Practice Exam 1
Are you ready to assess your preparedness for the CCNA 200-301 exam? Practice Exam 1 and Practice Exam 2 are here to help.
As you take this practice exam, consider the following test-taking tips:
▸ Watch your time in the simulations: Just like the real exam, this practice exam includes simulations. You access these simulations from the companion website. Download these files before starting your exam. When you encounter one in this practice exam, launch the exercise and complete it, making sure to be careful about how much time you spend in the exercise—just as you would in the real exam.
▸ Read each question twice if necessary: Be sure to read each question carefully so that you fully understand it. You may need to read some questions twice.
▸ Read the answers starting from the bottom: When you read the answers from the bottom, you force yourself to carefully read each answer. If you read the answers from the top, you might find yourself quickly selecting an answer that looks right and skipping over the other answers. This is dangerous as there might be a better answer later in the options.
▸ Time yourself: The CCNA 200-301 exam is a 90-minute exam. Time yourself during this practice exam to make sure that you stay within this time limit.
▸ If you do not know the answer to a question, make a note of it: Go back and review any trouble areas later. Be sure that you are mastering each topic area, not just looking up the answers to individual questions. If you are unsure about one aspect of a topic, chances are you might be unsure about other areas related to that same topic.
▸ Prepare mentally to take a test: To properly assess yourself, take this practice exam as you would take the real exam. This means that you should find a quiet place without any distractions so that you can focus on each question. Equip yourself with scratch paper and a pen and pencil. For the actual exam, you will be allowed no other tools (such as calculators), so you shouldn’t use additional tools for the practice exams either.
▸ If you cannot determine the correct answer(s), begin by eliminating incorrect answer(s): If there are four options, and you know that three are absolutely wrong, the fourth option has to be the correct one.
▸ Consider taking this practice exam, as well as the next one, multiple times until you get perfect scores: Consistently scoring high on these practice exams is a good indication that you’re ready to take the actual exam.
▸ Pay close attention to the Answer Key: The answers to the practice exam questions include explanations, which often bring up related important information. Even if you answered a question correctly, be sure to read the explanation in the Answer Key.
▸ Use the online materials: There are even more practice exams waiting for you on the Pearson Test Prep software that is available to you either online or as an offline Windows application. Be sure to use those materials as well.
▸ Don’t despair: Do not be overly upset if on your first attempt at this practice exam, you do not score well. It only means that you need to continue studying. Be glad that you can spot your weak areas now and not after getting into the actual exam. Go back through and review your problem areas now to ensure that you are ready!
Congratulations on your pursuit of this valued IT certification!
1. What transport layer protocol features the use of sequencing and synchronization methods?
![]() A. ICMP
A. ICMP
![]() B. TCP
B. TCP
![]() C. UDP
C. UDP
![]() D. ARP
D. ARP
2. Examine the figure. If devices 1, 2, and 3 are all Cisco Layer 2 switches in their default configurations, how many collision domains exist in this network?

_________
3. You have configured your gi0/1 Cisco switch port as follows:
interface gi0/1 switchport mode access switchport port-security
Which of the following statements is true?
![]() A. The default violation mode is Restrict.
A. The default violation mode is Restrict.
![]() B. The mode must be Trunk for port security to be used.
B. The mode must be Trunk for port security to be used.
![]() C. The default number of dynamic MAC addresses is one.
C. The default number of dynamic MAC addresses is one.
![]() D. This configuration prevents the logging of port security violations.
D. This configuration prevents the logging of port security violations.
![]() E. The violation mode in use here is Protect.
E. The violation mode in use here is Protect.
4. What protocol is used with an Integrated Services approach to QoS?
![]() A. ICMP
A. ICMP
![]() B. VTP
B. VTP
![]() C. SPAN
C. SPAN
![]() D. NTP
D. NTP
![]() E. RSVP
E. RSVP
5. What is the default administrative distance for OSPF?
![]() A. 20
A. 20
![]() B. 120
B. 120
![]() C. 110
C. 110
![]() D. 200
D. 200
![]() E. 90
E. 90
6. What is the IPv4 address range 224.0.0.0 to 239.255.255.255 used for?
![]() A. To send a packet to all systems
A. To send a packet to all systems
![]() B. To send a packet to a group of systems
B. To send a packet to a group of systems
![]() C. To send a packet to a single specific system
C. To send a packet to a single specific system
![]() D. To send multiple packets to only a single specific system
D. To send multiple packets to only a single specific system
7. Which RF band is used with 802.11ac?
![]() A. 2.4 GHz
A. 2.4 GHz
![]() B. 5 GHz
B. 5 GHz
![]() C. Both 2.4 GHz and 5 GHz
C. Both 2.4 GHz and 5 GHz
![]() D. 7 GHz
D. 7 GHz
8. What is the privilege level for the user in the command username johns secret cisco123?
![]() A. 0
A. 0
![]() B. 1
B. 1
![]() C. 15
C. 15
![]() D. 8
D. 8
9. HANDS-ON SIMULATION QUESTION 1
10. Examine the figure. What is the Layer 2 destination address?

_________
11. Examine the code shown here. What format is in use?
"templateConfig":{
"vInfraPolicy":"cloud82",
"networks":[
{
"networkName":"lan0",
"networkType":1000,
"vlanIDPool":"100-199",
"networkPool":1000,
"ipSubnetPool":1000,
"networkIP":"10.10.10.0",
"networkMask":"255.255.255.0",
"gatewayIP":"10.10.10.1"
},
![]() A. XML
A. XML
![]() B. YAML
B. YAML
![]() C. JSON
C. JSON
![]() D. PBF
D. PBF
12. What technology provides multiple default gateways in a redundant manner and automates load sharing?
![]() A. FHRP
A. FHRP
![]() B. HSRP
B. HSRP
![]() C. VRRP
C. VRRP
![]() D. GLBP
D. GLBP
13. You are in privileged mode on R1. Provide all configuration commands in order to configure this device as a router-on-a-stick (ROAS) using the following information:
Physical interface: GigabitEthernet 0/1
Protocol: 802.1Q
Subinterfaces: GigabitEthernet 0/1.10 (VLAN 10); GigabitEthernet 0/1.20 (VLAN 20)
IP addressing:
GigabitEthernet 0/1.10: 10.1.10.1/24
GigabitEthernet 0/1.20: 10.1.20.1/24
_________
14. How is a playbook expressed in Ansible?
![]() A. YAML
A. YAML
![]() B. XML
B. XML
![]() C. JSON
C. JSON
![]() D. HTML5
D. HTML5
15. Create an extended ACE that permits Telnet traffic from a Telnet server on the network 10.10.10.0/24, going to a host on network 192.168.1.0/24. Use ACL 101.
_________
16. What keyword enables the use of PAT in a NAT configuration?
![]() A. load
A. load
![]() B. ports
B. ports
![]() C. overload
C. overload
![]() D. pool
D. pool
17. How many syslog levels are there with Cisco equipment?
![]() A. 8
A. 8
![]() B. 6
B. 6
![]() C. 4
C. 4
![]() D. 16
D. 16
18. What wireless security standard replaces PSK with SAE?
![]() A. WPA3
A. WPA3
![]() B. AES
B. AES
![]() C. TKIP
C. TKIP
![]() D. WPA2
D. WPA2
19. Examine the topology shown here. How many collision domains exist between the PC and Router 1?
![]() A. 0
A. 0
![]() B. 1
B. 1
![]() C. 2
C. 2
![]() D. 3
D. 3
20. Which of the following provides a secure method to transfer files in a Cisco network?
![]() A. TFTP
A. TFTP
![]() B. FTP
B. FTP
![]() C. Telnet
C. Telnet
![]() D. SCP
D. SCP
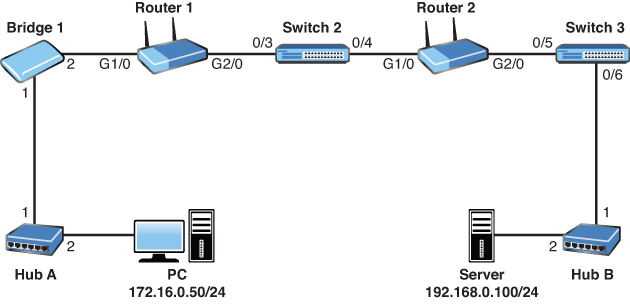
21. Examine the topology shown in the figure. The PC has sent a ping request to the server. Which devices in the network operate only at the physical layer of the OSI reference model? (Choose two.)

![]() A. Ethernet cabling
A. Ethernet cabling
![]() B. Bridge 1
B. Bridge 1
![]() C. Router 2
C. Router 2
![]() D. Hub A
D. Hub A
![]() E. Switch 3
E. Switch 3
![]() F. PC network interface card
F. PC network interface card
22. Which of the following are true on a typical Cisco access layer switch? (Choose two.)
![]() A. It can have IP routing enabled.
A. It can have IP routing enabled.
![]() B. It can have an IP address configured for management.
B. It can have an IP address configured for management.
![]() C. It can be used for NAT or PAT.
C. It can be used for NAT or PAT.
![]() D. A default gateway allows the switch to access remote networks.
D. A default gateway allows the switch to access remote networks.
![]() E. Ports default to no switchport mode.
E. Ports default to no switchport mode.
23. What feature does DAI rely on?
![]() A. ACLs
A. ACLs
![]() B. DHCP snooping
B. DHCP snooping
![]() C. QoS DiffServ
C. QoS DiffServ
![]() D. NBAR
D. NBAR
![]() E. OSPF
E. OSPF
24. Examine the switch configuration shown. What problem exists with this suggested configuration change?
SW1 configure terminal interface fa0/10 switchport trunk encapsulation isl switchport mode trunk switchport port-security switchport port-security max 2 no shutdown
![]() A. Port security can only support a single secure MAC address.
A. Port security can only support a single secure MAC address.
![]() B. Port security can be used on trunks (depending on the switch), but it is likely that there will be many more than two learned MAC addresses on that port.
B. Port security can be used on trunks (depending on the switch), but it is likely that there will be many more than two learned MAC addresses on that port.
![]() C. Port security can only be used with 802.1Q trunks.
C. Port security can only be used with 802.1Q trunks.
![]() D. A violation mode for port security must be selected.
D. A violation mode for port security must be selected.
25. Which of the following is not an HTTP method used with REST APIs?
![]() A. PUT
A. PUT
![]() B. POST
B. POST
![]() C. SEND
C. SEND
![]() D. GET
D. GET
![]() E. DELETE
E. DELETE
26. Examine the topology shown in the figure. If OSPF, EIGRP, and RIPv2 were all enabled on each interface on each router, which routing protocol would R4 use to determine the best route to 10.77.67.0/24?

![]() A. EIGRP because its metric considers bandwidth and delay
A. EIGRP because its metric considers bandwidth and delay
![]() B. OSPF because its cost is derived from bandwidth and delay
B. OSPF because its cost is derived from bandwidth and delay
![]() C. OSPF because it is an advanced distance-vector routing protocol
C. OSPF because it is an advanced distance-vector routing protocol
![]() D. EIGRP because of administrative distance
D. EIGRP because of administrative distance
27. You decided to reduce the size of your existing Layer 2 broadcast domains by creating new VLANs. What network device that forwards packets between those VLANs would be operating (at a minimum), and at which OSI layer?
![]() A. A switch at Layer 1
A. A switch at Layer 1
![]() B. A switch at Layer 2
B. A switch at Layer 2
![]() C. A router at Layer 2
C. A router at Layer 2
![]() D. A router at Layer 3
D. A router at Layer 3
28. Examine the topology shown in the figure. Provide the Router 2 configuration for OSPFv2 to enable OSPF area 0 for process 100 on G2/0. The G2/0 IP address is 192.168.0.1/24. Do not use the interface-level OSPF command and ensure that OSPF runs on no other interface.
_________

29. Which of the following statements regarding ICMP is correct?
![]() A. ICMP functions at the network layer of the OSI model.
A. ICMP functions at the network layer of the OSI model.
![]() B. ICMP relies on TCP for reliable packet delivery.
B. ICMP relies on TCP for reliable packet delivery.
![]() C. ICMP relies on UDP for efficient packet delivery.
C. ICMP relies on UDP for efficient packet delivery.
![]() D. ICMP functions at the session layer of the OSI model.
D. ICMP functions at the session layer of the OSI model.
30. What device can use a dual-band approach and 802.11 standards for connecting end users to the network?
![]() A. Firewall
A. Firewall
![]() B. WLC
B. WLC
![]() C. AP
C. AP
![]() D. Router
D. Router
31. Which is not a major menu option in Cisco DNA Center?
![]() A. Compliance
A. Compliance
![]() B. Policy
B. Policy
![]() C. Design
C. Design
![]() D. Provision
D. Provision
32. What is the last usable host address, given the IP address and subnet mask 172.16.10.101 with 255.255.224.0?
_________
33. What command produced the following output?
MK5 unit 0, NIM slot 1, NIM type code 7, NIM version 1 idb = 0x6150, driver structure at 0x34A878, regaddr = 0x8100300 IB at 0x6045500: mode=0x0108, local_addr=0, remote_addr=0 N1=1524, N2=1, scaler=100, T1=1000, T3=2000, TP=1 buffer size 1524 DTE V.35 serial cable attached RX ring with 32 entries at 0x45560 : RLEN=5, Rxhead 0 00 pak=0x6044D78 ds=0x6044ED4 status=80 max_size=1524 pak_size=0
_________
34. What is a potential underlay protocol for a VXLAN EVPN fabric?
![]() A. VTP
A. VTP
![]() B. eBGP
B. eBGP
![]() C. RIP
C. RIP
![]() D. EIGRP
D. EIGRP
35. Which of the following addresses is a private-use-only address?
![]() A. 12.43.56.120
A. 12.43.56.120
![]() B. 177.12.34.19
B. 177.12.34.19
![]() C. 201.92.34.100
C. 201.92.34.100
![]() D. 10.123.23.104
D. 10.123.23.104
36. What must be in place before you can route other devices’ IPv6 traffic through a Cisco router?
![]() A. The command dual-stack routing
A. The command dual-stack routing
![]() B. A loopback 0 interface with an IPv4 address assigned
B. A loopback 0 interface with an IPv4 address assigned
![]() C. IPv4 interfaces
C. IPv4 interfaces
![]() D. The ipv6 unicast-routing global configuration command
D. The ipv6 unicast-routing global configuration command
37. Which command displays a quick view of OSPF neighbor status?
![]() A. show ip ospf neighbor
A. show ip ospf neighbor
![]() B. show ospf peers
B. show ospf peers
![]() C. show ip ospf routers
C. show ip ospf routers
![]() D. show ospf peers
D. show ospf peers
38. What are two reasons a duplex mismatch can be difficult to find? (Choose two.)
![]() A. Users are presented with an error message that varies by operating system.
A. Users are presented with an error message that varies by operating system.
![]() B. Connectivity is typically intermittent.
B. Connectivity is typically intermittent.
![]() C. Users cannot communicate on the network at all.
C. Users cannot communicate on the network at all.
![]() D. Connectivity might be slow.
D. Connectivity might be slow.
39. What command would you use on a Cisco Layer 2 switch to verify errors regarding sending or receiving frames?
![]() A. show controllers
A. show controllers
![]() B. show interface
B. show interface
![]() C. show collisions
C. show collisions
![]() D. show version
D. show version
40. A Cisco switch is currently in VTP Client mode. You issue the vlan 100 command in global configuration mode to create a new VLAN. What is the result?
![]() A. The switch produces an error message.
A. The switch produces an error message.
![]() B. The switch sends VLAN 100 configuration information to the VTP server.
B. The switch sends VLAN 100 configuration information to the VTP server.
![]() C. The switch reverts to Transparent mode.
C. The switch reverts to Transparent mode.
![]() D. The switch configures the VLAN but on the local device only.
D. The switch configures the VLAN but on the local device only.
41. What traditional 802.1D STP port state does not exist in 802.1w RSTP?
![]() A. Discarding
A. Discarding
![]() B. Listening
B. Listening
![]() C. Learning
C. Learning
![]() D. Forwarding
D. Forwarding
42. What global configuration command allows you to disable CDP on an entire Cisco switch?
![]() A. no cdp
A. no cdp
![]() B. no cdp enable
B. no cdp enable
![]() C. no cdp run
C. no cdp run
![]() D. no cdp search
D. no cdp search
43. When you enable port security for a switch port, what is the default violation mode?
![]() A. Restrict
A. Restrict
![]() B. Shutdown
B. Shutdown
![]() C. Protect
C. Protect
![]() D. Passive
D. Passive
44. What is the default administrative distance for internal EIGRP?
![]() A. 20
A. 20
![]() B. 110
B. 110
![]() C. 120
C. 120
![]() D. 90
D. 90
45. What architectural model is used with Cisco ACI?
![]() A. 2-tier spine-leaf
A. 2-tier spine-leaf
![]() B. 2-tier collapsed core
B. 2-tier collapsed core
![]() C. 3-tier
C. 3-tier
![]() D. Concentric
D. Concentric
46. Examine the configuration that follows. What is the next hop for 10.10.20.0/24?
ip route 10.10.20.0 255.255.255.0 172.16.1.1
![]() A. 255.255.255.0
A. 255.255.255.0
![]() B. 10.10.20.1
B. 10.10.20.1
![]() C. 172.16.1.1
C. 172.16.1.1
![]() D. 0.0.0.0
D. 0.0.0.0
47. What command permits you to see your locally used OSPF routes?
![]() A. show ip ospf database local
A. show ip ospf database local
![]() B. show ospf all
B. show ospf all
![]() C. show ip route ospf
C. show ip route ospf
![]() D. show ospf routes local
D. show ospf routes local
48. HANDS-ON SIMULATION QUESTION 2
49. What tool produced the output shown?
Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: www.yahoo.com canonical name = fd-fp3.wg1.b.yahoo.com. Name: fd-fp3.wg1.b.yahoo.com Address: 98.139.183.24 Name: fd-fp3.wg1.b.yahoo.com Address: 98.139.180.149
![]() A. netstat
A. netstat
![]() B. nbtstat
B. nbtstat
![]() C. nslookup
C. nslookup
![]() D. msconfig
D. msconfig
50. What interface configuration mode command configures a Cisco router as a DHCP client?
![]() A. ip address auto
A. ip address auto
![]() B. ip address enable dhcp
B. ip address enable dhcp
![]() C. dhcp address
C. dhcp address
![]() D. ip address dhcp
D. ip address dhcp
51. What command allows you to confirm the IP address and mask assigned to an interface?
![]() A. show interfaces terse
A. show interfaces terse
![]() B. show addresses
B. show addresses
![]() C. show ip interface brief
C. show ip interface brief
![]() D. show ip interface
D. show ip interface
52. What is the stratum of a Cisco router if you use the command ntp master to configure it to use its internal clock as a time source?
![]() A. 0
A. 0
![]() B. 1
B. 1
![]() C. 2
C. 2
![]() D. 8
D. 8
![]() E. 13
E. 13
53. Examine the access list shown here. What is the issue with this access list?
access-list 1 permit any access-list 1 deny host 10.10.10.1 access-list 1 deny host 10.10.10.2 access-list 1 deny host 172.16.1.1 access-list 1 deny any log
![]() A. The access list cannot end with a deny statement.
A. The access list cannot end with a deny statement.
![]() B. The access list permits the traffic before it denies any traffic.
B. The access list permits the traffic before it denies any traffic.
![]() C. The access list is not named, and naming is required.
C. The access list is not named, and naming is required.
![]() D. Standard access lists do not support logging.
D. Standard access lists do not support logging.
54. What do you use in dynamic NAT configuration in order to identify the traffic you intend to translate?
![]() A. An access list
A. An access list
![]() B. A pool
B. A pool
![]() C. A NAT list
C. A NAT list
![]() D. An interface reference
D. An interface reference
55. What is the name of the “database” used with SNMP?
![]() A. AGENT
A. AGENT
![]() B. MIB
B. MIB
![]() C. TREE
C. TREE
![]() D. VARSTORE
D. VARSTORE
56. What suite of protocols is often found in use with modern VPN connections?
![]() A. IPsec
A. IPsec
![]() B. SLA
B. SLA
![]() C. DNSSEC
C. DNSSEC
![]() D. PGP
D. PGP
57. Which of the following is not a step for supporting SSH connections on a Cisco router?
![]() A. Configure a DNS domain.
A. Configure a DNS domain.
![]() B. Generate the SSH key.
B. Generate the SSH key.
![]() C. Configure the hostname command.
C. Configure the hostname command.
![]() D. Enable SSH globally.
D. Enable SSH globally.
58. Examine the configuration shown here. Which statement is false?
no service password-encryption ! enable secret rtYHS3TTs ! username admin01 privilege 15 secret Cisco123 ! line vty 0 4 password ChEeEs&WiZ login transport input telnet
![]() A. Telnet users will be required to provide a password for Telnet access.
A. Telnet users will be required to provide a password for Telnet access.
![]() B. Telnet users will be required to provide the password ChEeEs&WiZ for access to privileged mode.
B. Telnet users will be required to provide the password ChEeEs&WiZ for access to privileged mode.
![]() C. The account password of the admin privilege-level user is not very secure.
C. The account password of the admin privilege-level user is not very secure.
![]() D. New plaintext passwords will not be encrypted.
D. New plaintext passwords will not be encrypted.
59. A new Layer 2 switch in its default configuration has just been powered up. In addition to a console connection, there are two Windows hosts and an IP phone (using PoE) connected to its Ethernet ports. Which of the following are true? (Choose two.)
![]() A. If either Windows host has successfully completed an ARP resolution, the switch will have learned the MAC addresses of both Windows hosts.
A. If either Windows host has successfully completed an ARP resolution, the switch will have learned the MAC addresses of both Windows hosts.
![]() B. The switch would see the two Windows hosts’ directly connected devices from CDP.
B. The switch would see the two Windows hosts’ directly connected devices from CDP.
![]() C. The switch would not know if the IP phone is a Cisco IP phone or a third-party IP phone until a call is initiated from the phone.
C. The switch would not know if the IP phone is a Cisco IP phone or a third-party IP phone until a call is initiated from the phone.
![]() D. The switch can be configured with an IPv4 address on interface VLAN 1.
D. The switch can be configured with an IPv4 address on interface VLAN 1.
60. Refer to the network topology that follows. Your senior network administrator is concerned about network security. He has asked you to ensure that the PC-10 device in VLAN 10 does not overflow the switch’s CAM table. How should you respond? (Choose two.)

![]() A. Configure OSPF on all network devices and use MD5 authentication.
A. Configure OSPF on all network devices and use MD5 authentication.
![]() B. Configure the service password-encryption command on the switch.
B. Configure the service password-encryption command on the switch.
![]() C. Configure port-security on interface 0/2 of the switch.
C. Configure port-security on interface 0/2 of the switch.
![]() D. Configure Router A to route traffic sourced from any device other than PC-10 to Null0.
D. Configure Router A to route traffic sourced from any device other than PC-10 to Null0.
![]() E. Configure a static MAC address as part of port-security.
E. Configure a static MAC address as part of port-security.
