
Another popular tool hackers use for web application attacks is called BeEF. This tool is used to launch XSS attacks against victims. BeEF stands for Browser Exploitation Framework. This tool can be thought as an enhanced version of Autopwn2 with more features and a GUI interface. BeEF has the option of running Autopwn2 if you wish to use it. BeEF is designed to launch client-side attacks against a victim's browser. The main objective for BeEF is to hook the victim's browser.
Once the browser is hooked, BeEF offers a variety of options to exploit the victim's browser. We have prepared another lab to show you how to use BeEF. We have included screenshots to help you follow along. For this lab, we will use Kali Linux as both the attacker and victim. Before we get started we need to make sure everything is updated and upgraded. First type apt-get update and then apt-get upgrade. Since BeEF is included in Kali Linux distro, we can easily open it from the applications list.
The following screenshot will show you where this will be located:
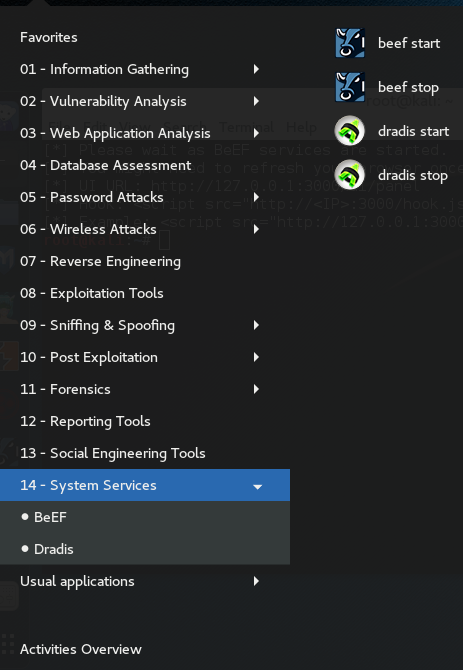
As you can see, if you scroll down to number 14 - System Services, you can start and stop BeEF. Click the BeEF start button to begin. Once you start BeEF open Iceweasel on Kali Linux. Sometimes BeEF will automatically start Iceweasel for you, bringing you to the BeEF login page. The login credentials for BeEF are: username: beef and password: beef. The following screenshot shows you what the BeEF login screen looks like:

After you have logged into BeEF, you can begin to hook a browser. For this lab, we are going to hook our own browser for testing purposes. On the BeEF starting page, you will see an option that says Hook Me! to hook you own browser. The following screenshot displays what screen you should see to hook your own browser:
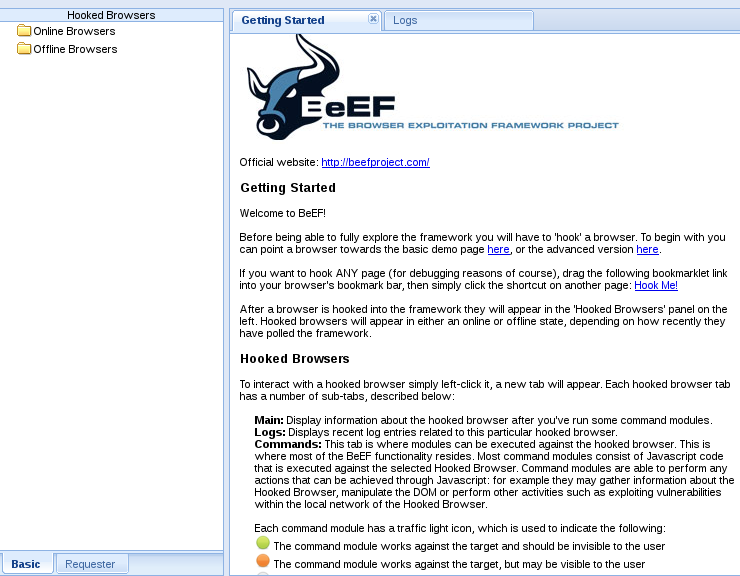
Click Hook Me! highlighted in blue. After we hook our own browser, the next screen will be the BeEF dashboard. This dashboard will give us lots of options to exploit our browser.
The following screenshot shows what the dashboard looks like once a browser has been hooked:

As you can see from the screenshot, we can get the details of the browser we hooked. Starting from the top of the dashboard tab, we can determine the type of browser, the version, language, platform architecture, plugins, and window size. We also get details of the browser components. Now we will select a social engineering attack against our hooked browser.
The following screenshot will demonstrate what this will look like:

This attack allows the hacker to steal the auto-complete information found in the search box in the victim's browser. This can be useful for reconnaissance. As you can see from the screenshot, there are many attacks we can experiment with. We suggest that you take some time and explore some of the other attacks found on the BeEF dashboard. Remember this is an extremely powerful tool that should be used in a responsible manner. We do not encourage you to use this information for illegal activities. BeEF is one of the favorite tools used by hackers for web application attacks. As you will have observed from the preceding lab, BeEF is even easier to use than Autopwn2. The user-friendliness of this tool makes it dangerous. Script-kiddies can now be just as effective as an experienced hacker in attacking web applications. XSS attacks continue to plague web applications and compromise victims every day. As a cyber security professional, it is critical to have a solid understanding of how these tools function. Next, we will discuss some defenses that can be used against web application attacks.
