CHAPTER 5
Network Security Components, Concepts, and Architectures
This chapter presents the following topics:
• Physical and Virtual Network and Security Devices
• Applications and Protocol-Aware Technologies
• Advanced Network Design (Wired/Wireless)
• Complex Network Security Solutions for Data Flow
• Secure Configuration and Baselining of Networking and Security Components
• Software-Defined Networking
• Network Management and Monitoring Tools
• Advanced Configuration of Routers, Switches, and Other Network Devices
• Security Zones
• Network Access Control
• Network-Enabled Devices
• Critical Infrastructure
All chapters up until this point focused on different aspects of risk management. Risk management was important enough to cover first because security controls cannot be accurately prioritized and allocated until after we’ve performed all relevant risk management processes. We are beginning a new series of chapters that focus on enterprise security architecture. This chapter focuses on the integration of network and security components, concepts, and architectures. We’ll dig into a ton of hardware and networking devices, data flow and network design concepts, software-defined networking, and security zones—just to name a few topics.
Physical and Virtual Network and Security Devices
Considering this chapter has a strong focus on integrating network and security components into an enterprise, we’ll start with the devices themselves. Knowledge of the strengths and weaknesses of these devices is important for securing an enterprise.
UTM
Unified threat management (UTM) incorporates the functions of multiple network and security appliances into a single appliance. Although the device looks much like any other network appliance, it may integrate several additional security functions, such as the following:
• Antimalware
• Antispam
• Content filtering
• Data loss prevention (DLP)
• Firewall
• Intrusion detection system (IDS)
• Intrusion prevention system (IPS)
• Load balancing
• Quality of service (QoS)
• Virtual private network (VPN)
Like multifunction printers, UTM’s all-in-one approach provides several benefits, including single-vendor consolidation from respected names like Cisco. Whether we’re experiencing a firewall, QoS, or spam issue, qualifying issues can be conveniently escalated to a single Cisco support line. Otherwise, all UTM security issues handled internally are addressed through a single integrated management tool. This greatly simplifies network management since you don’t have to learn and configure multiple independent devices. Access to this tool uses a single set of accounts rather than different account sets scattered among multiple separate devices. UTM appliances also help organizations conserve rack space, given their individual footprint. For the same reason, UTM appliances reduce power consumption.
There are some downsides to UTM appliances, with the single point of failure topping the list. If the overall device fails, all security features go down with the ship. A sudden loss of so many security functions would create a gaping hole in the organization’s security posture. In addition, appliance consolidation also leads to a potential over-consolidation of workloads and, subsequently, performance bottlenecks. A sudden sharp load increase on the firewall module could act as a bottleneck for other security functions.
NIDS/NIPS
Since host intrusion detection systems (HIDSs) and host intrusion prevention systems (HIPSs) are sufficiently covered in Chapter 6, this section focuses on network intrusion detection systems (NIDSs) and network intrusion prevention systems (NIPSs) only.
A common question asked is, which type of system should be used: an NIPS/NIDS or HIPS/HIDS? The answer depends on your environment, because each has its advantages and disadvantages. A host-based system is focused on what is happening to that particular host. As such, it will not notice what is going on in the network in general. On the other hand, a network-based system will have a “bird’s-eye view” of what is going on overall in the network, yet it will not see what is actually occurring within each of the individual hosts. So, for example, an intruder that attempts a single login using a known default user ID/password combination on a host before trying it on all other hosts in a network will probably not be noticed (because systems are often not tuned to alert on single occurrences of failed logins) by an HIPS/HIDS, but an NIPS/NIDS could notice this activity occurring on all systems throughout the network. An NIPS/NIDS, on the other hand, has some of the same issues that firewalls do in terms of their effectiveness in the face of encrypted traffic. Detection of specific attacks that require inspection of the contents of network packets will not be successful if the packets are encrypted, but an HIPS/HIDS would have a chance of detecting the attack at the host level.
An NIPS/NIDS identifies intrusion attempts by examining network traffic, potentially looking at both the header and contents of packets that are being transmitted. It can monitor both inbound and outbound traffic. The reason for monitoring inbound traffic is obvious, but outbound traffic monitoring may also provide clues that a system on the network has been penetrated because it may detect signs of activity such as unusual downloading of large or sensitive files.
A sample rule might follow the pattern of this example from Snort, a well-known IDS/IPS:
alert tcp any any -> any any (msg: "example howdy alert rule"; content:"howdy")
In this example, we tell the system to generate an alert if it sees any TCP packet coming from any source IP address or port going to any source IP address or port where the word “howdy” is found in the contents of the packet. The message we’d like it to alert us with if the word is found is “example howdy alert rule.”
Where to place an NIPS/NIDS is always an interesting question. Generally, the discussion comes down to whether to place it inside the organization’s firewall (on the inside of the network), outside of the organization’s firewall (on the outside of the network), or in both locations. Placing the device on the outside of the firewall will mean that it can see all traffic destined for the network and will be able to see any attempted intrusive activity. It may also mean an extremely high number of alerts. Placing it on the inside of the firewall means that a certain amount of traffic will not be seen because the firewall will filter it. This will cut down on the number of alerts generated, but it also means that a number of attempted attacks will be missed that could provide early indicators of unusual interest in your organization’s network. Putting one on both sides and tuning them for their specific location, so as to look for specific types of traffic, will allow you to see all attempts without being overloaded with too many alerts.
One of the best known and most common network intrusion detection/prevention systems is Snort. Snort is an open-source product that combines both signature- and anomaly-based inspection. Although the program is open source, the all-important real-time database of rules is not. The official rules for Snort are generated by the Sourcefire Vulnerability Research Team and distributed by subscription to their customers.
INE
Inline network encryptors (INEs) are devices that encrypt sensitive information en route between sources and destinations across insecure networks like the Internet and company WAN links. Although most network encryption is performed prior to delivery, INE appliances receive traffic and encrypt it on the fly. INEs are typically used to transmit highly classified government or military materials; therefore, they are typically certified by the National Security Agency (NSA) as being High Assurance Internet Protocol Encryptor (HAIPE) compliant.
The General Dynamics Mission Systems organization manufactures a popular line of INEs called Tactical Local Area Network Encryption (TACLANE) devices, which must be HAIPE complaint. Typical HAIPE devices use a stronger version of IPSec for confidentiality and integrity purposes, while also employing a self-destruct or zeroization of cryptographic keys should a threat be detected.
NAC
Once upon a time, all desktops were provided by the organization for internal use only. Laptops eventually stretched this by permitting remote access. In either case, the devices were still issued by the company, with configuration and security set up prior to employee usage. With today’s employees increasingly working from personal devices, including desktops, laptops, tablets, and smartphones, organizations are increasing their risk by depending on staff to configure and secure their devices themselves.
To provide assurances that users aren’t connecting insecure devices to the organizational network, organizations can implement what is called network access control (NAC). NAC improves network security by employing policies that mandate devices meet certain security minimums before being granted network access. This is similar to an elementary school requiring students to possess a fully updated immunization card prior to gaining admittance. The school is concerned about students bringing dangerous diseases in or taking diseases home with them.
Cisco and Microsoft have a lot of history with NAC. Microsoft’s NAC feature—which is known as Network Access Protection (NAP)—can implement health policies with requirements that VPN clients cannot connect to the corporate network unless they have suitable antimalware tools installed, enabled, and updated—in addition to Windows Update and Windows Firewall compliance. Whether users seek connectivity via VPN, IPSec, 802.1X, or DHCP, any devices noncompliant with the health policy are either denied connectivity or quarantined to a restricted network for remediation of security deficiencies.
Although NAC is great for stopping trouble at the door, it does little to stop trouble that has gotten past the door. Also, it doesn’t do anything for company data that has leaked outside the corporate boundary. NAC’s requirement of system hardening is an important step, but more network security controls are needed. The good news is, we have the rest of this chapter to cover topics that help fill in all the gaps left behind by NAC.
SIEM
Security information and event management (SIEM) utilities analyze and correlate logs and events from multiple sources as well as provide real-time alerting features, as shown in Figure 5-1. SIEM utilities can also aid in the collection of information for compliance purposes. Before deploying an SIEM, you should identify log sources of critical systems and services in the organization’s network. Critical systems commonly include but are not limited to the following:
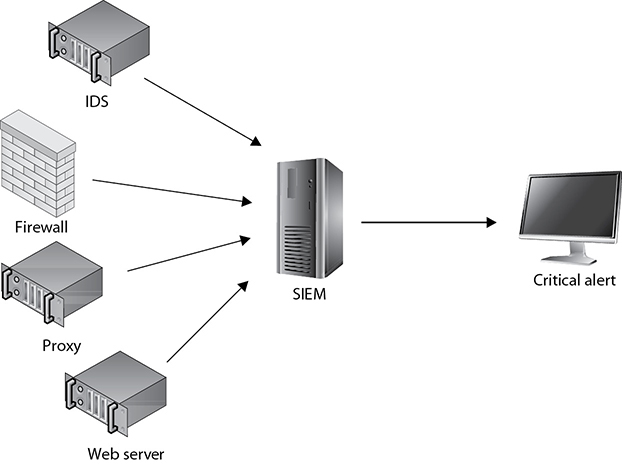
Figure 5-1 SIEM
• Databases
• File servers
• Domain controllers
• Internet and intranet web services
• Web applications
• Proxies and filters
• Intrusion detection systems
• Firewalls
• Routers
Consider all possible log sources, including application logs, operating system logs, antivirus logs, and malware detection logs. Be sure to configure the SIEM to look at successful and unsuccessful authentication attempts, detected attacks, detected viruses and malware, and general activity such as service requests. Also, consider the expected and actual network sources of connections and requests. Set the initial alert thresholds as something you would think unlikely to occur for non-malicious activity. After deployment, be sure to spend time tuning the SIEM to reduce the number of false positives and irrelevant alerts. Also, be sure to tune for performance and ensure an appropriate amount of resources is free to protect against denial-of-service attacks and to allow for growth. Remember that an SIEM utility producing too many alerts will likely result in valid alerts going unnoticed.
An additional security consideration often overlooked is the security of security utilities. Before purchasing an SIEM, review the security of the SIEM service itself. Are the service and data-collection agents communicating in a secure manner with reasonable protections from eavesdropping, modification, and injection? Be sure to frequently update the data-collection agents and SIEM service to protect against newly discovered vulnerabilities.
Switch
Switches are network appliances that connect devices such as workstations, servers, and printers together to form a network. They are an upgraded version of hubs in that they provide increased network performance, security features, flexibility, and management capabilities. Considering how malicious insiders frequently rely on switches to perform network-based attacks, securing the switch is important. Although advanced switch configurations will be detailed later in this chapter, here are some cursory definitions of popular switch security features:
• Virtual LANs (VLANs) VLANs provide multiple benefits, one of which is to secure networks by isolating hosts into separate logical groups. Devices not explicitly permitted access to the VLAN are implicitly blocked—including devices used by hackers. Should hackers gain access, the VLAN’s isolation from the rest of the network will significantly impair how much traffic is visible to a hacker’s unauthorized packet-sniffing tool.
• Port security Port security helps filter out unapproved devices by preapproving specific MAC addresses.
• Flood guards A switch feature that guards against MAC flooding or denial-of-service (DoS) attacks.
• Loop protection Detects and avoids switch loops by using the Spanning Tree Protocol (STP).
Firewall
Because host-based firewalls are covered in Chapter 6, this section focuses on network-based firewalls—also known as physical firewalls. Perhaps the most important network security device in the organization, a network firewall evaluates incoming and outgoing traffic to determine if the traffic should be allowed or denied entry across a network boundary. Like a security guard at a theme park screening all visitors, a firewall attempts to provide assurances that only authorized traffic is permitted to enter and leave a network. In general, firewalls are more concerned about the traffic coming into a network (ingress) than traffic leaving a network (egress). Firewalls can also maintain a log of permitted and denied network connections to help organizations determine if unauthorized travel is passing through.
There are many kinds of firewalls, and they can differ in terms of the following characteristics:
• Generalized or specialized purpose
• Depth of packet analysis encompassing a few or several OSI model layers
• Architecture (bastion host, dual-homed, multi-homed, or screened host)
• Location within the network infrastructure (internal or edge)
• Number of network interfaces
Next is a brief look at some of the more popular types of firewalls. These firewalls essentially vary in terms of security achieved via depth of packet inspection versus the subsequent loss of network performance from the overhead:
• Packet-filtering firewall Considered a basic firewall since it only evaluates the source/destination IP addresses and port numbers (OSI Layer 3 and a smidge of Layer 4) of traffic. Due to the minimal inspection overhead, this firewall is the fastest of the bunch. However, its failure to analyze deeper (OSI Layers 5, 6, and 7) into the packet makes it highly vulnerable to numerous spoofing, fragmenting, and other TCP-based exploits.
• Stateful firewall An improvement over packet-filtering firewalls, stateful firewalls consider the “state” or history of a connection (OSI Layer 4) as opposed to focusing only on individual packets. These firewalls maintain a connection-state table that stores details of a connection’s TCP 3-way handshake in order to help determine if subsequent traffic matches both a firewall rule and the connection state data in the table. Whereas a packet-filtering firewall’s rule wouldn’t catch a TCP-based attack, stateful firewalls can determine if attackers are injecting malicious TCP flag packets such as a packet beginning with a SYN/ACK as opposed to a SYN. Such TCP flag patterns may foreshadow packet spoofing and port scanning. The downside to stateful firewalls is that this overhead results in reduced network performance.
• Application-level firewall An improvement over stateful firewalls, application-level firewalls can understand the application and protocol data contained in the data portions of the traffic (OSI Layers 5, 6, and 7). Firewalls need to understand the application context of a packet in order to determine if an unapproved application is attempting to bypass the firewall by using an approved port number or IP address. The bad news is, this additional examination of the application portion of traffic will further reduce network performance.
• Next-generation firewall Next-generation firewalls (NGFWs) are designed to replace the “traditional firewalls,” which aren’t designed to examine the application/protocol data like stateful and packet-filtering firewalls. In addition to incorporating these application-level firewall capabilities, NGFWs may also add intrusion prevention, user/group-level access, plus the incorporation of intelligence from outside sources like the Internet. The downside is that they are more complex to manage; plus, their increased integration of features can create more single points of failure.
Wireless Controller
Enterprise environments may have several or even dozens of wireless access points (WAPs). Manually implementing security configurations on all WAPs can be time-consuming, error-prone, and lead to inconsistencies. Plus, additional security and networking features are needed in today’s modern environments. To address these concerns, enterprises are implementing wireless controllers that are network appliances or software solutions that enable administrators to centralize security configurations across multiple WAPs simultaneously. Although their features can vary, shown here are the features you may find on wireless controllers:
• Aggregate configurations across all access points
• Automated failover and mitigation of wireless interference
• Threat detection
• Content filtering
• Authentication based on user’s ID and location
Router
Routers are devices that connect networks to networks in order to forward traffic based on network addresses such as IP addresses. Unlike traditional switches, which make forwarding decisions based on the MAC addresses in packets (OSI Layer 2), routers utilize the IP protocol (OSI Layer 3), which supports internetworking and path determination. Since routers typically have more networking scope than switches, security exploits can be equally magnified.
Routers are configured with routing tables, which consist of network destinations and the possible routes the router will choose to efficiently deliver data to those destinations. Since dynamic routers (routers that automatically build their routing tables) broadcast routing table updates to other routers, they should be set up with authentication and encryption channels with other routers to ensure hackers cannot easily set up a rogue router, or intercept and understand the network details contained within the routers’ traffic. Another security option is to configure static routing tables (which are manually built by an administrator), since these routers don’t need to broadcast their routing tables to other routers. Hackers cannot intercept traffic that is never sent to begin with. To secure a router, it is also recommended to change the default usernames/passwords for logging in and managing the router’s configuration. Also, refrain from using Telnet to the extent possible since it doesn’t support cryptography—use SSH instead.
Proxy
Although there are different types of proxy servers, most are hardware or software systems that act as connection intermediaries between internal clients and Internet resources. Given the proxy server’s position as a “middleman,” it can cache requested files and websites to provide local content retrieval, conceal client IP addresses for anonymity, filter out malicious or irrelevant websites, and provide the organization with monitoring capabilities. Let’s look at an example of a client accessing the www.mheducation.com website using a proxy server:
1. The client’s web browser generates a request to visit the www.mheducation.com website.
2. The client’s request is delivered to a local proxy server.
3. The proxy server strips away the client’s source IP address and other identifying characteristics, and then forwards the traffic to www.mheducation.com on behalf of the client.
4. The www.mheducation.com website delivers its website to the proxy server.
5. The proxy server may cache the website and other requested files to its local hard drive.
6. The proxy server delivers the www.mheducation.com website to the client’s web browser.
7. Subsequent clients desiring the www.mheducation.com website are likely to receive a response from the proxy server’s cache as opposed to the original on the Internet. This will speed up responses.
Load Balancer
Load balancers are network devices or programs that distribute traffic across a group of similar servers, known as a server farm or pool, in order to increase server performance and availability. When users send a request to the load balancer, the load balancer will either forward the communication directly to the most practical server or reply to the user with a referral to the most appropriate server.
Despite the server pool being constructed of multiple physical machines, the pool gives the appearance of being just one server due to the load balancer’s clever use of algorithms. The algorithms are selected based on the needs of the organization. Here are a few popular algorithms:
• Round robin Traffic is distributed to the server pool members sequentially.
• Least connections Traffic is distributed to the server pool member with the least amount of connections.
• Source IP hash Traffic is distributed to the server pool member based on the client’s source IP address. Typically, the chosen server is located on, or close to, the client’s subnet.
HSM
Hardware security modules (HSMs) are devices that provide key generation and safeguarding services, speed up specific cryptographic operations on platforms requiring strong authentication, and provide access control capabilities. They run the gamut from thumbnail-sized USB devices, to internal expansion cards, to network appliances serving the network. Their powerful crytoprocessors can perform key generation for Certificate Authorities (CAs) and SSL/TLS-based connections, which helps speed up the cryptography process while also maintaining cryptographic key confidentiality, integrity, and nonrepudiation.
Another important function of HSMs is the prevention of unauthorized applications executing on the local host system or network. When such software is discovered, the HSM will deny the execution, lock down the system, send an alert, or passively log the activity. These are important benefits for large and highly secure environments such as government, military, financial, and other organizations.
On the flipside, the right HSM device can be very expensive. HSMs come in many forms and have differing benefits/drawbacks; therefore, security professionals must perform their due diligence before making a vendor/model selection.
MicroSD HSM
The smaller versions of their PCI/PCIe, USB, and network appliance counterparts, microSD HSMs are tiny HSM cards that plug into the microSD ports of smart devices such as Android smartphones and tablets. These cards incorporate secure hardware-based authentication and AES/RSA/SHA-2 cryptography capabilities right into your Android smart device—which is a huge boon for military and government workers in particular. Here are some common features found in microSD HSMs:
• Built-in public key infrastructure (PKI)
• Device PIN numbers
• Encrypted channels set up for local and remote devices
• Key and certificate generation
• Key backup and restoration
• Key restrictions and limits
Application and Protocol-Aware Technologies
Application and protocol-aware technologies are those that can identify specific applications that are connected to them in order to collect information about the connection state of those applications. Armed with this information, technologies such as web application firewalls, passive vulnerability scanners, and database monitors are able to tailor their security controls to the applications and protocols in use to improve their security. This section goes over these technologies.
WAF
Web application firewalls (WAFs) specialize in the monitoring and filtering of unauthorized and malicious traffic sent to and from web applications to provide them with protection against various Internet threats. Unlike traditional firewalls, WAF rules and policies are designed around HTTP/HTTPS traffic since web servers are targeted more than nearly all other IT systems. WAFs can help protect web applications from many kinds of attacks, including the following:
• Buffer overflow
• Cookie poisoning
• Cross-site scripting
• Directory traversal
• Hidden field manipulation
• SQL injection
Most WAFs are implemented inline with traffic having to pass through them to reach the web application. This empowers inline WAFs to stop traffic in real time, yet performance will be reduced and genuine traffic may occasionally be mistakenly blocked. Reversing the pros and cons are out-of-band WAFs. Although these do not block real-time traffic, they do not slow down traffic or interfere with it.
Firewall
Packet-filtering, stateful, application-level, and next-generation firewalls were covered in the “Physical and Virtual Network and Security Devices” section, earlier in this chapter.
Passive Vulnerability Scanner
Passive vulnerability scanners (PVSs) analyze network traffic in order to non-intrusively discover vulnerabilities with organizational assets. They can perform discovery operations on clients, servers, web applications, network appliances, virtual and cloud-based systems, and mobile devices, in addition to rooted or jailbroken devices. Once the PVS locks into scanning a particular asset, it’ll gather and point out relevant vulnerability information in order to help you mitigate the vulnerability. Examples of vulnerabilities include critical traffic not being encrypted, system port scans, and missing application and operating systems. The best thing about a PVS is its non-interfering nature; yet, it also suffers from not being able to resolve the issues it discovers. The onus is on you to review the discovered vulnerabilities and mitigate them using separate solutions.
DAM
Database access monitors (DAMs), also referred to as database activity monitors, independently monitor the transactions and other activity of database services. DAMs are an important part of a defense-in-depth strategy. Common uses of DAMs include monitoring applications and users for unauthorized or fraudulent activity. Accountability and compliance auditing can also be aided by DAMs.
Several different types of DAMs exist, each gathering data at different levels. Data may be gathered on the network, by libraries, by the operating system, or directly from memory. Sniffing database traffic at the network level provides better isolation but requires the database connections to be unencrypted, which should be avoided if possible. DAMs that gather information directly from memory are a good choice because they require no changes to the current network and are able to intercept any means of access to the database service. If the blocking and prevention of suspected attacks is available, the cost and risk of a successful attack must be weighed against the cost and risk of blocking a legitimate request.
Advanced Network Design (Wired/Wireless)
Security is a process—you can’t “buy” absolute security, as much as many of us would like to. It simply does not exist. Security is also a constantly moving target. As your business needs change and technologies change, so must your approach to security and the steps you take to secure your infrastructure. Security is often at odds with the needs of the business since businesses always want to do “more” and security is largely about finding ways to make you cope with “less.” Employees want access to data any time, from any place, and using any platform they are able to get their hands on at the time.
So how does one go about securing an organization facing this type of challenge? A good place to start thinking about and planning for security is in the design and implementation of your network infrastructure. A good network design can absolutely help in your quest to secure and defend your network and critical resources. Given the amount of remote access, and the variety of client devices within and outside the organization, many network design elements centralize around remote access. We’ll cover several remote access topics, all of which equally apply to wired and wireless networks.
Remote Access
In the modern work environment, the concept of a static workspace with a phone, network jack, and desk is essentially dead. Many organizations are embracing the idea of a truly mobile workforce that can work anytime from anywhere. All they need are their laptops, tablets, smartphones, and network connectivity. It’s a great model for efficiency and productivity, but it’s not a great one for security. Each of those mobile employees must be able to reach back into the organization for e-mail and access to data/resources. Some of those employees are connecting from home, whereas others are connecting from hotels, coffee shops, airport lounges, and so on. The question security practitioners need to ask is, How to allow employees to connect from any place, with multiple platforms, and still maintain some semblance of security? Fortunately, there are steps you can take to design and implement a more secure remote access solution.
Segmenting remote access traffic is an important step in the design of your infrastructure. Many organizations treat remote access traffic as potentially hostile and do not allow remote access traffic to come directly into the internal network. One approach is to accept remote connections at the VPN/access gateway, decrypt the traffic there, and then pass the traffic through a firewall and IDS/IPS configuration, as shown in Figure 5-2. This allows for the filtering of remote access traffic (do remote users really need access to port 1433 or 3306?) as well as monitoring of the traffic for suspicious or malicious activity. Although, in theory, anyone making a successful connection to your VPN infrastructure is “legit,” there’s nothing wrong with keeping an eye on their activity, particularly if you’re looking to protect yourself against infected or compromised hosts. Segmentation also gives you a control point to restrict or reject all remote connections if necessary.

Figure 5-2 Segmentation of remote access traffic
Another common security practice is to verify the patch and antivirus (AV) status of any host that connects to the VPN network. For example, Microsoft’s Network Access Protection product can help control a client computer’s access to organizational resources based on whether or not that client meets the defined corporate policy. Is the client fully patched? Is it running an approved AV product? Is that AV product up to date with the latest signatures? If a connecting client is not in compliance, you can bring that client into compliance before allowing it to connect. Remote clients may not be routinely scanned and updated and should be checked before being allowed to connect to any internal resources.
Another topic that should be examined in your design is the use of token-based or multifactor authentication. Although by no means perfect, token-based or multifactor authentication systems can add one more layer of complexity to deter and thwart potential attackers. Some organizations shy away from these solutions due to the extra cost and complexity associated with tokens, biometrics, and so on. Your design must take all these factors into account and weigh the risk against the cost to see if deploying something beyond the traditional user ID/password in your remote access solutions is right for your organization.
VPN
A virtual private network (VPN) offers security by tunneling data across a network through the use of technology that offers a secure means of transport. Although VPN connections typically occur over the Internet, they are sometimes used internally as well due to their cryptography benefits. A wide range of VPN technologies have been developed and employed, each with advantages and disadvantages. VPNs can be implemented using hardware, software, or a combination of both. Table 5-1 describes some common VPN technologies.

Table 5-1 Common VPN Technologies
VPN connections typically involve remote users connecting over the Internet to a corporate network in what is known as remote access VPNs. Organizations also implement site-to-site VPNs to connect sites together over the Internet to cut costs on expensive T1 or T3 links from a telecommunications provider.
IPSec
Internet Protocol Security (IPSec) is a suite of protocols for securing packets that traverse an IP network. IPSec is a set of extensions to IPv4, and is native to IPv6, designed to provide both authentication headers and encapsulating security payloads to offer a variety of protections to packets. IPSec can be used to encrypt just the data portion of the traffic (transport mode) or the entire transmission (tunnel mode). Use transport on internal networks and tunnel mode for any traffic leaving an internal network or any traffic leaving a network you consider to be secure. Shown here are some protocols common to IPSec:
• Internet Key Exchange (IKE) A protocol used when setting up IPSec to document the required security association between the parties.
• Encapsulated Security Payload (ESP) A protocol from the IPSec suite that provides confidentiality, connectionless integrity, data origin authentication, and protection from replay attacks.
• Authentication Header (AH) A protocol from the IPSec suite that provides connectionless integrity, data origin authentication, and protection from replay attacks but does not provide confidentiality.
SSL/TLS
Detailed coverage of Secure Sockets Layer/Transport Layer Security (SSL/TLS) is provided in Chapter 15, so only a brief summary is provided here. SSL is a protocol for securing communication sessions over IP networks, whereas TLS is its more powerful and relevant successor. Both commonly utilize asymmetric, symmetric, key exchange, hashing, and digital signature features to provide authenticity of servers, integrity, and confidentiality of data. SSL creates secure connections between web browsers and web servers over an otherwise insecure network. HTTPS is the outcome of using SSL to encrypt HTTP communications. HTTP uses TCP port 80, and HTTPS uses TCP port 443. As noted earlier, some Windows-based networks may rely on an SSL/TLS variant of a tunneling protocol called SSTP.
SSH
Secure Shell (SSH) is a protocol for obtaining a remote shell session with an operating system over a secured channel, using TCP port 22. Unlike Telnet on port 23, which doesn’t encrypt the authentication or data flow, SSH implements a set of cryptographic ciphers similar to SSL/TLS to secure the connection. It is commonly used on command-line interface (CLI) connections to routers, switches, firewalls, and Linux and Unix servers, given their CLI capabilities. The current version is SSHv2, which modernizes its ciphers with enhanced key sharing and integrity checks via message authentication codes. Although it’s not commonly used for VPN, the OpenSSH protocol has built-in support for VPN connections.
More coverage on SSH is provided in Chapter 15.
RDP
Created by Microsoft in the late 1990s for its Windows operating systems, Remote Desktop Protocol (RDP) provides a secure, graphical, remote access connection over a network between computers via port 3389. Once the user connects to the destination computer, the user experience transforms from one being attached to the local computer to one sitting directly in front of the remote system with access to that system’s screen, mouse, keyboard, operating system, and programs. It is similar to SSH/Telnet, but the connection is graphical, not CLI based. The following is a list of RDP security features:
• Originally used RC4 encryption but can also support SSL/TLS and AES connections.
• Network-level authentication (NLA) requires RDP clients to be authenticated in advance of an RDP session. This is common for Active Directory–based Windows domain environments.
• Limits users who can log in using RDP.
• Uses RDP gateways to restrict access.
• Implements multifactor authentication.
• Implements logging of connections.
• Configures session period and idle period limitations on connected sessions.
VNC
Unlike RDP, Virtual Network Computing (VNC) is a platform-independent, graphical desktop-sharing protocol that uses the Remote Frame Buffer (RFB) protocol. Given VNC’s vendor neutrality, many technical support departments rely on it to support their Windows and macOS users. VNC relies on a client/server architecture in that the VNC server hosts the desktop sharing, and the VNC client connects to the desktop-sharing host.
Perhaps due to its broad compatibility benefits, VNC is not secure by default. It is subject to encryption key and password eavesdropping attacks; plus, older versions of VNC capped password lengths at eight characters. Consider implementing UltraVNC, which supports cryptographic plug-ins to improve the encryption strength of a VNC connection. You may also consider tunneling VNC traffic over existing VPNs, DirectAccess, or SSH connections for extra cryptographic strength.
VDI
Virtual Desktop Infrastructure (VDI) involves the hosting of a desktop OS within a virtual environment on a centralized server. VDI allows the migration of a user’s entire desktop, including operating system, applications, data, settings, and preferences, into a virtual machine. VDI is an improvement over other client/server models due to its strong platform independence.
Reverse Proxy
Unlike proxy servers, which act as an intermediary between internal machine connections to outside resources such as the Internet, reverse proxy servers flip the script by securely providing Internet users with access to servers behind an enterprise firewall. Single sign-on (SSO) capabilities are often paired up with this server to provide intuitive and secure access for remote workers using business and personal devices alike.
IPv4 and IPv6 Transitional Technologies
IPv6 is the intended replacement for the commonly used Internet protocol IPv4. IPv6 brings many improvements, but most prominently a much larger address space of 128 bits (compared to 32 bits in IPv4). Important but less publicized additions to IPv6 include the required support of optional security features such as IPSec. IPSec can provide authentication, integrity, confidentially, and protection against replay attacks.
Although IPv6 was standardized in 1998, its multi-decade adoption has only increased in recent years due to the advent of mobile devices and IoT consuming most of the remaining IPv4 addresses. Other factors slowed its adoption, including Network Address Translation (NAT), which has delayed the need for the additional address space provided by IPv6. Because of this, many networks, especially home networks, use NAT routing, which is not supported by IPv6 (which further hinders the adoption of IPv6).
Despite adoption issues, IPv6 is here to stay, and security practitioners need to know how to secure IPv6 networks and how to take advantage of the security benefits inherent in IPv6. The IPv6 header is illustrated in Figure 5-3, showing the required elements and their placement in a packet header.

Figure 5-3 IPv6 packet header
IPv6 brings security benefits other than IPSec. Packet fragmentation is only performed by hosts, partially removing a source of common vulnerabilities used to exploit TCP/IP stacks and bypass firewalls. Better support for quality of service (QoS) is built into IPv6, thus improving availability. The larger address range and required use of Classless Inter-Domain Routing (CIDR) notation enables better planning and deployment through the easier allocation of addresses and configuration of routes. Although NAT does have some security advantages, the removal of NAT can lead to much-needed improvements in security. NAT generally gives a false sense of security and can be a barrier to the integration of other security measures such as IPSec in transport mode.
Before deploying IPv6 on any network, you must give some additional security considerations careful thought. Some older security devices and tools such as firewalls, IDSs, log analyzers, and flow analyzers may not support IPv6, thus enabling attackers to circumvent these security mechanisms. Furthermore, even devices supporting IPv6 may not be able (or configured correctly) to analyze the IPv6 encapsulation of IPv4 packets. Encapsulation of packets is used to maintain backward compatibility for older IPv4 hardware and software. Networks employing NAT should have security policies thoroughly reviewed and updated due to the removal of NAT. Remember to update security devices such as firewalls, IDSs, and analysis tools to account for the additional addresses.
Although the ultimate transition to IPv6 won’t take place until we no longer need IPv4, we will be using IPv6 transitional technologies (tunneling) for the foreseeable future, which allow for the friendly coexistence of IPv4 and IPv6 in the same organization. Here are the most common IPv6 transitional technologies:
• 6to4 tunneling Permits tunneling of IPv6 traffic over the IPv4 Internet, assuming there’s no NAT device
• Teredo tunneling Permits tunneling of IPv6 traffic over the IPv4 Internet and is NAT friendly
• ISATAP tunneling Permits IPv6 traffic within an IPv4 intranet
• Dual stack Permits IPv4 and IPv6 to run simultaneously on the same software and devices
• GRE tunneling Permits tunneling of IPv6 traffic over IPv4 networks via the generic Routing Encapsulation Protocol
Network Authentication Methods
Whereas Chapter 14 will dive deeper into more advanced authentication concepts, this section focuses specifically on network authentication methods. Authentication of users and computers on the network is crucial to assuring only authorized users and devices connect to the organization’s network. As can be expected, there are many network authentication methods to choose from. This section outlines several authentication protocols:
• Password Authentication Protocol (PAP) Used with older dial-up or VPN connections, PAP is considered a weak protocol due to it sending passwords over the network in cleartext. It should be avoided unless the endpoints cannot agree on a stronger method.
• Challenge Handshake Authentication Protocol (CHAP) Typically implemented on non-Microsoft devices, CHAP uses a 3-way handshake for authentication. Once the client and the server connect, the server sends a challenge message to the client. The client combines its password with that challenge message and sends a hash value back to the server. The server compares the client’s hash to the information it has in the database and determines if there’s a match. CHAP should be used over PAP wherever possible. However, it is a legacy protocol, so stronger authentication protocols should be favored over it, if possible.
• Microsoft Challenge Authentication Protocol (MS-CHAP) Microsoft’s first proprietary implementation of CHAP provides better password storage than CHAP but is otherwise considered weak by today’s standards.
• Microsoft Challenge Authentication Protocol version 2 (MS-CHAPv2) This upgrade to MS-CHAPv1 provides mutual authentication between endpoints to prevent rogue server attacks and other nonrepudiation and integrity violations. It also uses different keys for sending and receiving.
• Extensible Authentication Protocol (EAP) Commonly implemented on VPN and wireless networks, this protocol is a framework for plugging in more powerful hardware and software authentication methods, ranging from smart cards and fingerprint readers to PKIs and certificates. In general, EAP methods provide the strongest level of network authentication. There are multiple variants, including but not limited to the following.
• Protected Extensible Authentication Protocol (PEAP) Although EAP supports strong authentication plug-ins such as MS-CHAPv2 and token devices, EAP by itself isn’t strong. In ice cream terms, EAP is the cone and a smart card is the ice cream. The ice cream makes up for the cone’s lack of flavor but certain scenarios call for both the ice cream and the cone to have “flavor.” EAP’s innate insecurities can be mitigated by encapsulating the EAP process inside of a TLS tunnel. The outcome of this is called Protected Extensible Authentication Protocol (PEAP). This protects the authentication process from man-in-the-middle exploits.
• Lightweight Extensible Authentication Protocol (LEAP) This is a Cisco proprietary EAP implementation aimed squarely at wireless networks. It was designed to use Wired Equivalent Privacy (WEP) for security and therefore should be discarded in favor of stronger methods like EAP-PEAP.
802.1x
The 802.1x standard is a port-based network access control method that requires users to authenticate prior to connecting to a wired or wireless network. Originally designed for dial-up networks, it has since grown to support wireless, VPN, and Ethernet switch authentication scenarios. One of the challenges is today’s networks often have too many devices to manage an organization’s authentication, access control, and auditing requirements. To mitigate this, these network devices defer these responsibilities to a central authentication point such as Remote Dial-in User Service (RADIUS) or Terminal Access Controller Access-Control System Plus (TACACS+) servers for processing. These are also known as authentication, authorization, and accounting (AAA) servers since they focus on these three key areas.
802.1x authentication is made up of three components:
• Supplicant The wired or wireless device attempting a network connection (for example, a VPN client).
• Authenticator The Ethernet switch or wireless access point that initially receives the supplicant’s connection attempt, which then gets redirected to an authentication server (for example, a VPN server).
• Authentication server The RADIUS or TACACS+ centralized authentication point that receives the authentication attempt from the authenticator and processes any AAA policies.
RADIUS is somewhat outdated by today’s standards, given its usage of UDP, meager password encryption, and reduced protocol support. Cisco’s TACACS+ uses TCP and supports better password and data encryption; plus, it supports more protocols.
Mesh Networks
Mesh networks involve all devices being directly connected to all other network devices in order to increase path redundancy and, thus, availability of the network. Most meshes are implemented on wireless networks and redundant switch and router topologies. Since mesh networks don’t require a centralized device to control all interconnectivity, they are highly tolerant of failures.
Placement of Hardware, Applications, and Fixed/Mobile Devices
Security practitioners all agree that security devices are needed to defend a network from the nearly constant onslaught of hostile Internet-based traffic. Where practitioners differ in their opinions is where security devices should be placed, and in some cases, how many of those devices should be deployed. When examining the design of your network, and considering the placement of security devices, you must think about many different factors:
• What are you protecting?
• What type of traffic are you filtering?
• How much traffic will be encrypted?
• What volume of traffic can you expect?
Placement of security devices must take several factors into consideration, such as the purpose of the device, its own survivability, and at what point you want this device to interact with the network traffic. Generally speaking, security devices can be placed either at the network border or internally, both of which provide important security benefits. Using security devices both internally and at the border is an important part of a defense-in-depth strategy. Consider the simple network in Figure 5-4, which shows four different locations where you could consider placing a security device such as an IDS/IPS or firewall. Each location greatly affects what traffic can be seen by security devices, what traffic they can filter/control, and so on.
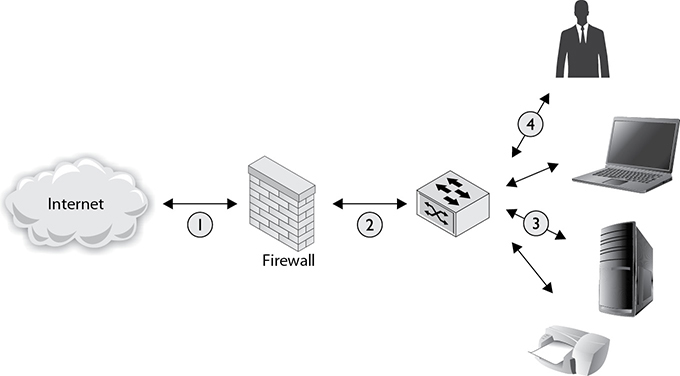
Figure 5-4 Possible locations for security devices
Security devices placed at the network border serve to keep malicious traffic out and to prevent sensitive information from leaving the network. Your first line of defense at the network border should be a firewall. Better security can be achieved by using two firewalls—an outward-facing stateless firewall with a separate stateful firewall immediately behind it. Place intrusion prevention (or detection) systems immediately behind your firewall, where they can see all of the traffic entering or leaving your network. This arrangement also keeps intrusion prevention systems from generating alerts and wasting resources on traffic blocked by the firewall.
Internal networks can be divided into multiple tiers, as described later, and even the most basic networks should be divided into a publicly accessible portion, usually called the DMZ, and a non-publicly accessible internal network. Separate and protect the divisions between network tiers with stateful firewalls and inline IPSs. IDS or IPS devices should also be placed along internal network paths that may be carrying sensitive information such as internal directory services, network storage, or Supervisory Control and Data Acquisition (SCADA) communications.
Place devices monitoring network traffic, such as IDSs, on network taps rather than SPAN ports. If security devices are placed on SPAN ports, ensure that the total bandwidth of these ports will not be exceeded at any time under normal circumstances and ensure that your device can handle mirroring all the traffic you want without overloading the switch and dropping packets. Remember to regularly check for updated software and firmware for all devices in the network, especially security devices. Almost all security devices, such as IDSs and IPSs, also require regular updates to their signature databases.
Complex Network Security Solutions for Data Flow
Monitoring data flowing through networks is an important security objective for many organizations. Sensitive information such as customer data, intellectual property, and classified information are of critical importance. Monitoring data flows allows organizations to detect sensitive information leaving the network. Analysis of network traffic also helps in efforts to detect other threats such as malware and botnets. This section covers various data flow topics, including DLP, deep packet inspection, data flow enforcement, network flow (S/flow), and data flow diagrams.
DLP
As the name implies, the goal of data loss prevention (DLP) is to monitor, detect, and prevent loss of sensitive data. DLP is managed through policies that identify specific sensitive data types as well as the “allow,” “prompt,” “block,” “encrypt,” “reroute,” and “quarantine” actions to take on data whenever potentially risky behaviors have been detected. These behaviors include e-mailing, printing, or copying a file. This guards against malicious attacks and accidents as well. Here are common data types to be identified by a DLP policy:
• Financial
• Credit card numbers
• Debit card numbers
• Account information
• Bank account numbers
• Bank routing numbers
• Medical
• PII identifiers
• Medical terms
• Privacy
• Driver’s license numbers
• National identification numbers
• Passport numbers
• Social security numbers
• Tax identification numbers
Deep Packet Inspection
First-generation firewalls examine packet headers for source and destination addressing, but they don’t consider the state of the traffic. Second-generation firewalls examine addressing and the traffic state, but they disregard the data payload. Third-generation firewalls such as application-level and next-generation firewalls perform deep packet inspection (DPI). DPI occurs when application-level and next-generation firewalls scan and analyze the header, state, and data portions of packets before allowing or dropping them. The data payload contains crucial application information needed by firewalls to make the most informed decisions about whether or not packets are malicious or unauthorized in nature.
DPI can make decisions not only on individual packets but also larger data flows since the flow is often more telling than the individual packets.
Data Flow Enforcement
Data flow enforcement refers to the secured and controlled flow of data within a device, between devices within a network, and across other networks. Organizations establish flow control policies for identifying data containing specific security attributes such as Confidential, and the destinations to which that data is authorized to flow (for example, destinations with a security attribute matching the data’s label of Confidential).
In addition to the policies, organizations also implement mechanisms to enforce said policies (for example, firewalls, routers, and encrypted tunnels). These policies are enforced via rule sets and configuration settings that govern the actions the network must take upon discovery of data types that are compliant or noncompliant with data flow policies. These enforcement mechanisms may also filter packets and communications messages based on predefined criteria.
Taken together, flow control policies and enforcement mechanisms make data flow enforcement pretty straightforward within a system or network; however, difficulties can arise when data must flow between networks—or what they call “cross-domain” data flow. This is because if the source and destination networks have incompatible security policies, security violations may result—or worse, data leakage and other data breaches may occur.
The requirements of data flow enforcement are rather detailed, but here are some general decisions that need to be made:
• Which data types are authorized to flow in a unidirectional or bidirectional manner?
• Which data types are not authorized to flow within a system, between systems, and between networks, yet are accessible in their current location?
• Which data types, and circumstances, warrant the reassignment of different security attributes to the data?
According to NIST Special Publication 800-53 (Rev. 4), “Security Controls and Assessment Procedures for Federal Information Systems and Organizations,” restrictions on data flow are required for the following scenarios:
• Ensuring traffic sent to and from the Internet is encrypted
• Blocking outside traffic that claims to originate from the internal network
• Restricting web requests to the Internet that are not from the internal web proxy
• Limiting data transfers between organizations based on data structures and content
Network Flow
Enforcing data flow policies is important, yet it is also important for us to be able to capture, analyze, and understand the data flows. A network flow is a sequence of packets transferred from a sending host to one or more receiving hosts. We use network flow monitoring tools to observe the traffic that is flowing across a network. These tools can help us in several ways, including the following:
• Creating performance baselines and determine deviations from baselines
• Identifying network connectivity and performance issues
• Identifying security issues
• Ensuring quality of service (QoS)
• Identifying historical traffic trends
Focusing on the security aspects, we can use network flow data to help us identify security issues such as abnormal traffic spikes caused by denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks. Malware may also be discovered via the network flows it generates, the port numbers used, and the Internet-based servers the malware communicates with. Another important aspect of a network monitoring tool is threshold-based alerts, which are generated based on preconfigured volume levels for “top senders,” “top receivers,” “failed connections,” and so forth. Finally, the network monitoring tool should include an intuitive and comprehensive reporting engine to help us understand the historical and current traffic we’re collecting.
sFlow
Any discussion on network data flow would be remiss without including one of its biggest advocates, called Sampled Flow or, more commonly, sFlow. According to RFC 3176, sFlow is a “method for monitoring traffic in switched and routed networks.” sFlow is a global standard for packet sampling technologies and is currently in version 5. It is supported by numerous hardware and software vendors, including Cisco, HP, Juniper, Arista, Extreme Networks, and a ton of others. Often built into routers and switches, sFlow empowers organizations to gain detailed insights into network data flow usage, routes, traffic and application mixes, in addition to trend analysis and capacity planning. It uses port number 6343.
Data Flow Diagram
The last section discussed how network monitoring can help us to better understand our network data from a measurement perspective. However, as they say, a picture is worth a thousand words. Wouldn’t we understand our network flows even better if we built a diagram visually depicting the data flow paths and processes? Data flow diagrams graphically represent the data flow that occurs between computer systems on a network. Figure 5-5 shows an example of a basic data flow diagram. Data flow diagrams help us understand the following data flow functions:
Figure 5-5 Data flow diagram
• What data types are sent by a system
• What data types are received by a system
• How data flows to and from the sending and receiving systems
• Where data is stored
• Which systems depend on other systems
Although this is just a basic data flow diagram, you are encouraged to create multiple versions based on the level of detail required. Initially, you’ll want to create a basic diagram to give you the broad strokes of a system and then branch out from there as required.
Secure Configuration and Baselining of Networking and Security Components
We’ve discussed all kinds of security and network devices, advanced network design, and security solutions for data flow. The next section covers some general network baselining and configuration lockdown topics. These topics are covered throughout the book, so only a cursory overview is provided here, with more information piecemealed throughout the book.
Network Baselining
Before we get started with configuration lockdowns, a great time to start measuring and determining network baselines is right after you build the network. At that point, the technology is in its purest condition. Baselining allows us to document what the normal and acceptable levels of performance are and use this performance level as the measuring stick to determine if subsequent measurements (benchmarks) are better, worse, or equal to the most recent baseline. Since networks are always changing, additional benchmark tests need to be done to see if our performance needs to be returned to the baseline levels, or if a new baseline will need to be created.
Configuration Lockdown
We capture network baselines before implementing configuration lockdowns because network baselines are so important that we don’t want anything messing them up. We want to prevent the very configurations that helped shape the baselines from being changed. Configuration lockdown effectively “seals” the configurations into our network devices to prevent unauthorized changes. The lockdown is strict enough that even network and systems administrators are restricted. Because if changes can be made, then baselines are much more likely to suffer integrity violations.
Change Monitoring
Even though configuration lockdown does a great job of preventing unauthorized changes to our network devices, the operative word here is “our” devices. Configuration lockdown won’t stop attackers from connecting unapproved laptops into open switch ports or setting up rogue wireless access points. Change monitoring will help us deal with both outcomes. Change monitoring checks for signs of failed or successful attempts at modifying our network’s configuration baselines as well as any signs of unauthorized devices or behaviors being introduced into the network. The change monitoring system might block the unauthorized changes and send an alert, or simply generate the alert for us so we can mitigate the incident ourselves.
Availability Controls
The confidentiality, integrity, and availability (CIA) triad teaches us that it’s great to keep secrets, and to be able to trust their veracity, but it won’t do us any good if the secrets aren’t there when we need them. That is why availability represents a whole one-third of the triad. Despite the myriad of topics in this section, we’re really talking about one thing still—baselines. We’ve created a baseline and then implemented lockdown configurations and change monitoring on the baseline. The baselines would also benefit from availability controls to ensure data is accessible and resistant to failure.
Implementing availability controls can be expensive, but failed networks due to lack of availability controls are more expensive. Let’s discuss some availability options:
• Redundant hard drives Hard drive redundancy is achieved with RAID arrays. RAID 1 disk mirroring or RAID 1 disk duplexing can survive a single hard drive failure without data or performance loss, but disk duplexing can survive a controller card loss as well since it relies on two of them. RAID 5 can survive a single drive failure put performs slower after failure. RAID 6 can survive two simultaneous drive failures but will perform slower during failure. RAID 10 (technically RAID 1+0) can survive more than one drive failure and will continue to perform well during the failure.
• Redundant NICs Sometimes found in workstations but often found in servers, redundant NICs are like the NIC equivalent of RAID in that you have multiple NICs for performance and fault tolerance reasons. Frequently, this is known as NIC teaming. You might have one primary NIC in use, with other NICs either on standby until the primary NIC fails (Active/Passive), or the primary and secondary NICs work simultaneously for performance reasons (Active/Active), and a third NIC remains on standby until another one fails.
• Redundant power supplies These are often found in servers. If one power supply fails, the other one takes over without disruption of data or services.
• Redundant servers with a load balancer Often called a server farm, server pool, or a server cluster, using multiple servers allows performance improvements in addition to higher availability should a server fail. Load balancers can help direct traffic to available servers should a preferred server become unavailable.
• Redundant ISPs Having redundant ISPs is more important now than ever, considering the amount of public, community, and hybrid cloud computing solutions organizations are utilizing online. If an ISP connection fails, all cloud computing services are unavailable to us unless we have a second ISP to failover to.
• Redundant data centers Although some organizations have redundant data centers, we generally experience them through cloud computing providers. Cloud computing providers carefully set up data centers in regions where a single catastrophic event, such as a tsunami, earthquake, tornado, hurricane, or volcano, will only affect one data center (and not other ones).
• Generators Generators can supply power to organizations for several hours or even days should they lose power. This is especially critical for healthcare providers like hospitals, where patients’ lives are at stake during power failures.
• UPSs Uninterruptible power supplies (UPSs) are commonly connected to servers, routers, switches, and firewalls to ensure they can function for a little while during a power failure or, more likely, provide users with the opportunity to gracefully shut down these units and ride out the storm.
Network ACLs
Access control lists (ACLs) can be defined in different contexts. There’s the file system variety, networking ACLs, and even SQL implementations for that matter. For the sake of this section, we’ll define network ACLs. ACLs are lists of rules that we apply to routers, firewalls, and so on, in order to, for example, define what packets are permitted or denied entry through a network interface. The ACL filtering actions are known for taking IP addresses and port numbers into consideration. The goal is to ensure that unauthorized traffic is not permitted to flow, which, ultimately, will help protect the network from bad guys. Here are some best practices for ACLs:
• Ensure ACLs are listed in the appropriate order—from most specific to least specific—so that rules that should “win” are more likely to win should conflicts arise.
• Ensure the implicit deny rule is at the bottom of the ACL. If no other rules exist to allow a connection, the connection will be implicitly denied due to this rule.
• Test ACLs on a test network before implementing them on a production network.
• Ensure ACLs fulfill the objectives of both the security policy and the organization’s business objectives.
Here is a sample Cisco router ACL configuration. Since Telnet is generally frowned upon in favor of SSH, we’ll often need to create an ACL restriction for Telnet.
access-list 105 deny tcp any any eq 23
access-list 105 permit ip any any
The first line configures the ACL to restrict Telnet. The second line configures the ACL to permit all other IP traffic.
Software-Defined Networking
Traditional management of network devices is typically performed by the network devices themselves (in other words, in a decentralized manner). There’s no central network governance. Since networks are constantly changing, network devices such as routers respond by not only making changes to themselves but also broadcasting these changes (such as routing table updates) to other routes in order to help them update their respective routing tables. Such updating can take a while; plus, some network devices are configured statically, so they will not dynamically update other devices at all.
Software-defined networking (SDN) addresses these concerns, in addition to others, by centralizing the configuration and control of devices. A centralized SDN application or server can push out network changes to the network devices due to changing network conditions, or proactively notify the network devices that a change is about to occur. Think of SDN as decoupling the control element of the router from the forwarding element. The control element refers to the router’s responsibility over its internal routing table and protocol operations—such as routing table updates, topology discovery processes, and so on. On the other hand, the forwarding element is the more elementary aspect of the router that simply forwards traffic based on the information in the routing table. The forwarding plane doesn’t make decisions; it just reads the script. SDN is taking over the control plane aspect so that the router is only responsible for the forwarding element. Routers still route, but they are no longer in charge of the rules that define their routing.
This has tremendous applications in the real world. Cloud computing providers thrive on SDN since the centralization of network device management will enable automation of network management and configuration changes, in addition to monitoring. SDN also enables the mixing of platforms so that Cisco, Juniper, and Extreme Networks products can all be configured with similar policies. This will improve operational efficiencies, which in turn reduces overall costs, addresses vendor lock-in challenges, cuts costs on hardware, and creates more consistent security configurations on disparate networking devices.
Network Management and Monitoring Tools
It is imperative that CASP+ professionals are diligent about security as it relates to network management and monitoring. Granted, IT professionals will handle the nuts and bolts of network management and monitoring, but they might be a little rough around the edges when it comes to the security context of network management and monitoring. That’s where we come in. Throughout this chapter, we’ve talked about a handful of management and monitoring tools such as SIEM, IDS, IPS, wireless controllers, UTMs, and so on. We will list out a few others here to round off the discussion. Each of these topics will be revisited in more detail in later chapters:
• Auditing Auditing is the practicing of determining who to hold accountable for recorded actions. For example, who logged in? What time did they log in? What resources did they access? What actions did they perform on those resources? What computer did they use to perform these actions? Having access to and understanding this information will allow us to determine who to hold responsible for both good behaviors and bad. Auditing is often performed in response to an organization’s security policy—which was created in response to a state or federal law. It is critical that organizations know what to audit and to what level of detail the auditing should be performed.
• Logging Logging is the practice of recording activities into a file for troubleshooting, tracking, and evidence collection purposes. All kinds of products maintain logs—from operating systems, to applications, to network devices such as routers, switches, and even firewalls. For troubleshooting purposes, auditing, and even data retention reasons, logs should be generated, maintained, and retained since it is likely that data retention laws will apply to your organization. Failing to produce logs during an audit can earn the organization a handsome fine or worse.
• Sniffers Like auditing and logging, sniffing is a monitoring technique, only it is focused on capturing and analyzing network traffic as opposed to collecting information that is generated internally on the computer or device. Packet sniffers such as Wireshark are an excellent resource for surveillance purposes, network troubleshooting, or identifying possible malicious packets or attackers on the network.
Alerting
Most if not all modern network devices are capable of generating and sending alerts to administrators. These alerts may range from a firewall detecting a port scan, to an IPS detecting a SYN flood attack, to a router sending an alert that another router is down. Regardless of the specific alert types, alerting basically boils down to two varieties—alerting at the individual device level and at the overall network level. Although device issues are important, it’s more important to be made aware of issues affecting the overall network. For example, bandwidth utilization is at 100 percent with a suspected cause of a DDoS attack.
Alerting is important enough that devices have built-in default alert types and actions; however, these are not likely to be adequate. You will have to write some rules of your own in order to be notified of activities important to you and your business. To that end, standing atop the alerting “Mount Rushmore” is Cisco’s Snort tool. The Snort software is a hugely popular, free, open source IDS/IPS product. Snort rules follow a particular outline:
• Action What is the alert going to do? Usually the action is “Alert.”
• Protocol The protocol that was captured by Snort. TCP is common.
• Source IP The sending device’s IP address.
• Source Port The sending device’s source port number.
• Destination IP The receiving device’s IP address
• Destination Port The receiving device’s port number.
• Rule Options For example, send a message indicating what the rule has detected.
Here’s an example of a Snort rule:
alert tcp any any -> 192.168.1.100 22
This rule tells Snort to generate an alert whenever any device attempts to connect to 192.168.1.100 on port 22 (which is used by SSH services).
It’s one thing to receive alerts because a packet with a certain source/destination IP and port number matched a Snort rule, but does that mean that alert should be generated every time there’s a match? The frequency of an action that caused the alert is just as important as what the behavior was itself. In other words, a single ICMP ping packet may not be worthy of triggering a Snort alert, but if there’s, let’s say, hundreds or thousands of ICMP ping packets in a short period of time, an alert should be generated because this could indicate a DDoS attack. The trick is to find that balance between alerts that help us and alerts that we collectively drown in. We’ll talk more about this topic in the next section.
Alert Fatigue
As children, we heard the story about the boy who cried wolf. The long and the short of it is the boy learned the hard way that when you report a false threat often enough, no one will pay attention to you when you report a real threat. Many IT gurus complain about receiving an excessive amount of false positive alerts—which are alerts that don’t indicate a threat. Eventually, they grow tired of them and start ignoring the alerts, or they dial down the alert aggression level to reduce the number of alerts or false positives. Although this will solve the alert fatigue issue, they’ll start to experience an even worse issue—false negatives. False negatives are the absence of alerts when a real threat is present.
Advanced Configuration of Routers, Switches, and Other Network Devices
Network devices such as routers, switches, and printers are growing ever more complex, with ever-increasing remote management features and configuration options. Here are some good security measures to take for any network device:
• Disable any anonymous access to information.
• Change the default usernames and passwords.
• Disable any unused or unnecessary services or features.
• Enforce the use of secure protocols only.
A common and very insecure protocol used on many networking devices is Simple Network Management Protocol (SNMP). SNMP is used for remote management and monitoring of network devices and allows the reading and writing of data such as statistics and configuration options. SNMP uses community strings for authentication that are basically passwords transmitted in the clear. SNMP should be disabled unless absolutely required. If SNMP must be enabled, then community write strings should be disabled on all devices possible. Default community strings should always be changed to the maximum possible length and contain both upper- and lowercase letters as well as numbers. Furthermore, all SNMP traffic should be blocked at the network perimeter. SNMP agents should also be configured to filter SNMP traffic from unauthorized internal hosts. Because all SNMP traffic including community strings is transmitted in the clear, SNMP should be used only on top of other secure protocols providing at least confidentiality and integrity. Efforts are being made to replace the traditional insecure SNMPv1 with the more secure SNMPv3.
Use the following additional guidelines when appropriate for configuring switches and routers:
• Use, but do not rely on, MAC address filtering when possible.
• A policy of one MAC address per switch port should be enforced.
• Configure ACLs to not permit known-bad traffic, such as inappropriate or unused IP addresses, or internal source IP addresses on external ports.
• Ensure passwords for controlled access are required for all interfaces, including the console, AUX, and VTY interfaces.
• Do not enable DHCP or BOOTP for edge routers.
• Set the correct date and time.
• Set up proper logging to a syslog server.
• Back up your switch and router configurations.
Transport Security
TLS and SSL exist on top of the transport layer, encapsulating application layer protocols. TLS and SSL provide confidentiality and integrity for application layer protocols such as HTTP, SNMP, and SIP. However, because the encryption occurs at the application layer, transport layer headers such as TCP and UDP headers are not encrypted. TLS and SSL can be used to create tunnels for specific applications. TLS and SSL can both be used to create VPNs by tunneling application layer protocols to their destination network.
IPSec is actually a collection of protocols to perform various functions. IPSec can provide confidentiality, integrity, and authentication of packets as well as protect against replay attacks. Authentication Headers (AHs) provide authentication, integrity, and protection against replay attacks for entire packets. Encapsulation Security Payload (ESP) provides authentication, integrity, and authentication for data or entire packets, depending on the choice of mode. When in transport mode, encryption occurs at the Internet layer, protecting the transport layer protocols. When in tunneling mode, the entire Internet layer packet is encrypted, and a new IP header created, encapsulating the packet. Both modes are useful for secure communication between two hosts. Tunneling mode can allow users to connect a single host on an untrusted network to a trusted remote network. Tunneling mode is also used to create VPNs by bridging two fixed, trusted networks.
Generally speaking, IPSec provides better security but comes with greater overhead, can be more difficult to deploy, and requires specialized support. Wireless networks, mobile devices, and remote access are much more easily handled by SSL-based VPNs. Additionally, SSL-based VPNs can provide more granular access controls.
Trunking Security
VLAN-hopping attacks enable an attacker on one VLAN to gain access to traffic on other VLANs, as shown in Figure 5-6. There are two general types of VLAN-hopping attacks: switch spoofing and double tagging. Although the threat of VLAN-hopping attacks can be mitigated, the best protection is to use separate, dedicated hardware for each VLAN.

Figure 5-6 VLAN hopping attack
Some switches have a dynamic trunking negotiation feature called Dynamic Trunking Protocol (DTP) to assist in their deployment. Even when static trunks are manually configured, DTP is still active. It is possible for attackers to abuse this feature and set up a trunk, enabling them to gain access to and inject traffic into other VLANs. This type of attack is called switch spoofing. To prevent switch spoofing, dynamic trunking should be disabled everywhere, if possible, and should never be enabled for any ports connected to end users. Switchport modes should be statically configured to be either access or trunk. DTP can then be disabled by issuing the switchport “nonegotiate” command on certain platforms.
A second type of VLAN-hopping attack is called double tagging. Due to backward-compatibility features in the 802.1q protocol, native VLAN traffic is not tagged by trunk ports. Attackers can exploit this by creating specially crafted packets with two tags. The first tag is stripped off by the trunk port of the first switch. The second tag, however, remains intact and allows the specially crafted packet to hop to a VLAN specified by the attacker. In order to prevent this attack, follow these procedures:
• Explicitly specify the native VLAN as an unused VLAN ID for all trunking ports.
• Do not use the native VLAN (VLAN 1) for any access port.
• Place any unused ports on a separate, unused VLAN.
• Enable tagging of native VLAN traffic for all ports.
• Use ingress filtering on edge ports to drop tagged packets.
Port Security
We implement port security on switches to provide assurances that only approved devices are permitted to communicate on switchports. This generally involves the whitelisting of approved MAC addresses or, much less commonly, the blacklisting of unapproved MAC addresses. Disabling the port entirely is the most secure option, but that will prevent legitimate devices from plugging in. Port security can be broken down into a few types:
• One-to-one mapping A single MAC address is mapped to a single port. This offers the highest security and requires the most administrative effort.
• Many-to-one mapping A range of MAC addresses is mapped to a single port. This offers medium security and requires a medium amount of administrative effort.
• Many-to-many mapping A range of MAC addresses is mapped to a range of ports. This offers the lowest security but requires the least amount of administrative effort.
Route Protection
Protecting networking routes within an organization and at its borders is critical to security. Attackers exploiting routing protocols and vulnerabilities may gain access to sensitive information, inject traffic, and redirect traffic flows. Successful exploitation may also lead to avenues of attack such as man-in-the-middle or denial-of-service attacks.
The Open Shortest Path First (OSPF) protocol is primarily used for internal routing. In the OSPF protocol, each node announces its link destinations and cost to its neighbors. Nodes also re-announce received link information so that all the nodes know the network topology. Each node then decides routes by calculating the shortest path.
Routing information in OSPF must be exchanged in a secure manner to avoid spoofing attacks. Use only MD5 authentication for the entire network. Authentication keys should be changed on regular basis. Some devices come with simple password-based security enabled and a preconfigured default password. With simple password-based authentication, the password is transmitted in the clear, which should be avoided. Be sure to configure all of the interfaces of OSPF devices to use non-broadcast mode. Non-broadcast mode aids in security through the explicit configuration of valid OSPF neighbors. Autonomous system boundary routers (ASBRs) can filter invalid routes from external sources. Additionally, administrators should be aware of IPv6 ICMP and multicast security implications discussed earlier.
Border Gateway Protocol (BGP) is used for interdomain routing between ISPs or sometimes within very large private networks. BGP is typically used to join multiple organizations that are separately owned and managed. Each organization is referred to as an autonomous system (AS) and is assigned an AS number (ASN). Because BGP typically involves routing communication through multiple autonomous systems, routes are chosen based on a number of factors, including local preference.
Security in BGP is hampered by the inability to control external security policies and BGP routers. However, the security of BGP can be improved by filtering incoming messages with improper address spaces such as your address space, the Martian address space, and known unallocated address spaces. Explicitly configure BGP peers, and only allow BGP prefix announcements with expected ASNs. Additionally, explicitly configuring the TTL of BGP packets to 255 and only accepting incoming BGP packets with a TTL of 254 will help to ensure that the packets originated from one hop away. Limiting the allowed number of received prefixes helps prevent malicious or accidental denial-of-service attacks.
Attackers, eavesdropping on BGP communications, may learn sensitive information about business relationships. Injection and modification of communications is also a serious threat, as previously discussed. In order to ensure authentication, confidentiality, and integrity for BGP communications, work with neighboring autonomous systems to secure the underlying TCP/IP connections used for the BGP protocol. MD5-based authentication, using shared secret passwords, should be enabled. Additionally, TCP/IP connections may be secured through the use of secure protocols such as IPSec.
Routing Information Protocol version 2 (RIPv2) is an older routing protocol intended for smaller, internal networks. RIPv2 is generally easier to configure but has many deficiencies compared to OSPF. Deficiencies include but are not limited to the following:
• Fifteen-hop maximum.
• No assigned cost; each hop has a cost of 1.
• Slower convergence could lead to availability issues.
• Higher bandwidth usage.
If deploying or upgrading a network, consider using OSPF instead. If RIP must be used instead of OSPF, use only RIPv2 because RIP version 1 has even more deficiencies and no support for authentication. When using RIPv2, always enforce MD5-based authentication for updates.
DDoS Protection
A denial-of-service (DoS) attack involves a single threat actor attacking a system in a way that renders its services unusable. Although this is typically achieved through an overwhelming amount of traffic, it can also occur at the smallest of levels—say, a buffer overflow attack. In this case, the outcome is more important than the cause.
If you add multiple threat actors into the equation, DoS attacks are upgraded to distributed denial-of-service (DDoS) attacks. DDoS attacks are more frequent due to their effectiveness of achieving the attacker’s goals of distributing spam, cracking passwords or encryption keys, or, most commonly, disabling the target. DDoS attacks are typically launched by hacker botnets—an army of hundreds, thousands, or millions of systems controlled by a hacker’s command and control (C&C) server. This server in turn controls the botnet machines (bots, zombies, or drones) through the use of malware, typically in the form of a worm or Trojan horse. Upon direction from the hacker, the botnet strikes. Generally, the bots attack with spoofed addresses to confuse the target’s true source. There are numerous countermeasures for DDoS attacks, including the following:
• Patch all network and OS software.
• Disable unused services.
• Implement TCP intercept.
• Use rate limiting to control the rate of inbound traffic.
• Use ISP anti-DDoS services.
• Block ICMP messages.
• Drop requests.
• Absorb the attack with extra bandwidth.
• Disable noncritical services.
Remotely Triggered Black Hole
Black hole routing refers to the practice of dropping traffic before it reaches its intended destination. The sender of the traffic is not notified of the dropped packets, and the black hole is not directly observable with network monitoring tools since the black hole never sends replies. The only way to “see” the black hole is through monitoring lost traffic. A remotely triggered black hole (RTBH) is a more advanced type of black hole routing in that ISPs will react to DDoS attack traffic by triggering an immediate routing table update to deny traffic from affecting a destination company network.
Security Zones
They say that when you chase two rabbits, they both get away. A critical aspect of network design is the creation of security zones. Security zones allow organizations to create a secure environment by choosing appropriate security levels for different networks. There are multiple types of zones, including the following:
• Internet zone Represents the Internet. This is outside our boundary; therefore, we cannot control it. We can only restrict what we send to it or receive from it.
• Internet DMZ Represents the edge of our internal network. This zone is created by our edge firewall, which provides a barrier between the Internet and our internal networks. It also serves as a protected yet visible network to the Internet for consumption of our public servers, including DNS, web services, e-mail services, VPN services, and others.
• Extranet zone Accessible to partner locations from over the Internet. Has the public visibility of the Internet DMZ but is more restricted from an authentication and authorization perspective like the Intranet zone.
• Management zone Contains network, virtualization, and security management systems.
• Intranet zone Represents our internal network. This is where most organizational productivity occurs.
• Restricted zone Mission-critical systems operate here.
DMZ
Multitier network architectures typically have tiers grouped by functionality and arranged by the flow of data. The boundaries between tiers are typically secured using firewalls and other security devices such as IPSs. The key to multitier networking architectures is the deployment of firewalls and proper rules. Proper rules improve security by only allowing communication between adjacent tiers and limiting that communication to essential ports. Thus, in theory, an attacker only has limited access to a single adjacent tier. Multitier network architectures are a good example of employing a defense-in-depth strategy. Figure 5-7 shows the simplest multitier concept, with a DMZ for Internet-visible services separated from the internal network.

Figure 5-7 Simple DMZ implementation
A common multitier network architecture divides the network into three tiers: the DMZ, the application tier, and the data tier. The DMZ consists of Internet-facing services such as web servers, proxies, e-mail gateways, and public DNS servers. A firewall is typically configured to only allow incoming connections to the public services in the DMZ. Nonpublic services such as internal web servers, directory services, internal DNS servers, and application servers are placed in the application tier. The application tier is placed behind the DMZ, with a firewall placed in between and configured to only allow incoming connections from the DMZ on ports used by the application servers. Lastly, the data tier is placed behind the application tier and contains services such as database servers, file servers, storage area networks (SANs), network attached storage (NAS), internal DNS servers, and any devices that contain sensitive information. Once again, the data tier is separated from the application tier with a firewall set to allow incoming traffic from only the application tier, on only the ports required to access the data.
Sometimes the DMZ and application tiers are combined into a single tier and placed behind a new proxy tier. External requests go to the proxy tier, which then makes appropriate requests to the services in the DMZ tier.
Separation of Critical Assets
In chess, the King starts in the middle of the bottom row, and moves toward the corner to isolate itself from the advancing opposition. Yet, the pawns start on the frontlines and move toward the enemy without regard for isolation. Although important, pawns are simply not as vital as the King or Queen. Organizational assets are no different than anything else in our custody—more important objects require stronger security and isolation than others. The most fundamental of all protections is isolation, since a threat too far away cannot cause us harm. Isolating the more important assets from the lesser important assets is what zoning is all about. If security solutions were free from costs and trade-offs, we would simply secure everything to the utmost. Since this is not the case, we judiciously implement the most security on critical assets, and less security on the other assets.
With most enterprises, the critical stuff is on the inside. The Intranet zone is tasked with containing and protecting the internal systems and data with various controls, including physical security, internal firewalls, IDS/IPS, packet sniffers, network encryption, permissions, auditing, and so forth. Yet, the Internet zone threats pose enough risk to our Intranet zone that we stick another zone in between the two—the DMZ as described earlier. The DMZ serves to shield the Intranet zone from the Internet while making resources available to the Internet customers and remote workers. Since the DMZ resources are important, we increase their visibility over Intranet zone resources, yet we still have a perimeter firewall, DMZ, and so forth, to protect those assets.
Let’s take a more mixed approach. What type of zone is publicly visible like the DMZ but requires authentication and authorization like the Intranet zone? As stated earlier, the Extranet zone. This zone is often accessed by franchise groups that wish to connect to a parent company’s Extranet portal from anywhere in the world. The portal is accessible over the Internet but only to authenticated users.
The final method of separating critical assets is to use cloud computing services. Some organizations will go the hybrid cloud route by putting the least important assets in the cloud and the more critical assets on-premises. Whichever your approach is, make sure your critical assets are protected with the strongest security controls and are kept reasonably isolated from all the other assets. Also, if going the cloud computing route, make sure your cloud provider meets the compliance requirements needed by your organization and gives you the security, privacy, and administrative controls necessary to adequately protect your critical assets.
Network Segmentation
Network segmentation is a basic security tool used as part of practicing a defense-in-depth and layered security strategy. The philosophy behind such a strategy is to create layers of security between the organization’s critical or sensitive assets and the outside environment from where attacks might be launched. The idea behind having different layers is that if one layer is penetrated, there remain others still protecting the information or assets. The attacker will have to penetrate each subsequent layer, in turn, which gives security personnel an increased chance to detect the penetration and respond to it. Typically, the outermost layer is considered the network perimeter, which is the boundary between the corporate network and the Internet. The next layer might be the individual operating system security controls on individual hosts. After this may be application security controls regulating who may be able to access specific services. Inside of this is the data, which all of the layers are designed to protect. At each layer, multiple security mechanisms may be in place to help detect intrusive activity and to prevent it from being successful.
Defense-in-depth is a complementary and related topic. It involves taking a look at personnel, technology, and operations to create a coordinated approach to implementing security. It includes more than just the layers of security; it also addresses items such as disaster recovery, forensic analysis, and emergency response. Network segmentation can also play a part in this strategy.
The idea behind network segmentation is to separate parts of your network into related portions, each of which you trust to the same level or degree. The individuals within each segment have common network requirements and related job functions. Segmentation allows the organization to provide a degree of separation between functions, which is one of the fundamental principles of security. This is also related to the principle of “need to know,” in which an individual is only provided with the minimal amount of information (or authorization) they need to accomplish their job. Segmentation for these purposes addresses the internal threat posed by employees who have access to the organization’s networks. By segmenting the data and services, the organization can limit the amount of damage a single user can cause.
Each segment forms a zone that you will monitor separately. You will need to then determine what communication, if any, is required between the zones, and at each one of these communication links you place various access control and monitoring devices (such as firewalls and intrusion detection/prevention systems). An example of where you might see something like this is in the separation of an organization’s business/administrative network and its control systems networks used in operations such as manufacturing, power generation/delivery, and water distribution. Because a common vector for infection of systems with malware is for end users to access sites or open e-mail attachments that they shouldn’t, it is important to separate these functions from the control systems. For an interesting study of how control systems may be compromised, even when there is a degree of separation, review the events surrounding the Stuxnet attack that impacted Iran’s nuclear program.
One way to accomplish network segmentation is through the implementation of a virtual local area network (VLAN). A VLAN consists of a set of systems, all of which have a common set of requirements and communicate as if they were connected to the same domain, regardless of their actual physical location. The VLAN appears to users to be the same as a LAN. In a VLAN, traffic is controlled so that instead of all connected hosts thinking they are on the same broadcast domain, the switch is divided up so that only certain ports can communicate with each other.
Delegation is a related topic, although it has separate goals. Delegation quite simply is the assignment of authority to another person for some specific activity. This may be necessary in a segmented environment because one user may not have authority, or access, to certain services or data. It is not advisable for an individual to simply provide another with their authorization or access control credentials (for example, their user ID/password combination). This would mean that an individual would appear to be somebody else and thus accountability could be lost. Instead, an access control model such as role-based access control (RBAC) could be utilized to provide a level of granularity sufficient to delegate access to specific roles.
Network Access Control
Network access control (NAC) was discussed in a fair amount of detail earlier in the chapter; therefore, only some of the finer details are provided in the upcoming sections on quarantine/remediation, agents, and agentless implementations.
Quarantine/Remediation
Since NAC is all about ensuring that devices meet predefined health policy criteria prior to connecting to the network, what happens when the devices aren’t compliant with the policy? The NAC server may either drop the connection entirely until the client resolves the compliance issue or quarantine the client to a restricted network where a remediation server is available to help the client “get compliant.” This usually amounts to the remediation server deploying antimalware definitions or operating system updates to the client. Shortly thereafter, the client can attempt to connect to the production network again and should be granted access.
Persistent/Volatile and Nonpersistent Agents
Agent software runs on NAC clients in order to perform authentication and compliance checking prior to connecting to an organization. These agents behave differently depending on what type of agent is in use. Persistent agents reside on the client after connections are severed, whereas nonpersistent agents disappear from a client once a connection is ended.
Agent vs. Agentless
Despite the prevalence of agents, not all clients should use them. Agents are commonly used on trusted devices that reside within or external to the organization for long stretches of time. They provide us with better control, security, and tracking capabilities than agentless solutions. The downside is, agents increase costs and overhead for an organization, particularly for devices that are untrusted, don’t belong to the organization, and are here one minute and gone the next. Typically, the best route to go with unknown/untrusted devices is agentless. Granted, there’s less control and insights into device behaviors, but it also reduces deployment overhead.
Network-Enabled Devices
We’ve spent quite a bit of time going over fan-favorite network devices like switches, routers, firewalls, intrusion detection/prevention systems, and so forth. Yet, other devices, which traditionally hadn’t occupied the realm of networking and information security, may now fall under your list of responsibilities. These devices include building and home automation systems, IP video devices, HVAC controllers, sensors, physical access control systems, A/V systems, and scientific and industrial equipment. What’s changed is, these technologies are now likely to have network interface cards (including Wi-Fi), MAC addresses, IP addresses, protocols, firmware, software, and operating systems—all of which can be vulnerable and exploited by various threats. The upcoming sections talk about these network-enabled devices.
System on a Chip (SoC)
SoCs are electronic devices that combine the functions of CPUs, memory, and other hardware onto a single circuit board. Essentially, an entire system is consolidated onto a single chip. Although SoCs are not network-enabled devices in themselves, they provide the core functionality to many such devices, including Internet of Things (IoT) devices, mobile devices, and home appliances. Most importantly, SoCs are critical to some of the topics in this chapter, such as building and home automation systems, HVAC controllers, and industrial equipment.
Building/Home Automation Systems
Outside of IT, organizations still have the rest of the building to worry about, such as this not-so-small thing called facilities. Management of power, lighting, ventilation, water systems, alarms, and physical security systems can present certain administrative challenges from equipment being proprietary, managed separately from other equipment, and expensive due to the reliance on multiple specialists to keep everything running.
These concerns are being addressed due to these technologies adopting many of the protocols, firmware, operating systems, and application programing interfaces (APIs) as regular computers today. Everything from security systems and lighting to refrigerators and watches are connecting to our wireless and wired networks. Given this technological integration, organizations are able to implement unified control centers called building automation systems (BASs). A BAS is a centralized management system to manage and monitor facilities and environmental technologies. Organizations are providing increased employee comfort, productivity, cost-savings, and efficiencies due to better management, monitoring, notifications, logging, and maintenance tasks being performed by an advanced and unified toolset.
IP Video
With camera devices built into our laptops, smartphones, and tablets, and even connected externally to a lot of desktop systems, organizations are able to improve both their collaboration and surveillance capabilities. Many organizations are installing IP-based cameras throughout the building to perform video surveillance of critical areas and systems. Although discussed at greater length in Chapter 16, the most common usage of IP video is for video conferencing. With IP video devices, people are able to attend “face-to-face” meetings remotely, teach or attend classes online, and have remote job interviews, all the while saving time and money on travel expenses. Given the prevalence of IP video in today’s business and consumer markets, be mindful of the following considerations:
• IP video is bandwidth-intensive. Make sure you have more bandwidth than you need.
• Most IP video conversations lack encryption capabilities, which increases the risk of packet sniffing, man-in-the-middle attacks, and session hijacking.
• Implement quality of service (QoS) to guarantee connection quality.
• If you’re storing video data long term, make sure you have adequate storage.
HVAC Controllers
Heating, ventilation, and air conditioning (HVAC) controllers allow us to centrally control the heating and cooling temperatures for the enterprise. It goes without saying how important the physical comfort of employees is to the success of an organization. To keep everyone happy, organizations typically put their HVAC systems on autopilot. This will help cut operational costs, reduce management overhead, and ensure that employee comfort is maintained throughout business hours. To that end, HVAC systems are configured with “floors” (minimums) and “ceilings” (maximums). For example, if the temperature goes below 72 degrees, the heater turns on to raise the temperature. If the temperature reaches 78 degrees, the A/C turns on to reduce the temperature. The system will probably remain on standby while temperatures are in between those two values. After business hours, the system will turn off to cut down on power usage and reduce wear and tear.
Despite the central management provided by HVAC controllers, they are still isolated from the rest of the facilities and IT networks. Our recent coverage of building automation systems calls for the integration of HVAC into the rest of our facilities networks to further centralize management and improve operational efficiencies. We use a protocol called BACnet/IP, abbreviated as B/IP to make BACnet IP-friendly and allow interfacing with BAS networks.
Sensors
Sensors are crucial in our facilities and networks because they allow our technologies to understand important environment measurements and when changes occur. It’s important that sensors quickly react to changes in the environment because changing conditions can affect everything from the performance and availability of systems, to our physical health and safety. In HVAC systems, sensors are used to help measure temperatures, but what about the sensors from a smoke alarm detecting smoke? Sensors can also detect motion, sound, space utilization, air pressure, humidity levels, voltage, oxygen, mold, and even carbon monoxide levels.
Since sensors are specific to a type of technology, the risks, threats, and exposures common to them will vary from one technology to the next. A hacker compromising an HVAC is not nearly as dangerous as a compromised smoke alarm or carbon monoxide sensor. Regardless, these things can and will be hacked—it’s just a matter of time. We must perform risk assessments of all equipment, including the facilities equipment that contain physical sensors in order to find vulnerabilities and mitigate them before it’s too late.
Physical Access Control Systems
Physical access control systems help determine if access to a building, area, or room should be permitted or not. As this book will often state, physical security is the most important kind of security there is; therefore, organizations must invest heavily in physical access control systems to protect not only our physical and digital assets, but also the lives of the people and customers in the establishment. Other than common methods like doors and locks, the following are some examples of physical access control systems:
• Proximity readers The reader is installed in the wall and admits a person into an area if that individual places an approved and activated card onto the reader. This is a convenient method but is subject to people forgetting to bring their cards.
• Biometric readers Similar to a proximity reader, but instead people place their finger on the biometric reader, or position their eye in alignment and within range of the reader. This is more convenient than a proximity reader because if the fingerprint feature is used, people are not likely to forget their fingers at home.
• Mantraps To prevent unauthorized individuals from tailgating or piggybacking through a door behind other authorized individuals, we can use mantraps. Mantraps are a combination of a room with two doors, one on each end. A mantrap forces authorized staff members to enter the first door alone, provide credentials again in the room, and then exit through the second door before anyone else can enter through the first door. If two individuals try to enter through the first door at the same time, an alert will warn them that one individual must leave the room; otherwise, a security or law enforcement person will be notified. These are more common in highly sensitive environments.
A/V Systems
Add audio/video (A/V) systems such as TVs, projectors, surveillance, video-conferencing devices, live-broadcast devices, microphones, and speakers to the long list of devices connected to our networks. Many enterprises have lobbies with a wall-mounted TV broadcasting company products, employee recognition awards, and PowerPoint slides, as well as radios playing music in the background, cameras taking picture IDs of visitors, and an IP camera performing lobby surveillance. The IP camera and TV in particular are likely being controlled remotely by a client or server application.
Any A/V systems that are attached to the network infrastructure are subject to malicious attacks. They are subject to DoS attacks and data being intercepted in transit. Also, they can be remotely controlled by a hacker, who can then aim the camera and adjust the camera and microphone sensitivity levels for increased surveillance. If any of these devices have firmware, updating the firmware to the latest version is important as a security countermeasure. Also, basic hardening practices should be observed on the clients or servers that manage these devices remotely, including patching, strong password policies, locking systems when not in use, encrypting traffic between clients and A/V devices, and disabling microphones, cameras, and speakers when not in use.
Scientific/Industrial Equipment
If you haven’t noticed by now, just about all technology is connecting to TCP/IP networks. It’s not just home security systems, cars, airplanes, toys, and refrigerators, but also scientific, medical, and industrial equipment. Although this integration with IP provides a host of benefits, including easier management, monitoring, reporting, and communication within and across different business teams, there’s also the increased security and privacy risks that naturally arise from the convenience of integration.
Imagine healthcare devices such as MRI machines, CAT scan machines, and X-ray machines being hacked into. Not only can hackers compromise millions of dollars’ worth of medical equipment, but there’s also the risk of electronic health records (EHRs) being leaked or held for ransom.
Industrial facilities such as warehouses may have much older equipment that doesn’t support cryptography. This subjects the organization to eavesdropping and various other threats common to plaintext network traffic.
Critical Infrastructure
Critical infrastructure refers to systems that are essential to the health and safety of a society or economy. If something were to happen to the infrastructure of food producers, health services, power generators, telecommunications, defense systems, water supplies, agricultural systems, or pharmaceuticals, our well-being could be in significant danger. With critical infrastructures migrating further into IT wheelhouses, IT and security professionals must have knowledge of the workings of critical infrastructures and how to secure them. As the SCADA worm called Stuxnet made clear to the entire world, if nuclear facilities can be hacked in order to halt nuclear progression, what can’t be hacked?
Today’s critical infrastructure systems are increasingly controlled by industrial control systems (ICSs). The most prominent examples are SCADA systems. SCADA systems were originally designed primarily for reliability and safety without security as a primary objective. SCADA systems are typically made up of several sensors for data collection, with a SCADA master system monitoring the sensor data, alerting an operator if a change-of-state (CoS) event occurs. Some SCADA systems incorporate system control functions, allowing for the automated response to CoS events. Because SCADA systems are commonly used to control the physical processes of industrial systems, including critical infrastructure, successful attacks can have a devastating impact in the physical world.
For protection against remote attacks, do not connect SCADA systems to the Internet or other networks if you can possibly avoid it—what cannot be reached at all usually cannot be breached. However, sometimes communication over other networks is required. If SCADA systems must be connected to other networks, isolate the SCADA systems as much as possible in the following manner:
• Always protect the SCADA systems from other networks with a firewall.
• Configure routers to restrict network traffic via access control lists (ACLs).
• Use VLANs to facilitate secure communication between networks.
• Filter traffic based on MAC address (although this can be spoofed).
• Closely monitor all traffic passing on the VLANs and networks used for SCADA traffic.
Even isolated SCADA networks are vulnerable from onsite attacks or attacks on management devices. Here are some additional steps that should be taken in order to improve the security of the SCADA devices themselves:
• Replace default passwords with secure passwords.
• Do not use the same password for different devices or users.
• Change passwords on a regular basis.
• Disable unused or unnecessary device features.
• Configure banners and device names to reveal no information.
• Manage the devices with secure hosts used for no other purpose.
• Use physical access control and monitoring.
• Perform regular security training and auditing.
Chapter Review
In this chapter we covered the integration of network and security components, concepts, and architectures to meet organizational security requirements. It began with a large section on physical security devices, which may also have virtual instances available. These physical security devices include UTMs, which consolidate multiple security devices into one. We also provided coverage of IDS/IPS devices, which scan network traffic to detect and stop attacks, respectively. We talked about how INE devices encrypt traffic on the fly over potentially insecure WAN links. We mentioned that NAC systems require connecting systems to comply with health requirements or be subjected to a quarantined status until remediation is provided. SIEM was discussed in terms of how it aggregates log information from multiple sources into a consolidated and analyzed format.
We then ventured into more traditional network hardware, such as switches, which connect devices to a network, and physical firewalls, which filter traffic entering and leaving a network. We talked about wireless controllers and how they centralize the configuration and deployment of policies for all of the organization’s wireless access points. We talked about routers and how they connect networks to networks, and we talked about proxy servers, which connect to the Internet on behalf of internal systems. The next topic was load balancers and how they distribute traffic to one of multiple choices of endpoints based on utilization of those endpoints. The last two topics were HSMs and microSD HSMs. HSM devices help secure networks by being a root of trust for key generation as well as key and certificate signing, plus an authentication point for validated applications to be permitted or denied execution.
The next section focused on application and protocol-aware technologies, beginning with WAFs. WAFs are application-level firewalls designed specifically to protect web applications from unauthorized traffic flows. The next topic was passive vulnerability scanners, which attempt to discover vulnerabilities in network traffic without interfering with the traffic flow itself. The last topic in this section was DAMs, which focus on monitoring databases for signs of malicious activity.
The third section in this chapter went over advanced network design elements, beginning with remote access. The first remote access topic was VPN and how it enables workers to connect to organizational networks securely from anywhere. That lead us to the next related topic of IPSec, which helps perform the encryption that VPN depends on for security. Another way of securing VPN is through SSL/TLS-based security techniques, which are typically used for web connections. We then ventured over to SSH and the encryption benefits it provides for terminal emulation–based connections. Another popular remote access method is RDP, which is targeted at Windows systems for remote graphical control of other Windows systems. An alternative to RDP is VNC, which is a vendor-neutral remote desktop sharing application commonly used in scenarios where RDP is not practical or supported. We switched gears to discuss VDI, which is a thin-client scenario where clients can access their desktop and application environment on a remote server. We discussed how reverse proxy servers publish internal web applications for external access through the reverse proxy server. Given the steady migration from IPv4 to IPv6, we provided a brief discussion about how that migration can work and the basics of IPv6. We included coverage on various network authentication methods such as PAP, CHAP, MS-CHAP, MS-CHAPv2, EAP, and 802.1x. We discussed mesh networks and their redundant links to all other endpoints. The final topic focused on placement of fixed/mobile devices, hardware, and applications, which centered around locating security systems in carefully chosen locations to maximize our security posture.
The next section was on complex network security solutions for data flow. We began the section with coverage of DLP, which uses policies on certain data types to restrict unapproved movement or leakage of sensitive data. We then went into deep packet inspection, which involves application-level firewalls and next-generation firewalls scanning the data portion of packets to identify application fingerprints. We also covered data flow enforcement, focusing on how data may be restricted in terms of movement as well as the directions of movement within and across networks. That led us to a discussion on network flow (sFlow), which focused more on network monitoring considerations and best practices. We finished this section with coverage of data flow diagrams, which provide a visual for understanding data flows throughout the organization.
We began the next section on secure configuration and baselining of networking and security components by discussing network baselining. Network baselining helps us identify normal and acceptable network performance levels so that we know what to strive for. Afterward, we covered configuration lockdown to “seal” the baseline configurations to prevent modification at a later date. We talked about change monitoring, which allows us to detect and prevent unauthorized changes to the network baseline. We discussed availability controls, which help keep the systems and their baselines available when needed by end users.
The following section was on software-defined networking, which uses centralized management tools, on-premises or in the cloud, to control the function of networking devices, whereas the devices themselves handle the actual forwarding of data.
Another brief section followed on network management and monitoring tools. We began this section discussing the merits and criteria of alerts, particularly from the Snort application since it is very popular. We also went into alert fatigue, which happens whenever too many junk alerts desensitize the interest of administrators.
We began the next section with coverage of advanced configurations of routers, switches, and other network devices. Transport security was discussed in order to ensure that network devices require cryptography for traffic in transit. We followed this up with coverage on trunking security, which identifies techniques for preventing both VLAN hopping and switch spoofing. Port security is crucial to switch security since it has the potential to prevent unauthorized users based on their unapproved MAC addresses. We talked about route protection techniques specific to the RIP, OSPF, and BGP routing protocols. DDoS countermeasures include patching, black hole routing, and bandwidth absorption, as well as remotely triggered black holes providing a DDoS countermeasure from the ISP.
In the next section we discussed security zones, talking about the DMZ and the isolation it provides to the internal network while slightly exposing the perimeter network to Internet customers and remote workers. We also talked about the need for separating critical assets from the less-critical assets, and finally we talked about network segmentation through VLANs.
The next section was on network access control and how it polices non-healthy devices from connecting to the network until they receive assistance from a remediation service, which is typically found on a remediation network. We followed this up with a discussion on persistent versus nonpersistent agents. Persistent agents survive after a connection ends, whereas nonpersistent agents dissolve immediately after the connection is terminated. We finished this section with a discussion on the need for agents on company devices, whereas personal devices can generally do without agents.
The next-to-last section in the chapter discussed network-enabled devices, beginning with system on a chip. These all-in-one chips are frequently found on mobile devices and IoT devices. We then moved on to building/home automation systems, which simplify how organizations and residences manage their various non-IT equipment using centralized and automated tools. We talked about IP video, including its benefits, security issues, and mitigations. We covered HVAC controllers and their changing role, from operating in a silo to being integrated with the rest of the organization’s network infrastructure. We discussed the various sensors found in IT and facilities equipment and how they help us discover issues. The next topic was physical access control systems, which lead to mantrap doors, proximity readers, and biometric readers. We went into audio/video systems and the unique challenges they bring to an organization, and we finished the section discussing scientific and industrial equipment such as healthcare and warehouse systems.
The final section in the chapter focused on critical infrastructure components such as the industrial control system known as SCADA. We talked about the continued integration of SCADA systems into IP networks and the unique benefits and challenges that brings to the organization.
Quick Tips
The following tips should serve as a brief review of the topics covered in more detail throughout the chapter.
Physical and Virtual Network and Security Devices
• Unified threat management (UTM) incorporates the functions of multiple network and security appliances into a single appliance.
• An NIPS/NIDS identifies intrusion attempts by examining network traffic, potentially looking at both the header and contents of packets being transmitted.
• Inline network encryptors (INEs) are devices that encrypt sensitive information en route between sources and destinations across insecure networks like the Internet and company WAN links.
• NAC improves network security by employing policies that mandate devices meet certain security minimums before being granted network access.
• Security information and event management (SIEM) utilities analyze and correlate logs and events from multiple sources as well as provide real-time alerting features.
• Switches are network appliances that connect devices such as workstations, servers, and printers together to form a network.
• Network firewalls are devices that evaluate incoming and outgoing traffic to determine if the traffic should be allowed or denied entry across a network boundary.
• Wireless controllers are network appliances or software solutions that enable administrators to centralize security configurations across multiple WAPs simultaneously.
• Routers are devices that connect networks to networks in order to forward traffic based on network addresses such as IP addresses.
• Proxy servers are hardware or software systems that act as connection intermediaries between internal clients and Internet resources.
• Load balancers are network devices or programs that distribute traffic across a group of similar servers known as a server farm or pool, in order to increase server performance and availability.
• Hardware security modules (HSMs) are devices that provide key generation and safeguarding services, speed up specific cryptographic operations on platforms requiring strong authentication, and provide access control capabilities.
• MicroSD HSMs are tiny HSM cards that plug into the microSD ports of smart devices such as Android smartphones and tablets.
Application and Protocol-Aware Technologies
• Web application firewalls (WAFs) specialize in the monitoring and filtering of unauthorized and malicious traffic sent to and from web applications to provide them with protection against various Internet threats.
• Passive vulnerability scanners (PVSs) analyze network traffic in order to non-intrusively discover vulnerabilities with organizational assets.
• Database activity monitors (DAMs) monitor the transactions and other activity of database services.
Advanced Network Design (Wired/Wireless)
• Many organizations treat remote access traffic as potentially hostile and do not allow remote access traffic to come directly into the internal network.
• A virtual private network (VPN) offers security by tunneling data across a network through the use of technology that offers a secure means of transport.
• Internet Protocol Security (IPSec) is a suite of protocols for securing packets that traverse an IP network.
• SSL is a protocol for securing communication sessions over IP networks, whereas TLS is its more powerful and relevant successor.
• Secure Shell (SSH) is a protocol for obtaining a remote shell session with an operating system over a secured channel, using TCP port 22.
• Remote Desktop Protocol (RDP) provides a secure, graphical, remote access connection over a network between computers via port 3389.
• Virtual Network Computing (VNC) is a platform-independent graphical desktop sharing protocol that uses the Remote Frame Buffer (RFB) protocol.
• Virtual Desktop Infrastructure (VDI) involves the hosting of a desktop OS within a virtual environment on a centralized server.
• Reverse proxy servers provide Internet devices with access to servers behind an enterprise firewall.
• PAP is an authentication protocol that sends credentials over the network in plaintext.
• CHAP uses a 3-way handshake and an encrypted hash of the password to authenticate to other devices.
• MS-CHAP is Microsoft’s first proprietary implementation of CHAP. It provides better password storage than CHAP but is otherwise considered weak by today’s standards.
• MS-CHAPv2 provides mutual authentication between endpoints to prevent rogue server attacks and other nonrepudiation and integrity violations. It also uses different keys for sending and receiving.
• EAP is a framework for plugging in more powerful hardware and software authentication methods, ranging from smart cards and fingerprint readers to PKIs and certificates.
• PEAP enhances EAP by encrypting it in a TLS tunnel.
• LEAP was designed to use Wired Equivalent Privacy (WEP) for security and therefore should be discarded in favor of stronger methods like EAP-PEAP.
• The 802.1x standard is a port-based network access control method that requires users to authenticate prior to connecting to a wired or wireless network.
• Mesh networks involve all devices being directly connected to all other network devices in order to increase path redundancy and, thus, the availability of the network.
• Placement of security devices must take several factors into consideration, such as the purpose of the device, its own survivability, and at what point you want this device to interact with the network traffic.
Complex Network Security Solutions for Data Flow
• Monitoring data flows allows organizations to detect sensitive information leaving the network.
• The goal of data loss prevention (DLP) is to monitor, detect, and prevent the loss of sensitive data.
• Deep packet inspection (DPI) occurs when application-level and next-generation firewalls scan and analyze the header, state, and data portions of packets before allowing or dropping them.
• Data flow enforcement refers to the secured and controlled flow of data within a device, between devices within a network, and across other networks.
• A network flow is a sequence of packets transferred from a sending host to one or more receiving hosts.
• sFlow is a method for monitoring traffic in switched and routed networks.
• Data flow diagrams graphically represent the data flow that occurs between computer systems on a network.
Secure Configuration and Baselining of Networking and Security Components
• Baselining allows us to document what the normal and acceptable levels of performance are and to use this performance level as the measuring stick for future measurements.
• Configuration lockdown seals the configurations into our network devices to prevent unauthorized changes.
• Change monitoring checks for signs of failed or successful attempts at modifying our network’s configuration baselines as well as any signs of unauthorized devices or behaviors being introduced into the network.
• Availability controls help ensure data is accessible and resistant to failure.
• ACLs are lists of rules that we apply on routers, firewalls, and so on, in order to, for example, define what packets are permitted or denied entry through a network interface.
Software-Defined Networking
• Software-defined networking (SDN) centralizes the configuration and control of network devices.
• SDN decouples the control element of network devices from the forwarding element.
• The control element refers to the router’s responsibility over its internal routing table and protocol operations.
• The forwarding element simply forwards traffic based on the information in the routing table.
• Cloud computing providers thrive on SDN since the centralization of network device management will enable automation of network management and configuration changes, in addition to monitoring.
• SDN improves operational efficiencies, which in turn reduces overall costs, addresses vendor lock-in challenges, cuts costs on hardware, and creates more consistent security configurations on disparate networking devices.
Network Management and Monitoring Tools
• Auditing is the practicing of determining who to hold accountable for recorded actions.
• Logging is the practice of recording activities into a file for troubleshooting, tracking, and evidence collection purposes.
• Sniffers capture and analyze network traffic.
• Network devices send us alerts to keep us aware of changing and malicious conditions that require immediate attention.
• Alert fatigue occurs when administrators stop paying attention to alerts due to too many false positives.
Advanced Configuration of Routers, Switches, and Other Network Devices
• TLS and SSL provide confidentiality and integrity for application layer protocols such as HTTP, SNMP, and SIP.
• Trunking security helps mitigate various switch attacks, including switch spoofing and double-tagging attacks.
• Port security helps provide assurances that only approved devices are permitted to communicate on its ports.
• Route protection ensures routing table contents, transmissions, and router configurations are protected from unauthorized access and modification.
• DoS attacks involve a single threat actor attacking a system in a way that renders its services unusable.
• A remotely triggered black hole (RTBH) is a more advanced type of black hole routing in that ISPs react to DDoS attack traffic by triggering an immediate routing table update to deny traffic from affecting a destination company network.
Security Zones
• Security zones allow organizations to create a secure environment by choosing appropriate security levels for different networks.
• DMZs are perimeter networks that simultaneously protect the internal network while providing secured access to edge resources.
• Separation of critical assets provides the strongest level of isolation to the most important assets.
• Network segmentation creates layers of security between the organization’s critical or sensitive assets and the outside environment from which attacks might be launched.
Network Access Control
• Clients not compliant with network access control policies are quarantined to a restricted network where they seek remediation for their deficiencies, such as missing Windows updates or antivirus definitions.
• Agent software runs on NAC clients in order to perform authentication and compliance checking prior to connecting to an organization.
• Persistent agents will reside on the client after connections are severed.
• Nonpersistent agents will disappear from a client once a connection is ended.
• Agents are commonly used on trusted devices that reside within or external to the organization for long stretches of time.
• Agentless clients are common for devices that are not owned by the organization.
Network-Enabled Devices
• Network-enabled devices refer to devices that have only recently started integrating with IP networks.
• SoCs are electronic devices that combine the functions of CPUs, memory, and other hardware onto a single circuit board.
• Building automation systems are centralized management systems that manage and monitor facilities and environmental technologies.
• IP-based cameras provide video surveillance of critical areas and systems.
• Heating, ventilation, and air conditioning (HVAC) controllers allow us to centrally control the heating and cooling temperatures for the enterprise.
• Sensors are crucial in our facilities and networks because they allow our technologies to understand important environment measurements and when changes occur.
• Physical access control systems help determine if access to a building, area, or room should be permitted or not.
• Audio/video (A/V) systems such as TVs, projectors, surveillance, video-conferencing, live-broadcast devices, microphones, and speakers are now routinely connected to the network and are therefore subject to attacks.
• Scientific and industrial systems are merging with IP networks and are now subject to the same risks, threats, and vulnerabilities.
Critical Infrastructure
• Critical infrastructure refers to systems that are essential to the health and safety of a society or economy.
• If something were to attack the infrastructure of food producers, health services, power generators, telecommunications, defense systems, water supplies, agricultural systems, or pharmaceuticals, our well-being could be in significant danger.
• SCADA systems are commonly used to control the physical processes of industrial systems, including critical infrastructure.
Questions
The following questions will help you measure your understanding of the material presented in this chapter. Read all the choices carefully because there might be more than one correct answer. Choose all correct answers for each question.
1. Segmenting remote access traffic allows you to do which of the following?
A. Treat remote access traffic as potentially hostile.
B. Filter traffic through a firewall and IDS/IPS.
C. Verify the patch and antivirus status of remote users before allowing them to connect to the organizational network.
D. All of the above.
2. If you’re looking to get maximum visibility into attacks launched at your organization from hostile Internet sources, where would you place an IDS/IPS?
A. Right behind the main firewall between your organization and the Internet
B. Between your server farm and user base
C. In front of the main firewall between your organization and the Internet
D. In the DMZ, preferably next to a web server
3. Which of the following is not a best practice when securing SCADA networks?
A. Replace default passwords.
B. Filter traffic based on MAC address.
C. Place SCADA devices on VLANs with other Internet-visible traffic.
D. Perform regular auditing of devices.
4. Which of the following is an advantage of IPv6 over IPv4?
A. Smaller address space
B. Widely used by most organizations
C. Support for IPSec and better QoS capabilities
D. Protocol and Type of Service fields in header
5. Which of the following device types is likely to provide multiple security and network services, including DLP, QoS, and VPN services?
A. UTM
B. Router
C. Proxy server
D. Firewall
6. Which of the following modern physical access control systems provides consolidated IP-based control over all facilities equipment?
A. HVAC controller
B. BAS
C. SoC
D. SCADA
7. Which of the following IPv6 tunneling methods can traverse a NAT device?
A. Teredo
B. 6to4
C. ISATAP
D. SIEM
8. Hardware security modules perform which security functions for an enterprise? (Choose all that apply.)
A. Sniffing the network in search of malicious or unapproved traffic
B. Safeguarding of keys
C. Key generation
D. Preventing execution of unauthorized applications
9. A common multitier network architecture might consist of which of the following layers?
A. DMZ, SAN, and VLAN tier
B. DMZ, application tier, and data tier
C. NAS, DMZ, and data tier
D. Public tier, private tier, and FMZ
10. What is the first step in secure infrastructure design?
A. Determine the placement of firewalls and other perimeter devices.
B. Identify network components and their security needs.
C. Identify supported protocols.
D. Catalog applications that will be used within the network.
11. Which of the following guidelines should be used when configuring routers and switches?
A. Do not enable DHCP or BOOTP for edge routers.
B. Use Telnet for access to management interfaces.
C. Disable MAC filtering on internal switches.
D. Configure ACLs to only monitor traffic originating from outside your network.
12. What are the two common types of VLAN-hopping attacks?
A. Switch spoofing and double tagging
B. MAC switching and reverse tagging
C. Route poisoning and DDoS
D. ARP spoofing and reverse VLAN injection
13. Where is the Open Shortest Path First (OSPF) routing protocol most commonly used?
A. As an internal routing protocol
B. Between gateway routers
C. Between DMZs and external firewalls
D. For dynamic routing updates given to remote access users
Answers
1. D. Segmenting network traffic allows you to treat remote access traffic as potentially hostile, filter traffic through a firewall and IDS/IPS, and verify the patch and antivirus status of remote users before allowing them to connect to the organizational network.
2. C. The best place to view and analyze attacks originating from Internet sources is on your main network link between your firewall and your Internet connection.
3. C. You specifically want to avoid placing SCADA devices in situations where they are exposed to Internet-visible traffic such as in a DMZ.
4. C. IPv6 has integrated support for IPSec and better QoS capabilities than IPv4.
5. A. UTM devices integrate numerous security and networking functions into a single all-in-one device.
6. B. Building automation systems (BASs) integrate and automate building systems management across an IP network.
7. A. Teredo tunnels can traverse NAT devices.
8. B, C, D. Among other things, HSMs can provide safeguarding of cryptographic keys and key generation services as well as prevent the execution of unauthorized applications.
9. B. A common multitier architecture might consist of a DMZ, application tier, and data tier.
10. B. Identifying network components and their security needs is the first step in secure infrastructure design.
11. A. DHCP and BOOTP should not be enabled on edge routers.
12. A. The two main types of VLAN-hopping attacks are switch spoofing and double tagging.
13. A. The Open Shortest Path First (OSPF) routing protocol is most commonly used as an internal routing protocol.