Chapter 12. Implementing Configuration Changes to Existing Controls to Improve Security
This chapter covers the following topics related to Objective 3.2 (Given a scenario, implement configuration changes to existing controls to improve security) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Permissions: Discusses the importance of proper permissions management
• Whitelisting: Covers the process of whitelisting and its indications
• Blacklisting: Describes a blacklisting process used to deny access
• Firewall: Identifies key capabilities of various firewall platforms
• Intrusion prevention system (IPS) rules: Discusses rules used to automate response
• Data loss prevention (DLP): Covers the DLP process used to prevent exfiltration
• Endpoint detection and response (EDR): Describes a technology that addresses the need for continuous monitoring
• Network access control (NAC): Identifies the processes used by NAC technology
• Sinkholing: Discusses the use of this networking tool
• Malware signatures: Describes the importance of malware signature and development/rule writing
• Sandboxing: Reviews the use of this software virtualization technique to isolate apps from critical system resources
• Port Security: Covers the role of port security in preventing attacks
In many cases, security monitoring data indicates a need to change or implement new controls to address new threats. These changes might be small configuration adjustments to a security device or they might include large investments in new technology. Regardless of the scope, these actions should be driven by the threat at hand and the controls should be exposed to the same cost/benefit analysis to which all organizational activities are exposed.
“Do I Know This Already?” Quiz
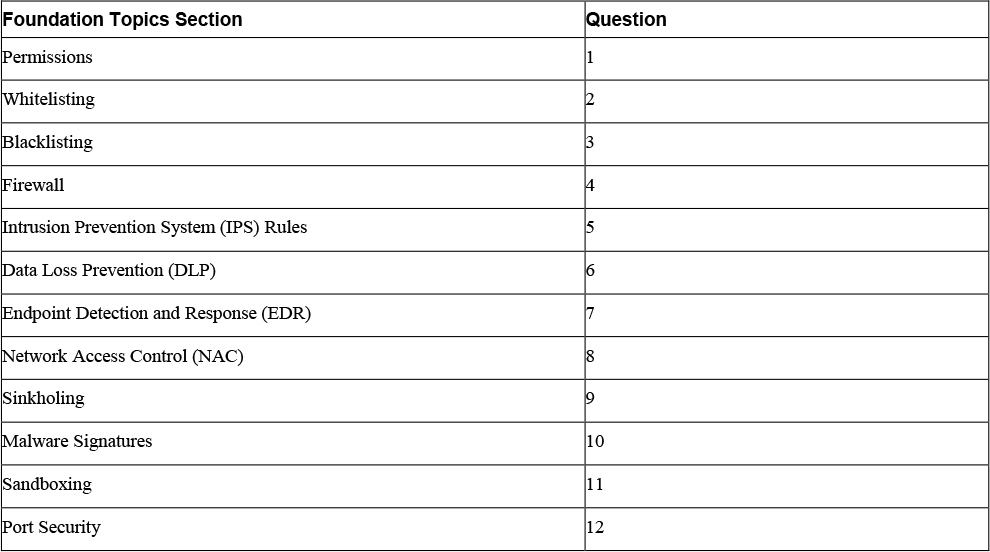
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these 12 self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks” section. Table 12-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 12-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping
1. Which of the following is an example of a right and not a permission?
a. Read access to a file
b. Ability to delete a file
c. Ability to reset passwords
d. Ability to change the permissions of a file
2. When you allow a file type at the exclusion of all other file types, you have created what?
a. Whitelist
b. Access list
c. Blacklist
d. Graylist
3. Which of the following requires the most effort to maintain?
a. Whitelist
b. Access list
c. Blacklist
d. Graylist
4. Which of the following is a category of devices that attempt to address traffic inspection and application awareness shortcomings of a traditional stateful firewall?
a. NGFW
b. Bastion host
c. Three-legged firewall
d. Proxy
5. Which of the following is a type of IPS and is an expert system that uses a knowledge base, an inference engine, and programming?
a. Rule-based
b. Signature-based
c. Heuristics-based
d. Error-based
6. Preventing data exfiltration is the role of which of the following?
a. Trend analysis
b. DLP
c. NAC
d. Port security
7. Which of the following shifts security from a reactive threat approach to one that can detect and prevent threats before they reach the organization?
a. NAC
b. DAC
c. EDR
d. DLP
8. Which of the following is a service that goes beyond authentication of the user and includes examination of the state of the computer the user is introducing to the network when making a remote-access or VPN connection to the network?
a. NAC
b. DAC
c. EDR
d. DLP
9. Which of the following can be used to prevent a compromised host from communicating back to the attacker?
a. Sinkholing
b. DNSSec
c. NASC
d. Port security
10. Which of the following could be a filename or could be some series of characters that can be tied uniquely to the malware?
a. Key
b. Signature
c. Fingerprint
d. Scope
11. Which of the following allows you to run a possibly malicious program in a safe environment so that it doesn’t infect the local system?
a. Sandbox
b. Secure memory
c. Secure enclave
d. Container
12. Which of the following is referred to as Layer 2 security?
a. Sandbox
b. Port security
c. Encoding
d. Subnetting
Foundation Topics
Permissions
Permissions are granted or denied at the file, folder, or other object level. Common permission types include Read, Write, and Full Control. Data custodians or administrators will grant users permissions on a file or folder based on the file owner’s request to do so.
Rights allow administrators to assign specific privileges and logon rights to groups or users. Rights manage who is allowed to perform certain operations on an entire computer or within a domain, rather than on a particular object within a computer. While user permissions are granted by an object’s owner, user rights are assigned using a computer’s local security policy or a domain security policy. User rights apply to user accounts, while permissions apply to objects.
Rights include the ability to log on to a system interactively, which is a logon right, or the ability to back up files, which is considered a privilege. User rights are divided into two categories: privileges and logon rights. Privileges are the right of an account, such as a user or group account, to perform various system-related operations on the local computer, such as shutting down the system, loading device drivers, or changing the system time. Logon rights control how users are allowed access to the computer, including logging on locally or through a network connection or whether as a service or as a batch job.
Conflicts can occur in situations where the rights that are required to administer a system overlap the rights of resource ownership. When rights conflict, a privilege overrides a permission.
Many times an attacker compromises a device by altering the permissions, either in the local database or in entries related to the device in the directory service server. All permissions should undergo a review to ensure that all are in the appropriate state. The appropriate state may not be the state they were in before the event. Sometimes you may discover that although permissions were not set in a dangerous way prior to an event, they are not correct. Make sure to check the configuration database to ensure that settings match prescribed settings. You should also make changes to the permissions based on lessons learned during an event. In that case, ensure that the new settings undergo a change control review and that any approved changes are reflected in the configuration database.
Whitelisting and Blacklisting
Whitelisting occurs when a list of acceptable e-mail addresses, Internet addresses, websites, applications, or some other identifier is configured as good senders or as allowed to send. Blacklisting identifies bad senders. Graylisting is somewhere in between the two, listing entities that cannot be identified as whitelist or blacklist items. In the case of graylisting, the new entity must pass through a series of tests to determine whether it will be whitelisted or blacklisted. Whitelisting, blacklisting, and graylisting are commonly used with spam filtering tools. But there are other used for whitelists and blacklists as well. They are used in routes to enforce ACLs and in switches to enforce port security.
Application Whitelisting and Blacklisting
Application whitelists are lists of allowed applications (with all others excluded), and blacklists are lists of prohibited applications (with all others allowed). It is important to control the types of applications that users can install on their computers. Some application types can create support issues, and others can introduce malware. It is possible to use Windows Group Policy to restrict the installation of software on network computers, as illustrated in Figure 12-1. Using Windows Group Policy is only one option, and each organization should select a technology to control application installation and usage in the network.

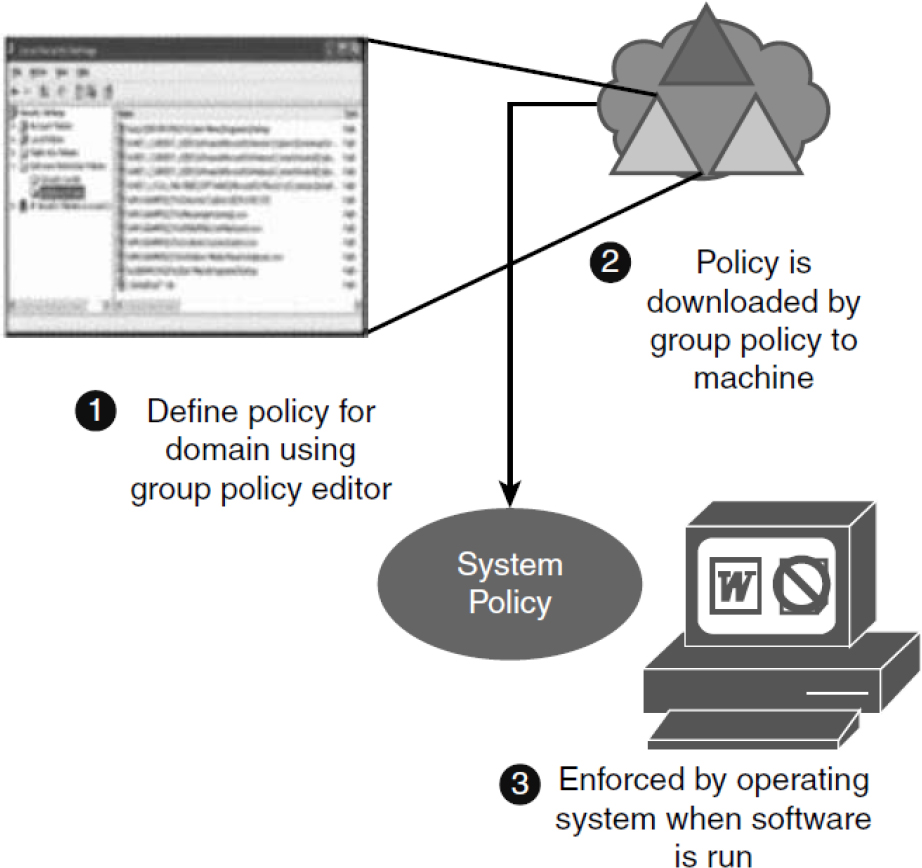
Figure 12-1 Software Restrictions
Input Validation
Input validation is the process of checking all input for things such as proper format and proper length. In many cases, these validators use either the blacklisting of characters or patterns or the whitelisting of characters or patterns. Blacklisting looks for characters or patterns to block. It can prevent legitimate requests. Whitelisting looks for allowable characters or patterns and only allows those. The length of the input should also be checked and verified to prevent buffer overflows.
Firewall
Chapter 11, “Analyzing Data as Part of Security Monitoring Activities,” discussed firewall logs and Chapter 8, “Security Solutions for Infrastructure Management,” discussed the various architectures used in firewalls; at this point we need to look a little more closely at firewall types and their placement for effective operation. Firewalls can be software programs that are installed over server or client operating systems or appliances that have their own operating system. In either case, the job of a firewall is to inspect and control the type of traffic allowed.
NextGen Firewalls
Next-generation firewalls (NGFWs) are a category of devices that attempt to address traffic inspection and application awareness shortcomings of a traditional stateful firewall, without hampering the performance. Although unified threat management (UTM) devices also attempt to address these issues, they tend to use separate internal engines to perform individual security functions. This means a packet may be examined several times by different engines to determine whether it should be allowed into the network.
NGFWs are application aware, which means they can distinguish between specific applications instead of allowing all traffic coming in via typical web ports. Moreover, they examine packets only once, during the deep packet inspection phase (which is required to detect malware and anomalies). The following are some of the features provided by NGFWs:
• Nondisruptive inline configuration (which has little impact on network performance)
• Standard first-generation firewall capabilities, such as network address translation (NAT), stateful protocol inspection (SPI), and virtual private networking
• Integrated signature-based IPS engine
• Application awareness, full stack visibility, and granular control
• Ability to incorporate information from outside the firewall, such as directory-based policy, blacklists, and whitelists
• Upgrade path to include future information feeds and security threats and SSL/TLS decryption to enable identifying undesirable encrypted applications
An NGFW can be placed inline or out-of-path. Out-of-path means that a gateway redirects traffic to the NGFW, while inline placement causes all traffic to flow through the device. Figure 12-2 shows the two placement options for NGFWs.

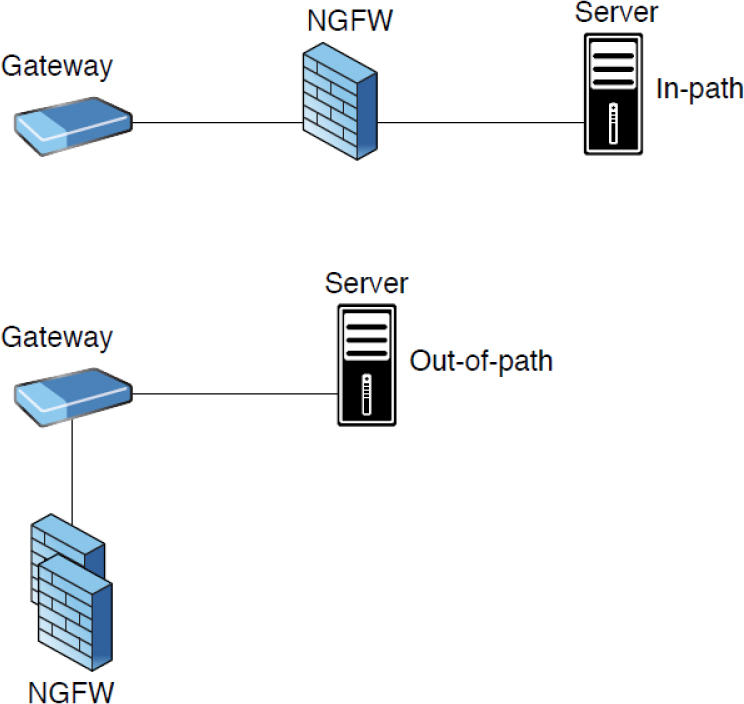
Figure 12-2 Placement of an NGFW
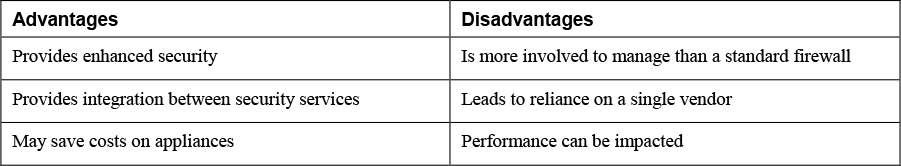
Table 12-2 lists the advantages and disadvantages of NGFWs.

Table 12-2 Advantages and Disadvantages of NGFWs
Host-Based Firewalls
A host-based firewall resides on a single host and is designed to protect that host only. Many operating systems today come with host-based (or personal) firewalls. Many commercial host-based firewalls are designed to focus attention on a particular type of traffic or to protect a certain application.
On Linux-based systems, a common host-based firewall is iptables, which replaces a previous package called ipchains. It has the ability to accept or drop packets. You create firewall rules much as you create an access list on a router. The following is an example of a rule set:
iptables -A INPUT -i eth1 -s 192.168.0.0/24 -j DROP iptables -A INPUT -i eth1 -s 10.0.0.0/8 -j DROP iptables -A INPUT -i eth1 -s 172. -j DROP
This rule set blocks all incoming traffic sourced from either the 192.168.0.0/24 network or the 10.0.0.0/8 network. Both of these are private IP address ranges. It is quite common to block incoming traffic from the Internet that has a private IP address as its source, as this usually indicates that IP spoofing is occurring. In general, the following IP address ranges should be blocked as traffic sourced from these ranges is highly likely to be spoofed:
10.0.0.0/8 172.16.0.0/12 192.168.0.0/16 224.0.0.0/4 240.0.0.0/5 127.0.0.0/8
The 224.0.0.0/4 range covers multicast traffic, and the 127.0.0.0/8 range covers traffic from a loopback IP address. You may also want to include the APIPA 169.254.0.0 range as well, as it is the range in which some computers give themselves IP addresses when the DHCP server cannot be reached. On a Microsoft computer, you can use Windows Defender to block these ranges.
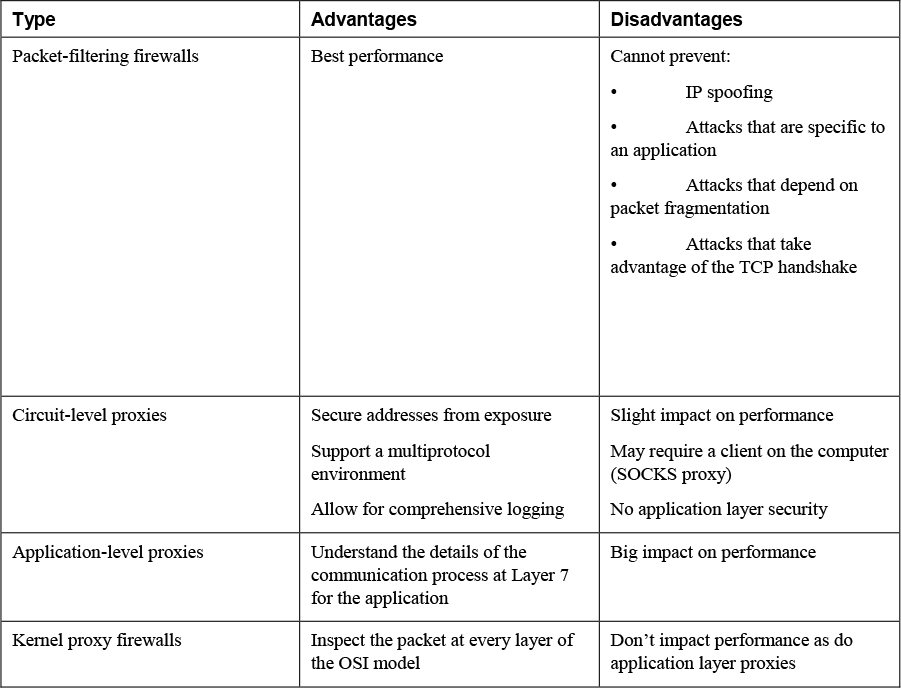
Table 12-3 lists the pros and cons of the various types of firewalls.

Table 12-3 Pros and Cons of Firewall Types
Intrusion Prevention System (IPS) Rules
As you learned earlier, some IPSs can be rule-based. Chapter 3, “Vulnerability Management Activities,” and Chapter 11, “Analyzing Data as Part of Security Monitoring Activities,” covered these IPSs in more detail. Chapter 11 covered rule writing in more detail.
Data Loss Prevention (DLP)
Data loss prevention (DLP) software attempts to prevent data leakage. It does this by maintaining awareness of actions that can and cannot be taken with respect to a document. For example, DLP software might allow printing of a document but only at the company office. It might also disallow sending the document through e-mail. DLP software uses ingress and egress filters to identify sensitive data that is leaving the organization and can prevent such leakage. Another scenario might be the release of product plans that should be available only to the Sales group. You could set the following policy for that document:
• It cannot be e-mailed to anyone other than Sales group members.
• It cannot be printed.
• It cannot be copied.
There are two locations where you can implement this policy:
• Network DLP: Installed at network egress points near the perimeter, network DLP analyzes network traffic.
• Endpoint DLP: Endpoint DLP runs on end-user workstations or servers in the organization.
You can use both precise and imprecise methods to determine what is sensitive:
• Precise methods: These methods involve content registration and trigger almost zero false-positive incidents.
• Imprecise methods: These methods can include keywords, lexicons, regular expressions, extended regular expressions, metadata tags, Bayesian analysis, and statistical analysis.
The value of a DLP system resides in the level of precision with which it can locate and prevent the leakage of sensitive data.
Endpoint Detection and Response (EDR)
Endpoint detection and response (EDR) is a proactive endpoint security approach designed to supplement existing defenses. This advanced endpoint approach shifts security from a reactive threat approach to one that can detect and prevent threats before they reach the organization. It focuses on three essential elements for effective threat prevention: automation, adaptability, and continuous monitoring.
The following are some examples of EDR products:
• FireEye Endpoint Security
• Carbon Black CB Response
• Guidance Software EnCase Endpoint Security
• Cybereason Total Enterprise Protection
• Symantec Endpoint Protection
• RSA NetWitness Endpoint
The advantage of EDR systems is that they provide continuous monitoring. The disadvantage is that the software’s use of resources could impact performance of the device.
Network Access Control (NAC)
Network access control (NAC) is a service that goes beyond authentication of the user and includes examination of the state of the computer the user is introducing to the network when making a remote-access or VPN connection to the network.
The Cisco world calls these services Network Admission Control (NAC), and the Microsoft world calls them Network Access Protection (NAP). Regardless of the term used, the goals of the features are the same: to examine all devices requesting network access for malware, missing security updates, and any other security issues the devices could potentially introduce to the network.
Figure 12-3 shows the steps that occur in Microsoft NAP. The health state of the device requesting access is collected and sent to the Network Policy Server (NPS), where the state is compared to requirements. If requirements are met, access is granted.

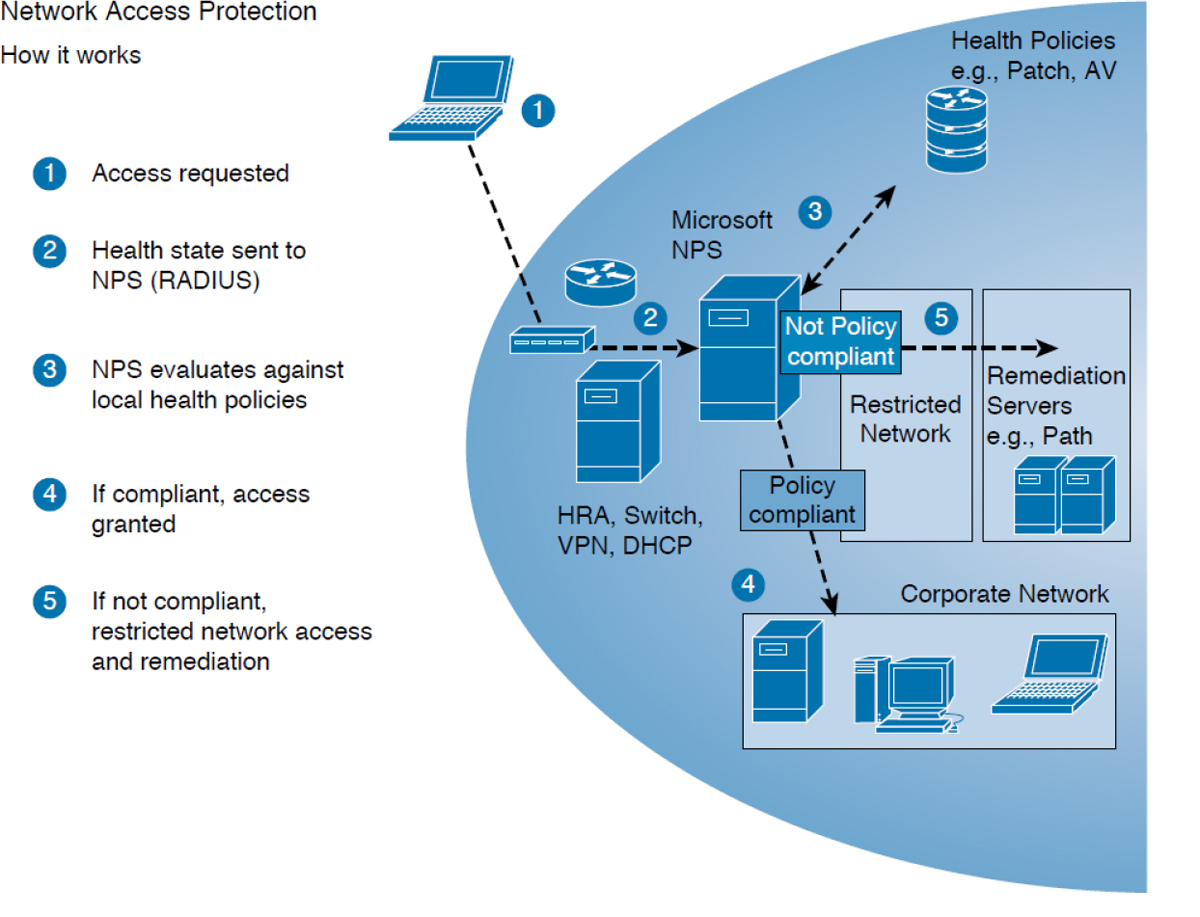
Figure 12-3 NAC
The limitations of using NAC and NAP are as follows:
• They work well for company-managed computers but less well for guests.
• They tend to react only to known threats and not to new threats.
• The return on investment is still unproven.
• Some implementations involve confusing configuration.
Access decisions can be of the following types:

• Time based: A user might be allowed to connect to the network only during specific times of day.
• Rule based: A user might have his access controlled by a rule such as “all devices must have the latest antivirus patches installed.”
• Role based: A user may derive her network access privileges from a role she has been assigned, typically through addition to a specific security group.
• Location based: A user might have one set of access rights when connected from another office and another set when connected from the Internet.
Quarantine/Remediation
If you examine step 5 in the process shown in Figure 12-3, you see that a device that fails examination is placed in a restricted network until it can be remediated. A remediation server addresses the problems discovered on the device. It may remove the malware, install missing operating system updates, or update virus definitions. When the remediation process is complete, the device is granted full access to the network.
Agent-Based vs. Agentless NAC
NAC can be deployed with or without agents on devices. An agent is software used to control and interact with a device. Agentless NAC is the easiest to deploy but offers less control and fewer inspection capabilities. Agent-based NAC can perform deep inspection and remediation at the expense of additional software on the endpoint.
Both agent-based and agentless NAC can be used to mitigate the following issues:
• Malware
• Missing OS patches
• Missing anti-malware updates
802.1X
Another form of network access control is 802.1X Extensible Authentication Protocol (EAP). 802.1X is a standard that defines a framework for centralized port based authentication. It can be applied to both wireless and wired networks and uses three components:
• Supplicant: The user or device requesting access to the network
• Authenticator: The device through which the supplicant is attempting to access the network
• Authentication server: The centralized device that performs authentication
The role of the authenticator can be performed by a wide variety of network access devices, including remote-access servers (both dial-up and VPN), switches, and wireless access points. The role of the authentication server can be performed by a Remote Authentication Dial-in User Service (RADIUS) or Terminal Access Controller Access Control System Plus (TACACS+) server. The authenticator requests credentials from the supplicant and, upon receipt of those credentials, relays them to the authentication server, where they are validated. Upon successful verification, the authenticator is notified to open the port for the supplicant to allow network access. Figure 12-4 illustrates this process.


Figure 12-4 802.1X Architecture
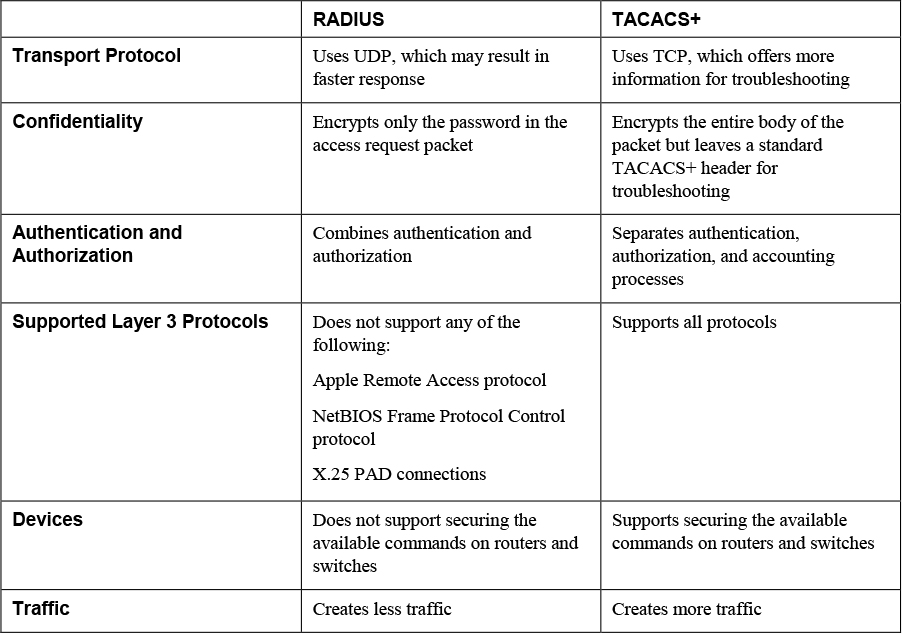
While RADIUS and TACACS+ perform the same roles, they have different characteristics. These differences must be taken into consideration when choosing a method. Keep in mind also that while RADIUS is a standard, TACACS+ is Cisco proprietary. Table 12-4 compares them.

Table 12-4 RADIUS vs. TACACS+
Among the issues 802.1X port-based authentication can help mitigate are the following:
• Network DoS attacks
• Device spoofing (because it authenticates the user, not the device

Sinkholing
A sinkhole is a router designed to accept and analyze attack traffic. Sinkholes can be used to do the following:
• Draw traffic away from a target
• Monitor worm traffic
• Monitor other malicious traffic
During an attack, a sinkhole router can be quickly configured to announce a route to the target’s IP address that leads to a network or an alternate device where the attack can be safely studied. Moreover, sinkholes can also be used to prevent a compromised host from communicating back to the attacker. Finally, they can be used to prevent a worm-infected system from infecting other systems. Sinkholes can be used to mitigate the following issues:
• Worms
• Compromised devices communicating with command and control (C&C) servers
• External attacks targeted at a single device inside the network
Malware Signatures
While placing malware in a sandbox or isolation area for study is a safe way of reverse engineering and eventually disarming the malware, the best defense is to identify and remove malware when it enters the network before it infects the devices.
To do this, network security devices such as SIEM, IPS, IDS, and firewall systems must be able to recognize the malware when it is still contained in network packets before it reaches devices. This requires identifying a malware signature. This could be a filename or it could be some series of characters that can be tied uniquely to the malware.
You learned about signature-based IPS/IDS systems earlier. You may remember that these systems and rule-based systems both rely on rules that instruct the security device to be on the lookout for certain character strings in a packet.
Development/Rule Writing
One of the keys to successful signature matching and therefore successful malware prevention is proper rule writing, which is in the development realm. Just as automation is driving network technicians to learn basic development theory and rule writing, so is malware signature identification. Rule creation does not always rely on the name of the malicious file. It also can be based on behavior that is dangerous in and of itself.
Examples of rules or behavior that can indicate that a system is infected by malware are as follows:
• A system process that drops various malware executables (e.g., Dropper, a kind of Trojan that has been designed to “install” some sort of malware)
• A system process that reaches out to random, and often foreign, IP addresses/domains
• Repeated attempts to monitor or modify key system settings such as registry keys
Sandboxing
Chapter 11 briefly introduced sandboxing. You can use a sandbox to run a possibly malicious program in a safe environment so that it doesn’t infect the local system.
By using sandboxing tools, you can execute malware executable files without allowing the files to interact with the local system. Some sandboxing tools also allow you to analyze the characteristics of an executable. This is not possible with some malware because it is specifically written to do different things if it detects that it’s being executed in a sandbox.
In many cases, sandboxing tools operate by sending a file to a special server that analyzes the file and sends you a report on it. Sometimes this is a free service, but in many instances it is not. Some examples of these services include the following:
• Sandboxie
• Akana
• Binary Guard True Bare Metal
• BitBlaze Malware Analysis Service
• Comodo Automated Analysis System and Valkyrie
• Deepviz Malware Analyzer
• Detux Sandbox (Linux binaries)
Another option for studying malware is to set up a “sheep dip” computer. This is a system that has been isolated from the other systems and is used for analyzing suspect files and messages for malware. You can take measures such as the following on a sheep dip system:
• Install port monitors to discover ports used by the malware.
• Install file monitors to discover what changes may be made to files.
• Install network monitors to identify what communications the malware may attempt.
• Install one or more antivirus programs to perform malware analysis.
Often these sheep dip systems are combined with antivirus sensor systems to which malicious traffic is reflected for analysis. The safest way to perform reverse engineering and malware analysis is to prepare a test bed. Doing so involves the following steps:

Step 1. Install virtualization software on the host.
Step 2. Create a VM and install a guest operating system on the VM.
Step 3. Isolate the system from the network by ensuring that the NIC is set to “host” only mode.
Step 4. Disable shared folders and enable guest isolation on the VM.
Step 5. Copy the malware to the guest operating system.
Also, you need isolated network services for the VM, such as DNS. It may also be beneficial to install multiple operating systems in both patched and unpatched configurations. Finally, you can make use of virtualization snapshots and reimaging tools to wipe and rebuild machines quickly. Once the test bed is set up, you also need to install a number of other tools to use on the isolated VM, including the following:

• Imaging tools: You need these tools to take images for forensics and prosecution procedures. Examples include SafeBack Version 2.0 and Linux dd.
• File/data analysis tools: You need these tools to perform static analysis of potential malware files. Examples include PeStudio and PEframe.
• Registry/configuration tools: You need these tools to help identify infected settings in the registry and to identify the last-saved settings. Examples include Microsoft’s Sysinternals Autoruns and Silent Runners.vbs.
• Sandbox tools: You need these tools for manual malware analysis in a safe environment.
• Log analyzers: You need these tools to extract log files. Examples include AWStats and Apache Log Viewer.
• Network capture tools: You need these tools to understand how the malware uses the network. Examples include Wireshark and Omnipeek.
While the use of virtual machines to investigate the effects of malware is quite common, you should know that some well-written malware can break out of a VM relatively easily, making this approach problematic.

Port Security
Port security applies to ports on a switch or wireless home router, and because it relies on monitoring the MAC addresses of the devices attached to the switch ports, it is considered to be Layer 2 security. While disabling any ports that are not in use is always a good idea, port security goes a step further and allows you to keep a port enabled for legitimate devices while preventing its use by illegitimate devices. You can apply two types of restrictions to a switch port:
• Restrict the specific MAC addresses allowed to send on the port.
• Restrict the total number of different MAC addresses allowed to send on the port.
By specifying which specific MAC addresses are allowed to send on a port, you can prevent unknown devices from connecting to the switch port. Port security is applied at the interface level. The interface must be configured as an access port, so first you ensure that it is by executing the following command:
Switch(config)# int fa0/1 Switch(config-if)# switchport mode access
In order for port security to function, you must enable the feature. To enable it on a switchport, use the following command at the interface configuration prompt:
Switch(config-if)# switchport port security
Limiting MAC Addresses
Now you need to define the maximum number of MAC addresses allowed on the port. In many cases today, IP phones and computers share a switchport (the computer plugs into the phone, and the phone plugs into the switch), so here you want to allow a maximum of two:
Switch(config-if)# switchport port security maximum 2
Next, you define the two allowed MAC addresses, in this case, aaaa.aaaa.aaaa and bbbb.bbbb.bbbb:
Switch(config-if)# switchport port security mac-address aaaa.aaaa.aaaa Switch(config-if)# switchport port security mac-address bbbb.bbbb.bbbb
Finally, you set an action for the switch to take if there is a violation. By default, the action is to shut down the port. You can also set it to restrict, which doesn’t shut down the port but prevents the violating device from sending any data. In this case, set it to restrict:
Switch(config-if)# switchport port security violation restrict
Now you have secured the port to allow only the two MAC addresses required by the legitimate user: one for his phone and the other for his computer. Now you just need to gather all the MAC addresses for all the phones and computers, and you can lock down all the ports. Boy, that’s a lot of work! In the next section, you’ll see that there is an easier way.
Implementing Sticky MAC
Sticky MAC is a feature that allows a switch to learn the MAC addresses of the devices currently connected to the port and convert them to secure MAC addresses (the only MAC addresses allowed to send on the port). All you need to do is specify the keyword sticky in the command where you designate the MAC addresses, and you’re done. You still define the maximum number, and Sticky MAC converts up to that number of addresses to secure MAC addresses. Therefore, you can secure all ports by only specifying the number allowed on each port and specifying the sticky command in the port security mac-address command. To secure a single port, execute the following code:
Switch(config-if)# port security Switch(config-if)# port security maximum 2 Switch(config-if)# port security mac-address sticky
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 12-5 lists a reference of these key topics and the page numbers on which each is found.

Table 12-5 Key Topics
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
next-generation firewalls (NGFWs)
endpoint detection and response (EDR)
Review Questions
1. Granting someone the ability to reset passwords is the assignment of a(n) ________.
2. List at least one disadvantage of packet filtering firewalls.
3. Match the following terms with their definitions.
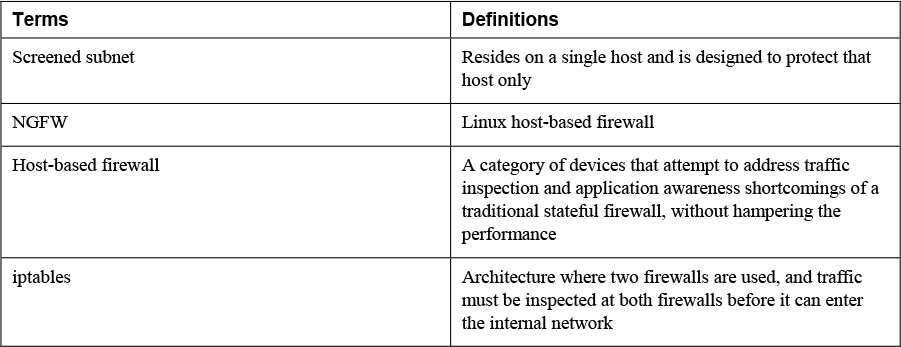
4. List at least two advantages of circuit-level proxies.
5. ___________________ is installed at network egress points near the perimeter, to prevent data exfiltration.
6. Match the following terms with their definitions.
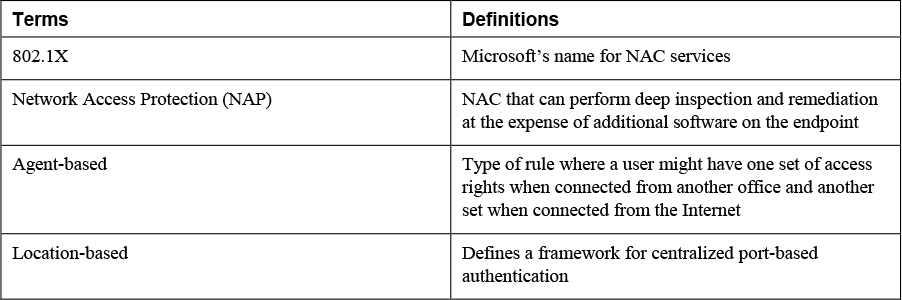
7. List at least two disadvantages of RADIUS.
8. _______________ is a system that has been isolated from the other systems and is used for analyzing suspect files and messages for malware.
9. Match the flowing terms with their definitions.

10. List at least two measures that should be taken with sheep dip systems.
