Chapter 1
Getting Started with Ethical Hacking
 II. Analysis/Assessment
II. Analysis/Assessment
- C. Risk assessments
- D. Technical assessment methods
 III. Security
III. Security
- L. Privacy/confidentiality (with regard to engagement)
 V. Procedures/Methodology
V. Procedures/Methodology
- H. Security testing methodology
 VII. Ethics
VII. Ethics
- A. Professional code of conduct
- B. Appropriateness of hacking activities
In this book you will learn the various technologies and methodologies involved in becoming an ethical hacker. You will learn what it means to become an ethical hacker and the responsibilities you will be assuming both technically and ethically when you take on this role.
The reality of your taking on the ethical hacker skill set is that companies and enterprise environments have had to quickly and effectively address the threats and vulnerabilities that they face. Through a robust and effective combination of technological, administrative, and physical measures, all these organizations have learned to address their given situation and head off major problems. Technologies such as virtual private networks (VPNs), cryptographic protocols, intrusion detection systems (IDSs), intrusion prevention systems (IPSs), access control lists (ACLs), biometrics, smart cards, and other devices have helped security. Administrative countermeasures such as policies, procedures, and other rules have also been strengthened and implemented over the past decade. Physical measures include cable locks, device locks, alarm systems, and similar devices. Your new role as an ethical hacker will deal with all of these items, plus many more.
As an ethical hacker you must not only know the environment you will be working in, but also how to find weaknesses and address them as needed. However, before we get to all of that this chapter discusses the history of hacking and what it means to be an ethical hacker. We’ll also look the process of penetration testing and explore the importance of contracts.
Hacking: A Short History
Hacker is one of the most misunderstood and overused terms in the security industry. It has almost become the technological equivalent of a boogeyman, which so many either fear or end up ignoring. What is a hacker and where do we, as ethical hackers, fit in? Well, to answer that question let’s take a look at the history of hacking along with some notable events.
The Early Days of Hacking
As the story goes, the earliest hackers were a group of people who were passionate and curious about new technology. They were the equivalent of those modern-day individuals who not only want the latest technology, such as a smartphone or iPhone, but also want to learn all the juicy details about what the device does and what type of undocumented things they can do. Since the early days things have evolved dramatically: Individuals are more advanced and innovative and have access to newer and more powerful tools.
Hackers or enthusiasts were always working with the best technology available at the time. In the 1970s it was the mainframes that were present on college campuses and corporate environments. Later, in the 1980s the PC became the newest piece of technology, with hackers moving to this environment. The 1980s saw hackers moving to more mischievous and later malicious activities; their attacks could now be used against many more systems because more people had access to PCs. In the 1990s the Internet was made accessible to the public and systems became interconnected; as a result, curiosity and mischief could easily spread beyond a small collection of systems and go worldwide. Since 2000, smartphones, tablets, Bluetooth, and other technologies have been added to the devices and technologies that hackers target. As hackers evolved, so did their attacks.
When the Internet became available to the public at large, hacking and hackers weren’t too far behind. When the first generations of browsers became available in the early 1990s, attacks grew in the form of website defacements and other types of mischief. The first forays of hacking in cyberspace resulted in some humorous or interesting pranks, but later more aggressive attacks started to emerge. Incidents such as the hacking of movie and government websites were some of the first examples. Until the early 2000s, website defacing was so common that many incidents were no longer reported.
Current Developments
In the early 2000s, more malicious activity started to appear in the form of more advanced attacks. In fact, in the first few years of the new millennium the aggressiveness of attacks increased, with many attacks criminally motivated. Malicious attacks that have occurred include the following, among many more:
- Denial-of-service attacks
- Manipulation of stock prices
- Identity theft
- Vandalism
- Credit card theft
- Piracy
- Theft of service
One of the many situations that have contributed to the increase in hacking and cybercrime is the amount of information being passed and the overall dependency on the Internet and digital devices. Over the last decade the number of financial transactions has increased, creating a tempting target for crooks. Also, the openness of modern devices such as smartphones and technologies such as Bluetooth has made hacking and stealing information easier. Lastly, we could also point to the number of Internet-connected devices such as tablets and other gadgets that individuals carry around in increasing numbers. Each of these examples has attracted the attention of criminals with the temptation of stealing never before heard of amounts of money, data, and other resources. As computer crime laws began to be passed, the bragging rights for hacking a website became less attractive. The prank activity seemed to slow down whereas real criminal activity increased. With online commerce, skills started going to the highest bidder, with crime rings, organized crime, and nations with hostile interests using the Internet as an attack vector.
Hacking: Fun or Criminal Activity?
As stated earlier, hacking is by no means a new phenomenon; it has existed in one form or another since the 1960s. It is only for a portion of the time since then that hacking has been viewed as a crime and a situation that needs to be addressed.
Here’s a look at some famous hacks over time:
- In 1988, Cornell University student Robert T. Morris, Jr. created what is considered to be the first Internet worm. According to Morris, his worm was designed to count the number of systems connected to the Internet. Because of a design flaw, the worm replicated quickly and indiscriminately, causing widespread slowdowns across the globe. Morris was eventually convicted under the 1986 Computer Fraud and Abuse Act and was sentenced to community service in lieu of any jail time.
- In 1999, David L. Smith created the Melissa virus, which was designed to e-mail itself to entries in a user’s address book and later delete files on the infected system.
- In 2001, Jan de Wit authored the Anna Kournikova virus, which was designed to read all the entries of a user’s Outlook address book and e-mail itself out to each.
- In 2004, Adam Botbyl, together with two friends, conspired to steal credit card information from the Lowe’s hardware chain.
- In 2005, Cameron LaCroix hacked into the phone of celebrity Paris Hilton and also participated in an attack against the site LexisNexis, an online public record aggregator, ultimately exposing thousands of personal records.
- In 2011, the hacking group Lulzsec performed several high-profile attacks against targets such as Sony, CNN, and Fox.com. The group still appears to be active from time to time despite their claims of retiring.
- In 2010 through the current day, the hacking group Anonymous also has attacked multiple targets, including local government networks, new agencies, and others. The group is still active.
The previous examples represent some of the higher-profile incidents that have occurred, but for every news item or story that makes it into the public consciousness, many more never do. Note that for every incident that is made public, only a small number of the individuals who carry them out are caught, and an even smaller number are prosecuted for cybercrime. In any case, hacking is indeed a crime, and anyone engaging in such activities can be prosecuted under laws that vary from location to location. The volume, frequency, and seriousness of attacks have only increased and will continue to do so as technology evolves.
Here are some generic examples of cybercrime:
- Stealing passwords and usernames, or using vulnerabilities in a system to gain access, falls under the category of theft of access and the stealing of services and resources that the party would not otherwise be given access to. In some cases stealing credentials but not using them is enough to have committed a cybercrime. In a few states even sharing usernames and passwords with a friend or family member is a crime.
- Network intrusions are a form of digital trespassing where a party goes someplace that they would not otherwise have access to. Access to any system or group of systems to which a party would not normally be given access is considered a violation of the network and therefore a cybercrime. In some cases the actual intrusions may not even involve hacking tools; the very act of logging into a guest account may be sufficient to be considered an intrusion.
- Social engineering is both the simplest and the most complex form of hacking or exploiting a system by going after its weakest point, the human element. On the one hand, this is easy to attempt because the human being is many times the most accessible component of a system and the simplest to interact with. On the other hand, it can be extremely difficult to read both the spoken and unspoken cues to get the information that may be useful to the attacker.
- Posting and/or transmitting illegal material has gotten to be a difficult problem to solve and deal with over the last decade. With the increase of the use of social media and other Internet-related services, illegal material can spread from one corner of the globe to the other in a very short period of time.
- Fraud is the deception of another party or parties to elicit information or access typically for financial gain or to cause damage.
- Software piracy is the possession, duplication, or distribution of software in violation of a license agreement, or the act of removing copy protection or other license-enforcing mechanisms. Again this has become a massive problem with the rise of file-sharing services and other mechanisms designed to ease sharing and distribution; in many cases the systems are used for distribution without the system owner’s consent.
- Dumpster diving is the oldest and simplest way to gather material that has been discarded or left in unsecured or unguarded receptacles. Often, discarded data can be pieced together to reconstruct sensitive information.
- Malicious code refers to items such as viruses, worms, spyware, adware, rootkits, and other types of malware. This crime covers any type of software deliberately written to wreak havoc and destruction or disruption.
- Unauthorized destruction or alteration of information includes modifying, destroying, or tampering with information without permission.
- Embezzlement is a form of financial fraud that involves theft or redirection of funds as a result of violating a position of trust. The crime has been made much easier through the use of modern digital means.
- Data-diddling is the unauthorized modification of information to cover up activities.
- Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks are ways to overload a system’s resources so it cannot provide the required services to legitimate users.
The Evolution and Growth of Hacking
As you will see in this book, attacks and strategies have improved and evolved over the years in ways you may not be aware of. Attackers have constantly sought to “up” their game with new tactics and strategies to include new types of malware such as worms, spam, spyware, adware, and even rootkits. Although they already knew how to harass and irritate the public, in recent years they have caused ever bolder disruptions of today’s world by preying on our “connected” lifestyle.
Hackers have also started to realize that it is possible to use their skills to generate money in many interesting ways. For example, attackers have used techniques to redirect web browsers to specific pages that generate revenue for themselves. Another example is where a spammer sends out thousands upon thousands of e-mail messages that advertise a product or service. Because sending out bulk e-mail costs mere pennies, it takes only a small number of purchasers to make a nice profit.
The field you are entering (or may already be working in as a security administrator or engineer) is one that changes rapidly. In this field attacker and defender are in an ongoing struggle to gain dominance over each other. As attackers have become highly flexible and adaptable, so must you be as an ethical hacker. Your ability to think “outside the box” will serve you well as you envision new strategies and potential attacks before they are used against you.
Making your life as a security manager even harder today is that attackers have adopted a new pack mentality that makes defensive measures and planning much harder. In the early days the attacking person was just that—one person. Nowadays groups such as Anonymous and Lulzsec have shown us quite convincingly that attacking in numbers makes a difference even in the cyberworld. The collective or hive-like mentality has reaped huge benefits for attackers who are able to employ multiple methods in a short period of time to obtain impressive results. Such groups or packs are able to enhance their effectiveness by having a wide range of numbers, diversity, or complementary skill sets and also by the addition of clear leadership structures. Also adding to the concern is that some groups can be linked to criminal or terrorist organizations.
In this book you will learn these methods and what is being used on the front lines to perpetrate increasingly complex and devastating attacks. You must be aware of how these attacks have evolved, how technology has played a part, and how the law is dealing with an ever more complicated landscape.
In this book you will also learn more about the motivations of attackers and their mind-set. This is one of the challenges that you will have as an ethical hacker: understanding and empathizing with your attackers. Understanding the motivations can, in some cases, yield valuable insight into why a given attack has been committed or may be committed against an asset. For now you should keep in mind that an attacker needs three things to carry out a crime:
- Means, or the ability to carry out their goals or aims, which in essence means that they have the skills and abilities needed to complete the job
- Motive, or the reason to be pursuing the given goal
- Opportunity, or the opening or weakness needed to carry out the threat at a given time
What Is an Ethical Hacker?
When you explore this book and the tools it has to offer, you are learning the skills of the hacker. But we can’t leave it at that, as you need to be an ethical hacker, so let’s explore what that means.
Ethical hackers are employed either through contracts or direct employment to test the security of an organization. They use the same skills and tactics as a hacker, but with permission from the system owner to carry out their attack against the system. Additionally, an ethical hacker does not reveal the weaknesses of an evaluated system to anyone other than the system owner. Finally, ethical hackers work under contract for a company or client, and their contracts specify what is off-limits and what they are expected to do. It depends on the specific needs of a given organization. In fact, some organizations keep teams on staff specifically to engage in ethical hacking activities.
One of the details you need to understand early and never forget is that of permission. As an ethical hacker you should never target a system or network that you do not own or have permission to test. If you do so you are guilty of any number of crimes, which would be detrimental not only to your career but perhaps to your freedom as well. Before you test a target, you should have a contract in hand from the owner giving you permission to do so. Also remember that you should only test those things you have been contracted to test. If the customer or client decides to add or remove items from the test, the contract must be altered to keep both parties out of legal harm. Take special notice of the fact that ethical hackers operate with contracts in place between themselves and the target. Operating without permission is unethical; operating without a contract is downright stupid and illegal.
Additionally, a contract must include verbiage that deals with the issue of confidentiality and privacy. It is possible that during a test you will encounter confidential information or develop an intimate knowledge of your client’s network. As part of your contract you will need to address who you will be allowed to discuss your findings with and who you will not. Generally clients will want you to discuss your findings only with them and no one else.
According to the International Council of Electronic Commerce Consultants (EC-Council) you, as a CEH, must keep private any confidential information gained in your professional work (in particular as it pertains to client lists and client personal information). You cannot collect, give, sell, or transfer any personal information (such as name, e-mail address, social security number, or other unique identifier) to a third party without your client’s prior consent. Keep this in mind since a violation of this code could not only cause you to lose trust from a client, but also land you in legal trouble.
Once ethical hackers have the necessary permissions and contracts in place, they can engage in penetration testing, also known as pen testing. This is the structured and methodical means of investigating, uncovering, attacking, and reporting on the strengths and vulnerabilities of a target system. Under the right circumstances, pen testing can provide a wealth of information that the owner of a system can use to adjust defenses.
Ethical Hacking and Penetration Testing
Ethical hackers engage in sanctioned hacking—that is, hacking with permission from the system’s owner. In the world of ethical hacking, most tend to use the term pen tester, which is short for penetration tester. Pen testers do simply that: penetrate systems like a hacker, but for benign purposes.
As an ethical hacker and future test candidate you must become familiar with the lingo of the trade. Here are some of the terms you will encounter in pen testing:
Hack Value This term describes a target that may attract an above-average level of attention to an attacker. Presumably because this target is attractive, it has more value to an attacker because of what it may contain.
Target of Evaluation (TOE) A TOE is a system or resource that is being evaluated for vulnerabilities. A TOE would be specified in a contract with the client.
Attack This is the act of targeting and actively engaging a TOE.
Exploit This is a clearly defined way to breach the security of a system.
Zero Day This describes a threat or vulnerability that is unknown to developers and has not been addressed. It is considered a serious problem in many cases.
Security This is described as a state of well-being in an environment where only actions that are defined are allowed.
Threat This is considered to be a potential violation of security.
Vulnerability This is a weakness in a system that can be attacked and used as an entry point into an environment.
Daisy Chaining This is the act of performing several hacking attacks in sequence with each building on or acting on the results of the previous action.
As an ethical hacker, you will be expected to take on the role and use the mind-set and skills of an attacker to simulate a malicious attack. The idea is that ethical hackers understand both sides, the good and the bad, and use this knowledge to help their clients. By understanding both sides of the equation, you will be better prepared to defend yourself successfully. Some things to remember about being an ethical hacker are:
- You must have explicit permission in writing from the company being tested prior to starting any activity. Legally, the person or persons that must approve this activity or changes to the plan must be the owner of the company or their authorized representative. If the scope changes, update the contracts to reflect those changes before performing the new tasks.
- You will use the same tactics and strategies as malicious attackers.
- You have every potential to cause harm that a malicious attack will have and should always consider the effects of every action you carry out.
- You must have knowledge of the target and the weaknesses it possesses.
- You must have clearly defined rules of engagement prior to beginning your assigned job.
- You must never reveal any information pertaining to a client to anyone but the client.
- If the client asks you to stop a test, do so immediately.
- You must provide a report of your results and, if asked, a brief on any deficiencies found during a test.
- You may be asked to work with the client to fix any problems that you find.
As an ethical hacker you must agree to the following code of ethics:
- Keep private and confidential information gained in your professional work (in particular as it pertains to client lists and client personal information). Do not collect, give, sell, or transfer any personal information (such as name, e-mail address, social security number, or other unique identifier) to a third party without prior client consent.
- Protect the intellectual property of others by relying on your own innovation and efforts, thus ensuring that all benefits vest with its originator.
- Disclose to appropriate persons or authorities potential dangers to any e-commerce clients, the Internet community, or the public, that you reasonably believe to be associated with a particular set or type of electronic transactions or related software or hardware.
- Provide service in your areas of competence; be honest and forthright about any limitations of your experience and education. Ensure that you are qualified for any project on which you work or propose to work by an appropriate combination of education, training, and experience.
- Never knowingly use software or a process that is obtained or retained either illegally or unethically.
- Do not engage in deceptive financial practices such as bribery, double billing, or other improper financial practices.
- Use the property of a client or employer only in ways properly authorized, and with the owner’s knowledge and consent.
- Disclose to all concerned parties those conflicts of interest that cannot reasonably be avoided or escaped.
- Ensure good management for any project you lead, including effective procedures for promotion of quality and full disclosure of risk.
- Add to the knowledge of the e-commerce profession by constant study, share the lessons of your experience with fellow EC-Council members, and promote public awareness of the benefits of e-commerce.
- Conduct yourself in the most ethical and competent manner when soliciting professional service or seeking employment, thus meriting confidence in your knowledge and integrity.
- Ensure ethical conduct and professional care at all times on all professional assignments without prejudice.
- Do not associate with malicious hackers or engage in any malicious activities.
- Do not purposefully compromise or allow the client organization’s systems to be compromised in the course of your professional dealings.
- Ensure all pen testing activities are authorized and within legal limits.
- Do not take part in any black hat activity or be associated with any black hat community that serves to endanger networks.
- Do not take part in any underground hacking community for purposes of preaching and expanding black hat activities.
- Do not make inappropriate references to the certification or misleading use of certificates, marks or logos in publications, catalogs, documents, or speeches.
- Do not violate any law of the land or have any previous conviction.
Under the right circumstances and with proper planning and goals in mind, you can provide a wealth of valuable information to your target organization. Working with your client, you should analyze your results thoroughly and determine which areas need attention and which need none at all. Your client will determine the perfect balance of security versus convenience. If the problems you uncover necessitate action, the next challenge is to ensure that existing usability is not adversely affected if security controls are modified or if new ones are put in place. Security and convenience often conflict: the more secure a system becomes, the less convenient it tends to be. Figure 1.1 illustrates this point.

FIGURE 1.1 Security versus convenience analysis
A pen test is the next logical step beyond ethical hacking. Although ethical hacking sometimes occurs without a formal set of rules of engagement, pen testing does require rules to be agreed on in advance in every case. If you choose to perform a pen test without having certain parameters determined ahead of time, it may be the end of your career if something profoundly bad occurs. For example, not having the rules established before engaging in a test could result in criminal or civil charges, depending on the injured party and the attack involved. It is also entirely possible that without clearly defined rules, an attack may result in shutting down systems or services and stopping the functioning of a company completely, which again could result in huge legal and other issues for you.
When a pen test is performed it typically takes one of three forms: white box, gray box, or black box. The three forms of testing are important to differentiate between, as you may be asked to perform any one of them at some point during your career, so let’s take a moment to describe each:
Black Box A type of testing in which the pen tester has little or no knowledge of the target. This situation is designed to closely emulate the situation an actual attacker would encounter as they would presumably have an extremely low level of knowledge of the target going in.
Gray Box A form of testing where the knowledge given to the testing party is limited. In this type of test, the tester acquires knowledge such as IP addresses, operating systems, and the network environment, but that information is limited. This type of test would closely emulate the type of knowledge that someone on the inside might have; such a person would have some knowledge of a target, but not always all of it.
White Box A form of testing in which the information given to the tester is complete. This means that the pen tester is given all information about the target system. This type of test is typically done internally or by teams that perform internal audits of systems.
Another way to look at the different types of testing and how they stack up is in Table 1.1.
TABLE 1.1 Available types of pen tests
| Type | Knowledge |
| White box | Full |
| Gray box | Limited |
| Black box | None |
In many cases, you will be performing what is known as an IT audit. This process is used to evaluate and confirm that the controls that protect an organization work as advertised. An IT audit is usually conducted against some standard or checklist that covers security protocols, software development, administrative policies, and IT governance. However, passing an IT audit does not mean that the system is completely secure; in the real world, the criteria for passing an audit may be out of date.
An ethical hacker is trying to preserve what is known as the CIA triad: confidentiality, integrity, and availability. The following list describes these core concepts and what they mean. Keep these concepts in mind when performing the tasks and responsibilities of a pen tester:
Confidentiality The core principle that refers to the safeguarding of information and keeping it away from those not authorized to possess it. Examples of controls that preserve confidentiality are permissions and encryption.
Integrity Deals with keeping information in a format that is true and correct to its original purposes, meaning that the data that the receiver accesses is the data the creator intended them to have.
Availability The final and possibly one of the most important items that you can perform. Availability deals with keeping information and resources available to those who need to use it. Information or resources, no matter how safe and sound, are only useful if they are available when called upon.
Another way of looking at this balance is to observe the other side of the triad and how the balance is lost. Any of the following break the CIA triad:
- Disclosure is the inadvertent, accidental, or malicious revealing or accessing of information or resources to an outside party. If you are not supposed to have access to an object, you should never have access to it.
- Alteration is the counter to integrity; it deals with the unauthorized or other forms of modifying information. This modification can be corruption, accidental access, or malicious in nature.
- Disruption (also known as loss) means that access to information or resources has been lost when it should not have. Information is useless if it is not there when it is needed. Although information or other resources can never be 100-percent available, some organizations spend the time and money to get 99.999-percent uptime, which averages about 6 minutes of downtime per year.
An ethical hacker will be entrusted with ensuring that the CIA triad is preserved at all times and threats are dealt with in the most appropriate manner available (as required by the organization’s own goals, legal requirements, and other needs). For example, consider what could happen if an investment firm or defense contractor suffered a disclosure incident at the hands of a malicious party. The results would be catastrophic.
Hacking Methodologies
A hacking methodology refers to the step-by-step approach used by an aggressor to attack a target such as a computer network. There is no specific step-by-step approach used by all hackers. As can be expected when a group operates outside the rules as hackers do, rules do not apply the same way. A major difference between a hacker and an ethical hacker is the code of ethics to which each subscribes.
The following steps, illustrated in Figure 1.2, typically comprise hacking process.
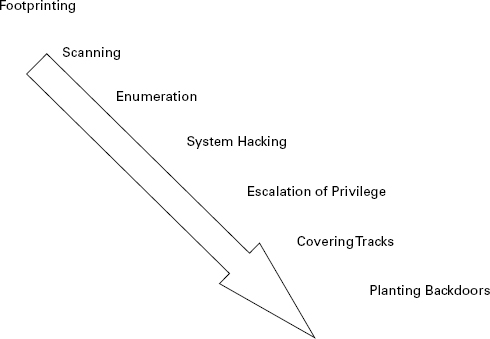
FIGURE 1.2 The hacking process
- Footprinting means that you are using primarily passive methods of gaining information from a target prior to performing the later active methods. Typically, you keep interaction with your target to a minimum to avoid detection, thus alerting the target that something is coming in their direction. A myriad of methods are available to perform this task, such as Whois queries, Google searches, job board searches, and discussion groups. We will examine this topic in Chapter 4, “Footprinting and Reconnaissance.”
- Scanning is the phase in which you take the information gleaned from the footprinting phase and use it to target your attack much more precisely (see Chapter 5, “Scanning Networks”). The idea here is to act on the information from the prior phase, not to blunder around without purpose and set off alarms. Scanning means performing tasks like ping sweeps, port scans, observations of facilities, and other similar tasks. One of the tools you will use is nmap, which is very useful for this purpose.
- Enumeration is the next phase (see Chapter 6, “Enumeration of Services”) where you extract much more detailed information about what you uncovered in the scanning phase to determine its usefulness. Think of the information gathered in the previous phase, walking down a hallway and rattling the doorknobs, taking note of which ones turn and which ones do not. Just because a door is unlocked doesn’t mean anything of use is behind it. In this phase you are looking behind the door to see if there is anything of value behind the door. Results of this step can include a list of usernames, groups, applications, banner settings, auditing information, and other similar information.
- System hacking (Chapter 7, “Gaining Access to a System”) follows enumeration. You can now plan and execute an attack based on the information you uncovered. You could, for example, start choosing user accounts to attack based on the ones uncovered in the enumeration phase. You could also start crafting an attack based on service information uncovered by retrieving banners from applications or services.
- If the hacking phase was successful, then you can start to obtain privileges that are granted to higher privileged accounts than you broke into originally. Depending on your skills at escalation of privilege, it might be possible to move from a low-level account such as a guest account all the way up to administrator or system-level access.
- Covering tracks is the phase when you attempt to remove evidence of your presence in a system. You purge log files and destroy other evidence that might give away the valuable clues needed for the system owner to determine an attack occurred. Think of it this way: If someone were to pick a lock to get into your house versus throwing a brick through the window, the clues are much less obvious in the former than the latter. In the latter case you would look for what the visitor took immediately, and in the former case you might notice the break-in much later, after the trail had gone cold.
- The purpose of planting back doors is to leave something behind that would enable you to come back later if you wanted. Items such as special accounts, Trojan horses, or other items come to mind.
When you decide to carry out this process, seek your client’s guidance and ask the following questions along with any others that you think are relative. During this phase, your goal is to clearly determine why a pen test and its associated tasks are necessary.
- Why did the client request a pen test?
- What is the function or mission of the organization to be tested?
- What will be the constraints or rules of engagement for the test?
- What data and services will be included as part of the test?
- Who is the data owner?
- What results are expected at the conclusion of the test?
- What will be done with the results when presented?
- What is the budget?
- What are the expected costs?
- What resources will be made available?
- What actions will be allowed as part of the test?
- When will the tests be performed?
- Will insiders be notified?
- Will the test be performed as black or white box?
- What conditions will determine the success of the test?
- Who will be the emergency contacts?
Pen testing can take several forms. You must decide, along with your client, which tests are appropriate and will yield the desired results. Tests that can be part of a pen test include the following:
- An insider attack is intended to mimic the actions that may be undertaken by internal employees or parties who have authorized access to a system.
- An outsider attack is intended to mimic those actions and attacks that would be undertaken by an outside party.
- A stolen equipment attack is a type of attack where an aggressor steals a piece of equipment and uses it to gain access or extracts the information desired from the equipment itself.
- A social engineering attack is a form of attack where the pen tester targets the users of a system seeking to extract the needed information. The attack exploits the trust inherent in human nature.
Once you discuss each test, determine the suitability of each, and evaluate the potential advantages and side effects, you can finalize the planning and contracts and begin testing.
Vulnerability Research and Tools
An important part of your toolkit as an ethical hacker will be the information gathered from vulnerability research. This process involves searching for and uncovering vulnerabilities in a system and determining their nature. Additionally, the research seeks to classify each vulnerability as high, medium, or low. You or other security personnel can use this research to keep up to date on the latest weaknesses involving software, hardware, and environments.
The benefit of having this information is that an administrator or other personnel could use this information to position defenses. Additionally, the information may show where to place new resources or be used to plan monitoring.
Vulnerability research is not the same as ethical hacking in that it passively uncovers security issues whereas the process of ethical hacking actively looks for the vulnerabilities.
Ethics and the Law
As an ethical hacker, you need to be aware of the law and how it affects what you will do. Ignorance or lack of an understanding of the law is not only a bad idea, but it can quickly put you out of business—or even in prison. In fact, under some situations the crime may be serious enough to get you prosecuted in several jurisdictions in different states, counties, or even countries due to the highly distributed nature of the Internet. Of course, prosecution of a crime can also be difficult considering the web of various legal systems in play. A mix of common, military, and civil laws exists, requiring knowledge of a given legal system to be successful in any move toward prosecution.
Always ensure that you exercise the utmost care and concern to ensure that you observe proper safety and avoid legal issues. When your client has determined their goals along with your input, the contract must be put in place. Remember the following points when developing a contract and establishing guidelines:
Trust The client is placing trust in you to use the proper discretion when performing a test. If you break this trust, it can lead to the questioning of other details such as the results of the test.
Legal Implications Breaking a limit placed on a test may be sufficient cause for your client to take legal action against you.
The following is a summary of laws, regulations, and directives that you should have a basic knowledge of:
- 1973: U.S. Code of Fair Information Practices governs the maintenance and storage of personal information by data systems such as health and credit bureaus.
- 1974: U.S. Privacy Act governs the handling of personal information by the U.S. government.
- 1984: U.S. Medical Computer Crime Act addresses illegally accessing or altering medication data.
- 1986 (Amended in 1996): U.S. Computer Fraud and Abuse Act includes issues such as altering, damaging, or destroying information in a federal computer and trafficking in computer passwords if it affects interstate or foreign commerce or permits unauthorized access to government computers.
- 1986: U.S. Electronic Communications Privacy Act prohibits eavesdropping or the interception of message contents without distinguishing between private or public systems.
- 1994: U.S. Communications Assistance for Law Enforcement Act requires all communications carriers to make wiretaps possible.
- 1996: U.S. Kennedy-Kassebaum Health Insurance and Portability Accountability Act (HIPAA) (with the additional requirements added in December of 2000) addresses the issues of personal healthcare information privacy and health plan portability in the United States.
- 1996: U.S. National Information Infrastructure Protection Act enacted in October 1996 as part of Public Law 104-294; it amended the Computer Fraud and Abuse Act, which is codified in 18 U.S.C. § 1030. This act addresses the protection of the confidentiality, integrity, and availability of data and systems. This act is intended to encourage other countries to adopt a similar framework, thus creating a more uniform approach to addressing computer crime in the existing global information infrastructure.
- 2002: Sarbanes–Oxley (SOX or SarBox) is a law pertaining to accountability for public companies relating to financial information.
- 2002: Federal Information Security Management Act (FISMA) is a law designed to protect the security of information stored or managed by government systems at the federal level.
Summary
When becoming an ethical hacker, you must develop a rich and diverse skill set and mind-set. Through a robust and effective combination of technological, administrative, and physical measures, organizations have learned to address their given situation and head off major problems through detection and testing. Technology such as virtual private networks (VPNs), cryptographic protocols, intrusion detection systems (IDSs), intrusion prevention systems (IPSs), access control lists (ACLs), biometrics, smart cards, and other devices have helped security become much stronger, but still have not eliminated the need for vigilance. Administrative countermeasures such as policies, procedures, and other rules have also been strengthened and implemented over the past decade. Physical measures include devices such as cable locks, device locks, alarm systems, and other similar devices. Your new role as an ethical hacker will deal with all of these items, plus many more.
As an ethical hacker you must not only know the environment you will be working in, but also how to find weaknesses and address them as needed. You will also need to understand the laws and ethics involved, and you also must know the client’s expectations. Understand the value of getting the proper contracts in place and not deviating from them.
Hacking that is not performed under contract is considered illegal and is treated as such. By its very nature, hacking activities can easily cross state and national borders into multiple legal jurisdictions. Breaking outside the scope of a contract can expose you to legal harm and become a career-ending blunder.
Exam Essentials
Know the purpose of an ethical hacker. Ethical hackers perform their duties against a target system only with the explicit permission of the system owner. To do so without permission is a violation of ethics and the law in some cases.
Understand your targets. Be sure you know what the client looking to gain from a pen test early in the process. The client must be able to provide some guidance as to what they are trying to accomplish as a result of your services.
Know your opponents. Understand the differences between the various types of hackers. What makes a gray-hat hacker different from a black hat is a detail that you should know for the exam, as are the differences between all types.
Know your tools and terms. The CEH exam is drenched with terms and tool names that will eliminate even the most skilled test takers because they simply don’t know what the question is even talking about. Familiarize yourself with all the key terms, and be able to recognize the names of the different tools on the exam.
Review Questions
If you have been contracted to perform an attack against a target system, you are what type of hacker?
- White hat
- Gray hat
- Black hat
- Red hat
Which of the following describes an attacker who goes after a target to draw attention to a cause?
- Terrorist
- Criminal
- Hacktivist
- Script kiddie
What level of knowledge about hacking does a script kiddie have?
- Low
- Average
- High
- Advanced
Which of the following does an ethical hacker require to start evaluating a system?
- Training
- Permission
- Planning
- Nothing
A white box test means the tester has which of the following?
- No knowledge
- Some knowledge
- Complete knowledge
- Permission
Which of the following describes a hacker who attacks without regard for being caught or punished?
- Hacktivist
- Terrorist
- Criminal
- Suicide hacker
Which of the following is the purpose of the footprinting process?
- Entering a system
- Covering tracks
- Escalating privileges
- Gathering information
Which of the following forms are usually malicious?
- Software applications
- Scripts
- Viruses
- Grayware
What is a self-replicating piece of malware?
- A worm
- A virus
- A Trojan horse
- A rootkit
What is a piece of malware that relies on social engineering?
- A worm
- A virus
- A Trojan horse
- A rootkit
Which of the following best describes what a hacktivist does?
- Defaces websites
- Performs social engineering
- Hacks for political reasons
- Hacks with basic skills
Which of the following best describes what a suicide hacker does?
- Hacks with permission
- Hacks without stealth
- Hacks without permission
- Hacks with stealth
Which type of hacker may use their skills for both benign and malicious goals at different times?
- White Hat
- Gray Hat
- Black Hat
- Suicide Attackers
What separates a suicide hacker from other attackers?
- A disregard for the law
- A desire to be helpful
- The intent to reform
- A lack of fear of being caught
Which of the following would most likely engage in the pursuit of vulnerability research?
- White Hat
- Gray Hat
- Black Hat
- Suicide
Vulnerability research deals with which of the following?
- Actively uncovering vulnerabilities
- Passively uncovering vulnerabilities
- Testing theories
- Applying security guidance
How is black box testing performed?
- With no knowledge
- With full knowledge
- With partial knowledge
- By a black hat
A contract is important because it does what?
- Gives permission
- Gives test parameters
- Gives proof
- Gives a mission
What does TOE stand for?
- Target of evaluation
- Time of evaluation
- Type of evaluation
- Term of evaluation
Which of the following best describes a vulnerability?
- A worm
- A virus
- A weakness
- A rootkit
