Chapter 7
Summarizing the Techniques Used in Security Assessments
This chapter covers the following topics related to Objective 1.7 (Summarize the techniques used in security assessments) of the CompTIA Security+ SY0-601 certification exam:
Threat hunting
Intelligence fusion
Threat feeds
Advisories and bulletins
Maneuver
Vulnerability scans
False positives
False negatives
Log reviews
Credentialed vs. non-credentialed
Intrusive vs. non-intrusive
Application
Web application
Network
Common Vulnerabilities and Exposures (CVE) and Common Vulnerability Scoring System (CVSS)
Configuration review
Syslog/Security information and event management (SIEM)
Review reports
Packet capture
Data inputs
User behavior analysis
Sentiment analysis
Security monitoring
Log aggregation
Log collectors
Security orchestration, automation, and response (SOAR)
This chapter starts by introducing threat hunting and how the threat-hunting process leverages threat intelligence. Then you learn about vulnerability management tasks, such as keeping up with security advisories and performing vulnerability scans. You also learn about the importance of collecting logs (such as system logs [syslogs]) and analyzing those logs in a Security Information and Event Management (SIEM) system. In addition, you learn how security tools and solutions have evolved to provide Security Orchestration, Automation, and Response (SOAR) capabilities to better defend your network, your users, and your organizations overall.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read this entire chapter thoroughly or jump to the “Chapter Review Activities” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 7-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Review Questions.”
Table 7-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section |
Questions |
|---|---|
Threat Hunting |
1–3 |
Vulnerability Scans |
4–6 |
Syslog and Security Information and Event Management (SIEM) |
7–8 |
Security Orchestration, Automation, and Response (SOAR) |
9–10 |
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. What is the act of proactively and iteratively looking for threats in your organization that may have bypassed your security controls and monitoring capabilities?
Threat intelligence
Threat hunting
Threat binding
None of these answers are correct.
2. Which of the following provides a matrix of adversary tactics, techniques, and procedures that modern attackers use?
ATT&CK
CVSS
CVE
All of these answers are correct.
3. Which identifier is assigned to disclosed vulnerabilities?
CVE
CVSS
ATT&CK
TTP
4. Which broad term describes a situation in which a security device triggers an alarm, but no malicious activity or actual attack is taking place?
False negative
True negative
False positive
True positive
5. Which of the following is a successful identification of a security attack or a malicious event?
True positive
True negative
False positive
False negative
6. Which of the following occurs when a vulnerability scanner logs in to the targeted system to perform deep analysis of the operating system, running applications, and security misconfigurations?
Credentialed scan
Application scan
Noncredentialed scan
None of these answers are correct.
7. Which of the following are functions of a SIEM?
Log collection
Log normalization
Log correlation
All of these answers are correct.
8. Which solution allows security analysts to collect network traffic metadata?
NetFlow
SIEM
SOAR
None of these answers are correct.
9. Which solution provides capabilities that extend beyond traditional SIEMs?
SOAR
CVSS
CVE
IPFIX
10. Which of the following can be capabilities and benefits of a SOAR solution?
Automated vulnerability assessment
SOC playbooks and runbook automation
Orchestration of multiple SOC tools
All of these answers are correct.
Foundation Topics
Threat Hunting
No security product or technology in the world can detect and block all security threats in the continuously evolving threat landscape (regardless of the vendor or how expensive it is). This is why many organizations are tasking senior analysts in their computer security incident response team (CSIRT) and their security operations center (SOC) to hunt for threats that may have bypassed any security controls that are in place. This is why threat hunting exists.

Threat hunting is the act of proactively and iteratively looking for threats in your organization. This chapter covers details about threat-hunting practices, the operational challenges of a threat-hunting program, and the benefits of a threat-hunting program.
The threat-hunting process requires deep knowledge of the network and often is performed by SOC analysts (otherwise known as investigators, threat hunters, tier 2 or tier 3 analysts, and so on). Figure 7-1 illustrates the traditional SOC tiers and where threat hunters typically reside. In some organizations (especially small organizations), threat hunting could be done by anyone in the SOC because the organization may not have a lot of resources (analysts). The success of threat hunting completely depends on the maturity of the organization and the resources available.

FIGURE 7-1 The SOC Tiers
Some organizations might have a dedicated team within or outside the SOC to perform threat hunting. However, one of the common practices is to have the hunters embedded within the SOC.
Threat hunters assume that an attacker has already compromised the network. Consequently, they need to come up with a hypothesis of what is compromised and how an adversary could have performed the attack. For the threat hunting to be successful, hunters need to be aware of the adversary tactics, techniques, and procedures (TTPs) that modern attackers use. This is why many organizations use MITRE’s ATT&CK framework to be able to learn about the tactics and techniques of adversaries. Later in this chapter you learn more about how MITRE’s ATT&CK can be used in threat hunting.
Threat hunting is not a new concept. Many organizations have performed threat hunting for a long time. However, in the last decade many organizations have adopted new ways to enhance the threat-hunting process with automation and orchestration.
Threat hunting is not the same as the traditional SOC incident response (reactive) activities. Threat hunting is also not the same as vulnerability management (the process of patching vulnerabilities across the systems and network of your organization, including cloud-based applications in some cases). However, some of the same tools and capabilities may be shared among threat hunters, SOC analysts, and vulnerability management teams. Tools and other capabilities such as data analytics, TTPs, vulnerability feeds, and threat feeds may be used across the different teams and analysts in an organization.
A high-level threat-hunting process includes the following steps:
Step 1. Threat hunting starts with a trigger based on an anomaly, threat intelligence, or a hypothesis (what could an attacker have done to the organization?). From that moment you should ask yourself: “Do we really need to perform this threat-hunting activity?” or “What is the scope?”
Step 2. Then you identify the necessary tools and methodologies to conduct the hunt.
Step 3. Once the tools and methodologies are identified, you reveal new attack patterns, TTPs, and so on.
Step 4. You refine your hunting tactics and enrich them using data analytics. Steps 2–3 can take one cycle or be iterative and involve multiple loops (depending on what you find and what additional data and research need to be done).
Step 5. A successful outcome could be that you identify and mitigate the threat. However, you need to recognize that in some cases this may not be the case. You may not have the necessary tools and capabilities, or there was no actual threat. This is why the success of your hunting program depends on the maturity of your capabilities and organization as a whole.
You can measure the maturity of your threat-hunting program within your organization in many ways. Figure 7-2 shows a matrix that can be used to evaluate the maturity level of your organization against different high-level threat-hunting elements.

FIGURE 7-2 Threat-Hunting Maturity
These threat-hunting maturity levels can be categorized as easily as level 1, 2, and 3, or more complex measures can be used.
When it comes to threat intelligence and threat hunting, automation is key! Many organizations are trying to create threat intelligence fusion techniques to automatically extract threat intelligence data from heterogeneous sources to analyze such data. The goal is for the threat hunter and network defender to maneuver quickly—and faster than the attacker. This way, you can stay one step ahead of threat actors and be able to mitigate the attack.
Security Advisories and Bulletins

In Chapter 5, “Understanding Different Threat Actors, Vectors, and Intelligence Sources,” you learned how vendors, coordination centers, security researchers, and others publish security advisories and bulletins to disclose vulnerabilities. Most of the vulnerabilities disclosed to the public are assigned Common Vulnerability and Exposure (CVE) identifiers. CVE is a standard created by MITRE (www.mitre.org) that provides a mechanism to assign an identifier to vulnerabilities so that you can correlate the reports of those vulnerabilities among sites, tools, and feeds.
Note
You can obtain additional information about CVE at https://cve.mitre.org.
One of the most comprehensive and widely used vulnerability databases is the National Vulnerability Database (NVD) maintained by the National Institute of Standards and Technology (NIST). NVD provides information about vulnerabilities disclosed worldwide.
Note
You can access the NVD and the respective vulnerability feeds at https://nvd.nist.gov.
Most mature vendors such as Microsoft, Intel, and Cisco publish security advisories and bulletins in their websites and are CVE Numbering Authorities (CNAs). CNAs can assign CVEs to disclosed vulnerabilities and submit the information to MITRE and subsequently to NVD.
Note
You can find additional information about CNAs at https://cve.mitre.org/cve/cna.html.
The following links include examples of security advisories and bulletins published by different vendors:
Microsoft: https://www.microsoft.com/en-us/msrc
Red Hat: https://access.redhat.com/security/security-updates
Palo Alto: https://security.paloaltonetworks.com
Vulnerability disclosures in security advisories are often coordinated among multiple vendors. Most of the products and applications developed nowadays use open-source software. Vulnerabilities in open-source software could affect hundreds or thousands of products and applications in the industry. In addition, vulnerabilities in protocols such as TLS, TCP, BGP, OSPF, and WPA could also affect numerous products and software. Patching open-source and protocol-related vulnerabilities among upstream and downstream vendors is not an easy task and requires good coordination. Figure 7-3 shows the high-level process of a coordinated vulnerability disclosure and underlying patching.
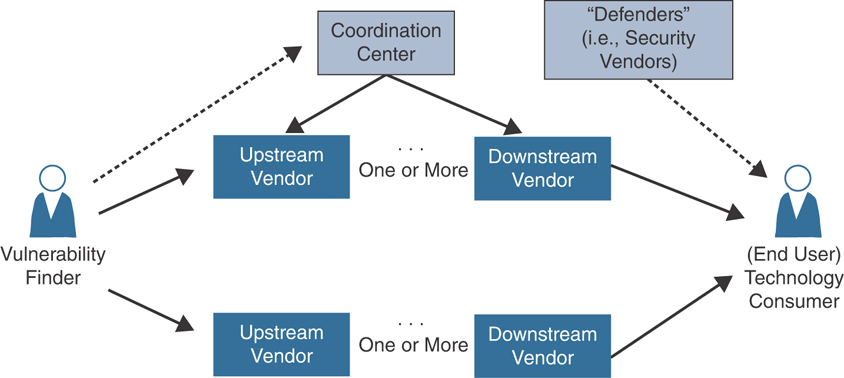
FIGURE 7-3 Coordinated Vulnerability Disclosures
The following steps are illustrated in Figure 7-3:
The finder (this can be anyone—a security researcher, customer, security company, an internal employee of a vendor) finds a security vulnerability and reports it to a vendor. The finder can also contact a vulnerability coordination center (such as www.cert.org) to help with the coordination and disclosure.
The upstream vendors triage and patch the vulnerability.
There could be one or more downstream vendors that also need to patch the vulnerability. In some cases, the coordination center may also interact with downstream vendors in the notification.
Security vendors (such as antivirus/antimalware, intrusion detection, and prevention technology providers) may obtain information about the vulnerability and create signatures or any other capabilities to help the end user detect and mitigate an attack caused by the vulnerability.
The end user is notified of the patch and the vulnerability.
Tip
The preceding process can take days, weeks, months, or even years! Although this process looks very simple in an illustration like the one in Figure 7-3, it is very complicated in practice. For this reason, the Forum of Incident Response and Security Teams (FIRST) has created a Multi-Party Coordination and Disclosure special interest group (SIG) to help address these challenges. You can obtain details about guidelines and practices for multiparty vulnerability coordination and disclosure at https://www.first.org/global/sigs/vulnerability-coordination/multiparty/.
Vulnerability Scans
Vulnerability management teams often use other tools such as vulnerability scanners and software composition analysis (SCA) tools. Figure 7-4 illustrates how a typical automated vulnerability scanner works.

FIGURE 7-4 Coordinated Vulnerability Disclosures
The following are the steps illustrated in Figure 7-4. Keep in mind that vulnerability scanners are all different, but most follow a process like this:
-
In the discovery phase, the scanner uses a tool such as Nmap to perform host and port enumeration. Using the results of the host and port enumeration, the scanner begins to probe open ports for more information.
-
When the scanner has enough information about the open port to determine what software and version are running on that port, it records that information in a database for further analysis. The scanner can use various methods to make this determination, including banner information.
-
The scanner tries to determine if the software that is listening on the target system is susceptible to any known vulnerabilities. It does this by correlating a database of known vulnerabilities against the information recorded in the database about the target services.
-
The scanner produces a report on what it suspects could be vulnerable. Keep in mind that these results are often false positives and need to be validated.

One of the main challenges with automated vulnerability scanners is the number of false positives and false negatives. False positive is a broad term that describes a situation in which a security device triggers an alarm, but no malicious activity or actual attack is taking place. In other words, false positives are false alarms, and they are also called benign triggers. False positives are problematic because by triggering unjustified alerts, they diminish the value and urgency of real alerts. Having too many false positives to investigate becomes an operational nightmare, and you most definitely will overlook real security events.
There are also false negatives, which is the term used to describe a network intrusion device’s inability to detect true security events under certain circumstances—in other words, a malicious activity that is not detected by the security device.
A true positive is a successful identification of a security attack or a malicious event. A true negative occurs when the intrusion detection device identifies an activity as acceptable behavior and the activity is actually acceptable.
There are also different types of vulnerability scanners:
Application scanners: Used to assess application-specific vulnerabilities and operate at the upper layers of the OSI model
Web application scanners: Used to assess web applications and web services (such as APIs)
Network and port scanners: Used to determine what TCP or UDP ports are open on the target system
Credentialed vs. Noncredentialed

To reduce the number of false positives, some vulnerability scanners have the capability to log in to a system to perform additional tests and see what programs, applications, and open-source software may be running on a targeted system. These scanners can also review logs on the target system. They can also perform configuration reviews to determine if a system may be configured in an unsecure way.
Intrusive vs. Nonintrusive

Vulnerability scanners sometimes can send numerous IP packets at a very fast pace (intrusive) to the target system. These IP packets can potentially cause negative effects and even crash the application or system. Some scanners can be configured in such a way that you can throttle the probes and IP packets that it sends to the target system in order to be nonintrusive and to not cause any negative effects in the system.
Common Vulnerability Scoring System (CVSS)
The Common Vulnerability Scoring System (or CVSS) is an industry standard used to convey information about the severity of vulnerabilities. In CVSS, a vulnerability is evaluated under three aspects, and a score is assigned to each of them. These three aspects (or groups) are the base, temporal, and environmental groups.
The base group represents the intrinsic characteristics of a vulnerability that are constant over time and do not depend on a user-specific environment. This is the most important information and the only mandatory information to obtain for a vulnerability score.
The temporal group assesses the vulnerability as it changes over time.
The environmental group represents the characteristic of a vulnerability taking into account the organization’s environment.
The CVSS score is obtained by taking into account the base, temporal, and environmental group information. The score for the base group is between 0 and 10, where 0 is the least severe and 10 is assigned to highly critical vulnerabilities (for example, for vulnerabilities that could allow an attacker to remotely compromise a system and get full control). Additionally, the score comes in the form of a vector string that identifies each of the components used to make up the score. The formula used to obtain the score takes into account various characteristics of the vulnerability and how the attacker is able to leverage these characteristics. CVSS defines several characteristics for the base, temporal, and environmental groups.
Tip
You can read and refer to the latest CVSS specification documentation, examples of scored vulnerabilities, and a calculator at www.first.org/cvss.
The base group defines exploitability metrics that measure how the vulnerability can be exploited, and impact metrics that measure the impact on confidentiality, integrity, and availability. In addition to these two, a metric called scope change (S) is used to convey the impact on systems that are affected by the vulnerability but do not contain vulnerable code.
Exploitability metrics include the following:
Attack Vector (AV): Represents the level of access an attacker needs to have to exploit a vulnerability. It can assume four values:
Network (N)
Adjacent (A)
Local (L)
Physical (P)
Attack Complexity (AC): Represents the conditions beyond the attacker’s control that must exist in order to exploit the vulnerability. The values can be one of the following:
Low (L)
High (H)
Privileges Required (PR): Represents the level of privileges an attacker must have to exploit the vulnerability. The values are as follows:
None (N)
Low (L)
High (H)
User Interaction (UI): Captures whether user interaction is needed to perform an attack. The values are as follows:
None (N)
Required (R)
Scope (S): Captures the impact on systems other than the system being scored. The values are as follows:
Unchanged (U)
Changed (C)
The Impact metrics include the following:
Confidentiality Impact (C): Measures the degree of impact to the confidentiality of the system. It can assume the following values:
Low (L)
Medium (M)
High (H)
Integrity Impact (I): Measures the degree of impact to the integrity of the system. It can assume the following values:
Low (L)
Medium (M)
High (H)
Availability Impact (A): Measures the degree of impact to the availability of the system. It can assume the following values:
Low (L)
Medium (M)
High (H)
The temporal group includes three metrics:
Exploit code maturity (E): Measures whether or not public exploits are available
Remediation Level (RL): Indicates whether a fix or workaround is available
Report Confidence (RC): Indicates the degree of confidence in the existence of the vulnerability
The environmental group includes two main metrics:
Security Requirements (CR, IR, AR): Indicate the importance of confidentiality, integrity, and availability requirements for the system
Modified Base Metrics (MAV, MAC, MAPR, MUI, MS, MC, MI, MA): Allow the organization to tweak the base metrics based on specific characteristics of the environment
For example, a vulnerability that could allow a remote attacker to crash the system by sending crafted IP packets would have the following values for the base metrics:
Access Vector (AV) would be Network because the attacker can be anywhere and can send packets remotely.
Attack Complexity (AC) would be Low because it is trivial to generate malformed IP packets.
Privilege Required (PR) would be None because no privileges are required by the attacker on the target system.
User Interaction (UI) would also be None because the attacker does not need to interact with any user of the system in order to carry out the attack.
Scope (S) would be Unchanged if the attack does not cause other systems to fail.
Confidentiality Impact (C) would be None because the primary impact is on the availability of the system.
Integrity Impact (I) would be None because the primary impact is on the availability of the system.
Availability Impact (A) would be High because the device becomes completely unavailable while crashing and reloading.
CVSS also defines a mapping between a CVSS Base Score quantitative value and a qualitative score. Table 7-2 provides the qualitative-to-quantitative score mapping.
Table 7-2 Qualitative-to-Quantitative Score Mapping
Rating |
CVSS Base Score |
|---|---|
None |
0.0 |
Low |
0.1–3.9 |
Medium |
4.0–6.9 |
High |
7.0–8.9 |
Critical |
9.0–10.0 |
Tip
Organizations can use the CVSS score as input to their own risk management processes to evaluate the risk related to a vulnerability and then prioritize the vulnerability remediation.
Logs and Security Information and Event Management (SIEM)

Security Information and Event Management (SIEM) is a specialized device or software used for security monitoring; it collects, correlates, and helps security analysts analyze logs from multiple systems. SIEM typically allows for the following functions:
Log collection: This includes receiving information from devices with multiple protocols and formats, storing the logs, and providing historical reporting and log filtering. A log collector is software that is able to receive logs from multiple sources (data input) and in some cases offers storage capabilities and log analysis functionality.
Log normalization: This function extracts relevant attributes from logs received in different formats and stores them in a common data model or template. This allows for faster event classification and operations. Non-normalized logs are usually kept for archive, historical, and forensic purposes.
Log aggregation: This function aggregates information based on common information and reduces duplicates.
Log correlation: This is probably one of the most important SIEM functions. It refers to the capability of the system to associate events gathered by various systems, in different formats and at different times, and create a single actionable event for the security analyst or investigator. Often the quality of SIEM is related to the quality of its correlation engine.
Reporting: Event visibility is also a key functionality of SIEM. Reporting capabilities usually include real-time monitoring and historical base reports.
Most modern SIEMs also integrate with other information systems to gather additional contextual information to feed the correlation engine. For example, they can integrate with an identity management system to get contextual information about users or with NetFlow collectors to get additional flow-based information.
Note
NetFlow is a technology created by Cisco to collect network metadata about all the different “flows” of traffic on your network. There’s also the Internet Protocol Flow Information Export (IPFIX), which is a network flow standard led by the Internet Engineering Task Force (IETF). IPFIX was designed to create a common, universal standard of export for flow information from routers, switches, firewalls, and other infrastructure devices. IPFIX defines how flow information should be formatted and transferred from an exporter to a collector. IPFIX is documented in RFC 7011 through RFC 7015 and RFC 5103. Cisco NetFlow Version 9 is the basis and main point of reference for IPFIX. IPFIX changes some of the terminologies of NetFlow, but in essence they are the same principles of NetFlow Version 9.
Several commercial SIEM systems are available. Here’s a list of some commercial SIEM solutions:
Micro Focus ArcSight
LogRhythm
IBM QRadar
Splunk
Figure 7-5 shows how SIEM can collect and process logs from routers, network switches, firewalls, intrusion detection, and other security products that may be in your infrastructure. It can also collect and process logs from applications, antivirus, antimalware, and other host-based security solutions.
Security operation center analysts and security engineers often collect packet captures during the investigation of a security incident. Packet captures provide the greatest detail about each transaction happening in the network. Full packet capture has been used for digital forensics for many years. However, most malware and attackers use encryption to be able to bypass and obfuscate their transactions. IP packet metadata can still be used to potentially detect an attack and determine the attacker’s tactics and techniques.

FIGURE 7-5 SIEM Collecting and Processing Logs from Disparate Systems
One of the drawbacks of collecting full packet captures in every corner of your network is the requirement for storage because packet captures in busy networks can take a significant amount of disk space. This is why numerous organizations often collect network metadata with NetFlow or IPFIX and store such data longer than when collecting packet captures.
Several sophisticated security tools also provide user behavior analysis mechanisms in order to potentially find insiders (internal attackers). Similarly, they provide insights of user behavior even if they do not present a security threat.
Organizations can also deploy sentiment analysis tools and solutions to help monitor customer sentiment and brand reputation. Often these tools can also reveal the intent and tone behind social media posts, as well as keep track of positive or negative opinions. Threat actors can also try to damage a company’s reputation by creating fake accounts and bots in social media platforms like Twitter, Facebook, or Instagram. Attackers can use these fake accounts and bots to provide negative public comments against the targeted organization.
Security Orchestration, Automation, and Response (SOAR)

CSIRT analysts typically work in an SOC utilizing many tools to monitor events from numerous systems (firewalls, applications, IPS, DLP, endpoint security solutions, and so on). Typically, these logs are aggregated in a SIEM. Modern SOCs also use Security Orchestration, Automation, and Response (SOAR) systems that extend beyond traditional SIEMs.
The tools in the SOC are evolving and so are the methodologies. For example, now security analysts not only respond to basic cyber events but also perform threat hunting in their organizations. SOAR is a set of solutions and integrations designed to allow organizations to collect security threat data and alerts from multiple sources. SOAR platforms take the response capabilities of SIEM to the next level. SOAR solutions supplement, rather than replace, the SIEM. They allow the cybersecurity team to extend its reach by automating the routine work of cybersecurity operations.
Tip
Unlike traditional SIEM platforms, SOAR solutions can also be used for threat and vulnerability management, security incident response, and security operations automation.
Deploying SOAR and SIEM together in solutions makes the life of SOC analysts easier. SOAR platforms accelerate incident response detection and eradication times because they can automatically communicate information collected by SIEM with other security tools. Several traditional SIEM vendors are changing their products to offer hybrid SOAR/SIEM functionality.
Another term adopted in the cybersecurity industry is Extended Detection and Response (XDR). XDR is a series of systems working together that collects and correlates data across hosts, mobile devices, servers, cloud workloads, email messages, web content, and networks, enabling visibility and context into advanced threats. The goal of an XDR system is to allow security analysts to analyze, prioritize, hunt, and remediate cybersecurity threats to prevent data loss and security breaches.
Chapter Review Activities
Use the features in this section to study and review the topics in this chapter.
Review Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 7-3 lists a reference of these key topics and the page number on which each is found.

Table 7-3 Key Topics for Chapter 7
Key Topic Element |
Description |
Page Number |
|---|---|---|
Paragraph |
Defining threat hunting |
175 |
Paragraph |
Understanding security advisories, bulletins, and what a CVE is |
177 |
Paragraph |
Understanding false positives and false negatives |
181 |
Section |
Credentialed vs. Noncredentialed |
182 |
Section |
Intrusive vs. Nonintrusive |
182 |
Paragraph |
Defining what SIEM is |
186 |
Paragraph |
Understanding the SOAR concept |
188 |
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Common Vulnerability and Exposures (CVE)
Review Questions
Answer the following review questions. Check your answers with the answer key in Appendix A.
1. What type of vulnerability scanner can be used to assess vulnerable web services?
2. What documents do vendors, vulnerability coordination centers, and security researchers publish to disclose security vulnerabilities?
3. What term is used to describe an organization that can assign CVEs to vulnerabilities?
4. What public database can anyone use to obtain information about security vulnerabilities affecting software and hardware products?
5. How many score “groups” are supported in CVSS?
6. A vulnerability with a CVSS score of 4.9 is considered a ___________ severity vulnerability.
7. What is the process of iteratively looking for threats that may have bypassed your security controls?
