Chapter 11
Denial of Service
 III. Security
III. Security
- E. Network security
- P. Vulnerabilities
This chapter will give you a firm understanding of what constitutes a denial-of-service (DoS) attack, the tools and methods used to deploy it, and strategies used to defend against such attacks. DoS is one of the most interesting methodologies employed by the hacking community because of its dramatic impact on the targeted victim and the widely varied base of tools used to launch the attack. Additionally, the means of successfully launching a DoS attack are many, but the end result is essentially the same; as an attacker, your goal is to completely remove the availability of the targeted resource. As you progress through the sections of this chapter, remember your focus when exploring DoS in all its variations. Your goal is to remove the “A” from the Confidentiality, Integrity, and Availability triad.
Understanding DoS
Denial of service is an attack that aims at preventing normal communication with a resource by disabling the resource itself, or by disabling an infrastructure device providing connectivity to it. The disabled resource could be in the form of customer data, website resources, or a specific service, to name a few. The most common form of DoS is to flood a victim with so much traffic that all available resources of the system are overwhelmed and unable to handle additional requests. The attacker floods the victim network with extremely large amounts of useless data or data requests, thereby overwhelming the network and rendering it useless or unavailable to legitimate users.
So what are the signs of a potential DoS attack? Well, there are a few that may indicate that a DoS attack may be in effect, such as:
- Unavailability of a resource
- Loss of access to a website
- Slow performance
- Increase in spam e-mails
Typical victims of DoS attacks range from government-owned resources to online vendors and others, and the intent of the attack is usually the deciding factor in terms of which target will be engaged. Consider a few simple examples to give you an idea of the impact of a successful DoS attack. From a corporate perspective, the focus is always on the bottom line. A successful DoS attack against a corporation’s web page or availability of back-end resources could easily result in a loss of millions of dollars in revenue depending on company size. Also, consider the negative impact to the brand name and company reputation. As you can see, the impact of a single DoS attack with specific directed intent can prove extremely damaging to the victim on many different levels.
Another theme that pervades DoS attacks, as well as other attack forms, is hackers who take action against a target based on “principle” or a sense of personal mission, which is known as hacktivism. Hacktivists are a particularly concerning threat because their focus is not necessarily on personal gain or recognition; their success is measured by how much their malicious actions benefit their cause. This thought process ties in nicely with DoS attacks in that the message being “sent” can be left up to interpretation or, more commonly, be claimed by a group or individual.
DoS attacks have also become extremely popular with cybercriminals and organized crime groups. These groups have organized themselves into complex hierarchies and structures designed to coordinate and magnify the effects of the attack. Additionally the groups use their organization to sometimes enact extortion schemes or to set up other moneymaking schemes. In yet other situations, these groups have been known to create botnets (which we’ll discuss later in this chapter) that they can later rent out for a price to any party who wants them.
DoS Targets
DoS attacks result in a multitude of consequences. Let’s look at some common examples of what is seen in the real world, and what you’ll most likely see on the exam:
Web Server Compromise A successful DoS attack and subsequent compromise of a web server constitutes the widest public exposure against a specific target. What you see most often is a loss of uptime for a company web page or web resource.
Back-end Resources Back-end resources include infrastructure items that support a public-facing resource such as a web page. DoS attacks that take down a back-end resource such as a customer database or server farm essentially render all front-end resources unavailable.
Network or Computer Specific DoS attacks are also launched from within a local area network, with intent to compromise the network itself, or to compromise a specific node such as a server or client system. Various tools and methods for launching a DoS attack against a client or network are discussed further in this chapter.
Types of Attacks
DoS attacks come in many flavors, each of which is critical to your understanding of the nature of the DoS attack class.
Service Request Floods
In this form of DoS attack, a service such as a web server or web application is flooded with requests until all resources are used up. This would be the equivalent of calling someone’s phone over and over again so they could not answer any other calls due to their being occupied. When a single system is attacking another, it is tough to overwhelm the victim, but it can be done on smaller targets or unprepared environments.
Service request floods are typically carried out by setting up repeated TCP connections to a system. The repeated TCP connections consume resources on the victim’s system to the point of exhaustion.
SYN Attack/Flood
This type of attack exploits the three-way handshake with the intention of tying up a system. For this attack to occur, the attacker will forge SYN packets with a bogus source address. When the victim system responds with a SYN-ACK, it goes to this bogus address, and since the address doesn’t exist, it causes the victim system to wait for a response that will never come. This waiting period ties up a connection to the system as the system will not receive an ACK.
ICMP Flood Attack
An ICMP request requires the server to process the request and respond, thus consuming CPU resources. Attacks on the ICMP protocol include smurf attacks, ICMP floods, and ping floods, all of which take advantage of this by flooding the server with ICMP requests without waiting for the response.
Ping of Death
A true classic indeed; originating in the mid- to late-1990s, the Ping of Death was a ping packet that was larger than the allowable 64 K. Although not much of a significant threat today due to ping blocking, OS patching, and general awareness, back in its heyday the Ping of Death was a formidable and extremely easy-to-use DoS exploit.
Teardrop
A teardrop attack occurs when an attacker sends custom-crafted fragmented packets with offset values that overlap during the attempted rebuild. This causes the target machine to become unstable when attempting to rebuild the fragmented packets.
Smurf
A smurf attack spoofs the IP address of the target machine and sends numerous ICMP echo request packets to the broadcast addresses of intermediary sites. The intermediary sites amplify the ICMP traffic back to the source IP, thereby saturating the network segment of the target machine.
Fraggle
A fraggle attack is a variation of a smurf attack that uses UDP echo requests instead of ICMP. It still uses an intermediary for amplification. Commonly a fraggle attack targets the UDP echo requests to the chargen (character generator) port of the intermediary systems via a broadcast request. Just as in a smurf attack, the attacker spoofs the victim’s IP address as the source. Each client that receives the echo to the chargen port will in turn generate a character to be sent to the victim. Once it’s received, the victim machine will echo back to the intermediary’s chargen port, thus restarting the cycle.
Land
A land attack sends traffic to the target machine with the source spoofed as the target machine itself. The victim attempts to acknowledge the request repeatedly with no end.
Permanent DoS Attacks
Most DoS attacks are temporary and only need to be stopped and any mess they created cleaned up to put everything back the way it was. However, some types of DoS attacks destroy a system and cause it to become permanently offline.
Phlashing is a form of permanent DoS that involves pushing bogus or incorrect updates to a system’s firmware to a victim’s system. When this is done, the hardware becomes unusable in many cases without being replaced. When a system is attacked in such a manner, it is said to be bricked. In other words, it is worthless as a computer and now is a brick.
Application-level Attacks
Application-level attacks are those that result in a loss or degradation of a service to the point it is unusable. These attacks can even result in the corruption or loss of data on a system. Typically these types of attacks take the form of one of the following:
Flood This attack overwhelms the target with traffic to make it difficult or impossible to respond to legitimate requests.
Disrupt This attack usually involves attacking a system with the intention of locking out or blocking a user or users—for example, attempting to log into a system several times to lock up the account so that the legitimate user cannot use it.
Jam In this attack, typically the attacker is crafting SQL queries to lock up or corrupt a database. We’ll discuss jam attacks in Chapter 14, “SQL Injections.”
See Exercise 11.1 on how to perform a SYN flood.
Buffer Overflow
Buffer overflow is a DoS technique that takes advantage of a flaw in a program’s coding by inputting more data than the program’s buffer, or memory space, has room for. Once the buffer of a program is an overflow state, all further input that is written to the buffer can have negative consequences, such as crashes, security issues, or other problems. As with many DoS attacks, the intent is to place the program or system in an unpredictable or unexpected state. This ties in with buffer overflow in that once a program is in an unexpected state, the potential for a DoS condition is extremely high.

Some C functions do not perform bounds checking, which means they are prime candidates for allowing a buffer overflow to occur. Be on the lookout for gets(), scanf(), strcpy(), and strcat() functions. Any of these in the code should make you suspect a buffer overflow.
The Heap and Stack
The stack and the heap are two areas of memory a program uses for storage:
Heap The heap is a dynamic storage location that does not have sequential constraints or an organizational scheme. It is considered the larger pool of free storage for programs to use as needed. Once the dynamic memory space is no longer needed and the program has retrieved the needed data, the occupied space in the heap is freed up for future use.
Stack The stack refers to the smaller pool of free storage: memory allocated to a program for short-term processing. This is the main action area, where program variables are temporarily stored, added, and removed as needed to perform a specific function. The name stack comes from the fact that accessing its resources is similar in function to the way you access information from a stack of dominos, for instance. You can see the value of the top domino, you can remove a domino from the top, and you can stack another domino on top. If you pull the bottom or middle domino from the stack, the whole pile comes tumbling down. Thus you are limited to manipulating the stack from the top down. This is how a program stack operates as well. Another name for this kind of access is last-in, first-out (LIFO). The last item to be stacked is the first item to be removed. In programming lingo, the term push is used to describe adding a new item to the stack, and pop describes removing an item. So, if a program wants to add or remove something to or from the stack, it uses the push and pop actions accordingly, and it does so in a linear top-to-bottom fashion. Take a look at Figure 11.1 to get a quick visual of a basic program stack.
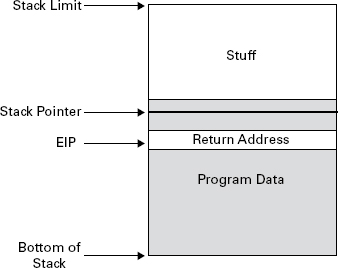
FIGURE 11.1 Basic program stack

Figure 11.1 is a simplified version of a program stack. To understand buffer overflows and how they play into DoS attacks, you only need to understand the basic sequence and functions. For an excellent tutorial, Google “Smashing the Stack for Fun and Profit.”
The key takeaway from this is to understand how the stack can be “overflowed” and thus create a DoS condition within the program or system. Knowing the basics of how the stack is used gives you insight into how it might be compromised.
Now that you are familiar with the heap and the stack, let’s go over some key concepts that will be important for passing the exam, as well as for understanding the operation of a successful DoS attack via buffer overflow:
Smashing the Stack “Smashing” the stack refers to the use of buffer overflow to compromise the stack integrity and gain program-level access for running malicious code. Refer back to the basic program stack in Figure 11.1; smashing the stack modifies normal stack operation by submitting excess data to the stack, surpassing its normal bounds (if left unchecked). The excess data overwrites legitimate variables in the stack and resets the saved Extended Instruction Pointer (EIP) value to point to the injected malicious code. Figure 11.2 shows this process.
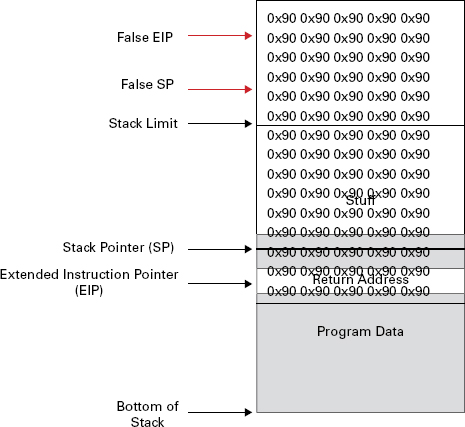
FIGURE 11.2 Smashing the stack
Figure 11.2 deserves just a bit more explanation, as it may look a little confusing at this point. Let’s take it one piece at a time. Underlying the “0x90” block (which will be discussed in “NOP Sled” in a moment) is the basic program stack from Figure 11.1. Remember that Figure 11.1 represents normal operation, where the program’s variables and stored data all stay within normal memory bounds, which is between the stack pointer (the top of the stack) and the bottom of the stack. The 0x90 overlay in Figure 11.2 represents the overflow portion that has been applied, or pushed onto the normal stack. The excess data, which has far surpassed the stack limit, has put the stack in an overflow condition. Once this is achieved, the program’s reference point for the next legitimate instruction execution has been shifted up into the attacker’s overflowed code. At this point, the program executes the attacker’s malicious code with privileges identical to those of the original legitimate program. And if you are ready to throw this book in the trash and give up your quest to become a CEH, rest assured you will not have to regurgitate this paragraph for the exam. We are going for reference and understanding, so keep going and stick this stuff in your mental file cabinet for later retrieval.

Don’t be overwhelmed by the code and lingo. Remember, as a CEH your interest lies in understanding only what you need in order to achieve the desired effect on the system or program. Understand the process and terms, and you’ll be fine.
NOP Sled NOP sled refers to shellcode (machine code) used in a buffer overflow attack that uses multiple “No Operation” commands in a sequenced chunk. NOP by itself stands for “No Operation”; thus it follows that a NOP sled is a large sequence of no operation function calls. The value 0x90, which you saw in Figure 11.2, is the hexadecimal value of a NOP instruction as it applies to Intel processors; therefore, a NOP instruction with a value of 0x90 will instruct an Intel processor to perform a one-clock cycle on an empty process. In plain English, 0x90 will force an Intel CPU to dry fire a single cycle. Now, take a series of 0x90 values, as you saw in Figure 11.2, and you have a fairly large “padding” on the stack that can set the stage for the execution of malicious code.

The value 0x90 is a near dead giveaway for a buffer overflow exploit. Watch for the 0x90 value, as it may be hiding among other values and processes. However, keep in mind that in certain situations the appearance of a NOP may not necessarily mean that a problem exists because it is a part of normal operation.
A quick summary is in order at this point to make sure we are all on the same page. A program uses the stack and the heap for storage. The heap is dynamic, whereas the stack is linear in operation (top, bottom, LIFO). Buffer overflow overfills the heap, exceeding the memory boundaries. This in turn creates an unpredictable condition in which the OS now sees the program as operating outside its allotted memory space. One of the following will probably happen:
- The OS terminates the offending program due to the program operating outside its allotted memory space.
- The address of the hacker’s malicious code, which now resides in the overflowed stack, winds up in the EIP, causing that code to execute.

Basic operators such as < (less than), > (greater than), and => (equal to or greater than) are used to test your understanding of memory bounds and buffer overflows. Remember the basic concept of a buffer overflow, and also keep in mind that any value outside the normal range constitutes an overflow condition.
Understanding DDoS
Distributed denial-of-service (DDoS) attacks have the same goals, but the implementation is much more complex and wields more power. Whereas a DoS attack relies on a single system or a very small number of systems to attack a victim, a DDoS attack scales this up by having several attackers go after a victim. How many attackers? Anywhere from a few hundred to a few million in some cases.
DDoS Attacks
DDoS attacks have the same goal as regular DoS methods; however, the difference lies in the implementation of the attack. A standard DoS attack can be launched from a single malicious client, whereas a DDoS attack uses a distributed group of computers to attack a single target. Check out Figure 11.3 to see a diagram of a DDoS setup.
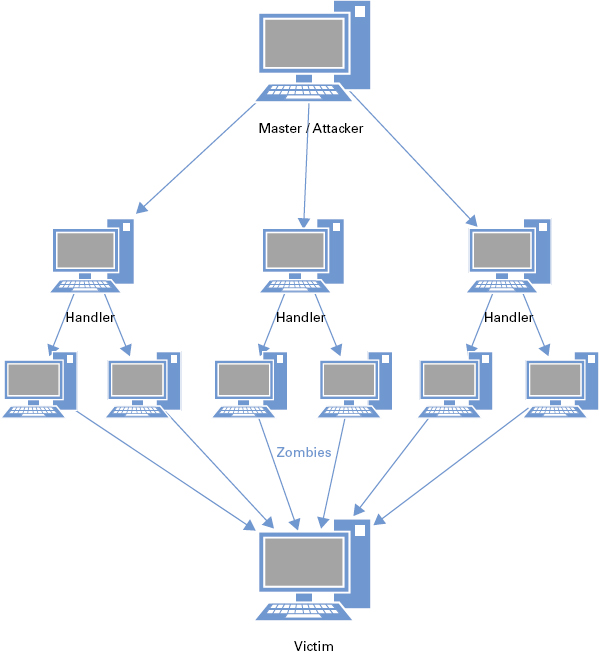
FIGURE 11.3 Smashing the stack
As you can see in Figure 11.3, quite a few parts are involved when launching a DDoS attack. Conceptually, the process is quite simple. The attacker first infects the handler, or master computer, with a specific DDoS software build commonly known as a bot. The bot in turn sifts through the victim’s network searching for potential clients to make slaves, or zombies. Note that the attacker purposely chooses their handler unit or units based on the positional advantage it will give them for their DDoS attack. This equates to a unit that has maneuverability in the network, such as a file server or the like. Once the handler systems have been compromised and the zombie clients are infected and listening, the attacker need only identify the target and send the go signal to the handlers.

For the exam you must be able to draw a distinction between a DoS and a DDoS. With DoS, you typically see a single or a very small number of clients attacking a target; with DDoS, a large number of clients attack a target. You could thus say that the main difference is scale; however, in either case the end result is the same—a victim is taken offline.
A common method of covertly installing a bot on a handler or client is a Trojan horse that carries the bot as a payload. Once the handler and subsequent zombies have been infected, the attacker communicates remotely with the so-called botnet via communication channels such as Internet Relay Chat (IRC) or Peer-to-Peer (P2P).
Tools for Creating Botnets
Various tools are used to create botnets, including the following:
- Shark
- Plugbot
- Poison Ivy
- Low Orbit Ion Cannon (LOIC)
DoS Tools
The following is a list of DoS tools:
DoSHTTP DoSHTTP is an HTTP flood DoS tool. It can target URLs, and it uses port designation.
UDP Flood This utility generates UDP packets at a specified rate and to a specific network.
Jolt2 This IP packet fragmentation DoS tool can send large numbers of fragmented packets to a Windows host.
Targa This 8-in-1 tool can perform DoS attacks using one or many of the included options. Attacks Targa is capable of land, WinNuke, and teardrop attacks.
DDoS Tools
The following is a list of DDoS tools:
Trinoo This DDoS tool uses UDP flooding. It can attack single or multiple IPs.
LOIC Low Orbit Ion Cannon (LOIC) has become popular because of its easy one-button operation. Some people suspect that groups such as Anonymous, which use DDoS attacks as their primary weapon, use LOIC as their main tool. (See Exercise 11.2.)
TFN2K This DDoS attack tool is based on TFN (Tribe Flood Network) and can perform UDP, SYN, and UDP flood attacks.
Stacheldraht This DDoS tool has similar attack capabilities as TFN2K. Attacks can be configured to run for a specified duration and to specific ports.

The exam will expect you to be familiar with the tools listed in this chapter and throughout the book, which means you must know what each tool does and how it’s used. Memorizing the details and nuances of each tool is not required.
EXERCISE 11.2: Seeing LOIC in Action
LOIC is one the easiest DDoS tools available, yet its simplicity and remote connection features make it an extremely effective tool. In this exercise you will see just how easy it is to launch a DoS attack using LOIC. For this exercise you will use a Windows Server 2008 client with LOIC installed and a Windows 7 target with Wireshark for traffic capture.
- First, we run the
LOIC.exefile. Do not perform an in-depth installation; just run the executable.
- Once you run the EXE, the program pops up and is ready for a quick configuration. Note that you can target a URL as well as a specific IP address. For our purposes just enter the IP of your Windows 7 box.
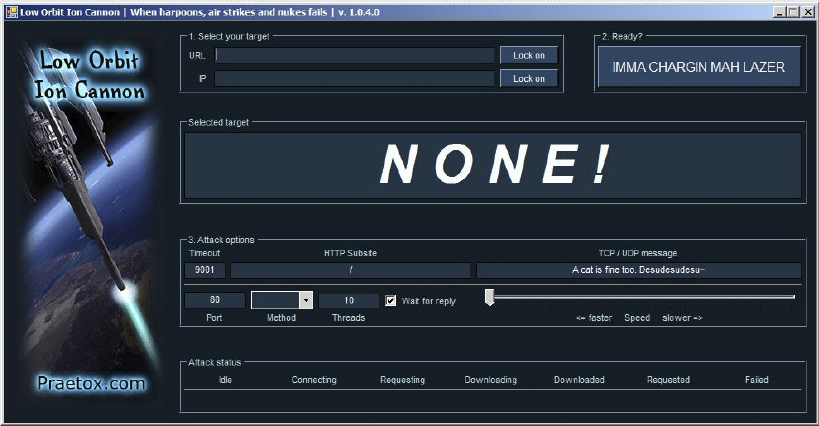
- Click the Lock On button. The IP address shows up as the target; there is no doubt where this traffic is going.
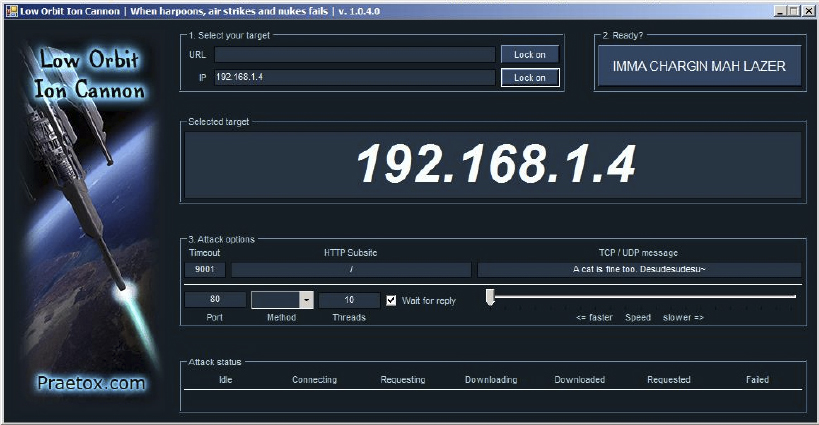
- Now that you have the IP input and target selected, you can configure a few more details for your attack preferences. For this exercise use port 80, the TCP method, 10000 threads, and the default TCP/UDP message, as shown here:
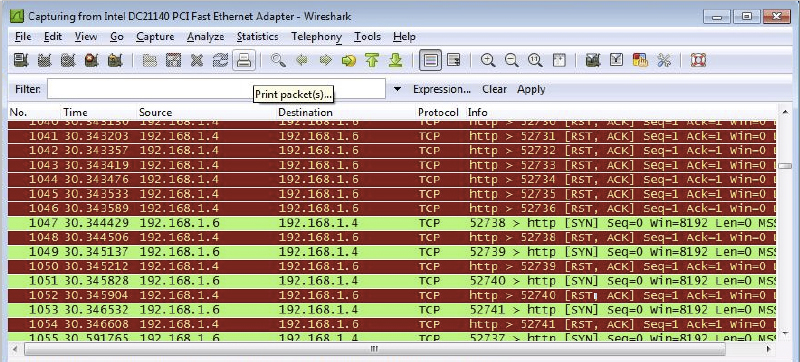
- Before you hit the fire button, hop back over to your Windows 7 system and start Wireshark to see the traffic generated by LOIC.
- Now you can fire your LOIC beam and view the traffic.
DoS Defensive Strategies
Let’s look at some DoS defensive strategies:
Disabling Unnecessary Services You can help protect against DoS and DDoS attacks by hardening individual systems and by implementing network measures that protect against such attacks.
Using Anti-Malware Real-time virus protection can help prevent bot installations by reducing Trojan infections with bot payloads. This has the effect of stopping the creation of bots for use in a botnet. Though not a defense against an actual attack, it can be a proactive measure.
Enabling Router Throttling DoS attacks that rely on traffic saturation of the network can be thwarted, or at least slowed down, by enabling router throttling on your gateway router. This establishes an automatic control on the impact that a potential DoS attack can inflict, and it provides a time buffer for network administrators to respond appropriately.
Using a Reverse Proxy A reverse proxy is the opposite of a forward or standard proxy. The destination resource rather than the requestor enacts traffic redirection. For example, when a request is made to a web server, the requesting traffic is redirected to the reverse proxy before it is forwarded to the actual server. The benefit of sending all traffic to a middleman is that the middleman can take protective action if an attack occurs.
Enabling Ingress and Egress Filtering Ingress filtering prevents DoS and DDoS attacks by filtering for items such as spoofed IP addresses coming in from an outside source. In other words, if traffic coming in from the public side of your connection has a source address matching your internal IP scheme, then you know it’s a spoofed address. Egress filtering helps prevent DDoS attacks by filtering outbound traffic that may prevent malicious traffic from getting back to the attacking party.
Degrading Services In this approach, services may be throttled down or shut down in the event of an attack automatically in response to an attack. The idea is that degraded services make an attack tougher and make the target less attractive.
Absorbing the Attack Another possible solution is to add enough extra services and power in the form of bandwidth and another means to have more power than the attacker can consume. This type of defense does require a lot of extra planning, resources, and of course money. This approach may include the use of load balancing technologies or similar strategies.
Botnet-specific Defenses
The following are botnet-specific defensive strategies:
RFC 3704 Filtering This defense is designed to block or stop packets from addresses that are unused or reserved in any given IP range. Ideally this filtering is done at the ISP level prior to reaching the main network.
Black Hole Filtering This technique in essence creates a black hole or area on the network where offending traffic is forwarded and dropped.
Source IP Reputation Filtering Cisco offers a feature in their products, specifically their IPS technologies, that filters traffic based on reputation. Reputation is determined by past history of attacks and other factors.
DoS Pen Testing Considerations
When you’re pen testing for DoS vulnerabilities, a major area of concern is taking down integral resources during the testing phase. The ripple effect of taking out a file server or web resource can be pretty far reaching, especially if bringing the system back online proves challenging after a successful DoS test attack. As with all pen testing activities, an agreement between the tester and the client should explicitly define what will be done and the client’s timeframe for when the testing will occur. Also, as always, documenting every step is crucial in every part of the process.
Summary
In this chapter you learned that a denial-of-service attack involves the removal of availability of a resource. That resource can be anything from a web server to a connection to the LAN. DoS attacks can focus on flooding the network with bogus traffic, or they can disable a resource without affecting other network members. We also discussed buffer overflow, which pushes data beyond the normal memory limit, thereby creating a DoS condition. Additionally, you saw that a NOP sled can be used to pad the program stack, which lets the attacker run malicious code within the compromised stack. You learned about compromised handlers and their role in infecting and controlling zombie clients in a DDoS attack. We also explored a number of attack methods and tools for performing attacks. Lastly, we reviewed some preventive measures, such as router throttling, that you can use to defend against DoS attacks.
Exam Essentials
Remember the basic concept of DoS and DDoS. Be familiar with the basic orchestration of a DoS attack as well as a DDoS attack. Browse the Web for DDoS images to become comfortable with recognizing the layout of an attack.
Understand the targets. Know what resources can, and usually do, get targeted. This applies also to the focus of the DoS attack, which can be traffic or network saturation, or a single target.
Know the stack. Review Figure 11.1 and Figure 11.2 and make sure you understand the parts that act on the stack. Remember that the EIP is the point of execution in a stack and that the EIP gets shifted when an overflow occurs.
Understand buffer overflow. Know that a buffer overflow occurs when data, through either malicious or unintentional means, gets pushed beyond the normal memory bounds of the stack. Be familiar with the difference between a buffer overflow and smashing the stack.
Know the dangerous C functions. Memorize and be on the lookout for those C functions that do not perform bounds checking: gets(), scanf(), strcpy(), and strcat(). Ensure that you are comfortable recognizing these commands in compiled code.
Understand the NOP sled. Remember that NOP means No Operation; this equates to a full CPU cycle with no actual work being accomplished. A NOP sled is a sequence of NOP functions; know how it relates to buffer overflow and smashing the stack. Memorize and recognize the hexadecimal value of a NOP, which is 0x90.
Be familiar with attack methods. You don’t have to know all the details of how to perform each attack method, but be sure to know what each method uses to perform the attack. For example, a fraggle attack uses UDP echo requests to the chargen port.
Know the preventive measures. Know the preventive measures available as well as the actions each one takes to prevent the attack. Ensure that you are familiar with the operation of a reverse proxy and ingress and egress filtering.
Know your tools and terms. The CEH exam is drenched with terms and tool names that will eliminate even the most skilled test taker because they simply don’t know what the question is even talking about. Familiarize yourself with all the key terms, and be able to recognize the names of the DoS tools on the exam.
Review Questions
What is the hexadecimal value of a NOP instruction in an Intel system?
- 0x99
- 0x90
- 0x80
- 99x0
Which pointer in a program stack gets shifted or overwritten during a successful overflow attack?
- ESP
- ECP
- EIP
- EBP
Groups and individuals who hack systems based on principle or personal beliefs are known as _______.
- White hats
- Black hats
- Script kiddies
- Hacktivists
Jason is the local network administrator who has been tasked with securing the network from possible DoS attacks. Within the last few weeks, some traffic logs appear to have internal clients making requests from outside the internal LAN. Based on the traffic Jason has been seeing, what action should he take?
- Throttle network traffic.
- Update antivirus definitions.
- Implement egress filtering.
- Implement ingress filtering.
Which DoS attack sends traffic to the target with a spoofed IP of the target itself?
- Land
- Smurf
- Teardrop
- SYN flood
Adding and removing to and from a program stack are known as what?
- Pop and lock
- Push and pop
- Stack and pull
- Plus and minus
Zombies Inc. is looking for ways to better protect their web servers from potential DoS attacks. Their web admin proposes the use of a network appliance that receives all incoming web requests and forwards them to the web server. He says it will prevent direct customer contact with the server and reduce the risk of DoS attacks. What appliance is he proposing?
- Web proxy
- IDS
- Reverse proxy
- Firewall
In a DDoS attack, what communications channel is commonly used to orchestrate the attack?
- Internet Relay Chat (IRC)
- MSN Messenger
- ICMP
- Google Talk
What is the name for the dynamic memory space that, unlike the stack, doesn’t rely on sequential ordering or organization?
- Pointer
- Heap
- Pile
- Load
Which function(s) are considered dangerous because they don’t check memory bounds? (Choose all that apply.)
gets()strcpy()scanf()strcat()
The stack operates on a _______ basis.
- FIFO
- LIFO
- FILO
- LILO
While monitoring traffic on the network, Jason captures the following traffic. What is he seeing occur?
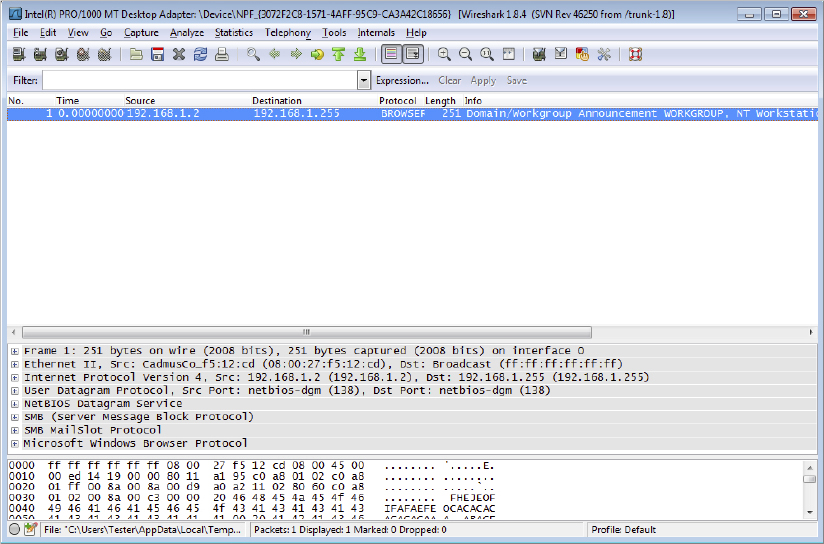
- ICMP flood
- SYN flood
- Teardrop
- Land
What is a single-button DDoS tool suspected to be used by groups such as Anonymous?
- Trinoo
- Crazy Pinger
- LOIC
- DoSHTTP
What is an 8-in-1 DoS tool that can launch such attacks as land and teardrop?
- Jolt
- Targa
- TFN2K
- Trinoo
What command-line utility can you use to craft custom packets with specific flags set?
- nmap
- Zenmap
- Ping
- hping3
What protocol is used to carry out a fraggle attack?
- IPX
- TCP
- UDP
- ICMP
What is the key difference between a smurf and a fraggle attack?
- TCP vs. UDP
- TCP vs. ICP
- UDP vs. ICMP
- TCP vs. ICMP
What is the main difference between DoS and DDoS?
- Scale of attack
- Number of attackers
- Goal of the attack
- Protocols in use
What is the most common sign of a DoS attack?
- Weird messages
- Rebooting of a system
- Slow performance
- Stolen credentials
What response is missing in a SYN flood attack?
- ACK
- SYN
- SYN-ACK
- URG
