Practice Exam 2
Are you ready to assess your preparedness for the CCNA 200-301 exam? Practice Exam 1 and Practice Exam 2 are here to help.
As you take this practice exam, consider the following test-taking tips:
▸ Watch your time in the simulations: Just like the real exam, this practice exam includes simulations. You access these simulations from the companion website. Download these files before starting your exam. When you encounter one in this practice exam, launch the exercise and complete it, making sure to be careful about how much time you spend in the exercise—just as you would in the real exam.
▸ Read each question twice if necessary: Be sure to read each question carefully so that you fully understand it. You may need to read some questions twice.
▸ Read the answers starting from the bottom: When you read the answers from the bottom, you force yourself to carefully read each answer. If you read the answers from the top, you might find yourself quickly selecting an answer that looks right and skipping over the other answers. This is dangerous as there might be a better answer later in the options.
▸ Time yourself: The CCNA 200-301 exam is a 90-minute exam. Time yourself during this practice exam to make sure that you stay within this time limit.
▸ If you do not know the answer to a question, make a note of it: Go back and review any trouble areas later. Be sure that you are mastering each topic area, not just looking up the answers to individual questions. If you are unsure about one aspect of a topic, chances are you might be unsure about other areas related to that same topic.
▸ Prepare mentally to take a test: To properly assess yourself, take this practice exam as you would take the real exam. This means that you should find a quiet place without any distractions so that you can focus on each question. Equip yourself with scratch paper and a pen and pencil. For the actual exam, you will be allowed no other tools (such as calculators), so you shouldn’t use additional tools for the practice exams either.
▸ If you cannot determine the correct answer(s), begin by eliminating incorrect answer(s): If there are four options, and you know that three are absolutely wrong, the fourth option has to be the correct one.
▸ Consider taking this practice exam, as well as the next one, multiple times until you get perfect scores: Consistently scoring high on these practice exams is a good indication that you’re ready to take the actual exam.
▸ Pay close attention to the Answer Key: The answers to the practice exam questions include explanations, which often bring up related important information. Even if you answered a question correctly, be sure to read the explanation in the Answer Key.
▸ Use the online materials: There are even more practice exams waiting for you on the Pearson Test Prep software that is available to you either online or as an offline Windows application. Be sure to use those materials as well.
▸ Don’t despair: Do not be overly upset if on your first attempt at this practice exam, you do not score well. It only means that you need to continue studying. Be glad that you can spot your weak areas now and not after getting into the actual exam. Go back through and review your problem areas now to ensure that you are ready!
Congratulations on your pursuit of this valued IT certification!
1. Examine the following NAT configuration. What is the problem with this configuration?
interface gi0/0 ip address 10.10.10.1 255.255.255.0 ip nat inside ! interface gi0/1 ip address 10.10.20.1 255.255.255.0 ip nat inside ! interface serial 0/0 ip address 172.16.10.64 255.255.255.0 ! ip nat pool MYPOOL 172.16.10.1 172.16.10.1 prefix 24 ip nat inside source list 7 pool MYPOOL overload access-list 7 permit 10.10.10.0 0.0.0.31 access-list 7 permit 10.10.20.0 0.0.0.31
_________
2. Which wireless security protocol makes the use of CCMP mandatory?
![]() A. DAI
A. DAI
![]() B. IPsec
B. IPsec
![]() C. WPA2
C. WPA2
![]() D. WEP
D. WEP
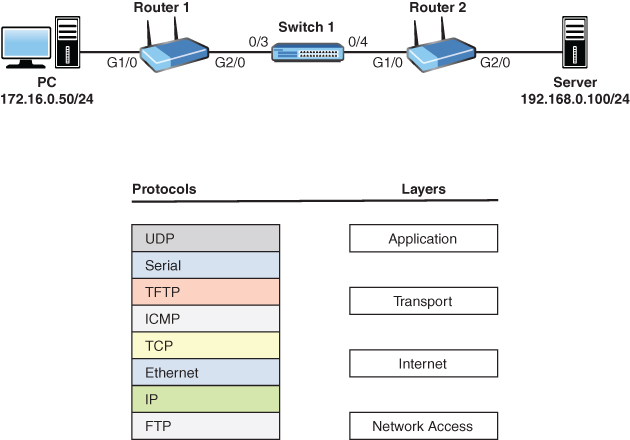
3. The user at the PC shown in the figure is copying a file from the server by using a program that uses a connectionless transport protocol. Which protocols on the left match up to the layers on the right regarding the encapsulation done by the PC? (Note that not all the protocols are used.)
4. What declarative language is shown in this example?
user { 'asequeira':
ensure => present,
uid => '1453',
shell => '/bin/bash',
home => '/var/tmp'
}
![]() A. Puppet
A. Puppet
![]() B. Ruby
B. Ruby
![]() C. Python
C. Python
![]() D. C#
D. C#
5. How are the connections made between devices in the spine-leaf architecture of Cisco ACI?
![]() A. Each leaf device connects to every other leaf device.
A. Each leaf device connects to every other leaf device.
![]() B. Each spine device connects to every other spine device.
B. Each spine device connects to every other spine device.
![]() C. Exactly one spine device connects to exactly one leaf device.
C. Exactly one spine device connects to exactly one leaf device.
![]() D. Each leaf device connects to every spine device.
D. Each leaf device connects to every spine device.
6. Examine the configuration shown here. Why is this configuration producing an error when pasted into the CLI?
Current configuration : 2945 bytes ! ... hostname Router-A ! ... ! interface GigabitEthernet0/0 no ip address shutdown duplex auto speed auto media-type rj45 ! interface GigabitEthernet0/1 ip address 172.16.1.64 255.255.255.224 duplex auto speed auto media-type rj45 ! ip forward-protocol nd ! ! no ip http server no ip http secure-server ip route 10.10.10.0 255.255.255.0 172.16.1.2 ! ! ! access-list 101 permit ip 10.10.0.0 0.0.255.255 any access-list 101 deny ip host 10.10.10.1 any access-list 101 deny ip any any log ! ... ! end
![]() A. There is no enable password set.
A. There is no enable password set.
![]() B. The hostname is not legal.
B. The hostname is not legal.
![]() C. The hostname contains an invalid character.
C. The hostname contains an invalid character.
![]() D. There is a bad IP address and mask combination.
D. There is a bad IP address and mask combination.
![]() E. The second entry of ACL 101 will in effect not deny anything more than the next ACE.
E. The second entry of ACL 101 will in effect not deny anything more than the next ACE.
7.What information for a wireless network can you choose not to broadcast?
![]() A. SSID
A. SSID
![]() B. The AP’s MAC address
B. The AP’s MAC address
![]() C. Type
C. Type
![]() D. Version
D. Version
8. What QoS technology is often used for congestion management in VoIP environments?
![]() A. LLQ
A. LLQ
![]() B. CBWFQ
B. CBWFQ
![]() C. WFQ
C. WFQ
![]() D. FIFO
D. FIFO
9. What is smaller and more efficient than a virtual machine (VM)?
![]() A. Bucket
A. Bucket
![]() B. Cluster node
B. Cluster node
![]() C. API
C. API
![]() D. Container
D. Container
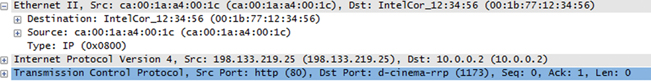
10. What is true regarding a network device that receives the packet shown in the protocol analyzer output that follows? (Choose two.)
![]() A. A bridge would forward the packet based on the Layer 1 destination address.
A. A bridge would forward the packet based on the Layer 1 destination address.
![]() B. A hub would forward the packet based on the Layer 2 destination address.
B. A hub would forward the packet based on the Layer 2 destination address.
![]() C. A switch would forward the frame based on the Layer 2 destination address.
C. A switch would forward the frame based on the Layer 2 destination address.
![]() D. A router would forward the packet based on the Layer 2 source address.
D. A router would forward the packet based on the Layer 2 source address.
![]() E. A router would forward the packet based on the Layer 3 source address.
E. A router would forward the packet based on the Layer 3 source address.
![]() F. A router would forward the packet based on the Layer 3 destination address.
F. A router would forward the packet based on the Layer 3 destination address.
11. Which RSTP port role functions to provide a fast converging replacement for the current root port?
![]() A. Disabled
A. Disabled
![]() B. Alternate
B. Alternate
![]() C. Backup
C. Backup
![]() D. Designated
D. Designated
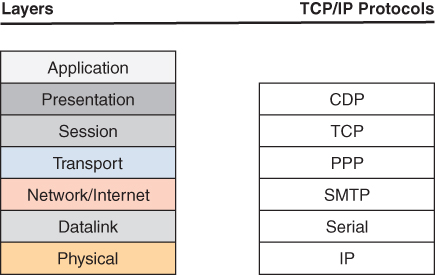
12. Map the layers on the left to the protocols on the right. Note that not all layers are used, and some layers may be used more than once.
13. What Cisco wireless controller feature simplifies controller configuration by no longer requiring the setup of primary and secondary ports for each interface?
![]() A. RSTP
A. RSTP
![]() B. SNMP
B. SNMP
![]() C. VTP
C. VTP
![]() D. LAG
D. LAG
14. What transport layer protocol provides sequencing and synchronization?
![]() A. HTTP
A. HTTP
![]() B. TCP
B. TCP
![]() C. ICMP
C. ICMP
![]() D. UDP
D. UDP
15. What device protects “internal” networks from “external” networks?
![]() A. WLC
A. WLC
![]() B. Firewall
B. Firewall
![]() C. AP
C. AP
![]() D. Layer 2 switch
D. Layer 2 switch
16. What layer of the classic Cisco network model is typically not collapsed in a simplified two-layer design?
![]() A. Access
A. Access
![]() B. Internet
B. Internet
![]() C. Core
C. Core
![]() D. Distribution
D. Distribution
17. You are examining the interfaces on a Cisco WLAN controller. You observe an interface named Students-VLAN. What is most likely the type of this interface?
![]() A. Service port interface
A. Service port interface
![]() B. User-defined dynamic interface
B. User-defined dynamic interface
![]() C. Management interface
C. Management interface
![]() D. AP-Manager interface
D. AP-Manager interface
18. What is the standard maximum frame size in a typical Ethernet network (in bytes)?
![]() A. 1500
A. 1500
![]() B. 1600
B. 1600
![]() C. 1900
C. 1900
![]() D. 9000
D. 9000
19. In the network depicted, the user at PC1 has asked which program to use to copy a file from the server to PC1 using a reliable Layer 4 transport protocol. Which of the following would meet both requirements? (Choose two.)

![]() A. OSPF
A. OSPF
![]() B. TFTP
B. TFTP
![]() C. FTP
C. FTP
![]() D. SCP
D. SCP
![]() E. DNS
E. DNS
20. Which statement about PortFast on Cisco switches is incorrect?
![]() A. PortFast is used exclusively on trunk ports.
A. PortFast is used exclusively on trunk ports.
![]() B. PortFast speeds convergence.
B. PortFast speeds convergence.
![]() C. PortFast is supported in STP and RSTP.
C. PortFast is supported in STP and RSTP.
![]() D. PortFast is designed for use on edge ports.
D. PortFast is designed for use on edge ports.
21. What technology is used to allow a switch port to carry the traffic of multiple data VLANs from one device to another in a Cisco network?
![]() A. VLAN hopping
A. VLAN hopping
![]() B. Trunking
B. Trunking
![]() C. Port security
C. Port security
![]() D. VTP
D. VTP
22. Examine the following MAC addresses on two switches:
SwitchA: c001.3412.9301
SwitchB: 0019.e728.8101
In a tiny network with only these two switches, which switch becomes the root bridge if the default STP priority values are in place?
![]() A. SwitchA
A. SwitchA
![]() B. SwitchB
B. SwitchB
![]() C. Neither of these switches
C. Neither of these switches
![]() D. Both devices
D. Both devices
23. What port security approach is considered a mix of dynamic and static configuration?
![]() A. Trunking
A. Trunking
![]() B. Violation null
B. Violation null
![]() C. Sticky learning
C. Sticky learning
![]() D. Blocked learning
D. Blocked learning
24. Your junior administrator is examining the routing table on a Cisco router and asks you what is the meaning of the D she sees in routing table entries. What does this indicate?
![]() A. OSPF
A. OSPF
![]() B. BGP
B. BGP
![]() C. RIP
C. RIP
![]() D. EIGRP
D. EIGRP
25. What prefix is reserved for IPv6 link-local addresses?
![]() A. fe80::/10
A. fe80::/10
![]() B. fec0::/10
B. fec0::/10
![]() C. fe80::/8
C. fe80::/8
![]() D. fec0::/8
D. fec0::/8
26. Examine the command shown here. What is the purpose of the last argument in this command (121)?
ip route 10.10.10.0 255.255.255.0 172.16.1.1 121
![]() A. This is a sequence number.
A. This is a sequence number.
![]() B. This is the metric value for the route entry.
B. This is the metric value for the route entry.
![]() C. This is an administrative distance value to create a floating static route.
C. This is an administrative distance value to create a floating static route.
![]() D. This is a weight value.
D. This is a weight value.
27. Which of the following is used by an IPv6 multicast address?
![]() A. f080::/10
A. f080::/10
![]() B. ff00::/8
B. ff00::/8
![]() C. fc00::/8
C. fc00::/8
![]() D. f008::/10
D. f008::/10
28. What networking device provides instructions to APs?
![]() A. Router
A. Router
![]() B. Firewall
B. Firewall
![]() C. Switch
C. Switch
![]() D. WLC
D. WLC
29. Which of the following does not need to match when configuring OSPF version 2 peering?
![]() A. The local process ID
A. The local process ID
![]() B. The hello and dead timers
B. The hello and dead timers
![]() C. The area ID
C. The area ID
![]() D. Authentication
D. Authentication
30. What type of modern computer threat involves the use of zombies or botnets?
![]() A. Reconnaissance
A. Reconnaissance
![]() B. Man-in-the-middle attack
B. Man-in-the-middle attack
![]() C. DDoS attack
C. DDoS attack
![]() D. Trojan horse
D. Trojan horse
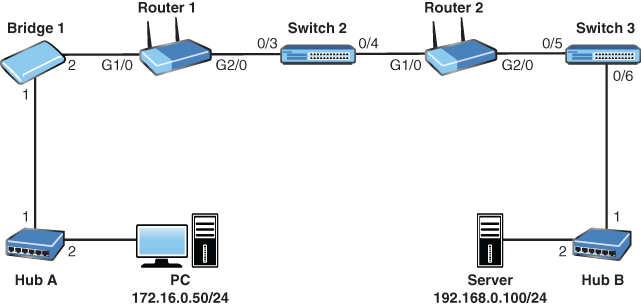
31. In the network depicted, the server is sending HTTP content back to the PC that requested it. Which of the following is true as the packets are forwarded over the network?
![]() A. The bridges and switches use Ethernet addresses to make forwarding decisions.
A. The bridges and switches use Ethernet addresses to make forwarding decisions.
![]() B. The hubs, bridges, and switches use Ethernet addresses to make forwarding decisions.
B. The hubs, bridges, and switches use Ethernet addresses to make forwarding decisions.
![]() C. The routers, bridges, and switches use Ethernet addresses to make forwarding decisions.
C. The routers, bridges, and switches use Ethernet addresses to make forwarding decisions.
![]() D. The hubs, routers, bridges, and switches use Ethernet addresses to make forwarding decisions.
D. The hubs, routers, bridges, and switches use Ethernet addresses to make forwarding decisions.
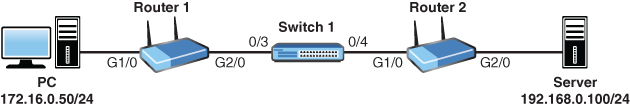
32. Based on the network depicted, provide the complete syntax for a standard ACL for Router 2 G2/0 that permits traffic sourced from the PC but denies all other traffic. This ACL must use the number 10 and must use the most efficient syntax possible.
_________
33. After identification has been accomplished with a DDoS attack, what is typically the next step in mitigation?
![]() A. Forwarding
A. Forwarding
![]() B. Filtering
B. Filtering
![]() C. Monitoring
C. Monitoring
![]() D. Redirection
D. Redirection
34. Which of the following is essentially a standards-based version of HSRP?
![]() A. OSPF
A. OSPF
![]() B. SNMP
B. SNMP
![]() C. VRRP
C. VRRP
![]() D. GLBP
D. GLBP
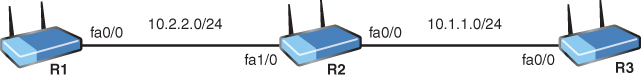
35. Examine the topology shown. Given that the IP address assigned to R2 fa1/0 is 10.2.2.2, provide a default static route on R1 that uses R2 as the default gateway.
_________
36. Your junior admin notes that when he just performed a ping, one of the packets failed. What is the most likely cause of the following results?
Router1# ping 10.255.0.126 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.255.0.126, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 35/72/76 ms
![]() A. Load balancing, with one of the next hops being unavailable
A. Load balancing, with one of the next hops being unavailable
![]() B. ARP resolution
B. ARP resolution
![]() C. Half-duplex operation
C. Half-duplex operation
![]() D. 10 Mbps being used instead of Fast Ethernet or Gigabit Ethernet
D. 10 Mbps being used instead of Fast Ethernet or Gigabit Ethernet
37. Router A is assigning IP addresses to hosts in VLAN 10, as shown in the network depiction. The user powers up PC-10 and checks https://www.reuters.com/ for news. What are the first four protocols used by PC-10 when it powers up, in order?
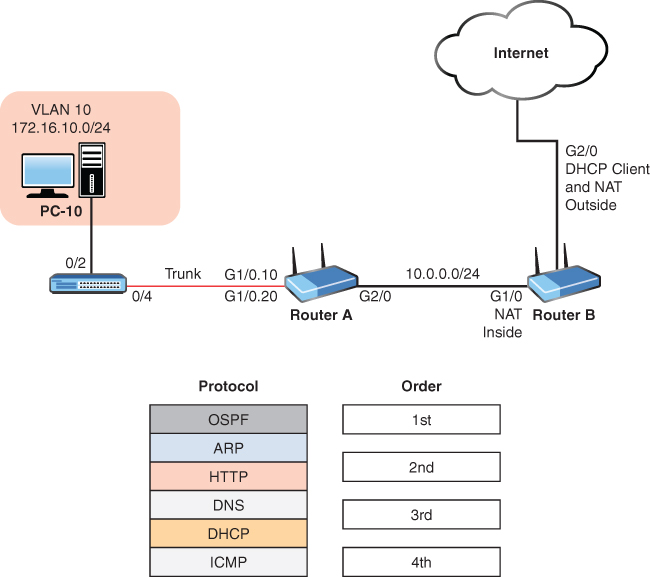
_________
38. Given the following address and mask 172.16.10.1 255.255.248.0, what is the broadcast address for the subnet?
![]() A. 172.16.15.255
A. 172.16.15.255
![]() B. 172.16.8.0
B. 172.16.8.0
![]() C. 172.16.16.255
C. 172.16.16.255
![]() D. 172.16.255.255
D. 172.16.255.255
![]() E. 172.16.10.255
E. 172.16.10.255
39. What is the authentication method used in many RADIUS environments today?
![]() A. EAP
A. EAP
![]() B. PAP
B. PAP
![]() C. Telnet
C. Telnet
![]() D. MD5
D. MD5
40. What is the term for an API that communicates from a network management station to the SDN controller?
![]() A. West
A. West
![]() B. East
B. East
![]() C. Southbound
C. Southbound
![]() D. Northbound
D. Northbound
41. What is the purpose of the command service timestamps log datetime msec?
![]() A. To prevent attackers from manipulating the time in syslog messages
A. To prevent attackers from manipulating the time in syslog messages
![]() B. Not applicable as this command is not valid
B. Not applicable as this command is not valid
![]() C. To mark syslog messages with the data and time, including the milliseconds
C. To mark syslog messages with the data and time, including the milliseconds
![]() D. To indicate the time of transference for syslog messages to the server
D. To indicate the time of transference for syslog messages to the server
42. What command does a client use to enable stateless autoconfiguration of IPv6 address information on an interface?
![]() A. ipv6 address autoconfig
A. ipv6 address autoconfig
![]() B. ipv6 address dhcp
B. ipv6 address dhcp
![]() C. ipv6 address enable
C. ipv6 address enable
![]() D. ipv6 enable
D. ipv6 enable
43. OSPF is properly configured and working on both routers shown in the depicted network. The following is added to Router X: ip route 10.255.0.128 255.255.255.224 10.255.0.75 89. What will be the result?

![]() A. The static route will have an administrative distance that is better than that of OSPF.
A. The static route will have an administrative distance that is better than that of OSPF.
![]() B. There will be a Layer 2 loop.
B. There will be a Layer 2 loop.
![]() C. Router X will attempt to send to PC 1 packets destined to subnet 10.255.0.128/27.
C. Router X will attempt to send to PC 1 packets destined to subnet 10.255.0.128/27.
![]() D. A broadcast storm will occur.
D. A broadcast storm will occur.
44. Examine the topology shown here. PC1 is sending an HTTP packet to Server 1. What is true about this traffic as it is forwarded through Switch C? (Choose three.)

![]() A. The source physical address will be 0000.3333.3333.
A. The source physical address will be 0000.3333.3333.
![]() B. The source Layer 2 address will be 00:00:11:11:11:11.
B. The source Layer 2 address will be 00:00:11:11:11:11.
![]() C. The source address will be 10.255.0.92.
C. The source address will be 10.255.0.92.
![]() D. The destination physical address will be 00:00:66:66:66:66.
D. The destination physical address will be 00:00:66:66:66:66.
![]() E. The destination address will be 0000.4444.4444.
E. The destination address will be 0000.4444.4444.
45. As shown in the switch MAC address table below the topology depicted, PC 1’s ARP cache is empty, and the user at PC 1 uses ping to test the IP address reachability of Server 1. Which of the following is true when the user presses Enter?
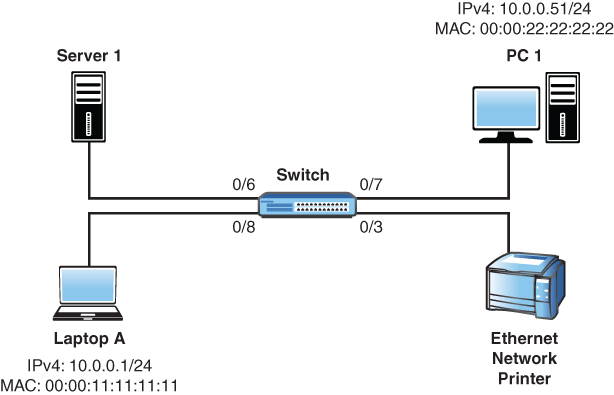
MAC Address |
VLAN |
Port |
|---|---|---|
0000.1111.1111 |
1 |
0/8 |
0000.2222.2222 |
1 |
0/7 |
0000.6783.BEEF |
1 |
0/6 |
![]() A. The first frame will be sent out port 0/6 only.
A. The first frame will be sent out port 0/6 only.
![]() B. The switch will add the printer’s MAC address to the MAC address table.
B. The switch will add the printer’s MAC address to the MAC address table.
![]() C. The first frame from PC1 will be forwarded out all ports except 0/7.
C. The first frame from PC1 will be forwarded out all ports except 0/7.
![]() D. The reply to the ping request will cause the server’s MAC address to be added to the table.
D. The reply to the ping request will cause the server’s MAC address to be added to the table.
![]() E. The first frame will use Server 1’s MAC address as the destination MAC address.
E. The first frame will use Server 1’s MAC address as the destination MAC address.
46. A host runs the command ipconfig on the local system. The output is as follows:
Ethernet adapter: Connection-specific DNS Suffix . : IPv4 Address. . . . . . . . . . . : 172.18.62.255 Subnet Mask . . . . . . . . . . . : 255.255.248.0 Default Gateway . . . . . . . . . : 172.18.63.254 Which of the following are true? (Choose two.)
![]() A. The broadcast address for the host’s subnet is 172.18.71.255.
A. The broadcast address for the host’s subnet is 172.18.71.255.
![]() B. The host is attached to a subnet of a Class B private network.
B. The host is attached to a subnet of a Class B private network.
![]() C. The subnet the host is connected to can support up to 2048 hosts.
C. The subnet the host is connected to can support up to 2048 hosts.
![]() D. The host with IP address 172.18.64.5 would be on the same network as the host in the question.
D. The host with IP address 172.18.64.5 would be on the same network as the host in the question.
![]() E. The host address is on the 172.18.56.0/21 network.
E. The host address is on the 172.18.56.0/21 network.
47. Which of the following are valid host addresses when using the mask 255.255.248.0? (Choose three.)
![]() A. 34.45.56.0
A. 34.45.56.0
![]() B. 40.50.60.0
B. 40.50.60.0
![]() C. 50.60.70.255
C. 50.60.70.255
![]() D. 51.61.71.255
D. 51.61.71.255
![]() E. 60.70.80.0
E. 60.70.80.0
![]() F. 60.70.80.255
F. 60.70.80.255
48. Refer to the depicted network. All the switches and R1 have had their startup configurations deleted and then were rebooted before saving to NVRAM. These devices are now running in their default configuration. Which of the following are true? (Choose three.)

![]() A. Clients shown in the diagram as being on VLANs 10, 20, and 30 will now all be on the same VLAN.
A. Clients shown in the diagram as being on VLANs 10, 20, and 30 will now all be on the same VLAN.
![]() B. SW1 will see CDP neighbors on at least three interfaces.
B. SW1 will see CDP neighbors on at least three interfaces.
![]() C. The commands show protocols, show ip interface, show interface, or show ip interface brief can be used to confirm that R1 G0/0 is up/up.
C. The commands show protocols, show ip interface, show interface, or show ip interface brief can be used to confirm that R1 G0/0 is up/up.
![]() D. If the command ip address 10.0.0.1 /24 were added for G0/0 on R1, SW1 would learn that IP address within 60 seconds.
D. If the command ip address 10.0.0.1 /24 were added for G0/0 on R1, SW1 would learn that IP address within 60 seconds.
![]() E. SW2 will see two CDP neighbors.
E. SW2 will see two CDP neighbors.
49. Provide the switch configuration to meet these requirements:
![]() The user account BOB should be created with the password ToUgH1!23, which is stored using MD5.
The user account BOB should be created with the password ToUgH1!23, which is stored using MD5.
![]() Telnet should be disabled on the switch.
Telnet should be disabled on the switch.
![]() SSHv2 should be enabled on the switch.
SSHv2 should be enabled on the switch.
![]() The local user accounts should be used to authenticate on the vty lines.
The local user accounts should be used to authenticate on the vty lines.
![]() Existing and future plaintext passwords should be encrypted.
Existing and future plaintext passwords should be encrypted.
![]() The password to get into privileged mode should be iTsMe@HeRe$, and it should be stored using MD5.
The password to get into privileged mode should be iTsMe@HeRe$, and it should be stored using MD5.
![]() The management interface should use the default VLAN and have the IP address 10.20.30.75/27.
The management interface should use the default VLAN and have the IP address 10.20.30.75/27.
![]() The default gateway should be set to 10.20.30.94.
The default gateway should be set to 10.20.30.94.
_________
50. CSMA/CD technology is critical for what type of Ethernet network?
![]() A. Full mesh
A. Full mesh
![]() B. Partial mesh
B. Partial mesh
![]() C. Star
C. Star
![]() D. Half-duplex
D. Half-duplex
51. HANDS-ON SIMULATION QUESTION 3
52. How is CDP carried on the network?
![]() A. Using 802.1Q messages
A. Using 802.1Q messages
![]() B. Using VTP messages
B. Using VTP messages
![]() C. Using Layer 2
C. Using Layer 2
![]() D. Using Layer 1
D. Using Layer 1
53. What is the default administrative distance of iBGP?
![]() A. 20
A. 20
![]() B. 90
B. 90
![]() C. 120
C. 120
![]() D. 200
D. 200
54. What two options exist for the next-hop information in a static route? (Choose two.)
![]() A. Specifying the next-hop IP address
A. Specifying the next-hop IP address
![]() B. Specifying the next-hop MAC address
B. Specifying the next-hop MAC address
![]() C. Specifying the next-hop CDP ID
C. Specifying the next-hop CDP ID
![]() D. Specifying the exit interface
D. Specifying the exit interface
55. What is the default lease duration for a Cisco DHCP server?
![]() A. One hour
A. One hour
![]() B. One day
B. One day
![]() C. One week
C. One week
![]() D. One month
D. One month
56. How do you configure a Cisco router to use its internal clock as the reference time source and then become an NTP server?
![]() A. Use the ntp server command.
A. Use the ntp server command.
![]() B. Use the ntp master command.
B. Use the ntp master command.
![]() C. Use the ntp source command.
C. Use the ntp source command.
![]() D. Use the ntp clock command.
D. Use the ntp clock command.
57. What is the default privilege level for a local user account created with the username command?
![]() A. 0
A. 0
![]() B. 1
B. 1
![]() C. 8
C. 8
![]() D. 15
D. 15
58. What vty line command causes the local username database to be checked for remote access?
![]() A. login
A. login
![]() B. local
B. local
![]() C. login local
C. login local
![]() D. aaa login local
D. aaa login local
59. HANDS-ON SIMULATION QUESTION 4
60. What component does Ansible use to gather plays that perform tasks on a network?
![]() A. Playbook
A. Playbook
![]() B. Inventory
B. Inventory
![]() C. Cookbook
C. Cookbook
![]() D. Runbook
D. Runbook
