Chapter 1. Security Threats
With the increase of hacking attacks, worms, viruses, and other networking threats, security is a major problem in today’s networks. 10 to 15 years ago, security was a simple problem requiring simple solutions; in those days, the Internet was small and had only a small number of universities and government agencies connected to it. Aging passwords were used to protect accounts, and simple packet-filtering firewalls were used to restrict traffic flows. However, today is a different world from more than a decade ago. With the explosion of the Internet, the proliferation of software applications, and the ingenuity of hackers, security has become a complex problem that requires a well-thought-out security solution to deal with it. The security solution must be capable of dealing with the security threats that your network will face, but it also must allow your company to reach its business goals and must be flexible enough to adapt to network topology and technology changes.
This chapter contains a brief overview of the kinds of threats that you will face in securing your network, as well as some generic solutions that you can use to deal with these threats. Understanding these topics will greatly help you choose and implement the correct Cisco security feature on your router. The main purpose of this book is to explain how to use a Cisco perimeter router as a complete firewall solution or as a component of a firewall solution. The end of the chapter explains the Cisco Security Model, which is used to implement security solutions.
Tip
Most hackers are intimate with UNIX operating systems; thus, most hacking, as well as security tools, is done in UNIX. Many tools are available for Windows platforms, but most of these are expensive commercial products. Therefore, if you are interested in becoming a security specialist, I highly recommend that you become familiar with the UNIX operating system, network administration with UNIX, and how to use many of the different security tools in a UNIX environment. At a minimum, most security job positions require this level of expertise. One of my favorite UNIX system administration books is Unix Systems Administration Handbook (3rd Edition), by Evi Nemeth, Garth Snyder, Scott Seebass, and Trent T. Hein (Prentice Hall PTR, August 2000). I used the first edition of this book to help me with my UNIX skills more than a decade ago; it is simple to read and easy to understand.
Planning for Security
Probably the most difficult task when dealing with security is the planning stage, in which you need to develop a solution to meet your company’s business and security needs. When examining your network and identifying critical and insecure areas and components, you need to approach a security plan from various perspectives:
• Business goals and user needs
• People and politics
• Technical issues
First, you have to remember that your company has business goals outlined in a business plan. These are used as a roadmap to increase your company’s success. A good security solution should help, not hinder, a company in reaching its business goals. The company’s users have needs that are related to the company’s business plan. Whereas the business plan is a general guideline, users have specific needs to reach the company’s business goals.
You must deal with all kinds of users from different departments and divisions when determining what assets and resources your company is using to reach its business goals. This means that you need to be intimate with the corporate organization ladder and have political savvy when dealing with various users and departments, as well as their diverse needs.
When you understand what resources either are being used by or are required by users to reach the company’s business goals, you need to determine what kind of security solution should be implemented that will protect your company yet allow it to achieve its goals. A solution that is completely secure yet prevents a company from reaching its goals is counterproductive and useless.
Diverse Platforms
Probably one of the most difficult things you face when designing a security solution is trying to find a one-size-fits-all solution—in other words, trying to find all your security products from one vendor with a management system that easily enables you to implement your security polices across all your security products.
For example, your security solution must encompass many types of hardware devices and software applications. Here is a small list of some of the types of devices that your security solution might have to deal with:
• PCs and laptops running Windows 95, 98, Me, 2000, XP, and 2003, as well as UNIX desktops and Macintoshes
• Servers running NT, 2000, 2003, NetWare, Linux, Solaris, HP-UX, and other operating systems
• Mainframes running Multiple Virtual Storage (MVS) and Virtual Machine (VM)
• Routers from Cisco, Juniper, Nortel, Lucent, and others
• Switches from Cisco, Foundry, Extreme, and others
This list is not all encompassing, by any means: Many more types of hardware devices, as well as dozens, if not hundreds, of software applications, play a role in your network.
Note
In many situations, you might have to buy security products from different vendors to implement a security solution that will meet your company’s policies and goals. In this situation, take care when determining a management solution that will be used to maintain your security implementation. I have found that the more products that you have from different vendors, especially as related to security, the more difficult it becomes to manage the solution.
Security Goals
A security solution can become complex quickly, especially in large enterprise networks. To help simplify the process, a good security solution should meet these goals:
• A single cohesive security policy should be created, based on your company’s business plan and goals.
• Security policies should dictate the choice of security solutions and products, not vice versa.
• Security management should be centralized under a single umbrella.
First, you should create a single, cohesive, company-wide security policy. This policy should be based on your company’s business plans and goals. It should be flexible enough to allow your company to meets its business objectives, while still protecting your company’s assets at a cost-effective price.
Second, the security products that you purchase should complement your security plan. You should never try to force a particular product into a role that it was not meant to be used in. Instead, develop a security solution with general components, and then find specific products that will meet the design guidelines for the included components.
Third, ongoing management and support of your products is critical, especially as they relate to detecting and dealing with security threats in a real-time manner. Some companies like to purchase all of their security products from one vendor, which makes management integration of the products easier: It is easier to deploy, manage, and support platforms from a single vendor than from multiple vendors. Of course, this approach might not be an option, based on the kinds and types of products that you need for your security solution.
If you need to purchase equipment and software from different vendors to develop a cohesive security solution, remember that you must manage these products after you implement them. Therefore, you should choose a security-management software product(s) that will ease the management and monitoring of your security devices. Choosing the right management solution will allow you to scale your security solution to a large size. It is also important to point out that even if you buy all of your security products from one vendor, that vendor might not have a single security-management platform to manage your security.
Tip
When developing a security solution, keep in mind that there is a total dollar cost for implementing any type of security measure, which includes equipment purchases, installation, training, management, and ongoing support. You need to carefully weigh the costs of a particular security measure with its benefits to determine whether the cost of the security measure outweighs the cost of the asset(s) being protected. There is no such thing as a completely secure network. Therefore, you need to examine your company’s business plan, the needs of your users, and your critical resources to find a solution that adequately will protect these items.
Causes of Security Problems
Literally thousands of elements can pose security threats to your company’s network, as well as to your company itself:
• Outside people and hackers
• The people who work for your company
• The applications that your users use to perform their business tasks
• The operating systems that run on your users’ desktops and your servers, as well as the equipment employed
• The network infrastructure used to move data across your network, including devices such as routers, switches, hubs, firewalls, gateways, and other devices
In a large network, these elements might include thousands of devices and hundreds of applications. When tackling security, at first a large number like this sounds daunting, if not impossible to tackle. However, if you use a divide-and-conquer approach, you can break up your network into areas and components, making the development of a solution easer.
To help simplify the security process, security problems are divided into three general categories:
• Weaknesses in policy definitions—These weaknesses include both business and security policy weaknesses. A simple example of this type of weakness is not having a written security policy. If you do not have a policy, how can you enforce it?
• Weaknesses in computer technologies—These weaknesses include security weaknesses in protocols, such as TCP/IP and IPX, as well as operating systems, such as UNIX, Novell NetWare, and Windows. An example of a computer technology weakness is the BackOrifice attack, which allows a hacker to remotely control a Windows-based system.
• Weaknesses in equipment configurations—These weaknesses include the setup, configuration, and management of your networking devices. An example of equipment configuration weakness is not assigning a password to a Windows 2000 server’s Administrator account or to a Cisco router’s console port.
The following sections cover these three weaknesses in more depth.
Policy Definitions
The first weakness relates to definitions of business and security policies. Many times I have walked into small and some medium-size companies to face this problem: lack of a written security policy or business policy, or, in the worst case, both. For a company to develop and meet business goals, it needs a well-written business plan that includes the company’s goals and policies. Likewise, to implement and maintain a good security solution that will help a company meet the objectives outlined in its business plan, you need to develop a well-written security policy. The security policy should be based on the company’s business plan. This ensures that the security plan follows the restrictions placed on how the company performs its day-to-day business, and that the security plan allows the company to meet its business objectives.
Policies: Business and Security
At a minimum, a well-written security policy should address the following questions:
• What should be protected?
• How you will protect it?
• How much protection should be used?
Even though these three questions are simple, in enterprise networks, the “what” and “it” mentioned can refer to 10,000 PCs, 400 servers, 2 minicomputers, 5 UNIX database servers, remote and Internet access, and many other items. However, as you are answering each of these three questions for important hardware and software components in your network, you should refer back to your company’s business policies and plans, to ensure that your proposed security solution will not hinder your company in meeting its business objectives.
As an example, a corporation might have 30 remote offices that connect to a corporate office. This corporation sells widgets as its primary business. The remote offices contain sales staff who access the corporate office’s database software to place orders and check the status of orders for their local customers. If you implemented a security solution that would protect the corporation’s database contents, you would need to ensure that the remote offices could access this information (in a secure manner). If you could not meet this business goal, your security solution actually would create a hindrance to the company’s business plan.
Note
I cannot begin to stress how important a security policy is. However, it is beyond the scope of this book to discuss all the components that are involved, as well as how to put one together. However, here is an excellent starting place that you can visit to learn more about security policies and see some sample policies: http://infosyssec.master.com/texis/master/search/+/Top/Computers/Security/Policy/.
People
One of the most difficult issues to face with the development of a cohesive security policy is people and their politics. This is especially true in large companies in which each division or department has its own agenda: Each has certain goals and has tunnel vision concerning what is and what is not important for the company as a whole. As long as each department meets its goals, it is happy. You will have to deal with many people who have different ideas about what is and is not important in the network.
Each of these people is different—and, be forewarned, you cannot treat them the same. It would be convenient if each was a computer running Windows 2000 Professional; each would react in an expected manner based on the questions that you ask. However, this is not a world filled with computers; it’s a world filled with people. You must consider this when you are interacting with them to learn about their issues and problems so that you can develop a cohesive security policy that meets not only their needs, but also the needs of the company as a whole.
Enforcement
Another weakness in policy definition is exposed when you have created all of these business and security policies but do not enforce them or follow through with them. In other words, having a security policy and then not implementing it completely (or at all), or not enforcing it, will not help you with your security problems; it actually creates security problems for you.
Here is a simpler example of policy enforcement. You might have written guidelines for choosing passwords for accounts in your security policy. To test your system, you might use a password-cracking program against your users’ accounts to make sure that they do not use their names, addresses, or other easy-to-guess passwords. If you are able to break a password, you might talk to the user, explain the guidelines in the security policy, and have that user change the password to something less easy to guess.
Change Management
A lack of a change-management policy also will cause security problems in your network. A change-management policy typically is used to ensure that when changes are made in your network, such as upgrading a file server or changing an access control list on a router (used for filtering traffic), you do not inadvertently affect services for employees or resources, or create a security problem.
Therefore, before any change is made to the network, you should document it and take it before a committee that usually comprises network administrators and employees from various departments. This committee can discuss the proposed change and determine its impact on the network. Based on this information, the committee might modify the change request or might specify that the change occur at 2:00 A.M., to minimize its impact.
Having a change-management system in place enables other people to examine the proposed changes for problems, especially those related to security, and to catch them before they become a problem. Too often I have seen situations in which people haphazardly change the configurations on their networking equipment, typically without documenting those changes. It becomes almost impossible in this type of environment to determine what security holes these unapproved changes have created.
Disaster Recovery
When you think of a disaster-recovery plan, thoughts of natural disasters such as tornados, floods, hurricanes, and fires come to mind first. A disaster-recovery plan is used to implement a backup solution when the absolute worst case occurs.
Disaster-recovery plans also should apply to security threats and attacks. For example, your company might be selling products through its e-commerce servers. Perhaps this is your company’s only line of revenue. What would happen if a hacker flooded your network with garbage traffic, possibly affecting the service that you are providing and maybe even crashing some or all of your web servers? What ramifications would occur if your e-commerce servers are hacked and it takes two or three days to bring them back online? Is your company prepared to deal with this? Do you have a plan of action that details what steps to take to deal with the problem?
A good disaster-recovery plan, in this instance, would have a redundant system in place at a different location that could be switched to easily in less than an hour, if not minutes. By placing the resources in a separate building, you are protecting yourself against natural disasters. Also, a good disaster-recovery plan lists, in detail, steps that should be taken to simplify the problem of cutting over to the new system. This reduces the likelihood of errors occurring during the cutover.
Tip
Before you actually cut over to your backup system, if your primary system was hacked, make sure that you know how it was hacked, and implement protection measures on the backup system before bringing it online. Otherwise, the hacking attack will be repeated and you will have run out of backup options.
Computer Technologies
The second security weakness relates to computer technologies. Weaknesses in computer technologies deal with the protocols and software that use these protocols. Computer technology weaknesses are divided into three general categories:
• Network protocols
• Operating systems
• Network equipment
The following sections discuss the weaknesses that these three categories face.
Network Protocol Weaknesses
Networking protocol weaknesses deal with the weaknesses in the networking protocols and applications that use these protocols. The most popular and most implemented networking protocol is TCP/IP. TCP/IP is actually a suite of protocols, including IP, TCP, UDP, ICMP, OSPF, IGRP, EIGRP, ARP, RARP, and others.
Some of these protocols have weaknesses that hackers exploit. A good example is TCP, which uses a three-way handshake process to set up a connection before transmitting data. During the three-way handshake, three exchanges occur between the source and destination, as shown in the top part of Figure 1-1. With TCP, the source sends a segment with the SYN flag set, indicating that it wants to establish a connection. The destination responds with a segment in which the SYN and ACK flags are set in the segment header, indicating that the connection can proceed. The source then acknowledges receipt of the destination’s segment by sending the ACK flag in a segment to the destination. When this process is complete, the source can begin transmitting data.
One weakness in TCP is that the destination expects the source to send a final ACK back to the destination, completing the setup of the connection. Hackers can exploit this weakness by flooding a service with TCP SYNs, without following through and completing the setup of these connections, as shown in bottom part of Figure 1-1. These connections sometimes are referred to as embryonic, or half-open, connections. The hacker’s goal is to tie up finite resources on the target server and thus disrupt valid connection attempts. For example, some lower-end Windows machines can handle only 128 half-open connections before they run out of resources, which then makes new connection attempts fail.
Many TCP/IP applications also have weaknesses. Probably the four most common ones that hackers like to attack are HTTP, SMTP, SNMP, and finger. On many occasions, hackers have used exploits to gain unauthorized access to a server or to crash it by focusing on TCP/IP application attacks.
Operating System Weaknesses
For users and servers to support applications, their respective devices run an operating system to control hardware functions. Each operating system that you have deployed is guaranteed to have one or more security holes in it. This is especially true of operating systems that are used widely because hackers have a tendency to target these in their attacks. A hacker’s thought process is that if he can find a security hole in an operating system such as Windows XP, he has just opened up hacking possibilities to tens of thousands of PCs. On the other hand, if a hacker spent time trying to find security weaknesses in DOS, he would be very hard pressed to find PCs connected to the Internet that still use this operating system.
When I refer to operating system weaknesses, I am talking specifically about operating systems that run on a server, PC, or laptop. These are some of the most popular operating systems that hackers focus on:
• Microsoft Windows 95, 98, NT, Me, 2000, XP, and 2003
• The many flavors of UNIX, including Linux
• Novell NetWare
One of the most targeted platforms is UNIX because the source code for many UNIX flavors, such as Linux and FreeBSD, is free. This makes it easier for a hacker to find security weaknesses and holes because the hacker can scrutinize the source code for possible problems. Because of Microsoft’s popularity as a desktop solution, hackers also focus on Microsoft’s many different operating systems. As an example, I use Microsoft Windows 2000 Professional for my personal and business use. On a semiweekly basis, I download security patches for this operating system, which gives you an idea of how busy hackers are in finding exploits of security holes in Windows.
Network Equipment Weaknesses
Network equipment weaknesses refer to security vulnerabilities in equipment such as routers, switches, firewalls, and others that also run an operating system. Typically, you are dealing with the security mechanisms that are built into this equipment, such as how passwords are implemented, how authentication is performed, and what security features they support and have been implemented. However, sometimes, based on a protocol, or an application that uses a protocol such as finger or SNMP, you must scrutinize your networking equipment, look at the default configurations, and make adjustments to provide for tighter security.
Tip
When security weaknesses are discovered in a protocol, an operating system, or a particular piece of networking equipment, the person who discovered the weakness should notify the Computer Emergency Response Team (CERT). CERT then verifies the vulnerability, notifies the vendor about the problem, and publishes the problem to make sure that everyone is aware of the security weakness so that they can obtain the appropriate patch from the vendor. You can view a list of the past and current security problems at http://www.cert.org. Other popular sites include http://www.infosyssec.com/ and http://www.securityfocus.com/.
Equipment Configurations
The third security weakness relates to equipment configuration problems. Weaknesses in equipment configurations are some of the hardest security problems to deal with because these weaknesses are a result of human error in the configuration or a misunderstanding about how the equipment should be configured. When I talk about networking equipment, I am talking about pretty much everything that you connect to your network, from a PC or file server to a router, switch, firewall, or other product.
You should be most concerned about controlling access to your network equipment. All user accounts should have secured passwords. This means that, for some equipment that uses default accounts, you either should change these passwords or should deactivate the accounts. You also should be concerned about the passwords that are assigned to these accounts:
• Do they have easily guessed passwords?
• How often are passwords changed?
• Do passwords travel across the network in clear text?
If you are concerned about authentication and authorization—what users access and what they are doing on a piece of network equipment—you might want to centralize authentication and authorization into a central security server. Chapter 5, “Authentication, Authorization, and Accounting,” discusses how this is done on Cisco IOS routers.
One of the most difficult tasks that you will face with an Internet connection and the configuration of network equipment is exposing the applications and services running on them to the entire world. Many of these applications, such as WWW and SMTP, are known to be sure targets of hackers because of hackers’ past successes in exploiting these common applications. Another example of applications that can give a hacker a way into your network is Java and ActiveX scripts that typically are embedded within web pages. One of your users might download and inadvertently run one of these scripts, giving a hacker access to your network.
To reduce the threats to your network, disable any unnecessary services on all of your networking devices. For instance, if you have a DNS server, you should disable FTP, SMTP, and other services. Likewise, on a web server, you should disable SMTP, FTP, and other services. If you have a Cisco router, you should disable all unnecessary services, such as finger and chargen. Many of these tasks are tedious work, especially if you have 300 routers and 300 servers running in your network. The work that you put into securing these services will make it that much harder for a hacker to gain a foothold into your network, however. Disabling services on a Cisco IOS router is discussed in Chapter 4, “Disabling Unnecessary Services.”
Caution
You should run only the applications that are absolutely necessary on a device. All unnecessary applications and services should be disabled, to minimize your threat exposure.
Types of Security Threats
Now that you have a basic understanding of the kinds of weaknesses that you have to deal with in a security solution, this section turns to some of the many security threats that your network faces. As I mentioned earlier, your network might face thousands of threats daily. The Computer Security Institute (CSI) conducted a study on network security threats and security breaches and discovered that, out of all of the companies polled, 70 percent have had some type of security breach. These security threats can be categorized as external versus internal, and unstructured versus structured.
External and Internal Threats
Security threats can come from two locations:
• External users
• Internal users
An external security threat occurs when someone outside your network creates a security threat to your network. If you are using an intrusion-detection system (IDS), which detects attacks as they occur, you probably will be mildly shocked at the number of probes and attacks that occur against your network daily.
An internal security threat occurs when someone from inside your network creates a security threat to your network. Interestingly, the CSI study has found that, of the 70 percent of the companies that had security breaches, 60 percent of these breaches come from internal sources. Some of these security breaches were malicious in intent; others were accidental. Therefore, you should not just be concerned about protecting the perimeter of your network, you should also aim to protect every key resource and service. This topic is discussed in more depth in Chapter 2, “Introduction to Firewalls.”
Caution
Most security threats are internal. Therefore, when you design a security solution, you must address this issue by using internal measures to protect important resources.
Unstructured and Structured Threats
General methods of security threats fall under two categories:
• Unstructured threats
• Structured threats
An unstructured security threat is one created by an inexperienced person who is trying to gain access to your network—a wannabe hacker. A good security solution easily should thwart this kind of attack. Many tools available to anyone on the Internet can be used to discover weaknesses in a company’s network. These include port-scanning tools, address-sweeping tools, and many others. Most of these kinds of probes are done more out of curiosity than with a malicious intent in mind. This is especially true of internal users who are interested in what kinds of devices exist in their own network.
A structured security threat, on the other hand, is implemented by a technically skilled person who is trying to gain access to your network. This hacker creates or uses some very sophisticated tools to break into your network or to disrupt the services running in your network. A good example of a structured attack is a distributed ICMP flood. A person with very little hacking skill probably would send a flood of pings from the same source machine, making it fairly easy to track down the culprit. A sophisticated hacker, on the other hand, will try to hide the source of the ICMP packets by changing the source address inside the packets (called spoofing), as well as executing the attack from several different sources. Tracking down the culprit of this kind of attack takes a lot of work and patience.
Figure 1-2 shows a simple example of a sophisticated spoofing attack. In this example, the hacker changes the source address in ICMP packets to those of Server C, which is the device that the hacker is attacking. He sends these packets to both Server A and Server B.
These servers respond to the ICMP messages to the destination listed as the source in the packets, Server C. In this example, with the hacker flooding packets to both Server A and Server B, which, in turn, hit Server C twice as hard, it becomes more difficult, from Server C’s perspective, to figure out who the real culprit of the attack is: the hacker.
Note
Even though you might be able to determine both the source (external versus internal) and the type of attack (structured versus unstructured), you should take each event seriously.
Categories of Threats
Now that you understand the basic components of a security threat, this section covers how security threats are categorized. When talking about a specific type of a security threat, it typically is categorized by using one of the following terms:
• Reconnaissance attacks
• Access attacks
• Denial of service (DoS) attacks
The following sections cover these three categories more thoroughly, including some specific attacks that fall under these categories and solutions that can be used to deal with these threats.
Reconnaissance Attacks
In a reconnaissance attack, a hacker tries to gain information about your network, including its topology, the devices that reside inside it, the software running on them, and the configuration that has been applied to these devices. The hacker then uses this information to execute further attacks, such as DoS or access attacks. Reconnaissance attacks come in different types, including the following:
• Scanning
• Eavesdropping
The following sections cover the basics of these types of reconnaissance attacks.
Scanning Attacks
The most common type of reconnaissance attack is a scanning attack. A network scanning attack occurs when a hacker probes the machines in your network. He might do this by sending an ICMP ping to every IP address in your network, or he might use a network ping, in which he pings the IP address of the directed broadcast of every network. As an example, if you have a network of 200.200.200.0/24, the hacker would ping 200.200.200.255. There are other ways to scan networking devices, but these two methods are the most popular.
Of course, a network scan tells the hacker only that there are machines in your network with a configured IP address; it does not tell what services are running on these machines. To find out what services are running on a machine, a hacker uses a port-scanning utility. A port-scanning utility probes the port numbers of a machine to detect whether a service is running. Using this approach, a hacker can determine whether the machine is running SMTP, Telnet, FTP, WWW, or other services. The hacker then can use this to plan further attacks against your device.
Tip
Many scanning tools are available—freeware, shareware, and commercial. One of my favorites, GFI’s LANguard Network Security Scanner, is a feature-rich network-scanner tool. It comes with a 30-day trial, after which certain features are disabled unless you purchase the full version. It can be downloaded from http://www.gfi.com/. I use this tool a lot when examining networks to see what services are running, which is helpful in determining whether devices are exposed. I also use a product called Nessus, available at http://www.nessus.org/, and Cisco Scanner (formerly known as NetSonar), available at http://www.cisco.com/univercd/cc/td/doc/pcat/nssq.htm.
The most common method of stopping networking and port-scanning attacks is to use filtering devices. This can be something as simple as using Cisco routers with access control lists or a sophisticated firewall. These concepts are discussed in much more depth in Chapter 2.
Of course, you always should play it safe and disable all services that are not necessary on all of your resources. For instance, if you have a web server, you should disable services such as Telnet, SMTP, finger, and FTP on it. You want to make it as hard as possible for any hacker to get even the smallest of footholds in your network. Performing these tasks on a Cisco router is discussed in Chapter 4.
Eavesdropping Attacks
Another form of reconnaissance attack is eavesdropping. Eavesdropping is the process of examining packets as they are in transit between a source and destination device. A hacker typically uses a protocol-analyzer tool to perform eavesdropping. Figure 1-3 shows how eavesdropping works. In step 1 of this example, the hacker is examining traffic between the user and the server. The hacker notices that the user is establishing a Telnet connection and authenticates with a username and password. Because Telnet passes this information in clear text, the hacker now knows how to log into the Telnet server, spoofing the identity of the user. In step 2, the hacker uses this information to log into the Telnet server.
The protocol analyzer used for eavesdropping, sometimes referred to as a packet sniffer, might be a sophisticated hardware-based protocol analyzer, such as the Network Associates Sniffer products, or it might be a software-based application running on a PC (Network Associates also sells a software-based Sniffer version). For software applications, the hacker needs a promiscuous network interface card (NIC); this is a NIC that processes all frames, not just frames with a destination MAC address that matches the one on the NIC. Many commercial, shareware, and freeware protocol-analyzer products are available.
To execute this attack, the hacker typically must be connected physically to the network somewhere between the source and the destination, and must see the actual packets. Another approach that a hacker more typically uses is to compromise a PC in the network and download a packet-sniffing program to it. When eavesdropping, the hacker looks for account names and passwords, such as these:
• Microsoft Windows login
• Novell Netware login
• Telnet login
• FTP login
• HTTP login
Hackers also use eavesdropping to examine other information, perhaps database or financial transactions.
To prevent eavesdropping, your best solution is to use some form of encryption on your packets. VPNs, which are discussed in Part VIII, “Virtual Private Networks,” allow you to use Data Encryption Standard (DES), 3DES, and AES encryption algorithms to protect your data. For terminal access, you should use a Secure Shell (SSH) program, which is an encrypted form of Telnet. For web access, you should use HTTP with Secure Socket Layer (HTTPS), which uses Secure Socket Layer (SSL) encryption.
You always should encrypt the following types of information:
• Passwords (and sometimes usernames)
• Personal information, such as telephone numbers, medical information, driver’s license numbers, and social security numbers
• Credit card information
• Financial transactions
• Company trade secrets and sensitive information
Two basic methods of implementing encryption exist:
• Link encryption—The entire frame (Ethernet, token ring, Frame Relay, HDLC, and so on) is encrypted. This method of encryption can be used only on point-to-point connections in which both sides are configured for encryption.
• Packet encryption—Only the packet contents, such as the TCP or UDP segments in an IP packet (the payload), are encrypted; the addressing information (IP addresses in the IP header) is not. This method of encryption is used on connections that traverse multiple hops, such as internal networks, public networks, and the Internet.
Note
Because encryption is very process intensive, it typically is used for external connections; in other words, it typically is not used inside your network. For internal security, you might want to include in your security policy a statement that prohibits eavesdropping, with severe penalties applied. However, for sensitive information, encryption should be used to protect it. Obviously, certain network administrators should be allowed to perform eavesdropping in certain situations, such as troubleshooting connectivity issues. Any other type of eavesdropping by anybody else (other employees), however, should not be tolerated and should be dealt with immediately.
Another solution is to employ a switched infrastructure, giving every device its own switch port connection. Using this design, even if a hacker has compromised one of the PCs in your network and loads a packet-sniffing tool onto the PC, the hacker will be able to see only traffic directed at the compromised PC or multicast or broadcast traffic. However, one concern to consider is the security of the switches themselves. If the hacker can compromise both a PC and the switch connected to the PC, the hacker can set up port mirroring, to have the switch mirror traffic from other ports to the port of the compromised PC. Cisco calls this mirroring process SPAN, short for switched port analyzer.
Access Attacks
Another common type of attack is an access attack. In an access attack, a hacker attempts to gain unauthorized or illegal access to your network and its resources, particularly resources such as file, e-mail, and web servers. He typically does this by trying to access password files, using password-cracking programs, or examining traffic on your network for packets that contain clear-text passwords (eavesdropping attack). Other types of attacks include exploiting weaknesses in operating systems and applications, such as buffer overflows, that can allow a hacker access without first authenticating.
After a hacker has broken into one of your networking devices, he usually tries to raise his privilege level to the highest possible degree and then uses this account to break into other networking devices. He also might modify files on your resources or, in the worst possible scenario, erase everything on the disk drive and laugh as he tells his story to his friends. The following sections cover the basics of these types of access attacks.
Unauthorized Access Attack
In the most basic form of an access attack, a hacker tries to gain illegal access to equipment in your network. This is called an unauthorized access attack. To accomplish this kind of attack, a hacker can use many tools, including the following:
• Guessing passwords for well-known accounts, such as root and Administrator
• Using a protocol analyzer and executing an eavesdropping attack to examine clear-text passwords in packets
• Accessing a password file and using a password-cracking program on it
• Using social engineering
The last item, social engineering, is probably the hacker’s easiest method of gaining unauthorized access to resources in your network. With social engineering, a hacker calls various users in your network, pretending to be a network administrator. The hacker tells the user about some fictional network security problem and, using guile and ingenuity, gathers information from the user that the hacker then can use to access resources on your network. This can go the other way, too; the hacker can pretend to be a user and can call a network administrator, acting as if he has forgotten his password.
The solution that you implement to restrict unauthorized access attacks depends on the method the hacker is using to gain unauthorized access. For instance, if the hacker is trying to gain illegal access to your network through your network’s remote access (dialup) server, you probably would want to implement the following solutions:
• Use the Challenge Handshake Authentication Protocol (CHAP) with PPP (Point-to-Point Protocol), where the password is not sent across the wire, is tied to a specific user, and is verified by a security server
• Use double authentication. Cisco IOS routers have two features: Lock-and-key access control lists (ACLs) and authentication proxy. Lock-and-key works hand-in-hand with PPP’s CHAP. The user is authenticated first through CHAP and then through lock-and-key. However, lock-and-key also works over nondialup links. Lock-and-key is discussed in Chapter 13, “Lock-and-Key Access Lists.” Authentication proxy (AP) is the preferred method of authenticating users and is discussed in Chapter 14, “Authentication Proxy.” It also has the capability to authenticate users before allowing them access to network resources. As you will see in Chapter 14, Cisco recommends using AP over lock-and-key because it is more flexible, supporting Telnet, FTP, HTTP, and HTTPS for authentication.
For application security, if your applications support additional security mechanisms, you definitely should implement them. For some applications, you might consider replacing them. For instance, the standard Telnet application uses clear-text passwords when performing authentication. You might want to consider replacing your standard Telnet application with a secure one that encrypts the password before sending it across the network, such as SSH. You also should disable all unnecessary services and consider using a host-based firewall. Host-based firewalls are discussed in more depth in Chapter 2.
One of the biggest problems that you will face is the management of your security solution. A much better and more manageable solution than the one discussed in the previous sidebar is to use a centralized security server; Cisco has one called Cisco Secure ACS. You configure all of your user accounts and security policies on this server, and you have your routers and other networking devices use this security server to perform authentication functions. By centralizing the authentication process, you have more control over who is accessing your devices and what they are doing on them, making it easier to determine whether unauthorized access attacks are occurring. Centralizing authentication functions is discussed in Chapter 5.
One often-neglected prevention method, but one that is easy to implement, is user training. By training users not to write their passwords on their desk, to use passwords that do not have common words and that have a mixture of letters and numbers, and to be careful about what they say to people over the telephone or in person, you make your security job easier.
Data-Manipulation Attack
Data manipulation is simply the process of a hacker changing information. These changes could be something as simple as modifying file contents on a file server or something as sophisticated as changing packet contents as they are in transit from a source to a destination machine.
A common attack that hackers employ is to break into your web server and change the content (web pages). This form of attack is called graffiti. This type of attack has happened to many organizations, typically government resources; a hacker breaks into a web server and replaces the web content with pornography or “interesting” political content. To execute this kind of attack, a hacker typically first performs a reconnaissance attack, such as eavesdropping, to discover user accounts and passwords, and then executes an unauthorized access attack. A more ingenious hacker might use Java or ActiveX scripts either to learn information about a client’s device or to break into it. Likewise, a hacker might try to take advantage of known vulnerabilities in a web server application or operating system.
The best method of preventing data-manipulation attacks is to implement a centralized and robust authentication and authorization system, such as Cisco Secure ACS, which is discussed briefly in the previous section. With this solution, you can restrict what users can access, restrict what they can do on the service that they access, and record the event for security purposes.
For file servers, tools are available to take a snapshot of your files, and the snapshot then is stored in a secured location. You periodically should compare the critical files on your server to the snapshot that you took previously. If there is a difference between the two, you might be a victim of a data-manipulation attack. One of the most common security tools that performs this function is Tripwire, which can be accessed from http://www.tripwire.com/.
To prevent Java and ActiveX attacks on your users, and possibly your web servers, you should use a filtering solution that can filter Java and ActiveX scripts that are embedded in HTML pages. Many solutions are available, including the use of Cisco IOS routers and the PIX firewall. If you are concerned about the actual content that users access or what Internet sites that they can view, you might want to put in place a web filtering solution, such as WebSense or N2H2. Many sites have inappropriate material for business purposes, as well as hacking and cracking tools. Cisco IOS routers and the PIX firewall can work hand in hand with WebSense and N2H2. Both of these products enable you to enter policy information about what URLs a user can or cannot access. When the Cisco IOS router or PIX sees a web access request from a user, it first verifies it with the policy server before permitting it. Filtering of Java and ActiveX scripts, as well as URL filtering, is discussed in Chapter 10, “Filtering Web and Application Traffic.”
To prevent a hacker from using known vulnerabilities to access your system, you should make sure that your applications and operating systems have the latest security patches applied. Microsoft Windows products simplify this process with the Windows Update tool, which automates the process.
Session Attacks
One of the most difficult attacks that a hacker can carry out is a session layer attack. In a session attack, a hacker attacks a session layer connection, hoping either to use this information to mount another attack, or, through subterfuge, to take over the session in which he pretends to be either the source or the destination device. Four general categories of session attacks exist:
• Masquerading
• Session replay
• Session hijacking
• Repudiation
The following sections cover these session attacks in more depth.
Masquerading Attack
Masquerading is an attack method that a hacker uses to hide his identity. He pretends to be a different machine by changing his source address in his IP packets. An example of this attack is discussed earlier in the chapter in the “Unstructured and Structured Threats” section and in Figure 1-2.
In TCP/IP, this form of an attack is called IP spoofing. To carry out an IP spoofing attack, a hacker typically uses a software program that changes the source address of packets (and even the TCP sequence numbers for TCP segments). Many programs are available on the Internet to perform this process, including Hping (http://www.hping.org/) and Nemesis (http://www.packetfactory.net/Projects/nemesis/), as well as others. In some instances, the hacker can do this at the operating system level in certain versions of Linux.
A hacker typically implements a reconnaissance attack that involves the use of a port scanner to discover open ports, and possibly even an eavesdropping attack, using a protocol analyzer, to see the actual traffic flow, including usernames and passwords. Sophisticated hackers use a source IP address that resides inside your network to execute a masquerading attack. They combine this with a routing attack so that the packets sent to a destination are returned not to the source inside your network, but to the hacker himself. This requires excellent technology skills on the hacker’s part.
Note
Most DoS attacks use IP spoofing, which makes tracking down the hacker difficult. I discuss this issue in more depth in Chapter 17, “DoS Protection.”
Session-Replay Attacks
When a hacker executes a session-replay attack, he captures (actually, eavesdrops on) packets from a real session data transfer between two devices with a protocol analyzer. Then he uses this information to execute an attack on the source device, the destination, or both, at a later time. Sometimes a hacker downloads Java or ActiveX scripts to clients that capture web transactions—possibly even online order information such as credit card numbers—and then uses this for his own purposes. Another favorite method of hackers is to use cookies to masquerade as a site, and then to get the client device to believe that the hacker’s computer is the real web destination.
Session-Hijacking Attacks
In a session-hijacking attack, a hacker attempts to take over an existing session between two computers. As an example, the hacker might cut the source device out of the picture and pretend to be the source, tricking the destination device into believing that the destination still is communicating with the original source. A sophisticated hacker even might be able to insert himself into the middle of the session, pretending to be the source to the real destination, and pretending to be the destination to the real source device.
A session-hijacking attack typically involves a handful of other attacks, such as masquerading, eavesdropping, and data manipulation. You might think that executing this type of attack would be very complicated; however, some protocols, such as TCP, are fairly predictable, especially in their use of sequence numbers for TCP segments. With a good hacking software program, a skilled hacker can insert himself into the middle of an existing connection. The top part of Figure 1-4 shows what a session looks like from the perspective of the source and destination that have been hijacked. The bottom of Figure 1-4 shows the actual data path of a hijacked session.
One of the easiest attacks that hackers like to employ involves masquerading and session hijacking. Almost all TCP/IP services use the Domain Name System (DNS) to resolve names to IP addresses. A skilled hacker can intercept DNS replies from servers and replace the IP addresses for the requested names with addresses of machines that the hacker controls, thus providing an easy method for ongoing session attacks.
Repudiation Attacks
Repudiation is a process in which you cannot prove that a transaction took place between two entities. The goal of the hacker is to perform repudiation when executing session layer attacks. Nonrepudiation, on the other hand, is having absolute proof of the identities of the parties in a transaction that has taken place. As an example, certain types of transactions need a nonrepudiation process. For instance, signing electronic documents, transferring money electronically, and buying a product online with your credit card all must have a nonrepudiation process, or else they cannot be legally binding.
Hackers typically use a repudiation attack when users are accessing web information. Hackers like to use Java or ActiveX scripts, port-scanning utilities, masquerading, and eavesdropping to carry out their repudiation attack. Perhaps one of the simplest forms of repudiation attacks is to use public e-mail systems such as hotmail.com, yahoo.com, and others to generate garbage mail and execute a DoS attack against a company’s e-mail server. Getting a free e-mail account from these systems is usually a simple process, with little identity proof required. This makes it easy for a hacker to get an e-mail account and hide his activities behind a cloud of anonymity.
Two common issues with e-mail are spamming and e-mail bombs. Spamming is the process by which you receive unsolicited e-mail. This is perhaps one of the biggest complaints of anyone who has an Internet e-mail account; I am constantly getting spam e-mails. Another security problem is an e-mail bomb, an e-mail that contains code that is executed either automatically upon receipt or when a user clicks something, like a hyperlink or an attachment. The most common form of an e-mail bomb is a virus or worm. My Internet provider constantly scans for these types of e-mails, as does the antivirus software that I run on my PC.
Preventing Session Attacks
You can use many solutions to prevent session layer attacks against your user and service connections:
• Using VPNs
• Using SSL for web browser connections
• Authenticating with digital signatures
• Filtering Java and ActiveX scripts
• Blocking e-mail from public e-mail sites
Probably the most important is using a Virtual Private Network (VPN) to encrypt information going across the connection. With a VPN, a hacker cannot see the actual data that is being transferred between the source and destination devices. Part VIII covers an overview of VPNs using IPSec and discusses how to configure IPSec connections on a Cisco IOS router. Secure Sockets Layer (SSL) provides security in web transactions. The main difference between IPSec and SSL is that IPSec can protect any type of IP traffic, whereas SSL can protect only web application traffic.
Another popular method used for providing identity verification is to use digital signatures. A digital signature is similar to a written signature, a person’s thumbprint, a retinal scan of a person’s eye, or a DNA profile of a person. In other words, it is used to uniquely identify the user. In the online world, a special third-party device called a Certificate Authority (CA) is used to handle the repository of identities. A CA performs a similar function to what a notary does in real life: It handles and validates identities of individuals. For instance, if you wanted to set up a connection to a remote site, but you wanted some kind of proof of the remote site’s identity, your networking device could get the digital signature of the remote site from the CA and then request the remote site’s own digital signature. Your networking device then would compare the two signatures. If they matched, you would know that you were dealing with the correct device; if they did not match, you would know that a session attack is occurring.
Another tool that you should consider using is a router or firewall that can filter Java and ActiveX scripts from untrusted sites. By filtering these scripts and applets, you are reducing the likelihood of a hacker performing a session layer attack. To make your life easier, your networking devices always should have logging enabled, and they should transfer this logging information to a central repository where you can keep an audit trail of important connections and transaction.
Caution
Be very careful if you decide to filter Java and ActiveX. Many, if not most, web sites take advantage of this technology to provide enhanced web features. Therefore, I recommend filtering these scripts only from networks in which known security threats exist.
To prevent spamming and e-mail bombs, as well as to reduce the likelihood of a hacker using a public e-mail site to execute a repudiation attack, you should block all e-mail access from public e-mail sites. This might mean that some legitimate people might not be able to send you e-mail any longer, but, on the other hand, you are greatly reducing the likelihood of exposure to reconnaissance, DoS, and repudiation attacks against your e-mail system. Many commercial products on the market help deal with spamming. The next section discusses some other solutions to e-mail bombs.
Tip
I use a program called MailWasher that scans my e-mail before downloading it. It is excellent for detecting spam messages and bouncing these back to the sender. Information about this excellent freeware product can be found at http://www.mailwasher.net/. However, this tool is for end-user use only; you also should have a good server tool to detect and remove SPAM.
Virus, Trojan Horse, and Worm Attacks
Viruses, worms, and Trojan horses are probably the most well-known attacks on computer systems because these are the most publicized, as well as the most likely to affect the general user public. Many different views actually exist regarding the definition of these three types of attacks. Generally, a virus is a program or a piece of code that is loaded onto and run on your computer without your knowledge. Many viruses also replicate themselves to spread their damage. Unlike bugs, viruses are manmade. A worm is a program that replicates itself over a network with some malicious intent in mind, such as crashing a system or using up all the resources on the system. Many people view viruses and worms as the same type of attack. A Trojan horse is a program loaded onto your computer that acts as a benign application, waiting for the user to activate it through normal computer and application activity. Unlike viruses and worms, Trojan horses do not replicate themselves. Sometimes Trojan horses pretend to be your antivirus software or replace it, hoping to add instead of remove viruses from your system.
These kinds of attacks might be something as simple as an e-mail attachment that you click or something as sophisticated as a software program that is executed because of a security problem with your e-mail program.
Typically, most of these attacks are exploited through the e-mail system, although there are other methods, such as executing an infected program. When executed as a reconnaissance attack, these attacks can send your e-mail’s address book or your password file back to the hacker. When executed as a DoS attack, these attacks can affect the CPU cycles, memory, disk space, or bandwidth of a networking device, such as a PC.
You can employ three different methods in combating these kinds of attacks:
• User training
• Antivirus software
• Application-verification software
One of the best defenses is to train your user population. For instance, you should warn your users never to open e-mails or attachments from individuals whom they do not know. Any suspicious e-mail should be reported immediately to a network administrator.
Of course, one of the most popular methods of dealing with these kinds of attacks is to deploy antivirus software. Many packages are available on the market, with the most popular being antivirus software packages from Network Associates and Norton (I use Norton on my PC). When deploying these in an enterprise network, you need to make absolutely sure that all of your desktops and servers have the most recent data files that contain the list of known viruses. You definitely will want to explore some type of automation process, in which a client’s software is updated periodically (all commercial antivirus packages that I have dealt with support automatic updates of virus information on clients and servers).
Another typical solution for file servers is to use application verification software. This type of software takes a snapshot of existing files and keeps it in a secure place (usually on a separate, secure device). You typically include files such as executables, batch scripts, and configuration files in this snapshot. You then run a periodic analysis with the application-verification software, comparing the current files on the server with the secured ones. If there is a difference, the application alerts you to this. A difference might indicate that an access attack has taken place, possibly with a worm or Trojan horse attack, and that one of your files has been replaced with a hacker’s file.
Note
To see an encyclopedia of viruses, worms, and Trojan horses, visit Symantec’s site at http://securityresponse.symantec.com/avcenter/vinfodb.html.
Denial of Service Attacks
Besides reconnaissance attacks, the second most common form of security threat and attack is the DoS attack. With a DoS attack, a hacker attempts to deny legitimate traffic and user access to a particular resource, or, at the very least, reduce the quality of service for a resource. Many kinds of DoS attacks exist; the simplest to implement is a flood attack, in which the hacker overwhelms a device or network with a flood of ICMP packets. The next two sections cover some common DoS attacks, as well as methods used to prevent these kinds of attacks.
Types of DoS Attacks
Hackers can use many types of DoS attacks against your network. Some of these affect the performance of a particular service running on a server, and some drastically can affect the performance of all the machines on a particular network segment. Because there are literally hundreds of DoS attacks, the following list is limited to some of the most common ones:
• An application attack is simply an attack against an application running on a server. Hackers typically attack such popular applications as Microsoft’s IIS web server, web browsers such as Microsoft Internet Explorer and Netscape Navigator, and e-mail applications such as Sendmail and Microsoft Exchange and Outlook because of their widespread use. Hackers try various methods, such as buffer overruns and e-mail bombs, to disable a system or to send information back to the hacker to be used for other types of attacks.
• An e-mail bomb is a form of an attack that a hacker uses to tie up e-mail resources on your system or possibly even compromise the security of your e-mail server. An unsophisticated hacker typically sends large messages to your e-mail server, hoping to fill up the disk space and crash it. A sophisticated hacker, on the other hand, includes Trojan horses, viruses, or worms that either are embedded in the e-mail or are included as an attachment. If a user activates these, they can cause damage to your system or open a security hole that will allow a hacker into the networking device.
• CPU hogging is a type of attack that affects the CPU cycles of a service. This is a general category of a DoS attack in which more specific attacks, such as packet fragmentation or chargen, are used.
• Chargen is a character generator that produces serialized character output. Typically, chargen uses UDP, but it can be implemented with TCP. Chargen runs on port 19 and usually is enabled on most operating systems. Hackers sometimes send garbage data to this port, hoping that your resource will process this information and thus take away CPU cycles from other legitimate processes on the resource.
• A packet fragmentation and reassembly attack is an ingenious attack in which a hacker sends hundreds of fragments to a destination service, hoping that the destination device will perceive these as valid connections and thus waste both buffer space and CPU cycles to process them. A good hacker makes this flood of fragments appear as a set of legitimate connections, which can cause a buffer overrun on the destination and possibly crash the machine. Even if the machine does not crash, the hacker is tying up buffer space, which prevents legitimate traffic from being processed.
• Land.c is a program that sends TCP segments to a destination where both the source address and destination are the same in the packet. Upon receiving the packet, the destination tries to forward the packet to itself. To make it even more confusing for the destination device, the packet might contain the same port number for both the source and the destination. In some instances, this can cause the device to try repeatedly to establish connections to itself, tying up resources.
• Hackers sometimes use Java or ActiveX scripts to create malicious applets. When downloaded to user’s desktop, these applets sometimes can damage the user’s file system or send information back to the hacker that he then can use to attempt further attacks.
• A ping of death attack is one of my favorite attacks because of its simplistic beauty. A hacker sends a single ICMP message with an offset field indicating that the data is larger than 65,535 bytes. On some systems, this crashes the device. When this bug was discovered, for a period of two or three days, many companies were disconnecting their connection to the Internet to prevent hackers and curious people from bringing down their resources.
• One of the most difficult attacks to implement is an attack on your router’s routing protocols, called a rerouting attack. In this type of attack, a hacker tries to feed your routers with either bad routing information that will cause your packets to be routed to a dead end, or misinformation that will cause your packets to be routed back to the hacker so that he can perform eavesdropping and use this information to execute another attack. Typically, a hacker uses a protocol analyzer and special software to implement this type of attack.
• TCP SYN flood attacks occur when a hacker floods a particular service with TCP SYN segments without any intent of completing the connection. With this kind of attack, the hacker basically is tying up the connection resources on a particular server.
• Smurf attacks occur when a hacker sends ICMP traffic to a destination (a directed broadcast address) but replaces its own source IP address in the packet header with the IP address of the device that it wants to attack. When the ICMP traffic reaches the destination network, the devices respond to the spoofed source address, which is the device that the hacker wants to flood.
• WinNuke is a program that was developed to take advantage of a bug in certain versions of Microsoft operating systems, including 95, 98, Me, XP, NT, and 2000. The hacker sends out-of-band information to port 139, hoping to bring down the server.
An enhanced form of DoS attacks are Distributed DoS (DDoS) attacks. With a DDoS attack, a hacker subverts or controls multiple sources and uses these sources to attack one or more destinations. Tracing the culprit in these kinds of attacks can be difficult, especially if the hacker is using many different ISPs as the source of the attack. For more information on common DDoS attacks and tools, visit Dave Dittrich’s site at http://staff.washington.edu/dittrich/misc/ddos/.
DoS Attack-Prevention Methods
Just as hackers use many DoS attacks to hamper your network’s performance, you can use many solutions to prevent or at least hinder a hacker’s DoS attack. The following are common solutions used to detect and prevent DoS attacks:
• Performing packet filtering
• Using an intrusion-detection system (IDS)
• Using routing protocols with authentication
• Running detailed audits and logs
The first solution that you should implement is filtering. You can use something as simple as ACLs on a Cisco router, or you can use a firewall system such as the PIX or the Cisco IOS Firewall feature set available on Cisco routers. The Cisco IOS Firewall feature set supports a feature called Context-based Access Control (CBAC), which implements a firewall system on a router. To protect yourself from malicious applets, you should use a firewall system, such as the Cisco IOS router or PIX, to filter Java and ActiveX scripts and applets. CBAC is discussed in Chapter 9, “Context-Based Access Control.”
You also should consider using an IDS. An IDS solution examines traffic and, based on its contents, classifies the traffic as either an attack or not an attack. One large advantage of using an IDS is that these can detect reconnaissance attacks and probes, alerting you to the fact that possible hacking problems are looming. More sophisticated IDS solutions even can interact with your network equipment, such as routers and firewalls, and automatically configure them to filter the offending traffic when it is detected. Cisco has a range of IDS solutions, which enable you to implement a feature called IP blocking or shunning. With IP blocking, when a Cisco IDS detects an attack, it can log into a Cisco PIX or router and add a temporary filtering rule to block the attack. IDS and IP blocking are discussed in Chapter 16, “Intrusion-Detection System.”
To prevent routing attacks, you can use a routing protocol that has built-in authentication, such as RIPv2, EIGRP, OSPF, IS-IS, or BGP. These use the MD5 hashing algorithm, which creates a unique digital signature that is added to all routing information. The MD5 hashing algorithm, which also is used by PPP’s CHAP and by IPSec’s AH and ESP, is discussed in Chapter 19, “IPSec Site-to-Site Connections.” You also might want to configure filters to allow routing update traffic from only certain routing sources; however, if the hacker is smart about this process, he typically changes the source address to match an address that is specified in your allowed list. If your router is located at the perimeter of your network, you might want to consider using static routes instead of using a dynamic routing protocol. Routing protocol protection is discussed in Chapter 15, “Routing Protocol Protection.”
At the very least, your networking equipment should keep extensive audits and logs to keep track of security issues. You should peruse these periodically, looking for DoS attacks. Or, if you are smart, you will use a system that parses the logs and does all of this work for you. Logging is discussed in Chapter 18, “Logging Events.”
Security Solutions
It is beyond the scope of this book to cover every type of security solution that is available on the market. This section covers some basic solutions that you should be aware of, as well as a security checklist to help strengthen your company’s network security. The rest of this book focuses on the Cisco IOS routers for firewalls in implementing security in your network.
Designing a Security Solution
As you have seen throughout this chapter, a hacker can cause damage to your network in many ways (and this chapter barely skims the surface on the different kinds of attacks that your network will face). Therefore, you need to design a solid security solution to deal with these threats. This solution also should be easy to maintain and should be flexible enough to handle changes in your network. Here is a simple checklist that should describe your security solution:
• It should be easy to use and implement—It also should be easy to monitor and maintain. If a security solution is complex, with a lot of configuration tasks to perform and management systems to monitor, you might be making your security worse. Misconfigurations easily can create security holes, and if you have too many management platforms to monitor, the administrators might miss key events or might become lax in their monitoring duties.
• It should enable your company to develop and deploy new applications in your network—In other words, you should not have to change your security system completely to accommodate new applications. Remember that your security solution should meet the outline created in your security policy, and your security policy should allow your company to meet the goals that were developed in its business plan.
• It should enable your company to use the Internet in a secure manner—The company should feel secure that its key resources are protected and that the Internet can be used to further the company’s business goals.
Note
Chapter 2 goes into more depth on developing a security solution, particularly the roles that firewalls play in protecting your network and different design philosophies in the use of firewalls.
The Cisco Security Wheel
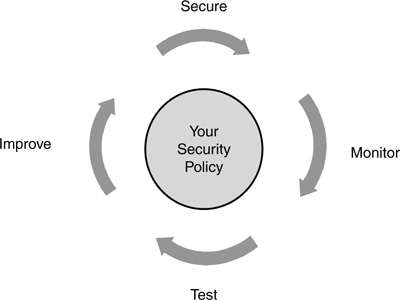
As you quickly will learn, network security is not a one-time implementation. You do not implement your security solution and walk away from it. Instead, network security is a continuous process that is built around your company’s security policy. Cisco developed a concept called the security wheel that outlines a four-step process that is repeated continuously. Here are the four steps in the security wheel, shown in Figure 1-5:
1. Secure your network.
2. Monitor your network’s security.
3. Test your network’s security.
4. Improve your network’s security, based on your monitoring and testing results in Steps 2 and 3.
The next four sections cover these four steps in more depth.
Secure Your Network
In the first step, you should do what is necessary to secure your network. This includes many of the prevention methods that I mentioned in this chapter, but it also includes physical security (locking up key components and removing the likelihood that users or strangers physically can get their hands on key resources in your network). Some of the solutions that you might consider implementing are authenticating through the use of one-time passwords, smart cards, and authentication servers; using firewalls to filter traffic; using VPNs to encrypt your traffic; and keeping up-to-date on security holes in your equipment and ensuring that they have the latest security patches applied. Chapter 2 goes into the design philosophy in a lot more depth.
Monitor Your Security
When you have put your security solution in place, your next step is to monitor your network to ensure that no security breaches take place. One very common tool that many companies use is an IDS. These devices enable you to monitor traffic and look for attacks, alerting you through a management station, e-mail, or a pager for a quick response. A security solution is no good if you do not monitor it.
Test Your Security
As the previous sidebar example points out, it is also important to follow the third step: Test your security periodically. The company in my example should have been at least attempting certain kinds of tests on the ISP’s security periodically, not just to verify that its assets are protected, but also to ensure that the money that it is paying the ISP is being well spent. These tests should include reconnaissance attacks (network scanning and port probing), as well as checks on the security logs of networking devices.
Improve Your Security
The last step is to examine the results of your monitoring and testing events, and use this information either to make changes to your security system or to improve upon your security system. Likewise, you should use this information to make adjustments to your security policy.
After you have completed these four steps, your job is not over yet. Instead, you should go back to Step 1 and start over. You will repeat this process continually, adjusting your security policy and security solution to meet all existing and newly developing security threats.
Security Checklist
Internet Security Systems (ISS) has developed a similar concept to the Cisco security wheel. I have summarized it in the following security checklist:
![]() Create a well-defined security policy that is complementary to your company’s business objectives.
Create a well-defined security policy that is complementary to your company’s business objectives.
![]() Create an easy-to-read security handbook that will be distributed to all of your employees, to help educate and train them in your company’s security policies and procedures.
Create an easy-to-read security handbook that will be distributed to all of your employees, to help educate and train them in your company’s security policies and procedures.
![]() Adequately protect your mission-critical resources and services.
Adequately protect your mission-critical resources and services.
![]() Develop a security plan of action that lays out what actions and responses your company will take if a security breach or problem occurs.
Develop a security plan of action that lays out what actions and responses your company will take if a security breach or problem occurs.
![]() Develop a disaster-recovery plan that deals with the worst-case situations for security breaches, such as if a hacker reformats the hard drives on all of your web servers, or if an arsonist torches your company’s headquarters.
Develop a disaster-recovery plan that deals with the worst-case situations for security breaches, such as if a hacker reformats the hard drives on all of your web servers, or if an arsonist torches your company’s headquarters.
![]() Purchase damage insurance for the software and hardware that you own, in case an individual intentionally physically damages your company’s computer and networking assets. You might even want to include insurance for lost data and downtime requirements to restore your system to its previous state.
Purchase damage insurance for the software and hardware that you own, in case an individual intentionally physically damages your company’s computer and networking assets. You might even want to include insurance for lost data and downtime requirements to restore your system to its previous state.
![]() Train your networking employees so that they can implement and monitor your proposed security solution.
Train your networking employees so that they can implement and monitor your proposed security solution.
![]() Use an IDS to detect security attacks.
Use an IDS to detect security attacks.
![]() Use a firewall system to filter all unnecessary traffic as it comes into your network.
Use a firewall system to filter all unnecessary traffic as it comes into your network.
![]() Use a VPN solution to protect data between sites and devices in a remote access network.
Use a VPN solution to protect data between sites and devices in a remote access network.
![]() Implement a corporate-wide antivirus solution that incorporates your PCs, laptops, and file servers.
Implement a corporate-wide antivirus solution that incorporates your PCs, laptops, and file servers.
![]() Disable all unnecessary services on your devices.
Disable all unnecessary services on your devices.
This is not meant to be a comprehensive checklist, but it contains some of the basic things that you should be doing and implementing in your network. More information about ISS and their products can be found at http://www.internetsecuritysystems.com/.
Additional Information
If you are a novice to security, you will soon find that you have a lot to learn about security, threats, and solutions. To help you with this process, I have included some links to additional information that you will find useful:
• For an overview of security, visit http://www.cisco.com/univercd/cc/td/doc/cisintwk/ito_doc/security.htm.
• For information about CERT and published security threats, visit http://www.cert.org.
• For information concerning the security life cycle and checklist, visit this ISS document at http://documents.iss.net/whitepapers/securityCycle.pdf.
• For an overview of Cisco security products, visit either of these two URLs:
— http://www.cisco.com/univercd/cc/td/doc/product/vpn/ciscosec/index.htm
— http://www.cisco.com/en/US/netsol/index.html
• For an overview of Cisco security features, visit http://www.cisco.com/univercd/cc/td/doc/product/iaabu/newsecf/index.htm.
• Other important security sites that I commonly use include these:
— http://www.securityfocus.com/
Summary
This chapter discussed some of the basics of security. Planning for security can be a complex process, but having a security policy simplifies it. A security policy is one of the most important tools that you will use to design and implement a security solution.
Causes of security problems include weaknesses in policy definitions, computer technologies, and equipment configurations. Security threats can come from internal as well as external sources and are either structured or unstructured. Most security threats originate inside your network.
Security threats are categorized as a reconnaissance, DoS, or access attack. In a reconnaissance attack, the hacker it trying to learn information about your network, including its weaknesses. The hacker then uses this information to implement a DoS or access attack.
Cisco has developed a four-step security wheel to help deal with the implementation and maintenance of a security solution. Security is a never-ending process, so you will be repeating the four steps quite often.
Next up is Chapter 2, which discusses what a firewall is, the types of firewalls, and how to design networks with firewalls.