Chapter 14
Understanding the Security Implications of Embedded and Specialized Systems
This chapter covers the following topics related to Objective 2.6 (Explain the security implications of embedded and specialized systems) of the CompTIA Security+ SY0-601 certification exam:
Embedded systems
Raspberry Pi
Field-programmable gate array (FPGA)
Arduino
Supervisor control and data acquisition (SCADA)/Industrial control system (ICS)
Facilities
Industrial
Manufacturing
Energy
Logistics
Internet of Things (IoT)
Sensors
Smart devices
Wearables
Facility automation
Weak defaults
Specialized
Medical systems
Vehicles
Aircraft
Smart meters
Voice over IP (VoIP)
Heating, ventilation, air conditioning (HVAC)
Drones
Multifunction printer (MFP)
Real-time operating system (RTOS)
Surveillance systems
System on chip (SoC)
Communication Considerations
5G
Narrow-band
Baseband radio
Subscriber identity module (SIM) cards
Zigbee
Constraints
Power
Compute
Network
Crypto
Inability to patch
Authentication
Range
Cost
Implied Trust
As we are striving to fit more functionalities into smaller embedded systems, their security is often neglected. Internet of Things (IoT) mobile devices such as smartphones, tablets, and wearables are already ubiquitous, but as the IoT market is expanding, nonmobile IoT systems are expected to outnumber the current IoT-enabled mobile devices in a few years. Embedded systems are getting smaller and smarter, enabling us to get more things done than ever before. As more functionalities are embedded in smaller device footprints, there also is an upsurge in security concerns. Device vendors prefer to add new features that often crowd out the basic security systems, thus launching devices with low security capabilities.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read this entire chapter thoroughly or jump to the “Chapter Review Activities” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 14-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Review Questions.”
Table 14-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section |
Questions |
|---|---|
Embedded Systems |
1–2 |
SCADA/ICS |
3 |
Internet of Things (IoT) |
4–5 |
Specialized Systems |
6 |
Surveillance Systems |
7 |
Communication Considerations |
8 |
Embedded System Constraints |
9 |
System on a Chip (SoC) |
10 |
Real-Time Operating Systems (RTOS) |
11 |
Drones |
12 |
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Which of the following embedded devices are field programmable and are a reconfigurable integrated circuit that can perform logic gates such as AND gate, OR gate, and NOT gate?
FPGA
PStat
BIOS
None of these answers are correct.
2. Which of the following Supervisory Control and Data Acquisition systems are part of the logistics ecosystem?
Just-in-time manufacturing
Fish tank controls
Industrial plant mixing platforms
None of these answers are correct.
3. Which of the following embedded devices can read plant field device output and input and can control or regulate devices like motors and generators?
PLC
PStat
Bios
None of these answers are correct.
4. Which IoT device is considered a wearable device and is helpful for your well-being?
Smart tennis shoes
Smart watch
Smart jackets
Smart headband
5. Which of the following IoT devices are part of facility automation?
Lighting and air conditioning
Raspberry Pi
Garage door sensors
Computer Energy Star
6. Security associated with specialized systems generally requires the user to set up logging and auditing of passwords. What else should the user do to ensure the system is secure?
Lock passwords in a password vault that only staff has access to.
Ensure the network operations center is aware of hard drive failures in critical systems.
Always log passwords in the security operations center log book.
Always create and rotate very complex passwords.
7. Today’s surveillance systems are cable of using technology to perform all of the tasks listed here except for which of the following?
Monitoring the data center access
Pivoting from one system to another
Performing facial recognition
Authenticating application usage
8. Which communication method is part of the IEEE’s 802.15.4 standard and has a transmission rate of 250 kbps?
5G
Narrow band
Baseband radio
Zigbee
9. A major constraint on embedded systems deals with the size of the unit and capability. What is one of the concerns related to security?
The amount of energy required to load the boot loader at startup
The ability to reboot the system remotely with a password
The amount of code required to implement a secure algorithm
The amount of power and amperage available to power on the unit at startup
10. Which of the following is considered a system on a chip?
The desktop computer used to perform number calculations that can be used to create documents
The ability to reboot the system remotely with a password
A cell phone and cell phone–type device with personal data access
A tablet with WiFi and/or cell LTE connectivity capabilities
11. Which is one application of a real-time operating system being used in the commercial space that helps save lives?
Nucleus RTOS from Mentor, used in medical devices
Raspberry PI using the optional POE module for power
A SOC that can be used to provide fusion
The Arduino med-xcapp heart register system connected to a WiFi network
12. Which low-power device has been used in commercial applications to reduce human interaction capabilities and keep people safe?
Catapults with wireless controllers that can move objects across enemy lines and determine troop sizes
Drones used in harsh environments such as refineries and terminals where flammable gases can be dangerous to humans
Robotic window washers, which ensure that windows are washed without the need for a human to be on a scaffolding
Microdots that enable spies to see inside facilities to ensure it’s safe for them to carry out operations
Foundation Topics
Embedded Systems
Embedded systems are microprocessor-based computer hardware systems with software that is designed to perform a dedicated function, either as an independent system or as a part of a larger system. At the core is an integrated circuit designed to carry out computation for real-time operations. The following embedded systems are used in everyday projects, systems, and commercial products:

Raspberry Pi: A low-cost, credit-card-sized computer (see Figure 14-1) that plugs into a computer monitor, keyboard, and mouse. It’s capable of doing everything a desktop computer can do—from browsing the Internet and playing high-definition video to creating spreadsheets, doing word processing, and playing games. If you watched Mr. Robot, Season 1, Episode 4, you saw Elliott use a Raspberry Pi to hack the HVAC system to raise the temperature to destroy backup tapes.

FIGURE 14-1 Raspberry Pi
Note
The Raspberry Pi is a capable computer that can interact with the outside world and can be used in a wide array of digital maker projects, from hacking projects, music machines, and weather stations to tweeting birdhouses with infrared cameras.
Note
For more information on Raspberry Pi, visit www.raspberrypi.org/.
Arduino: An open-source electronics platform based on easy-to-use hardware and software. Arduino boards are extremely flexible; they are able to read inputs such as a light on a sensor, button presses, and even a Twitter message (and turn it into an output), activating a motor, turning on an LED, and publishing something online. You can tell your board what to do by sending a set of instructions. The Arduino software is easy for beginners to use yet flexible enough for advanced users. It runs on Mac, Windows, and Linux. Teachers and students use it to build low-cost scientific instruments, to prove chemistry and physics principles, and to get started with programming and robotics. Designers and architects build interactive prototypes, and musicians and artists use it for installations and to experiment with new musical instruments. Arduino is like any compute platform, so it is susceptible to a series of attacks including buffer overflows, stack smashing (data leakage), and code execution. These devices also run Linux operating systems, which also can be exploited. Care should be taken where these devices run, protecting them from exposure to unprotected networks and systems.
Tip
You can visit the Arduino open-source community at https://arduino.cc for all kinds of projects and Arduino device add-ons.
Field-Programmable Gate Array (FPGA): An integrated circuit designed to be configured by a customer or designer after manufacturing—hence the term field-programmable. Modern FPGAs consist of mixes of configurable static random-access memory (SRAM), high-speed input/output (I/O) pins, logic blocks, and routing. More specifically, an FPGA contains programmable logic elements called logic elements (LEs), as well as a hierarchy of reconfigurable interconnects that allow the LEs to be physically connected to one another. You can configure LEs to do complex functions or simply perform basic logic gates, such as AND gate, OR gate, and NOT gate. FPGAs are vulnerable to supply chain attacks because chips are manufactured in a number of countries with varying degrees of oversight and attention to processes. FPGAs are particularly vulnerable to readback attacks directly obtained when the device is in the Field mode. There are killswitch and backdoor attacks in which the device itself can be programmed with specific code, waiting for an attacker to initiate it remotely.

Supervisory Control and Data Acquisition (SCADA)/Industrial Control Systems (ICS)
Supervisory control and data acquisition (SCADA) systems and industrial control systems (ICSs) are made up of a combination of specialized software and hardware elements that allow organizations to
Monitor equipment processes and performance
Perform data monitoring and collection
Facilitate data analysis and storage of analyzed data
Perform remote control of equipment, devices, components, and processes
Trigger alerts and alarms when performance or deviation aberrations are detected
Report generators for scheduled and automated variance reporting and comparison, as well as production efficiency and status code statistics
SCADA systems are crucial for industrial organizations because they help to maintain efficiency, process data for smarter decisions, and communicate system issues to help mitigate downtime.
The basic SCADA architecture starts with a series of configurable devices called programmable logic controllers (PLCs) or remote terminal units (RTUs). PLCs and RTUs are microcomputers that communicate with an array of objects such as turbines, machines, gauges, sensors, and end devices, and then route the information from those objects to computers with SCADA software. The SCADA software processes, distributes, and displays the data, helping operators and other employees analyze the data and make important decisions.
For example, the SCADA system quickly notifies an operator that a batch of products shows a high incidence of errors. The operator pauses the operation and views the SCADA system data via a human-machine interface (HMI) to determine the cause of the issue. The operator reviews the data and discovers that a specific machine in the process was malfunctioning. The SCADA system’s capability to notify the operator of an issue helps him or her to resolve it and prevent further loss.
To defend against cyber attacks, a firewall can act as a security buffer between the SCADA network and the corporate network. SCADA systems should never be connected to the Internet, even with firewalls in place. You should configure internal firewalls that include virtual private networks (VPNs) for remote SCADA systems internal administration as an added extra layer of protection. To address authentication and authorization security concerns, you need to configure the authentication process in the software to identify authorized users for access to the SCADA system, enable logging to track users’ activity and alerting to warn of deviations to critical controls, and ensure least privilege access. Depending on the perceived risk of cyber attack on the SCADA system, you should deploy intrusion detection and offsite redundancy, as part of a defense-in-depth strategy:
Facilities: From facility controls like HVAC, elevators, lighting, room thermal and temperature, occupancy, parking sensors, device usage sensors and much more, facility managers are able to monitor and control whether a building is operating optimally. SCADA systems can help organizations reduce their carbon footprint through energy management, by automatically turning off lights and air conditioning to sections of the building that are unoccupied.
Industrial: ICS and SCADA systems monitor, control, sense, and warn engineers of all aspects of the processes in industrial plants. From refineries, chemical plants, and more, SCADA systems can control the flow of crude oil being turned into gasoline, asphalt, and chemicals like cleaning supplies. This complex process has many controls that could be dangerous if inappropriately configured.
Manufacturing: Control systems in the manufacturing process depend heavily on data, performance monitoring, and capabilities to control remote equipment, which are among the most-discussed concerns in manufacturing. These components are frequently mentioned as the backbones of “Industry 4.0.” Industry 4.0 is the current trend of automation and data exchange in manufacturing technologies. It includes cyber-physical systems, the Internet of Things, and cloud computing. Industry 4.0 creates what has been called the “smart factory.” Monitoring, data capture and analysis, and equipment control from anywhere are recognized as highly effective ways to improve facility and equipment productivity, performance, and efficiency. The benefits of using SCADA control systems in the manufacturing process include reducing product errors and discards (thanks to earlier problem detection and remedies), improving productivity, and maximizing the effectiveness of machine uptime. Maintenance benefits through the use of data and sensors include more accurate diagnostics, more efficient maintenance processes, and the enablement of predictive maintenance. Data-driven insights into equipment performance can facilitate more accurate calibration, operation, and decision-making processes.
Energy: SCADA systems aid in energy management because the global need for cost-effective electrical power is on the rise. With an increase in factory automation productivity and accuracy, with ever-expanding data centers, there is a greater demand on electrical power utilities. An organization can integrate alternative energy sources, such as solar and wind, in their overall facility power source planning to obtain efficiency, stability, and safety. For power distribution system generators, operators and manufacturers alike, unplanned downtime is extremely costly, risky, and inconvenient. For operators, a stable, sustainable load flow across all components of a system is key for uninterrupted, safe operation. For manufacturers, any unplanned downtime can mean delays in production and missed deadlines. In both cases, predictive and proactive maintenance strategies can maximize uptime by alerting operators and manufacturers to potential issues early. Transit authorities use SCADA technology to regulate electricity to subways, trams, and trolley buses.
Logistics: SCADA systems are capable of managing parts inventories for just-in-time manufacturing, regulating industrial automation and robots, and monitoring processes and quality control. Transit authorities use SCADA technology to automate traffic signals for rail systems; to track and locate trains, trucks, and buses; and to control railroad crossing gates. Continuous communication for trucks, locomotives, and transport vehicles provides valuable information, such as location and status, and is especially important for unmanned vehicles. SCADA systems can regulate traffic lights, control traffic flow, and detect out-of-order signals. Other specialized systems extend GPS and cargo tracking systems because knowing where ships, trains, trucks, and inventory are located anywhere in the world is critical to meet today’s demand for products. These systems require special security considerations; regulators have long insisted that these systems be air-gapped to reduce threats. An air-gapped system is standalone in terms of a system on its own or a network that is isolated from the outside world. A key mitigation or control against attacks on SCADA systems and ICS is to implement physical segregation of internal and external networks, to reduce the attack surface by segregating the SCADA network from the corporate LAN with a firewall. An ICS is managed via a SCADA system. SCADA systems drive HMI for operators to monitor the status of a system while in the field. Other ICS components include industrial automation and control systems (IACS), distributed control systems (DCS), programmable logic controllers (PLCs), and remote terminal units (RTUs).
Figure 14-2 shows a basic SCADA diagram.

FIGURE 14-2 SCADA Diagram
Internet of Things (IoT)
The benefits of the Internet of Things (IoT) are undeniable; and yet high-profile attacks, combined with uncertainty about security best practices and their associated costs, are keeping many businesses from adopting the technology. Besides, end users are wary of the consequences of IoT security breaches. Recent research indicates that 90 percent of consumers lack confidence in IoT device security.
NOTE
IoT manufacturers should do a thorough security risk assessment that examines vulnerabilities in devices and network systems as well as in user and customer back-end systems. Risk must be mitigated for the entire IoT lifecycle of the deployment, especially as it scales.
Tip
You should change default manufacturer usernames and passwords.

Cybersecurity must be designed into IoT devices from the ground up and at all points in the ecosystem to prevent vulnerabilities in one part from jeopardizing the security of the entire system. Today’s IoT ecosystems are complex; devices in virtually every industry, which includes cellular networks to cloud applications and back ends, can be connected and configured to send data. Hackers are consistently looking for ways to exploit IoT system vulnerabilities. Because IoT devices are so diverse, there is no “one size fits all” cybersecurity solution that can protect any IoT deployment.
The following components are associated with the Internet of Things (IoT).
Sensors: Sensor cybersecurity implications go well beyond the voice- controlled devices you talk to at home, such as your lights and TV. Sensors are part of the critical infrastructure that monitors and manages power plants, refineries, maritime ships, and air traffic controllers. Because sensors are small and versatile, functionality is crucial, but security is usually secondary and largely dependent on outside security systems. To protect sensors from attacks, you should use a layered and air-gapped approach when designing and deploying supporting networks.
Smart devices: Smart devices are everywhere, from wired and wireless networks that control lighting to A/C, garage doors, security systems, and curtains; they are embedded in TVs, toasters, and even your barbecue grill. To protect smart devices, you should disable features that you are not using and enable them only when required, use strong encryption methods, and employ complex passwords. You should turn privacy settings to their highest levels and select to not share data, or not turn them on at all, and where possible, change the default manufacturer usernames and passwords.
Wearables: Wearables include smart watches, pedometers, glasses, 3D headsets, smart clothing, health and fitness devices, heart and chemical and gas sensors, and much more. Security for these devices has been improving with the advent of high-performing processors but is still lacking in many aspects. We have seen the breach of smart watches that disclose running patterns. To protect wearables, much like most other devices, you should change all default settings, disable features and functions you’re not using, set privacy settings to their highest level, and turn off location tracking where possible.
Facility automation: An unprotected building automation system can quickly become a high risk with potential life-threatening damage to its occupants and the building itself; therefore, securing these systems is a necessity. Even the most severe data breach in a traditional organization is unlikely to have a direct physical impact on the life of occupants of the building. However, a malicious attack on a building automation system can very easily pose a significant threat to the health and safety of the occupants. Protecting these systems typically starts with a separate and isolated network from the corporate network, separate firewalls and monitoring, and abiding by a strict zero-trust approach to any connections made to this network.
Weak defaults: From the implementation of weak protocols to default usernames and passwords, many of today’s IoT devices are shipped with weak defaults. There are countless IoT devices and applications in your home and business; using weak or default passwords places devices at greater risk of exposing personal information or being used as pivot devices to gain a strong foothold inside. Pending legislation would require IoT device manufacturers to use strong encryption methods and require complex passwords during setup. However, until that happens, you must change default passwords and utilize the strongest encryption method the device supports. If you are unable to get past this, consider changing the device to something that has stronger capabilities. Don’t use Admin as a username because it’s the most common username used in attacks. Also, be sure to change default passwords to complex nondictionary types. In addition, you should run regular audits and scans on all IoT devices (several open-source IOT scanners are available), check for new and/or unknown devices on your network, and check the logs of those devices for password lockouts and strange activity. Another option is to check Shodan (a repository of Internet-accessible devices); this is where attackers go to find insecure devices to attack. Make sure your devices are not listed, but if they are, plug the device in behind a firewall, turn off unused features, and use complex secure passwords.
Specialized Systems
Embedded specialized systems like those used in hospitals, vehicles, aircraft, and smart meters have a long history of placing functionality and convenience before security. There are some simple and not so simple steps an organization can take to reduce the exposure that these devices present. First, you should always utilize the strongest encryption method available on the device. Second, always create and rotate very complex passwords. Third, set up a continuous method to log and audit access to the devices. Fourth, ensure you use the latest manufacturer updates to keep your devices up to date, and do not use beta, test, or bleeding edge updates. If all else fails, disable communication protocols such as WiFi, Bluetooth, Zigbee, and any others.
Specialized systems can include those systems that monitor other systems. For example, a supply chain attack was recently perpetrated by a specific nation outside the U.S.; we call these attacks Nation State attacks, and this specific attack perpetrator was nicknamed APT29 or Cozy Bear. The attack was against a rather well-known network and system monitoring product. Thousands of customers from the U.S. government to cybersecurity companies were affected. In the end, root cause analysis determined an intern used a weak password to protect a rather high-profile system used for pushing updates of its products to customers. (Ref: CVE-2020-166).
Another example of a high-profile attack comes from CVE-2020-14750—a remotely exploitable without authentication attack on a webserver technology, where an attacker can take complete control of the system. This specific web server was prevalent and deployed and used widely. These types of vulnerabilities are reported infrequently; however, when they hit, they affect large populations of systems.
As a security professional, you should always be aware and on alert for notifications and warnings of vulnerabilities to your environment and sign up for alerts from cve.mitre.org, us-cert.cisa.gov, and Cisco Talos to help stay ahead of attackers.

Medical Systems
The Linux operating system has become one of the main operating systems for embedded medical devices. Certain real-time operating systems (RTOSs) such as the Nucleus RTOS from Mentor can be acquired pre-certified, as can other embedded software components from a number of vendors for medical devices. Linux is generally handled using a concept from IEC 62304 called Software of Unknown Provenance (SOUP) for today’s medical devices. Under SOUP guidelines, Linux is considered part of the risk assessment of the overall device, and potential failures of Linux as used in the device must be considered and mitigated if they might cause harm to a patient. This risk assessment must meet the requirements of the FDA’s pre- and post-submission guidance. When it comes to safety, things that could go wrong will impact a patient’s health. For example, you have likely seen movies in which someone becomes able to control a heart device (such as a pacemaker) and cause the death of an enemy. Consider a virus attacking the network controlling the updates to those devices. A manufacturer of insulin pumps did a complete recall due to a MITM replay attack that allowed hackers to replay traffic, essentially doubling someone’s insulin. Medical device users should disable WiFi, Bluetooth, and other outside communications unless absolutely necessary and protect the connection with a strong wireless password and access control rules to limit communications to only vendor-specific IP address/domains.

Vehicles
Most new vehicles are equipped with some sort of connected infotainment system, such as Apple CarPlay, Android Auto, or a similar mobile device–connected standard, allowing for seamless integration with the operator’s smartphone or tablet. In some cases, malware stored on a mobile device can be transferred to the automotive computer when connected via USB. With any group of connected systems, it is possible to subvert one technology to gain access to another. An automobile will use the controller area network (CAN) bus to allow communications between the dozens of control units, including the engine control unit and onscreen display. With self-driving vehicles becoming popular, we can expect a whole new landscape.
There are potential vulnerabilities all over the place if a system isn’t designed well. With so many auto manufacturers and models, the risk level only increases. Many modern vehicles also have an SD card slot, used to update GPS/maps or other automotive software. Infected SD cards could possibly be used by a person with physical access to corrupt the vehicle’s GPS system with the potential for location information being sent via the operator’s mobile device or from the vehicle itself. SD card slots can be disabled on some vehicles, and the settings for the on-board computer can be locked with a passcode. In the case of the CAN bus, the engine control unit is usually air-gapped. Many vehicles now use WiFi and Bluetooth, as well as proprietary technologies. When they are Bluetooth enabled, you should utilize complex Bluetooth passcodes. Also, you should consider whether WiFi and/or Bluetooth are really necessary, and if not, you can disable them within the vehicle’s onboard computer settings. In an automotive CAN bus system, electronic control units (ECUs) can be the engine control unit, airbags, audio system, and so on. A modern car may have up to 70 ECUs, and each of them might have information that needs to be shared with other parts of the network.
Figure 14-3 shows CAN bus communication.
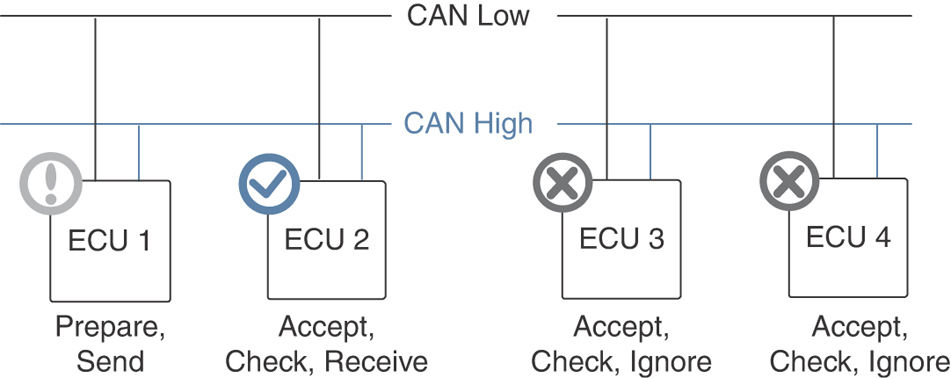
FIGURE 14-3 CAN Bus Communication
The CAN bus system enables each ECU to communicate with all other ECUs—without complex dedicated wiring. The CAN bus system consists of only two wires. An ECU can send sensor data information via the CAN bus by broadcast. The broadcasted data is accepted by all other ECUs on the CAN network, and each ECU checks the data and determines whether to receive or ignore it.
Note
The CAN bus is simple and low cost, fully centralized, efficient, and extremely robust.

Aircraft
Because of the high safety and dependability requirements for aircraft systems, regulations are very strict. Software (DO-178B), hardware (DO-254), and network (AFDX) design are all standardized. DO-178B is the primary document by which the Federal Aviation Administration (FAA) approves all commercial software-based aerospace systems. The FAA introduced AC20-171 to clarify and provide guidance to DO-178B. DO-254/ED-80 is the well-established software standard counterpart for DO-178C that contains both hardware and software, where both are critical to safe operations of an aircraft.
Note
For more information, see www.faa.gov/aircraft/air_cert/design_approvals/air_software/media/differences_tool.pdf.
The FAA regulates all aircraft; therefore, software is a critical component of all aircraft. Recently, software glitches from a major manufacturer caused two plane crashes and the deaths of 346 people.
The autopilot is a system that serves to reduce the workload of the human pilot. Sensors produce a signal according to the direction the aircraft is flying. The control system compares this information with the desired direction. If there is a difference, the autopilot tries to correct the present situation by controlling the actuator. In the more advanced, three-axis systems, more signals are used than in the one-axis system. The control system controls both the desired orientation of the plane and the desired course of the aircraft (in direction and altitude). In that case, a small deflection from the balanced situation causes the aircraft to become unstable and uncontrollable; for example, if an attacker makes a minor trim adjustment in the balance, the pilot could be unaware of the issue, potentially drifting into another plane on descent.
There is a long list of aerospace application-embedded systems, and the list is continually getting longer. Some aircraft have embedded systems at work from tip to tail, whereas others use embedded systems in very specific ways. Embedded systems are designed in a ruggedized manner to withstand extreme conditions without any kind of loss of function. Some embedded systems perform critical functions that are responsible for passenger and operator safety. Commercial airliners provide a good example of embedded systems being used for in-flight entertainment systems, temperature control, speed control, flight management systems, flight data recorders, engine control, and phone calls, to name just a few.
The increased use of some new types of cockpit communications, including controller-pilot data link communications (CPDLC), means the cockpit is at a higher risk of hacking or interference than ever before. CPDLC enhances air traffic control (ATC) surveillance and has some intervention capability. It also plays an instrumental role in reducing mid-air collision risk, while also decreasing voice traffic on radio frequencies. Airlines have taken some steps to reduce the exposure of these systems to prying eyes, including nontransmission of the tail number or aircraft identification information, and isolation of infotainment and other critical systems. With the help of policies and education programs for all flight personnel, they can reduce the social engineering risk.

Smart Meters
A smart grid is an electrical distribution system that includes a variety of operational and energy measuring devices that provide up-to-the-minute consumption, generation, and operations data to control centers. Included as part of the smart grid are smart and advanced meters. Smart meters enable control centers to view, manage, regulate, and turn down power if an issue occurs on the larger power grid and provide additional power if it is not available. Californians have seen these used for years in rolling outages. SCADA systems usually provide a back end for what smart meters are talking to; these systems collect and manage data.
In the past, attackers have been able to manipulate measured energy consumption, cause destabilization in sections of the grid, and obtain private data related to consumption usage of customers. In 2015, hackers launched an attack on the Ukraine power grid using Crash Override malware that took down an entire city for days. Smart meters are getting smarter, however. Newer versions of these embedded devices now have the capability to detect anomalies and warn of parameter changes. Even after these capabilities are widely deployed, these systems must use layered security. Utility companies have begun isolating the metering systems from their corporate networks by setting up firewalled networks, separate control system networks, and restricted access to ensure protection and privacy. Meter manufacturers need to be able to provide the right connectivity for their meters, according to strict service-level agreements (SLAs), and by ensuring security is top priority.
Figure 14-4 shows a smart meter.

FIGURE 14-4 Smart Meter

Voice over IP (VoIP)
Voice over Internet Protocol (VoIP) is a process for sending audio signals, primarily voice, over a data network, such as the Internet. The audio is converted into a digital signal and compressed to reduce data throughput requirements. Then it’s converted into packets and streamed across the network. At the receiving end, the data is decompressed and converted back to an audio signal.
There are a number of advantages to using VoIP instead of analog transmission, with the main one being that you do not need dedicated analog cables to carry the signal. In many situations, an existing data network, wired or wireless, can be used for VoIP. Routing the signals to different destinations is also much easier because it’s just a matter of changing the destination address instead of physically switching the analog circuit. Because the signals are converted from analog to digital, maintaining good audio quality is easier, even in harsh industrial environments.
VoIP communications typically occur between two endpoints. Data packets can be sent directly between them and may not need an intermediary server during a conversation. In many industrial applications, the required endpoints are known and can be programmed directly into the systems. Phones are now embedded small computers that have features and capabilities like showing video, directories of users, and ticker-type data. To secure these systems, you can configure phones to connect to only specific server IP addresses, whether onsite or in the cloud. If you are hosting a call management system (CMS) on-premises, you should firewall it off from the rest of your network and allow communication only on specific UDP/TCP ports. Securing VoIP systems starts with segmenting voice traffic to dedicated VLANs and includes the following preventive measures:
Deploy firewalls and intrusion prevention systems (IPSs) to monitor and filter authorized and unauthorized VoIP traffic, as well as track unusual voice activities on all voice traffic networks.
Use VPNs for remote phones, especially when HTTPS/SRTP is not available.
Enable encryption SRTP for all VoIP traffic to block eavesdroppers with sniffers and traffic monitoring tools.
Encrypt signaling at the gateway to your provider with Session Initiation Protocol (SIP) over Transport Layer Security (TLS).
Lock voice servers physically and logically for administration.
Centralize administration, use domain restrictions, and enable two-factor authentication for administrative access.
Regularly install OS updates.
Enforce strict security policies with users.
Limit software updates/loading on phones to administrators only.
Figure 14-5 shows a VoIP device being used through the Internet.

FIGURE 14-5 VoIP on a Network
Heating, Ventilation, and Air Conditioning (HVAC)
Heating, ventilation, and air conditioning (HVAC) is important for server rooms, data centers, and other technology-oriented areas of your building. Servers run hot; their CPUs can make the temperature inside the case skyrocket. This heat needs to be dissipated and exhausted outside the case. All the heat from servers and other networking equipment is enough to make your servers fail.

The controls for data center HVAC systems should be within the server room or network operation center and be protected by a key code. This way, only authorized IT personnel (who have access to the room) can change the temperature or humidity outside the SCADA system. These control systems can also be hooked up to the door access system or other monitoring systems to log who made changes and when. Since most servers and other IT equipment use front-to-back heat dissipation, the heat should be exhausted out behind the row.
A heating system is rarely needed in a server room, unless the organization’s building is in the coldest of environments. This is due to the amount of heat that servers give off and the fact that they run 24/7. To help monitor HVAC systems and their power consumption, industrial control systems (ICSs) such as the supervisory control and data acquisition (SCADA) computer-controlled system are used. A SCADA system combines hardware monitoring devices such as PLCs (pressure gauges, electrodes, and remote terminal units that connect to sensors) with software that is run on an administrator’s (or building management employee’s) workstation, allowing the administrator to monitor the HVAC system in real time. There could also be a human-machine interface that displays SCADA animations on a separate screen in a strategic place in the building.
SCADA systems can be vulnerable to viruses (such as Stuxnet) that can be used to access design files. To protect against these issues, the workstations that run the software portion of SCADA should have AV/malware software updated, and any separate physical interfaces, displays, and sensors should be secured.
Your network is only as strong as its weakest link. In the case of one department store chain, for example, an attacker gained access to the HVAC system and used it to pivot into the rest of the network by loading malware on retail point-of-sale (POS) systems to steal credit cards. In this case, approximately 40 million credit cards were collected. The obvious lesson here is that remote access should be limited and handled via VPN, secure token, and least privileged access, and monitored with intrusion detection for usage, changes, anomalies, and issues.

Drones
Embedded computers used in unmanned system applications are often characterized by their low SWaP-C (Size, Weight, Power, and Cost) profiles, small form factor (SFF), and rugged operating ranges, which are vital components for unmanned aerial vehicles (UAVs), autonomous underwater vehicles (AUVs) and remotely operated underwater vehicles (ROVs). Commercial, military drones, home and hobby drones, and professional service drones all use embedded compute platforms. Drone systems rely on dedicated functions assigned to embedded computers that include video compression and streaming for drones, deep learning and neural networks for image classification and object detection in autonomous cars, and processing of sensor-acquired data such as GPS.
The FAA estimates that by 2023 there will be more than 835,000 commercial drones in the United States. As the use of drones for many commercial purposes such as aerial inspections, utility projects, real estate monitoring, and construction activities increases, more and more organizations will consider how to integrate these devices into existing networks and systems. However, these organizations must also consider how to limit the cybersecurity and privacy risks associated with the data collected by the drones.
Drones operate by using software or firmware, and drone operators use computers and mobile devices to run drone applications that control the drones. Drones communicate via wireless connections to ground stations and operators below. Hackers are already exploiting drone software and firmware vulnerabilities to take over drones and gain access to connected systems and networks. Malware is often embedded in drone software and can compromise not only the data collected on drones, but also the systems that the drones, software, or connected devices are linked to. According to Cybersecurity and Infrastructure Security Agency (CISA, www.cisa.gov), you should ensure that devices used for the download and installation of unmanned aircraft system (UAS) software and firmware do not have access to the enterprise network and contain appropriate antivirus software. You also should properly verify and securely conduct all UAS activity on a vendor’s website only and ensure file integrity using hashes. In addition, you should ensure the data link communicating with the drone supports a high encryption algorithm for securing Wi-Fi communication. Also, be sure to use the most secure encryption standards available and use complex keys that are changed regularly.

Multifunction Printers (MFP)
A multifunction printer (MFP)/multifunction device (MFD) all-in-one (AIO) is an office machine that incorporates the functionality of multiple devices in one. The purpose is to have a smaller footprint specialized in document management/distribution/production in a large office setting. A typical MFP may act as a combination of emailer, fax, photocopier, printer, and scanner. MFPs have all of the components a computer has: hard drive, operating system, and network connection, which can be wired or wireless.
MFPs are vulnerable to attacks from your network and can be compromised. Once compromised, an MFP can be used for acquiring information about your network, which an attacker will use to penetrate mission-critical targets, such as servers. Attackers can also use the MFP for spamming, network scanning, and denial-of-service (DoS) attacks like downing a network. Threats can even come in the form of routing all scans from an MFP to an unintended user.
Securing these devices starts with password protecting them; unfortunately, many companies decline to password protect their printers due to the inconvenience it causes to users and administrators. It’s important to remember that any time you send an email, fax, or remote print job through your connected office printer, data transmissions are being sent and received by the equipment. If these transmissions are not encrypted, they can be intercepted by malicious attackers, and therefore, confidential data and sensitive documentation can be stolen or compromised. Before you sell or discard old office printers, it’s vital that all information and data are wiped from the internal storage. Most printers can format internal storage through the administrative control panel.

Real-Time Operating Systems (RTOS)
A real-time operating system (RTOS) is a software component that rapidly switches between tasks, giving the impression that multiple programs are being executed at the same time on a single processing core. In fact, the processing core can execute only one program at any one time, and the RTOS is actually rapidly switching between individual programming threads or tasks to give the impression that multiple programs are executing simultaneously.
An RTOS differs from a typical operating system in that it normally provides a hard real-time response, providing a fast, highly deterministic reaction to external events.
When switching between tasks, the RTOS has to choose the most appropriate task to load next. Several scheduling algorithms are available, including round robin, cooperative, and hybrid scheduling. However, to provide a responsive system, most RTOSs use a preemptive scheduling algorithm; one such RTOS is VxWorks.
Securing the RTOS starts with minimizing the attack surface by turning off features, services, and access that are not necessary. You should assume external systems are insecure. Do not make assumptions about what other devices the system is connected to. It is safer to assume that external devices are insecure and then approach securing them from this perspective.

Surveillance Systems
In the last few years, the deployment and use of video surveillance systems have increased to meet commercial needs. Uses include the industrial control industry, environmental monitoring, warehouses, facility controls, and more. These systems have contributed significantly to the reduction of crimes and the preservation of property and an increase in safety.
Far from the days of CCTV, where cameras held little to no information and were not connected to a corporate network, advances in digital video mean that connected IP cameras and associated devices on the network are at risk of being hacked and used as pivot devices. The importance of the data captured by video surveillance cameras—and what can be done with it—has led to a new breed of cyber criminals, looking for insights to steal and sell. Updated surveillance systems have many capabilities, one of which is that they can provide object and facial recognition, intrusion detection through motion, and more. Even air-gapped systems are susceptible to attacks; no system is 100 percent immune from hacks. New cyber vulnerabilities are discovered frequently, but whether they pose a critical risk depends on two factors: First is the probability that a vulnerability can be easily exploited; second is the impact that its exploitation could have on the rest of the system.
What happens when you don’t take all the necessary steps but leave your data exposed to an attack? Under the EU’s General Data Protection Regulation (GDPR) rules, you can be fined up to 4 percent of annual global turnover or 20 million Euros, whichever is highest.
GDPR applies also to the data captured by your security surveillance. Under the regulation, you, as network security administrator, should take all appropriate measures to provide the monitored persons with information in a brief, transparent, comprehensible, and easily accessible manner concerning the processing of their data by the camera system. The IP surveillance industry recommends you first change default usernames and passwords on all cameras and connected devices. You also should utilize the strongest encryption methods available on the devices and consider firewalling the network off from your corporate network.

System on a Chip (SoC)
A system on a chip (SoC) is essentially an integrated circuit or an IC that takes a single platform and integrates an entire electronic or computer system onto it. It is, exactly as its name suggests, an entire system on a single chip. The components that an SoC generally looks to incorporate within itself include a central processing unit, input and output ports, internal memory, as well as analog input and output blocks, among other things. Depending on the kind of system that has been reduced to the size of a chip, it can perform a variety of functions, including signal processing, wireless communication, artificial intelligence (AI), and more. Another way of looking at an SoC is to consider the size and capabilities of the Raspberry Pi covered earlier in this chapter, all of the functionality built into a small platform.
One of the main motivators behind the creation of systems on a chip is the fact that moving into the future, the primary goal is to reduce energy waste, save on spending costs, and reduce the space occupied by large systems. With an SoC, you can achieve all of those goals as you essentially shrink down what is normally a multichip design onto a single processor, and one that uses much less power than previous generations. SOCs have made it possible for the creation of an amazing number of portable devices that you can conveniently carry anywhere and everywhere with you without ever having to compromise on the capability and functionality of the gadgets. As such, SoCs are frequently used in systems pertaining to the Internet of Things, embedded systems, as well as cars and many more. They are used in most, if not all, portable tech such as smartphones, cameras, tablets, and other small capable wireless technologies.
Your smartphone is an example of how a system on chip works. You use your cell phone not only to make and receive calls; you also use it to browse the Internet, play games, view videos, listen to audio, take photos, and send text messages. None of this would be possible without having multiple components combined into one, such as a graphics card, 4G/5G LTE support, wireless connections, GPS, and many other elements.
An SoC allows you to take all of these components, put them on a single chip, shrink it down to a size that can fit in the palm of your hand, and carry it around as a living component in your phone. Security on these devices has improved over the last few years and is expected to continue to innovate. Until then, many of these devices that use SoC have security concerns and capabilities, as previously discussed. To secure a SOC-based device, enable password protection and encryption, utilize complex nonpatterned upper/lower/numeric/special character passwords, and require the devices to wipe themselves after a certain number of incorrect entries.

Communication Considerations
Nearly every IoT and embedded system has some form of communication, whether it uses Bluetooth Low Energy (BLE), Wi-Fi, Zigbee, 3G, 4G LTE, or even the latest 5G. These devices are created to communicate with the outside world. This capability extends your corporate and home perimeter network to virtually an unlimited scope.
5G
Many countries have been involved in the race toward realizing 5G networks. 5G, or fifth-generation, is an advanced wireless network technology developed based on the 802.11ac IEEE wireless standard. It will replace its predecessor, the fourth-generation 4G LTE network, and is expected to increase the data transmission and communication by over three times. Industry experts agree that 5G will offer unlimited potential toward enhancing human life. It is considered to be a key enabler of developing more reliable and fast connections to smartphones and all other smart devices. Following are some of the key advantages of the network:
Expanded communication capabilities, thus increasing the capacity to connect more people and devices
A lower latency of 1 ms, which will enable users to encounter fewer lags and delays when attempting to access data through the network
Higher rates of data, which can range between 1 and 10 Gbps, thus enabling users to download and game quickly
5G device development is still ongoing as most organizations strive to ensure their IoT devices are 5G-ready. It works alongside the existing 4G and 3G technologies to help drive an unprecedented increase in IoT innovations. It provides the platform required to process vast data amounts to help realize a more connected and smarter world. To mention just a few applications, 5G is and will continue to connect everything, including surveillance, smart cities, and autonomous vehicles, and it can even enable a surgeon to operate on a patient in a different country in real time.
As you would expect, 5G networks also raise considerable concerns with regard to cybersecurity. 5G requires a conversion of most software-related networks; implementing future upgrades will be like installing new updates to a smartphone or computer program. This will breed numerous cyber vulnerabilities, so security professionals will have to contend with retooling tools and procedures to secure this essential network in the 21st century. From self-driving vehicles, IoT, AI, and machine learning (ML) to health care with high speeds and always-connected devices, attackers have a new playground. Securing 5G devices starts with the same familiar advice: You should disable services that are not required and configure devices with zero trust (per NIST Special Publication 800-207).
One major 5G security feature is international mobile subscriber identity (IMSI) encryption. All user data passing through 5G networks is confidentiality protected and integrity protected hop by hop. On end devices, you should ensure you use strong passwords. To help reduce your devices’ exposure, be sure to disable discovery-based protocols and settings. After devices are set up and configured, disable all discovery capabilities, and disable services that are not necessary.
NarrowBand
NarrowBand-Internet of Things (NB-IoT) standards are based on low-power wide-area (LPWA) technology developed to enable a wide range of new IoT devices and services. NB-IoT significantly improves the power consumption of user devices, system capacity, and spectrum efficiency, especially in deep coverage. NB-IoT low-power consumption extends battery life to more than 10 years, which can be supported for a wide range of use cases. New physical layer signals and channels are designed to meet the demanding requirement of extended coverage (rural and deep indoors) and ultra-low device complexity. Initial costs of the NB-IoT modules are comparable to GSM/GPRS. The underlying technology is, however, much simpler, and its cost is expected to decrease rapidly as demand increases. Supported by all major mobile carriers, along with chipset and module manufacturers, NB-IoT can coexist with 2G, 3G, 4G, and 5G mobile networks. It also benefits from all the security and privacy features of mobile networks, such as support for user identity confidentiality, entity authentication, confidentiality, data integrity, and mobile equipment identification.
Baseband Radio
Baseband radio refers to the original frequency range of a transmission signal before it is modulated; it can also refer to the type of data transmission in which analog data is sent over a single non-multiplex channel. Whereas a baseband unit (BBU) processes baseband in telco systems, in a cellular phone system, a cell site has a digital signal processor (DSP) to process and forward voice signals to a mobile unit. Telecommunication networks, as we know them now, consist of four distinct parts:
A radio access network (RAN)
A core network
A transport network
An interconnect network
These networks carry three distinct traffic types, commonly referred to as planes. The control plane carries the signaling traffic, the user plane carries the user data, which is the content of communications, and the management plane carries the administrative traffic. The administrative traffic contains configuration and control commands for the RAN and core functions. Network security is critical to these planes because all three of them are prone to unique and diverse types of threats. There are serious issues in pre-5G baseband, including the ability to remotely turn on a microphone and listen in, send all calls to voicemail, remotely execute code, and crash the device. It’s now trivial to set up a fake base station and have phones connect to exploit. Users should ensure they only load known signed/good applications, that their phones have the SIM chip encrypted/password protected, that they allow updates to the operating system, and that they immediately report any issues to their providers.
5G and the rapidly evolving associated technologies in the market put new security demands on telecommunication networks compared to previous mobile generations. The separation of RAN and core was critical to the evolution of 5G networks because gNBs, also known as 5G base stations, terminate the encryption of user data, except where it was previously encrypted and is outside the controls of a 5G operator’s network. These capabilities allow for the enhanced security mechanisms of 5G, including the use of mutual authentication—confirming sender and receiver have an established trust and the end-to-end relationship is secure. The mandating of encryption of inter/intra-network traffic and enhanced subscriber identity protection provide increased security measures.
Subscriber Identity Module (SIM) Cards
A subscriber identity module (SIM), widely known as a SIM card, is an integrated circuit that is intended to securely store the IMSI number and its related key, which are used to identify and authenticate subscribers on mobile telephony devices like mobile phones and computers. SIM cards (see Figure 14-6) can also be used in satellite phones, smart watches, computers, or cameras. SIM cards are transferable between different mobile devices. A SIM card contains a unique serial number (ICCID), IMSI number, security authentication and ciphering information, temporary information related to the local network, a list of the services the user has access to, and two passwords—a personal identification number (PIN) for ordinary use and a personal unblocking key (PUK) for PIN unlocking. We have seen an increase in SIM jacking/swapping; that’s where someone convinces an employee of a telco to move a legitimate user’s IMSI number to a new SIM card for the attacker, and the attacker then uses this access to reset passwords and perform account takeovers.

FIGURE 14-6 SIM Card
Security for SIM cards includes using built-in capabilities and setting a SIM card lock; moving away from SMS 2FA codes and using an application instead; and logging in to the carrier’s website and setting up a PIN and security question. In addition, certain carriers allow you to “port freeze” your number.
Zigbee
Zigbee creates flexibility for developers and end users while delivering stellar interoperability. Created on the IEEE’s 802.15.4 standard, using the 2.4-GHz band and a self-healing true mesh network, the technology defined by the Zigbee specification is intended to be simpler and less expensive than other wireless personal area networks (WPANs), such as Bluetooth or more general wireless networking such as WiFi. Zigbee is commonly implemented in wireless light switches, home energy monitors, traffic management systems, and other industrial equipment that requires short-range low-rate wireless data transfer. Its low power consumption limits transmission distances to 10–100 meters line-of-sight, depending on power output and environmental characteristics. Zigbee devices can transmit data over long distances by passing data through a mesh network of intermediate devices to reach more distant ones. Zigbee is typically used in low data rate applications that require long battery life and secure networking. Zigbee networks are secured by 128-bit symmetric encryption keys. And Zigbee has a defined rate of 250 kbps, best suited for intermittent data transmissions from a sensor or input device.

Embedded System Constraints
Many embedded systems have substantial design constraints over desktop computing applications. The combination of cost pressure, long lifecycle, real-time requirements, reliability requirements, and design culture nonstandards can make it difficult to be successful applying traditional computer design methodologies and tools to embedded applications. Embedded systems in many cases must be optimized for lifecycle and business-driven factors rather than for security and maximum computing throughput. Knowing the strengths and weaknesses of current approaches can set expectations appropriately, identify risk areas, and suggest ways in which to build and meet industrial needs.
Power
Embedded systems (ESs) are typically designed for a specific purpose or task, and are optimized to meet certain constraints, performance, timing, power, and cost. Power consumption is one of the main design constraints for embedded electronic systems, such as wireless sensors, compute systems, and controller devices. Embedded systems also need to be concerned about the power dissipation ion when executing software instructions; a designer must balance the power consumption with features and capabilities. Stronger encryption levels will execute more CPU cycles, drawing more power. Extensive software instructions also consume more power. An attacker can simply cause a loop instruction somewhere on the system and cause the system to consume all power and shut down or crash. When deploying these devices, you should consider securing power sources and ensuring adequate power during the highest utilization periods.
Compute
Many embedded computers are physically located within some larger component. Therefore, their form factor may be dictated by form factors existing in pre-electronic versions or having to fit into interstices among mechanical components. In transportation and portable systems, weight may be critical for fuel economy or human endurance. For example, a mission-critical system has much more stringent size and weight requirements than others because of its use in a flight vehicle.
Network
A computer is often embedded to interact with the environment for the purpose of monitoring and controlling external devices. To do this, analog inputs and outputs must be transformed to and from digital signal levels. Also note that significant current loads may need to be switched to operate motors and actuators, all these requirements can lead to the need for a larger computer. In some systems, smart sensors and actuators that contain their own analog interfaces, power switches, and small CPUs are often used to offload interface hardware from the central embedded computer. This brings the additional advantage of reducing the amount of system wiring and number of connector contacts by employing an embedded network rather than a bundle of analog wires.
Crypto
One of the first steps in building a secure embedded system is to see whether cryptography is actually needed. Cryptography is an important part of securing applications, but it is not a security panacea, nor is it always necessary for building a secure system. The constraints on cryptography in building secure embedded systems hardware and software have to do with the amount of code required to implement a secure algorithm and the processing power required to crunch the number. Also public key infrastructure (PKI) and certificates require space to store the certificates and require CPU cycles to perform operations. The limits of the platform need to be tested to ensure full compliance.
Inability to Patch
Patches for post-release bugs in OS software have shown that nearly 25 percent of all fixes are incorrect and directly impact the end user. And if that’s not bad enough, 40 percent of these faulty fixes resulted in crashes, hangs, data corruption, or additional security problems. Patches don’t always solve the security issues they were designed to address. The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) saw a 60 percent failure rate in patches fixing the reported vulnerability in control system products. Even good security patches can cause issues because most patches require shutting down and restarting the manufacturing process. Some can also break or remove functionality previously relied on by the control system.
Authentication
Similar to cryptology implementations, which start with limits of embedded system CPU, memory, and flash/storage components, the impact of certain authentication types must be considered. Authentication, digital signatures, and encryption are generally based on a set of keys and algorithms for transforming digital data, called clear text, into an encrypted form and back again. Digital signatures are based on the encryption of a checksum of the data being signed. Secure authentication is accomplished using digital signatures, and all of these functions take a toll on memory and CPU.
Range
Embedded systems are typically constrained in terms of three system performance criteria: space, time, and energy. Performance requirements are directly translated into constraints imposed on the system’s resources, such as code size, execution time, and energy consumption. These resource constraints conflict with each other in a complex manner, making it difficult for a system developer to apply a well-defined design methodology in developing a real-time embedded system. The smaller the device, the more direct relationship to the size of the transmitter, thereby dictating the frequency and distance range the device supports. Obviously, the smaller the transmitter, the shorter the distance.
Cost
The emergence of multimedia and wireless applications as growth leaders has created an increased demand for embedded systems. Applications range from digital cellular phones to high-performance avionics systems. Along with the increased market share of these products comes an increase in system complexity and cost. These systems consist of programmable-multiprocessor arrays to meet performance requirements. Time-to-market and lifecycle costs are key factors in the success of these products in the competitive electronics marketplace. These costs have a dominant influence on the design of embedded microelectronic systems. In addition, these systems must meet rigid form factors, such as size, power, and weight constraints, which further complicate the design task. For designers of high-end embedded microsystems or large-volume consumer products, rapidly prototyping cost-effective implementations that meet stringent performance, functional, timing, and physical requirements is a formidable challenge.
Implied Trust
A trusted computing platform is a computing infrastructure that provides a variety of hardware-supported and software security functions. Although trust, trusted, and trustworthiness are never defined, it is hoped that trusted computing platforms and resulting improvements in the security of computing infrastructure and applications will enable trustworthy applications and systems. Implied trust is where a specific section of code or a component depends on the previous code or component for its security, thereby making it reliant on that code to have appropriately performed the security measures required to make the entire system safe. When it comes to cybersecurity, implied trust should be used sparingly as it relates to embedded systems. There are constraints that limit what full-fledged trust can be implemented, let alone what can be operationally expedient; therefore, certain aspects of the design rely on an implied trust, even if that is “assuming” the wireless network will be secure so that there is no need to protect plaintext protocols.
Chapter Review Activities
Use the features in this section to study and review the topics in this chapter.
Review Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 14-2 lists a reference of these key topics and the page number on which each is found.

Table 14-2 Key Topics for Chapter 14
Key Topic Element |
Description |
Page Number |
|---|---|---|
List |
Embedded Systems |
339 |
Section |
Supervisory Control and Data Acquisition (SCADA)/Industrial Control Systems (ICS) |
341 |
Paragraph and list |
Internet of Things (IoT) |
344 |
Section |
Medical Systems |
347 |
Section |
Vehicles |
347 |
Section |
Aircraft |
348 |
Section |
Smart Meters |
350 |
Section |
Voice over IP (VoIP) |
351 |
Paragraph |
Heating, Ventilation, and Air Conditioning (HVAC) |
352 |
Section |
Drones |
353 |
Section |
Multifunction Printers (MFP) |
354 |
Section |
Real-Time Operating Systems (RTOS) |
355 |
Section |
Surveillance Systems |
355 |
Section |
System on a Chip (SoC) |
356 |
Section |
Communication Considerations |
357 |
Section |
Embedded System Constraints |
361 |
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Field-Programmable Gate Array (FPGA)
supervisory control and data acquisition (SCADA)
industrial control system (ICS)
Voice over Internet Protocol (VoIP)
heating, ventilation, and air conditioning (HVAC)
real-time operating system (RTOS)
NarrowBand-Internet of Things (NB-IoT)
Review Questions
Answer the following review questions. Check your answers with the answer key in Appendix A.
1. What is an Arduino device?
2. What is the purpose of an FPGA?
3. What systems do the SCADA/ICS control systems actually control in the manufacturing process?
4. Look around your house. What IoT-related devices do you own? What is the number one problem with IoT devices being developed and sold?
5. Today’s vehicles are mostly computerized. Which protocol/system do most vehicles use for ECU to communicate between themselves?
