Chapter 2
Attacks and Monitoring
THE CISSP EXAM TOPICS COVERED IN THIS CHAPTER INCLUDE:
- Access Control
- Control access by applying the following concepts/methodology/techniques:
- Policies; types of controls (e.g., preventative, detective, corrective, etc.); techniques (e.g., nondiscretionary, discretionary, and mandatory); identification and authentication; decentralized/distributed access control techniques; authorization mechanisms; logging and monitoring
- Understand access control attacks
- Assess effectiveness of access controls
- Control access by applying the following concepts/methodology/techniques:
- Operations Security
- Implement and support patch and vulnerability management
- Understand fault tolerance requirements
The Access Control domain in the Common Body of Knowledge (CBK) for the CISSP certification exam deals with topics and issues related to the monitoring, identification, and authorization of granting or restricting user access to resources. Generally, access control is any hardware, software, or organizational administrative policy or procedure that grants or restricts access, monitors and records attempts to access, identifies users attempting to access, and determines whether access is authorized or not.
The Access Control domain is discussed in this chapter and in the previous chapter (Chapter 1, “Accountability and Access Control”), as well as in Chapter 14. Be sure to read and study the materials from all these chapters to ensure complete coverage of the essential material for the CISSP certification exam.
The Operations Security domain in the CBK for the CISSP exam deals with topics and issues related to identifying the controls over hardware, media, and those operators with access privileges to any such resources. Audit and monitoring refer to those mechanisms, tools, and facilities that enable security events to be detected, and for subsequent actions to occur so that key elements are identified and reported appropriately. Operations security is also covered in Chapter 13, “Administrative Management.”
Monitoring is a programmatic means by which subjects are held accountable for their actions while authenticated on a system. It is also the process by which unauthorized or abnormal activities may be detected on a system. Monitoring is necessary to detect malicious actions by subjects as well as to detect attempted intrusions and system failures. It can help reconstruct events, provide evidence for prosecution, and produce problem reports and analysis. Auditing and logging are usually native features in an operating system and for most applications and services. Thus, configuring a system to record information about specific types of events is fairly straightforward.
Using log files to detect problems is another matter. In most cases, when sufficient logging and auditing are enabled to monitor a system, so much data is collected that important details can get lost in the sheer volume of resulting data. You can use numerous tools to search through log files for specific events or ID codes. The art of data reduction is crucial when working with large volumes of monitoring data obtained from log files. The tools used to extract the relevant, significant, or important details from large collections of data are known as data mining tools. For true automation and even real-time analysis of events, a specific type of data mining tool is required, namely, an intrusion detection system (IDS, covered in the next section).
Accountability is maintained by recording the activities of subjects and objects as well as core system functions that sustain the operating environment and security mechanisms. The audit trails created by recording system events to logs can be used to evaluate a system’s health and performance. System crashes may indicate faulty programs, failing hardware, corrupt drivers, or intrusion attempts. The event logs leading up to a crash can often be used to discover the reason a system failed. Log files provide an audit trail for re-creating a step-by-step history of an event, intrusion, or system failure.
![]()
Monitoring Activity
Accountability is absolutely necessary at every level of business, from the frontline infantry to the high-level commanders overseeing daily operations. Without monitoring the actions and activities of users and their applications on a given system, how can you hold them accountable for any mistakes or misdeeds they might commit?
Meet Alex, a quality assurance supervisor for the data entry department at an oil-drilling data mining company. During his daily routine, he sees many highly sensitive documents and the kind of juicy information that can earn a heavy tip from a greasy palm. He also corrects the kind of mistakes that could cause serious backlash from his company’s clientele, because sometimes a minor clerical error can cause serious issues for a client’s entire project.
Whenever Alex touches or transfers such information on his workstation, his actions leave an electronic trail of evidence that Brianna, his supervisor, can examine in the event that Alex’s actions should come under scrutiny. She can observe where he obtained or placed pieces of sensitive information, when he accessed and modified such information, and just about anything else related to the handling and processing of the data as it flows in from the source and out to the client.
Without the electronic ability to observe and analyze the way Alex handles this highly sensitive information, how can you be certain about what he does with this information both in and out of the workplace? You can’t, and that’s what makes monitoring important (and required, pursuant to legislation such as the Sarbanes-Oxley Act, HIPAA, EU privacy laws, and so forth for some markets or types of information).
Monitoring is a necessary function of the auditing process through which subjects are held accountable for their actions and activities with regard to other subjects, objects, or functions on any given system. Additionally, you can build up multiple supportive layers of defense around monitoring, auditing, and accounting practices that include real-time detection and deterrence of network-borne attack patterns that originate both inside and outside the perimeter of your business environment.
An intrusion detection system is a product that automates the inspection of audit logs and real-time system events. IDSs are primarily used to detect intrusion attempts, but they can also be employed to detect system failures and to rate overall performance. IDSs watch for violations of confidentiality, integrity, and availability. The goal of an IDS is to provide perpetrator accountability for intrusion activities and provide a means for a timely and accurate response to intrusions. An IDS can recognize attacks that come from external connections (such as the Internet or partner networks), viruses, malicious code, trusted internal subjects attempting to perform unauthorized activities, and unauthorized access attempts from trusted locations. An IDS is considered one form of technical detective security control.
An IDS can actively watch for suspicious activity, peruse audit logs, and send alerts to administrators as specific events are detected. It can also lock down important system files or capabilities, track slow and fast intrusion attempts, highlight vulnerabilities, identify an intrusion’s origination point, and track down the logical or physical location of the perpetrators. In addition, an IDS can terminate or interrupt attacks and intrusion attempts and can reconfigure routers and firewalls to prevent repeats of known attacks. IDS alerts can be sent or communicated with an onscreen notification (the most common) by playing a sound, sending an email notification, alerting a pager, or recording information in a log file.
A response from an IDS can be active, passive, or hybrid:
Active response. Directly affects malicious activity in network traffic or a host application
Passive response. Does not affect malicious activity but records information about the issue and notifies the administrator
Hybrid response. Stops unwanted activity, records information about the event, and possibly even notifies the administrator
Generally, an IDS is used to detect unauthorized or malicious activity originating from inside or outside a trusted network. In general, an IDS has only limited capability to stop current or prevent future attacks. Typical responses an IDS can take against an attack include blocking ports, blocking protocols, blocking source addresses, and disabling all communications over some specific cable segment. Whenever an IDS discovers abnormal behavior (such as spoofed traffic) or violations of its security policy, filters, or rules, it records a log detail of the issue and then drops, discards, or deletes the relevant packets.
![]()
I Detect an IDS
Chance can’t seem to understand why he needs an IDS. Doesn’t a firewall take care of everything? Doesn’t a firewall provide sufficient security on a business network for every conceivable purpose? Deidre explains to Chance that a firewall is reactive in its approach: It has a basic idea of what is allowed where and from what addresses connections may be made. For example, her firewall blocks illicit connections to unused service ports and authorizes restricted access to publicly accessible mission-critical services.
Chance is left to wonder what else there could possibly be to safeguard against. Isn’t it enough to prevent unauthorized access to network resources? Deidre then describes to Chance how an IDS is more responsive because it’s “aware” of unusual application behavior patterns that may indicate a possible attack that a firewall does not directly analyze. There may be allowable forms of traffic that include impermissible or potentially harmful protocols or data formats. For example, Deidre once deterred a protocol field attack from executing against a vulnerable network-accessible service because her IDS had a rule set to catch that very attack in place; otherwise, it would have bypassed the firewall and caught them unprotected.
Although Deidre has the real-world experience to grasp the capabilities of an IDS as compared to a firewall, she’s not sure Chance appreciates the difference. How might you differentiate an IDS from a firewall so you could explain it to nontechnical personnel (perhaps one of your superiors) and convey its significance and security impact?
The best approach is to emphasize that a firewall responds to traffic and within limits can apply state information to that traffic. On the other hand, an IDS attends to overall patterns of behavior to which a firewall may be oblivious. If you explain how distributed denial-of-service attacks, slow iterations on a password attack, or obvious network scanning and profiling works—and why an IDS can catch such things easily, whereas firewalls may not—you’ll be able to make the case without too much effort. You can also make a case that an IDS contributes to layered security or defense in depth in that it goes beyond what firewalls or various security appliances can do.
An IDS should be considered one of many components that a well-formed security endeavor employs to protect a network. An IDS is complementary to a firewall. Other security controls, such as physical restrictions and logical access controls, are also necessary components (refer to Chapter 1 for a discussion of those controls).
Intrusion prevention requires adequate maintenance of overall system security, such as applying patches and setting security controls. It also involves responding to intrusions that an IDS discovers by erecting barriers to prevent future occurrences of the same attack. This could be as simple as updating software or reconfiguring access controls, or it could be as drastic as reconfiguring a firewall, removing or replacing an application or service, or redesigning an entire network.
When an intrusion is detected, your first response should be to contain the intrusion. Intrusion containment prevents additional damage to other systems but may allow continued infestation of already compromised systems. Later, once compromised systems are rebuilt from scratch, be sure to double-check compliance with your security policy—including checking ACLs, service configurations, and user account settings—before connecting the reestablished system to your network. Be aware that if you wipe and re-create a system, no parts of the previous system, nor any intrusion footprints, remain behind.
![]()
It is considered unethical and risky to actively launch counterstrikes against an intruder or to actively attempt to reverse-hack an intruder’s computer system. Instead, rely upon your logging capabilities and sniffing collections to provide sufficient data to prosecute criminals or to simply improve the security of your environment in response.
IDS type and classification define the scope of responsibility and functional role for each system. Among the many variations in type and classification for IDSs there are enough complementary elements that enable two or more systems to combine their efforts toward a single common goal on the network.
Host- and Network-Based IDSs
IDS types are most commonly classified by their information source. There are two primary types of IDSs: host based and network based. A host-based IDS watches for questionable activity on a single computer system, especially by watching audit trails, event logs, and application logs. A network-based IDS watches for questionable activity occurring on the network medium by inspecting packets and observing network traffic patterns. You may even occasionally find mention of an application-based IDS, which monitors application activity in a networked environment.
Host-Based IDS
Because the attention of a host-based IDS is focused on a single computer (whereas a network-based IDS must monitor the activity on an entire network), it can examine events in much greater detail than a network-based IDS can. A host-based IDS is able to pinpoint the files and processes compromised or employed by a malicious user to perform unauthorized activity.
Host-based IDSs can detect anomalies undetected by network-based IDSs; however, a host-based IDS cannot detect network-only attacks or attacks on other systems. Because a host-based IDS is installed on the computer being monitored, attackers can discover the IDS software and disable or manipulate it to hide their tracks. A host-based IDS has some difficulty with detecting and tracking down denial-of-service (DoS) attacks, especially those that seek to consume all available bandwidth. A host-based IDS also consumes resources from the computer being monitored, thereby reducing its performance. A host-based IDS is also limited by the auditing capabilities of the host operating system and applications.
Host-based IDSs are considered more costly to manage than network-based IDSs. Host-based IDSs require that an installation on each server be monitored. They require administrative attention at each point of installation, while network-based IDSs usually require only a single installation point. Host-based IDSs have other disadvantages as well; for example, they degrade host system performance significantly, and they are easier for an intruder to discover and disable.
Network-Based IDS
Network-based IDSs detect attacks or event anomalies through the capture and evaluation of network packets. A single network-based IDS can monitor a large network if installed on its backbone, where a majority of network traffic travels. Some versions of network-based IDSs use remote agents to collect data from various subnets and report to a central management console. Network-based IDSs are installed onto single-purpose computers. This allows them to be hardened against attack, reduces the number of vulnerabilities in the IDS, and allows the IDS to operate in stealth mode. In stealth mode, an IDS is invisible to the network, and intruders would have to know its exact location and system identification to discover it. A network-based IDS has little negative effect on overall network performance, and because it is deployed on a single-purpose system, it doesn’t adversely affect performance on any other computer.
On networks with large volumes of traffic, a network-based IDS may be unable to keep up with the flow of data. This could cause the IDS to miss an attack that occurred during high traffic levels. Network-based IDSs do not usually work well on a switched network, especially if its routers do not have monitoring ports. Network-based IDSs cannot monitor the content of encrypted traffic in transit over the network medium. They are usually able to detect initiation of an attack or ongoing attempts to perpetrate an attack (including DoS), but they are unable to provide information about whether an attack succeeded or about which specific systems, user accounts, files, or applications may have been affected.
Often, a network-based IDS can provide some limited functionality to discover the source of an attack by performing Reverse Address Resolution Protocol (RARP) or reverse Domain Name System (DNS) lookups. However, because most attacks are launched by malicious individuals whose identity is masked through spoofing or by proxy through so-called “zombies,” this is not always reliable.
An IDS should not be viewed as a security panacea. It is only one part of a multifaceted security solution for an environment. Although an IDS can offer numerous benefits, there are several drawbacks to consider. A host-based IDS may not be able to examine every detail if the host system is overworked and insufficient execution time is granted to the IDS processes. A network-based IDS can suffer the same problem if network traffic load is high and it is unable to process packets efficiently and swiftly. A network-based IDS is also unable to examine the contents of encrypted traffic. A network-based IDS is not an effective network-wide solution on switched networks because it is unable to view all network traffic if it is not placed on a mirrored port (that is, a port specifically configured to send all data to the IDS). An IDS may initially produce numerous false alarms, and it requires significant management on an ongoing basis.
![]()
A switched network is often a preventative measure against rogue sniffers. Whenever an IDS is attached to a switch, if the switch is not configured to mirror all traffic, then only a small portion of network traffic is accessible to the IDS. However, numerous types of attacks, such as MAC or ARP flooding, can cause a switch to default into hub mode, thus granting the attacker access to all data (as well as greatly reducing the efficiency and throughput of your network).
Knowledge- and Behavior-Based Detection
An IDS can detect malicious behavior using two common methods. One way is to use knowledge-based detection (also called signature-based detection or pattern-matching detection). Here, the IDS uses a signature database and attempts to match all monitored events to its contents. If a match is made, the IDS assumes that an attack is taking place (or has taken place). The IDS vendor develops a suspect chart by examining and inspecting numerous intrusions on various systems. What results is a description, or signature, for common attack methods or behaviors. An IDS using knowledge-based detection functions in much the same way as many antivirus applications.
The primary drawback for a knowledge-based IDS is that it is effective only against known attack methods. New attacks or slightly modified versions of known attacks often go unrecognized by the IDS. This means that a knowledge-based IDS lacks a learning model; that is, it is unable to recognize new attack patterns as they occur. Thus, this type of IDS is only as useful as its signature file is correct and up-to-date. Keeping the signature file current is an important aspect in maintaining the best performance from a knowledge-based IDS.
The second detection type is behavior-based detection (also called statistical intrusion detection, anomaly detection, and heuristics-based detection). Basically, behavior-based detection learns about the normal activities and events on your system by watching and tracking what it sees. Once it has accumulated enough data about normal activity, it can detect abnormal and possibly malicious activities or events.
A behavior-based IDS can be labeled an expert system or a pseudo-artificial intelligence system because it can learn and make assumptions about events. In other words, the IDS can act like a human expert by evaluating current events against known events. The more information provided to a behavior-based IDS about normal activities and events, the more accurately it can detect anomalies. A behavior-based IDS can also detect newer attacks that have no signatures and will thus be invisible to a signature-based approach.
The primary drawback for a behavior-based IDS is that it produces many false alarms. Normal patterns of user and system activity can vary widely, and thus establishing a definition of normal or acceptable activity can be difficult. The more a security detection system creates false alarms, the less likely it is that security administrators will heed its warnings, just as in the fable of the boy who cried wolf. Over time, an IDS can become more efficient and accurate, but its learning process takes a long while to become usable. Using known behaviors, activity statistics, and heuristic evaluation of current vs. previous events, a behavior-based IDS can detect unforeseen, new, or unknown vulnerabilities, attacks, and intrusion methods.
Although knowledge-based and behavior-based detection methods do have their differences, both employ an alarm-signal system. When an intrusion is recognized or detected, an alarm is triggered. The alarm system notifies administrators via email or pop-up messages or by executing scripts to send pager messages. In addition to administrator notification, the alarm system can record alert messages in log and audit files as well as generate violation reports detailing the detected intrusions and discoveries of vulnerabilities.
Some IDSs also perform what’s called stateful packet analysis, which means that they understand enough of the protocols used for communications to monitor potentially dangerous or malicious communications. If a known pattern of unwanted or malicious activity emerges, the IDS can then block further communications of that kind.
Anomaly analysis also adds to an IDS’s capabilities in that these devices can recognize and react to sudden increases in traffic volume or activity (which can indicate a direct attack of some kind, if not a denial-of-service attack), multiple failed login attempts (indicative of possible password cracking attacks), logons or program activity outside normal working hours for accounts in use, or sudden increases in error or failure messages (which can also indicate that attacks are underway).
An IDS (or intrusion prevention system, aka IPS) can also respond to unwanted or untoward patterns of behavior by changing ACLs for routers, deliberately dropping suspicious packets, or denying access to suspicious, ill-behaved, or anomalous users. IDSs and IPSs can also help to drive quick, effective responses to unwanted or unexpected behavior, thanks to their abilities to generate instant messages or email alerts, to page on-duty security or administrative staff, and to pop up onscreen alerts in IT department control centers that are manned 24/7/365.
Intrusion detection systems are often deployed in concert with other components. These IDS-related tools expand the usefulness and capabilities of IDSs and make them more efficient and less prone to false positives. These tools include honeypots, padded cells, and vulnerability scanners. They are described in the following sections.
Understanding Honeypots
Honeypots are individual computers or entire networks created to serve as a snare for intruders. They look and act like legitimate networks, but they are 100 percent fake. Honeypots tempt intruders by presenting unpatched and unprotected security vulnerabilities as well as by hosting attractive and tantalizing but faux data. They are designed to grab an intruder’s attention and direct them into a restricted playground while keeping them away from the legitimate network and confidential resources. Legitimate users never enter the honeypot; there is no real data or useful resources in the honeypot system. Thus, when honeypot access is detected, it is most likely an unauthorized intruder. Honeypots are deployed to keep an intruder logged on and performing malicious activities long enough for the automated IDS to detect the intrusion and gather as much information about the intruder as possible. The longer the honeypot retains the attention of the intruder, the more time an administrator has to investigate the attack and potentially identify the intruder.
![]()
A honeynet is two or more networked honeypots used in tandem to monitor or re-create larger, more diverse network arrangements. Often, these honeynets facilitate intrusion detection systems.
The use of honeypots raises the issue of enticement vs. entrapment. A honeypot can be legally used as an enticement device if the intruder discovers it through no outward efforts of the honeypot owner. Placing a system on the Internet with open security vulnerabilities and active services with known exploits is enticement. Enticement occurs when the opportunity for illegal or unauthorized actions is provided but perpetrators make their own decisions to perform such action. Entrapment, which is illegal, occurs when the honeypot owner actively solicits visitors to access the site and then charges them with unauthorized intrusion. In other words, it is considered to be entrapment when you trick or encourage a perpetrator into performing an illegal or unauthorized action.
Understanding Padded Cells
A padded cell system is similar to a honeypot, but it performs intrusion isolation using a different approach. When an IDS detects an intruder, that intruder is automatically transferred to a padded cell. The padded cell has the look and layout of the actual network, but within the padded cell the intruder can neither perform malicious activities nor access any confidential data.
A padded cell is a simulated environment that offers fake data to retain an intruder’s interest. The transfer of the intruder into a padded cell is performed without informing the intruder that the change has occurred. Like a honeypot, a padded cell system is heavily monitored and used by administrators to gather evidence for tracing and possible prosecution.
Understanding Vulnerability Scanners
Another type of IDS-related tool is a vulnerability scanner. Vulnerability scanners are used to test a system for known security vulnerabilities and weaknesses. They are used to generate reports that indicate the areas or aspects of the system that need to be managed to improve security. The reports may recommend applying patches or making specific configuration or security setting changes to improve or impose security.
A vulnerability scanner is only as useful as its database of security issues. Thus, the database must be updated from the vendor often to provide a useful audit of your system. The use of vulnerability scanners in cooperation with IDSs may help reduce false positives by the IDS and keep the total number of overall intrusions or security violations to a minimum. When discovered vulnerabilities are patched quickly and often, the system provides a more secure environment.
An extension to the concept of the IDS is the intrusion prevention system (IPS), which was mentioned earlier. An IPS seeks to actively block unauthorized connection attempts or illicit traffic patterns as they occur. IPS designs fall under the same type (host and network based) and classification (behavior and signature based) as IDS counterparts, and they are often deployed together for complete network coverage. Additionally, many IPS platforms are capable of dissecting higher-level application protocols in search of malicious payloads. In fact, the line between IDSs and IPSs can be quite blurry in that many self-professed IDSs have IPS capabilities. These days, detection and prevention systems occur together more than they do separately.
In security terms, a penetration occurs when an attack is successful and an intruder is able to breach the perimeter around your environment. A breach can be as small as reading a few bits of data from your network or as big as logging in as a user with unrestricted privileges. A primary goal of security is to prevent penetrations.
One common method to test the strength of your security measures is to perform penetration testing, a vigorous attempt to break into your protected network using any means available. It is common for organizations to hire external consultants to perform penetration testing so testers are not privy to confidential elements of the environment’s security configuration, network design, and other internal secrets.
Penetration testing seeks to find any and all detectable weaknesses in your existing security perimeter. The operative term is detectable; there are undetected and presently unknowable threats lurking in the large-scale infrastructure of network software and hardware design that no amount of penetration testing can directly discover or reveal. Once a weakness is discovered, countermeasures can be selected and deployed to improve security in the environment. One significant difference between penetration testing and an actual attack is that once a vulnerability is discovered during a penetration test, the intrusion attempt ceases before a vulnerability exploit can cause any damage. There are open-source and commercial tools (such as Metasploit and Core IMPACT) that take penetration testing one step further and attempt to exploit known vulnerabilities in systems and networks and may be used by good guys and bad guys alike.
Penetration testing may employ automated attack tools or suites or be performed manually using common network utilities and scripts. Automated attack tools range from professional vulnerability scanners to wild, underground tools discovered on the Internet. Tools are also often used for penetration testing performed manually, but the real emphasis is on knowing how to perpetrate an attack.
Penetration testing should be performed only with the consent and knowledge of management (and security staff). Performing unapproved security testing could cause productivity losses, trigger emergency response teams, or even cost you your job and potentially earn you jail time.
Regularly staged penetration tests are a good way to accurately judge the security mechanisms deployed by an organization. Penetration testing can also reveal areas where patches or security settings are insufficient and where new vulnerabilities have developed. To evaluate your system, benchmarking and testing tools are available for download at www.cisecurity.org.
![]()
We discuss penetration testing further in Chapter 14, “Auditing and Monitoring.”
Identifying and repelling attacks require an explicit, well-defined body of knowledge about their nature and occurrence. Some attack patterns leave behind signatures that make them readily apparent to casual observation with IDS instrumentation; other forms of attack are esoteric or not conducive to pattern-matching engines and therefore must be measured against a baseline of acceptable activity.
What elements or properties signify an attack sequence rather than some benign traffic formation? Answering this question depends on keeping up with the latest attacks, vulnerabilities, exploits, and demands that careful, attentive security professionals keep up with security bulletins (like those from the U.S. Computer Emergency Readiness Team at www.us-cert.gov/cas/bulletins or those from the Common Vulnerabilities and Exposures database at http://cve.mitre.org).
As discussed in Chapter 1, one of the goals of access control is to prevent unauthorized access to objects. This includes access into a system (a network, a service, a communications link, a computer, and so forth) or access to data. In addition to controlling access, security seeks to prevent unauthorized alteration and disclosure and to provide consistent availability (remember the CIA Triad in Chapter 1).
However, malicious entities often focus on violating the security perimeter of a system to obtain access to data, alter or destroy data, and inhibit valid access to data and resources. The actual means by which attacks are perpetrated vary greatly. Some are extremely complex and require detailed knowledge of the victimized systems and programming techniques, whereas others are dead simple to execute and require little more than an IP address and the ability to manipulate a few tools or scripts. But even though there are many kinds of attacks, they can be grouped into a handful of classifications or categories.
The following are the most common or well-known access control attacks or attack methodologies (these are listed in alphabetical order):
- Brute-force and dictionary attacks
- Denial-of-service attacks
- Malware: viruses, worms, Trojans, spyware, and more
- Man-in-the-middle attacks
- Sniffers
- Spamming
- Spoofing
All these methods will eventually be attempted on your network. Assessing the severity of each on a case-by-case basis is less relevant than assessing each element as part of a much larger combination of risk potential and threat value.
Simple one-stage attacks (brute-force/dictionary lookups, spoofing, malware, and denial-of-service attacks) are the most common because they’re the easiest to mount against a target and require only basic Internet access. Eavesdropping, sniffing, and man-in-the-middle attacks are more complex and involve an intrusion component to propel an attacker inside the network perimeter. They occur less frequently but can have more serious consequences if they succeed. Malware straddles these two categories in that anyone can propagate it, many can assemble kit-based instances, but expert malefactors create the most dangerous malware.
Brute-Force and Dictionary Attacks
We discuss brute-force and dictionary attacks together because they are waged against the same entity: passwords. Either type of attack can be waged against a password database file or against an active logon prompt.
A brute-force attack is an attempt to discover passwords for user accounts by systematically attempting all possible combinations of letters, numbers, and symbols. With the speed of modern computers and the ability to employ distributed computing, brute-force attacks prove successful even against strong passwords. With enough time, all passwords can be discovered using a brute-force attack. Most passwords of 14 characters or less can be discovered within 7 days on a fast system using a brute-force attack program against a stolen password database file (the actual time it takes to discover passwords depends upon the algorithm used to encrypt them).
This window can be exploited in a time-memory trade-off known as rainbow tables, often used to speed up and amplify dictionary attacks or hybrid combinations of brute-force and dictionary attacks. Precomputed inputs (passwords and password combinations) are compactly represented in an iterated series of variations that make up a dictionary of possible password hashes. These precomputed hashes are then referenced against target hashes to find a matching entry. Two immediate problems arise: Any given password must be predetermined by some means (dictionary word lists, combinations and variations of alphanumeric elements, and so on) and contain no password salts, which extend the length and complexity of a password entry. Both of these conditions make rainbow tables effective only so long as the target password is knowable and predictably defined. Nevertheless, rainbow tables often play a complementary front-runner role to more exhaustive brute-force methods.
The longer a password (or the greater the number of keys in an algorithm’s key space), the more costly and time-consuming a brute-force attack becomes. As the number of possibilities increases, the cost of performing an exhaustive attack goes up. In other words, the longer the password, the more secure it is against brute-force attacks. In addition, some password storage facilities also use a technique called “salting” to add additional bits (and increase complexity) for stored password hash values to stymie such attacks and make password data less susceptible to brute-force methods.
A dictionary attack is an attempt to discover passwords by presenting every possible password in a predefined list of common or expected passwords. This type of attack earns it name because the possible password list is so long, it is as if you were using an entire dictionary one word at a time to discover passwords.
Password attacks employ a specific cryptographic attack method known as the birthday attack. This attack is also called reverse hash matching or the exploitation of collision. Basically, the attack exploits the fact that if two messages are hashed and the hash values are the same, then the two messages are probably the same. A way of expressing this in mathematical or cryptographic notation is H(M)=H(M'). Passwords are stored in an account’s database file on secured systems. Instead of being stored as plain text, though, passwords are hashed and only their hash values retained. This provides a reasonable level of protection. However, using reverse hash matching, a password attacker tool looks for possible passwords (through either brute-force or dictionary methods) with the same hash value as an entry stored in the account’s database file. When a hash value match occurs, then the tool is said to have cracked the password.
Combinations of these two password attack methodologies can be used as well. For example, a brute-force attack could use a dictionary list as one source for its guesswork.
![]()
Finesse and Careful Access Controls Beat Brute Force
Brute-force login attacks are relatively simple and rather effective against many types of targets. Claire sees thousands of failed and unauthorized connection attempts on her Internet-facing secure FTP servers, which includes Damien’s constant inability to remember his own password. The effectiveness of a brute-force login attack hinges entirely on the notion that people tend to seek the path of least resistance, which in this case means using easily guessed passwords devoid of creativity or variation.
Claire runs a modified version of the secure FTP server that thwarts brute-force attempts and includes a user/group access list for its configuration, but she also wisely deploys an access list of permitted IPs on the firewall. This gives her several layers of protection over less-experienced administrators who don’t enforce strong password choices or configurations and rule sets.
She knows that for every Damien in her user group who can’t understand why his password is of a certain length and difficulty level, there’s an Elaine or Frank on some other network who never forgets their password. Neither does the surreptitious attacker who keeps using their accounts, the passwords for which he found in a dictionary-driven attack.
Dictionary attacks often succeed because it’s human nature to select passwords based on personal experiences. Unfortunately, those personal experiences are often broadcast to the world simply by the way you live and act on a daily basis. If you are a sports fan, your password might be based on a player’s name or a hit record. If you have children, your password might be based on their names or birth dates. If you work in a technical industry, your password might be based on industry acronyms or product names. The more data about a victim that a custom dictionary list includes, whether that data is obtained through intelligence gathering, dumpster diving, or social engineering, the more successful it will be.
Protecting passwords from brute-force and dictionary attacks requires numerous security precautions and rigid adherence to a strong security policy. Here are some key elements to consider:
Control physical access to systems. You must control physical access to your systems. If a malicious entity can gain physical access to an authentication server, they can often steal the password file within seconds. Once a password file is stolen, all passwords should be considered compromised.
Control electronic access to password files. Tightly control and monitor electronic access to password files. End users and those who are not account administrators have no need to access the password database file for regular, daily work tasks. If you discover unauthorized access to the database file, investigate immediately. If you cannot determine that all such access is valid, then consider all passwords compromised.
Create a strong password policy. Craft a password policy that programmatically enforces strong passwords and provides guidance to help end users create stronger passwords. The stronger and longer a password, the longer it will take for it to be discovered in a brute-force attack. However, with enough time, all passwords can be discovered via brute-force methods. Thus, changing passwords regularly is required to maintain security. Static passwords older than 30 days should be considered compromised even if no other aspect of a security breach has been discovered.
Deploy multifactor authentication. Deploy multifactor authentication, such as using biometrics or token devices. If passwords are not the only means used to protect the security of a network, their compromise will not automatically result in a system breach.
Use account lockout controls. Use account lockout controls to prevent brute-force and dictionary attacks against logon prompts. For those systems and services that don’t support account lockout controls, such as most FTP servers, employ extensive logging and an IDS to look for attempted fast and slow password attacks.
Encrypt password files. Encrypt password files with the strongest encryption available for your OS. Maintain rigid control over all media that have a copy of the password database file, such as backup tapes and some types of boot or repair disks.
Passwords are a poor security mechanism when used as a sole deterrent against unauthorized access. Brute-force and dictionary attacks show that passwords alone offer little more than a temporary blockade. Don’t lose sight of the importance of physical security, multifactor authentication, and constant monitoring of access behaviors and patterns of use.
Denial-of-Service Attacks
Denial-of-service (DoS) attacks are attacks that prevent a system from processing or responding to legitimate traffic or requests for resources and objects. The most common form of denial-of-service attacks is transmitting so many data packets to a server that it cannot process them all. Other forms of denial-of-service attacks focus on the exploitation of a known fault or vulnerability in an operating system, service, or application. Exploiting the fault often results in system crash or 100 percent CPU utilization. No matter what the actual attack consists of, any attack that renders its victim unable to perform normal activities can be considered a denial-of-service attack. Denial-of-service attacks can result in system crashes, system reboots, data corruption, blockage of services, and more.
Unfortunately, denial-of-service attacks based on flooding (that is, sending sufficient traffic to a victim to cause a DoS) are a way of life on the Internet. In fact, there are few means by which you can prevent any and all denial-of-service flood attacks (though individual attacks can be shut down once they’re recognized and the source addresses involved identified). Furthermore, because of the ability to spoof packets or exploit legitimate Internet services, it is often impossible to trace the actual origin for such an attack or to apprehend the culprit.
There are several types of DoS flood attacks. The first, or original, type of attack employed a single attacking system flooding a single victim with a steady stream of packets. Those packets could be valid requests that were never completed or malformed or fragmented packets that consume the attention of the victimized system. This simple form of DoS is easy to terminate just by blocking packets from the source IP address.
Another form of attack is called a distributed denial of service (DDoS). A distributed denial of service occurs when the attacker compromises several systems and uses them as launching platforms against one or more victims. The compromised systems used in the attack are often called slaves or zombies, which operate in loose federations called botnets (short for “network of robots”) managed in the background by shadowy control stations and covert servers. A DDoS attack results in the victims being flooded with data from numerous sources. DDoS attacks can be stopped by blocking packets from the compromised systems. But this can also result in blocking legitimate traffic because the sources of the flood packets are victims themselves and not the original perpetrators of the attack. These types of attacks are labeled as distributed because numerous systems are involved in the propagation of the attack against the victim.
A more recent form of DoS, called a distributed reflective denial of service (DRDoS), has been discovered. DRDoS attacks take advantage of the normal operation mechanisms of key Internet services, such as DNS and router update protocols. DRDoS attacks function by sending numerous update, session, or control packets to various Internet service servers or routers with a spoofed source address for the intended victim. Usually these servers or routers are part of the high-speed, high-volume Internet backbone trunks. What results is a flood of update packets, session acknowledgment responses, or error messages sent to the victim. A DRDoS attack can result in so much traffic that upstream systems are adversely affected by the sheer volume of data focused on the victim. This type of attack is called a reflective attack because the high-speed backbone systems reflect the attack to the victim. Unfortunately, these types of attacks cannot be prevented because they exploit normal functions of the systems involved. Blocking packets from these key Internet systems effectively cuts the victim off from a significant section of the Internet.
Not all instances of DoS result from a malicious attack. Errors in coding operating systems, services, and applications have resulted in DoS conditions. For example, a process failing to release control of the CPU or a service consuming system resources out of proportion to the service requests it is handling can cause DoS conditions. Most vendors quickly release patches to correct these self-inflicted conditions, so it is important to stay informed.
Many forms of DoS attacks have been committed over the Internet. Specific, historically significant examples of denial-of-service attacks are discussed in greater detail in the following sections.
SYN Flood Attack
SYN flood attacks are waged by breaking the standard three-way handshake used by TCP/IP to initiate communication sessions. Normally, a client sends a SYN packet to a server, the server responds with a SYN/ACK packet to the client, and the client then responds with an ACK packet back to the server. This three-way handshake establishes a communication session that is used for data transfer until the session is terminated (using a three-way handshake with FIN and ACK packets). A SYN flood occurs when numerous SYN packets are sent to a server but the sender never replies to the server’s SYN/ACK packets with the final ACK.
![]()
A TCP session can also be terminated with an RST (reset) packet. In some instances, attackers forge or counterfeit reset packets in attempts to disconnect other users.
In addition, bogus SYN packets usually have a spoofed source address, so the SYN/ACK response is sent elsewhere, not to the actual originator of the packets. The server waits for the client’s ACK packet, often for several seconds, holding open a session and consuming system resources. If a significant number of sessions are held open (for example, through the receipt of a flood of SYN packets), this causes a DoS. A server can be easily overtaxed by keeping sessions that are never finalized open, thus causing a failure. That failure can be as simple as an inability to respond to legitimate requests for communications or as serious as a frozen or crashed system.
One countermeasure to SYN flood attacks is increasing the number of connections a server can support. However, this usually requires additional hardware resources (memory, CPU, and so on) and may not be possible for all operating systems or network services. A more useful countermeasure is to reduce the time-out period while waiting for the concluding ACK packet. However, this can also result in failed sessions for clients connected using slower links or hindered by intermittent Internet traffic jams. Network-based IDSs may offer some protection against sustained SYN flood attacks by noticing that numerous SYN packets originate from one or only a few locations, resulting in incomplete sessions. An IDS could warn of such an attack or dynamically block flooding attempts.
Smurf Attack
A smurf attack occurs when an amplifying server or network is used to flood a victim with useless data. An amplifying server or network is any system that generates multiple response packets, such as Internet Control Message Protocol (ICMP) echo packets or special User Datagram Protocol (UDP) packets, from a single submitted packet.
A common smurf attack method is to send a message to the broadcast address for a subnet or network so that every node on that network produces one or more response packets. The attacker sends information request packets with the victim’s spoofed source address to the amplification system. Thus, all the responses are sent to the victim. If the amplification network can produce sufficient response packet volume, the victim’s system will experience a DoS.
Figure 2.1 shows the basic elements in a smurf attack. The attacker sends multiple IMCP ping packets with a spoofed source address for the victim (V) and a destination with the broadcast address for the amplification network (AN:B). The amplification network responds with high volumes of echo packets to the victim, thus fully consuming the victim’s connection bandwidth. Another DoS attack similar to smurf is called fraggle. Fraggle attacks employ spoofed UDP packets rather than ICMP packets.
FIGURE 2.1 A smurf attack
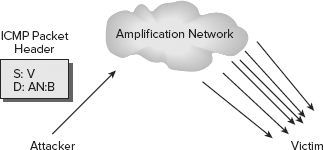
Countermeasures for smurf attacks include disabling directed broadcasts on all network border routers and configuring all systems to drop ICMP ECHO packets. An IDS may be able to detect this type of attack, but there are no means to prevent the attack other than blocking the addresses of the amplification network. This tactic is problematic because the amplification network is usually also a victim.
Ping-of-Death, Stream, Teardrop, and Land Attacks
The attacks named in this section date back as far as the 1990s, but each uses interesting and devastating (at the time of their creation) techniques to subvert how incoming IP data is handled on the unwitting recipient’s end. In the interim, specific defenses have been erected so that these attacks are highly unlikely to succeed today.
A ping-of-death attack employs an oversized ping packet. Using special tools, an attacker sends numerous oversized ping packets to a victim. In many cases, when the victimized system attempts to process those packets, an error occurs, causing the system to freeze, crash, or reboot. The ping of death is really a buffer-overflow attack, but because it often crashes its target server, it is considered a DoS attack. Countermeasures to this attack include keeping up-to-date with OS and software patches, properly coding in-house applications to prevent buffer overflows, running no untested code with system- or root-level privileges, and blocking ping packets at border routers/firewalls.
A stream attack occurs when a large number of packets are sent to numerous ports on a victim system using random source and sequence numbers. The processing performed as the victim system attempts to make sense of the data results in a DoS. Countermeasures include patching the system and using an IDS for dynamic blocking.
A teardrop attack occurs when an attacker exploits an operating system bug. This bug exists in the routines used to reassemble (that is, resequence) fragmented packets. An attacker sends numerous specially formatted fragmented packets to the victim, which causes the system to freeze or crash. Countermeasures for this attack include patching the OS and deploying an IDS for detection and dynamic blocking.
A land attack occurs when the attacker sends numerous SYN packets to a victim and the SYN packets have been spoofed to use the same source and destination IP address and port number as the victim. This causes the system to think it initiated a TCP/IP session with itself, which causes a system failure along with a system freeze, crash, or reboot. Countermeasures for this attack include patching the OS and deploying an IDS for detection and dynamic blocking.
Beware the Botnets!
All the attack methods described in the preceding section are well documented today, which grants them zero stealth capability and minimal effectiveness when used against modern computing networks and operating systems. A more troubling trend has, however, emerged in recent years, including the rise of botnets. These are coordinated networks of compromised machines used in a cohesive or scheduled manner to attack, compromise, and disrupt other end users or entire networks. They are also widely employed to distribute spam on behalf of third parties who seek to find paying customers through unwanted email or to disseminate phishing lures to part unwary or naive recipients from their hard-earned cash.
For every botnet, there is usually one or more controlling computers, often called botnet controllers, which provide cutouts between the actual botnet operator (usually called a bot herder) and the compromised machines. This enables bot herders to control larger numbers of computers (many botnets exceed more than 100,000 compromised PCs, and botnets bigger than 10 million machines were reported in 2008) and to protect themselves from discovery even when their botnets are detected and disabled.
With hundreds of thousands to tens of millions of potential attack machines in their corrals, botnet abilities to mount huge and devastating DoS attacks are painfully obvious. As we write this chapter, they’ve been used recently in attacks against high-profile security organizations such as SANS and the CIA as well as major Web portals such as Google, Yahoo, and MSN.
Spoofing Attacks
Spoofing is the art of pretending to be something you’re not. Spoofing attacks consist of replacing a valid source and/or destination IP address and node numbers with false ones. Spoofing is involved in most attacks because it grants attackers the ability to hide their identities through misdirection. Spoofing is employed when an intruder uses a stolen username and password to gain entry, when an attacker changes the source address in a malicious packet, or when an attacker assumes the identity of a client to fool a server into transmitting controlled data.
Two specific types of spoofing attacks are impersonation and masquerading. Ultimately, these attacks are the same: Someone is able to gain access to a secured system by pretending to be someone else. These attacks often result in unauthorized access to a system through a valid user account that has been compromised. Impersonation is considered a more active attack because it requires the capture of authentication traffic and the replay of that traffic in such a way as to gain access to the system. Masquerading is considered a more passive attack because the attacker uses previously stolen account credentials to log on to a secured system.
Countermeasures for spoofing attacks include patching the OS and software, enabling source/destination verification on routers, and employing an IDS to detect and block attacks. As a general rule, whenever your system detects spoofed information, it should record relevant data elements into a log file; then the system should drop or delete the spoof itself.
Man-in-the-Middle Attacks
A man-in-the-middle attack occurs when a malicious user is able to gain a position between the two endpoints of an ongoing communication. There are two types of man-in-the-middle attacks. One involves copying or sniffing the traffic between two parties; this is basically a sniffer attack (see the next section). The other involves attackers positioning themselves in the line of communication where they act as a store-and-forward or proxy mechanism (see Figure 2.2). The attacker functions as the receiver for data transmitted by the client and the transmitter for data sent to the server. The attacker is invisible to both ends of the communication link and is able to alter the content or flow of traffic. Through this type of attack, the attacker can collect logon credentials or sensitive data as well as change the content of the messages exchanged between the two endpoints.
FIGURE 2.2 A man-in-the-middle attack
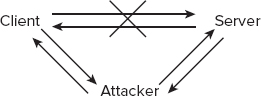
To perform this type of attack, the attacker must often alter routing information and DNS values, steal IP addresses, or falsify ARP lookups to impersonate a server from the perspective of the client and to impersonate the client from the perspective of the server.
An offshoot of a man-in-the-middle attack is known as a hijack attack. In this type of attack, a malicious user is positioned between a client and server and then interrupts the session and takes it over. Often, the malicious user impersonates a client to extract data from the server. The server is unaware that any change in the communication partner has occurred. The client is aware that communications with the server have ceased, but there is no indication as to why the communications were terminated, so it’s invariably written off as a dropped connection.
Another type of attack, a replay attack (also known as a playback attack), resembles hijacking. A malicious user records traffic between a client and server; then packets sent from the client to the server are played back or retransmitted to that server with slight variations in the time stamp and source IP address (that is, spoofing). In some cases, this allows a malicious user to restart an old link with a server. Once this communication session is reopened, the malicious user can attempt to obtain data or additional access. Such captured traffic is often authentication traffic (which typically includes logon credentials, such as username and password), but it could be service access traffic or message control traffic. Replay attacks can be prevented by employing complex sequencing rules and time stamps to prevent retransmitted packets from being accepted as valid.
Countermeasures to these types of attacks require improvement in session establishment, identification, and authentication processes. Some man-in-the-middle attacks are thwarted through patching the OS and software. An IDS cannot usually detect man-in-the-middle or hijack attacks, but it can detect abnormal activities occurring over “secured” communication links. Operating systems and many IDSs can often detect and block replay attacks.
Sniffer Attacks
A sniffer attack (also known as a snooping attack) is any activity that results in a malicious user obtaining information about a network or the traffic over that network. A sniffer is some kind of packet-capturing program that dumps the contents of packets traveling over a network medium into a file. Sniffer attacks often focus on the initial connections between clients and servers to obtain logon credentials (for example, usernames and passwords), secret keys, and so on. When performed properly, sniffing attacks are invisible to all other entities on the network and often precede spoofing or hijack attacks. A replay attack (discussed in the preceding section) is a type of sniffer attack.
Countermeasures to prevent or stop sniffing attacks require improving the physical access control, actively monitoring for sniffing signatures (such as looking for packet delay, additional routing hops, or lost packets, which can be performed by some IDSs), and using encrypted traffic over internal and external network connections.
Spamming Attacks
Spam is the term that describes unsolicited email, newsgroup, or discussion forum messages. Spam can be as innocuous as an advertisement from a well-meaning vendor or as malignant as floods of unrequested messages with viruses or Trojan horses attached. Aside from emails that carry malicious (malware) payloads, spam is most often perceived as a type of denial-of-service attack, though it is also a significant security threat as well. As the level of spam increases, locating or accessing legitimate messages can be difficult. In addition to its nuisance value, spam consumes a significant portion of Internet resources (in the form of bandwidth and CPU processing), resulting in overall slower Internet performance and lower bandwidth availability for everyone.
Spamming attacks are directed floods of unwanted messages to a victim’s email inbox or other messaging system. Such attacks cause DoS issues by filling up storage space and preventing legitimate messages from being delivered. In extreme cases, spamming attacks can cause system freezes or crashes and interrupt the activity of other users on the same subnet or ISP.
Spam attack countermeasures include using email filters, email proxies, and IDSs to detect, track, and terminate spam flood attempts.
Crackers, Hackers, and Attackers
Crackers are malicious users intent on waging an attack against a person or system. Crackers may be motivated by greed, power, or recognition. Their actions can result in stolen property (data, ideas, and so on), disabled systems, compromised security, negative public opinion, loss of market share, reduced profitability, and lost productivity.
A term commonly confused with crackers is hackers. Hackers are technology enthusiasts with no malicious intent. Many authors and the media often use the term hacker when they are actually discussing issues relating to crackers. To avoid confusion, we use the term attacker for malicious intruders throughout this book.
Thwarting an attacker’s attempts to breach your security or perpetrate DoS attacks requires vigilant effort to keep systems patched and properly configured. IDSs and honeypot systems often offer means to detect and gather evidence to prosecute attackers once they have breached your controlled perimeter.
Access control is used to regulate or specify which objects a subject can access and what type of access is allowed or denied. Numerous attacks, discussed in the previous sections, are designed to bypass or subvert access control. In addition to specific countermeasures for each of these attacks, you can use certain measures to help compensate for access control violations. A compensation measure does not directly prevent problems but rather provides a means by which you can design resiliency into your environment to support a quick recovery or response.
Backups are the best means of compensation against access control violations. With reliable backups and a mechanism to restore data, any corruption or file-based asset loss can be repaired, corrected, or restored. RAID technology can provide fault tolerance to allow for quick recovery in the event of a failure or severe access violation.
In general, avoiding single points of failure and deploying fault-tolerant systems helps ensure that the loss of use or control over a single system, device, or asset does not directly lead to the compromise or failure of your entire network environment. Fault tolerance countermeasures seek to combat threats to design reliability. Having backup communication routes, mirrored servers, clustered systems, failover systems, and so on can provide instant automatic or quick manual recovery in the event of an access control violation.
Your business continuity plan should include procedures for dealing with access control violations that threaten the stability of your mission-critical processes. Likewise, you should include in your insurance coverage categories of assets for which you may require compensation in the event of severe access control violations.
Managing a system’s access control involves a thorough understanding of system monitoring and common forms of malicious attacks. Monitoring a system provides the basis for accountability of authenticated users. Audit trails and logging files provide details about valid and unauthorized activities as well as system stability and performance. Using an IDS can simplify the process of examining the copious amount of data gathered through monitoring.
There are two types of IDSs: host based and network based. A host-based IDS is useful for detecting specific intrusions on single systems. A network-based IDS is useful for detecting overall aberrant network activity. There are two types of detection methods employed by IDSs: knowledge based and behavior based. A knowledge-based IDS uses a database of attack signatures to detect intrusion attempts. However, it fails to recognize new attack methods. A behavior-based IDS uses learned patterns of activity to detect abnormal events, but it produces numerous false positives until it gains sufficient knowledge about the system it is monitoring.
Honeypots, honeynets, and padded cells are useful tools to prevent malicious activity from occurring on a production network while enticing intruders to stick around long enough to gather evidence for prosecution.
Vulnerability scanners are signature-based detection tools that scan a system for a list of known vulnerabilities. These tools produce reports enumerating any discovered vulnerabilities and provide recommendations to improve system security.
Penetration testing is a useful mechanism to check the strength and effectiveness of deployed security measures and an organization’s security policy. Be sure to obtain management approval before performing a penetration test.
There are numerous methods of attacks that intruders perpetrate against systems. Some of the more common attacks include brute-force, dictionary, denial-of-service, spoofing, man-in-the-middle, spamming, and sniffing attacks. Each type of attack employs different means to infiltrate, damage, or interrupt systems, and each has unique countermeasures to prevent them.
Understand the use of monitoring in relation to access controls. Monitoring is used to hold subjects accountable for their actions and to detect abnormal or malicious activities.
Understand the need for intrusion detection systems (IDSs) and that they are only one component in a security policy. An IDS is needed to automate the process of discovering anomalies in subject activity and system event logs. IDSs are primarily used to detect intrusions or attempted intrusions. An IDS alone will not secure a system. It must be used in conjunction with access controls, physical security, and maintaining secure systems on the network.
Know the limits of using host-based IDSs. Host-based IDSs can monitor activity on a single system only. In addition, they can be discovered by attackers and disabled.
List the pros and cons of network-based IDSs. Network-based IDSs can monitor activity on the network medium, and they can be made invisible to attackers. They do not, however, work well on switched networks.
Know how to explain differences between knowledge-based and behavior-based IDS detection methods. Knowledge-based detection employs a database of attack signatures. Behavior-based detection learns what is normal about a system and assumes that all unknown activities are abnormal or possible signs of intrusion.
Understand honeypots, honeynets, and padded cells. A honeypot is a fake system or network that is designed to lure intruders with fake data to keep them on the system long enough to gather tracking information. A honeynet is a network composed of two or more honeypots. A padded cell is a simulated environment that intruders are seamlessly moved into once they are detected on the system. The simulated environment varies from the real environment only in that the data is fake and therefore malicious activities cause no harm.
Be able to explain vulnerability scanners and penetration testing. Vulnerability scanners are used to detect known security vulnerabilities and weaknesses. They are used to generate reports that indicate the areas or aspects of the system that need to be managed to improve security. Penetration testing is used to test the strength and effectiveness of deployed security measures with an authorized attempted intrusion attack.
Know how brute-force and dictionary attacks work. Brute-force and dictionary attacks are carried out against a password database file or the logon prompt of a system. They are designed to discover passwords. In brute-force attacks, all possible combinations of keyboard characters are used, whereas a predefined list of possible passwords is used in a dictionary attack.
Understand the need for strong passwords. Strong passwords make password-cracking utilities less successful. Strong passwords are dynamic passwords and should be strengthened by using two-factor authentication, enabling account lockouts, and using strong encryption on the password database file.
Know what denial-of-service (DoS) attacks are. DoS attacks prevent a system from responding to legitimate requests for service. The two types of DoS attacks are traffic flooding and fault exploitation.
Be able to explain the SYN flood DoS attack. The SYN flood DoS attack takes advantage of the TCP/IP three-way handshake to inhibit a system by requesting numerous connection sessions but failing to provide the final acknowledgment packet.
Know how the smurf DoS attack works. Smurf attacks employ an amplification network to send numerous response packets to a victim.
Know how ping-of-death DoS attacks work. Ping-of-death attacks send numerous oversized ping packets to the victim, causing the victim to freeze, crash, or reboot.
Understand stream DoS attacks. Stream attacks send a large number of packets to numerous ports on the victim system by using random source and sequence numbers. The processing performed by the victim system attempting to make sense of the data will result in a DoS.
Be able to explain teardrop DoS attacks. A teardrop attack occurs when an attacker exploits an operating system bug in the routines used to reassemble fragmented packets. An attacker sends numerous specially formatted fragmented packets to the victim, which causes the system to freeze or crash.
Understand land DoS attacks. A land attack occurs when an attacker sends numerous SYN packets to a victim that have been spoofed to use the victim’s own source and destination IP address and port number. This causes the victim to think it sent a TCP/IP session-opening packet to itself, which in turn causes a system failure, usually resulting in a freeze, crash, or reboot.
Understand botnets, botnet controllers, and botnet herders. A botnet is a collection of compromised PCs whose unauthorized software payload includes remote control software that lets a coordinating computer (the botnet controller) issue instructions and schedule and coordinate attacks from those compromised PCs. The botnet herder is the often shadowy person or group in the background who manages the botnet controllers and determines what attacks or activities the botnet computers will undertake.
Understand spoofing attacks. Spoofing attacks are any form of attack that uses modified packets in which the valid source and/or destination IP address and node numbers are replaced with false ones. Spoofing grants attackers the ability to hide their identities through misdirection.
Understand man-in-the-middle attacks. A man-in-the-middle attack occurs when a malicious user is able to gain position between the two endpoints of a communications link. There are two types of man-in-the-middle attacks. One involves copying or sniffing traffic between two parties; this is basically a sniffer attack. The other requires the attacker to position itself in the line of communication and act as a store-and-forward or proxy mechanism between the two endpoints.
Be able to explain hijack attacks. The hijack attack is an offshoot of a man-in-the-middle attack. In this type of attack, a malicious user positions himself between a client and server and then interrupts the session and takes it over. Often, the malicious user impersonates the client to extract data from the server. The server is unaware that any change in the communication partner has occurred.
Understand replay or playback attacks. In a replay attack, a malicious user records traffic between a client and server. Then packets sent from the client to the server are played back or retransmitted to the server with slight variations in the time stamp and source IP address (that is, spoofing). In some cases, this allows a malicious user to restart an old session with a server.
Know what sniffer attacks are. A sniffer attack (or snooping attack) is any activity that results in a malicious user obtaining information about a network or traffic on that network. A sniffer is a packet-capturing program that dumps the contents of packets traveling over the network medium into a file.
Understand spamming attacks. Spam is a term describing unsolicited email, newsgroup, or discussion forum messages. Spam can be as innocuous as an advertisement from a well-meaning vendor or as malignant as floods of unrequested messages with viruses or Trojan horses attached. Spam is usually not a security threat but rather a type of denial-of-service attack. As the level of spam increases, locating or accessing legitimate messages can be difficult.
Be able to list the countermeasures to all types of DoS attacks and to spoofing, man-in-the-middle, sniffer, and spamming attacks. Countermeasures include patching the OS for vulnerabilities, using firewalls and routers to filter and/or verify traffic, altering system/protocol configuration, and using IDSs.
1. Describe the two primary intrusion detection system types.
2. Identify and define the three intrusion detection system response types.
3. What is penetration testing, and why is it necessary?
4. Name at least four common methods of network-based attack.
1. Host-based IDSs examine events on individual computers in great detail, including file activities, accesses, and processes. Network-based IDSs examine general network events and anomalies through traffic evaluation.
2. Active response directly responds to malicious network activity or host process. Passive response observes and reports findings of intrusion or malicious activity but does not take action. Hybrid response halts identified malicious activity, records the event, and potentially notifies administration.
3. Penetration testing is the act of detecting infrastructure or system weakness, identifying vulnerabilities, and possibly exercising exploitative attacks as demonstrative proof.
4. Brute-force and dictionary word list attacks; denial-of-service (DoS) attacks, distributed DoS (DDoS), and distributed reflective DoS (DRDoS); spoofing attacks; botnets; protocol sniffing attacks; spamming; man-in-the-middle attacks; vulnerability exploitation; and resource/service saturation attack.
1. What is used to keep subjects accountable for their actions while they are authenticated to a system?
A. Access controls
B. Monitoring
C. Account lockout
D. Performance reviews
2. Which of the following tools is most useful in sorting through large log files to search for intrusion-related events?
A. Text editor
B. Vulnerability scanner
C. Password cracker
D. IDS
3. An intrusion detection system (IDS) is primarily designed to perform what function?
A. Detect abnormal activity.
B. Detect system failures.
C. Rate system performance.
D. Test a system for vulnerabilities.
4. IDSs are capable of detecting which types of abnormal or unauthorized activities? (Choose all that apply.)
A. External connection attempts
B. Execution of malicious code
C. Unauthorized access attempts to controlled objects
D. None of the above
5. Which of the following is true for a host-based IDS?
A. It monitors an entire network.
B. It monitors a single system.
C. It’s invisible to attackers and authorized users.
D. It’s ineffective on switched networks.
6. Which of the following types of IDS is effective only against known attack methods?
A. Host based
B. Network based
C. Knowledge based
D. Behavior based
7. Which type of IDS can be considered an expert system?
A. Host based
B. Network based
C. Knowledge based
D. Behavior based
8. Which of the following is a fake network designed to tempt intruders with unpatched and unprotected security vulnerabilities and false data?
A. IDS
B. Honeynet
C. Padded cell
D. Vulnerability scanner
9. When a padded cell is used by a network for protection from intruders, which of the following is true?
A. The data offered by the padded cell is what originally attracts the attacker.
B. Padded cells are a form of entrapment.
C. The intruder is seamlessly transitioned into the padded cell once they are detected.
D. Padded cells are used to test a system for known vulnerabilities.
10. Which of the following is true regarding vulnerability scanners?
A. They actively scan for intrusion attempts.
B. They serve as a form of enticement.
C. They locate known security holes.
D. They automatically reconfigure a system to a more secure state.
11. When using penetration testing to verify the strength of your security policy, which of the following is not recommended?
A. Mimicking attacks previously perpetrated against your system
B. Performing attacks without management consent
C. Using manual and automated attack tools
D. Reconfiguring the system to resolve any discovered vulnerabilities
12. Which of the following attacks is an attempt to test every possible combination against a security feature in order to bypass it?
A. Brute-force attack
B. Spoofing attack
C. Man-in-the-middle attack
D. Denial-of-service attack
13. Which of the following is not a valid measure to take to improve protection against brute-force and dictionary attacks?
A. Enforce strong passwords through a security policy.
B. Maintain strict control over physical access.
C. Require all users to log in remotely.
D. Use two-factor authentication.
14. Which of the following is not considered a denial-of-service attack?
A. Teardrop
B. Smurf
C. Ping of death
D. Spoofing
15. A SYN flood attack works by what mechanism?
A. Exploiting a packet processing glitch in Windows 95
B. Using an amplification network to flood a victim with packets
C. Exploiting the three-way handshake used by TCP/IP
D. Sending oversized ping packets to a victim
16. Which of the following attacks sends packets with the victim’s IP address as both the source and the destination?
A. Land
B. Spamming
C. Teardrop
D. Stream
17. In what type of attack are packets sent to a victim using invalid resequencing numbers?
A. Stream
B. Spamming
C. Distributed denial of service
D. Teardrop
18. Spoofing is primarily used to perform what activity?
A. Send large amounts of data to a victim.
B. Cause a buffer overflow.
C. Hide the identity of an attacker through misdirection.
D. Steal user accounts and passwords.
19. Spamming attacks occur when numerous unsolicited messages are sent to a victim. Because enough data is sent to the victim to prevent legitimate activity, it is also known as what?
A. Sniffing
B. Denial of service
C. Brute-force attack
D. Buffer-overflow attack
20. What type of attack occurs when malicious users position themselves between a client and server and then interrupt the session and takes it over?
A. Man-in-the-middle
B. Spoofing
C. Hijack
D. Cracking
1. B. Accountability is maintained by monitoring the activities of subjects and objects as well as of core system functions that maintain the operating environment and the security mechanisms.
2. D. In most cases, when sufficient logging and auditing is enabled to monitor a system, so much data is collected that the important details get lost in the bulk. For automation and real-time analysis of events, an intrusion detection system (IDS) is required.
3. A. An IDS automates the inspection of audit logs and real-time system events to detect abnormal activity. IDSs are generally used to detect intrusion attempts, but they can also be employed to detect system failures or rate overall performance.
4. A, B, C. IDSs watch for violations of confidentiality, integrity, and availability. Attacks recognized by IDSs can come from external connections (such as the Internet or partner networks), viruses, malicious code, trusted internal subjects attempting to perform unauthorized activities, and unauthorized access attempts from trusted locations.
5. B. A host-based IDS watches for questionable activity on a single computer system. A network-based IDS watches for questionable activity being performed over the network medium, can be made invisible to users, and is ineffective on switched networks.
6. C. A knowledge-based IDS is effective only against known attack methods, which is its primary drawback.
7. D. A behavior-based IDS can be labeled an expert system or a pseudo-artificial intelligence system because it can learn and make assumptions about events. In other words, the IDS can act like a human expert by evaluating current events against known events.
8. B. Honeypots are individual computers, and honeynets are entire networks created to serve as a snare for intruders. They look and act like legitimate networks, but they are 100 percent fake. Honeypots and honeynets tempt intruders with unpatched and unprotected security vulnerabilities as well as attractive and tantalizing but faux data.
9. C. When intruders are detected by an IDS, they are transferred to a padded cell. The transfer of intruders into a padded cell is performed automatically, without informing the intruder that the change has occurred. The padded cell is unknown to the intruder before the attack, so it cannot serve as an enticement or entrapment. Padded cells are used to detain intruders, not to detect vulnerabilities.
10. C. Vulnerability scanners are used to test a system for known security vulnerabilities and weaknesses. They are not active detection tools for intrusion, they offer no form of enticement, and they do not configure system security. In addition to testing a system for security weaknesses, they produce evaluation reports and make recommendations.
11. B. Penetration testing should be performed only with the knowledge and consent of the management staff. Unapproved security testing could result in productivity loss or trigger emergency response teams. It could even cost you your job.
12. A. A brute-force attack is an attempt to discover passwords for user accounts by systematically attempting every possible combination of letters, numbers, and symbols.
13. C. Strong password policies, physical access control, and two-factor authentication all improve the protection against brute-force and dictionary password attacks. Requiring remote logons has no direct effect on password attack protection; in fact, it may offer sniffers more opportunities to grab password packets from the data stream.
14. D. Spoofing is the replacement of valid source and destination IP and port addresses with false ones. It is often used in DoS attacks but is not considered a DoS attack itself. Teardrop, smurf, and ping of death are all DoS attacks.
15. C. A SYN flood attack is waged by breaking the standard three-way handshake used by TCP/IP to initiate communication sessions. Exploiting a packet processing glitch in Windows 95 is a WinNuke attack. The use of an amplification network is a smurf attack. Oversized ping packets are used in a ping-of-death attack.
16. A. In a land attack, the attacker sends a victim numerous SYN packets that have been spoofed to use the same source and destination IP address and port number as the victim’s. The victim then thinks it sent a TCP/IP session-opening packet to itself.
17. D. In a teardrop attack, an attacker exploits a bug in operating systems. The bug exists in the routines used to reassemble (that is, resequence) fragmented packets. An attacker sends numerous specially formatted fragmented packets to the victim, which causes the system to freeze or crash.
18. C. Spoofing grants the attacker the ability to hide their identity through misdirection. It is therefore involved in most attacks.
19. B. A spamming attack is a type of denial-of-service attack. Spam is the term describing unwanted email, newsgroup, or discussion forum messages. It can be an advertisement from a well-meaning vendor or a flood of unrequested messages with viruses or Trojan horses attached.
20. C. In a hijack attack, which is an offshoot of a man-in-the-middle attack, a malicious user is positioned between a client and server and then interrupts the session and takes it over.
