![]()
CHAPTER SIX
E-NETWORKING
The Backbone of E-Health Care
Joseph Tan, Winnie Cheng
III. E-Networking Requirements
A. E-Consumer Health Informatics
A. E-Network Infrastructure Support
B. Data, Image, and Video Representation and Storage
V. E-Networking Infrastructures
A. Open Systems Interconnect Model
C. Cellular Versus Satellite Infrastructures
IX. Mobile Health Networks Case: Unconfined Mobile Bluetooth Technology for E-Medical Services
Learning Objectives
- Realize the e-networking requirements for the major classes of e-health applications: e-consumer health informatics, e-clinical care, and biomedical research
- Identify e-networking standards for various components, including e-network infrastructure support, digital data formats and storage, and e-security
- Conceptualize the open systems interconnect model and its significance for e-networking in health care
- Differentiate between ISDN and mobile e-network infrastructures and among various satellite configurations for deploying e-health care applications
- Understand medicolegal considerations in e-networking
Introduction
Traditionally, health care information systems have been deployed to provide rapid administration of patient data to support either mostly clinical or mostly administrative and financial services. These systems are highly autonomous, not designed to share information among administrators and caregivers working from various sites. Naturally, given the autonomous working environments, differing organizational cultures, and distinctive work ethics found in these settings, the information relating to a specific patient is typically captured in widely varying formats, impeding integration of information from different sources. Details of the patient's progress and treatment are often not included with the electronic patient records, even if these records were available, because isolated legacy systems using different coding standards are employed to capture and house that information. As a result, inefficiencies abound, leading to poor coordination and discontinuities in the care process among caregivers.
This lack of integration among legacy systems quickly spirals into unnecessary delays and poor-quality health care. In an emergency, for example, the patient's medical history is often not readily available to assist in diagnosis. Delays in treatment occur when requested copies of diagnostic results or images cannot be delivered quickly to the hospital or clinic. Information collated from the separate legacy systems is often time-consuming to locate, leading to further dissatisfaction with the quality of health care. Patients often complain about having to repeat the same information or, even worse, having to undergo a similar test procedure because results of the previous test were unavailable. Fortunately, rapid advances in computer memory and storage capacity, improved managed care processes, and recent consolidations among health provider organizations and health maintenance organizations into integrated delivery systems have all led to aggressive efforts by care providers to eliminate much of the inefficiency in health data processing and to provide greater accountability for health care services, gradually ushering in a new era of health care delivery, the e-health care era.
With the advent of e-health care, a wide range of technologies can now be applied to provide medical care products and services. In earlier chapters, it was noted that these technologies are the result of new advances in information and communication technologies, including the Internet and other advanced telecommunication and interactive network technology such as videoconferencing and wireless services. The use of e-technologies implies not only the ability to integrate information from many different sources but also the ability to practice medicine across long distances. Accordingly, e-health practices promise rapid access to shared, integrated administrative, financial, and even medical information and expertise regardless of the whereabouts of the patients as well as the caregivers.
Given these advances, the range of e-health care services can vary from on-line appointments to remote surgical procedures, including services directed by surgeons. Remote assessment of patient problems, on-line diagnoses, e-consultations between physicians and specialists, virtual consultations among patients and providers, massive digital data transfer, teleradiological transmissions of X-rays and magnetic resonance imaging archives, and interactive education and training sessions are all examples of emerging e-health care services and e-clinical applications. To understand the needs of the evolving e-health care system, this chapter provides a continuation and integration of the discussions of previous chapters by focusing on e-network infrastructures and configurations. Without e-networking, the backbone of all these emerging e-technological applications, limitations of time, space, location, and facility resources will restrict the provision of up-to-the-minute health care services.
E-networking is the term we will use to refer to the connectivity among various networks and their communication devices, such as servers, routers, and personal computers. Tan and Hanna (1994) argue for a three-tier implementation of e-network connectivity standards for health care applications: physical, systems, and applications connectivity. Physical connectivity has to do with promoting hardware compatibility, effecting teleprocessing, and administering network management. Systems connectivity refers to the use of flexible systems to interconnect platforms, and the concept of an open systems interconnect (OSI) model. Applications connectivity is concerned with software standards, as in the application of eXtensible Markup Language (XML), and user training. Together, these elements of network integration, which we refer to as e-networking, will result in the appropriate design and deployment of functional network infrastructures and configurations to link traditional health care networks and systems. E-networking will accomplish this integration not only by cutting across geographical and organizational boundaries but also by breaking down long-standing barriers to effective and productive exchange of key patient information.
This chapter first examines the e-networking requirements of three major categories of e-health applications: e-consumer health informatics, e-clinical care, and biomedical research. Next, we survey the e-networking standards for different components that support e-health networks and applications. Against this backdrop, we discuss the range of solutions offered by existing e-network technologies and, where applicable, the technical advances needed to solve these problems. We then review e-network infrastructures and configurations that have been tried for some e-health applications, highlighting broadly the issues that challenge the adequacy of these configurations. Equally important to the success of e-network technology are medicolegal infrastructures, which we explore briefly. Finally, we conclude the chapter with a look at the future growth and development of e-networks.
E-Networking Requirements
The evolution of e-health care services demands a wide range of applications with different e-networking requirements. In this chapter, we divide our discussion of e-health applications into three somewhat discrete categories—e-consumer health informatics, e-clinical care, and biomedical research—for the purpose of studying their varying e-networking needs. The e-networking requirements for each of these application categories are analyzed by examining their bandwidth, latency, security, and accessibility needs. Latency refers to the time delay prior to the transfer of data just after an instruction for its transfer has been received or provided (that is, from a storage device).
E-Consumer Health Informatics
E-consumer health informatics is probably the area in which e-health care products and services are most visible. Today, e-health care vendors and providers are recognizing the importance of engaging their clients and patients in order to provide more meaningful and effective e-health care information on products and services. More significantly, there is a global trend toward emphasizing preventive care and endorsing the general concept of self-care by empowering e-consumers with accurate and reliable information and knowledge. Promoting healthy lifestyles through systematic health education and changes in everyday routines and even through transforming current unhealthy behaviors (such as quitting smoking, becoming less sedentary by participating actively in walking and stretching exercises, and paying attention to eating disorders and poor eating habits) has caught on with younger people, who are often also well versed in the use of the Internet and other technologies. The e-consumers of tomorrow want accurate and reliable medical and other health-promoting information. E-consumer health applications include consumer-oriented Web sites, chat sessions, newsgroups, e-mail exchanges with medical experts, wireless and digital broadcasts, and other compilations of on-line resources.
The number of e-consumers searching for health information on the Internet seems to have been steadily increasing over the years. By 1999, just a few years following the initial diffusion of this e-technology into popular use, this number was already estimated to have reached a staggering 30 million at least (National Research Council Committee, 2000). It is believed that e-consumer health informatics will soon become the primary means of providing laypersons and nonprofessionals with health information.
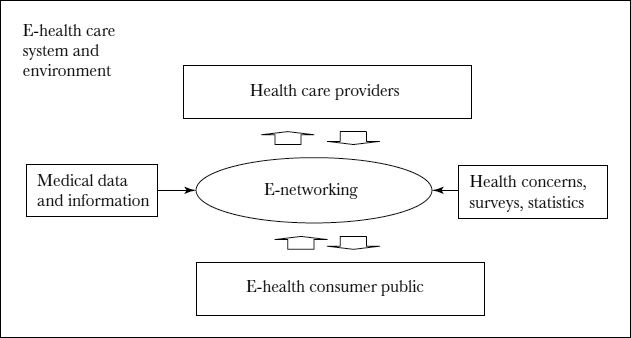
As shown in Figure 6.1, e-consumer health informatics assumes a bidirectional information flow between the health care provider community and the general public. Notwithstanding, many health administrators and providers feel somewhat frustrated and helpless in trying to ensure that the health information and knowledge that e-consumers glean via the Internet or otherwise is authoritative or definitive. For example, e-consumers are constantly faced with uncertainties about the safety and effectiveness of particular health care products and services advertised on the Internet. Perhaps a clearinghouse to validate many such claims is badly needed. More and more private and governmental Internet sites and on-line surveys collect and disseminate demographic, accident, and work injury statistics to help promote preventive health and encourage the growth of e-consumer health informatics. However, such epidemiological data and biostatistics cannot be easily collected without a secured, publicly accessible infrastructure and platform. E-consumers are also demanding that the scientific accuracy of medical information or findings that are presented or released be verifiable and that potential biases be disclosed.
FIGURE 6.1. E-NETWORKING FOR E-CONSUMER INFORMATICS
One approach to e-consumer health informatics is the community health information network (CHIN). Basically, a CHIN may be understood as a regional ring that links health care stakeholders throughout a community (see Chapter Three). Essentially, a CHIN refers to an integrated collection of telecommunication and e-networking capabilities that facilitate communications among patients and clinicians, as well as transfer financial information among multiple providers, payers, employers, pharmacies, and related health care entities, all within a specified geographical region. CHINs are further discussed in Tarn, Wen, and Tan (2001), who also provide several examples of how these networks can improve e-consumer informatics.
The bandwidth required by e-consumer informatics varies depending on the type of information to be transferred and on the number of users who will be accessing the information at any one time. For example, Web sites that provide a database of health risks and pharmaceutical products are usually adequately served by the access network (that is, a base station providing connection to associated networks that eventually lead to information site to be retrieved) capabilities offered by current Internet service providers (ISPs). On the Web server side, the bandwidth demand is driven largely by the volume of requests to be serviced. In most cases, e-consumer health informatics can accommodate interactivity that is characterized by a higher latency, except in such applications as on-line medical training courses where low latency interactivity is desired. While the networking requirements for e-consumer health informatics are not very stringent, architecture improvements are still necessary for the field to advance because of greater rising e-consumer expectations.
Of great importance to e-consumer health applications are issues relating to the accessibility, reliability, security, and legal aspects of e-health computing and networking. Some of these topics will be discussed in other parts of this chapter and this text. Here, we emphasize two general issues that need to be addressed. First, e-consumer health applications should be highly accessible, in order to serve the general public. To this end, the Internet plays a significant role in the dissemination of e-health information. However, with each passing day, the volume of information on the Internet is surpassing the ability of existing search tools. Search capabilities need to be further enhanced to allow the growing number of users to locate more precisely the information they are looking for. Moreover, people who are clearly underserved or disadvantaged due to the “digital divide”—for example, seniors, people living in poverty or in underdeveloped countries, and many others—still lack the knowledge of or training in how to get connected, how to extract relevant information, and how best to interpret the information gathered.
Second, health care policymakers and e-network designers can and should work together to institute mechanisms for providing e-consumers with accurate medical information. For example, policies can and should be established to identify sites that provide erroneous or misleading information. Authentication technologies may be applied to ensure that e-consumers are receiving information from approved sources. Also, e-consumer health applications require on-line anonymity and security because searching for information can reveal e-consumers' identities or health concerns about AIDS, sexual dysfunction, or other illnesses that may carry a public stigma. Appropriate infrastructures must be put in place to allow legitimate users to access accurate health information anonymously.
E-Clinical Care
E-clinical care involves the use of virtual clinics and medical services across distances. Virtual clinics are extending health care and clinical care services to a more geographically dispersed population than is possible with traditional care, including people in rural areas and in restricted places such as military bases, war zones, and planes and ships. In such instances, e-health care providers and e-patients typically do not meet physically; hence, medical specialists often interact with these patients via teleconsultation.
The success of e-clinical care today depends on the integration of four key application domains:
- Teleconsultation (or e-consultation)
- Digital medical imaging
- Remote patient monitoring
- Electronic health records
Teleconsultation (e-consultation) is a cost-effective alternative to staffing multiple clinics with the same set of specialists (Elsner, Kottkamp, and Hindricks, 2000). This e-technology allows rural areas, underserved urban areas, prisons, and other areas to receive medical services that may otherwise be unavailable (Kontaxakis, Walter, and Sakas, 2000). The bandwidth requirement for successful e-consultation varies depending on the types of data that are being transferred.
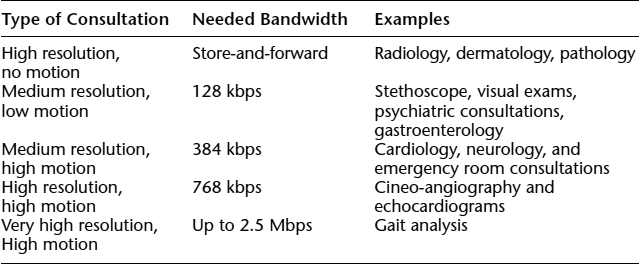
Table 6.1 specifies the bandwidth demands for five common categories of e-consultation interactions. As shown, the bandwidth demands for e-consultation can be quite significant for certain application categories. Current access networks for the Internet are based on an asymmetric upstream-downstream model in that downstream is much faster than upstream (Prior, 1996) and are not yet cost-effective enough to provide enough bandwidth to satisfy the demands of e-consultations. Latency guarantees are also necessary for e-consultation because this is a real-time, interactive application. As a result, dedicated networks are often needed.
Table 6.1. NOMINAL BANDWIDTH REQUIREMENTS FOR DIFFERENT TELEMEDICINE APPLICATIONS
Source: David Balch, East Carolina University, personal communication, Feb. 2, 1999.
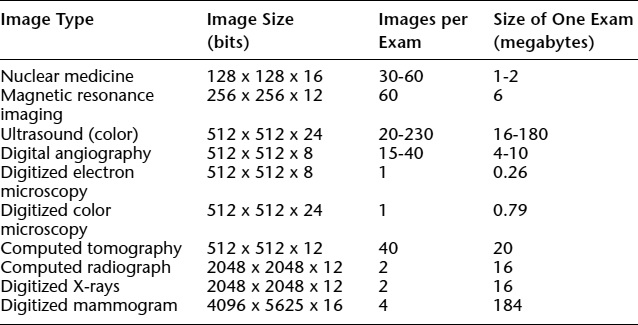
Another aspect of e-clinical care that is closely related to e-consultation is sharing digital medical imaging information. This capability enables e-care providers to transfer medical information among specialists for interpretation as needed (Zhang and others, 2000). An on-line repository for medical images is commonly referred to as a picture archiving and communications system (PACS). The size of medical images varies: uncompressed radiographic images may range from several kilobytes to tens of megabytes. Table 6.2 summarizes the amount of medical imaging information that is typically transferred for the different image types. Up to hundreds of megabytes may be needed—for example, to store nuclear medicine images.
The bandwidth required to support digital image transfer applications depends on two factors: the amount of time in which the image must be transmitted and the degree of compression that can be employed. In many teleradiological applications, medical images may be sent as e-mail attachments with an interpretation or diagnosis turnaround time of one to two days. However, a busy mammography center may perform eighty to one hundred examinations per day. To transmit all of the results would require an average sustained throughput of approximately 1 megabyte per second without compression and a throughput of almost 100 kilobytes per second with 10:1 compression. Of course, any compression used must not degrade the image to the extent of possibly impairing interpretation. There are two types of compressions: lossless and lossy. Lossless compression emphasizes a coding technique that captures all information in a smaller number of bits. It allows a file size reduction by a factor of three or four. Lossy compression can typically provide a reduction by a factor of between ten and twenty without sacrificing diagnostic quality (Pradhan, 2001). Lossy compression uses a number of compression techniques that allow loss of information, for example scalar and vector quarantization, which are outside the scope of this discussion (for more info see Case section in latter part of this chapter). Further compression can be employed, depending on the application domain and the intended users. For example, a specialist reviewing a radiograph requires much higher resolution than a primary care physician looking at the same file. For some applications, such as mammography, how much the images can be compressed without significantly impairing their interpretation is a matter of some controversy. Techniques such as the use of intelligent systems to preprocess medical images may further reduce the bandwidth requirements. In general, medical imaging can benefit from faster e-networks with shorter turnaround time and greater access to the repositories.
TABLE 6.2. NOMINAL FILE SIZES OF COMMON MEDICAL IMAGES
Source: Huang, 1999.
A third domain of e-clinical care is remote patient monitoring. Remote patient monitoring provides a different interaction between the e-care provider and the patient. During an e-consultation session, it may be necessary for the provider to take vital signs and other measurements. In addition, some patients may require ongoing treatment and monitoring. Deployment of remote monitoring requires specific network infrastructure to be in place. Home networking is leading the way in the area of remote patient monitoring; for example, devices may be interconnected in a home using a local area network, with a central gateway governing the information access, processing, and control of these devices. Advances in micro-electromechanical systems are also enabling the control of microscopic mechanical devices such as pacemakers and sugar-level monitors via electrical signals. The amount of information communicated is usually small so that it is unlikely that high-bandwidth connections will be required. However, the aggregation of these devices may require careful management of e-network resources. In other words, latency and bandwidth control may be critical for some applications—for example, monitoring many patients simultaneously. The e-care provider should be able to handle an aggregate load of information from different remote devices and respond to critical situations in a timely manner. This type of monitoring also requires an e-network of high reliability.
Security and network availability are crucial to the success of remote patient monitoring. Data must not be altered while in transit through the network. In addition, the privacy of patient information must be protected. E-network downtime must also be within reasonable bounds and be as short as possible. The accessibility requirements for remote monitoring are analogous to those of emergency phone line support. Imagine the difficulties and confusions that accessibility problems would cause in dealing with patients undergoing e-clinical care. What if a particular instance of e-clinical care were a result of a bioterrorist attack that had caused the treatment location to be physically inaccessible to caregivers because of road closures and other transportation barriers?
Finally, electronic health records (EHRs) represent a critical component of e-clinical care. EHRs consist of a centralized on-line repository that enables authorized access to medical records (see Chapter Four). EHRs can house comprehensive records of patient information gathered from different sources over an extended period of time. Bandwidth demands for these on-line patient records vary depending on the type and nature of information stored. Web-based storage of medical records can provide needed accessibility; however, security measures should be implemented to protect patient privacy and guard against any inappropriate disclosure of highly confidential and sensitive data.
Biomedical Research
An important aspect of any e-health care system is preventing and controlling the spread of disease, injury, and disability. Chapter Five shows how Internet-based information exchange allows the timely dissemination of information and collection of data so that public health concerns and trends can be analyzed. Information and statistics are compiled on individual health, personal risk factors, and medical treatments. Data on potential sources of diseases and injury in the environment and resources that can be used to take effective action against such threats can be made available to the public, thus providing better prevention and control of epidemics and other disease outbreaks.
The Internet has demonstrated its power in promoting collaborative research. With rapid advances in communications, the biomedical field can benefit from the ability to quickly disseminate information. Not only can researchers share large databases, but they can also participate in linked simulations to exploit the power of distributed computing. Improvements in e-networking technologies will enable remote control of experimental apparatus, virtual reality training, and even remote surgery.
Again, in collecting biostatistics and epidemiological data, e-networks must provide mechanisms to protect patient privacy and confidentiality. Schemes and policies must be in place to ensure anonymity. Accessibility to patient information is also very important, as the information is relevant to the public and the individuals. The bandwidth and latency requirements are less stringent because most of the data transferred will be of manageable size. E-public health information systems should be supported by a network infrastructure that can accommodate a variety of bandwidths, allowing users connected to different networks to access the information.
Biomedical databases will differ from e-public health information databases in size and bandwidth requirements. Some biomedical databases shared among research projects cover DNA sequences, protein sequences, and human genetic diseases. A typical search retrieves a large amount of data; therefore, the demand on bandwidth may be high. To support a distributed computing environment in which linked simulations can occur among various high-end computing nodes, the network must provide enough bandwidth to allow results from one simulation to be fed to another simulation residing elsewhere in the network. Linked simulations impose both high bandwidth and stringent latency requirements on the e-network. However, in many cases, high-end machines are connected through private networks, so these requirements can be met through cost-effective sharing of these expensive computing workstations or servers.
Costly experimental equipment and apparatus such as electron microscopes, DNA sequencing facilities, and nuclear magnetic resonance spectrometers may also be shared. The ability to remotely control experimental equipment opens up resources to a broader research community and enables collaboration on the analysis of experimental results. A researcher from afar may send samples of interest to device operators, then run experiments remotely, specifying the desired magnification, controlling the focus and field of view, and retrieving images as desired. The researcher may also request another authorized researcher or expert to examine the image. Trainees can connect to video-streaming servers for on-line training classes or to simulation servers in order to participate in a virtual operation. Advances in robotics coupled with those in networking can bring virtual training as far as the performance of remote surgery in hard-to-reach areas (see Chapter Sixteen).
In most cases, biomedical research applications involve control data that must be transferred reliably and in sequence. The bandwidth requirements of these applications may vary. Because they are interactive applications, they require systems that meet latency specifications in order to be effective. Global accessibility is rarely necessary and in most cases is undesirable. Rather, only authorized researchers can have access to such costly and powerful equipment. Once again, authentication, encryption, and other standard security measures that ensure privacy and confidentiality are crucial to success.
E-Networking Standards
Having reviewed the e-networking requirements for major classes of e-health applications, we now move to discussing e-networking standards. More specifically, we will focus on standards that align technical advances in the various e-health component areas to support the development of e-health care applications, including e-network infrastructure support, digital data and image representation and storage, and e-security.
E-Network Infrastructure Support
E-network infrastructure support is concerned with achieving accessibility, bandwidth, and latency requirements. As we saw earlier, demands on the e-network infrastructure vary for different e-health applications. Low-quality networks may be adequate for some simple applications such as the transmission of on-line clinical reports. At the higher end of the spectrum, complex e-health transactions require sophisticated e-networks; one such application is the transmission of teleradiographic images and exchange of multimedia information for e-consultation and e-clinical services among networks connected via servers.
In real-time interactive e-health applications such as e-consultation, low latency and adequate bandwidth guarantees are required to sustain a session. These applications also demand symmetric link speeds, dictating an equal upstream-downstream data transmission rate that is not common in today's access networks. Medical information may contain high-resolution imaging data that are susceptible to data loss. E-health-related applications may involve critical functions that require fast and reliable information delivery. Hence, the field of e-networking faces many challenges. Recent deployments of faster networks that offer increased bandwidth have provided better resolution of images and some relief from network congestion. The predominant Internet Protocol (IP) networks currently operate on a best-effort assumption—an assumption that the best route will be traversed to satisfy requests; however, the need for quality of service (QoS) standards in the future is evident.
In recent years, considerable attention has been given to the need for QoS standards in e-networking. QoS parameters are used to distinguish traffic with different transfer requirements. For example, the audio stream of an e-consultation session requires much lower latency than e-mail traffic that may be competing for bandwidth simultaneously on a network. The transmission control protocol (TCP), which was developed a decade ago to ensure reliability in data transfer, has become the de facto standard, but it has many undesirable characteristics. First, it attempts to eliminate network congestion by pushing network utilization to its maximum until a retransmission caused by lack of capacity triggers it to backtrack. Moreover, the latency caused by retransmission may be unacceptable for real-time applications. Applications in e-health may also require the frequent exchange of multimedia information. Because multimedia traffic is likely to be carried over the same IP-based network as data traffic that typically uses TCP, this poses significant challenges. Unlike data traffic, multimedia traffic requires a minimum bandwidth to function. In order to guarantee multimedia services, the aggressiveness of TCP applications must be controlled to reserve at least the minimum bandwidth for multimedia traffic. Therefore, it is essential to employ e-networks with guaranteed QoS for more complex e-health applications in domains such as specialty e-consultations, real-time e-clinical care, and biomedical research such as a real-time, on-line clinical trial network for new drugs being tested on a global scale.
Two types of standardized QoS schemes have been discussed in the literature:
- Integrated services (IntServ)
- Differentiated services (DiffServ)
In addition to basic best-effort service, the IntServ model proposes two service classes—one that guarantees service and one that guarantees controlled load service, that is, it will be able to service all of the requests over time (Wachter, 2000). The precedence bits of the type of service (ToS) field in the IP packet header determine the packets relating to each service class (Skolnick, 1998). The IntServ model requires a telecommunications signaling protocol such as the Resource ReSerVation Protocol (RSVP). RSVP is therefore a policy-based network scheme that reserves paths on the Internet for transmitting video and other high-bandwidth messages. The IntServ model is characterized by the ability to reserve resource per-flow (in other words, a scheme to denote network resource reserved in a specific transmission) and, hence, provides end-to-end QoS guarantees. However, per-flow information must be stored and processed at each intermediate node in a network. This places high processing requirements on routers and inhibits scalability.
The DiffServ model alleviates the scalability problems encountered by IntServ. It aims to shift the processing to the edge of the networks by classifying and conditioning traffic at the boundaries before it enters the DiffServ domain (Woodward, Istepanian, and Richards, 2001). Core routers within the DiffServ domain can then provide fast switching. DiffServ supports a wider range of classes by replacing the To S field in the IP header with a new field, the differentiated services (DS) field. Per-class (that is, a scheme to specify the class of network resource to be reserved and used in a transmission) rather than per-flow information is then processed. A service-level agreement (SLA) may also need to be specified between the user and the network provider. SLAs may be negotiated statically or dynamically through the use of a signaling protocol such as RSVP (Clarke, Fragos, Jones, and Lioupis, 2000). In the absence of significant overprovisioning and explicit signaling to reserve resources, research has shown that simple DiffServ mechanisms can provide a high probability of meeting users' QoS requests for point-to-point communications. However, deployment of DiffServ is difficult over networks owned by different ISPs. Thus, end-to-end QoS will remain a challenge until new standards can be developed and agreed on by the various ISPs.
A QoS solution that can harness the advantages of both IntServ and DiffServ, overcoming scalability issues while providing end-to-end QoS guarantees is the Internet Engineering Task Force's (IETF's) Integrated Services over Specific Link Layers, which combines the end-to-end service definitions and signaling of IntServ with the scalable queuing and classification techniques of DiffServ. Another approach is the use of virtual overlay networks (VONs) (Tyrer, 2000). This technique aims to virtually divide the Internet into isolated networks such that different QoS and security requirements can be serviced independently. Packet flows belonging to different VONs are tagged with flow identifiers. For example, if a hospital creates multiple VONs to serve different applications, each network could connect to different end points and offer different levels of service. Routers would then determine how packets with different flow identifiers should be treated.
When bandwidth of a particular link is fixed, priority is often given to some packets at the expense of others in order to meet QoS demands. Ideally, all users would like their packets routed with the highest priority, but for some applications, average priority may be acceptable, while others may require a minimum guarantee at all times—for example, when transporting health-critical information in remote monitoring applications. Along with technology to support packet routing of different QoS classes, policies are needed to determine the priority of the traffic and hence the class to which each data packet should be assigned. RSVP is a flexible signaling mechanism that can allow some policy-related data to be exchanged. The Common Open Policy Service protocol has been defined to enable routers processing RSVP requests to exchange policy data with policy servers. These servers store policy information, such as types of requests allowed from a certain institution and the preemption priority of certain applications. Policy decisions are complex and require the agreement of the health care community as a whole.
Today, the predominant IP networks operate on a best-effort assumption in which packets are dropped when the network is close to saturation. Many health-related applications have critical functions requiring that information be delivered not only quickly but also reliably. Hence, networking faces many challenges in delivering the infrastructure needed to support these applications. Not surprisingly, despite ongoing research (for example, Tan and Hanna, 1994; Clarke, Fragos, Jones, and Lioupis, 2000), more studies in the area of health e-networks, particularly on data compression techniques for reduced bandwidth requirements, standardized QoS schemes, faster and more acceptable data and image transmission priority schemes, and ISP policy issues are still needed.
Data, Image, and Video Representation and Storage
We now turn to data format standards, particularly some commonly used standards in image and video compression techniques. For example, for the storage of medical information, systems known as picture archiving communication systems (PACS) have been developed to address some of the accessibility issues and e-networking requirements for the exchange of medical imaging data. Essentially, PACS are systems for storage of massive digital images. These systems also support simultaneous access to digital imaging data from various connected terminals, systems, and networks. E-health applications require storage and retrieval of images that can vary from 40 to 300 megabytes in size, with an average expected access time of 2 seconds or less. High compression ratios may cause important details that are crucial for proper diagnosis to be lost; hence, a high bandwidth requirement is often necessary (Sarek, 1997). To overcome these challenges, Stentor Inc. has proposed an innovative approach to lighten the load on e-networks. In this scheme, images are encoded using wavelet transformations (numerical techniques), thereby requiring only small chunks of data of 4 to 32 kilobytes to be exchanged at any one time and eliminating the need for dedicated links to support high bandwidth requirements. Moreover, instead of transmitting an entire medical study in one transfer, users can be presented with several low-resolution images that can then be separately “zoomed” to the image sizes with higher resolution needed at later points.
Other emerging standards for image and video compression have been applied to enhance the integration of multimedia applications with software and networks. The Joint Photographic Experts Group (JPEG) compression standard has been commonly used to compress both gray-scale and photographic-quality color images, but this compression technique is “lossy.” The Moving Pictures Expert Group (MPEG) standards (MPEG-1, MPEG-2, MPEG-4, MPEG-7, and MPEG-21) can transmit different types of frames from a video clip. These techniques essentially compress the video clips into different types of frames, including intrapicture frames (I-frames), predicted frames (P-frames), and bidirectional frames (B-frames). Typically, I-frame is used as a reference for the B-frames and P-frames, which only record changes from the I-frames and thus use the I-frames to fill in the picture.
E-networking data format standards have been established among different e-stakeholders. Among these, Digital Imaging and Communications in Medicine (DICOM) and Health Level Seven (HL7) standards have aimed to specify the various hospital computer system interfaces DICOM provides guidelines on interfacing medical imaging devices, whereas HL7 comprises a set of data models that define data structure and transactions for communicating patient information and other financial and administrative data. HL7 is an organization accredited by the American National Standards Institute that is developing standards for representing and communicating data related to health care. The e-health care environment focuses on e-clinical and e-patient data such as EHRs (see Chapter Four). HL7 specifies a set of data models and transactions that have been adopted as the data interchange standard in many traditional as well as e-health applications. The HL7 data model has been implemented as a message-based format, as a relational data model, and as an object-oriented model. It has been extended to interoperate with eXtensible Markup Language (XML), which is becoming increasingly popular in implementation of e-health applications on the Internet.
The DICOM Standards Committee created a detailed specification that describes a means of formatting and exchanging images and associated information, particularly in a PACS environment for the storage and transmission of digital teleradiological images (DICOM Standards Committee and Working Groups, 1998; Rickards, 1996). DICOM guidelines apply to the operation of the interface used to transfer data in and out of an imaging device. The DICOM guidelines are a widely adopted standard for device interoperability in teleradiology, and it is probably at least partly a result of having such well-defined standards that teleradiology was one of the first forms of telemedicine to receive full reimbursement under Medicare and is among the most widely used forms of e-health services in the United States and worldwide. With standards in place, it can be determined whether an e-physician followed the standard of care.
E-Security
E-health applications frequently involve the exchange of sensitive information and knowledge. E-security opens doors to public acceptance of e-health care services by providing authentication of the identities of authorized users and ensuring patient anonymity in sensitive research, public health, and quality assurance applications. E-security features may be needed to authenticate parties before the exchange of confidential patient information (McDermott and others, 1999).
A common approach to ensuring e-security is the use of encryption technologies, which fall into two broad classes:
- Symmetric private key cryptography
- Asymmetric public key cryptography
Symmetric encryption uses the same key for data encryption and decryption. With this technique, distribution of keys is a major problem because security may be compromised. Thus, in many cases, asymmetric encryption using two different keys (a private key and a public key) is preferred. When data and knowledge elements are encrypted using the private key, they can only be decrypted using the public key, and elements encrypted with the public key can only be decrypted with the private key. Authentication is accomplished when the sender encrypts a message with its private key and the recipient decrypts it by using the sender's public key. Privacy is protected in the reverse scenario, in which the sender encrypts the message with the recipient's public key and the recipient decrypts it with its private key. This method permits “strangers” to share information and knowledge, with both authentication and privacy. It is especially useful, for example, when two unaffiliated organizational entities need to share patient records.
Asymmetric encryption typically requires more bits than symmetric encryption in order to achieve the same level of security. In addition, the management and distribution of public keys in asymmetric encryption poses challenges. A user who wishes to use a certain public key for either authentication or privacy protection needs to know for certain that the key belongs to the appropriate entity. This problem is usually handled through digitally signed documents distributed by a certificate authority or through certificates that accurately specify public-key-to-entity relationships. Difficulty arises because of the large number of certificates that need to be given to all potential participants in a variety of simultaneous transactions. One proposed solution that would improve scalability is to arrange certificate authorities in a hierarchical fashion for improved security management, but this solution raises many other issues that are outside the scope of this discussion. Public key infrastructure (PKI) refers to the class of problems that deal with the distribution of keys and certificates.
Another important e-security feature is the revocation of certificates. Mechanisms are often needed to invalidate a public-private key pair and to disseminate this updated information. A downside to the current certificate authority models is the way they bind public keys to a particular organization or individual, which can significantly compromise privacy. A working group of the IETF (the Simple PKI working group) is developing an Internet standard that addresses these issues. Several techniques have been developed to provide user authentication and protection of messaging traffic. Early protocols were aimed at providing link-level security, whereas today security is enforced across a range of different layers to provide greater flexibility and reassurance. Internet Protocol Security (IPSec), Transport Layer Security (TLS) and Pretty Good Privacy (PGP) operate respectively at the network, transport, and application layers.
IPSec is an architecture and set of standards at the network layer that provides a variety of services, such as the encryption and authentication of IP packets. It was devised by the IETF to provide a general framework rather than a complete set of functionality and encryption algorithms. Thus, it allows a pair of communicating entities to use whichever algorithms are adequate for the application. For example, an application that employs IPSec can choose whether to use an authentication facility that validates the sender or an encryption facility that also ensures the confidentiality of the payload (McWherter, Sevy, and Regli, 2000). The security may also be asymmetric, with authentication applied in one direction only. IPSec can protect traffic across any local area network (LAN) or wide area network (WAN). Traffic can also be terminated at end systems or at gateways, with encryption and decryption applied at the two endpoints.
IPSec technology was first used in virtual private networks (VPNs) to secure messages exchanged via an encrypted tunnel. For example, it has been used for exchange of information between health care providers and the Health Care Financing Administration in processing on-line Medicare claims. VPNs have several limitations; the tunneling scheme does not scale well, and VPNs often require prior knowledge of where connectivity will be required.
TLS is commonly used on the Internet in the form of the Secure Socket Layer (SSL) system (National Research Council Committee, 2000). TLS uses asymmetric encryption to authenticate the server (and sometimes the client) and symmetric encryption to secure information exchange between the end user and the server. It is widely used by financial institutions in electronic commerce and therefore can be used similarly in e-health applications to capture sensitive information such as credit card numbers. SSL can support encryption in both directions between the server and the client; however, it normally provides authentication of the host organization's Web site. Support of bidirectional encryption requires certificates to be assigned to both the client and the server. This may be needed in many e-health applications in which the authentication of the user and the e-health care provider are equally important. This requirement imposes constraints on the deployment of e-health applications because it entails careful assignment and distribution of certificates to the communicating parties.
Several initiatives are under way to set up certificate authorities for future e-health applications. Recently, Intel has announced a joint effort with the American Medical Association to provide digital certificates that will enable doctors to transmit information such as test results to patients and other e-health care professionals (Kontaxakis, Walter, and Sakas, 2000). In e-consumer health informatics, WebMD has agreed to provide a similar service to physicians. WellMed and Franklin Health also have plans in place to enhance e-consumer informatics. A $2.5 million grant has been awarded for a five-state Health Key research initiative on facilitating electronic exchanges of information among companies in the health sector while protecting data confidentiality (Prior, 1996).
At the application layer, particularly in adding security to e-mail exchanges, PGP has been a popular choice. PGP is a well-developed collection of commercially supported encryption software that is now freely available for noncommercial use. This technology combines symmetric and asymmetric cryptography: symmetric cryptography is used to generate a session key for a multirecipient e-mail message, while asymmetric cryptography is used to encrypt the message for its transmission. Moreover, PGP is a generic set of encryption algorithms that can be conveniently extended to applications beyond e-mail.
Security measures can also be taken to protect data and knowledge elements embedded in e-mails rather than the entire e-mail message. Multipurpose Internet Mail Extension (MIME) is an extension of standard e-mail formats that supports different data forms, such as video and audio, that are not typically represented as ASCII text. A secured version of MIME (Secure/MIME, or S/MIME) supports the use of digital signatures to encrypt data in e-mail messages. S/MIME uses a hierarchical certificate authorization model and uses certificates based on the X509 (Version 3) standard. Extensions that incorporate MIME or S/MIME encryption technologies can also be added to existing videoconferencing standards such as H323.
H323 is a widely used set of recommendations for transporting multimedia information across a packet-based network such as the Internet. Following the publication of H323 (Version 1) in 1996, several versions have added improvements such as support for QoS and e-security. These improvements make H323 useful for e-health applications such as e-consultation and remote surgery. H323 (Version 2), for example, includes e-security features specified in the H235 standards to support authentication, nonrepudiation, data integrity, and confidentiality. H235 does not restrict the authentication and encryption technologies that may be used; it provides a generic mechanism to negotiate these and supports various combinations of symmetric and asymmetric cryptographic technologies. H235 requires call control channels to be secured—for example, using IPSec. To provide greater e-security, authentication is implemented through end user digital certificates rather than through end terminals. As multimedia e-networking advances, new versions are incorporating more complex e-security features to ensure the integrity and validity of the data exchanged and to deal with issues such as user privacy, security, and confidentiality on e-networks.
Given the many technological options available to support telecommunication and Internet-associated technologies, it is clear that a wide range of varying e-health services is possible. These services include those directed by surgeons and physicians such as remote surgical procedures and e-consultation as well as services such as on-line appointments and remote patient monitoring. Notable examples of current, potential, and sometimes very successful applications include remote assessment of patient problems; on-line diagnostic, therapeutic, and prognostic services; remote drug dispensing services; remote patient monitoring and sending of reminders; provider-to-patient and patient-to-provider consultation; physician-to-physician referrals; knowledge management capability in the form of automatic transmission of clinical data, texts, X-rays, CT scans, and other forms of imaging, as well as e-consumer informatics, interactive education, research, and distance training related to e-health care applications (Zhang and others, 2000).
Again, the e-networking requirements and standards we have reviewed so far can only function appropriately within the context of an open systems interconnect model and appropriate e-networking infrastructures. Accordingly, we now turn to these topics.
E-Networking Infrastructures
In this section, we focus on the concept of an open systems interconnect model and on two contrasting approaches to e-network infrastructures and configurations. Besides describing a case scenario using cellular infrastructure, we show how terrestrial networks can be extended in geographical scope through the use of satellite technologies for a low-bandwidth or a high-bandwidth satellite infrastructure. The latter configuration is also used to examine the bottlenecks of satellite communications and some suggested improvements.
Open Systems Interconnect Model
Health organizations are sometimes locked into the technologies of the past because of legacy systems that are poorly integrated, costly, difficult to maintain, and hard to change. One strategy for moving toward e-health care is to learn how to leverage these investments to take advantage of both existing and new technologies. Major problems often faced in connecting legacy systems with e-networks are hardware incompatibility, layering of complex protocols, and difficulty in understanding how data can be exchanged between two computer systems within a network. The open systems interconnect (OSI) model addresses these problems in large part by showing how many devices can exchange and communicate information via a hierarchy of seven layers. These layers—which roughly correspond to the three-tier connectivity concept of systems, applications, and physical connectivity that was discussed in Tan and Hanna (1994)—are the application, presentation, session, transport, network, data link, and physical layers. Understanding the way these layers work to execute the exchange of information between the network and the transmitting host system and user (source) on one end, and between the network and the receiving host system and user (destination) on the other end will assist us in designing better e-networks.
Essentially, when a source—that is, a transmitting host system—is preparing to send information out, the user will appear to work directly via e-mail, file transfers, or remote logins from the application layer of the source computer to the application layer of the destination computer, independent of the e-network architecture or configuration. While this may appear intuitively simple, the actual process is quite sophisticated; the data are physically and sequentially moved from the highest (application) layer to the lowest layer and are transformed into bits and bytes to be physically channeled through the nodes of a network. At the receiving end, these bits and bytes are moved in reverse from the lowest (physical) layer to the highest layer and transformed into appropriately coded and formatted data available to the user of the receiving system.
Below the application layer, the presentation layer insulates the destination user from the source user by presenting the data to be transferred to the destination user in an understandable format even when the different host systems use different data formats. The presentation layer also provides the necessary security measures.
Just below the presentation layer is the session layer. Here, applications on the two different host systems may engage in a logical connection through a synchronization of the session, specifying to the users at both ends when to send or to receive the message. The session layer also handles error recovery.
The transport layer is next; it deals mainly with the end-to-end communications by dividing the data into segments and then either sending or receiving the data.
The next three layers—the network layer, the data link layer, and the physical layer—have to do with the physical routing and the actual network navigational process. In the network layer, the optimal data routing is determined, including the switching elements that will be used to conduct the transmission. The data link layer then supervises the flow of information among and between nodes in the network, while the physical or electrical aspects of data communication and exchange are controlled in the physical layer.
While the OSI model has not been commercially adopted, the concept is nevertheless valuable for our understanding of how e-health data can be transferred from one end of an e-network, where the data are available, to the other end, where the data are needed. Moreover, the development of narrowband and broadband integrated services digital networks (ISDNs) was based on the OSI model. At this point, it is important to understand how e-health data can be transferred via e-networks, not only in the digital environment of ISDN network infrastructures but in the environment of wireless and mobile network infrastructures.
ISDN Infrastructures
Integrated services digital network (ISDN) technology enables the merging of separate networks into a single high-speed multimedia communications infrastructure through digital switching and digital transmission. ISDN networks can be divided into narrowband (an amalgam of circuit-switched and packet-switched signals) and broadband (high speed packet-switched network). The performance of these networks has received some attention in the literature, most prominently, those of the Clarke experiments discussed next.
Using the Advanced Informatics Distributed Medical Access Network (AIDMAN) to deliver e-health services to remote areas in Greece, Clarke, Fragos, Jones, and Lioupis (2000) investigated the performance of three types of link protocols to determine how their characteristics affect the performance of e-health care applications when bandwidth is limited to 256 kilobytes per second. The three types of protocols that were tested are (1) a circuit-switched (or narrowband N-ISDN) network; (2) a packet-switched (or Transmission Control Protocol/Internet Protocol [TCP/IPv4]) network (analogous to broadband B-ISDN); and (3) a cell-switched (or Asynchronous Transfer Mode [ATM]) network (these differentiated terms are based on the bandwidth requirements and the type of technology used in the networks).
Figure 6.2 shows the different e-network configurations that were set up for the Clarke, Fragos, Jones, and Lioupis's investigation.
With the narrowband ISDN (circuit-switched) network shown in Figure 6.2a, videoconferencing and image transfers can be supported using the International Telecommunications Union H320 and T120 standards, respectively. These standards are useful for transferring images and sharing applications between videoconference participants. TCP/IP is not supported by H320, so applications based on the DICOM standard, such as X-ray transmission, cannot be used simultaneously with videoconferencing. The advantage of narrowband N-ISDN is that each application has exclusive rights to the full bandwidth, so performance is guaranteed.
ISDN allocates the entire bandwidth for an application, thereby enhancing performance. For the TCP/IP network shown in Figure 6.2b, videoconferencing is accommodated using the H323 standard, which also supports the T120 standard. In contrast to the narrowband ISDN network, TCP/IP applications can be used with videoconferencing, but they must compete for bandwidth, which may affect the speed of the transfer. As shown, the key difference in the two network configurations is the use of N-ISDN in the former and the use of B-ISDN for greater bandwidth transmission in the latter.
FIGURE 6.2. COMPARISON OF THREE E-NETWORK CONFIGURATIONS
The ATM network, shown in Figure 6.2c, differs from the TCP/IP network in its use of fixed-length cells (ATM uses 53-byte cells). Also, the ATM network implements QoS, which gives priority to specified streams of traffic such as voice and images over data.
A simulated typical e-consultation session was modeled and tested, using various combinations of traffic. The results showed that the narrowband ISDN network behaved almost perfectly during the simulation. The major drawback was that the narrowband ISDN link required separate transmission of X-rays over a TCP/IP connection, so the simulation could not transmit everything at the same time.
For the TCP/IPv4 network, with a satellite link bandwidth of 128 kilobytes per second which is no more than the 256 kbps limit set for the experiment, X-ray transmission and videoconferencing worked well separately, but the results were not encouraging when they were used together; the X-ray transfer time became unacceptably large, and the videoconference session suffered unacceptable delay and jitter. The slow start or latent time experienced in the transmission of the different types of data and global synchronization required of TCP in order to transmit both the X-ray and videoconference data resulted in X-ray transfers' using up most of the bandwidth. The transfer of maximum-length packets of TCP-based X-rays also caused intolerable delays in video transmission. An end delay as accumulated for video transmission was 244.5 milliseconds, significantly higher than the required 100 milliseconds.
The ATM network showed excellent performance at 128 kilobytes per second, which is again less than the 256 kbps limit set for the experiment. This is because the ATM network is based on small cells, which interleave much better than the large IP packets. Every stream is guaranteed bandwidth and given priority via ATM. The drawbacks of ATM, however, include its high cost and its lack of available tailored applications.
Clarke, Fragos, Jones, and Lioupis (2000) conclude that low-bandwidth satellite links can be used for e-health services that include videoconferencing and image transfer using TCP/IP. However, if the link is set at 128 kilobytes per second, they argue for the use of QoS to prioritize traffic. Even though the ATM network yielded excellent performance, it was not the recommended alternative, owing to its relatively high cost and lack of available applications. Because narrowband N-ISDN did not allow the simultaneous transmission of X-rays and videoconferencing, it was considered unacceptable.
To date, several solutions have been suggested to improve networking performance for e-health services. In addition to TCP spoofing, selective and forward acknowledgments have been proposed. TCP spoofing divides the TCP connection between a server and a client into two paths. One path connects the client to its gateway router, then to the satellite. The other path also emanates from the router, but traverses an Internet link. Both paths terminate at the destination client sites where information is to be sent or retrieved. Another solution is to pace TCP segments by appropriately spacing acknowledgments to control the rate at which data are put into the network so that the total capacity of the network is preserved at all times for optimizing data transmission.
Not surprisingly, various studies have also found that TCP/IP should be enhanced to give better performance for e-health care over satellite networks that allow a high rate of data transfer. Tyrer (2000), for example, claims that satellites should be used to provide the high-bandwidth infrastructure for e-health services because telephone companies and cable companies are not likely to be able to do so. He does not believe that TCP/IP performance in a satellite environment is adequate. Over a long propagation of transmission delay, the TCP features prove to be very inefficient. A minimum of 1 to 1.5 round-trip transmission times are required to establish network connections. Similarly, the long delay may hamper functionality, through such problems as congestion avoidance and slow start. Acknowledgments are delayed and loss recovery are also hindered.
Cellular Versus Satellite Infrastructures
A cellular communication network comprises many cells, or areas, each with limited signal coverage. Using a particular frequency channel repeatedly, the cells are just far enough from one another to be interference-tolerant. The repeated use of a particular frequency enables the network to support a large number of subscribers. Another important feature is the hands-off mechanism through which the frequency assigned for a call is seamlessly changed as the mobile terminal crosses cell boundaries.
Woodward, Istepanian, and Richards (2001) demonstrated one application of cellular communication technologies: transferring medical information and knowledge to remote areas. They used a 9.6-kilobytes-per-second global system for mobile communications (GSM) channel to send ten-minute electrocardiograms (ECGs) via cellular telephone. The ECG images were compressed, using wavelet techniques at ratios of up to 10:1, a ratio considered to yield acceptable quality as judged by a cardiologist. The data and knowledge elements were encrypted before the cellular phone signals were sent to a remote location via the GSM cellular network and the public switched telephone network (PSTN). A LAN server was then connected to the PSTN using a modem. Results of the experimental transmission via this cellular network infrastructure demonstrated that the main clinical features of the transferred images were retained.
The researchers hope that this cellular network system, when fully developed, will allow a doctor to monitor patients remotely while they are actively doing their jobs. A patient should be free to move around while being monitored, both at work and during sports and activities. Existing cellular technology can be used to create a very inexpensive setup that interferes minimally with the life of the patient or the doctor.
Communication satellite technology is another wireless or mobile network infrastructure that can be used to promote e-health services and products. A network consisting of satellites, a system control center, and gateways allows direct channels to users via links to air, marine, and land mobile terminals and connects feeder links to various land networks. Satellite infrastructure supports fixed wireless access, broadcast of e-health programs, and mobile health (m-health) services. Broadcast services are mostly offered through traditional geostationary earth orbit (GEO) systems, while global mobile satellite personal communications are mostly provided through low or mid-earth orbit (LEO/MEO) satellites. Satellite networks offer several advantages over cellular phones and the Internet, including wide bandwidth, guaranteed bit rate, broadcast and multicast capabilities, and secure connections (Wang, 1999).
Farserotu and Prasad (2000) note that the type of satellite used can make a difference. LEO satellites move at a lower altitude than GEO satellites and thus cost less to launch and have less round-trip delay. In contrast, GEO satellites have much greater coverage. The relatively limited coverage of LEO systems necessitates frequent handovers between ground terminals and satellites, as well as cross-links among neighboring satellites. This makes LEO systems more complex and more susceptible to delay jitter than GEO systems. E-health applications employ the latest in e-networking research and developments—specifically, integrated audio-video, telecommunication, and Internet-associated technologies; digital networks; and cellular technology and satellites—to provide e-clinical information and knowledge transfer services for geographically dispersed health care facilities operated by a network of multiprovider organizations catering to even more geographically dispersed populations. However, the medicolegal challenges to the future of e-networks must be overcome if e-health care is to flourish.
Conclusion
E-health encompasses a wide range of applications, from browsing for health information on the Web to remote surgical procedures. The e-networking requirements that these applications impose vary greatly. High-end applications such as e-consultation have stringent e-networking requirements. They require high bandwidth for the exchange of high-resolution medical imaging data. Real-time e-consultation and other interactive applications also demand low latency and possibly a symmetric transfer rate (upstream/downstream) that is not commonly supported in current access network infrastructures. Accessibility is a key requirement in some biomedical research projects, such as visualization of complex gene-based data as it provides a continuum of e-health care services for e-patients in remote and restricted areas.
In this chapter, we have demonstrated that e-health services can be provided using today's e-technologies, although many improvements in QoS guarantees and e-networking security need to be achieved in order to enable such services as remote surgery. As with traditional health care services, the success of e-health care depends on support from governments, e-vendors, e-providers, e-payers, and, most important, e-consumers.
Chapter Questions
- Discuss the open system interconnect (OSI) model. What is its significance in e-networking, and how does understanding of this model help in designing e-networks for major classes of e-health applications?
- How are ISDN and mobile e-network infrastructures different? What are some of the configurations of these e-network infrastructures that are used in e-health care applications?
- What is the importance of understanding the e-networking requirements for major classes of e-health applications? What are some of the more complex e-health applications with advanced e-network requirements?
- How do medicolegal considerations impede the diffusion of e-health services?
- Imagine that you are a radiologist who has been hired to do a teleradiological reading in order to examine a child's state of health and susceptibility to a lung problem. From a medicolegal standpoint, what would your reaction to this request be if the request comes from potential adoptive parents of the child? Would you feel that you or the minor child had a right to keep your conclusions from the adoptive parents if the results were detrimental to the child's future? Who would be the best people to decide such an issue? Why?
References
Clarke, M., Fragos, A., Jones, R., & Lioupis, D. (2000). Optimum delivery of telemedicine over low bandwidth links. IEEE EMBS International Conference Proceedings. Information Technology Applications in Biomedicine, 32–37.
Daley, H. (2000). Telemedicine: The invisible legal barriers to the health care of the future. Annual Health L, 9, 73.
DICOM Standards Committee and Working Groups. (1998, December). DICOM committee procedures. Retrieved May 15, 2001, from Digital Imaging and Communications in Medicine Web site: http://medical.nema.org/dicom/wgs.html
Elsner, C., Kottkamp, H., & Hindricks, G. (2000). Introducing new telemedical services into clinical environments: A step-by-step approach at the Heart Center, Leipzig, Germany. Computers in Cardiology.
Farserotu, J., & Prasad, R. (2000, June). A survey of future broadband multimedia satellite systems, issues and trends. IEEE Communications Magazine, 38, 128–133.
Huang, H. K. (1999). PACS: Basic Principles and Applications. New York: Wiley.
Kleinke, J. (2000, November–December). Vaporware.com: The failed promise of the health care Internet; Why the Internet will be the next thing not to fix the U.S. health care system. Health Affairs.
Kontaxakis, G., Walter, S., & Sakas, G. (2000). EU-TeleInViVo: An integrated portable telemedicine workstation featuring acquisition, processing and transmission over low-bandwidth lines of 3D ultrasound volume images. IEEE EMBS International Conference on Information Technology Applications in Biomedicine Proceedings.
McDermott, W., Tri, J., Mitchell, M., Levens, S., Wondrow, M., Huie, L., Khandheria, B., & Gilbert, B. (1999, July–August). Mayo Foundation, optimization of wide-area ATM and local-area Ethernet/FDDI network configurations for high-speed telemedicine communications employing NASA's ACTS. IEEE Network, 13(4), 30–38.
McWherter, D., Sevy, J., & Regli, W. (2000, July–August). Building an IP network quality-of-service testbed. IEEE Internet Computing, 4(4), 65–73.
National Research Council Committee. (2000). Networking health: Prescriptions for the Internet. Washington DC: National Academy Press.
Pradhan, M. (2001). Retrieved from http://www-smi.stanford.edu/people/pradhan/articles/telemed.html
Prior, F. (1996). Communication technology for telemedicine. Proceedings of the National Forum.
Rickards, T. (1996). Retrieved from http://www.uni-mainz.de/Cardio/dicom/links/2106.htm
Sarek, M. (1997). The transfer of multimedia information in biomedicine. Proceedings of the IEEE Engineering in Medicine and Biology Society Region 8 International Conference.
Skolnick, A. (1998, March 11). Monitor passes first tests with flying colors. Journal of the American Medical Association, 279(10).
Tan J., & Hanna, J. (1994). Integrating health care with information technology: Knitting patient information through networking. Health Care Management Review, 19(2), 72–80.
Tarn, J., Wen, H. & Tan, J. (2001). Communications system architecture: Networking health provider organizations and building virtual communities. In J. Tan, Health management information systems: Methods and practical applications (2nd ed., pp. 179–203). Sudbury, MA: Jones & Bartlett.
Tyrer, H. (2000). Satellite wide-area-network for telemedicine. IEEE Aerospace Conference Proceedings (Vol. 1, pp. 141–148).
Wachter, G. (2000, March 26). Two years of Medicare reimbursement of telemedicine: A post-mortem. Retrieved May 15, 2001, from http://tie.telemed.org/legal/issues/reimburse_summary.asp
Wang, C. (1999). Security issues to tele-medicine system design. IEEE Southeastcon '99 Proceedings.
Woodward, B., Istepanian, R., & Richards, C. (2001, March). Design of a telemedicine system using a mobile telephone. IEEE Transactions on Information Technology in Biomedicine, 5, 13–15.
Zhang, J., Stahl, J., Huang, H., Zhou, X., Lou, S., & Song, K. (2000). Real-time teleconsultation with high-resolution and large-volume medical images for collaborative healthcare. IEEE Transactions on Information Technology in Biomedicine, 4(2), 178–185.
Mobile Health Networks Case: Unconfined Mobile Bluetooth Technology for E-Medical Services
Qiang Cheng, Huyu Qu, Yingge Wang, Joseph Tan
Most conventional telemedicine (or e-medicine) systems use fixed wired LAN, cable, DSL (Digital Subscriber Line), and other landline systems to transmit medical data or operations. As wireless LAN technology becomes increasingly pervasive, e-health professionals are considering wireless LANs for their mobile medicine systems.
However, both landline and wireless systems used today have limited real-world applications. Landline systems are restricted to indoor use—for example, in hospitals, clinical wards, or family rooms (in family nursing systems); when patients or physicians leave those small areas, they lose access to the system. Data transmitted through wireless channels are more vulnerable to eavesdropping or interception than data transmitted through wired channels. To enable secure, real-time, distant health care, we therefore propose a new wireless e-medicine system that combines wireless LANs with wireless WANs, mobile PSTN networks, or satellite communication networks. Using our system, patients, physicians, nurses, and health care workers would be able to get real-time medical service anywhere in the world. We also propose to build covert channels of wireless LANs into our system to transmit important medical data or operations, which would greatly enhance the security of e-medicine.
Background
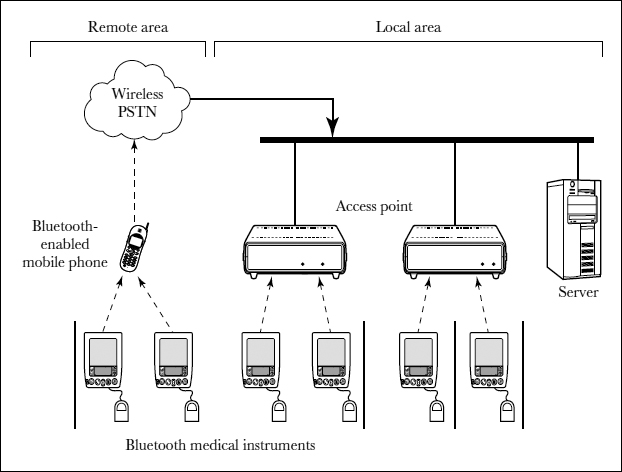
E-medicine uses telecommunication technologies to provide conduits for information exchange between physicians, nurses, and patients. The recent development of remote patient monitoring systems using Bluetooth wireless LAN techniques has eliminated wire lines and given patients the freedom to move around inside a hospital, clinic, or patient ward (Woodward and Rasid, 2003; Hung and Zhang, 2002). We will use the term mobile medicine to describe such a system. In these systems, the patient's body is equipped with Bluetooth-enabled smart sensors. The signals from the sensors are transmitted via wireless to the nearest receiver, a Bluetooth access point to the central nursing system.
Although the major advantage of wireless medicine is its mobility, existing remote patient monitoring systems still restrict the patient to a ward unit or a hospital, so the patient has to pay expensive inpatient care fees. To address this problem, we propose a family nursing system. A Bluetooth access point could be installed inside the patient's home. Sensor signals collected from the patient's body would be conveyed from Bluetooth-enabled instruments to the central nursing system in the hospital via the access point and the Internet (Woodward and Rasid, 2003; Hung and Zhang, 2002). With this family nursing system, the patient could substantially reduce medical cost yet still receive quality health care service.
Some patients undergoing medical monitoring need to move around for work, travel, or other outdoor activities. Existing nursing systems, including family nursing, will not permit this freedom of movement (Woodward and Rasid, 2003; Hung and Zhang, 2002; Luo and Cheng, 2004). Keeping these patients (for example, those with chronic diseases who need long-term health services) in wards or at home all the time is undesirable; thus, mobile medicine or monitoring can play a useful role.
To this end, we propose a new mobile system to provide unconfined health care services, one that combines wireless LANs (WLANs) with wireless WANs, the public switched telephone network (PSTN), and the Internet or satellite communication networks. With the help of our proposed wireless system, patients, physicians, and nurses could be empowered to receive or provide real-time, distant health care services. Both patients and providers would have the freedom to be anywhere in the world while sending, receiving, checking, and examining medical data in a timely fashion. The proposed system provides, among other benefits, a technological solution to the long-term shortage of nurses in the United States (Luo and Cheng, 2004).
We first present the prototype of our unconfined mobile wireless medicine system and illustrate the application of such a system. Next, we discuss the security issues and propose a covert channel to enhance the security of the system. Finally, we discuss future research possibilities.
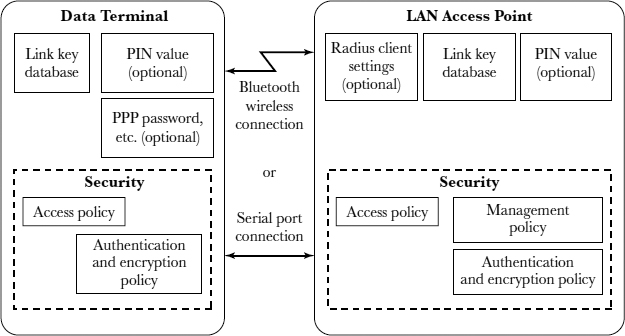
Prototype of a Bluetooth-Enabled Medicine System
With mobile medicine, reliability and security are key technical considerations. The two widely used WLAN standards are IEEE 802.11b and Bluetooth. In North America, WLAN systems operate in the unlicensed industrial, scientific, and medicine (ISM) band ranging from 2400 to 2483.5 MHz using Gaussian-filtered frequency shift keying (GFSK) modulation. To reduce the interference, spread spectrum (SS) techniques are used. For example, Bluetooth uses frequency-hopping SS with 1600 hops per second, and it hops among 79 channels spaced at 1 MHz; in contrast, IEEE 802.11b uses direct sequence SS for transmission. Bluetooth supports data transfer rates of less than 1 megabyte per second, while IEEE 802.11b supports up to 11 megabytes per second. Bluetooth forms networks on an ad hoc basis and covers short-range cells of less than 10 meters; IEEE 802.11b covers cells up to 20 meters in size (Molts, 2001; Haykin and Moher, 2003).
The IEEE 802.11b standard provides encryption and authentication mechanisms via the Wired Equivalent Privacy (WEP) protocol. WEP adopts the RC4 encryption algorithm to encrypt over-the-air transmissions (Molts, 2001; Haykin and Moher, 2003). RC4 concatenates a 128-bit secret key with a 24-bit random initialization vector (IV) and uses them to generate a pseudo-random sequence. This pseudorandom sequence is applied to the plain text to produce the cipher text. Upon receipt of the cipher text, the receiver uses the IV and the secret key to regenerate the pseudorandom sequence and reveal the original text. It is known that RC4 is vulnerable to various forms of attack based on statistical analysis (Knudsen et al., 1998; Xydis and Blake-Wilson, 2002). There are also weaknesses in the key-scheduling algorithm of RC4, so related key attack can be mounted on RC4 cryptosystems (Fluhrer, Mantin, and Shamir, 2001).
Bluetooth is a low-cost, low-power, and short-range radio communication technology. The Bluetooth protocol has two types of link: a synchronous connection-oriented (SCO) link and an asynchronous connection-less (ACL) link. The SCO link supports time-bounded information and thus can be used in time-critical e-medicine applications, such as stethoscope examinations. The ACL link supports packet-switched connection so that the system can be used to transmit large volumes of non–time-sensitive information, such as electrocardiogram (ECG) and photoplethysmogram files.
Bluetooth is essentially a replacement for physical cables. Up to eight Bluetooth-enabled devices can automatically form a piconet on the fly. Each piconet consists of one master and up to seven active slaves. All devices in a piconet are synchronized, and the master determines the frequency-hopping pattern (Haykin and Moher, 2003; Rappaport, 2002). A piconet distinguishes itself from neighboring piconets by its hopping frequency. Transmission can happen only between a master and a slave; there is no direct communication between the slaves within a piconet. The transmission is full duplex, using a slotted time-division-duplex (TDD) access strategy. Master-to-slave transmissions always start in an even-numbered slot, while slave-to-master transmissions begin in an odd-numbered time slot. All security functions are performed at the link level, and the security is based on a 48-bit unique device address, a 128-bit pseudorandom private key for authentication, an 8- to 128-bit private key for encryption, and a 128-bit pseudorandom number generated by the device. The security of Bluetooth is superior to that of IEEE 802.11b based on current research evidence (Xydis and Blake-Wilson, 2002).
Bluetooth supports low-power transmission with a range of 10 meters or less, which is very limited for wireless medicine. The problem of the short-range radio link can be overcome by combining Bluetooth personal area networks (PANs) with mobile public switched telephone networks (PSTNs)—that is, via Bluetooth-enabled cellular phones. For better security and wide availability in portable consumer electronics, we employ Bluetooth techniques in our proposed mobile medicine system.
Exhibit 6.1 illustrates the proposed Bluetooth-enabled system to perform mobile medicine.
A Bluetooth piconet allows the creation of a set of wireless serial connections between a master and up to seven active slaves. In our proposed system, the access point—either the local area network (for example, a corporate intranet) or a Bluetooth-enabled mobile phone for remote area networks—is the master, and the Bluetooth-enabled medical instruments are slaves. A data collector, such as a personal data assistant (PDA), can collect data from the medical instruments and convey the data through the mobile phone.
With Bluetooth standards, the wireless network can be constructed in two ways: ad hoc or through infrastructure. In an ad hoc network, any node can communicate with other nodes in the Bluetooth piconet. In an infrastructure network, every Bluetooth node must link through a fixed access point to communicate with other nodes inside or outside the piconet. We adopt an infrastructure network and use the phone as the Bluetooth hub.
EXHIBIT 6.1. MOBILE BLUETOOTH TELEMEDICINE SYSTEM
The medical instruments are based on an embedded computer running an operating system primarily designed to support real-time acquisition of data from biomedical sensors (Perez, 1998; Gomez et al., 1996; Banitsas, Tachakra, and Istepanian, 2002). Data can be stored in the instrument's memory or transmitted to a data collector for temporary storage, then sent to a central database server.
Two key parts of our unconfined mobile system are Bluetooth PANs or WLANs and wireless remote area networks. Many Bluetooth piconets cover a personal or local area environment—for example, a hospital or clinical ward unit or a home environment. The master of each piconet serves as the access point of a central medical database system, connecting wireless nodes in the sensor domain with the server or other nodes, either wired or wireless. A patient who is not bedbound can move around in the hospital or at home. The Bluetooth medical instruments worn by the patient send medical or patient data through a gateway (for example, a cellular phone) to the central database. Nurses or physicians can use their Bluetooth-enabled PDAs to access the central database to get data, including medical signals and images like ECGs and photoplethysmograms.
The patient can roam freely from one piconet to another. For unconfined wireless health services, we propose that the patient's cellular or mobile phone be exploited to collect data from the medical instruments, then the central database be accessed through a mobile PSTN or satellite network to store and retrieve data. The interaction of Bluetooth PANs and wireless remote area networks in a scalable and functional way is important, with the connectivity of the sensor domain and the remote area networks provided through packet translation, socket proxying, and so on.
In addition to connectivity, security is a key technical consideration as more than one server will be required to conduct secure wireless medicine. In this prototype, wireless service providers are given the responsibility of managing a central database for all of their cellular customers. The access control and authentication mechanisms currently used in cellular communication services are baseline security measures for a user (patient, physician, or nurse) to access the wireless database system. Additional security defenses will be needed, as we will discuss in the next section.
The rapid evolution of mobile and wireless telecommunication systems has given birth to faster data transfer rates and broader bandwidth. This evolution has facilitated our unconfined mobile medicine system, which requires high data transfer rates and on-line connection. Cellular telephones are commonplace today, and with improved services and increasing functionality, it would be practical for most patients to use cellular phones for the proposed unconfined mobile services. Several mobile phone models already have Bluetooth-enabled input and output—for example, Nokia's 7650. Adapting an ordinary mobile phone to be Bluetooth-enabled is technically straight-forward, and the associated cost is moderate; thus, the cost of implementing our proposed system is expected to be within the reach of most people.
The volume of patient data could become large. If on-line monitoring is not necessary, home computers, PDAs, or dedicated electronic patient cards could be used to collect the medical data, which would then be periodically transmitted to the central database. If on-line monitoring is important, the cellular phone could send the medical data to the database in real time. Because it might be costly to store a lot of data in a wireless database maintained by the service provider, patients or physicians could regularly download the medical data from the central database. The diagnosis report and patient bills could also be uploaded from the hospital to the patient's account in the wireless database, and the patient could be informed via his or her cellular phone. A Bluetooth-enabled data container could be designed and dedicated to data storage; it would automatically download any relevant data from the wireless central database to the patient's data management system or collect data from the wireless sensors the patient wears.
Applications of Wireless Medicine
Our proposed mobile system has numerous prospective applications. It could be used for remote stethoscope diagnosis that is time-critical or for remote cooperative medical imaging diagnosis. (Woodward and Rasid, 2003; Hung and Zhang, 2002; Gomez et al., 1996).
Another simple yet important application is distant mobile nursing and daily data collection (Luo and Cheng, 2004). As previously mentioned, the serious shortage of nurses in the United States is unlikely to change in the near future. Wireless nursing systems provide more patients per nurse monitoring time (with physical attention given only to those who need help based on results of the remote monitoring) and can alleviate the shortage of nurses to a great degree; however, for any patient not physically in the hospital or at home, existing wireless nursing systems cannot work. In our proposed unconfined wireless medicine system, a patient's cellular phone collects medical or patient data from the Bluetooth-enabled sensors or instruments that the patient wears, then forwards them dynamically to the patient's account in the central database that is maintained by the wireless service provider.
Exhibit 6.2 shows the data flow of the unconfined mobile Bluetooth nursing system. The arrows denote communication. Medical data such as blood pressure, pulse, oxygen saturation, stethoscope signal, ECG, and other key measures can be sensed and conveyed to the cellular phone through Bluetooth links. The cellular phone then sends the data through the cellular or satellite networks to the central database, which is connected with the nurses or physicians. The patient is unconfined geographically. Neither are nurses or physicians limited to the wards. Nurses can monitor continually or check the medical data from the central medical database at regular times via their PDAs or wireless laptops. This way, one nurse can take care of more patients simultaneously.
EXHIBIT 6.2. DATA FLOW IN UNCONFINED MOBILE BLUETOOTH NURSING SYSTEM
System Security Issues
For wireless medicine, security is critical (Banitsas, Tachakra, and Istepanian, 2002; Chakraborty, 1999). There are several ways to enhance the security of our proposed system: (1) designing access control mechanisms for the central database, including user authentication and authorization; (2) designing Bluetooth PAN or WLAN security based on secret keys and passwords or user biometrics such as retinal prints or other similar forms of identification useful for authentication so that the security will not be compromised even if the hardware is lost or stolen; (3) encapsulating PAN or WLAN security protocols with other security protocols like IPSec (Doraswamy and Harkins, 1999). Here, we will focus on the security of the Bluetooth protocol stack, because the stack is relatively vulnerable to both passive eavesdropping and active interfering, compared with the database or remote area networks.
The Bluetooth PAN or LAN offers both authentication and encryption at the baseband level (Gupta, Krishnamurthy, and Faloutsos, 2002). Exhibit 6.3 shows the security architecture for Bluetooth access.
In Bluetooth protocol, the commonly shared secret is called a link key. At initialization, the initialization key is the link key. Authentication is performed with a challenge-response scheme using the E1 algorithm, according to Bluetooth system specification. An encryption key is generated from the link key and a pseudorandom number, using the E3 algorithm. These mechanisms can be used to protect communications between two Bluetooth devices.
The security of Bluetooth is much better than that of IEEE 802.11b. The Bluetooth authentication never transmits the complete challenge-response pair. In addition, the E1 algorithm is not easily invertible. Even if an attacker has recorded an authentication challenge-response session, this individual cannot directly use this information to compute the authentication key.
EXHIBIT 6.3. SECURITY ARCHITECTURE FOR BLUETOOTH LOCAL AREA NETWORK ACCESS
Typical Attacks on Bluetooth
Despite the security improvements of Bluetooth, there are still potential weaknesses. For instance, if an attacker can successfully get the personal identification number (PIN) code and especially the initialization key at initialization, then the protocol is vulnerable to attacks.
Several known Bluetooth holes include unique device address defined by IEEE, key management issues, PIN code but no support for user authentication. We will now consider three typical attacks exploiting these holes and suggest defenses. Then we will build a covert channel method to enhance the security.
Until a secure link is established, all exchanges between two devices are sent as plain text, including the variables for deriving the keys. The only defense is that a PIN and a device identity are used to generate an initialization key. All other link keys and authentication procedures depend on the initialization key. Thus, the initialization procedure is the most vulnerable. If an attacker can successfully guess or obtain the PIN, the initialization key and other link keys can subsequently be determined; furthermore, the attacker can decipher encrypted information from Bluetooth devices (Xydis and Blake-Wilson, 2002). The communications can then be subjected to eavesdropping and impersonation attacks. If an attacker has intercepted all information from the wireless channel at the initialization stage, then this individual may break the PIN code using brute force attacks. In many cases the PIN is a short number, so it is not that difficult to unlock. Thus, longer or random PINs should be used, and initialization should be performed only in a private place.
Because applications can choose to make a device connectable or discoverable (using Service Discovery Protocol), an attack on the Bluetooth system can be mounted by placing a rogue access point close to an existing WLAN. As wireless nodes usually associate with the access point that offers the best signal-to-noise ratio, they may connect to the rogue access point and lose contact with valid networks. Site survey can frequently be conducted to detect hidden access points.
Denial of service (DoS) is an active interfering attack that is very challenging to detect and prevent (Gupta, Krishnamurthy, and Faloutsos, 2002). An attacker can cause network congestion by generating an excessive amount of traffic either by itself or through other nodes. For the security of our proposed system, we need to consider both DoS attacks in wired networks, such as transmitting falsified route updates and reducing the time-to-live field in the IP headers causing data losses (Gupta, Krishnamurthy, and Faloutsos, 2002), and those in wireless networks. An attacker can send a message to keep the wireless channel busy, so that no other Bluetooth devices can use the channel. The attacker may use a particular node to continually relay spurious data so that the battery life of that node is drained. An end-to-end authentication may help prevent these attacks from being launched; however, DoS attacks will still be feasible if two legitimate nodes (one sender and one destination) collude.
Enhancing Security Using a Bluetooth Covert Channel
To defend against eavesdropping, interception, and impersonation, much attention has been given to encryption algorithms and sender/receiver authentications in the wireless networks.
For Bluetooth security in our proposed system, biometric authentication techniques are one promising approach. The patient's biometric traits such as blood type are entered into the cellular phone and verified on initialization of communication.
A complementary approach is to design three covert channels. These channels exploit the data frame headers of the Bluetooth protocol to transmit seemingly innocuous information between access points and sensor nodes. To guarantee the security of our covert channels, the sender can further encrypt or encode the covert messages. Many encoding algorithms—for example, the chaotic mixing algorithm—can be applied to our system (Qu and Cheng, 2004).
In the baseband layer, 13 bits can be transmitted as covert information; in the L2CAP layer, 8 or 9 bits (8 bits for signaling command packets, 9 bits for data packets); in the SDP layer, 16 bits. Thus, a 37-bit (or 38-bit) covert channel can be established in one Bluetooth packet. The covert channel can be exploited innocuously to transmit some information. Because only 37 or 38 bits can be sent per packet, this covert channel can send short yet critical information. We propose to send the activating share, a small number, via the designed covert channels, so that the pre-positioned secret-sharing mechanism (Simmons, 1989) can be enabled during Bluetooth key establishment. This is a particularly promising and powerful technique because it addresses holes in regard to PIN codes and user authentication. Moreover, the public-key method is less likely to be useful due to its high computational and associated architectural complexity. Our covert channel method combined with the prepositioned secret sharing provides a solution. The covert channel method can also be applied to trace DoS attacks (Qu and Cheng, 2004).
Other security approaches relate specifically to medical image transmission. Some functional data are usually associated with the medical images, such as personal data of the patient and diagnosis results. Without the associated functional data, the medical image is of little use. One method to protect the security of these images is to selectively encrypt the image. The secret key can be established by using the secret-sharing scheme.
Exhibit 6.4 shows another method, in which the covert channel is used to transfer the patient's information, while the body field transfers the medical images. Encryption can be applied before the patient's data are sent through the covert channel.
Conclusion
Wireless medicine gives patients the freedom to go anywhere they like while receiving medical services and health care in a timely fashion. Our system minimizes interference in the patients' daily lives and empowers the medical providers as well. The system design and security issues can be managed, and a Bluetooth covert channel technique can enhance security. Miniaturized and portable medical instruments and sensors will further expand the application domains of our proposed system.
EXHIBIT 6.4. USING A COVERT CHANNEL TO TRANSFER MEDICAL IMAGES
In mobile and wireless medicine, the power supply and battery life of the sensors or instruments are important and need to be studied. Hence, one fruitful research direction might be studying how to optimize the energy consumption of the proposed system. Another challenge is learning how best to incorporate advanced disease detection and prevention systems, which would be capable of analyzing automatically and reliably the medical data from Bluetooth-enabled sensors and providing warnings to both patients and physicians.
Case Questions
- What other potential applications of the proposed mobile medicine system can you think of?
- Besides the interoperability and security of PANs, WLANs, and remote area networks, what important technical issues do you feel should be considered in the proposed system?
- Apart from technological issues, what are the social and economical implications of the proposed system? Imagine that you have been asked to evaluate the feasibility and acceptance of the proposed system among patients and providers. How would you go about doing this? What questions would you ask the providers and the patients?
References
Banitsas, K. A., Tachakra, S., & Istepanian, R.S.H. (2002, October). Operational parameters of a medical wireless LAN: Security, range and interference issues. In Proceedings of the joint EMBS/BMES conference. Houston, TX.
Bluetooth SIG Security Expert Group. (1999). Specification of Bluetooth system. (Vols. 1–2). Version 1.0, Part B.
Bluetooth SIG Security Expert Group. (2001, February). Baseband specification. Specification of the Bluetooth system and core, Version 1.1, Part B.
Bluetooth SIG Security Expert Group. (2002, April). Bluetooth security white paper, Version 1.0.
Chakraborty, S. (1999). Mobile multimedia: Concepts, services, and systems. In E. B. Furht (Ed.), Handbooks of Internet and multimedia systems and applications. CRC-IEEE Press.
Doraswamy, N., & Harkins, D. (1999). IPsec: The new security standard for the Internet, intranet and virtual private networks. Upper Saddle River, NJ: Prentice Hall.
Fluhrer, S., Mantin, I., & Shamir, A. (2001, August). Weakness in the key scheduling algorithm of RC4. In Proceedings of the Annual Workshop on Selected Areas in Cryptography.
Gomez, E.J., del Pozo, F., Quiles, J.A., Arredondo, M.T., Rahms, H., Sanz, M., & Cano, P. (1996). A telemedicine system for remote cooperative medical imaging diagnosis. Computer Methods and Programs in Biomedicine, 49, 37–48.
Gupta, V., Krishnamurthy, S., & Faloutsos, M. (2002). Denial of service attacks at the MAC layer in wireless ad hoc networks. In Proceedings of MILCOM.
Haykin, S., & Moher, M. (2003). Modern wireless communications. Upper Saddle River, NJ: Prentice Hall.
Hung, K., & Zhang, Y. T. (2002, October). Usage of Bluetooth in wireless sensors for tele-healthcare. In Proceedings of the joint EMBS/BMES Conference. Houston, TX.
Knudsen, L., Meier, W., Preneel, B., Rijmen, V., & Verdoolaege, S. (1998). Analysis method for (alleged) RC4. In Proceedings of ASIACRYPT.
Luo, X., & Cheng, Q. (2004, January). Unconfined mobile Bluetooth nursing and daily data collection. In Proceedings of the IEEE Consumer Communications Networking Conference. Las Vegas, NV.
Molts, D. (2001, December). Mobile and wireless technology. Network Computing.
Perez, R. (1998). Wireless communications design handbook. New York: Academic Press.
Qu, H., & Cheng, Q. (2004). Enhancing Bluetooth security with covert channel signaling. Unpublished manuscript.
Rappaport, T. S. (2002). Wireless communications principles and practice (2nd ed.). Upper Saddle River, NJ: Prentice Hall.
Simmons, G. J. (1989). Prepositioned shared secret and/or shared control schemes. In Proceedings of Advances in Cryptology-EUROCRYPT.
Woodward, B., & Rasid, M.F.A. (2003). Wireless telemedicine: The next step? In Proceedings of the annual IEEE Conference on Information Technology Applications in Biomedicine.
Xydis, T. G., & Blake-Wilson, S. (2002, February). Security comparison: Bluetooth communications vs. 802.11. Bluetooth Security Expert Group.
The authors would like to acknowledge the contributions of William J. Rogers, a graduate student in electrical engineering who was previously at Stanford University in Stanford, California.