CHAPTER 7
Mobile Security Controls
This chapter presents the following topics:
• Enterprise Mobility Management
• Security Implications/Privacy Concerns
• Wearable Technology
It goes without saying that mobile devices have permeated the globe in the past decade, with a variety of wearable devices catching fire in the past few years. When you hear people talking about mobile devices and wearables, there’s always that one person who comes out with the Terminator “Skynet” joke, where all the technology in our society coalesces into an artificial intelligence ring—always a threat to the human race. Look around: today’s mobile technologies have been scattered across the environment, into our homes, and are now being worn or implanted into our bodies. On top of this, surveys show that tens of billions of devices will be connected to the Internet by 2020. We’re all going to be hearing a lot more Skynet jokes over the next few years.
Our job as security practitioners is to understand this mobile device revolution, the various devices, how they work, how to manage them, and the unique security considerations inherent in their usage at the enterprise. We start this chapter off with enterprise mobility management, which is largely about mobile device management (MDM) tools. Next, we dive into the various security and privacy concerns inherent in an industry populated by devices loaded with cameras, microphones, and radio antennas. We then end the chapter by discussing various wearable technologies and their benefits, in addition to the security risks they bring.
Enterprise Mobility Management
One way or another, all enterprises have to deal with the mobile device “movement”—it’s just a question of how. Should enterprises shoulder the burden of purchasing all mobile devices? Should they transfer the costs to the users? Should they use a mobile device management tool or take their chances managing mobile devices in silos? Better yet, should they disallow mobile devices entirely? Not surprisingly, each path offers a sliding scale of costs versus benefits, and it’s up to the enterprise to choose wisely. Assuming that mobile devices will be permitted at some level, they must be managed. Yet again, it becomes a question of how, because mobile device management is challenging. Here are some challenges that enterprises must consider:
• Budget
• Compliance and security policy requirements
• Device types and versions
• OS types and versions
• Inventory management
• Logging and auditing
• Application management
• Patch management
• Employee usage patterns
One thing we feel fairly certain about is a centralized approach to management is usually the best option because it provides a consistent and comprehensive way of locking down devices to meet security policies and compliance requirements—while still allowing users to be productive. This section covers some of the issues regarding enterprise mobility management and the recommended solutions.
Containerization
Mixing business with pleasure is a balancing act in life, as it is with mobile computing. Enterprises routinely face the challenge of corporate data and personal data coexisting on the same device. Enterprises run the risk of either over-managing the device at the expense of personal data or under-managing the device at the expense of corporate data. This is a common occurrence in “bring your own device” (BYOD) scenarios since users accumulate more personal data on devices they own.
Containerization addresses this issue by isolating corporate data into a protected and encrypted container stored on the mobile device. Corporate data resides inside the container, and user data resides outside the container. Organizations are now free to manage the corporate data, or the container as a whole, without fear of compromising the personal data. Such management will typically be performed by MDM policies from products such as VMware AirWatch and Microsoft Intune.
Configuration Profiles and Payloads
A big part of managing mobile devices is ensuring their complete and timely configuration as per enterprise requirements. Considering the vast differences between devices, and potentially being located anywhere in the world, enterprises are turning to cloud-based MDM platforms to centralize control. MDM tools allow us to create and assign configuration profiles that are, essentially, the next-generation of group policies. Configuration profiles are groups of OS and application settings applied to various devices inside and outside of an enterprise. Configuration profiles can be tailored to specific device types or generalized across a mix of device types. Let’s take a look at some examples of configuration profiles that VMware AirWatch can add:
• Android
• Apple iOS
• Apple macOS
• Apple TV
• BlackBerry
• Chromebook
• Symbian
• Windows Mobile
• Windows PC
• Windows Phone
Let’s say you want to assign a Microsoft Intune configuration profile to an Android device. You could choose from the following configuration profile types:
• Device restrictions
• E-mail configuration
• Wi-Fi configuration
• VPN configuration
• SCEP certificate
• PKCS certificate
• Trusted certificate
• Custom
For example, if you were to select the “Wi-Fi” profile type and then select “Enterprise,” you would be required to set up the SSID, automatic connection option, SSID broadcast option, and the EAP type, such as EAP-TLS, EAP-TTLS, or PEAP. These individual settings are sometimes called payloads.
If we were to choose the “Device Restrictions” profile type, you could choose from a variety of password options, such as minimum length, password expiration, password complexity, biometric support, and so on. You would also be able to choose other generalized options, including disabling the device camera, screen capturing, and default app permissions, among several other options. Figure 7-1 shows a screenshot of creating a configuration profile for an Android device.

Figure 7-1 Microsoft Intune configuration profile
Personally Owned, Corporate-Enabled (POCE)
Personally owned, corporate-enabled (POCE) is basically another way of saying BYOD. Over 50 percent of enterprises allow workers to use personal devices to perform work-related tasks—with this number expected to steadily rise in the next few years. If this is the case, enterprises will typically require the device to be “onboarded” as a condition for allowing it to access the enterprise network. Onboarding formally aligns the device with company policies and requirements. This includes installing apps as well as enabling drive encryption, PIN numbers, biometrics, location, remote backup, remote wiping services, and numerous other device restrictions. The easier this outcome, the more likely enterprises will trust BYOD.
Application Wrapping
MDM policies allow us to apply additional protections to mobile applications through a configuration process called application wrapping. Application wrappers are additional security features added to a mobile application that don’t modify the underlying functionality of the application itself. These additional security requirements can include the following:
• User must authenticate to use the application. Even if the application itself doesn’t support authentication, the wrapping can still add the functionality.
• Restrict certain data types from being stored on the device.
• Restrict who is allowed to download specific applications.
Remote Assistance Access
MDM tools often provide the capability for IT departments to remotely assist users with their mobile devices. Through remote assistance, helpers can access the user’s device screen, observe settings and monitor performance, install or remove applications, and set up e-mail, VPN, or Wi-Fi services. The helper will also have the convenience of using a full-sized desktop to perform remote assistance on a user’s mobile device. As an example, VMware AirWatch offers this through its Remote Management tool, and Microsoft Intune performs remote assistance through a TeamViewer plug-in.
VNC
For enterprises not wishing to use MDM remote assistance capabilities, Virtual Network Computing (VNC) is another option. Discussed in more detail in Chapter 5, VNC’s graphical desktop-sharing capabilities can work for mobile devices because it specializes in vendor neutrality. If we install mobile versions of VNC on mobile devices, we can either support those mobile devices remotely or use the mobile devices themselves to support other devices.
Screen Mirroring
Sometimes called “screen casting” or just “casting,” screen mirroring involves projecting a copy of a device’s screen contents over a network to another screen, such as a monitor, TV, or projector. For example, if you’ve ever wanted to cast your smartphone’s pictures or videos onto a TV to enlarge them, screen mirroring makes sense. As a general principle, technical support folks’ frown upon screen mirroring for troubleshooting end-user devices since there are a few hoops to jump through. Most support professionals would prefer a dedicated remote management tool instead.
Application, Content, and Data Management
MDM tools have other capabilities when it comes to managing and securing applications and data. They can control the deployment of applications to the mobile devices. Typically, the MDM pushes out the application to specific user or device groups, as defined in the MDM console. In the case of Microsoft Intune, user and device groups are created and populated in Microsoft Azure, with Microsoft Intune subsequently assigning applications to the groups. Using the MDM console, we can track a specific application deployment, discover which users have the application, and see if anyone had trouble receiving the application.
MDM products often have the ability to create application configuration policies that, assuming the application supports them, permit deployment of applications to include custom configurations and security options. If the application doesn’t support such policies, you may be able to use a software development kit to add support to the application. Also, based on application support, MDM tools often provide another feature called application protection policies, which create restrictions on what applications can do to corporate-owned data. Here are some examples:
• Prevent or limit applications from running on jailbroken or rooted devices.
• Prevent protected applications from copying data to unprotected applications.
• Prevent protected applications from executing other privileges on corporate data such as saving, e-mailing, and copying and pasting content.
• Require additional authentication requirements to access the application.
• Wipe out company data without affecting the application.
In addition to these policies and profiles, we can also create compliance policies and conditional access policies. Here’s a brief summary of each:
• Compliance policy Regardless of whether or not device configurations were implemented by a configuration profile, compliance policies ensure that configurations match their requirements. Compliance policies are often criteria for meeting a conditional access policy.
• Conditional access policy These policies stipulate that a user cannot connect to a certain application and its data unless the requirements of the conditional access policy are met. For example, the condition might be the device has to be compliant with the requirements of a compliance policy beforehand. Failing that requirement, the device will not be granted access to an application.
Over-the-Air Updates (Software/Firmware)
The term “over-the-air updates” refers to the centralized and wireless distribution of new software, firmware, certificates, and encryption keys to mobile devices. It may also be called “over-the-air programming” or “over-the-air provisioning” (OTAP). OTAP generally provides this wireless service via short message service (SMS) text messages. Once the OTAP message is sent to a device, the update process begins.
Remote Wiping
Remote wiping is the process of sending a signal to a remote device to erase specified data. This action may remove enterprise and personal data by factory-resetting the device. In other cases, only the enterprise data is wiped. Our remote wipe capabilities, and the circumstances warranting the remote wipe, help determine whether to wipe out all data or just enterprise data. As you might expect, remote wiping is typically performed through MDM tools. If a remote wipe is needed, the enterprise should send a remote backup signal to back the data up to a cloud computing provider. Upon completion, the data can then be wiped. Here are some conditions that warrant remote wiping:
• Employee loses device or has it stolen Since the employee still works for the company, organizations may want to back up enterprise and personal data to a cloud location so that both parties can regain access to it, and then send a factory-reset remote wipe signal to the device. If a stranger finds the device, no useful data remains.
• Employee resigns or is terminated Since the individual no longer works for the company, if the ex-employee still has a company device, or has enterprise data on a personal device, the organization will need to exercise a backup process to back up the enterprise data and then think carefully about how to do the remote wipe. Should they remote-wipe the entire device, including the ex-employee’s personal data, or just wipe out the enterprise data? Organizations are usually protected in all outcomes due to the ex-employee’s signed consent, but that doesn’t mean that enterprises should delete the individual’s personal data also.
SCEP
Simple Certificate Enrollment Protocol (SCEP) provides an easy process for network equipment, software, and mobile devices to enroll in digital certificates. The word “simple” in the SCEP acronym refers to the minimal intervention required by network administrators to provision SCEP enrollment services and for users to utilize it. You may recall earlier that one of the Microsoft Intune configuration profile choices was called “SCEP Certificate.” Figure 7-2 shows an example of an SCEP configuration profile being created.

Figure 7-2 Microsoft Intune SCEP Certificate profile
In many cases, an MDM platform will push out a pre-shared secret to the devices, which the devices use to submit a digital certificate request to a Certificate Authority (CA) server. Upon verification of the pre-shared secret, the CA issues a certificate to the requesting device. Another request method involves the requestor submitting a request to the CA, which requires a CA administrator to manually approve. Either way, once the requestor has a certificate, they are free to use it for authenticated and secured communications with other devices on the network.
One of the knocks on SCEP is an unauthorized user might use the pre-shared secret to request their own device to get a certificate. One way to counter this threat is to have different pre-shared secrets for different devices, as opposed to having one pre-shared secret for all of them.
BYOD
Bring your own device (BYOD) is the process of allowing employees to bring in their own personal devices, such as laptops, smartphones, and tablets, to work in order to access enterprise applications and data. This is one of the more polarizing topics in the modern IT era due to its fairly even split of advantages and disadvantages.
COPE
The opposite of BYOD, corporate-owned, personally enabled (COPE) occurs when the enterprise purchases and owns the device, yet provides it to users for both enterprise and personal usage. Although the user gets to enjoy the device for personal usage, MDM tools may require security configurations such as drive encryption and PINs as conditions for accessing corporate e-mail. Enterprises are sacrificing the cost savings of BYOD for increased control, security, and privacy benefits.
CYOD
Choose your own device (CYOD) is BYOD with a twist. Rather than allowing employees to bring whichever personal devices they want to work, the CYOD model only permits a limited selection of devices. For example, the enterprise may have only tested company applications and processes on the latest Apple iPhones and Samsung Galaxy S and Note series. As long as users bring one of those devices to work, they will be permitted enterprise access. Think of CYOD as looser than COPE but stricter than BYOD.
VPN
With mobile devices often used by teleworkers and telecommuters, employees will occasionally require secured remote access over the Internet to the enterprise environment. MDM tools can provide preconfigured VPN configuration profiles to enrolled devices to ensure their successful connectivity to enterprise VPNs. Here are some common settings that go into VPN configuration profiles:
• Connection name Example: Work VPN
• VPN server IP address or FQDN Example: 55.55.55.55
• Authentication method Example: username/password or certificates
• Connection type Example: Cisco AnyConnect, Check Point Capsule, SonicWall
Application Permissions
Since we discussed application management earlier in this chapter, we’ll take a different approach here. Much to our chagrin, most mobile applications on the Android, iOS, and Microsoft app stores will not work unless we grant various device permissions to them. These permission requirements may include access to the device’s camera, microphone, call logs, e-mail, SMS messages, location data, application list, and various others.
Although users generally have the first right of refusal, many users feel compelled to accept the permission requirements or forfeit all usage of the application. Although such forfeiture is likely, some software will work if you suppress certain permissions. Check your mobile device’s settings to see if you can individually suppress some application permissions. There are also third-party applications available that can help you with permissions management.
Side Loading
Mobile applications are typically downloaded and installed from official app stores such as the Android, iOS, and Microsoft stores. Since these applications are vetted by the app store vendor, they will be inherently trusted by the mobile device for installation. However, some applications will be developed in-house or acquired from a third-party website. In neither case are the applications available on the app stores, so your device’s OS will likely prohibit its installation.
On Android and Microsoft mobile devices, users can enable an OS configuration called side loading. Side loading is the process of installing applications from sources outside the official app stores. More often than not, this is necessary for when enterprises develop their own in-house applications. Keep in mind that side loading places the device at risk; therefore, only enable it if you have to.
Unsigned Apps/System Apps
Although the vendors of official app stores inspect applications before publishing them, an application’s developer is responsible for digitally signing the application. The purposes behind the digital signature are to allow us to verify the integrity of the application and to prove the software’s origin—which is generally the software publisher. Here are explanations of these goals:
• Integrity The application’s signature allows us to verify that the application is in its original and tamper-free condition. The developer runs the application through a cryptographic hashing function that produces a message digest value. This value is linked bit-for-bit to the application’s code. With this hash value attached to the application, if it passes our hash verification check, we can feel reasonably assured that the application has maintained integrity. Should the hashes not match, this results in an integrity violation.
• Nonrepudiation The application’s signature allows us to verify who signed the application and that the signer cannot deny having signed the application. In other words, it represents proof of the application’s origin. After the application developer produces the hash value for their application, they encrypt the hash value with their secret asymmetric private key. The outcome of this is called a digital signature. Should the receiver of the public key successfully decrypt the encrypted hash value, it proves that the owner of the private key signed the application—thus nonrepudiation has been achieved.
If digital signatures give us these assurances, the question becomes what should we do about unsigned applications? In some cases, nothing, since unsigned applications are not intrinsically harmful. Yet, certain enterprises automatically forbid the usage of unsigned applications—and for good reason. Whether it’s unsigned applications, e-mails, certificates, or device drivers, unsigned code could infect systems with malware.
System apps are tools and accessories that are built into mobile devices. Although these apps are not likely to be dangerous, they might exercise undesirable permissions on the device, plus chew up unnecessary storage. As they say, when it doubt, leave it out. Remove the applications if you can. Since mobile devices often makes this difficult or impossible by default, you may have to contact the mobile device or application vendor for further assistance.
Context-Aware Management
The “old way” of securing devices considered nothing but a user’s credentials and group membership. If those considerations were met, the user was granted access at all times. The “new way” of securing devices requires additional considerations before access is granted. To that end, context-aware management applies restrictive policies to mobile devices based on certain device conditions, like location and the time of day. Since mobile devices travel between hostile and non-hostile networks, or might be lost or stolen, credentials are no longer sufficient on their own. Device circumstances should be factored into authorization decisions since credentials can be compromised quite easily in many scenarios. This section goes over a few of those circumstances, including geolocation, geofencing, user behavior, and time-based restrictions.
Geolocation and Geofencing
A device’s location changes everything when it comes to its risks and threats; therefore, security controls must adapt to the device’s location “context.” As you’d expect, devices are considerably more secure within the enterprise environment than outside of it. However, we’ve benefited from decades of all enterprise devices being located at the enterprise. Laptops broke the mold by taking business productivity on the road, and then mobile and personal devices stretched it out further. Now, people and devices are everywhere. Many professionals work from home or travel to customer sites, while enjoying the hostile public Wi-Fi networks at coffee shops, hotels, and airports. Enterprises need to know where mobile equipment is located so they can track its usage as well as apply the right security controls at the right times.
Two location contexts that are frequently misunderstood or mistakenly used interchangeably are geolocation and geofencing. Although they aren’t the same, they are quite easy to grasp:
• Geolocation The process of identifying a device’s geographical location by using GPS or cell towers. Once a device is located, the enterprise can apply security controls on it such as geofencing, which is covered next.
• Geofencing The process of creating a logical or virtual boundary around a mobile device. A device’s security controls will adapt dynamically based on the device’s proximity to the geofence—which might encompass a single physical campus. Should a device leave the campus’s geofence, additional restrictions may apply to the device to protect its data.
User Behavior
In addition to device location, a user’s daily behavior with a device provides important contextual information when it comes to security. Like most people, employees follow a predictable routine with their devices. They use certain applications every day—one or two applications in particular—while ignoring most others. With this behavior exhibited and tracked over time, an MDM stores it as a baseline. If users deviate from the behavior by not using the usual applications—while accessing never-used applications—the MDM suspects the device has been accessed by an unauthorized individual. Therefore, security policies will immediately kick in to lock the device down.
Time-Based Restrictions
Time factors are increasingly used as criteria for device restrictions. Time-based restrictions apply certain security controls on a device based on what time it is. Historically, time restrictions were limited to logon hours. For example, a front desk administrator is permitted to log in between 7:00 A.M. and 4:00 P.M. Pacific Time. Prior to and after this logon period, the user cannot access anything on the network. By today’s standards, logon hours are too blunt an instrument and would benefit from a more surgical feature. The good news is MDM tools are generally quite capable of limiting access as opposed to outright denial, or additional authentication steps may be required for a user to be granted access at certain times.
Security Restrictions
The whole point of context-aware management is for security configurations to be adequate and adaptable to changing conditions. Restricting or limiting device functions isn’t difficult in itself. However, applying the appropriate amount of restriction, at the right time, while allowing your users to be perfectly productive—there lies the rub.
Security Implications/Privacy Concerns
If you ask enterprises why they prohibit personal devices from accessing enterprise resources, security and privacy issues always come up. Many of these enterprises might change their tune if they learned how powerful cloud-based MDM solutions are today. Armed with these new and improved technologies, enterprises can reasonably solve security and privacy concerns. All it takes is the right tools, strategies, and people to make it happen. In this section, we cover a mix of security and privacy concerns, plus their associated mitigations.
Data Storage
The next several topics center around data storage. Given the ubiquity of mobile devices, coupled with the coexistence of enterprise and personal data, mobile data storage security takes on a greater urgency. There are different types of mobile data storage options to consider, and we need to understand each of their security considerations. These storage options range from nonremovable and removable storage, to cloud-based and even uncontrolled storage. Let’s start off with nonremovable storage.
Nonremovable Storage
Nonremovable storage is built into mobile devices such as smartphones and tablets, and cannot be removed or altered. Today’s mobile devices typically ship with 32GB, 64GB, or 128GB storage sizes, with even higher options available. If the device ships with 64GB of internal storage, that is all the internal storage the device will ever have. This storage typically houses the most important content, such as the OS, pre-installed applications, and other system software. If it’s supported, you should enable drive encryption. Today’s drive encryption options are almost always going to utilize the Advanced Encryption Standard (AES) cipher, which is the gold standard in symmetric encryption.
Removable Storage
Removable storage refers to the external storage cards that can be added or replaced in a mobile device to increase the available storage. Various forms of secure digital (SD) cards are used, with microSD being one of the more popular formats. If you were to add a 512-GB microSD card to a Samsung Galaxy Note 9, this 512 GB of storage will be in addition to the 512 GB of internal/nonremovable storage that the device comes with. Drive encryption and password protection are the most common security options available for removable storage. You can also train users to avoid storing sensitive materials on the removable storage, unless it cannot be avoided.
Cloud Storage
Although the options and storage capacity can vary widely, cloud storage is often used for backing up a mobile device’s settings, application data, photos and videos, purchase history, and other items. This is helpful not only for backup purposes but also to compensate for any lack of storage or storage options in the mobile device itself. Many smartphones are sold with free cloud storage accounts specifically for this reason. Be mindful of the fact that cloud providers will limit what types of data you can store in the cloud. Popular examples of cloud storage include Apple’s iCloud, Google Drive, and Microsoft OneDrive.
Typically, when users store content on a mobile device, it automatically synchronizes with the cloud storage provider. Try to figure out if the synchronization process uses encryption, and if the data stored in the cloud is also encrypted. Also, try to resist having the synchronization pre-authenticated because a lost or stolen device will make it easy for the other party to access the cloud account.
Transfer/Backup Data to Uncontrolled Storage
Frequently, devices back up their data to public or free cloud-based accounts. Products such as Microsoft OneDrive, Google Drive, and Dropbox provide free cloud storage services. Although you’ll receive basic services such as some free storage, file management, recycle bin, content sharing, and basic file versioning, you don’t get much “control” over the actual storage. Drive failures, backup and restoration, drive encryption, file system permissions, server hardening, and so on are all handled by the cloud provider. Unless you subscribe all the way up to Microsoft Azure or Amazon Web Services (AWS) cloud storage solutions, there’s not much you can do about the lack of control outside of keeping your sensitive data off of the cloud or buffering the cloud with on-premises storage.
USB OTG
Most people think of the USB port on their smartphone or tablet as strictly for charging or data transfer purposes. Much to the surprise of many, today’s smartphones and tablets often support USB On-the-Go (OTG), which is an older standard that permits USB devices to “host” other USB devices. When smartphones or tablets connect to other USB devices, those devices are now being hosted by the smart device. Shown next are the devices that can plug into a smart device for additional interactive features:
• Cellular adapters
• Charge other smartphones
• Digital cameras
• Flash drives
• Game controllers
• Keyboards
• Local area network adapters
• Mice
• Musical equipment
• Printers
In reference to these items, the smartphone or tablet would act as the “master” device, and the flash drive would act as the “slave” device. Due to USB OTG’s device-to-device data transferring capabilities, malware may be transferred between two smart devices, or between a flash drive and a smartphone. Physical restrictions of peripheral connections to smart devices, in addition to intelligent monitoring tools, are the best security countermeasures.
Device Loss/Theft
Mobile devices, particularly smartphones, are prone to being forgotten or stolen. Businesses have to plan for mobile devices eventually falling into unauthorized hands. When a device loss incident occurs, the enterprise will be best served by implementing the following security practices:
• GPS/cell tower tracking To possibly locate and recover the device
• Drive encryption with PIN protection To prevent access to the device
• Biometric authentication To prevent access to the device
• Remote data backup to cloud To recover data from the device prior to remote wiping
• Remote wipe To remove the data before the unauthorized user gets ahold of it
Hardware Anti-Tampering
Hardware anti-tampering technologies resist deliberate attempts at causing disruption to or malfunction of a device. Examples of hardware that contain anti-tampering capabilities are secure crytoprocessors such as smart cards, TPM chips, and hardware security modules (HSMs). These chips both contain sensitive information and have access to sensitive information located elsewhere; therefore, they resist tampering by only permitting internal software functions to access sensitive information. In other words, we cannot access the sensitive information (such as built-in private keys) through external means. Some tamper-resistant chips will go as far as “self-destructing,” as in zeroing out the data, should sufficient tampering activities be detected.
eFuse
A common example of hardware tampering takes place whenever hackers try to revert a device’s firmware to an earlier version. Earlier versions of firmware have vulnerabilities that can be exploited. To the rescue is an IBM-invented technology called eFuse, which supports the reprogramming of a computer chip’s programming. Akin to a circuit tripping whenever you plug in a hair dryer too powerful for an outlet, eFuse will “trip” the attempt at downgrading the firmware to a previous version. eFuse has an elaborate built-in tracking mechanism to help it determine forward firmware upgrades versus backward downgrades. Although designed for other purposes, eFuse can be used for hardware anti-tampering capabilities.
TPM
Trusted Platform Module (TPM) chips were covered extensively in Chapter 6, in the section on boot loader protections. As it relates to mobile devices, TPM chips serve much the same purposes as they would with their larger PC and laptop brethren. The TPM 2.0 mobile reference architecture explains how TPM 2.0 chips can be implemented in mobile devices to address various security challenges.
Rooting and Jailbreaking
Although most technicians probably won’t correct you for using “rooting” and “jailbreaking” interchangeably, these two terms are actually quite different. Not only do they apply to different OSs, but they’re also different in their respective outcomes. We’ll get into more detail next, but basically rooting achieves a deeper level of privilege escalation on Android devices than jailbreaking does for iOS devices.
Jailbreaking refers to the process of removing certain security restrictions from iOS devices such as iPhones and iPads. Jailbreaking involves installing iOS kernel patches to escalate the user’s privileges on the device. By jailbreaking, users will be able to download third-party software from outside the official Apple App Store, in addition to adding third-party extensions and themes. In other words, jailbreaking enables the type of software installations that we talked about earlier, called side loading. Since jailbreaking loosens the restrictions on software installation, malware is more likely to get into the device. To get a fuller grasp of the risk factors brought about by jailbreaking, here is the official list from Apple’s support website:
• Security vulnerabilities
• Instability
• Shortened battery life
• Unreliable voice and data
• Disruption of services
• Inability to apply future software updates
Unlike jailbreaking, rooting grants actual root-level privileges to the Android OS. Since Android is a Linux-based distribution, Android is an open source OS, unlike iOS, which is closed source. As a result, rooting an Android device grants the user complete control over the device. Rooting can even allow the user to remove the OS entirely and replace it with a new one. Rooting also permits CPU overclocking, memory flashing, new OS GUI skins, and easier removal of built-in software. As with jailbreaking Apple devices, rooting will likely result in the Android device’s warranty being voided, in addition to many of the additional security and device issues discussed with jailbreaking. Therefore, jailbreaking and rooting are not recommended practices.
Enterprises are combating jailbreaking and rooting concerns through security policies and training. If people jailbreak or root company devices, or use jailbroken or rooted personal devices to access corporate resources, disciplinary action may result, which can include employee termination. Organizations will need to raise awareness about the negative security effects that can result from jailbreaking or rooting devices.
Push Notification Services
Push notifications are important messages sent to mobile devices by an application publisher or an enterprise MDM system. An application publisher’s notification can range from sports scores and news updates to weather and environment alerts. In some cases, push notifications may even be sent by governments. On the other hand, MDM tools will deliver messages generated by enterprise administrators, which may contain warnings about a current security threat or a recommended action for users to take.
For maximum deliverability, push notifications are often sent using firewall and device-friendly protocols such as SSL/TSL. This ensures that the message makes it through and maintains integrity and a verifiable delivery origin for trust purposes.
Geotagging
Geotagging is the process of attaching geographically related information to common media types such as pictures, videos, SMS messages, and even websites. Since geotagging is largely about location, much of the geotagging attributes relate to the location of something. The following are some examples of geotagging properties for a photo:
• Business name and address
• Latitude and longitude coordinates
• Altitude
• Timestamp
Geotagging is also commonly used by hikers to track the route they’ve taken through a mountainous area—which can also assist others in locating the hikers should they get lost.
Social media applications like Facebook and Instagram make frequent use of geotagging software like Foursquare. Foursquare users often tag some data and then publish it to popular social media platforms for all their friends to see. The security consequences of this are enormous. Attackers on social media sites may observe your geotagging data to determine your current whereabouts. If it says, “John Smith has checked into JFK airport,” a social media attacker might use this as a window of opportunity to burglarize your home.
It is recommended that unless absolutely necessary, geotagging should be disabled on smartphones and on social media websites.
Encrypted Instant Messaging Apps
Enterprise workers frequently turn to real-time messaging services such as SMS texting and instant messaging (IM) for communication. Many IM tools such as Facebook Messenger, WhatsApp, Skype, Google Allo, and Signal support a protocol called Signal Protocol. Developed by Open Whisper Systems in 2013, Signal Protocol (formerly known as TextSecure) provides encryption capabilities for IM, voice, and video calls. Signal Protocol also provides authentication, perfect forward secrecy (PFS), and nonrepudiation services. It is important to add encryption support to IM conversations due to the sensitivity of information that may be transmitted—and subsequently captured by packet sniffers.
Tokenization
Imagine if you could buy something from Target by using your mobile device’s stored credit card, but you pay using a substituted number as opposed to the actual credit card number? Welcome to the clever payment security feature that is tokenization. Tokenization is the process of using a non-sensitive value (token) as a substitute for the original sensitive value (credit card number). The token, which is randomly generated by a tokenization system, is mapped to the credit card number. Tokenization significantly reduces the risks involved in utilizing mobile payment options.
OEM/Carrier Android Fragmentation
Ironically, the overwhelming global success of the Google Android OS has contributed to, arguably, its most consistent criticism—Android fragmentation. Android fragmentation refers to the wide disparity of active Android OS versions still in use due to many older Android devices being prevented by Google from updating to the latest Android version. According to StatCounter, as of December 2018, here is the global market share percentage breakdown of different Android versions:
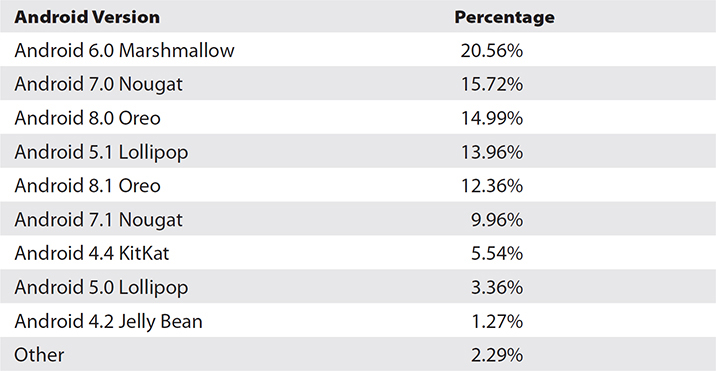
For those not counting, that is at least 10 different Android versions actively used in the global market. The primary reason for this is that Android manufacturers (and Google) aren’t going to make as much money if everyone can use the same smartphones and tablets forever; therefore, people are incentivized to get new smart devices in order to get the newest version of Android. Apple also blocks iOS upgrades on older iPhones and iPads for the same reasons, yet they don’t suffer nearly the same degree of fragmentation as Android since Apple is the only company that makes both Apple devices and the iOS operating system.
Mobile Payment
What was pure sacrilege just a few years ago has now become trendy, even commonplace—people submitting mobile payments via smartphones and smart watches. Admittedly, many people use mobile payment because it’s trendy, but there are practical advantages also, as listed next:
• People who use mobile payment report it to be more convenient than using cards or cash.
• Lines are statistically shorter in stores that support them.
• It is more secure than cash or credit/debit payments because actual financial details don’t have to be transmitted between the mobile device and payment machine.
• It reduces payment machine expenses for merchants.
• It integrates a company’s loyalty and reward programs into the mobile payment application.
• It leaves a data trail (much like a website cookie), which can be utilized by an organization to optimize inventories, learn customer payment patterns, and glean product interests, which leads to improved personalization of products and customer service.
If only it were that simple. Mobile payment has both positives and negatives. We’ll dive into the details in the upcoming sections on NFC-enabled transactions, inductance-enabled transactions, mobile wallets, and peripheral-enabled readers.
NFC-Enabled Transactions
Various mobile payment applications such as Android Pay, Apple Pay, Samsung Pay, Visa PayWave, and MasterCard PayPass support NFC payments. NFC payments are common because they are “contactless” and secure. They are contactless because the payment transactions are transmitted wirelessly without physical contact between mobile devices and the retailer’s payment machine. They are secure for a few reasons:
• Extremely limited range of NFC signals—which is about four centimeters.
• Encrypted channels are established between mobile devices and payment machines.
• NFC chips are only engaged during the few seconds of the financial transaction. The attacker would not be able to do anything if the phone is locked or not in use.
These security benefits don’t make NFC unhackable, however, because nothing ever is that secure. NFC communications can suffer from deliberate interference from the attacker, payments theoretically can be intercepted, and devices can be stolen. Malware may be present on the mobile device, which can extract mobile payment details. Therefore, be sure to run antimalware scans and remove undesirable applications. Despite these risk factors, NFC can be thought of as, overall, a secure form of mobile payment.
Inductance-Enabled Transactions
Mobile devices that have NFC antennas are inductance-enabled devices. NFC antennas use inductance, which is achieved by a wrapped coil of wire, to generate a very small magnetic field on the order of centimeters. Through this small magnetic field, a wireless connection can be established between mobile devices and payment machines.
Mobile Wallets
Mobile wallets are “virtual” wallets that store payment card information on mobile devices. Instead of carrying credit or debit cards in your wallet or purse, you can simply carry your smartphone or wear a smart watch, and use the mobile wallets stored on the devices. We discussed several mobile wallet technologies in the previous section on NFC, and we already discussed the tokenization process of transmitting tokens instead of the actual payment card information via the NFC channel. We also discussed the inherent risk factors of NFC, which are also equally attached to mobile wallets as well. The long and the short of it: mobile wallets offer multiple benefits over physical wallets.
Peripheral-Enabled Payments (Credit Card Readers)
If you’ve ever gone to that little mobile screen repair hut at the mall, or ordered pizza for delivery, you may have noticed a new payment trend involving credit card readers being physically attached to smartphones and tablets. The merchant downloads and registers a certain payment application, and then they attach the credit card reader device to their smartphone or tablet, and instantly they’ve turned their smart device into a “portable register.” Needless to say, this creates convenient payment opportunities for both buyers and sellers because credit card transactions can take place practically anywhere.
Tethering
Tethering is the process of sharing a wireless Internet connection to other devices via the Wi-Fi, USB, or Bluetooth protocols. Laptops and tablet devices frequently find themselves in situations where no public Wi-Fi hotspots or private Wi-Fi networks are available, yet they still require Internet. Most 3G/4G-enabled smartphones have an option to turn on a mobile hotspot capability so that nearby wireless devices can use either Wi-Fi, Bluetooth, or a USB cable to connect to the smartphone—which “tethers” those devices to the smartphone. The smartphone will then pass the device’s connections through to the Internet using the smartphone’s 3G/4G cellular capabilities. Since Wi-Fi is the most common and readily understood option, the subsequent sections focus on the less common tethering options, such as USB and Bluetooth.
USB
Although not the most common tethering option due to its lack of convenience, USB tethering has two things going for it. One, it’ll work in the extremely unlikely scenario that another wireless device doesn’t support either Wi-Fi or Bluetooth. Two, and far more likely, the user wants the network security that only a cable can bring.
Spectrum Management
In the context of tethering, spectrum management is the process of ensuring that cellular radio-based data transmissions don’t overly consume the radio frequency spectrum. We’re not so worried about Wi-Fi and Bluetooth because they use short-range radio waves. Smartphones, on the other hand, use the longer range 3G/4G-based cellular radio signals that can clutter up and create interference with devices across a much broader geographical area than mere Wi-Fi and Bluetooth can.
So, what does this have to do with tethering? By tethering multiple devices to a smartphone’s individual mobile hotspot, the one smartphone transmits its 4G signal to the Internet. Meanwhile, the other tethered devices are sticking with their Wi-Fi or Bluetooth signals as they communicate with the smartphone. Instead of having dozens or hundreds of devices generating 4G radio traffic, you have only a handful of smartphone hotspots generating the traffic. This helps minimize the long-range interference and clutter in a given geographical area—hence, the spectrum is being managed.
Bluetooth 3.0 vs. 4.1
Bluetooth tethering is not as common as Wi-Fi due to, historically speaking, its hit-or-miss support, limited range, limited performance, non-optimized power consumption, and interference with the smartphone’s cellular signals. Luckily, recent advances with the Bluetooth protocols have addressed these concerns, thereby making Bluetooth a viable replacement for Wi-Fi-based tethering. The following list shows the evolution of Bluetooth as it relates to tethering:
• Bluetooth 3.0 Improved power conservation, plus transmission speeds reached a theoretical 24 Mbps.
• Bluetooth 4.0 New low-energy feature supports minimal power output while retaining good range.
• Bluetooth 4.1 Interferes less with 4G LTE.
Authentication
As with desktops, servers, and laptops, authentication methods are needed when accessing mobile devices. Today’s mobile devices have multiple authentication methods to choose from, including swipe patterns, gestures, PINs, and biometrics. In this section, we explore each of these authentication options.
Swipe Patterns
Swipe patterns typically involve a user tracing their finger across a series of dots in a specified order. Although this is more secure than simply swiping your finger vertically or horizontally in one direction to unlock your screen, it doesn’t offer much more security than preventing “pocket dialing,” which occurs when you inadvertently call someone while the phone is in your pocket. Otherwise, hackers will either guess your swipe pattern or they’ll watch you enter it from afar.
Gestures
Gestures are basically a better version of swipe patterns. With gestures, a more complex series of finger motions are performed on the screen, typically on a chosen photo—hence, the alternate name of this authentication method being “picture passwords.” Gestures may include drawing a line between two objects within the picture, drawing a circle around an object in the picture, double-tapping an area, or pressing and holding another area. With many picture passwords, three unique and correct gestures are required to unlock a device.
Similar to swipe patterns, gestures can also be compromised through brute-force/guessing attacks, or the attacker can simply watch you perform the gestures and commits them to memory.
PIN Codes
PIN codes are generally preferred over swipe patterns and gestures because they are computationally more complex. They are much like a regular password, except you’re limited to just numbers. If available, choose a six-digit PIN versus a four-digit PIN to make brute-force attacks more difficult. Like swipe patterns and gestures, PIN codes are also susceptible to shoulder surfing, key loggers, and social engineering; therefore, it is highly recommended that you complement PIN codes with biometrics (multifactor authentication), which we discuss in the next section.
Biometrics
Swipe patterns, gestures, and PIN codes all have one thing in common—they are something you know. Things that are known to you can be known to others as well. As such, they are not strong authentication methods by themselves.
Biometrics, or “something you are,” rely on a human’s biological characteristics, such as fingerprints, retina scans, iris scans, and facial recognition scans. Unlike the “something you know” methods discussed earlier, a person’s fingerprint is uniquely their own and, as such, is difficult for someone else to replicate. Keep in mind that authentication is only considered strong if the method makes it difficult for someone else to impersonate you. Also, if you use fingerprint readers, you’re not likely to “forget” your finger at home. On the flipside, PIN codes can be mentally forgotten and smart cards can be left at home. The convenience, availability, and uniqueness of biometric authentication methods make them a strong option, which is why many modern smartphones have built-in fingerprint and iris scanners.
Facial Scans If supported by a mobile device, this scan records facial features such as the nose, chin, forehead, and the contours of eye sockets. Facial recognition may experience challenges handling lighting changes, facial expression changes, and facial hair or makeup changes. It may even have difficulties handling identical twins.
Fingerprint Scans Very commonly supported by mobile devices, fingerprint scans capture the impression from the ridges of a person’s finger. Fingerprints are generally more accurate than facial scans since fingers don’t change all that much; meanwhile, faces can be modified in many ways. Yet, fingerprint scanning is falling out of favor due to more hygienic, accurate, and convenient methods such as iris scans.
Iris Scans Increasingly common with mobile devices such as the newest Samsung Galaxy and iPhone X devices, this scan type identifies the colored ring-shaped portion surrounding the pupil of the eye. This is considered the most accurate biometric method due to the iris being internal, being randomly generated during early human development, producing minimal false-positives (authenticating the wrong person), and minimal false-negatives (not authenticating the right person). It’s also compatible with certain eyewear like contacts and glasses, unlike retinal scans.
Malware
Much to the surprise of many users, mobile devices not only get malware, but a ton of it. This really shouldn’t surprise anyone because malware developers have always targeted the popular products, and mobile devices are the most popular computing product in the world. The good news is, mobile devices are inherently more resistant to malware than PCs since mobile OSs place users behind restricted sandboxes (hence where all the prickly jailbreaking and rooting take place). Here are some antimalware recommendations to consider:
• Install and update antimalware software.
• Run antimalware scans frequently.
• Prohibit jailbreaking and rooting of devices.
• Download the latest firmware/OS updates.
• Avoid websites with malicious content.
• Avoid side-loading/third-party software installations unless absolutely necessary.
Unauthorized Domain Bridging
Most enterprise laptops have two network adapters—one Ethernet and the other Wi-Fi. Unbeknownst to enterprise staff, that laptop might be simultaneously connected to both the enterprise wired network and their public Wi-Fi hotspot network. Trouble arises when the Wi-Fi hotspot extends outside into the parking lot and next door to another organization.
Unauthorized domain bridging occurs when unauthorized Wi-Fi users connect through the dual-network-connected employee to reach the corporate wired network. This dual-network-connected employee acts as a “bridge” between the Wi-Fi and the corporate wired network. Operating systems can be configured to prevent network bridging.
Baseband Radio/SoC
Baseband processors, also known as baseband system on a chip (SoC), are hybrid CPU/RAM/firmware chips on mobile devices that handle their cellular radio communications. The good news is, they are not the most frequently attacked chips in the world; however, their proprietary nature makes them difficult to perform security assessments on to determine vulnerabilities and subsequent mitigations. Reverse engineering efforts have discovered that baseband processors may be vulnerable to backdoor attacks.
Augmented Reality
Unlike virtual reality, which completely replaces your real-world perception with a digital one, augmented reality merely adds digital enhancements to your real-world perception. Augmented reality technology enhances or “augments” your real world by adding auditory, visual, haptic, and other digital sensory elements so that it feels like new environmental elements have been physically added into your current space.
From a security perspective, augmented reality devices are constantly scanning the physical environment and “taking notes.” They don’t simply add stuff to your real-world experience; they’re also extracting information from it. For example, if you’re walking around and you look at someone, the augmented reality device can immediately pull up publicly available information about that individual. The fact that publicly available information is so quickly accessible for augmented reality devices is understandably bothersome to some.
SMS/MMS/Messaging
Short message service (SMS) is frequently used by mobile devices to deliver text messages over mobile networks like Verizon, AT&T, and T-Mobile. Encryption is supported by certain carriers but is typically not enabled. On the other hand, multimedia messaging service (MMS) is enhanced to support not only texting but also pictures and videos. Due to SMS/MMS typically lacking encryption, SMS/MMS conversations are highly vulnerable to eavesdropping and spoofing attacks.
To combat the encryption challenges, many are turning to IM tools like Facebook Messenger, WhatsApp, and Signal for their encryption capabilities.
Wearable Technology
As if mobile devices weren’t enough, now we’re wearing them! Wearable technology refers to smart devices that are either worn or implanted into the body. Wearable devices such as watches, fitness bands, and headsets are all the rage today. However, having these intelligent devices worn on our bodies should raise some questions as to what information, if any, they are collecting. Who is the information being shared with? Are others, unbeknownst to us, illegally capturing our information wirelessly? We briefly discuss several wearable devices in the following sections while factoring in basic features and any relevant security and privacy concerns.
Cameras
Cameras often serve as wearable technology for law enforcement, who often wear body cameras on their helmets, glasses, or torsos in order to record the events in which officers are involved. Unfortunately, attackers employ this technology for nefarious reasons—committing crimes, performing unauthorized surveillance, data theft, and information reconnaissance. There are also potential legal issues regarding consent (or the lack thereof), search and seizure considerations, and facial recognition risks.
Watches
Typically referred to as smart watches, these are mobile computing devices that we wear on our wrists like a watch. More like a smartphone than a watch, smart watches are touch screen devices that run a mobile-based operating system like Apple’s Watch OS or Google’s Wear OS, and typically support numerous capabilities, such as the following:
• Address book
• Alarms
• Calculator
• Calendar
• Caller ID
• Camera
• Clock
• Dial and answer function
• Heart and sleep monitor
• Music player
• Panic mode
• Recording
• SMS notifications
• Stand up reminders
Since smart watches often have built-in Wi-Fi and Bluetooth, security and privacy issues are inevitable. Bluetooth may allow an unauthorized device to pair with the smart watch, which can lead to stolen e-mails and address book entries. The risk is amplified if the watch has built-in 4G capabilities since the range far exceeds that of Bluetooth. Also, the data synchronization between smartphones and smart watches is not likely to be encrypted. If smart watches provide any built-in data security controls, be sure to implement them.
Fitness Devices
Unlike smart watches, fitness devices—often referred to as fitness bands—specialize in tracking physical fitness data points such as number of steps taken or climbed, number of minutes of exercise, walking speed, heart rate, and even caloric intake. They are worn like a smart watch and include basic watch functions, but will not have the other smart capabilities inherent in smart watches.
Glasses
In a way representing today’s version of bifocals, smart glasses are digitally enhanced glasses that contain an extra lens for augmenting your environment with helpful digital information. You can look through the normal lens as you would with glasses, or engage the digital lens area to see additional information such as contacts, messages, weather information, and people and landmark data. This has exciting applications for many industries due to its ability to immediately record information, display or deliver video streams between users, real-time translation, navigation and location benefits, inventory management, and more. Law enforcement officers are increasingly using them as body cameras. Plus there are the tremendous benefits already being experienced in the healthcare industry due to picture and video capabilities, data synchronization with other devices, consultation benefits, and more.
Privacy concerns are rampant, particularly regarding facial recognition. People are rightfully concerned that people wearing smart glasses will immediately be able to look at someone and download all their public information without their consent or knowledge. There are also concerns about people recording the visual and auditory components of random or private conversations.
Medical Sensors/Devices
Whereas fitness devices are great for basic health and health monitoring, medical devices are network-connected devices whose sensors are able to capture more advanced medical data, such as the following:
• Blood pressure
• Brain activity
• Glucose
• Hydration
• Motion
• Orientation
• Oxygen level
• Pulse/EKG
• Respiration
• Temperature
• Weight
Perhaps best part of all, due to their network connectivity, medical wearables are able to alert helpers during emergency circumstances.
Headsets
Headsets are generally the least technologically advanced wearable on this list since they largely include only a microphone and speakers for voice conversations. They may support Bluetooth wireless, voice activation, simulated surround-sound capability, and noise cancellation, and they may be waterproof and vibrate for a more immersive gaming experience. The most likely security issue arises from unauthorized voice recording software on the mobile device, computer, or telephone system.
Security Implications
As indicated throughout this section, wearable technologies are not without security risks. In this section we cover several security implications, including remote activation or deactivation of features, cryptography concerns, reconnaissance, data theft, privacy, and forensics.
Unauthorized Remote Activation/Deactivation of Devices or Features
Wearable technologies are often vulnerable due to their reliance on Bluetooth for paired-device communications. If a smart watch has its Bluetooth discovery and pairing options enabled, attackers might be able to illegitimately pair with the smart watch to steal data at rest and intercept data in transit. Worse, attackers may remotely deactivate sensors on medical devices, which can disrupt critical communications between patients and healthcare providers. If possible, disable discovery and pairing options after all required pairings have taken place. If available, firmware updates can also resolve certain wireless security vulnerabilities.
Encrypted and Unencrypted Communication Concerns
We touched on this a little bit earlier, and the news isn’t going to get a whole lot better. What is apparent not just with wearables, but with IoT in general, is that much of this stuff is just not designed with security in mind. They’re designed to have useful features and be easy to use. The odds are slim that ordinary wearables are going to support encryption capabilities. If they do, you should enable encryption, particularly on smart watch, smart glasses, and medical device communications. If wearables don’t support encryption, consider either not using the wearables or limiting their usage to certain job roles and environments to minimize data breaches.
Physical Reconnaissance
Physical reconnaissance occurs when attackers use wearable technology to gather information about an environment or its people. Body cameras can work but lack the discretion to be proper physical reconnaissance devices. For reconnaissance to be effective, the attacker’s wearables should blend in and not draw any attention to the attacker. Smart glasses are perfect for this, particularly since they have evolved to the point of looking like normal glasses. Attackers are using smart glasses to collect information about the people in a room, the devices they’re using, gestures on devices, PIN code combinations on devices and doors, and so on. Attackers can just record everything in the room and then replay the entire feed at a later time.
Users will need to exercise discretion themselves when they are performing gestures on devices or entering in PIN codes. Perhaps they can use one hand to cover the other, the screen, or the authentication inputs so attackers can’t witness their gestures from afar.
Personal Data Theft
Although the lack of encryption creates a data-in-transit issue, what about data at rest on the devices? Attackers may be able to remotely pair with a device and extract the data. Worse, if they steal the data, what can you do about it? In the unlikely event that remote backup and remote wipe features are available, you can engage them immediately. If drive encryption is enabled, implement that in advance. Otherwise, continue to be mindful of Bluetooth discovery and pairing modes, and check to make sure no unauthorized devices are listed as paired with your device. Every once in a while, back up your data and factory-reset your device to clean it out of any unauthorized software or malware.
Health Privacy
Fitness devices, particularly medical devices, generate, store, and transmit a lot of electronic health information about their owners. Hospitals, hospices, and retirement/nursery homes are the most likely candidates to use such medical devices. These organizations live and breath by the decrees of HIPAA, and if HIPAA requires specific security and privacy controls for the protection of a patient’s physical and electronic health records, we must ensure that wearables do that to the extent possible. If possible, use wearable technologies that offer encryption of data in transit and at rest. Also, limit sharing of electronic health information with other users and devices, unless sharing is compelled by job requirements or law. The key with HIPAA is to not allow unauthorized use, storage, transmission, and disclosure of medical information under any circumstances. As discussed earlier in this book, HIPAA fines can be quite painful.
Digital Forensics of Collected Data
Digital forensics is the practice of collecting, preserving, and analyzing digital evidence in order to understand all aspects of a digital crime. Typically, digital forensic processes are implemented on consistent technology types, such as computers, smartphones, tablets, fax machines, printers, and so forth. Wearable technologies are a different story in that they are quite new, lack standardization, and are subject to various operating system and software adaptations, which can create compatibility issues with digital forensic toolkits.
Here is a list of data that can be forensically collected from certain wearable devices:
• Audio
• Connected devices
• Contacts
• Messaging interactions
• Locations and destinations
• Phone calls
• Photos
• Search history
• Social media activity
• Sync information
• Videos
• Web browsing history
If you fulfill a forensic-type role in your enterprise, consider researching the market on forensic toolkits that support the types of wearables your users have.
Chapter Review
In this chapter, we talked about integrating security controls into mobile and small form factor devices to meet enterprise security requirements. We began by talking about enterprise mobility management, which focuses on mobile device management tools, their capabilities, and the mobile devices they manage. The first topic of the mobile device management section was containerization, which provides a means of locking corporate data into an isolated encrypted space to allow management of the container without affecting the personal data. The next topic talked about MDM configuration profiles for mobile devices and the specific configuration payloads specified in the profiles. Profiles and payloads are the primary mobile device management configuration features. We then talked about personally owned, corporate-enabled device scenarios, where people are bringing their devices to work to be onboarded by the enterprise for a managed mobile computing experience. The next topic was application wrapping, which involves MDM tools adding “wrappers” to deployed applications in order to add additional security features to them that are otherwise not included with the applications themselves. Remote assistance techniques such as VNC and screen mirroring were covered next. Remote assistance tools like VNC allow IT and security staff to remotely assist users with various type types of devices, including mobile devices. Screen mirroring allows a user to “cast” their screen content to an IT professional’s screen for support purposes.
After remote assistance, we went into application, content, and data management techniques in which MDM tools deploy mobile applications to devices, which are then protected through application configuration policies and application protection policies. This is largely about limiting the privileges that applications have with enterprise data. We also went into compliance policies and conditional access policies to ensure that user devices are configured to a required standard in order to grant them access to enterprise resources. Next, we covered over-the-air updates regarding software and firmware. Mobile devices, being wireless, can receive application or firmware updates via a centralized MDM tool to ensure compliance with security requirements. The next topic on remote wiping discussed how data on lost or stolen devices can be remotely deleted to protect the data from falling into unauthorized hands. We talked about SCEP, which simplifies the process of network and mobile devices requesting and receiving certificates from Certificate Authority (CA) servers. After that, we talked about BYOD and the various positives and negatives of bringing your own devices to work. After BYOD was COPE, which reverses BYOD by having enterprises purchase the device for users but enabling them for personal usage. We then added coverage of CYOD, which empowers users to choose and bring their own devices to work, but for the device to connect to the enterprise data it must be a pre-approved device for the sake of standardization and management.
The next covered topic was VPN. We discussed the different tunneling, encryption, and authentication protocols available for connecting to work networks remotely and securely. Next up was application permissions, which centralize on the device permissions mobile applications require as a condition for running on mobile devices. Then we went into side loading, which permits the installation of third-party software from outside official app stores if the appropriate settings are enabled on the mobile OS. Related to side loading is the concept of unsigned applications and system applications. It is not recommended that you side-load unsigned applications; therefore, procedures exist to generate a digital signature for an application. Context-aware management goes beyond automatic authorization after authentication by requiring that a user’s device, time, location, and behaviors comply with appropriate conditions or “contexts” prior to resource access being authorized.
The next section began a new category of topics focusing on security implications and privacy concerns—the first of which was the data storage topic of nonremovable storage. We talked about removable storage and recommendations on what data to put on it, data backup and recovery options, plus encryption. Next was cloud computing storage, with suggestions regarding permissions, sharing, authentication, and using business-orientated cloud storage providers as opposed to free ones. After that we talked about transferring or backing up data to uncontrolled storage locations. We recommended using a higher-end cloud service such as Microsoft Azure or Amazon AWS to receive more control over your storage than a public service like OneDrive or Dropbox. Then we talked about USB OTG, which involves attaching external peripherals to USB mobile devices, including cameras, flash drives, keyboards, or gaming controllers to gain additional features on mobile devices. The next topic was device loss or theft and the various countermeasures we can employ to combat it, including device tracking, encryption, biometrics, remote backup, and remote wiping. We talked about hardware anti-tampering crytoprocessors such as smart cards, TPMs, and HSMs. We also talked about the eFuse anti-tampering technology, which trips a mobile device if a hacker attempts to downgrade the firmware to a previous version.
We revisited TPMs and their key generation and key storage benefits briefly since they were covered in a previous chapter. We followed this up with risky privilege escalation techniques called rooting and jailbreaking, which apply to Android and iOS devices, respectively. Push notification services help protect mobile devices by sending warnings straight to people’s devices about security threats or pending updates. Geotagging was also discussed—in particular, how tagging our pictures and videos with geographical metadata and then putting it on social media networks is a risky practice. We discussed using encrypted instant messaging apps like Facebook Messenger and WhatsApp to substitute for the lack of encryption supported by most mainstream IM applications. Tokenization was covered to go over the process of mobile devices using substituted numbers (tokens) as opposed to actual payment information to pay for things using mobile devices. The next topic was OEM/carrier Android fragmentation, which dealt with the overwhelming popularity of Android but also the 10+ different versions of Android still running in the market, which harms Android’s security and support capabilities. We switched gears to talk about various mobile payment options, including the typical NFC-enabled mobile payment transfers, which use coiled wires to generate the inductance needed to generate and transmit the wireless signal. We ended that topic by talking about peripheral-enabled payments with credit card readers. In other words, people are attaching credit card readers directly to their smartphones to enable payment with credit cards anywhere.
The next subject was tethering, which involves a mobile device setting up a public Wi-Fi hotspot to allow other devices to access the Internet through the wireless host. USB tethering is supported in case you want a more secure connection. Spectrum management involves limiting cellular radio wave transmissions to tethering hosts so that local devices use Wi-Fi and Bluetooth signals. We then talked about Bluetooth versions 3.0 and higher to illustrate their various tethering pros and cons. After tethering, we talked about authentication topics such as the simple swipe patterns on mobile devices, and then the more advanced gesture-based authentication methods. We then went into the more commonplace PIN codes and an even stronger option in biometrics, which supports fingerprint scans, retina scans, iris scans, and facial recognition authentication. We briefly talked about malware and antimalware suggestions. Next we talked about unauthorized domain bridging, which involves a mobile device connected to Wi-Fi and the corporate Ethernet LAN simultaneously, and thus permitting wireless users to connect to the corporate LAN through the mobile device’s network bridge. Next, we talked about baseband radio and system on a chip (SoC), which are important cellular chips built into mobile devices that handle all cellular mobile and data transfers. Next up was augmented reality, which focuses on adding digitally enhanced content into our real-world experiences through smart glasses or similar devices. We touched on some of the security and privacy issues surrounding augmented reality. After that, we hit upon SMS/MMS messaging capabilities to indicate their prevalence but also their general lack of encryption capabilities.
The last section of the chapter focused on wearable technologies, beginning with cameras. Law enforcement officers often wear body cameras on their suits to track the various situations they find themselves in. The next topic was smart watches, their numerous benefits and security risk factors, including Bluetooth hacks, and unencrypted data transmission to/from smartphones. Then we went into fitness devices, which are designed to track a person’s health data more thoroughly than typical smart watches can. Next, we discussed smart glasses and their various location and navigation capabilities, access to contacts, people research, audio and video recording, and so much more. We then went into much more powerful versions of fitness devices, such as medical devices with their various sensors. We talked about the life-and-death benefits these provide to patients as well as the various security considerations relevant to them. The last wearable was headsets, which are your everyday headsets that people wear for voice calling while working at a front desk or customer service position.
The final subtopic was security implications as a result of wearable technologies. We went into the risk of attackers remotely activating or deactivating key features on wearable devices such as device synchronization and unpairing devices. Next, we talked about the lack of encryption and what alternatives, if any, are appropriate to deal with that challenge. We then talked about the physical reconnaissance that body cameras and smart glasses can perform to spy on a person and an environment without anyone knowing you’re collecting tons of data about them. We then went into personal data theft considerations often arising from Bluetooth and remote attackers. Then we talked about health privacy issues that can arise from fitness devices and medical devices generating, storing, and transmitting health information about people over networks. Finally, we touched on digital forensic considerations for gathering evidence from wearable devices.
Quick Tips
The following tips should serve as a brief review of the topics covered in more detail throughout the chapter.
Enterprise Mobility Management
• A centralized approach to management provides a consistent and comprehensive way of locking down devices to meet security policies and compliance requirements, while still allowing users to be productive.
• Containerization isolates corporate data into a protected and encrypted container stored on the mobile device.
• Configuration profiles are groups of OS and application settings applied to various devices inside and outside of an enterprise. Payloads are the individual settings in the configuration profiles.
• Personally owned, corporate-enabled (POCE) is BYOD but with official enterprise onboarding requirements to ensure the device is properly managed.
• Application wrappers are additional security features added to a mobile application that don’t modify the underlying functionality of the application itself.
• Remote assistance permits helpers to access the user’s device screen, observe settings and monitor performance, install or remove applications, set up e-mail, and configure VPN or Wi-Fi services.
• VNC is a graphical desktop sharing tool that permits remote management of other devices. It uses the Remote Frame Buffer (RFB) protocol for remote assistance.
• MDM products often have the ability to create application configuration policies, which, assuming the application supports them, permit deployment of applications to include custom configurations and security options.
• Over-the-air updates refer to the centralized and wireless distribution of new software, firmware, certificates, and encryption keys to mobile devices.
• Remote wiping is the process of sending a signal to a remote device to erase specified data.
• Simple Certificate Enrollment Protocol (SCEP) provides an easy process for network equipment, software, and mobile devices to enroll in digital certificates.
• BYOD is the process of allowing employees to bring in their own personal devices such as laptops, smartphones, and tablets to work in order to access enterprise applications and data.
• COPE occurs when the enterprise purchases and owns the devices, yet provides them to users for both enterprise and personal usage.
• CYOD allows users to bring their own devices to work, but they must comply with a pre-selected list of devices for standardization.
• With mobile devices often used by teleworkers and telecommuters, employees will occasionally require secure VPN access over the Internet to the enterprise environment.
• Many mobile applications require application permissions such as access to the device’s camera, microphone, call logs, e-mail, SMS messages, location data, application list, and so on.
• Side loading is the process of installing applications from sources outside the official app stores.
• The vendors of official app stores inspect applications before publishing them; an application’s developer is responsible for digitally signing the application.
• Context-aware management applies restrictive policies to mobile devices based on certain device conditions like location or time of day.
• Geolocation is the process of identifying a device’s geographical location by using GPS or cell towers.
• Geofencing is the process of creating a logical or virtual boundary around a mobile device.
• If user behaviors on mobile devices deviate from the expected norm, MDMs may deny authentication to protect the enterprise.
• Time-based restrictions apply certain security controls on a device based on what time it is.
Security Implications/Privacy Concerns
• Nonremovable storage is built into mobile devices such as smartphones and tablets, and cannot be removed.
• Removable storage refers to the external storage cards that can be added or replaced in a mobile device to increase the available storage.
• Cloud storage is often used for backing up a mobile device’s settings, application data, photos and videos, purchase history, and so on.
• Free cloud services provide basic services such as limited free storage, file management, recycle bin, content sharing, and basic file versioning. You don’t get much “control” over the actual storage.
• USB On-the-Go (OTG) is an older standard that permits USB devices to “host” other USB devices.
• Mobile devices, particularly smartphones, are prone to being forgotten or stolen.
• Hardware anti-tampering technologies resist deliberate attempts at causing disruption to or malfunction of a device.
• eFuse supports the reprogramming of a computer chip’s programming if adverse conditions, such as tampering, are detected.
• TPM chips are built into most motherboards to generate and store encryption keys in order to provide root of trust capabilities for devices using encrypted hard drives.
• Jailbreaking refers to the process of removing certain security restrictions from iOS devices such as iPhones and iPads.
• Rooting grants actual root-level privileges to the Android OS.
• Push notifications are important messages sent to mobile devices by an application publisher or an enterprise MDM system.
• Geotagging is the process of attaching geographically related information to common media types such as pictures, videos, SMS messages, and even websites.
• It is important to add encryption support to IM conversations due to the sensitivity of information that may be transmitted and subsequently captured by packet sniffers.
• Tokenization is the process of using a non-sensitive value (token) as a substitute for the original sensitive value (credit card number).
• Android fragmentation refers to the wide disparity of active Android OS versions still in use due to many older Android devices being prevented by Google from updating to the latest Android version.
• People are frequently using their smartphones and smart watches to submit mobile payments via their mobile devices’ payment applications.
• NFC payments are common because they are “contactless” and secure.
• NFC antennas use inductance, which is achieved by a wrapped coil of wire, to generate a very small magnetic field on the order of centimeters. Through this small magnetic field, a wireless connection can be established between mobile devices and payment machines.
• Mobile wallets are “virtual” wallets that store payment card information on mobile devices.
• Peripheral-enabled payments involve attaching credit card readers to smartphones in order to process credit cards.
• Tethering is the process of sharing a wireless Internet connection to other devices via the Wi-Fi, USB, or Bluetooth protocol.
• USB cables bring security to tethering, which cannot be achieved with wireless signals.
• Spectrum management is the process of ensuring that cellular radio–based data transmissions don’t overly consume the radio frequency spectrum.
• Bluetooth tethering is not as common as Wi-Fi due to, historically speaking, its hit-or-miss support, limited range, limited performance, non-optimized power consumption, and interference with the smartphone’s cellular signals. Recent Bluetooth versions have resolved these issues.
• Today’s mobile devices have multiple authentication methods to choose from, including swipe patterns, gestures, PINs, and biometrics.
• Swipe patterns typically involve a user tracing their finger across a series of dots in a specified order.
• Gestures may include drawing a line between two objects within the picture, drawing a circle around an object in the picture, double-tapping an area, or pressing and holding another area.
• PIN codes are generally preferred over swipe patterns and gestures because they are computationally more complex.
• Biometrics, known as “something you are,” rely on scanning a human’s biological characteristics, such as fingerprint, retina, iris, and facial recognition scans.
• Mobile devices are inherently more resistant to malware than PCs since mobile OSs place users behind restricted sandboxes.
• Unauthorized domain bridging occurs when unauthorized Wi-Fi users connect through the dual-network-connected employee to reach the corporate wired network.
• A baseband processor, also known as baseband system on a chip (SoC), is a hybrid CPU/RAM/firmware chip on mobile devices that handles its cellular radio communications.
• Augmented reality technology enhances or “augments” your real world by adding auditory, visual, haptic, and other digital sensory elements so that it feels like new environmental elements have been physically added into your current space.
• SMS messages are generally unencrypted and include text only.
• MMS messages are also generally unencrypted and can include pictures and videos.
Wearable Technology
• Wearable technology refers to smart devices that are either worn or implanted into the body.
• Cameras often serve as wearable technology for law enforcement officers, who often wear body cameras on their helmets, glasses, or torsos in order to record the events in which they are involved.
• Smart watches are mobile computing devices that we wear on our wrists like a watch.
• Fitness devices specialize in tracking physical fitness data points such as number of steps taken or climbed, number of minutes of exercise, walking speed, heart rate, and even caloric intake.
• Smart glasses are digitally enhanced glasses that contain an extra lens for augmenting your environment with helpful digital information.
• Medical devices are network-connected devices whose sensors are able to capture more advanced medical data, including blood pressure, glucose, and respiration.
• Headsets are generally the least technologically advanced wearables we discussed since they largely include only a microphone and speakers for voice conversations.
• If a smart watch has its Bluetooth discovery and pairing options enabled, attackers might be able to illegitimately pair with the smart watch to steal data at rest and intercept data in transit.
• If wearables don’t support encryption, consider either not using the wearables or limiting their usage to certain job roles and environments to minimize data breaches.
• Physical reconnaissance occurs when attackers use wearable technology to gather information about an environment or its people.
• Attackers may be able to remotely pair with a device and extract its data.
• Fitness devices, particularly medical devices, generate, store, and transmit a lot of electronic health information about their owners.
• Digital forensics is the practice of collecting, preserving, and analyzing digital evidence in order to understand all aspects of a digital crime.
Questions
The following questions will help you measure your understanding of the material presented in this chapter. Read all the choices carefully because there might be more than one correct answer. Choose all correct answers for each question.
1. Which of the following mobile device strategies specifically involves users buying their own mobile device based on an enterprise’s preselected list?
A. BYOD
B. CYOD
C. COPE
D. SCEP
2. Which of the following statements about jailbreaking and rooting are correct? (Choose all that apply.)
A. Jailbreaking is for iOS; rooting is for Android.
B. Rooting is for iOS; jailbreaking is for Android.
C. Jailbreaking provides root-level privileges to the mobile OS.
D. Rooting voids the warranty on the mobile device.
E. Jailbreaking increases the security of the mobile OS.
3. Which of the following provides an isolated encrypted space on mobile devices for storing enterprise data?
A. TPM
B. HSM
C. Virtual machine
D. Containerization
4. When attempting to install third-party applications outside of an official application store onto a mobile device, you receive an error preventing the installation. Which of the following will best solve the issue?
A. Firmware upgrade
B. Containerization
C. Side loading
D. Application wrapping
5. Which of the following capabilities of MDM ensures devices receive the settings they require?
A. Plug-ins
B. Configuration profiles
C. Tokens
D. SoCs
6. Which of the following best describes augmented reality?
A. Users’ perception of their real-world environment is completely replaced by a digital reality.
B. Users’ perception of their real-world environment is enhanced by digital elements.
C. Users’ devices and appliances are all networked together, forming a smart home.
D. Users’ devices and appliances are all networked together, forming a smart business.
7. Which of the following is a common method for enrolling network and mobile devices with digital certificates from a Certificate Authority?
A. SCEP
B. VNC
C. OSCP
D. OpenCert
8. Which of the following biometric factors is considered the most accurate?
A. Retina scan
B. Facial scan
C. Iris scan
D. Fingerprint scan
9. Which wireless protocol is most commonly used to make mobile payments at various retail locations?
A. Wi-Fi
B. NFC
C. LTE
D. Bluetooth
10. Which of the following options are available to tether devices to a smartphone’s mobile hotspot? (Choose all that apply.)
A. USB
B. Bluetooth
C. NFC
D. Wi-Fi
11. Which remote access protocol is associated with VNC for remote assistance purposes?
A. RDP
B. SSH
C. RPC
D. RFB
12. Which of the following technologies refers to locating a device’s geographical location by using GPS or cell towers?
A. Geotagging
B. Geofencing
C. Geolocation
D. Geosensing
13. Which of the following best describes mobile payment tokenization?
A. The process of a mobile device sending payment information to a payment machine
B. The process of a mobile device receiving confirmation of payment from the payment machine
C. The process of a mobile device encrypting the payment information
D. The process of a mobile device using a non-sensitive payment value as a substitute for the original sensitive payment value
Answers
1. B. Choose your own device (CYOD) involves users buying their own mobile device based on an enterprise’s preselected list.
2. A, D. Jailbreaking is for iOS, and rooting is for Android. Also, rooting voids the warranty on the mobile device.
3. D. Containerization provides an isolated encrypted space on mobile devices for storing enterprise data.
4. C. Side loading enables the permission to install third-party applications from outside official application stores.
5. B. Configuration profiles deploy OS and application configurations to mobile devices.
6. B. Users’ perception of their real-world environment is enhanced by digital elements.
7. A. SCEP provides enrollment of certificates for network and mobile devices from Certificate Authority servers.
8. C. Iris scanners are considered the most accurate.
9. B. NFC is the most commonly used for its short range and security.
10. A, B, D. USB, Bluetooth, and Wi-Fi are all supported for mobile tethering.
11. D. RFB Remote Frame Buffer is the protocol used by VNC.
12. C. Geolocation refers to locating a device’s geographical location by using GPS or cell towers.
13. D. Mobile payment tokenization is the process of a mobile device using a non-sensitive payment value as a substitute for the original sensitive payment value.




