CHAPTER 17
Research Methods and Industry Trends
This chapter presents the following topics:
• Performing ongoing research
• Threat intelligence
• Researching security implications of emerging business tools
• Global IA industry/community
An exciting yet difficult aspect of information security is the fast-paced and ever-changing environment that security practitioners have to deal with. Not only do you have to stay abreast of the latest advancements in technology, but also any newly discovered vulnerabilities in your applications, operating systems, and hardware. To succeed at this, security practitioners must exercise a high degree of resourcefulness because security issues and trends can be sourced from numerous places. A big part of this responsibility is performing ongoing research on the latest cybersecurity trends and vulnerabilities. Being the lead or one of the lead security professionals at a company, chances are nobody is going to tell you about these trends. It’ll be the other way around—people will be counting on you to keep them in the loop on the latest cybersecurity developments.
As you conduct your research, you’ll notice a pattern of numerous immediate and short-term threats, as well as a few long-term threats that will refine the cybersecurity landscape. As a result of the sheer volume of changes in technologies, vulnerabilities, and threats, you must repeat your research throughout the year to stay ahead of the curve. Your organization’s current and future security posture will depend on your ability to always know what’s going on in the industry.
This chapter discusses how we can apply various research methods to determine industry trends and their impact on the enterprise.
Performing Ongoing Research
A good chunk of your time should be spent conducting research—either formal as part of your job to improve the security posture of your organization’s computer systems and networks or informal to simply maintain your own level of currency and proficiency. Your research will include obtaining knowledge on the newest technologies in computer science and the potential impact they may have on your organization, both in productivity and in regard to security. You will also need to know what security services are offered that might be useful for your organization in protecting its computer systems and networks, and what the current best practices are for both the technology and the industry as a whole—especially for your given sector. For example, if you are in the banking and financial services sector, what are considered the standard best practices for banks and financial institutions specifically? Here are some suggestions to consider when doing your security research.
• Visit vendor websites for the latest information on vulnerabilities, updates, FAQs, other software downloads, and best security practices.
• Use official information security sources such as RFCs, ISO, NIST, ISACA, EC-Council, (ISC)², and SANS.
• Subscribe to security mailing lists such as Bugtraq and CERT Advisories and Security Weekly.
• Visit vulnerability websites such as the CVE database, SecurityTracker, and SecurityFocus.
• Create vendor-specific social media profiles on Facebook, Twitter, and LinkedIn.
• Attend security convention events like Black Hat, DEFCON, and HOPE.
Best Practices
People are interested in lists of best practices for various aspects of security because they want to determine what others, in a similar situation, are doing. With a limited amount of time, security administrators want to address the most important issues first. Having a list of tasks that others do in a similar situation provides an idea for where they need to get started. This is also important in case of litigation that might arise because of a security breach in an organization’s computer systems or network. If the organization hasn’t at least done what others in a similar situation have done, a court might decide the organization has been negligent in its security precautions. If, on the other hand, the organization can show that it took the same steps others have taken, that it has done what might be described as the “industry standards,” then the organization is much more likely to convince a court that it took all reasonable precautions and the incident was not its fault.
There are lists of best practices for many different aspects of security. The lists themselves can range from very detailed and proscriptive, describing very specific tasks that need to be done, to high-level discussions about the type of actions that should be taken but without any precise details on how to accomplish them. One list, for example, might be aimed at security programs in general—that is, what would you need to do in order to establish a viable and sustainable security program? It might include items such as the following:
• Do you have an established corporate security policy?
• Do you have a designated information security officer?
• Does your organization have an acceptable use policy for its devices and network?
• Do you have data retention and destruction policies?
• Do you have policies governing password creation and change?
• Do you have computer security awareness training for all employees?
• Do you have an identified incident response plan and individuals identified?
As can be seen, these are high-level items that are neither machine nor program specific. Another list might address securing an operating system, such as Microsoft’s Windows 10 Enterprise. Microsoft’s website has security checklists for their operating systems that include some system-specific but still not descriptive items, such as the following:
• Enable User Account Control.
• Configure the Windows Update application to search for and install updates at your desired day and time.
• Enable Windows Defender Security Center features.
• Enable Windows Defender Firewall.
• Utilize the Windows Backup and Restore features.
• Protect your files using BitLocker Drive Encryption.
This list does not contain “how-to” details on any one of the topics it presents, but rather mentions the features present in the operating system that the user should be aware of and utilizing. More detailed information can be found on these topics. For example, instructions can be found on Windows Defender Firewall, discussing each of the options and the recommended settings for them. Microsoft recommends that the firewall be turned on (a rather obvious choice) and allows you (“for maximum protection”) to choose to block all incoming connections. You also have the choice to have the firewall contact you whenever it blocks a connection.
In the case of Windows, Microsoft has done its best to provide the security applications users will need in order to maintain the security of the system—and has tried to provide them in a manner that gives user control using the easiest of interfaces. For users who don’t understand the specifics of what the system is doing, they can agree with the Microsoft recommended settings and can then expect to have a reasonable level of security. For the tech-savvy users, more granular options are provided to allow for more detailed security settings.
Linux has a number of best practices and security checklists as well, although they tend to be a bit more involved and descriptive. A typical Linux security checklist might contain the following:
• Ensure the latest patches and updates have been installed.
• Regularly check logs for signs of suspicious activity.
• Make regular backups.
• Install Secure Shell (SSH).
• Disable the ability to log on remotely as root.
• Remove the hosts.equiv and .rhosts files.
• Limit network access using iptables.
• Restrict access to the X server.
Because security is constantly changing—with new operating systems, applications, and versions of existing software being released continually—the best practices, especially those that are topic specific, will change constantly. Therefore, the wise security practitioner will regularly check to see what has changed in established checklists and what new items might have been added. Although there is no set period of time to accomplish this, any time new operating systems are installed or new applications loaded, it would be wise to check to see if best-practice checklists for these new packages are available.
You can check a number of locations for best-practice and guideline documents, such as the Information Assurance Support Environment (IASE), hosted by the Defense Information Systems Agency (DISA), as shown in Figure 17-1; the security special publications from the National Institute of Standards and Technology (NIST); and the security benchmarks maintained by the Center for Internet Security (CIS).

Figure 17-1 The DISA-hosted IASE site provides information on a variety of security guidelines, along with other documents.
New Technologies, Security Systems, and Services
Technology has changed a lot in the past 50 years. It evolved from being an intellectual curiosity in the 1960s to academic usage in the 1970s, to residential use in the 1980s, to global proliferation in the 1990s, to social media in the 2000s, to the complete integration into our lives in the form of mobile devices, wearables, and IoT of the 2010s. Although malicious hacking progressed in tandem with the technological advances, new technologies were also developed to counter the hackers.
Just as it is important to stay on top of the latest best practices, so too is it important to understand the new technologies that have been created that might impact the security of our computer systems and networks. With that said, the following are some of the new technology trends and security systems the modern security practitioner must be aware of:
• Artificial intelligence/machine learning
• Big data
• Blockchain/cryptocurrencies
• Cloud access security brokers
• Containerization
• Homomorphic encryption
• Internet of Things (IoT)
• Quantum computing
• User behavior analytics
The introduction of any new technology to an organization must be accomplished with an examination of the possibility for exploitation of the technology by others. Organizations that fall into the category of “early adopters” of technology will be the most vulnerable to new exploitations because the full potential for security vulnerabilities might not immediately be understood. By the time that majority of organizations adopt a new technology, most of the basic security concerns will have been examined and addressed at some level.
Not only do administrators need to know the potential security impact of any new technology, they also need to know something about the new security technologies that exist to both attack and defend computer systems and networks. New security devices and software are constantly being developed to address both new threats that have arisen as well as new approaches to old threats or issues. All of the security technologies we know today, such as firewalls, intrusion detection and prevention systems, and biometric access controls, were at some point new technologies that were just being introduced. Fortunately, in order to stay in touch with what new technologies are being introduced to help address cybersecurity, you can subscribe to one or more of a number of technology blogs or publications that frequently not only discuss technologies in general but often will provide reviews of new products when they are released. An example of this would be the trend over the last few years that has increased the computing power found in mobile devices. These devices can no longer be considered just phones because they provide quite a bit of processing power, and an ever-increasing number of applications are useable on them. This has led to them being targeted by individuals interested in gaining access to an individual’s personal information, which in turn has led to a number of new products designed to better secure the devices from attack.
In a similar manner, new security services are created and older ones improved, so security professionals need to also stay abreast of these as well. Services run the gamut, from those offered as systems that are being developed, before they become operational, and after they have been deployed. Service offerings might include the following:
• Code testing and review
• Threat modeling
• Security training (at multiple levels)
• Vulnerability assessment
• Risk analysis and assessment
• Penetration testing
• Social-engineering testing
• Security system monitoring and alert notification
A growing security business area is that of managed security services. Companies providing these services may be utilized to monitor security devices in your organization, providing security experts to look for signs of intrusive activity and to respond to it if found. These services may also include device management in which the company will configure, update, and maintain your systems in a manner that ensures the maximum level of security within your operating environment.
One area popular among security service providers is the concept of penetration testing, or “ethical hacking,” in which security professionals take the role of an attacker attempting to gain access to an organization’s computer systems and networks. This will generally include attempting to utilize various means to gain access to the systems and networks (for example, via the Internet, wireless connections, or telephone modems). It may also, depending on the arrangement with the company hired to conduct the test, include social engineering attacks, where they try to trick employees into providing access or information useful in gaining access to the network. It may even include other nontechnical techniques employed by attackers such as “dumpster diving,” in which an organization’s trash is examined to look for clues and information that might provide access to computers and the network.
Technology Evolution
Computers, networks, and the Internet are constantly evolving as technology advances. Frequently the advancements are minor and do not require large-scale changes to the Internet operating environment and the protocols on which it relies. Occasionally, however, advances are made that can have a much broader impact. When these occur, the community has to determine how to proceed (because there is no single entity that “owns” the Internet). The way this is done is often through Requests for Comments (RFCs), which are created by organizations such as the Internet Engineering Task Force (IETF). The IETF is a large, international community of network administrators, designers, vendors, and researchers who are concerned with the evolution of the Internet and its continued operation. They are responsible for 8,000+ RFCs, including some of the following:
• RFC 1321: The MD5 Message-Digest Algorithm
• RFC 2460: Internet Protocol, Version 6 (IPv6) Specification
• RFC 2616: Hypertext Transfer Protocol 1.1
• RFC 2660: The Secure HyperText Transfer Protocol
• RFCs 2865, 2866, 3575: Remote Authentication Dial-in User Service
• RFC 3748: Extensible Authentication Protocol (EAP)
• RFC 3766: Determining Strengths for Public Keys Used for Exchanging Symmetric Keys
• RFC 3820: Internet X.509 Public Key Infrastructure (PKI) Proxy Certificate Profile
• RFC 4301: Security Architecture for the Internet Protocol
• RFC 4949: Internet Security Glossary, Version 2
• RFC 6595: A Simple Authentication and Security Layer (SASL) and GSS-API Mechanism for the Security Assertion Markup Language (SAML)
• RFC 6749: The OAuth 2.0 Authorization Framework
• RFC 8446: The Transport Layer Security (TLS) Protocol Version 1.3
This is just a short list, but it illustrates the type of topics addressed in RFCs. It also serves to illustrate how the Internet is cooperatively designed and controlled by an open community of professionals. From a security standpoint, changes to technology and protocols can have a definite security implication, and discussions on subjects such as the preceding ones often have a security component.
After an appropriate amount of time is allowed for comments to be received on a subject, the IETF’s working group on the subject will evaluate the comments, and the RFC may result in the publication of a new Internet standard. Not all RFCs end up as standards. Some RFCs are designed as informational only. Others are intended to discuss best current practices. Even among RFCs that were intended for the “standards” track, there are categories such as Proposed Standard, Draft Standard, and Internet Standard.
The IETF is not the only international organization impacting the Internet and security communities. The International Organization for Standardization (ISO) is another international body that establishes standards. The ISO is composed of individual representatives from a variety of national standards organizations. It produces and disseminates proprietary, industrial, and commercial standards. A significant difference between the standards of IETF RFCs and those of the ISO is that the ISO obtains funding through the sale of its standards.
The point of this chapter is the fact that advances in technology will have an impact on trends that are seen and adopted in industry, and that this, in turn, has a potential impact on the security of organizations. Understanding this is critical, and there are plenty of examples, such as wireless networking evolving from wired networking. Wired networks have an overhead associated with them in terms of the wire that must be strung around the organization. It also impacts flexibility. Introducing wireless technology to a corporate network allows for much more flexibility and mobility throughout facilities. It, however, also introduces security concerns because wireless signals are not necessarily confined to the buildings or offices owned by the organization. This might allow attackers to listen in on network traffic or to use the corporate network for their own purposes. There are security responses to these vulnerabilities (such as encryption), but they, in turn, have been attacked (WEP encryption, for example, is widely known to be crackable), which led to the security community looking to WPA/WPA2 and to the new WPA3, which was announced by the Wi-Fi Alliance in January 2018. This never-ending cycle of advancing technology, followed by security discoveries, followed by new advances, and so forth, is something security personnel need to understand and accept. The corporate landscape is constantly changing with advances in technology, and the security posture of organizations will be constantly changing with it. Another common technology trend that is having tremendous security overtones (which security personnel need to understand) is the widespread use of mobile devices. The new phones of today are closer to computers now than they are to the first cell phones we once used. Unfortunately, most individuals still treat them as just phones and not computing devices, which means that attackers can take advantage of this carelessness to target these devices. Security personnel need to know how this new almost ubiquitous technology can have security implications for their organization.
Another, less widely understood technology change that has security implications is the somewhat gradual switch to IPv6 from IPv4. All of these technology trends provide great examples to study the pattern of technology change driving security changes, which is the focus of this chapter.
Threat Intelligence
Threat intelligence is the methodical process of collecting information about cybersecurity threats. This intelligence stems from multiple threat areas, including the threat’s goals, infrastructure, and resources. We use this information to make more intelligent decisions about preventing, detecting, and recovering from security incidents. Security practitioners must utilize various open source resources, including vendor websites, hacker channels, and Internet forums to help organizations adopt a more proactive cybersecurity posture.
If you’re wondering why we’re suggesting you visit hacker channels, it’s important to understand the nature of hackers. Many hackers struggle with keeping secrets. They have this relatively rare accumulation of knowledge, tools, and techniques, and they want to be recognized for it. After all, what is the fun in keeping a secret that no one knows you’re keeping? As a result, security professionals might be able to discover emerging threats and malicious intentions just by sniffing around a bit on the Internet. Not to mention, hackers might announce their hacking intentions directly to their targets.
A big part of threat intelligence involves awareness of the latest attacks. In this section, we’re going to cover threat intelligence components such as the latest attacks, knowledge requirements for current vulnerabilities and threats, zero-day mitigation strategies, and threat models.
Latest Attacks, Vulnerabilities, and Threats
As has been discussed, you need to have an understanding of your own networks and what constitutes normal activity so that you can better determine when abnormal activity is occurring. This is one aspect of situational awareness; another is to know what threats exist that can impact your organization’s critical cyber systems. Before we get into the latest attacks, vulnerabilities, and threats, it’s important to get some key terms out of the way. It’s important to know the specifics of these terms because much of the information you’ll be researching online will reference them.
• Threat agent Individual or group that carries out or gives rise to a threat.
• Threat Possible danger that may intentionally or unintentionally exploit a vulnerability that produces a loss.
• Exploit A defined method of attacking vulnerabilities.
• Vulnerability A weakness or absence of a countermeasure that can be exploited.
• Risk The probability and impact of a threat exploiting a vulnerability.
• Exposure The loss incurred from a threat exploiting a vulnerability.
It was only a few years ago when every mainstream media source in the world was talking about the infamous Heartbleed Bug, which affected roughly 66 percent of active websites worldwide and utilized the OpenSSL-based Apache and Nginx web platforms. The Heartbleed Bug is one of those “Mount Rushmore” attacks that people will be talking about for years to come due to its scale and longevity—and the rumor that the NSA exploited the Heartbleed Bug for two full years prior to its public discovery. To be fair, the NSA emphatically denies this claim and continues to state that they did not know about the bug until it was made public.
Now, not every cybersecurity threat will be broadcasted to us on national television; therefore, we’ll have to perform a little due diligence and go out and look for the information. Go to any search engine and type in “Cybersecurity trends 2018” or “Cybersecurity threats 2018” and you will be bombarded with articles predicting the upcoming cybersecurity landscape. Not only are the latest cybersecurity trends not hard to find, but you’ll quickly notice that most of the articles are predicting the same trends. Such a consensus really hammers home how imminent these threats are.
The following is a list of cybersecurity trends:
• Explosive growth of ransomware A type of malware that threatens to “dox” a user’s data or perpetually encrypt it until a ransom is paid—usually in the form of bitcoins to expedite payment while reducing paper trails. The legendary and ongoing WannaCry ransomware of May 2017 has caused billions of dollars of damages worldwide.
• Artificial intelligence attacks AI is being used by hackers to automate the collection, analysis, and learning of user data, and then that data is used to more intelligently attack targets. Such data collection also helps narrow down password possibilities based on the demographics gleaned from the data collection. Such narrowing down will significantly speed up password-based attacks.
• Internet of Things (IoT) With IoT devices expected to reach up to 50 billion in total by 2020, attackers will partake in a new gold rush. The frightening fact about IoT is most devices will not be designed with security in mind.
• State-sponsored attacks Despite all the current finger-pointing taking place regarding nations hacking other nations, the fact is international surveillance and hacking have always happened—not only between enemy nations but also between allies. The only differences are nations are more technologically equipped today to perform such state-sponsored activities than in years past. Given international tensions, cyberwarfare will only increase in the years to come.
• Sandbox-evading malware The clever among us attempt to sandbox malware inside of virtual machines in an effort to isolate, analyze, or extract any meaningful content from it. The reality, of course, is today’s more advanced malware is capable of discovering its sandboxing predicament, thereby suspending its payload or vacating the virtual machine to attack the hypervisor, physical host, or other virtual machines.
• App store malware App stores are frequently targeted with malware that is disguised as a security tool or other desirable application. This is a quick way to affect millions of devices with malware.
• Cryptojacking A method of hijacking a device’s hardware in order to mine cryptocurrency.
• Dronejacking With the number of drones in the skies now, hackers are hijacking not only the insecurities inherent in toy drones but also drones used for business purposes like deliveries and law enforcement.
• General Data Protection Regulation (GPDR) This new EU privacy law will directly or indirectly affect every major region in the world with compliance requirements that many organizations either cannot or deliberately will not meet. Supposedly the costs of compliance can be more expensive than the penalties incurred from noncompliance.
• Cloud computing With the explosion of data, applications, and services hosted in the cloud, attackers have found the proverbial sea with infinite fish. You can expect significant increases in cloud-based attacks from APTs, DDoS attacks, and malicious insiders in the data centers.
Zero-Day Mitigation Controls and Remediation
A zero-day vulnerability occurs when a software error or hole impacting security is discovered and exploited before a patch is developed to address the vulnerability. The term comes from the fact that up until the point of it being used in an attack, the vendor and public in general knew nothing about the vulnerability. The “clock” starts when the vulnerability is made public. How long it takes the vendor to develop a patch and how long it takes companies to develop a signature to detect it or methods to mitigate its impact will have a direct bearing on the amount of damage it can cause.
Another factor in how much damage may be caused by the vulnerability is how much publicity is generated. If it is generally announced or released, the damage can be considerable because numerous individuals may attempt to exploit the vulnerability while the software vendor scrambles to develop a patch for it and various security vendors rush to develop a signature that might be useable to detect and prevent attacks utilizing the exploit. Of course, it is also possible for a zero-day attack to go unnoticed if the result is subtle and the attacker does not do anything that causes the attack to be noticed. If everything is kept quiet, the attacker can continue to exploit the vulnerability until it is eventually noticed, until the vendor discovers the error leading to the vulnerability through their own efforts, or until another attacker discovers and exploits it in a more noticeable fashion.
There have been cases where a vulnerability has gone unnoticed for several years until a vendor discovers it. It is impossible to know in a case such as this whether somebody else had previously noticed it and had been exploiting it for their own benefit. The amount of time between when a vulnerability is detected (exploited) and when the vendor has a patch for the vulnerability (or vendors have a mechanism to counter it) is generally known as the vulnerability window.
Zero-day attacks are, by definition, often hard to discover and prevent. Because it is a new vulnerability, firewall and intrusion detection/prevention vendors won’t know about it and will therefore not have a signature in their database of vulnerabilities that matches it. Firewalls and signature-based IDS/IPS will therefore most likely not be able to block, detect, or prevent an attack utilizing the vulnerability. Because of the level of damage a zero-day attack can cause, the topic of how to counter zero-day exploits occupies considerable time in the security research community.
On the nontechnical side, ways to address zero-day attacks center around the speed at which information about them can be disseminated once a zero-day exploit is discovered. Discovering the exploits can occur in a number of ways. An easy one occurs when the individual who discovered the exploit or developed an exploit makes it available to the “hacking” community. Another way in which they may be discovered is if an attack utilizing the exploit is discovered and an analysis to determine how the attack occurs reveals the new vulnerability. A tool that has sometimes proven to be useful in the discovery of new exploits is the honeypot or honeynet. The concept behind both of these terms is to construct a system or network that appears to be official but in fact is not. The honeypot or honeynet can then be monitored, looking for individuals who are attempting to attack systems. Because honeypots or honeynets are not official, there shouldn’t be anybody who is trying to connect to them, so any attempted connection is likely to be somebody looking for systems and networks to attack. By monitoring the activities of the attackers, we can observe their tools and methods. Therefore, should a zero-day attack be attempted, its existence may be revealed.
Once a new exploit is discovered, receiving word about it becomes important in order for individuals to be prepared to address it. Some in the security community argue against the posting of information regarding the discovery of new vulnerabilities. The argument is that posting this information makes it easier for individuals in the “hacking community” to find out about these vulnerabilities and to then use them in attacks. The counter-argument is that the owners of systems need to know about these attacks so they can be prepared. Keeping information on a new exploit secret until it is announced along with a patch from a vendor simply provides a window of opportunity for attackers during which they can utilize the vulnerability without too much fear of being discovered. Even if a patch has not been issued to fix a vulnerability, the knowledge that it exists and details on what to look for will at least let security administrators know whether their own systems have been compromised.
Although we said that signature-based security systems will generally not be able to detect a zero-day attack because it will most likely exhibit a different signature, other methods are being used to spot potential new vulnerabilities. Often, this takes the form of attempts to identify unusual traffic patterns for the system or network. Unusual patterns may very well indicate attempts to attack the system. Knowing what is unusual means that the normal activity for the system or network needs to be known. Activity outside of the normal activity can then be identified. The unusual patterns may be part of a known attack; in fact, some activities (such as “general probing of a network”) are so common that although they are not part of the activities for which the system or network was intended, they can nonetheless be identified easily. Occasionally, however, a pattern may be discovered that is not part of the normal activity for the system or network and is also not indicative of any known attack pattern. In this case, it could be a strong indicator of a new exploit.
Of course, the best way to counter zero-day attacks is to prevent them in the first place, which means doing a better job of building bug-free software. This requires better design, coding, and testing practices. Operating systems have also taken steps to limit the damage events such as buffer overflows can have on a system. This makes it less likely that a vulnerability can have a disastrous impact on a system. Data Execution Prevention (DEP), for example, is an attempt to prevent programs from executing in memory locations that should contain data and not code. Address Space Layout Randomization (ASLR) moves pieces of programs around randomly in portions of memory in an attempt to make it harder for nefarious code segments to jump to some place in memory that they shouldn’t. Structured Exception Handler Overwrite Protection (SEHOP) attempts to make stack overflows harder to accomplish by checking to make sure that chains of exception handlers (interruptions) aren’t hijacked. These three techniques make it more difficult for any piece of code to take over a system, without knowing a precise attack signature.
Whitelisting is also seen as an approach to address at some level the issue of zero-day exploitation. This is the term used to refer to the process of providing a list of approved entities that are allowed to accomplish a certain task. A common example of this is found in browser security, where lists of approved URLs or IP addresses can be used to limit the sites a user is allowed to go to. The same technique can be used to limit who may access a system as well. The concept can also be extended to systems where lists of approved applications can be provided to limit what is allowed to be run on the system.
Another approach some have taken to avoid the exploitation of zero-day vulnerabilities is to offer rewards for previously unknown vulnerabilities. Approaching the problem in this way provides a financial incentive for individuals to try and exploit systems, thus increasing the likelihood that vulnerabilities are found. This method is looked upon differently by various vendors and security companies, and it cannot be said that it is a universally accepted approach to the problem.
Threat Model
Threat modeling is a process of identifying and analyzing a threat’s objectives, attack vectors, requirements, and the various ways in which it might exploit the vulnerabilities of an asset. Since threats are both numerous and shaped according to the assets themselves, many kinds of threat models will need to be created. To diversify analytical perspectives, threat models can be broader (organizationally based) in nature or more specific (asset focused versus attacker focused).
Despite the variety of threats, threat modeling is a cyclical process in that you can apply the threat modeling process to different kinds of threats.
Some well-known threat-modeling methodologies for IT purposes include the following:
• STRIDE Created by Microsoft to aid developers in identifying threats to programming projects.
• P.A.S.T.A. A seven-step process, threat-focused threat model that encompasses organizational objectives, technical requirements, and compliance issues.
• Trike Uses threat modeling for risk management and security auditing purposes.
• VAST A threat model designed for integration with an organization’s software development life cycles.
Researching Security Implications of Emerging Business Tools
There is a constant demand in organizations to find new ways to conduct business in faster, more efficient ways. Plenty of vendors are developing new tools or improving on existing tools that will appeal to this demand. When an organization finds a new tool it believes will help, the possible security implications should be considered, but all too frequently they are not. As previously discussed, technology such as mobile computing provides tremendous advantages in terms of allowing employees to continue to work no matter where they may be. They can stay in touch with their office so that important e-mail and messages are not missed, and they can conduct many routine office tasks almost no matter where they are. This freedom doesn’t come without a price, however, as a new avenue for attacks on the organizations is introduced.
When an organization is considering adoption of a new product or type of technology, where can they go in order to determine the security implications of the decision? The vendor may provide information on this, but if it is not favorable to their product, this is not likely to happen. Another possibility is to hire or employ security testers who can search for security holes before the product or technology is fully deployed within the organization. Any number of security companies can provide penetration testing services both before and after deployment. Periodic outside penetration testing is considered a good security practice because it provides an additional fresh look at an organization’s security posture from individuals who have no preconceived notion of the organization’s security status. A simple search of the Internet may also provide information on security issues related to a product or new technology, and several federal programs (such as the national Information Assurance Partnership validated products list as well as the Approved Products List kept by DISA, shown in Figure 17-2) can provide information on certain products that have been evaluated.
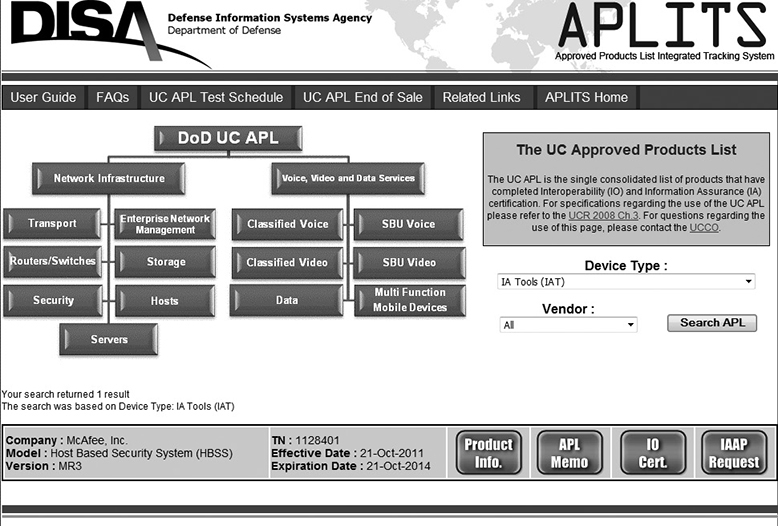
Figure 17-2 The DISA Approved Products List provides a list of products that have completed interoperability and information-assurance certifications for the Department of Defense.
Evolving Social Media Platforms
Social networks at first may seem harmless because they appear to simply be a way for individuals to “stay connected” to friends and families. Unfortunately, there are a couple of issues that security administrators need to be aware of associated with these networks. First is the fact that these networks are increasingly being used by attackers to attempt social-engineering attacks. These are surprisingly successful due to the nature of social networks, which encourage the sharing of information with an assumed level of trust—often misplaced.
Attackers also will attempt to trick users into going to potentially malicious sites where personal information—or corporate data, if the machine accessing the site is a work system—may be extracted. The common use of shortened URLs on social networks only adds to the problem.
Another issue with social networks is the possibility for employees to post sensitive information about the company. For decades, details of mergers or other important business transactions have been discussed by individuals when they weren’t supposed to. The issue today is that if done on a social networking site, the ability for it to be seen by large numbers of individuals and to quickly spread beyond an individual’s closest friends is tremendous.
Integration Within the Business
At first, organizations looked for ways to limit, or prohibit outright, the use of social networks in the workplace. As their use increased, however, and as the next generation of employees, raised on social networks, entered the workforce, most organizations have realized that social networks are now part of life, and instead of trying to prohibit their use, they need to help employees recognize the appropriate way to use them. Social media is beneficial to businesses in various ways, including the following:
• Crowdsourcing and soliciting public opinion through polls and user surveys
• Product promotion
• Brand exposure
• Competitive analysis
• Customer service and support
• Recruitment
• Business leads and sales
• Background checks to hire employees
Big Data
Big data refers to huge amounts of mostly unstructured data that is often too large for standard systems to process. Yet, big data is already seeing a lot of action in government, law enforcement, manufacturing, healthcare, education, media, insurance, science, financial trading, and sports analytics. It allows quick detection of errors and scams, real-time analysis, and has been especially valuable in the healthcare industry due to research and disease prevention reasons. However, the sheer volume of data can make analysis difficult, plus it aids privacy invasion due to the amount of data being aggregated about people. When describing characteristics of big data, consider the following factors:
• Volume The quantity of data
• Velocity The speed at which that data is generated and processed
• Variety The type and behavior of data
• Veracity The accuracy of data
• Value The quality of data
In order to tame the immovable object that is big data, it takes an irresistible force—artificial intelligence. Artificial intelligence and machine learning are discussed next.
AI/Machine Learning
Artificial intelligence (AI) involves computers performing tasks with a human-like intelligence. These machines are capable of incorporating perception of, and adaptation to, their environment in order to succeed at completing a task. Typical software and hardware devices have all of their knowledge pre-programmed internally. This “inherited” knowledge is then used to perform various tasks. However, the future of technology behaviors will not come from inherited knowledge but from learned knowledge. It is believed that a tool can exhibit greater levels of intelligence by acquiring information itself versus having the information built in.
Whenever most people think about AI, their thoughts inevitably become apocalyptic—machines becoming self-aware and turning on their human creators. Although AI is still in its early stages, human history reveals that most inventions designed for good are eventually repurposed with malicious intent. Although the jury is still out, we’re already seeing both positive and negative outcomes from AI.
The technological intelligence stemming from AI allows our software to learn from the consequences of past events in order to predict and identity threats. At the same time, hackers are also using AI to automate the collection of a victim’s information and then filtering out the irrelevant parts to launch a more focused and potent attack on vulnerabilities. Yet, AI is a complex topic that can be broken down into the following subgroups:
• Machine learning A type of AI where computers use certain built-in learning factors to guide their learning and adaptation of data. Although the learning aspects are guided by these statistical baseline factors, the outcomes themselves are dynamic in nature—hence, the purpose and value of “learning.”
• Deep learning A deeper form of machine learning in which technology tools don’t use any baseline factors to guide its learning; rather, the technology decides for itself what learning and classification modalities to implement based on the inputs it receives. This allows for even more human-like intelligent behaviors than generalized machine learning.
Common applications of AI/machine learning include Google’s search engine results, Amazon’s product recommendations, and Facebook’s news feed customizations. You may have seen IBM’s AI tool called Watson on various TV commercials in recent years. It utilizes machine learning and deep learning to intelligently discover and mitigate cybersecurity threats.
Global IA Industry/Community
The information assurance community is large—and growing. Numerous training companies, conferences, seminars, workshops, and webinars exist that can help security professionals stay on top of current security issues and developing trends. Overall, the community has a tendency to be very friendly, and any number of individuals are more than willing to help struggling security administrators having specific problems with their systems. Blogs and tips can be found discussing a variety of common security problems, which can be very useful for both those new to the community and those who are faced with a new problem they haven’t seen before. In addition, organizations such as the SANS Institute (a private U.S. company, with SANS derived from Sysadmin, Audit, Networking, and Security) provide a number of free resources in addition to their paid training that newcomers will find useful. In particular, the Reading Room (which can be found from the SANS home page at www.sans.org) includes numerous papers on dozens of topics written by security professionals going through one of its many courses. SANS also publishes a list of the top 25 programming errors and the top 20 critical controls, which can also be extremely helpful to individuals in the community. The SANS site is one that both novice and experienced security professionals will want to keep track of.
Other helpful hints can also be often found in one of the hundreds of security vendor sites. Many companies have produced white papers on a variety of security topics. In addition to white papers, quite a few open source security tools can be found on numerous sites. Obviously, a word to the wise concerning downloading and running software from unknown sites—what better way to convince individuals to run your exploit malware than to disguise it as a security tool designed to help secure the very system that the exploit is designed to take advantage of. Always be careful of what sites you visit, and be especially careful of any software you might download from them.
Computer Emergency Response Team (CERT)
Computer emergency response team (CERT) has a few different contexts. There’s the general usage involving any expert group of security professionals that implement an organization’s incident response plans. Then there’s the coalition of official security teams, or CERTs, scattered throughout the world—more accurately referred to as computer security incident response teams (CSIRT)—that assist organizations with incident response processes in their respective regions. Last, there’s the CERT trademark held by the Software Engineering Institute at Carnegie Mellon University.
A well-known U.S.-based CERT known as the United States Computer Emergency Readiness Team (US-CERT) provides incident response guidance to various enterprises.
Conventions/Conferences
One of the best ways to stay on top of what is happening in the security community is to attend one of the numerous computer security–related conferences that exist. Not all conferences aim to reach the same audience, so choosing which to attend will depend on individual goals. Security-related conferences can be roughly broken into three categories: industry, academic, and “hacker.” The best-known industry conference is RSA. This extremely large conference also includes one of the largest and best vendor exhibitions. The conference draws individuals from across government, academia, and industry as well as features national-level keynote speakers. Often with over a dozen simultaneous tracks, choosing the talk to attend during any given session is often challenging. Having over a dozen tracks ensures that the chance of finding a talk of interest to you will be very high. The only downside to the conference is the cost, which is fairly high in comparison to some of the other security conferences that exist.
Another large conference is Black Hat. The original Black Hat conference was in Las Vegas, held immediately before the annual DEFCON “hacker” conference. Las Vegas continues to be the largest Black Hat conference, but other versions exist in Europe, Asia, and the Middle East. The original intent of Black Hat was to bring individuals from the different “sides” of the hacking community together. Thus, it appealed to those in the government (law enforcement) as well as the “hacking” community. Today, it probably has somewhat of an even split between the government, industry, and “hacking” sectors, with a few from academia thrown in as well. The vendor area is not as large as RSA, but it is growing. Like RSA, it also has multiple simultaneous tracks, which again sometimes makes it challenging to decide on which talk to attend.
USENIX is a computer systems professional organization that, among other things, sponsors a number of different conferences. One of these is the USENIX Security Symposium, which has been conducted for over 20 years. It is a large security conference and serves as a bridge between conferences more focused on industry and conferences designed for researchers and the academic community. There are a number of academic workshops, symposiums, and conferences. No matter what the security research topic is, chances are good that there is a meeting, conference, workshop, or symposium on it somewhere.
Some of the better known and larger conferences include the IEEE Symposium on Security and Privacy, the Annual Computer Security Applications Conference, and the ACM Conference on Computer and Communications Security. All of these address a broad range of security topics. An example of a more focused security conference is the European Cryptology Conference (EuroCrypt) or the International Symposium on Recent Advances in Intrusion Detection (RAID).
Another type of conference focuses more on the “hacking” side of security and was originally designed more as an “underground” event that appealed to those in the community. DEFCON is the best known of these conferences—although it no longer is anywhere close to being an underground conference, nor is it attended only by those in the hacking community. Today, it probably has an even balance between professional security personnel from government, academia, and industry and individuals who might fall more into a “hobbyist” category. These conferences pride themselves as being not only more technical than some of the others, but also more practical and “hands on.” An additional attribute of conferences in this category is their more relaxed nature. Another example of a conference in this category is HOPE (Hackers On Planet Earth), sponsored by the 2600 magazine. Living up to its more relaxed nature, this is not an annual event but has been held on a periodic basis. Since 2000, it has occurred every two years. Another well-known conference seeking for a more relaxed atmosphere is CanSecWest.
Research Consultants/Vendors
Although a wide variety of security resources are available for research, two that should not be neglected are security consulting agencies and vendors. Although many organizations have sufficient security expertise on staff, some will feel more comfortable outsourcing certain security tasks to a security consulting company. However, which consulting firms should we consider? According to a Gartner 2016 Top 10 Security Consulting Services Firms list, the security organizations Deloitte, EY, PwC, KPMG, IBM, Accenture, Booz Allen Hamilton, HP Enterprise, Optiv Security, and BAE Systems, in that order, are the largest in terms of revenue. Any of these would be a good starting point for a researching consultant.
Finally, we have the vendors themselves that wrote the software or manufacture the hardware we’re using. Be sure to visit vendor websites for the latest news, alerts, downloads, documentation, firmware, and patches for your products. Be mindful of their support hours, region, and time zone, just in case you need support. Also, any contracts or service level agreements that they may have with you should be consulted during times of degraded services.
Threat Actor Activities
A question that administrators sometimes ask is, “Who would want to attack us?” The implication being that the company doesn’t do anything that the administrator would view as being worthy of interest to a cyber attacker. From the attacker’s standpoint, there are two general types of targets: targets of opportunity and explicit targets. If an organization is being targeted because of who they are or what sector they are in, they are an explicit target. If, on the other hand, the target was not specifically chosen for who they are but instead because they are running a specific piece of software or using a specific piece of hardware, then they are a target of opportunity. Targets of opportunity generally occur when an attacker is looking for somebody, anybody, who might have a system that is vulnerable to a specific exploit. The attacker is not concerned with who they are; they just want to gain access to somebody. If the attack is attempted and fails because the organization has protected itself against the exploit being used, the attacker moves on to the next organization and tries the attack against it.
On the other hand, if a specific exploit fails against the chosen target in an explicit attack, the attacker doesn’t move on to another potential target but instead moves on to another exploit to try. The goal for an explicit attack is to gain access to a very specific target. The goal of an attack on targets of opportunity is to find somebody who is vulnerable to an exploit.
Let’s return to the original question of who would want to attack a specific organization? It should now be obvious that for some attackers, the organization simply doesn’t matter. It is a matter of the technology being used. If the organization uses technology that the hacker feels comfortable exploiting, it may not matter whether the organization has assets that are inherently valuable to the attacker or not. In other words, all organizations, regardless of what they think hackers want, are at risk of being hacked; therefore, they must prepare for it.
Determining who the attackers might be depends on the type of target. The vast majority of attacks are unstructured attacks against targets of opportunity. The definition of what an attack in this case is very broad and can range from somebody simply testing to see if they can guess a password for an account, to an individual who just learned about an exploit and wants to find somebody who is vulnerable to it. A term that is often used in the community to describe the majority of individuals in this category is “script kiddies”—individuals who may have simply downloaded an exploitation script and are running it. They probably know very little about the vulnerability being exploited and might not have ever been able to actually create the exploit themselves. Unstructured attacks are generally not targeted against a single infrastructure (unless the new exploit is targeting systems only used in a specific sector) and are conducted by individuals with little to no financial backing.
Two additional groups that are often placed in the unstructured threat category are hacktivists (individuals who attack computer systems and networks in order to promote a cause or ideology, or “hacking activists”) and hacking groups. Hacking groups are simply groups of individuals interested in computer systems and security who band together to help each other learn more about the systems they attack. An example of hacktivism might be a group of individuals supporting animal rights who deface the website of a company that sells fur coats. Individuals in these categories may be loosely organized with no real financial backing, or they may, as is sometimes seen in the case of ideological hacktivists, have a bit more support and organization. Hacking groups also vary in the level of support and expertise they have. In both cases, the groups may no longer be considered to be in the unstructured threat category as they become more organized with a specific purpose in mind and if they begin to receive financial backing.
A structured attack is one in which a specific organization (or sector) is being targeted and is conducted by individuals with some financial backing and who have more time in which to obtain their goal. An example might be individuals with backing from organized crime attempting to gain access to computer systems owned by a financial institution. A highly structured attack is one in which the attacker has considerable time and financial backing in order to be able to conduct the attack. Multiple vectors (including attempts to usurp insiders) may be tried, and spotting this type of attack will be extremely challenging. The idea of the advanced persistent threat will often fall into this category, and attacks in this category will generally be supported by organizations with time and money, such as nation-states or organized crime going after extremely high-value targets.
Another way that attackers are sometimes categorized is in terms of what “hat” they wear. In this case, white hats are individuals in the community who perform what is often referred to as ethical hacking—also known as penetration testing—in order to help organizations secure their computer systems and networks. They do not break any laws in conducting their activities and work with the permission of the organization they are attacking when conducting their penetration attempts. On the other end of the spectrum are the black hats, who do violate laws with their activities and attack computer systems without permission for a variety of purposes, including theft, revenge, ideological purposes, or simply the intellectual challenge and the reputation they may obtain within the black hat community. In between these two groups are the gray hats, who may attack systems without permission from the organization (and thus are committing a crime) but are not driven by personal economic gain or other purposes, as are the black hats. Instead, they will often inform vendors of the problems or vulnerabilities they discover in software so that the vendor can fix them. Technically, they have acted illegally, though not for nefarious purposes.
In all three categories, the techniques and tools are often the same (although each may have developed their own individual tools), and it is simply whether the hacker has the permission of the organization and the intent that differentiates between which hat the person is wearing.
Emerging Threat Sources
One of the factors that makes cybersecurity such a challenging endeavor is the fact that the cost of entry for attackers is so very low. During the Cold War era, a nation wishing to become a superpower would have to spend considerable money on weapon systems and research. To become a cyber superpower, on the other hand, requires considerably less investment. The only entities that had the type of funding that would have allowed them to become superpowers during the Cold War were nations. The same is not true of cyber superpowers. The organizations that would have been targeted by the different sides in the Cold War were confined to the military, the defense industrial base, and the national infrastructures. The same is not true during the cyber era, where many different organizations may find themselves the target of an attack. The threats are different as well. Script kiddies, who will generally have no or only loose affiliation with any entity, have already been mentioned, but other potential threats exist as well. Organizations within one of the key national infrastructure sectors may find themselves the target of attacks from nation-states, such as have been seen in the power sector the last few years. Any organization that collects payment via credit cards could find itself a target of criminal organizations or individuals wishing to gain access to the credit card information.
Organizations that are part of an industry that is considered controversial may find themselves the target of hacktivists who may try to deface their websites in order to obtain publicity for their cause. Another interesting and more recent threat that has impacted individuals in different sectors is the rise of organizations such as Anonymous, which claims to be a group of hackers interested in various causes. In one example, this group announced an attack on the city of Orlando, Florida, because of certain activities that were going on within the city. This is an example of an emerging threat that was not heard of just a few years ago. Cities have generally not been the target of attacks, but now they may find themselves the focus of one because of any number of reasons—a specific industry in the city, a government organization with offices in the city, or policies or politics of interest to the city. What can be said of organizations and threats to them today is that no matter who you are, there is somebody who will attack you.
It should probably be mentioned that two of the issues driving the emerging threat sources are the level of dependence that society now has on computer systems and networks and the growing level of technical understanding of individuals and employees. As a result of this, individuals such as hacktivists see the opportunity to make their cause known through a new medium that arguably will have a much better chance of being seen by more individuals than traditional techniques such as protests outside of specific facilities. Disgruntled employees, instead of having no recourse or opportunity for revenge, now have a variety of easy ways they can address perceived grievances or actions taken by their heavily cyber-dependent companies. The disgruntled employee, in fact, has become one of the most dangerous threats to organizations because they will know what best to target in an organization in order to have the greatest impact on it.
Nation-states and terrorist organizations now no longer need to rely solely on physical attacks in order to affect adversaries. With the heavy reliance on the Internet and computer systems, they can target the cyber infrastructures of a nation’s critical infrastructures (for example, power, telecommunications, water, transportation, and so on) in order to disrupt the targeted nation. We have already seen this in attacks on both the nations of Estonia and Georgia in separate conflicts where cyberattacks were used to disrupt critical infrastructures or were used in conjunction with physical attacks. Finally, it has become painfully obvious how the dependence organizations place on the Internet in order to conduct financial transactions has led to a rise in attacks on computer systems and networks by individual criminals as well as organized crime organizations.
Chapter Review
This chapter covered research, development, and collaboration concepts. More specifically it covered how to apply research methods to determine industry trends and their impact to the enterprise.
The first section discussed the need for performing ongoing research into industry best practices regarding OS hardening, security policies, password policies, and end-user training. It also touched on the latest technologies as well as security systems and services such as AI, big data, blockchain, cloud access security brokers, containerization, homomorphic encryption, IoT, quantum computing, and user behavior analytics. It also mentioned technological evolution from the perspective of RFCs and ISO standards because these documents provide us with official sources of technological information.
The next section covered threat intelligence by starting off with some basic threat vocabulary. Then it provided coverage of the latest attacks, such as ransomware (particularly WannaCry), AI, IoT, state-sponsored hacking, sandbox-evading malware, app store malware, cryptojacking, dronejacking, GDPR, and cloud computing. The next topic covered zero-day vulnerabilities due to the dangers inherent in vendors not being aware of the vulnerabilities yet; therefore, no patches are available. Various mitigations of zero-day vulnerabilities were proposed as a result. We then covered threat modeling and how it helps us to analyze the attack vectors, requirements, and motivations behind threats attacking assets.
The next section involved researching security implications of emerging business tools. Starting this off was the evolving social media platforms and how they integrate with businesses. Social media provides various ingress and egress risks to businesses; yet it also provides businesses with many rewards through product promotion, brand awareness, customer service, customer leads and sales, and more. Big data was discussed, including basic vocabulary and how it helps us in many industries with analytics, plus error and scam detection. We then covered AI/machine learning and how its increased intelligence will automate information collection and attacks, but will also be equally effective at defending organizations with said intelligence.
The final section covered the global information assurance industry and communities. The first of these are computer emergency response teams (CERTs), which are collections of expert security groups that provide incident response assistance for both their respective organizations and for societies at large. We then provided coverage of security conventions/conferences such as RSA, Black Hat, DEFCON, and so on, and how they provide a tremendous networking and informational opportunity for security practitioners from all over the world. We then talked about researching consulting companies and vendors in order to provide us with much-needed security assistance, tools, documentation, maintenance, and more. We then discussed threat actor activities by covering the different types of malicious attackers out there and their various motives and techniques. We finished the section discussing emerging threat sources such as nation-state hackers, disgruntled employees, and more.
Quick Tips
The following tips should serve as a brief review of the topics covered in more detail throughout the chapter.
Performing Ongoing Research
• A good chunk of your time should be spent conducting research—either formally as part of your job requirements or informally to keep up your skills.
• Visit vendor websites for the latest information on vulnerabilities, updates, FAQs, other software downloads, and best security practices.
• Use official information security sources such as RFCs, ISO, NIST, ISACA, EC-Council, (ISC)², and SANS.
• Subscribe to security mailing lists such as Bugtraq, CERT Advisories, and Security Weekly.
• Visit vulnerability websites such as the CVE database, SecurityTracker, and SecurityFocus.
• Visit vendor-specific social media profiles on Facebook, Twitter, and LinkedIn.
• Attend security convention events like Black Hat, DEFCON, and HOPE.
• The introduction of any new technology to an organization must be accomplished with an examination of the possibility for exploitation of the technology by others.
• The IETF is a large, international community of network administrators, designers, vendors, and researchers who are concerned with the evolution of the Internet and its continued operation.
• ISO produces and disseminates proprietary, industrial, and commercial standards.
Threat Intelligence
• Threat intelligence is the methodical process of collecting information about cybersecurity threats.
• A zero-day vulnerability occurs when a software error or hole impacting security is discovered and exploited before a patch is developed to address the vulnerability.
• The best way to counter zero-day vulnerabilities is to prevent them in the first place through better coding practices.
• Threat modeling is a process of identifying and analyzing a threat’s objectives, attack vectors, requirements, and the various ways in which it might exploit the vulnerabilities of an asset.
• The five steps for threat modeling are identifying attacker objectives, identifying attack vectors and attack requirements, identifying targets, assessing targets, and identifying mitigation techniques.
Researching Security Implications of Emerging Business Tools
• Organizations should establish policies for the use of social media in the workplace and should provide guidelines on who can speak on behalf of the organization.
• Big data refers to huge amounts of mostly unstructured data that is often too large for standard systems to process.
• Artificial intelligence (AI) involves computers performing tasks with a human-like intelligence.
• Machine learning is a type of AI where computers use certain built-in learning factors to guide their learning and adaptation of data.
• Deep learning is a deeper form of machine learning in which technology tools don’t use any baseline factors to guide their learning; rather, the technology decides for itself what learning and classification modalities to implement based on the inputs it receives.
Global IA Industry/Community
• Numerous training companies, conferences, seminars, workshops, and webinars exist that can help security professionals stay on top of current security issues and developing trends.
• CERT is a coalition of official security teams scattered throughout the world that are more accurately known as computer security incident response teams (CSIRTs).
• One of the best ways to stay on top of what is happening in the security community is to attend security conferences such as RSA, Black Hat, DEFCON, USENIX Security Symposium, IEEE Symposium, and so on.
• Research into security consulting agencies and hardware/software vendors is a great way to gain insight or support on enhancing organizational security.
• From the attacker’s standpoint, there are two general types of targets: targets of opportunity and explicit targets.
Questions
The following questions will help you measure your understanding of the material presented in this chapter. Read all the choices carefully because there might be more than one correct answer. Choose all correct answers for each question.
1. Best-practice documents are useful for security personnel for which of the following reasons? (Choose all that apply.)
A. Following them will ensure that the organization will be free from security problems (breaches).
B. They allow security personnel to see what others may do in similar situations to the one they find themselves in.
C. With a limited amount of time, security personnel need to know what things to do first or to concentrate on what will yield the largest payback.
D. In case of a breach, the organization can show that it at least did what others are doing to secure their own systems, thus it has shown a reasonable level of due diligence.
2. Which of the following is true about the introduction of new technologies into an organization?
A. Because the security issue has been known for a while, new technologies are produced with security in mind, and introducing them will have no adverse impact on the security of an organization.
B. The introduction of new technology to an organization will usually result in a more secure network environment.
C. New technologies can have a negative impact on the security of an organization, potentially introducing new vulnerabilities.
D. New technology is more secure than older technology but can still have security implications if not installed correctly.
3. Your network administrator has informed you that your organization will be switching from IPv4 to IPv6. You’ve been asked to determine what impact this might have on the security of the corporate network. You know that others have also made this same move in their organizations, so you are sure that there must be some documents on what the security implications might be. Besides documents from vendors that often are obviously also trying to sell you a product or service, which of the following might you also check to learn as much about this new technology and its security implications from an objective standpoint?
A. There is no real way of determining the security implications of new technology before you implement it on your own network.
B. The National Institute of Standards and Technology (NIST) produces best-practice documents for all new technology that is introduced to the Internet.
C. RFCs are used to seek input from the community on issues and changes in technology that have an impact on the larger Internet community.
D. The International Internet Standards Organization must approve all new technology changes that will have an impact on the Internet before they are implemented. This organization produces standards for the implementation and use of new technologies, which you can download and follow.
4. Your CEO just came back from a luncheon where the speaker discussed zero-day threats. Your CEO has expressed a concern that your organization could be hit by one of these and wants to know what can be done to protect the organization from such a threat. The CEO wants you to do whatever is necessary to guarantee that such an event won’t impact your organization. What is your reply?
A. You tell your CEO that you can guarantee that you will never be susceptible to a zero-day exploit, but it will require a dramatic increase in the security budget so you can employ all possible countermeasures.
B. You try to allay some of the CEO’s fears by discussing how as long as you employ what are considered the standard best practices for your industry, you should be pretty much guaranteed that you will not be hit by a zero-day exploit.
C. You use Stuxnet as an example and explain that zero-day exploits are only the concern of specific sectors (such as the critical infrastructures such as power and water) and that because your company is not part of one of them, it is not going to be hit with an event such as Stuxnet.
D. You explain that by their very nature, zero-day exploits are extremely difficult to detect and that there is no way you can guarantee the company will never be impacted by one. You explain that there are steps that can be taken to minimize the potential impact and to increase the likelihood that you catch one quickly, but you can’t eliminate the possibility totally.
5. Which of the following are considered threats in computer security? (Choose all that apply.)
A. Hackers
B. Organized crime
C. Insiders
D. Lightning
6. Which of the following statements are true of social media/networking? (Choose all that apply.)
A. Social networks are harmless and present no security concern to an organization.
B. Social networks can be used as an avenue for attackers to have users inadvertently install malware on corporate systems and networks.
C. Employees might post sensitive information on a social networking site that could harm an organization.
D. Social networks should never be used by any business.
7. Which of the following are ways that an organization can determine the security implications of a new technology? (Choose all that apply.)
A. Check with the Better Business Bureau, which keeps a list of security vulnerabilities for products.
B. The vendor may supply information, as long as it benefits the product.
C. The organization can have a vulnerability or penetration test performed on the new product or technology.
D. Check to see what has been said about it on the Internet.
8. Which of the following statements is true about the information assurance community?
A. It is large and continually growing.
B. It has remained static for the last decade, neither growing nor shrinking.
C. With the downturn in the global economy, the security community has also been affected and has shrunk from its peak, which occurred around 2001.
D. It is not a legitimate source for security information.
9. Which of the following conferences was created to draw its audience from “all sides” of the hacking community—that is, from industry, government (including law enforcement), academia, and the hacking community?
A. DEFCON
B. RSA
C. Black Hat
D. USENIX
10. Which of the following is a characteristic of a highly structured threat?
A. It is conducted by script kiddies.
B. Attackers will take weeks or even months to accomplish their goal.
C. The attackers have considerable time and financial backing.
D. Attackers concentrate on only one attack vector until successful.
11. One type of attack occurs when an attacker is looking for somebody who has a system that is vulnerable to a specific exploit. The attacker is not concerned with the type of organization that is using the system, but only wants to find organizations that are utilizing the specific system or software. This is known as a(n):
A. Explicit target
B. Target of opportunity
C. Non-sector-based attack
D. Sector-specific attack
12. What is a “hacktivist”? (Choose all that apply)
A. An attacker who targets only controversial organizations.
B. A term used to refer to “hackers” who are not as talented and are not part of any organized group.
C. A term used to refer to individuals who are part of an organized hacking group targeting controversial organizations.
D. An attacker who “hacks” in order to obtain publicity for some cause.
13. Which organization is responsible for publishing RFCs?
A. ISO
B. IEEE
C. IETF
D. NIST
14. Which of the following are examples of malicious hackers who always hack for political or social reasons? (Choose all that apply.)
A. Suicide hackers
B. Hacktivists
C. Script kiddies
D. White hats
15. Which of the following best describes a zero-day vulnerability?
A. A vulnerability that can be quickly mitigated.
B. A vulnerability that disappears on its own.
C. A vulnerability that is unknown to the vendor of the vulnerable product.
D. A vulnerability too complex or risky to ever develop a patch for.
Answers
1. B, C, D. All of these are reasons that following security best practices will be useful for security professionals.
2. C. The introduction of some new technologies can absolutely have an impact on the security of the system and should therefore be closely examined to see what new vulnerabilities might have been introduced. An example of this is the introduction of wireless networks to an organization.
3. C. RFCs are often used to seek input for security issues due to changes in technology that may have a large impact on the Internet. Although the possibility was not provided, you can also often find fairly objective white papers produced by various vendors discussing security issues related to new technology.
4. D. Zero-day exploits can hit any software, so there is no way to guarantee that a piece of software your organization uses won’t be impacted by one. There are certainly steps you can take to make it less likely you will suffer a catastrophic impact from a zero-day exploit, but you simply can’t guarantee you will never be impacted by one.
5. A, B, C, D. All these can be considered threats to your computer systems and network.
6. B, C. Social networks can be a problem from several perspectives, including providing a new avenue for the insertion of malware and also the possibility of employees posting sensitive information.
7. B, C, D. The vendor may supply information on the security implications, but you can’t always count on this. If they have considered the implications and addressed them, then they will probably be mentioned. If not, they will be avoided and you will need to check elsewhere. If you have already purchased the product, you can conduct a vulnerability or penetration test, either using your own security personnel to conduct it or by hiring a third party. Finally, don’t forget the Internet. Chances are good that somebody has written something about the technology and its security implications already.
8. A. The community has been growing and doesn’t show any signs of a downturn.
9. C. Black Hat was originally created to bring together individuals from all sides to discuss security issues. It has grown to become a very large conference with attendees from all over the world and from every sector.
10. C. Highly structured threats are characterized by attackers who have considerable time and financial backing in order to accomplish their goal.
11. B. This is a description of a target of opportunity.
12. C, D. A term used to refer to individuals who are part of an organized hacking group targeting controversial organizations. Also, a hacktivist has a cause to promote and will attack sites associated with that issue or cause, but may also attack less protected sites in order to gain publicity.
13. C. IETF publishes RFCs.
14. A, B. Suicide hackers are essentially hacktivists who are willing to get caught or “take one for the team” in order to advance their agenda.
15. C. It a vulnerability that a product’s vendor is currently unaware of; therefore, the vendor has not developed a patch yet.




