INTRODUCTION
Day by day, nothing seems to change until one day everything is different. Given the theme of this book, one might surmise that I’m only referring to the current state of information security. Yet, take a glance at the news, social media, or emergency vehicles at the local high school, and you’ll discover that all aspects of our security are under attack. It’s not just the hackers we fear, but also previously mundane things like answering the phone, responding to a knock at the door, and the safety of our children at school. We’re also under constant surveillance by many devices in our homes and businesses, such as smartphones, tablets, TVs, and even smart speakers. At any moment our device’s built-in camera and microphone could be recording us while selling our personal information to various third parties. Most surprising, the majority of us are readily consenting to this collection and sale of our personal data. It’s safe to say that today we feel less secure about everything.
One could argue it is contradictory to suggesting that most people have become increasingly paranoid while at the same time a majority of such folks are deliberately sharing their personal information in order to play Candy Crush Saga for free. Perhaps those individuals have become resigned to the belief that their data was already stolen long ago; therefore, they might as well enjoy the application.
Technology cannot be blamed for all of the challenges in the world, yet it does play a crucial role in our uneasiness. With continual advances in technology devices, communication infrastructures, and information sources, billions of people have transitioned from being unplugged bystanders to technological choreographers of their environment. While most people choose to use technology to improve their quality of life, others are pulling off major credit card heists, and even triggering cyberwarfare between nations. This technological upheaval is responsible for seeding today’s most sophisticated attacker, the cybercriminal.
Hackers are literally everywhere. They are people just like you and me, only they’re no longer operating in the shadows. You’ll find them taunting the world via their social media channels––much to the applause of their thousands of subscribers. Meanwhile, other malicious insiders are having lunch with you at the office while plotting their next data breach. With names such as hackers, attackers, crackers, cyberterrorists, phreakers, script kiddies, suicide hackers, hacktivists, and more, it is clear that hacking is no longer just an intellectual curiosity. Nor are the majority of hackers operating as recluses like in years past. Hacking has become a capitalistic enterprise funded by organized cybercriminal corporations, governments, billionaires, and terrorist groups. Through strength in numbers, today’s cybercriminals are more powerful than at any time in history. With access to unlimited hacking tools, weaponized artificial intelligence, international botnets, state-sponsored military attacks, and infinite cloud computing resources, hackers have become true masters of societal disruption.
In many ways, security practitioners have mirrored the very hackers they were recruited to stop––by working as outsiders. Traditional security and IT departments operated in seclusion; they built security policies with minimal feedback from others, and implemented countermeasures only to put out fires. In essence, security solutions were reactionary as opposed to proactive. Solutions were mere ingredients that were sprinkled onto business operations rather than being sewn directly into the fabric of operations. Since hackers have evolved every aspect of their arsenal, the modern-day security practitioner must also adapt.
Today’s security practitioner must proactively bake security solutions into every aspect of the business, as opposed to only reacting after a breach has been reported. They must coordinate with all levels of the organization––from the CEO to the end user––in order to ensure that appropriate security solutions are implemented. Care must be taken to ensure that solutions provide adequate security, while also permitting the business to fulfill its financial and strategic goals. This is more challenging than it seems because security solutions are restrictive by nature. The omnipresence of security can become quite expensive too; yet data leakage, compliance failures, auditing fines or shutdowns, lost market share, corporate espionage, and damaged reputations are considerably more expensive.
I will say this with an ounce of affection and a pound of foreboding: Good security is annoying. Security solutions often come with unintended side effects, such as reductions in ease-of-use and functionalities to business processes. Most individuals will, at least initially, resist such trade-offs. The knowledge gained as security practitioners compels us to accept these side effects as quid pro quo for our improved security posture. It is the goal of CASP+, and my personal mission in security, to help you implement security solutions in a manner that is even more annoying to our adversaries than it is to us. When businesses operate from a place of freedom, they can exert more control over their destinies—provided that they never lose sight of the fact that freedom isn’t free.
—Nicholas Lane
CompTIA Advanced Security Practitioner (CASP+)
Back in 2012, the U.S. Navy approached CompTIA to develop an advanced cybersecurity certification that would serve as a viable alternative to the (ISC)² Certified Information Systems Security Professional (CISSP) certification. Like many organizations, the Navy had relied upon the CISSP for assessment and accreditation of advanced cybersecurity skills, yet it felt that something was missing. Despite CISSP’s global popularity, longevity, and irrefutable value in the security industry, the combination of its managerial slant and lack of performance-based questions created an imperfect alignment with the Navy’s “hands-on” security objectives. The CompTIA Advanced Security Practitioner (CASP+) certification was born out of a military need to certify security practitioners as possessing the advanced practical cybersecurity skills necessary to defend the nation. Shortly after the development of CASP+, the U.S. Department of Defense (DoD) approved it as part of the DoD 8570.01-M directive.
For civilians reading this book, don’t be deterred by CASP+ having military roots. Enterprises have considerable need of cybersecurity professionals with proven hands-on skills to protect assets from digital attackers. Enterprises from all over the world list the CASP+ certification as a prerequisite for job seekers.
The CompTIA Security+ certification is CompTIA’s entry-level security certification and one that is considered a precursor to the mastery-level CompTIA Advanced Security Practitioner certification. Security+ is a vendor-neutral certification that is designed to demonstrate an individual’s competency in the following areas:
• Network security
• Compliance and operational security
• Threats and vulnerabilities
• Application, data, and host security
• Access control and identity management
• Cryptography
CASP+ is designed to follow the CompTIA Security+ certification. It is also vendor-neutral and is designed to demonstrate an individual’s competency in risk management, enterprise security architecture, enterprise security operations, technical integration of enterprise security, and research, development, and collaboration regarding security trends. The exam covers the knowledge necessary for an individual to be able to conceptualize, design, and engineer secure solutions across complex enterprise environments and has a technical, hands-on focus at the enterprise level. Although there is no official prerequisite for the CASP+ certification, CompTIA recommends professionals to complete CompTIA Security+ as well as CompTIA PenTest+ or CompTIA Cybersecurity Analyst (CySA+), in either order.
The exam itself consists of a maximum of 90 questions, with a time limit of 165 minutes in which to complete the exam. There is no scaled scoring for this exam; it is pass/fail only. The recommended level of experience for exam candidates is 10 years of experience in IT administration, including at least five years of hands-on technical security experience.
The Five CASP+ Domains
Although the CASP+ certification is designed for practitioners with hands-on knowledge, skills, and abilities, you will see some managerial skill requirements listed among the exam objectives too. A security practitioner cannot be expected to produce practical solutions for security policies and frameworks if such requirements aren’t fundamentally understood. All of these skill requirements are covered throughout the five CASP+ domains. These domains, and their relative weights in terms of coverage, are as follows:
• 1.0 Risk Management (19%)
• 2.0 Enterprise Security Architecture (25%)
• 3.0 Enterprise Security Operations (20%)
• 4.0 Technical Integration of Enterprise Security (23%)
• 5.0 Research, Development and Collaboration (13%)
Performance-Based Exam Questions
Unlike CISSP, the CASP+ certification exam includes multiple types of questions, such as drag and drop, performance-based simulations, and the traditional multiple question/answer. An individual taking the exam will find some questions presented as a scenario and will then need to launch a simulated environment. The environment will be at the level of detail appropriate for an individual with the experience recommended for those taking the CASP+ exam. The individual will then need to perform whatever task is most appropriate, given the scenario and tools or information presented for the question. With this method, CompTIA is able to go beyond a simple “textbook understanding” of the subject and can test the skill level of individuals taking the exam.
CASP-Proposed Hardware and Software
Although the CASP+ certification is intended to be vendor-neutral, CompTIA nonetheless has provided a list of hardware and software that individuals taking the exam are expected to have some knowledge of. Some items in the list are simply types of tools that an individual might expect to see questions about, whereas others are examples of vendor-specific tools and technologies that individuals are expected to know something about. The list supplied by CompTIA is provided in Tables 1 through 5.
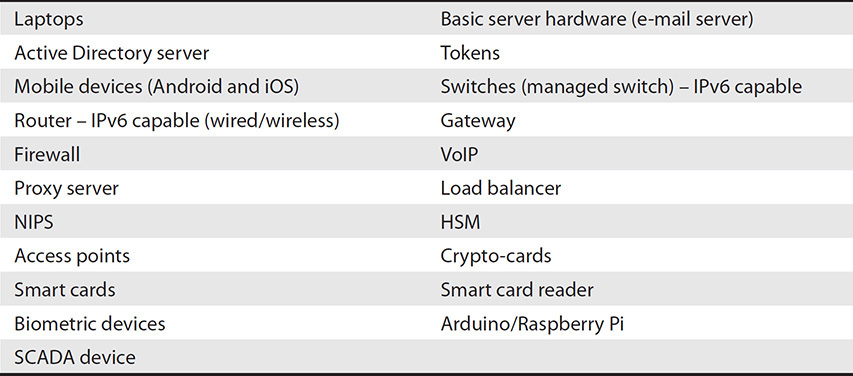
Table 1 List of Equipment Examples for the CASP+ Certification Exam

Table 2 List of Spare Hardware Examples for the CASP+ Certification Exam

Table 3 List of Tool Examples for the CASP+ Certification Exam
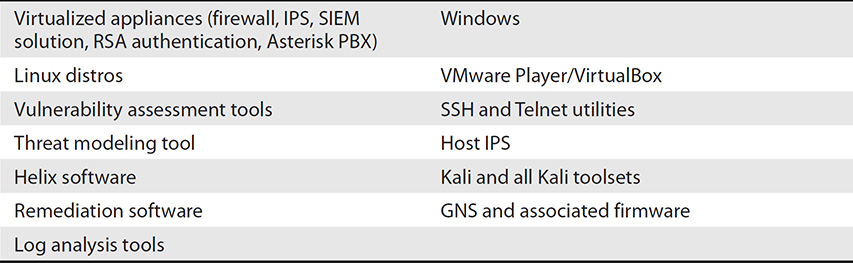
Table 4 List of Software Examples for the CASP+ Certification Exam
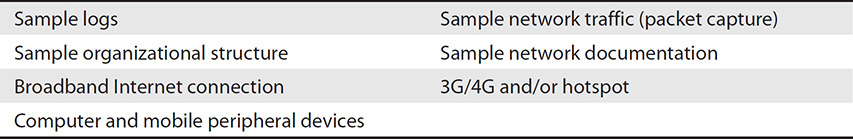
Table 5 List of Other Examples for the CASP+ Certification Exam
Accreditation
CASP+ is accredited by the American National Standards Institute (ANSI) in order to demonstrate compliance with the international ISO/IEC 17024 standard. ANSI is an organization that oversees the development of standards throughout the U.S. and globally.
How to Use This Book
True to its “All-In-One” namesake, this book packs enough information to help you pass the exam as well as to serve as an on-the-job reference. Yet, that information is only as useful as the diligence you put into understanding it. To help you get the most out of this book, let’s go over the book’s design elements and give you a few tips along the way:
• Certification Objectives This book’s chapters and topics are sequentially mapped to the CASP+ exam objectives to provide predictability in your learning experience––in addition to simplifying any subsequent exam objective research or review you’ll perform after completing a section. The end of this section contains the Objective Map, which is a summary of the CASP+ exam objectives. Visit the CASP+ portal on www.CompTIA.org for the detailed list.
• Tips Tip sections provide insider information or a best practice about a subject.
• Exam Tips Exam tip sections contain pertinent information likely to be targeted in the exam.
• Cautions Caution sections provide warnings about products, processes, and procedures that should be observed.
End-of-Chapter Questions
At the end of each chapter module you’ll find questions similar to the multiple-choice questions found on the actual exam. The answers to these questions can be found at the end of the book. By completing the end-of-chapter questions, you’ll reinforce what you’ve learned from that chapter while becoming familiar with the structure of any multiple-choice exam questions you receive on the real exam.
Using the Objective Map
The Objective Map included in this section has been constructed to help give you a bird’s-eye view of the official CASP+ exam objectives as published by CompTIA. Included with the Objective Map are the respective chapters that provide detailed coverage of the objectives. A more detailed exam objective mapping was not necessary since this book already conveniently covers each exam objective in sequential order.
The Accompanying Media
This book includes accompanying media that features the TotalTester exam software that allows you to generate a complete practice exam or quizzes by chapter module or by exam domain. See the appendix for more information about the online content.
Exam CAS-003 Objective Map



