14. Mobile Device Management Features
In Chapter 13, we talked about some of the advantages that Mobile Device Management has over “traditional” OTA management and configuration profiles, but we didn’t really get any details of what that means.
Flexibility and Power
Flexibility and power—those are the two words that describe the advantages of Mobile Device Management over the other management methods we’ve explored so far.
Mobile Device Management easily excels in flexibility. You can change or remove settings without any user involvement.
Mobile Device Management also excels in power because you can apply its flexibility to one or hundreds of devices at once. Note that with Mobile Device Management, you apply. Using manual profile installation, even OTA, you notify the users of a new profile, and then wait for them to download and install it. Maybe they will, maybe they won’t. If not installing it causes them some pain, well, that’s their motivation, but they’re still going to be unhappy with you. (After all, it’s always IT’s fault.)
With Mobile Device Management, you don’t have to wait for them and they don’t have to tap. Devices are configured, inventory is updated under your control, and it all just works. Even better, because the Mobile Device Management implementations out there include all the benefits of SCEP and none of its (considerable) pain, this all happens in a secure fashion. Bonus!
But, it’s boring to talk about this in the abstract, right? Let’s see some examples that illustrate why you would want to use Mobile Device Management.
Managing Passcodes
Passphrases, passcodes, and passwords—no matter what word you use for them, they are an alphanumeric pain for every IT person and user on the planet. Unfortunately, they’re also a fact of life. We have to deal with them, so we welcome any help we can get. Within Mobile Device Management, we can both remotely set and remove passcodes from devices.
Setting Passcodes
You set passcodes as you would set anything. You create the profile with the correct settings and push it to the device.
Let’s pretend that we have to set a consistent passcode policy for all of our devices. They cannot be simple (that is no “1234” or similarly lazy passcodes). They must have at least one letter, and a minimum length of five characters.
We also want the device to autolock after one minute, and to be unlockable for five minutes after an autolock without reentering a passcode. Finally, we won’t keep a history of passcodes, we won’t change the passcode on a regular basis, we won’t require special characters such as “&”, and we won’t be erasing the device if too many wrong passcode entry attempts are made.
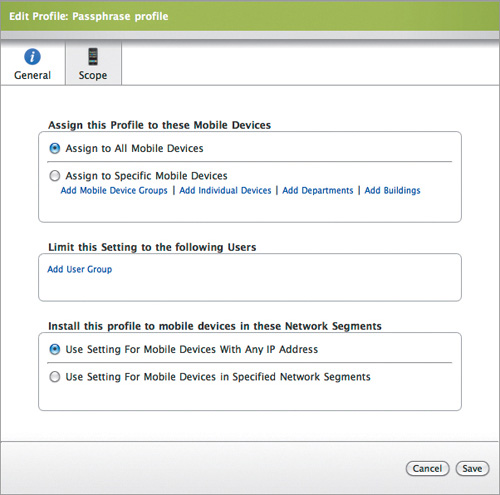
First, we create a profile with the appropriate settings (Figure 14.1). Then, we select the devices we want to push the profile to and push it to each device (Figure 14.2).
Figure 14.1. Passcode settings configuration
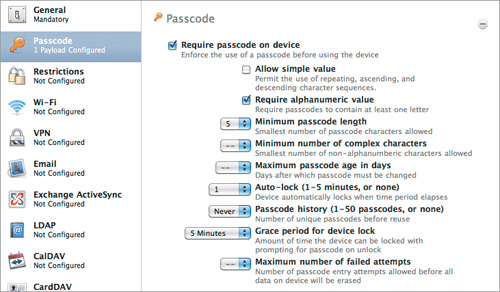
Figure 14.2. Profile scope settings
In the case of JAMF’s Casper (which appears in these screenshots), that’s all we need to do. The settings are then pushed out to the devices. We can verify this in the Management console (Figure 14.3).
Figure 14.3. Profile push results
![]()
So what does the user see on his device? Well, starting from a no-passcode state, once the new profile is pushed, the next time the user accesses the device, he’ll see an alert dialog telling him to set a passcode within the next 60 minutes.
If the user wishes, he can ignore this alert for the next hour and use his device. He’ll get nagged a lot but he can keep ignoring it until he gets to the end of the 60-minute grace period. Then he will have to enter a passcode.
He must tap Continue, enter a passcode that meets the requirements you’ve set, and confirm the passcode to set it.
If you now look at the passcode settings on the device, you’ll see a mixture of user-configurable settings and settings that are locked. Some of the user-configurable settings are manually set, such as the “Require Passcode After n min,” setting. Don’t worry. Apple’s not actually letting you bypass things. For example, in Figure 14.4, you can see that the profile automatically set the interval to five minutes. The user can change that to lock after five minutes, one minute, or immediately. In other words, the user can opt for more restrictive settings than you entered, but not less. I can live with that.
Figure 14.4. New passcode settings
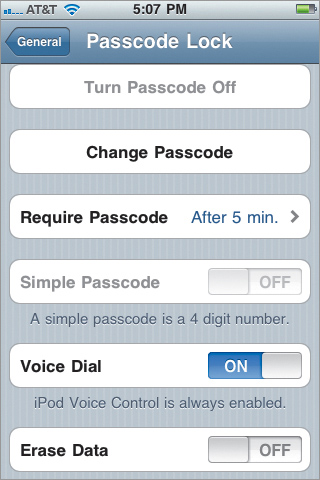
The same thing is true of the Erase Data setting. Because we didn’t set it, the user can opt to turn it on because that choice would be more restrictive.
Finally, if we look at the profiles on the device (Figure 14.5), we can see the profile we pushed out to the device to start this process.
Figure 14.5. Profiles showing passcode profile
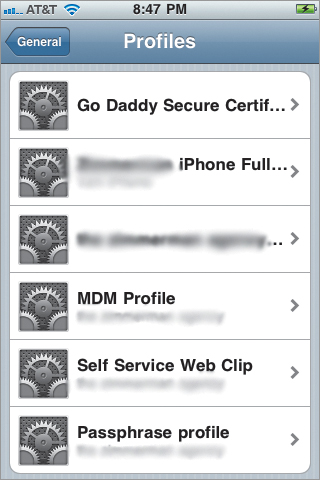
This is great. We have pushed a profile to all our devices, they’re passcode-protected, and life is good. At least it’s good until the phone rings, and that traveling user can’t seem to remember a passcode more complicated than “1111.” He’s forgotten his passcode. Groan. He’s also a thousand miles away. You don’t know what passcode he set, and of course, his entire world will collapse if he can’t get into his devices.
Without Mobile Device Management, this is a major pain. With Mobile Device Management, it’s only a minor annoyance because you can easily disable a passcode.
First, you tell your Mobile Device Management server that you want to clear a passcode from a remote device (Figure 14.6). You select the device and then confirm that you want to clear the passcode from the selected device, and send the command to do so. You’ll see that the command is pending (Figure 14.7).
Figure 14.6. Initiate the clear passcode command
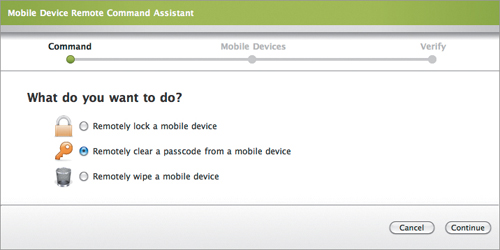
Figure 14.7. Passcode removal command pending
![]()
Within a few minutes (less than five if the device is reachable), the passcode is cleared. The device will be usable without a passcode, and even the settings will show that the passcode has been disabled (Figure 14.8).
Figure 14.8. On-device settings showing passcode removed
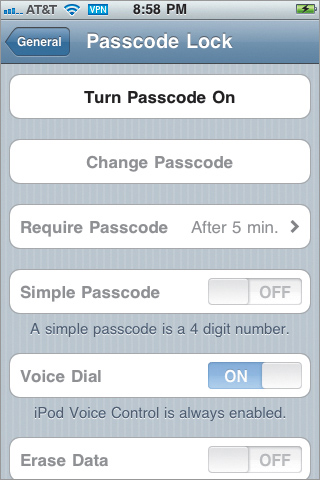
Well, that’s great, but we still want the device to be passcode protected! Do we now have to resend the profile? Nope. Within a few minutes, the device will once again display the 60-minute nag countdown to set a passcode as it did when you initially pushed out the profile.
Considering the amount of pain that IT people normally experience with such situations, let me tell you, this ease of management is Awesome. Also, it’s a way to deal with anyone who thinks he’s just found a clever way to make his passcode headaches go away.
Keep in mind that part of this solution (the remote removal of the passcode) is impossible without using Mobile Device Management. Further, unless you use Mobile Device Management and its push abilities, you’re not going to have an easy time handling mass passcode setup.
Let’s review the IT and user steps involved in pushing out a profile, any profile, without MDM:
1. Build the profile in the iPhone Configuration Utility and put it on a web server.
2. Send an email or text to users requesting they go to the website in the link and install the new profile. (Send an individual email or text for every device you need to configure/modify.)
3. The user taps a link to go to web site.
4. The user logs into website.
5. The user downloads and installs the profile and performs whatever steps are required by the profile.
Now, same thing, with MDM:
1. Build the profile in the iPhone Configuration Utility or the Mobile Device Management server tool.
2. Push the profile to the devices you select.
3. The user performs minimal configuration (enter passcode, provide password for server, and so on).
Cake! Mobile Device Management makes this process and others a lot easier. Let’s look at setting up a CardDAV server.
Managing CardDAV Settings
Installing the CardDAV Profile
The procedure here is virtually identical to installing the passcode profile. First, set up your profile with the CardDAV info (Figure 14.9). Notice the $USERNAME variable entered in the Account Username field. This is one of those “why I pay for things” features. When the profile is pushed to the device, the username associated with that device is automatically filled in. It’s a minor thing, but it’s really nice to have; and it means that the device user only has to enter her password for the CalDAV server.
Figure 14.9. CardDAV settings in the profile
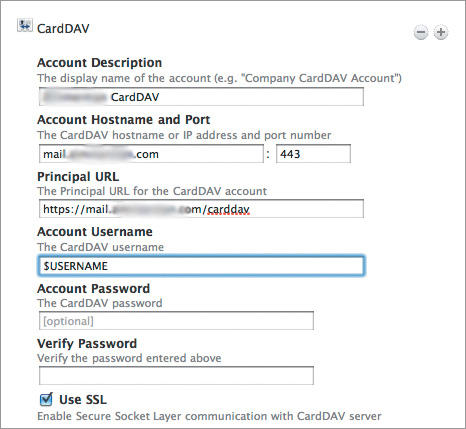
Save the profile, assign it to the correct devices, and within seconds, those devices, if reachable, will have the new profile. When I say “seconds,” I’m speaking literally. It took me longer to navigate from the Casper settings to the device settings than it did to push the profile. A minute or so of work, a few seconds to a few minutes of network traffic, a password tapped on a device, and (bang!) your users have CardDAV. Or email, or CalDAV, or what have you.
Removing the CardDAV Profile
Removing the profile is even simpler. Open the profile you want to remove (Figure 14.10), click Delete, or click Edit if you’re removing a profile setting but keeping the profile.
Figure 14.10. Profile with delete/edit options

The profile is removed, along with the CardDAV settings, and the device’s user has performed zero work. This is how these things are supposed to work: easily, quickly, and securely with a minimum of manual fiddling about for everyone.
All this is nice, but what about when you want to gather statistics on devices? Mobile Device Management comes to the rescue again!
Gathering Device Inventory/Information
Even if you are locking devices down, some information is going to be tedious to get without using Mobile Device Management. Device versions, device names, IMEI numbers, Wi-Fi MAC addresses, software versions, available space, model, currently-installed apps, installed certs, configuration profiles, and on and on. Some of these, such as the Wi-Fi MAC address, won’t change much. But others will, and if you can’t easily gather that information remotely, you have to manually collect it, or have the user try to read it to you. Yeah, that’s big fun.
Wouldn’t it be great if you could just collect this information in one place, and review it as necessary? That would be awful handy when you needed to know how many of your devices could support the latest iOS update, wouldn’t it? What you want is the kind of information a Mobile Device Management server can give you.
Need details on a device? How about determining which apps are installed on a device? (Figure 14.11) What about locating certificates? (Figure 14.12) Need to know the configuration profiles installed on a device? (Figure 14.13)
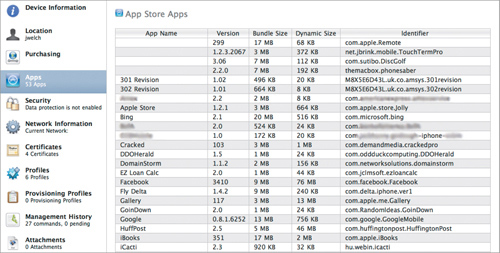
Figure 14.12. Certificate inventory
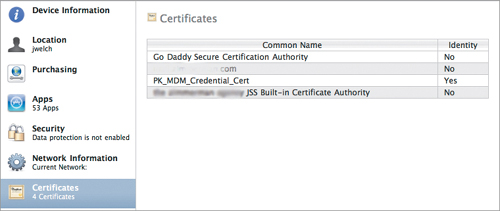
Figure 14.13. Configuration profile inventory
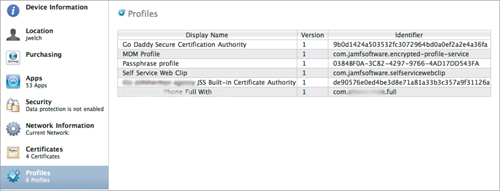
Done, done, done, and done. That is the flexibility and power you get with Mobile Device Management, and that is why it is such an improvement over past management methods.
Wrapping Up
With Mobile Device Management, you can actually manage your devices in a proactive way. (Yes, I know that according to pundits, you can’t do this with iOS devices. Oh look! The pundits are wrong. Again!)
In Chapter 15, we’ll look at what’s involved in setting up a Mobile Device Management server using Casper from JAMF software.
