol (in IPv4) field of the previous header, with a value of 51.
The AH extension contains the following fields (Figure 7.1).
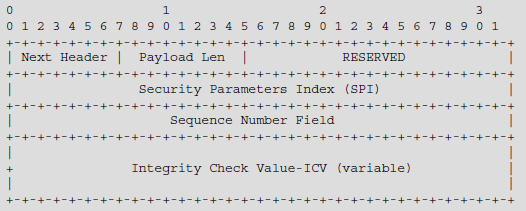
Figure 7.1. AH extension format
Next Header: this field, coded on one byte, indicates the type of header following the ESP extension.
Payload Length: this field, coded on 1 byte, provides the extension size in multiples of four bytes, not including the first eight bytes. The size of the extension in IPv6 must remain a multiple of eight bytes.
Security parameters index (SPI): this field, coded on four bytes, contains a value pertaining to the previously negotiated security association.
Sequence Number: this field, coded on four bytes, contains a value increased by one unit for each IPv4 or IPv6 packet transmitted. This field enables protection against replay. This field has a value of 1 for the first packet transmitted. When the counter reaches the maximum value, a new security association must be negotiated in order to avoid the start of a new cycle.
An extended sequence number (ESN), coded on eight bytes, constitutes an option, making it possible for the lifetime of the security association to be prolonged. In order to preserve the structure of the extension, the 32 least significant bits are transmitted in the sequence number field. However, the seal is calculated on all 64 bits.
Integrity check value (ICV): this field is coded on a multiple of four bytes and contains the seal of the data, ensuring authentication and integrity checking.
7.1.1.2. ESP extension
The presence of the ESP extension (Figure 7.2) is indicated by the Next Header (in IPv6) or Protocol (in IPv4) field of the previous header, with a value of 50.

Figure 7.2. ESP extension format
The ESP extension contains the same fields as the AH extension. It starts with the SPI and Sequence Number fields. After these fields come the encapsulated data, which may contain synchronization data (initialization vector) of the encryptor. Following the encapsulated data, the extension ends with the following fields: Padding, Pad, Length, Next Header and optionally ICV (authentication, data).
The Padding field is necessary when block encryption is used, and the block must be of a certain size, to align the packet size with a multiple of four bytes.
7.1.1.3. Transport and tunnel modes
For transport mode, the AH or ESP header is inserted between the IP header and the source IP packet payload. In the IPv6 environment, the AH or ESP header appears after the Hop-by-Hop, Destination, Routing and Fragment extensions.
For tunnel mode, the AH or ESP header encapsulates the source IP packet, and the whole is encapsulated in its turn by a new IP header. The tunnel corresponds to a data structure, in which an IP packet contains another IP packet.
When the AH header is used, authentication is applied to the whole packet except for the variable fields of the IP header (Figure 7.3).

Figure 7.3. Position of AH extension
The variable fields of the IPv4 header are set at ZERO to calculate the authentication digest:
- – DSCP (DiffServ Code Point): the value of this field can be modified by an intermediary router when it checks traffic characteristics;
- – ECN (Explicit Congestion Notification): the value of this field can be modified by an intermediary router to alert the destination that congestion is developing;
- – DF (Don’t Fragment): this bit can be set at ONE by an intermediary router;
- – Fragment Offset: insertion of the AH header occurs on non-fragmented IP packets, and, therefore, this field has a value of zero;
- – TTL (Time To Live): the value of this field is decreased by one unit for each router crossed;
- – Checksum: the value of this field is recalculated as soon as a field in the IP header changes value.
The set of IPv4 header options is considered as a single entity. Some options can be modified by an intermediary router. If a single modifiable option appears, then the set of options is set at ZERO for the authentication digest calculation.
The variable fields of the IPv6 header are set at ZERO for the authentication digest calculation. These are identical fields to the ones in the IPv4 header (DSCP, ECN and Hop Limit), as well as the Flow Label field.
The Hop-by-Hop and Destination extensions of the IPv6 header have a bit that indicates whether the option can be modified by an intermediary router or not. If this bit is set at ONE, then the extension is set at ZERO for the authentication digest calculation.
When the ESP header is used in transport mode, the confidentiality service is applied to the encapsulated data and ESP tail. Authentication and integrity services cover the ESP header, encapsulated data and ESP tail (Figure 7.4).

Figure 7.4. Position of ESP extension
When the ESP header is used in tunnel mode, the confidentiality service is applied to the source IP packet and ESP tail. Authentication and integrity services cover the ESP header, source IP packet and ESP tail (Figure 7.4).
Note that in transport mode, the Destination extension can appear before, after or simultaneously before and after the AH or ESP extension.
7.1.2. IKEv2 protocol
The IKEv2 protocol is more simplified than the previous version. It combines the functionalities defined in IKEv1 and Internet security association and key management protocol (ISAKMP) while removing unnecessary processes. It eliminates the generic character of the previous version, integrating the domain of interpretation (DOI) function, which defines the parameters specific to the ESP/AH security association.
Each IKEv2 message is composed of a header (HDR) and a sequence of blocks. The IKEv2 message is encapsulated by a UDP header with source and destination port values of 500 or 4500. When the 4500 port is used, the IKEv2 message is preceded by four bytes at ZERO.
7.1.2.1. Message header
The header of the IKE message contains the following fields (Figure 7.5):
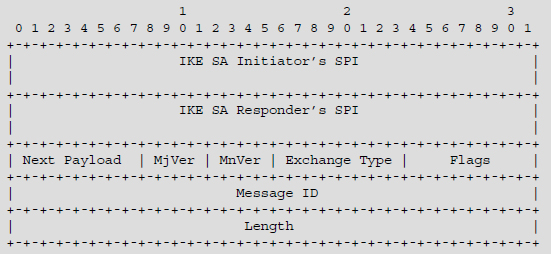
Figure 7.5. IKE message header format
Initiator’s SPI: this field, coded on eight bytes, incorporates a value chosen by the initiator. It initializes identification of the IKE security association.
Responder’s SPI: this field, coded on eight bytes, incorporates a value chosen by the responder. It completes the identification of the IKE security association.
Next Payload: this field, coded on one byte, incorporates the indication of the type of block following the header (Table 7.1).
Major Version: this field, coded on four bits, indicates the maximum value of the IKE protocol version that can be used. This value is equal to 2 for the implementation of the IKEv2 protocol.
Minor Version: this field, coded on four bits, indicates the minimum value of the IKE protocol version. This value is equal to 0 for the implementation of the IKEv2 protocol.
Exchange Type: this field, coded on one byte, indicates the type of exchange to which the message belongs:
- – IKE_SA_INIT: this exchange concerns the first phase of the establishment of the IKE security association;
- – IKE_AUTH: this exchange concerns the second phase of the establishment of the security association;
- – CREATE_CHILD_SA: this exchange concerns the establishment of the ESP/AH security association;
- – INFORMATIONAL: this exchange concerns event notification.
Each type of exchange imposes a certain number of required blocks composing the message and defines optional blocks.
Table 7.1. Block types
| Notation | Designation |
| SA | Security Association |
| KE | Key Exchange |
| Idi | Identification – initiator |
| IDr | Identification – responder |
| CERT | Certificate |
| CERTREQ | Certificate Request |
| AUTH | Authentication |
| Ni | Nonce – initiator |
| Nr | Nonce – responder |
| N | Notification |
| D | Delete |
| V | Vendor ID |
| TSi | Traffic Selector – initiator |
| TSr | Traffic Selector – responder |
| SK | Encrypted and Authenticated |
| CP | Configuration |
| EAP | Extensible Authentication |
Flags: this field includes the following three flags:
- – R (Response): this flag, positioned at ONE, indicates that this message is a response. An IKE termination must not respond to a response except when authentication has failed;
- – V (Version): this flag, positioned at ONE, indicates that the IKE termination is able to process a version higher than the one shown in the Major Version field;
- – I (initiator): this flag, positioned at ONE, indicates that the message is generated by the initiator of the IKE security association.
Message ID: this field, coded on four bytes, is an identifier used to control the retransmission of lost messages and to correlate the request and response. It also protects against replay attacks.
Length: this field, coded on four bytes, includes the IKE message size.
7.1.2.2. Blocks
Each block starts with a generic header containing the Next Payload field, the C (Critical) bit and the Payload Length field (Figure 7.6).
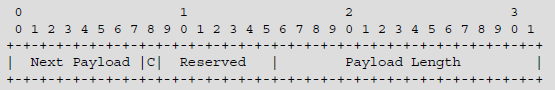
Figure 7.6. Format of generic block header
The Next Payload field indicates the type of block that comes next, thus enabling chaining.
The C bit determines the process to be executed when the receiver does not recognize the block:
- – if the C bit is positioned at ONE, the receiver rejects the message;
- – if the C bit is positioned at ZERO, the receiver ignores the block and processes the next block.
7.1.2.2.1. SA block
The SA block is used for the negotiation of the parameters of IKE and ESP/AH security association. An SA block can contain several proposals (P) ranked in order of preference. Each proposal defines a protocol (IKE, ESP or AH) and the value of the SPI. Each proposal includes several transformations (T), and each transformation includes one or more attributes (A).
The transformation T involves the following operations:
- – the encryption algorithm ENCR: this operation is used for negotiation pertaining to the IKE and ESP;
- – the pseudo-random function PRF: this operation is used for negotiation pertaining to the IKE;
- – the integrity algorithm INTEG: this operation is used for negotiation pertaining to IKE, AH and (optionally) ESP;
- – the Diffie–Hellman (D-H) group: this operation is used for negotiation pertaining to IKE and (optionally) AH and ESP;
- – the extended sequence number ESN: this operation is used for negotiation pertaining to the AH and ESP.
The attribute A specifies the length of the encryption algorithm key defined in the ENCR transformation. The other transformations, PRF, INTEG, D-H and ESN have no attributes.
7.1.2.2.2. KE block
The key exchange (KE) block contains the public Diffie–Hellman value, enabling each end point (initiator and responder) to construct a shared secret. The block also mentions the D-H group defined in the SA block.
7.1.2.2.3. IDi and IDr blocks
Identification initiator (IDi) and identification responder (IDr) blocks contain an identification of the initiator of the IKE message and the responder. This identification is based on an IPv4 or IPv6 address, a name, a messaging address or a group of bytes.
7.1.2.2.4. CERT block
The certificate (CERT) block provides a means of transporting a certificate or information pertaining to authentication.
7.1.2.2.5. CERTREQ block
The certificate request (CERTREQ) block is a request pertaining to a certificate. It is used in the response of the IKE_INIT_SA exchange response or in the IKE_AUTH exchange request. It also indicates the certification authority for the required certificate.
7.1.2.2.6. AUTH block
The authentication (AUTH) block contains the authentication digest (signature or seal) for the third-party authentication. The block also specifies the method used.
7.1.2.2.7. Ni and Nr blocks
Nonce initiator (Ni) and nonce responder (Nr) blocks contain a random number generated by the initiator and responder. These numbers are used in the creation of derived keys.
7.1.2.2.8. N block
The notification (N) blocks contain error messages indicating the reason why the security association cannot be established.
The N block also contains status messages that an SA management process wishes to communicate to a remote process.
7.1.2.2.9. D block
The delete (D) block includes the SPI of the SA that the message source wishes to delete. For an AH or ESP, it is possible to specify several SPI values. It is also possible to string several D blocks together in a single IKEv2 message.
7.1.2.2.10. V block
The vendor ID (V) block announces that the message source is capable of accepting private extensions of the IKEv2 protocol. These extensions can involve the introduction of new blocks, new types of exchange or new notification information.
7.1.2.2.11. TS block
The traffic selector (TS) block identifies the flows for which the ESP/AH security association is implemented. Flow determination is based on the following information:
- – the type of data encapsulated by the IP header, stated in the Protocol fields of the IPv4 header or the Next Header field of the IPv6 header;
- – the range of source and destination IP addresses;
- – the range of source and destination port numbers if the IP header encapsulates UDP or TCP segments;
- – the ICMP message type and code.
7.1.2.2.12. SK block
The SK (encrypted and authenticated) block is always located at the end of the IKEv2 message. The encryption and integrity algorithms for the IKEv2 message are negotiated during the implementation of the IKEv2 SA.
7.1.2.2.13. CP block
The configuration (CP) block is used to exchange configuration information between the two end points. In the case of an ESP/AH security association between a host and a security gateway, the host can request information concerning a host in the protected network.
7.1.2.2.14. EAP block
The extensible authentication protocol (EAP) block enables the use of EAP in IKEv2 message for authentication.
7.1.3. Procedure
7.1.3.1. IKE_SA_INIT exchange
The first exchange, IKE_SA_INIT, negotiates cryptographic algorithms and random numbers and executes a Diffie–Hellman exchange in order to create an IKE security association.
The initiator generates an IKE message containing the header (HDR) and the SAi1, KEi and Ni blocks. The header contains the initiator’s SPI, version numbers and flags. The SAi1 block contains the cryptographic algorithms proposed by the initiator for the IKE security association. The KEi block includes the Diffie–Hellman group and public value. The Ni block displays the initiator’s random number (Figure 7.7).
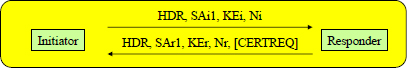
Figure 7.7. IKE_SA_INIT exchange
The responder chooses a cryptograph series from the initiator’s proposals and includes it in the SAr1 block. It completes the exchange of Diffie–Hellman keys with the KEr block. It sends its random number in the Nr block (Figure 7.7). It can possibly communicate a list of certificate authorities in the CERTREQ block.
At this stage of the negotiation, each end point can generate the SKEYSEED key. The keys used for encryption and integrity of IKE messages are produced by the SKEYSEED key and are known as SK_e (encryption) and SK_a (integrity). Message protection involves only the blocks; the header is not included.
The two different directions of traffic use different keys. The keys used to protect messages from the initiator are SK_ai and SK_ei. The keys used to protect messages in the other direction are SK_ar and SK_er.
Other keys are also derived from the SKEYSEED key. The SK_d key is used to derive the keys used in the ESP/AH security association.
The SKEYSEED key is calculated using the Diffie–Hellman secret (D-H key) and the random numbers Ni and Nr:
- SKEYSEED = PRF (D-H key, Ni | Nr)
The keys SK_d, SK_ai, SK_ar, SK_ei, SK_er, SK_pi and SK_pr are generated as follows:
- SK_d = PRF (SKEYSEED, Ni | Nr | SPIi | SPIr | 0x01);
- SK_ai = PRF (SKEYSEED, SK_d | Ni | Nr | SPIi | SPIr | 0x02);
- SK_ar = PRF (SKEYSEED, SK_ai | Ni | Nr | SPIi | SPIr | 0x03);
- SK_ei = PRF (SKEYSEED, SK_ar | Ni | Nr | SPIi | SPIr | 0x04);
- SK_er = PRF (SKEYSEED, SK_ei | Ni | Nr | SPIi | SPIr | 0x05).
7.1.3.2. IKE_AUTH exchange
The second exchange, IKE_AUTH, is used to authenticate previous IKE messages and communicate identities and possibly exchange certificates, as well as to establish the first AH/ESP security association. These messages are completely encrypted and protected by the keys established during the IKE_SA_INIT exchange.
The initiator indicates its identity with the IDi block. It authenticates its identity and protects the integrity of the first message in the IKE_SA_INIT exchange using the AUTH block.
It can possibly send its certificate in the CERT block and the certification authority’s identity in the CERTREQ block. In this case, the AUTH block contains the initiator’s signature (Figure 7.8).

Figure 7.8. IKE_AUTH exchange
The optional IDr block enables the initiator to specify which of the responder’s identities it wishes to communicate with (Figure 7.8).
The initiator starts the negotiation of the AH/ESP security association with the SAi2 block. The TSi block specifies the characteristics of the packets transferred by the initiator. The TSr block specifies the address for packets transferred to the responder (Figure 7.8).
The notation SK{ … } indicates that the blocks are completely encrypted and protected (Figure 7.8).
The responder communicates its identity in the IDr block. It may send a certificate. It authenticates its identity and protects the integrity of the second message of the IKE_SA_INIT exchange. It completes the negotiation of the ESP/AH security association with the SAr2 block (Figure 7.8).
7.1.3.3. CREATE_CHILD_SA exchange
The CREATE_CHILD_SA exchange is used to create the ESP/AH security association and to renew the keys of the IKE and ESP/AH security association.
For the exchange involving the creation of the ESP/AH security association, the initiator finalizes it in the SA block and the traffic selectors proposed for the SA in the TSi and TSr blocks. It transmits a random number in the Ni block and optionally a Diffie–Hellman value in the KEi block (Figure 7.9).

Figure 7.9. CREATE_CHILD_SA exchange creation of ESP/AH SA
The responder confirms the offer in the SA block. It transmits a Diffie–Hellman value in the KEr block, if the KEi block has been included in the request (Figure 7.9).
The KEYMAT key, used for the ESP/AH security association, is derived from the SK_d key and the random numbers Ni and Nr. If the exchange contains Diffie–Hellman values, then the secret D-H key obtained also participates in the creation of the KEYMAT key:
- KEYMAT = PRF (SK_d, Ni | Nr)
- KEYMAT = PRF (SK_d, D-H key | Ni | Nr)
To renew the IKE SA key, the initiator sends the parameters in the SA block, a random number in the Ni block and a Diffie–Hellman value in the KEi block. The initiator’s new SPI is provided in the SA block (Figure 7.10).
The responder confirms the offer in the SA block. It transmits a Diffie–Hellman value in the KEr block. The responder’s new SPI is provided in the SA block (Figure 7.10).

Figure 7.10. CREATE_CHILD_SA exchange renewal of IKE SA key
The new SKEYSEED key is computed from the old key SK_d, the secret key D-H and the random numbers Ni and Nr.
- SKEYSEED = PRF (old SK_d, D-H key | Ni | Nr)
To renew the ESP/AH SA key, the messages transmitted by the initiator and the responder are similar to the ones used in the creation of the security association. The initiator’s request contains an N block (REKEY_SA) containing the SPI value of the new security association (Figure 7.11).

Figure 7.11. CREATE_CHILD_SA exchange renewal of ESP/AH SA key
7.2. Application to the 4G mobile network
7.2.1. SWu tunnel establishment procedure
The IPSec mechanism is implemented for the establishment of the SWu tunnel, at the end of the authentication phase using the 802.1x mechanism described in Chapter 6, the mobile acting as the initiator and the evolved packet data gateway (ePDG) of the responder (Figure 7.12).

Figure 7.12. SWu tunnel establishment procedure
- 1) and 2) The two IKE_SA_INIT messages are used to negotiate the IKEv2 security association algorithms and to exchange D-H public values and random numbers (Nonce).
- 3) The mobile transmits the first message Request of the IKE_AUTH phase containing SWu tunnel configuration proposals in the SA block, its identity in the IDi block and access point name (APN) information in the IDr block.
The mobile does not transmit the AUTH block in order to warn the ePDG entity that it wishes to use the IKEv2 message to transport the EAP-AKA method.
The identity of the mobile conforms to the network access identifier (NAI) format containing the international mobile subscriber identity (IMSI) during the first authentication, or during the following authentications, a pseudonym or an identifier for the rapid renewal of authentication.
The mobile transmits the CP block (CFG_REQUEST) in the IKE_AUTH Request message to obtain its IPv4 and/or IPv6 address, and possibly the IP address of the PGW entity, in the case where the mobility is managed by the mobile.
- 4) The ePDG entity transmits to the AAA server the AAR (Authenticate and Authorize Request) DIAMETER message containing the identity of the mobile and the information relating to the APN.
NAI analysis allows the AAA server to distinguish between authentication for trusted Wi-Fi access based on the EAP-AKA’ mechanism and authentication for untrusted Wi-Fi access based on the AKA mechanism.
- 5) The AAA server requests the home subscriber server (HSS) for mobile cryptographic data in the AIR (Authentication-Information-Request) DIAMETER message.
The HSS entity generates the RAND sequence and creates the seals (RES and AUTN) and the keys (CK and IK) from the Ki key and the RAND sequence.
- 6) The HSS entity passes the authentication vectors to the AAA server in the AIA (Authentication-Information-Answer) DIAMETER message.
The AAA server derives the CK and IK to generate the master session key (MSK).
- 7) The AAA server initiates the authentication procedure with the message EAP Request/EAP-Method AKA Challenge containing the AUTN and RAND parameters. This message is transmitted in the AAA (Authenticate and Authorize Answer) DIAMETER message.
- 8) The ePDG entity transfers the message EAP Request/EAP-Method AKA Challenge in the message IKE_AUTH Response containing its identity, certificate and signature.
The mobile verifies the signature of the message IKE_AUTH Response with the public key of the ePDG entity retrieved from its certificate.
The mobile generates the RES, AUTN, CK and IK parameters from the Ki key and the received RAND sequence and compares the received AUTN seal with the locally calculated one. If both seals are identical, the AAA server is authenticated.
The mobile derives both CK and IK to generate the master key (MSK).
- 9) The mobile transmits the message EAP Response/EAP-Method AKA Challenge containing the RES seal in the message IKE_AUTH Request.
- 10) The ePDG entity transfers the message EAP Response/EAP-Method AKA Challenge in the AAR DIAMETER message to the AAA server, which compares the received RES seals respectively from the mobile and the HSS entity. If the two seals are identical, then the mobile is authenticated.
- 11) The AAA server transmits the SAR (Server-Assignment-Request) DIAMETER message to the HSS entity to register itself.
- 12) The HSS entity responds to the AAA server with the SAA (Server-Assignment-Answer) DIAMETER message containing the mobile profile. The AAA server verifies that Wi-Fi access is allowed.
- 13) The AAA server transmits to the ePDG entity the AAA DIAMETER message containing the EAP Success message, the MSK and the mobile profile.
- 14) The ePDG entity stores the MSK and forwards the EAP Success message into the message IKE_AUTH Response.
- 15) The mobile generates the message IKE_AUTH Request containing in the AUTH block a seal calculated from its MSK, which allows the authentication of the first message IKE_SA_INIT.
- 16) The ePDG entity checks the seal and starts the S2b tunnel setup procedure described in Chapter 8.
The ePDG entity responds with the message IKE_AUTH Response containing in the AUTH block a seal calculated from its MSK, which enables authentication of the second message IKE_SA_INIT.
The message IKE_AUTH Response is also used to transfer to the mobile its configuration in the CP block (CFG_REPLY) and the final configuration of the SWu tunnel in the SA block.
The mobile configuration was received from the PGW when establishing the S2b tunnel described in Chapter 8.
7.2.2. Procedure for rapid renewal of authentication
The procedure for rapid renewal of authentication is described in Figure 7.13.

Figure 7.13. Procedure for rapid renewal of authentication
Steps 1 to 4 are identical to those described for the establishment of the SWu tunnel in Figure 7.12.
The identifier for rapid renewal of authentication is transmitted in the IDi block of the first message IKE_AUTH Request.
- 5) The AAA server initiates the procedure for rapid renewal of authentication with the message EAP Request/EAP-Method AKA Reauthentication.
- 6) The ePDG entity transmits the message IKE_AUTH Response containing its identity, certificate and signature of the IKE_SA_INIT message in the AUTH block.
The message AKA Reauthentication EAP Request/EAP-Method is included to start the EAP procedure on IKEv2.
- 7) The mobile verifies the signature and responds with the message IKE_AUTH Request and the EAP Response/EAP-Method Reauthentication message containing the mobile seal.
- 8) The ePDG entity transfers the message EAP Response/EAP-Method Reauthentication to the AAA server.
Steps 9 to 12 are identical to steps 13 to 16 described for the establishment of the SWu tunnel in Figure 7.12.
The new MSK is generated by the AAA server and passed to the ePDG entity and the mobile. This new key is used to authenticate the first two IKE_SA_INIT messages.
