Chapter 2
System Fundamentals
 I. Background
I. Background
- A. Networking technologies
- C. System technologies
- D. Transport protocols
- G. Telecommunications technologies
- H. Backup and restore
 III. Security
III. Security
- A. Systems security controls
- B. Application/fileserver
- C. Firewalls
- E. Network security
- O. Trusted networks
- P. Vulnerabilities
 IV. Tools/Systems/Programs
IV. Tools/Systems/Programs
- G. Boundary protection appliances
- H. Network topologies
- I. Subnetting
- K. Domain Name System (DNS)
- L. Routers/modems/switches
- O. Operating environments
 V. Procedures/Methodology
V. Procedures/Methodology
- G. TCP/IP networking
Every skill set comes with a history of time and effort spent learning those foundational concepts that allow you to become proficient in a specific area. You are about to embark on a journey through one of those critical areas where understanding and true investment in the material can improve your technical understanding, your career, and your odds of passing the CEH exam. This is where it all begins—understanding those key fundamental concepts that give you a basis on which all other more complex subjects can firmly rest.
In this chapter we’ll delve into some basic concepts, most of which system administrators and network administrators should be comfortable with. These fundamentals are critical to building a solid base for the more advanced topics yet to come. We’ll take a step-by-step walk-through on key concepts such as the OSI model, the TCP/IP suite, subnetting, network appliances and devices, cloud technologies, and good old-fashioned client system concepts and architectures. Ever hear the phrase “where the rubber hits the road”? Well, consider this a burnout across a quarter-mile drag strip. Let’s dig in and devour this material!
Exploring Network Topologies
Whether you are a veteran or a novice—or just have a bad memory—a review of networking technologies is helpful and an important part of understanding the attacks and defenses we’ll explore later on.
Network topologies represent the physical side of the network, and they form part of the foundation of our overall system. Before we explore too far, the first thing you need to understand is that you must consider two opposing yet related concepts in this section: the physical layout of the network and the logical layout of the network. The physical layout of a network relates directly to the wiring and cabling that connects devices. Some of the common layouts we’ll cover are the bus, ring, star, mesh, and hybrid topologies. The logical layout of the network equates to the methodology of access to the network, the stuff you can’t readily see or touch, or the flow of information and other data. We’ll get to the logical side, but first let’s break down each physical design:
Bus The bus topology (Figure 2.1) lays out all connecting nodes in a single run that acts as the common backbone connection for all connected devices. As with the public transport of the same name, signals get on, travel to their destination, and get off. The bus is the common link to all devices and cables. The downside to its simplicity is its vulnerability; all connectivity is lost if the bus backbone is damaged. The best way to envision this vulnerability is to think of those strings of Christmas lights that go completely out when one light burns out or is removed. Although not seen in its purest form in today’s networks, the concept still applies to particular segments.
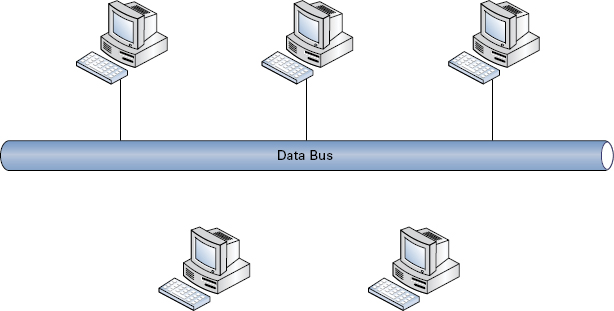
FIGURE 2.1 Bus topology
Ring Ring topologies (Figure 2.2) are as true to their names as bus layouts. Essentially the backbone, or common connector of the network, is looped into a ring; some ring layouts use a concentric circle design to provide redundancy if one ring fails. Each client or node attaches to the ring and delivers packets according to its designated turn or the availability of the token. As you can see in Figure 2.2, a concentric circle design provides redundancy; though a good idea, a redundant second ring is not required for the network to function properly. The redundant ring architecture is typically seen in setups that use Fiber Distributed Data Interface (FDDI).
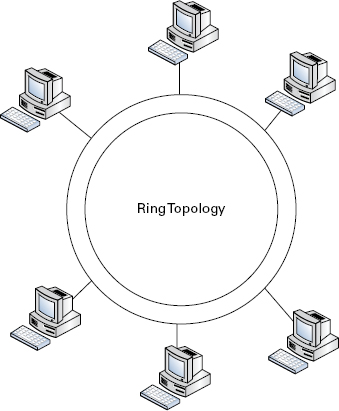
FIGURE 2.2 Ring topology
Star The star layout (Figure 2.3) is one of the most common because of its ease of setup and isolation of connectivity problems should an issue arise. A star topology attaches multiple nodes to a centralized network device that ties the network together. Think of it as looking like an old-style wagon wheel or the wheels on a bike. The hub is the centerpiece of the wheel, and the spokes of the wheel are the legs of the star. The center could be a hub or a switch; as long as it acts as a central point of connection, you have a star topology. Stars are popular for numerous reasons, but the biggest reason has long been its resistance to outages. Unlike nodes in bus and ring topologies, a single node of a star can go offline without affecting other nodes.
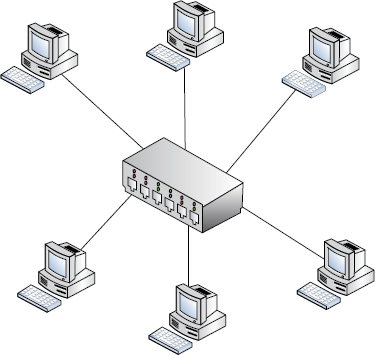
FIGURE 2.3 Star topology
Mesh A mesh topology (Figure 2.4) is essentially a web of cabling that attaches a group of clients or nodes to each other. It can look a little messy and convoluted, and it can also make troubleshooting a bear. However, this setup is often used for mission-critical services because of its high level of redundancy and resistance to outages. The largest network in the world, the Internet, which was designed to survive nuclear attack, is built as one large mesh network.
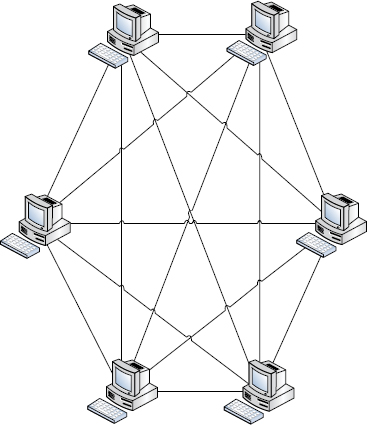
FIGURE 2.4 Mesh topology
Hybrid Hybrid topologies are by far the most common layout in use today. Rarely will you encounter a pure setup that strictly follows the topologies previously listed. Our networks of today are complex and multifaceted. More often than not, current networks are the offspring of many additions and alterations over many years of expansion or logistical changes. A hybrid layout combines different topologies into one mixed topology; it takes the best of other layouts and uses them to its advantage. Figure 2.5 shows one possibility.
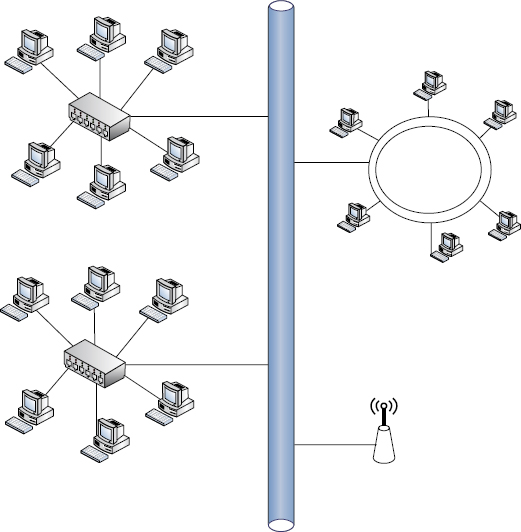
FIGURE 2.5 Hybrid topology
Working with the Open Systems Interconnection Model
No network discussion or network device explanation would be complete without a brief overview of the Open Systems Interconnection (OSI) model. Although this model may seem overly complex, it does have value in our later discussions of attacks, defenses, and infrastructure, as you will see. The OSI model is a general framework that enables network protocols, software, and systems to be designed around a general set of guidelines. Common guidelines allow higher probability of system compatibility and logical traffic flow. In other words, if we all play by the same rules everyone will get along with as few errors as possible.
The OSI model, shown in the left side of Figure 2.6, has seven layers. As you read through each layer’s function, keep in mind that we are working our way through how data flows. Each layer is connected to the next; this concept will prove valuable as a reference for more advanced data analysis.
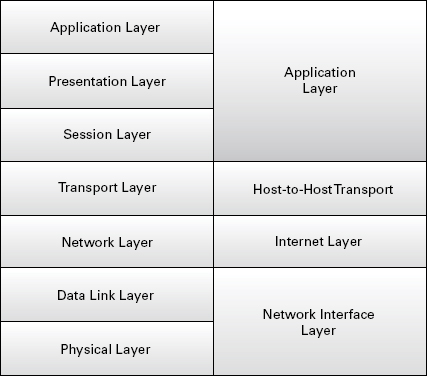
FIGURE 2.6 OSI TCP/IP comparative model
Layer 1: Physical The physical layer consists of the physical media and dumb devices that make up the infrastructure of our networks. This pertains to the cabling and connections such as Category 5e and RJ-45 connectors. Note that this layer also includes light and rays, which pertain to media such as fiber optics and microwave transmission equipment. Attack considerations are aligned with the physical security of site resources. Although not flashy, physical security still bears much fruit in penetration (pen) testing and real-world scenarios.
Layer 2: Data Link The data link layer works to ensure that the data it transfers is free of errors. At this layer, data is contained in frames. Functions such as media access control and link establishment occur at this layer. This layer encompasses basic protocols such as 802.3 for Ethernet and 802.11 for Wi-Fi.
Layer 3: Network The network layer determines the path of data packets based on different factors as defined by the protocol used. At this layer we see IP addressing for routing of data packets. This layer also includes routing protocols such as the Routing Information Protocol (RIP) and the Interior Gateway Routing Protocol (IGRP). This is the know-where-to-go layer.
Layer 4: Transport The transport layer ensures the transport or sending of data is successful. This function can include error checking operations as well as working to keep data messages in sequence. At this layer we find the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP).
Layer 5: Session The session layer identifies established system sessions between different network entities. When you access a system remotely, for example, you are creating a session between your computer and the remote system. The session layer monitors and controls such connections, allowing multiple, separate connections to different resources. Common use includes NetBIOS and RPC.
Layer 6: Presentation The presentation layer provides a translation of data that is understandable by the next receiving layer. Traffic flow is presented in a format that can be consumed by the receiver and can optionally be encrypted with protocols such as Secure Sockets Layer (SSL).
Layer 7: Application The application layer functions as a user platform in which the user and the software processes within the system can operate and access network resources. Applications and software suites that we use on a daily basis are under this layer. Common examples include protocols we interact with on a daily basis, such as FTP and HTTP.
Two mnemonics that I use to remember the order of layers are:
- All People Seem To Need Data Processing which uses the first letter of each layer as the first letter of each word in the sentence: Application, Presentation, Session, Transport, Network, Data Link, Physical.
- Please Do Not Teach Stupid People Acronyms, which does the layers in the opposite order—that is, from the ground up.
Knowing the order and numbers of these layers will be useful during your exploration and exam.
Dissecting the TCP/IP Suite
Complementary to the OSI model is the TCP/IP protocol suite. TCP/IP is not necessarily a direct offshoot, but it’s a progressive step from the standard OSI version of traffic flow. Each layer of the TCP/IP suite maps to one or several layers of the OSI model. The TCP/IP suite is important for protocol reference as well as aiding in tracking exactly where data is in the traffic flow process. The right side of Figure 2.6 earlier in this chapter shows the TCP/IP suite layers and how they map to the OSI model.
TCP is known as a connection-oriented protocol because it establishes a connection and verifies that packets sent across that connection make it to their destination. The process (see Figure 2.7) starts with what is called a SYN packet. This SYN packet starts the handshake process by telling the receiving system that another system wants its attention (via TCP of course). The receiving system then replies to the originating system with a SYN-ACK response. A SYN-ACK response is an acknowledgment response to the original SYN packet. Once the original sender receives the SYN-ACK response, it in turn responds with an ACK packet to verify that it has received the SYN-ACK and is ready to communicate via TCP. Wow! Really, it’s not that complicated.
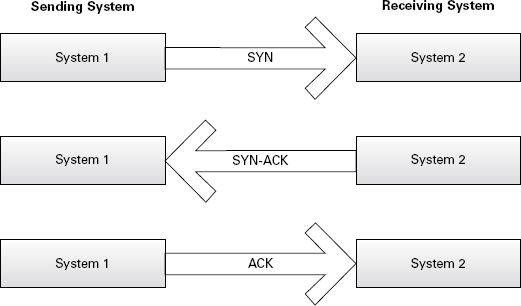
FIGURE 2.7 TCP three-way handshake
TCP packet sequence numbers are important both for the exam and for understanding attacks such as session hijacking and man-in-the-middle (MITM) exploits. You’ll see how this comes into play in Chapter 12, “Session Hijacking.” For now keep in mind how TCP works and how it uses sequence and acknowledgment numbers to guarantee data delivery.
For example, a SYN packet has a random beginning sequence number that will be sent to the target host. Upon receipt of the SYN packet, the receiving host will respond with a SYN-ACK that has its own randomized sequence number. The ACK response packet from the first host will bump the sequence number up accordingly to signify the order of the packets being transferred. Figure 2.8 shows the sequence numbers.
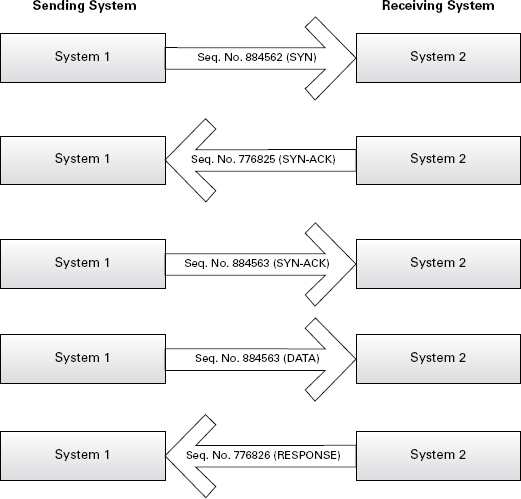
FIGURE 2.8 TCP sequencing
IP Subnetting
So far we’ve established the basics through an overview of the OSI model layers and the common network topologies. Let’s get a little deeper into the network layer and look at IP addressing and its subnetting capabilities. Our goal here is to flex those subnetting muscles and get our brains back to thinking about networking and its underlying nuances. Why? Well, if you can subnet you can pinpoint a target and know how to go after it in the most efficient and effective way.
Subnetting is the logical breakdown of a network address space into progressively smaller subnetworks. That’s it. Stop thinking and take it for what it is! Now, as you break down your address space into smaller subnetworks, you determine the numbers of network bits and host bits by the requirements of your network. Network bits and host bits are manipulated by the subnet mask. At this point I’m hoping you’re saying to yourself, “Oh yeah, I remember this stuff.” If not, please dig into the details on your own. We are looking at this topic in terms of how it will aid our effort as hackers.
Now that you grasp the basics of the subnet mask and how to use it to manipulate the address space, you can see how knowing a few IP addresses can give you a clue as to how an organization’s network is laid out. There’s more to come on this topic, but as a quick example, knowing a single internal IP address can give a hacker much insight into the company’s addressing scheme.
Hexadecimal vs. Binary
Understanding hexadecimal and binary conversion is an important skill to have for the exam. In the real world, for most network administrators conversion is done either by a calculator or is not needed, but as an ethical hacker, you have opportunities to apply the basic conversions to something useful. See Table 2.1 for the basic conversion between hex, binary, and decimal.
TABLE 2.1 Hex, binary, and decimal
| Hex | Binary | Decimal |
| 0 | 0000 | 0 |
| 1 | 0001 | 1 |
| 2 | 0010 | 2 |
| 3 | 0011 | 3 |
| 4 | 0100 | 4 |
| 5 | 0101 | 5 |
| 6 | 0110 | 6 |
| 7 | 0111 | 7 |
| 8 | 1000 | 8 |
| 9 | 1001 | 9 |
| A | 1010 | 10 |
| B | 1011 | 11 |
| C | 1100 | 12 |
| D | 1101 | 13 |
| E | 1110 | 14 |
| F | 1111 | 15 |
This should be a refresher for you, but for the exam it is important that you have a comfortable understanding of the conversion process. To rehash some of the basics, remember that bits are 1s and 0s, a nibble is 4 bits, and a byte is 2 nibbles. Your knowledge and ability to apply this across the conversion process will prove important for questions that expect you to identify network items and traffic based on hexadecimal values.
Exploring TCP/IP Ports
We can’t let you escape the fundamentals without touching on ports. Ports allow computers to send data out the door while simultaneously identifying that data by category. What this means is each of the common ports you use is associated with a particular protocol or particular application. For example, sending data from port 21 signifies to the receiving system that the traffic received is an FTP request because of the port it came from. Additionally, the response from the initially queried system will end up at the right location because the port from which the traffic came has already been identified. This holds true for web traffic, mail traffic, and so forth. Knowledge of these ports and their corresponding protocols and applications becomes important when you’re scanning a system for specific vulnerabilities. There will be more to come on that, but first let’s take a look at how these ports are categorized and what the well-known ones mean to you:
- Well-known ports are most common in daily operations and range from 1 to 1024. Much of the initial portion of this range should be familiar to you. Refer to Table 2.2 for a list of the ports you need to know.
TABLE 2.2 Well-known ports
Port Use 20–21 FTP 22 SSH 23 Telnet 25 SMTP 42 WINS 53 DNS 80, 8080 HTTP 88 Kerberos 110 POP3 111 Portmapper - Linux 123 NTP 135 RPC-DCOM 139 SMB 143 IMAP 161, 162 SNMP 389 LDAP 445 CIFS 514 Syslog 636 Secure LDAP - Registered ports range from 1025 to 49151. Registered ports are those that have been identified as usable by other applications running outside of the user’s present purview. An example would be port 1512, which supports Windows Internet Name Service (WINS) traffic. Take a look at Table 2.3 for a list of registered ports of interest.
TABLE 2.3 Registered ports of interest
Port Use 1080 Socks5 1241 Nessus Server 1433, 1434 SQL Server 1494, 2598 Citrix Applications 1521 Oracle Listener 2512, 2513 Citrix Management 3389 RDP 6662–6667 IRC - Dynamic ports range from 49152 to 65535. These are the free ports that are available for any TCP or UDP request made by an application. They are available to support application traffic that has not been officially registered in the previous range.
Domain Name System
Don’t want to remember all those IP addresses? Well, you don’t have to thanks to the Domain Name System (DNS) and its ability to translate names to IP addresses and back. The DNS that you may already be aware of, even if you don’t actively think about it, is the one used to translate names to IPs on the Internet. DNS is incredibly powerful and easy to use, but at the end of the day it is simply a database that contains name-to-IP mappings that can be queried by any DNS-aware applications.
The Internet root servers, or top-level servers, include the addresses of the DNS servers for all of the top-level domains, such as .com and .org. Each top-level server contains a DNS database of all the names and addresses in that domain.
Local networks that are isolated from the Internet may use their own domain name systems. These translate only the names and addresses that are on the local network. They often use DNS management software and protocols, which are similar or identical to those used by the Internet implementation.
Understanding Network Devices
We’ve covered the basic design fundamentals of common local area network layouts. Now let’s fill in the gaps by exploring those common networking devices that you typically see in a larger network setup.
Routers and Switches
Routers and switches are integral to the successful operation of nearly all of today’s modern networks. For that matter, many of our home networks are now advancing to their own local routing and switching capabilities not seen in homes just a decade ago. Remember that routers connect networks and that switches simply create multiple broadcast domains. Yes, back to the good stuff indeed, but don’t shy away just yet; concepts such as broadcast domains will play a large part in our more interesting endeavors, such as sniffing and packet capturing. A solid understanding of the functions of routers and switches will give you a substantial edge when spying out goodies on a network (authorized spying of course!).
Routers
Let’s begin with routers. Our aim here is to give you a firm understanding of the basic functions of routers, so you’ll use this knowledge for more complex hacking techniques and tools. A quick overview of the fundamentals: a router’s main function is to direct packets (layer 3 traffic) to the appropriate location based on network addressing. Because routers direct traffic at the network layer, they are considered layer 3 devices. When talking about routers, we are talking about common protocols such as IP—that is, we are dealing with IP addressing. Routers are also used as a gateway between different kinds of networks, such as networks on different IP ranges or networks that don’t understand each other’s protocol. For example, in an enterprise or business setup, it’s not possible to jam a fiber-run T1 connection into a client computer and expect to have blazingly fast network speeds. The computer, or more accurately the network interface card (NIC), is not capable of speaking the same language as the outside connection. Routers bridge that gap and allow the different protocols on different networks to communicate.
Routers also use Network Address Translation (NAT). This is an extremely useful technology that allows internal network clients to share a single public IP address for access to the outside world. Essentially a router has two interfaces: one for the outside world and one for the internal network. The outside connection, or the public side, is assigned a public IP address purchased from a local Internet service provider (ISP). The internal side of the router is connected to your local intranet, which contains all of your internal IPs and your protected resources. From the internal side you are free to create any IP scheme you want because it’s internal to your site. When an internal client then makes a request for an outside resource, the router receives that traffic and sends it out the public side with its public IP. This process safeguards the internal client’s IP address and also funnels all outbound requests through the same public IP. Because NAT is so common these days, you rarely notice that it’s actually occurring.
Switches
Switches deliver data (frames) based on the hardware addresses of the destination computers or devices. Hardware addresses, also called media access control (MAC) addresses, are permanent identifiers burned into each NIC by the manufacturer. MAC addresses are broken down into a six-pair hexadecimal value—for example, c0-cb-38-ad-2b-c4. The first half of the MAC is specific to the manufacturer. So, in this case the c0-cb-38 identifies the vendor. The ad-2b-c4 identifies the device or NIC itself. Switches are considered layer 2 devices because they operate just one level below the layer 3 router functions. Remember, layer 3 is the network layer. The network layer contains all the IP addressing; layer 2 deals strictly with MAC addresses (see Exercise 2.1). Note that quite a few switches are available today that operate at both layer 2 and layer 3, but for simplicity’s sake, and for our purposes, switches are at layer 2.
Working with MAC Addresses
To extend our conversation on switches a bit further, let’s take a quick peek at broadcast domains and collision domains since this concept will directly impact our network scanning capabilities. A broadcast domain simply means that traffic sent across the wire will be broadcast to all hosts or nodes attached to that network. Address Resolution Protocol (ARP) requests, which are sent to the network to resolve hardware addresses, are an example of broadcast traffic. Collision domains are network segments in which traffic sent will potentially collide with other traffic. In a collision domain, data sent will not be broadcast to all attached nodes; it will bump heads with whatever other traffic is present on the wire. So what this means is that when you throw your little penetration testing laptop on a wire and connect to a switch, you need to be aware that no matter how promiscuous your NIC decides to be, your captured traffic will be limited to the collision domain (aka switchport) you are attached to.
With the explosion of wireless routers and switches that have flooded the market in the last decade, sniffing has regained some of its prowess and ease. Sniffing a Wi-Fi network captures traffic from all of its clients; it is not limited to a particular switchport collision domain. A simple utility and a laptop can pull in some amazingly useful data.
Proxies and Firewalls
No network device discussion would be complete without delving into the world of proxies and firewalls. These devices are the bread and butter of ethical hackers in that they are the devices deliberately put in place to prevent unauthorized access. To test the strength of an organization’s perimeter is to ensure that their perimeter gate guard is alive and well.
Proxies
Proxy servers work in the middle of the traffic scene. You may have been exposed to the forwarding side of proxies; for example, your browser at work may have been pointed to a proxy server to enable access to an outside resource such as a website. There are multiple reasons to implement such a solution. Protection of the internal client systems is one benefit. Acting as an intermediary between the internal network client systems and outside untrusted entities, the proxy is the only point of exposure to the outside world. It prevents the client system from communicating directly with an outside source, thereby reducing exposure and risk. Additionally, as the middleman the proxy has the capability of protecting users (client systems) from themselves. In other words, proxies can filter traffic by content. This means proxies operate at the application layer (layer 7).
A substantial leg up on lower-level firewalls, proxies can filter outgoing traffic requests and verify legitimate traffic at a detailed level. Thus, if users try to browse to, say, hackme.com, they’ll be denied the request completely if the filters are applied to prevent it. Proxies also speed up browsing by caching frequently visited sites and resources. Cached sites can be served to local clients at a speed much faster than downloading the actual web resource.
Firewalls
The firewall category includes proxy firewalls; however, because of a proxy’s varied functions it seems appropriate to give them their own subsection. Firewalls are most commonly broken down into the following main categories:
- Packet filtering
- Stateful packet filtering
- Application proxies, which we covered earlier
Packet filtering firewalls look at the header information of the packets to determine legitimate traffic. Rules such as IP addresses and ports are used from the header to determine whether to allow or deny the packet entry. Stateful firewalls, on the other hand, determine the legitimacy of traffic based on the state of the connection from which the traffic originated. For example, if a legitimate connection has been established between a client machine and a web server, then the stateful firewall refers to its state table to verify that traffic originating from within that connection is vetted and legitimate.
Intrusion Prevention and Intrusion Detection Systems
Intrusion prevention systems (IPSs) and intrusion detection systems (IDSs) are important considerations for any smart hacker. It is important for you, as a hacker, to cover your tracks and keep a low profile—as in no profile at all. It should be common sense, but consider this: If instead of tiptoeing around a network, you slam the network with ARP requests, ping sweeps, and port scans, how far do you think you’ll get? Exactly! Not far at all. IPSs and IDSs are network appliances put in place to catch the very activity that serves our purposes best. The key is to walk lightly, but still walk. First let’s familiarize ourselves with IPS and IDS basics; if you know how something works, you can also learn how to circumvent its defenses.
The goal of an IDS is to detect any suspicious network activity. The keyword here is detect. An IDS is passive in nature; it senses a questionable activity occurring and passively reacts by sending a notification to an administrator signifying something is wrong. Think of it as a burglar alarm. While a burglar alarm alerts you that a burglar is present, it does not stop the burglar from breaking in and stealing items from you. Although such an appliance is passive, the benefit of using it is being able to reactively catch potentially malicious network activity without negatively impacting the operation of the network as a whole. The obvious drawback is that the only response such an appliance creates is a notification. IPSs, on the other hand, are proactive and preventive. Not only does an IPS sense potential malicious activity on the network, it also takes steps to prevent further damage and thwart further attacks.
Network Security
Many books deal with network security, but here we focus on what hackers can use. Firewalls and IDS/IPS appliances are part of a secure network, but in this section we’ll look briefly at the placement and functional value of each device. As you venture through the details, keep in mind that securing a network is a holistic process; breaking into a network, on the other hand, is a focused process. Consider it akin to building a dam. As the engineer of a dam, you must consider the integrity of the entire structure and plan accordingly. If you are looking to sabotage the dam, then all it takes is just one little poke in the right place and it all comes flooding down. The same is true with network security.
Taking our fundamental knowledge of firewalls, whether proxy or network, let’s look at some basic placement strategies that are commonly used in today’s networks.
Figure 2.9 is a basic setup you’ll run into in nearly every household setup today. Of course this isn’t necessarily the enterprise-level network you’ll be attacking, but this basic layout still encompasses the ingredients of the vulnerable points of larger layouts. The purpose of including this design is to give you an idea of how closely it relates to our larger network.
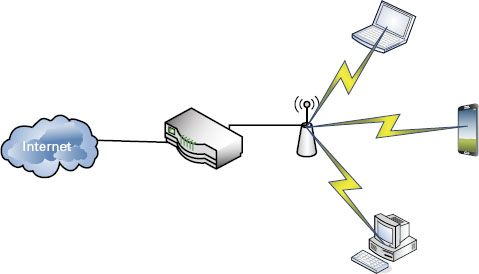
FIGURE 2.9 Residential network setup
Now that we’ve pushed past the basic vulnerabilities of our homegrown residential wireless setup, let’s dive right into a full-blown enterprise example. The enterprise environment we’ll be tasked with pen testing is similar to the one in Figure 2.10.
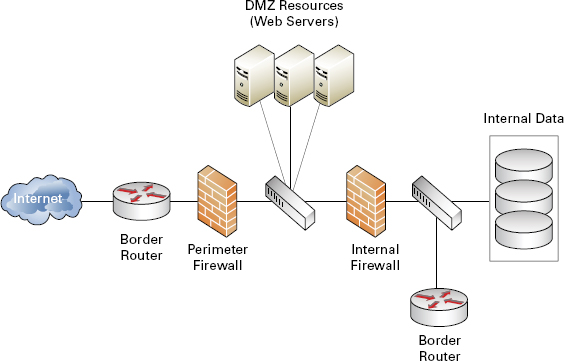
FIGURE 2.10 Typical enterprise network
As you can see, there are layers of protection to keep unauthorized visitors from perusing the internal network. A layered defense applies multiple levels (layers) of defensive roadblocks in hopes a hacker will get stuck midstream. Not all organizations have the funds to install such a solution, nor do they have personnel on hand properly trained to stay up to date and configure the protective appliances properly. A $10,000 firewall is only as good as the administrator maintaining it. Additionally, as ethical hackers we can rely on a wonderful variable for vulnerability generation: our beloved users.
Knowing Operating Systems
We’ll say more about operating systems when we discuss scanning and enumeration, but for now we are interested in laying out the fundamentals of each of the common OSs on the market today. Remember Achilles from Greek mythology? The hero who got shot in the heel and died because of it? Granted, this is an oversimplification of the total story, but the point is when attacking or pen testing a client’s network you must find the Achilles heel. We are not necessarily going to continually hammer away at a world-class firewall solution, or attempt to attack a back-end database server directly. We are going to find that one unpatched client system or web server running an antiquated Internet Information Services (IIS) version. What does all this banter have to do with operating systems? Operating systems offer some common vulnerabilities if not configured properly by the administrator, and as surprising as it may seem, quite a few organizations are running a fresh-out-of-the-box copy of an OS.
Windows
Although there are many different operating systems, in all likelihood it will be a flavor of Microsoft’s Windows OS that you will test against. There are other OSs in the wild that have a certain amount of enterprise market presence, but Microsoft still has a massive foothold on the OS market. By the end of 2013, Windows was the installed OS of choice for over 90 percent of the market. That’s a pretty big target! Let’s take a look at some common vulnerabilities of this market dominator:
- Patches, patches, and more patches. Microsoft, being an OS juggernaut, constantly compiles and distributes patches and service packs for their operating systems. But those patches may not get installed on the systems that need them most. As strange as it may seem, constant updating may in itself become a problem. It is not uncommon for a patch or update to be applied and introduce other problems that may be worse than the original.
- Major version releases and support termination impact Windows products. Yes, I have friends who still love their Windows 98 machines. What this translates into is a system with multiple vulnerabilities simply due to age, especially if that system is no longer supported by the manufacturer.
- Attempts at consumer friendliness have been a tough road for Microsoft. What this means is most installations deploy default configurations and are not hardened. For example, ports that a user may never use are left sitting open just in case a program requires them in the future.
- Administrator accounts still remain a tempting target. Admittedly, Microsoft has taken some effective steps in protecting users from unwanted or suspicious code execution, but quite a few systems exist that are consistently running admin accounts without any kind of execution filtering or user account control.
- Passwords also remain a weak point and a tempting target in the Windows world. Weak admin account passwords are common on Windows computers and networks; although these passwords are controlled by Group Policy in an enterprise environment, there are ways to circumvent these requirements, and many system admins do just that.
- Disabling Windows Firewall and virus protection software is an ongoing issue for Windows OSs. The Notification Center does notify the user of the lack of virus protection or a disabled firewall, but that’s as far as it goes. Granted, it’s not something that can be mandated easily, so proper virus protection remains a vulnerability in the Windows category.
Mac OS
Apple and its proprietary OS are making a larger and larger market presence, boosted by a strong advertising campaign and easy-to-use products. Just a few years ago Apple made an official statement regarding its company status as not a computer manufacturer but an electronics company. Regardless of how Apple classifies itself, the fact remains that more and more Apple products are making their way not just to the local Starbucks but into enterprise settings. In one company I worked for recently, it started with the iPhone. Then all of sudden we started seeing iPads walking down the halls. Then iMac desktops suddenly started appearing on users’ desks. Can they be classified as toys? Perhaps, but of greatest importance to both system admins and pen testers is that these things are attached to the network.
One interesting site that can be used for general comparison of system vulnerabilities is www.cvedetails.com. A quick perusal of the site for Max OS vulnerabilities brings up quite a list, such as the following. We intend no Apple bashing, but it’s a definite growing concern for enterprise administrators and a growing target for hackers like us.
- A primary concern among Mac users, and a benefit to the hacking community, is the Mac owner mind-set that Macs aren’t susceptible to viruses or attack. It is an interesting stance considering that the thing they are claiming to be naturally impervious from attack is, well, a computer! Even in my own painful years as a system administrator, the culture is similar even at the enterprise level. I remember calling our national office for guidance on group policies for our newly acquired Apple desktops. Answer: “Um, well, we don’t have any policies to apply or a method of applying them.”
- Feature-rich out-of-the-box performance for many Apples creates quite a juicy attack surface for those looking to break in. Features such as 802.11 wireless and Bluetooth connectivity are all standard in an out-of-the-box installation, and such features are all on the table for a potential doorway in.
- Apple devices simply don’t play well on a Windows domain. Yep, I said it. I’m sure some would fervently disagree, but Apple on a Windows domain is like spreading butter on toast outside in December in Grand Forks, North Dakota. Some features will play nicely, but the majority of those integral features will be a bit hokey. The point here is when stuff begins to get too hokey, administrators and users alike will begin to circumvent the normal processes (for example, appropriate login procedures).
Linux
Enter our open source favorite, Linux, which is not a completely foolproof operating system but one with a reputation for being a much more secure player in the OS category than Windows or Apple. As we saw with firewalls, the equipment—or in this case the operating system—is only as secure as the administrator configuring it. With Linux, this is particularly true because the OS does expect users to know what they are doing.
The OS has done a good job of separating administrative tasks from user accounts. Linux users aren’t usually running under the administrative account as superuser or root. This substantially reduces system risk by segregating these functions.
Open source is a double-edged sword. The open source community works hard to ferret out even the smallest issue in different iterations of Linux, but open source also means it’s open. Anybody and everybody are privy to the source code. Because it is open source, Linux is almost always in a beta format to one degree or another. With constant work being done on each release, the beta testers of these releases end up being you and me.
Backups and Archiving
Backing up data is essential to the survival and continuation of integral operations. Anyone in the support field who has spent an entire weeknight restoring a server can attest to this. Let’s cover a few of the basic backup schemes you’ll see in the wild.
Full Backup A full backup resets the archive bit of all files and backs them up accordingly.
Differential Backup This backs up all changed files since the last successful full backup. This job does not reset the archive bit. The reasoning behind not resetting the archive bit? Each differential is always based on the last full backup. Thus, any changes made since that last full backup are backed up...and backed up...and backed up. The benefit to this scheme is that during a full restore, only the last full backup and the most recent differential are needed to restore the entire site. The downside is that differentials can get huge!
Incremental Backup This job backs up all changed files since the last successful full backup, or since the last incremental. An incremental backup does reset the archive bit. What this equates to is a backup scheme that focuses on efficiency in the initial process. How? Once an incremental scheme has performed an incremental backup based on the last full, it bases all subsequent backups on the last incremental. In other words, you get a bunch of small backup jobs, all with the most recent changes. What this translates into is a tedious and lengthy full restoration job. The last full backup will need to be restored, as well as all the incrementals up to the current date.
Summary
Two complementary yet opposing concepts are at play when talking about network topologies: logical topology (how traffic enters the network) and physical topology. Common physical topologies are the bus, ring, star, mesh, and hybrid (the most common). A token can be passed around for permission to transmit, or a shared media strategy can be used in which nodes listen for an opening.
The OSI model is an industry standard for data communication. It is broken into seven layers: application, presentation, session, transport, network, data link, and physical. The OSI model is linear in design; data travels from one end to the other, and each layer communicates with the next. The TCP/IP protocol suite is an updated and more applicable framework. Protocols operate as either connection oriented or connectionless; TCP is a connection-oriented protocol and uses the three-way-handshake (SYN, SYN-ACK, ACK) in an effort to guarantee delivery.
Knowledge of subnetting—a sequential breakdown of IP addresses based on desired network size and host quantity—and of common TCP/IP port numbers can aid you in determining where to search first.
Routers work at layer 3 by directing packets and connecting different networks. Switches create a collision domain for each port; broadcast domains allow traffic to be broadcast to all connected nodes. Proxies work at the application layer and can be used for caching and filtering of web content. Proxy firewalls can be detailed in what they filter. A packet filtering firewall looks only at the header of the packet; a stateful firewall verifies a legitimate connection between client and host to prove that traffic is legitimate. IPSs are active and work to prevent further damage when unauthorized activity is sensed on the network. IDSs simply detect and report.
The main operating systems to be considered are Windows (easily the largest attack surface), Mac OS, and Linux. Backups and archiving are both critical and detrimental to a company’s operations. The three kinds of backup schemes are full, differential, and incremental.
Exam Essentials
Know the OSI model. Ensure that you have a good understanding of the OSI model and what actions take place at each layer. It is also a good idea to have a general idea of which protocols operate at which layers.
Know the TCP/IP three-way handshake. Know what each flag does within the handshake process: SYN (start), SYN-ACK (acknowledge start), ACK (acknowledge the acknowledgment).
Memorize the ports. Absolutely know your ports! This is where memory does come into play. Ports are important for the exam and especially for scanning and enumeration. Remember that Windows systems respond to scans whereas Linux systems don’t.
Understand how switches work. Be sure to understand switch operation, and know their limitations in terms of sniffing. Be familiar with ARP and what it accomplishes.
Know the purpose of firewalls, IDSs, and IPSs. Remember that IDSs are passive and IPSs are active.
Remember the benefits and weaknesses of backup schemes. Focus on the end result of each type of backup, not on the details of how to perform one.
Review Questions
At which layer of the OSI model does a proxy operate?
- Physical
- Network
- Data link
- Application
If a device is using node MAC addresses to funnel traffic, what layer of the OSI model is this device working in?
- Layer 1
- Layer 2
- Layer 3
- Layer 4
Which OS holds 90 percent of the desktop market and is one of our largest attack surfaces?
- Windows
- Linux
- Mac OS
- iOS
Which port uses SSL to secure web traffic?
- 443
- 25
- 23
- 80
What kind of domain resides on a single switchport?
- Windows domain
- Broadcast domain
- Secure domain
- Collision domain
Which network topology uses a token-based access methodology?
- Ethernet
- Star
- Bus
- Ring
Hubs operate at what layer of the OSI model?
- Layer 1
- Layer 2
- Layer 3
- Layer 4
What is the proper sequence of the TCP three-way-handshake?
- SYN-ACK, ACK, ACK
- SYN, SYN-ACK, ACK
- SYN-SYN, SYN-ACK, SYN
- ACK, SYN-ACK, SYN
Which of these protocols is a connection-oriented protocol?
- FTP
- UDP
- POP3
- TCP
A scan of a network client shows that port 23 is open; what protocol is this aligned with?
- Telnet
- NetBIOS
- DNS
- SMTP
What port range is an obscure third-party application most likely to use?
- 1 to 1024
- 1025 to 32767
- 32768 to 49151
- 49152 to 65535
Which category of firewall filters is based on packet header data only?
- Stateful
- Application
- Packet
- Proxy
An administrator has just been notified of irregular network activity; what appliance functions in this manner?
- IPS
- Stateful packet filtering
- IDS
- Firewall
Which topology has built-in redundancy because of its many client connections?
- Token ring
- Bus
- Hybrid
- Mesh
When scanning a network via a hardline connection to a wired-switch NIC in promiscuous mode, what would be the extent of network traffic you would expect to see?
- Entire network
- VLAN you are attached to
- All nodes attached to the same port
- None
What device acts as an intermediary between an internal client and a web resource?
- Router
- PBX
- VTC
- Proxy
Which technology allows the use of a single public address to support many internal clients while also preventing exposure of internal IP addresses to the outside world?
- VPN
- Tunneling
- NTP
- NAT
What network appliance senses irregularities and plays an active role in stopping that irregular activity from continuing?
- System Administrator
- Firewall
- IPS
- IDP
You have selected the option in your IDS to notify you via e-mail if it senses any network irregularities. Checking the logs, you notice a few incidents but you didn’t receive any alerts. What protocol needs to be configured on the IDS?
- NTP
- SNMP
- POP3
- SMTP
Choosing a protective network appliance, you want a device that will inspect packets at the most granular level possible while providing improved traffic efficiency. What appliance would satisfy these requirements?
- Layer 3 switch
- NAT-enabled router
- Proxy firewall
- Packet filtering firewall
