So far, what we’ve seen is bleak. I intended it that way on purpose. I do celebrate the reverse engineers and people that pick apart apps. I do, however, want you to know that you are in a difficult position and can’t afford to take shortcuts or be lazy about security. My goal of showing you and possibly other reverse engineers how to break Android apps was to get you to take a more serious approach to your security. You have to learn about the principles and work from there rather than rely on someone to build you yet another framework to help simplify your life. Therefore, in this chapter, I want to take you through some alternatives in security. These alternatives are still new and thus have not had enough of an impact on the reversing community as a whole. To this end, you will not find many blog posts or articles written about these topics. I think that you owe it to yourself to figure out some new ways of protecting your own apps, though. It doesn’t hurt and can only help strengthen the ecosystem further.
What I will do in this chapter is talk about some alternate approaches to handling sensitive aspects of app development – SSL Pinning being one of them. We will take a look at how some frameworks are designed and work and then consider alternatives to doing SSL Pinning based on the fact that Android is still, essentially, Linux. These topics are new even to me, and as such I am actively researching them and will publish more details on the companion website for this book [https://aas2book.com]. I would love to work closer with you if you have any thoughts on developing what I present here or even contributing to it. Thus, without much delay, let’s get started.
Flutter

Flutter system overview taken from https://flutter.dev/docs/resources/technical-overview
By changing just the Embedder layer, it is possible to transplant Flutter apps to both iOS and Android. There is even a web component that is equivalent to building HTML5 apps through other frameworks like Titanium, Ionic, Apache Cordova, and so on. There, the premise is to use HTML5 and JavaScript to build apps which compile to native packages. This is similar except that Flutter uses Dart, and the Flutter ethos is that you build, use, and reuse Widgets.
I won’t be covering Flutter in depth in this chapter and rely on you to do some of your own research. Flutter has some great installation instructions on how to get setup for the first time, so I encourage you to follow those instructions and get your developer environment setup. Start here [https://flutter.dev/docs/get-started/install] and continue on to the Test Drive section here [https://flutter.dev/docs/get-started/test-drive]. This is the standard demo that we will begin to work off of. My goal in this section is to show you an alternative to using SSL Pinning that is a little trickier to defeat. Fair warning, I have managed to break SSL Pinning described in this section and still intercept traffic going in between, but it was not straightforward and required some considerable time and research.

Flutter maintains its own networking and trusted root CAs
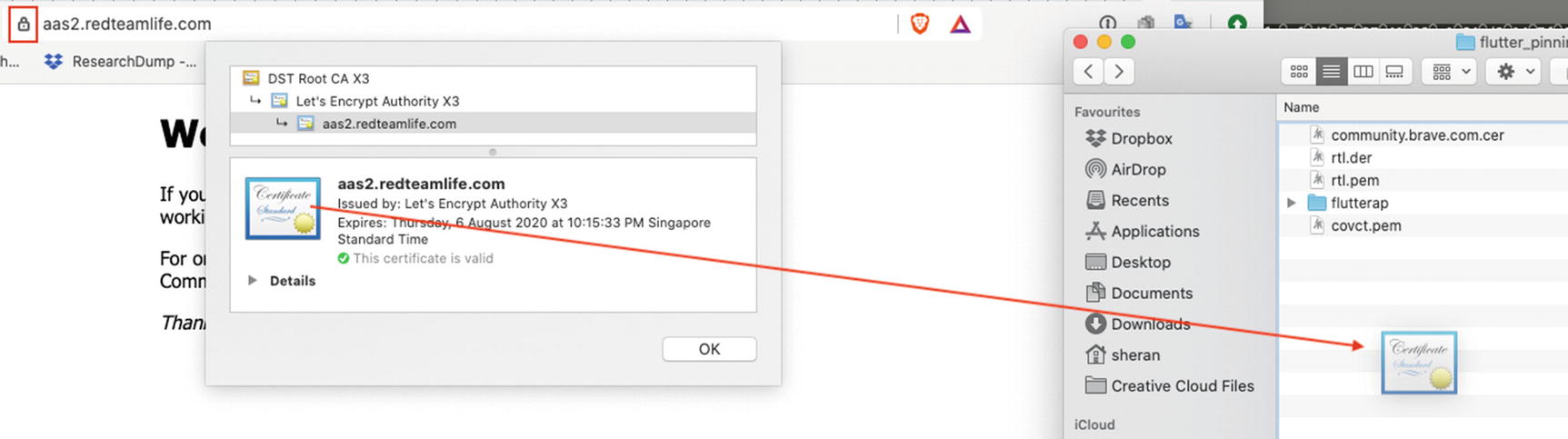
Flutter apps will have their own networking and trusted root CAs which is why they are not affected by the overall Android system settings. Therefore, to fully defeat SSL certificate verification, it is a little bit more of an elaborate process where you must look at the libflutter.so native library within the APK to find out where the SSL certificate verification takes place and then render it harmless through our standard techniques of using Frida. To divert all traffic, you will have to use something like iptables to route all network traffic to an IP address (your proxy server). SSL traffic can be looked at, but it isn’t as straightforward as how things are usually done.
The Flutter Certificate Verification

Flutter demo app
Now when you click the + button, your request is made to google.com and the output printed out into logcat. As an exercise, try intercepting traffic of this app the way we did in Chapter 9. You will find that you won’t see any traffic or notice how Burp Proxy doesn’t complain that it can’t establish a secure connection.
SSL Pinning with Flutter
Dart provides us with a class called SecurityContext. Now in SecurityContext, you can do two things. First, you can tell any HTTPS connection to not trust the stored root certificates. This means that it will not default to trusting its root CA certificates for each connection. The next thing you have to do is give it some form of a mechanism that it can use to base its decision on whether to connect or not to connect. This is the point where you can include your server’s certificate which means it will only trust that. You can find out more about what mechanisms there are to allow your client to trust the server that it speaks with here: https://api.flutter.dev/flutter/dart-io/SecurityContext/SecurityContext.html.
Save the server certificate

The Flutter project structure with our newly created assets directory
Here on line 2, what we’re doing is creating a SecurityContext and telling it not to trust or compare against our embedded trusted root CA certificates. Instead, on lines 3 through 7, we load up our file and copy its contents into a new list. Then in line 8, we load that certificate into our SecurityContext.
That’s because our client is only interested in speaking with the certificate issued by aas2.redteamlife.com. In this way, you can easily set up SSL Pinning in Flutter. Of course, you can take it a bit further and create a client that only looks at the SHA256 hash of the public key of a certificate, but I leave that up to you to try out.
What we saw here is an attempt to use SSL Pinning on newer and less used software to make it all that much more difficult for a reverse engineer. It is very much akin to security through obscurity because this can be beaten, and I have done exactly that. Yet again, as with obfuscation, very slight advantage counts, and this extra work that a reverse engineer has to put into bypassing SSL Pinning may be just the deterrent to make them pass over your app.
Golang
Golang or the Go language [https://golang.org/] is an open source programming language that was developed by Google and makes it easy to build performant and portable software. It is a breeze to cross-compile to different platforms and is very fast. I recall how I once rewrote a single API in one afternoon using Go in the startup that I worked for. Our code was a monolithic Java-based file, and we would deploy each large WAR file behind HAProxy load balancers but then only route certain APIs to each WAR file. So we would deploy like ten WAR files, and perhaps two handled one set of APIs, three another set, and the rest handled a third set of APIs. The two that handled one set of APIs would receive location data from thousands of mobile devices every 15 seconds. It would then write this to a database. Because of the load on this API, the VMs running this code had about 90–93% usage, and we were already debugging and profiling on the fly in production but didn’t have the time to see it through. That’s when I decided to rewrite that component in Go. After I deployed it, each of the servers hosting the Go binary had 2–3% CPU usage. It was completely unbelievable, if I hadn’t see it with my own eyes. I loved Go before that, but this one really cemented my relationship with Go. If I could hug a programming language while I slept every night, it would be Go.
The reason I bring up Go in this chapter is because I want to try and implement a native library in Go which I can include inside my Android APK. This library would handle the SSL connection and SSL Pinning functions of my app, and by extension, it would make things a little bit harder for a reverse engineer to decipher. Yes, I know that this is security through obscurity once again, like we did in Flutter, but the more barriers you can put up, the better. Plus, I have been familiarizing myself with the assembly code generated by the Go compiler. The Go compiler used to be written in C, but since 1.5 version of the language, the Go compiler was completely ported over to Go. Keep in mind that Go has a runtime that handles all aspects of program execution, including scheduling, garbage collection, memory management, and so on. This runtime is always included whenever you compile and link your program into a native binary. Therefore, when reverse engineering, you have to keep in mind that the code you’re looking at isn’t straightforward Go to assembly code. You will also have to navigate through the runtime. I’d like you to refer back to Figure 10-2 that shows how Flutter apps work with libflutter.so. We are going to replicate this same model, except we will use our own Go library instead of libflutter.so
Gomobile
Go introduced gomobile in version 1.10, and basically what it is is a tool to help you build mobile apps on Android and iOS by writing Go code. Once again, I will not be delving too deeply into Go, except to show you how to get gomobile setup and build a library for Android. To install Go, please follow the installation instructions found on their website [https://golang.org/doc/install].

Installing the Android NDK
Be careful that this piece of code does not perform any other certificate verification. You will ideally want to add more verification into this section to ensure that the certificate’s roots are also verified.
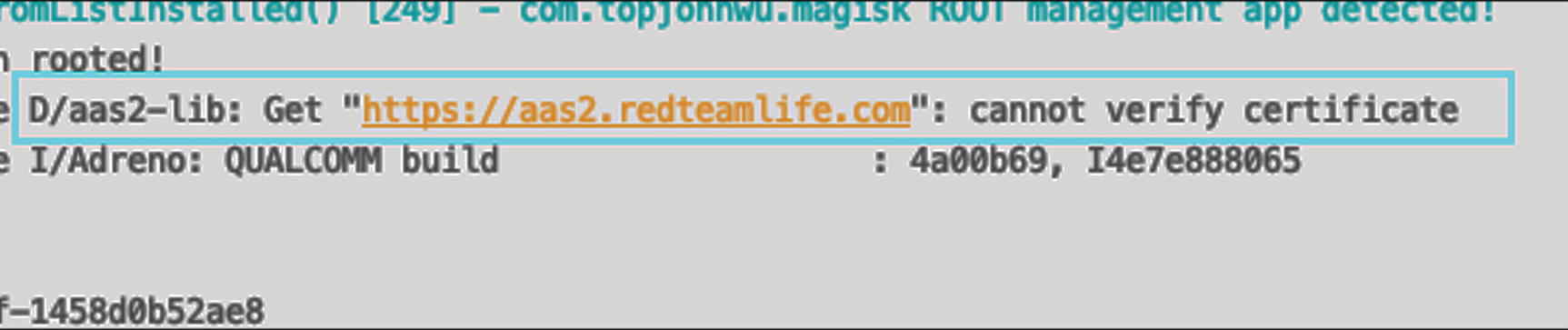
Let’s go over this code briefly. Essentially, this library has one function called GetVerify(). When you write libraries with gomobile bindings, you have to mark your functions as exported or public. In Go, you do this by capitalizing the first letter of your function name. Our GetVerify() function takes one string argument and returns a string – line 13. The argument it accepts is a URL. We are creating a new configuration for our TLS connection called config – line 15. In this, we configure the TLS connection to skip its own verification functions and use our function – line 16. We create this new verification function in line 19. The function is called VerifyPeerCertificate. Within this function, what we do is fetch all the certificates presented to us by the server – lines 20–27. Then we extract the public key from the server certificate, and we calculate its SHA256 hash – lines 28–34. Lastly, we compare it with the SHA256 hash value of our server certificate – lines 36–38. We define our known SHA256 hash in line 14.
Then, we create our HTTP client using the configuration we created – line 41. Then we go on to create our request, send the request, receive the response, and read and return the response body – lines 42–54. Here, for demonstration purposes, we’re only working on HTTP GET requests. Also, there’s no use of HTTP headers or request body. These can be added as per Go’s normal HTTP library found here: https://golang.org/pkg/net/http/. What’s important is that you create all your HTTP clients by using the customized configuration and that you initialize the HTTP client using this configuration: client := &http.Client{Transport: &http.Transport{TLSClientConfig: config}}

Adding a new module in Project Structure

Adding the netutils.aar archive
When you’re done, click Finish. Then back at the Project Structure window, click OK and the archive will be added.
For context, I am including my settings.gradle and build.gradle (Module:app) files as follows:
Error in verifying the certificate because we presented the fake SSL cert

The successfully retrieved HTTP response body from the server
This demo was a very brief look into how you can consider writing and including your code in your Android apps. Another option, besides C, would be to use Rust [www.rust-lang.org/]. I don’t have sufficient research done on using Rust at this moment, but will update whatever research I have on the book’s companion website in the future [https://aas2book.com].
Trusted Execution Environment

The Arm TrustZone for the ARM Cortex-A processor

Access to the Keymaster that lives in the secure world
An app that uses Trustonic’s TAP SDK
Admittedly, I have not done further research on the Trustonic TAP SDK, nor have I looked too in depth into the TEE. I do, however, am aware that there have been instances where the secure world has been compromised. Any further research that I do will be up on my blog as an extension to this chapter [https://aas2book.com].
Future Evolution of Android
I am not one to speculate on this, nor do I have sufficient evidence that Android will either continue to live or die. I do know for a fact that Google has been working on a new operating system called Fuchsia. The OS is said to be designed from the ground up for security and updatability. The security part of things, I fully understand and appreciate. Since based on Linux, Android has had a fair share of Linux’s vulnerabilities transplanted over to it. At Fuchsia’s core is the microkernel called Zircon. Zircon contains many of the services, drivers, and libraries that are necessary for it to boot, interface with hardware, load and run user processes, and so on. More information on Fuchsia can be found here: https://fuchsia.dev/.
Fuchsia is an exciting evolution that Android can take. Especially since it is language agnostic, you can write your apps in many languages including Rust and Go. Further, it is built in a manner where you can support new languages so it is possible to support building apps or programs in new languages which is really awesome. I’ll be doing more research on Fuchsia as well, and it would pay to definitely keep an eye on its progress.
Principles I (Try to) Live By
I figure rather than preaching to you, I’ll tell you some of my paranoia that leads my actions. Similar to how the TEE considers the Android world as insecure, so do I. You may think it is a bit of overkill, but I consider that every part of my app will be dissected and its data inspected and tampered with. The best I can choose to do is to design and develop my app on this principle. Therefore, I sit and think around some core concepts of app design and figure out how to give the attackers the lowest chance of success.
Data
Only store the bare minimum. Let the back end store the rest. Even if you don’t have an opportunity for getting accounts brute-forced, build your GET or data retrieving APIs in such a manner as to not leak sensitive personal data.
Encryption on Android, if you are not generating and saving your keys in KeyStore, is most likely going to fail. Whatever you encrypt can be decrypted later if you embed the secret key in your app. You may choose to pull a random string from one of your image assets as a secret key much like how early versions of WhatsApp used to do, but by tracing the encryption functions themselves, it is easy to narrow down where this piece of data is stored. Bottom line is if your app can see it, the attacker can see it.
Network
Even though SSL Pinning can be defeated, use it. Find some new or innovative ways to do pinning, put them in a library, and use them later in your code.
Consider using non-HTTP protocols such as gRPC [https://grpc.io/] as they don’t allow a traditional HTTP sniffer or MiTM tool to work. Again, your days may be numbered as there are already tools that do man-in-the-middle attacks on gRPC. There’s an upcoming version of HTTP/3 or version 3 of HTTP so it may be conceivable that new security testing or reversing tools will have to be used once again to intercept or tamper with that traffic. As with all cat and mouse games, it’s always about trying to stay ahead of the attackers.
Your back ends can be your downfall as well. Get them pen tested regularly or use a bug bounty platform. The usual progression of how an attack takes place is first dissecting the mobile app to determine how it communicates with the back-end server. More often than not, because for some reason developers think their traffic is magically hidden by virtue of its use in a mobile app, there are some abysmal choices made with regard to securing the back end. After the app is generally compromised, the next domino in line is the back-end server. Armed with knowledge of how it talks to the mobile app, it is very trivial to script most of the attacks against the back end. Protect that well.
User Experience
Don’t lose sight of what your application is supposed to do. Securing the crap out of a simple app that requires no sensitive data saving nor financial information can be detrimental to its performance and perhaps user experience. Take a look at the big picture first and decide the level of protection you want to give it. Approaching this and most other security-related issues from a user-centric manner will be better.
Wrapping Up
Jonathan Levin’s Android Internals – A Confectioner’s Cookbook, Volume I (I’m eagerly awaiting Volume II)
Nikolay Elenkov’s Android Security Internals
I will have sections for each of this book’s chapters at https://aas2book.com, and I will continue to add to those sections the further research that I do on those specific topics. At that site and the Apress site, you will be able to also send in any errors, omissions, or inconsistencies. Technical books are no longer written to remain static, and the growth of the Internet has allowed a far greater interaction between the author and the reader to a point where technical books are now more fluid. So feel free to engage and let me know where I can improve or point out something inaccurate.
I wish you the very best in your journey toward securing your Android apps. As long as you hold your user’s best interests at heart, you should have a good base with which to embark on this perilous journey. Bye for now.
