The 1990s were characterized by an IT investment frenzy. Everybody wanted to jump onto the Internet bandwagon. Little effort was expended on analyzing and justifying the IT investment requirements and benefits.
The bursting of the Internet bubble not only resulted in a myriad of failed businesses and large monetary losses but also led to a renewed emphasis on scrutiny and accountability when making investments in IT. Indeed, in many organizations, today’s IT investments are not made at the discretion of the CIO or CTO. The CFO is a key participant in the decision-making process for allocating the organization’s funds to IT. As a result, the need for a clear, concise, and robust IT business case has become imperative.
A term that is often used interchangeably or in conjunction with business case is return on investment (ROI). However, these two terms do not necessarily denote the same thing. In fact, ROI is only a subset of a business case and focuses exclusively on the financial ramifications of an investment.
ROI is often erroneously considered to be the silver-bullet metric that will ensure that the IT purchase will be beneficial to the organization. As you will see in this chapter, ROI has benefits and pitfalls. An ROI analysis is something senior management understands, and it instills rationality and standardization in the IT decision-making process. However, because the strategic impact of IT investments is next to impossible to quantify, ROI does not provide a vehicle for capturing these benefits. Furthermore, elements such as the risk associated with the investment and the time value of money are not accounted for by plain-vanilla ROI analysis. The specific benefits and pitfalls of ROI will be covered in greater detail later in this chapter.
The goal of a business case—for WLANs or for other assets—is to provide a holistic cost justification. This chapter demystifies the process of developing an exhaustive and vigorous business case for WLANs in your organization. It also provides frameworks for tackling the challenge of business-technology alignment and identification of opportune application points for WLANs within the organizational ecosystem. Quantitative, qualitative, and risk considerations are covered to provide an exhaustive view. Finally, given the importance of economic returns, the most common financial barometers including ROI, payback period, Net Present Value, and internal rate of return are described in detail.
Even though wireless networks form a very specific subset of information technology assets, several high-level considerations are required before making the decision to pursue a concrete design and implementation of a WLAN in your ecosystem. These considerations encompass both business and technology considerations, and they are not necessarily unique to WLANs. Indeed, whenever an investment opportunity or requirement is present, similar deliberations must be made. Examples include what the rationale for the investment is, what the scope is, how much capital outlay will be required, what the timing of these outlays is, what kinds of returns should be expected, and so on. The same considerations can be made whether you are making an investment in information technology, manufacturing equipment, real estate, or bonds.
There are, however, subtle differences when it comes to information technology infrastructure investments for two reasons:
First, after IT infrastructure investments are made, they should be considered sunk costs, which cannot be recovered. This is because the average shelf life of today’s IT assets is relatively short, even though the asset might be usable for a relatively long time. The key point to consider is the economic value, not the life span of usability of the asset. Many IT products have economic life spans of one to three years, after which they have no residual economic value. The lack of residual value does not, however, imply that the asset can no longer be used.
Consider a similar example of a car. The fair market value of an automobile that is 7 to 10 years old is almost non-existent. Nonetheless, assuming that the vehicle remains in good operating condition, the car can continue to be driven until it physically breaks down. As such, the cost of the car is sunk after it has reached a certain age, but this does not mean that it is no longer usable.
Now consider a real-estate investment such as a building or land. These costs are not considered sunk because the initial cost can be recovered many years after the purchase has occurred. The residual value of these assets remains relatively constant—in fact, we often hope that these assets appreciate.
A second difference relating to investments in IT infrastructure is that by design, infrastructure forms the foundation upon which many higher-order solutions rest, including applications such as Customer Relationship Management (CRM), Enterprise Resource Planning (ERP), and e-mail applications. The applications support business processes that in turn help an organization to achieve its primary goals. IT infrastructure thus not only becomes a core business enabler, but is often considered a core business necessity in today’s information-driven world.
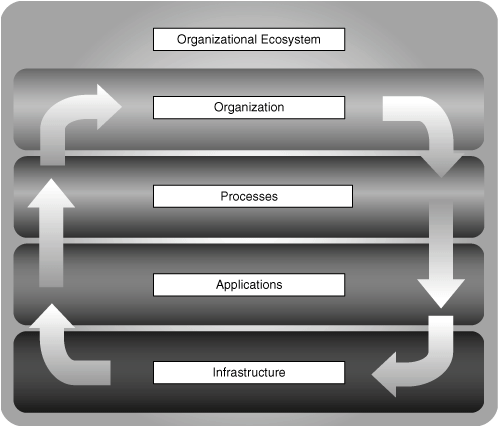
The organizational ecosystem can thus be deconstructed into several independent, tightly coupled layers, as shown in Figure 2-1. At the very bottom, the infrastructure assets enable data transformation, storage, and transport. These infrastructure assets are used by applications such as e-mail, web services, CRM, ERP, and many others that give the information meaning.
In their turn, the applications support various transactional, analytical, and collaborative processes. Transactional processes ensure that one activity in a sequence is committed before proceeding to the next one. Analytical processes create, mine, and destroy data. Collaborative processes make it possible to share information. Note that it is the collaborative process that actually creates real value because information in isolation has none. What is the value of a book that nobody reads? What is the value of an idea if nobody is aware of it?
At the very top, the organization has its specialized, dedicated teams that use the various processes to help the organization achieve its goals. Examples of corporate goals are increasing shareholder value, serving customers, providing employees with a superior working environment, and helping the community.
The flow of information in the institutional ecosystem creates a dynamic, fluid environment through which information flows with varying velocities. The ultimate purpose of acquiring, interpreting, and manipulating this information is to enable the institution to act upon it and adjust to changing conditions in the pursuit of its goals. For this to happen in a timely and relevant fashion, several criteria need to be fulfilled:
You must understand the external environment in which the organization exists.
You must be thoughtful of the internal constituents that make up the organization.
You must align internal and external elements so that you can identify and manipulate the relevant levers to effectively respond to the external environment.
Today, WLANs form an integral part of the IT infrastructure portfolio. However, it is not always clear whether this transport asset is relevant for any given organization. Indeed, when considering WLANs, you need to answer four basic questions:
Why are WLANs relevant to support my organizational goals?
What benefits should I target or expect?
Where should I deploy the WLANs?
How should I implement and operate the WLANs?
The remainder of this chapter covers the business-technology alignment challenge and arms you with the necessary tools to tackle and answer the first two questions. The following chapters cover the third and fourth questions.
In general, organizations exist to create value. The value creation process can take on many different forms, including the production of goods and materials in the manufacturing industry, the care of patients in the healthcare industry, the safekeeping and growth of financial assets in the financial services industry, and the sharing of knowledge in the academic world. The value can be tangible, as in the production of an automobile, or intangible, as when sharing knowledge.
To be effective at value creation, organizations must invest in tools that directly (or indirectly) support the value creation process. IT infrastructure assets are such tools. At a high level, investments in IT infrastructure assets are made to provide the organization with enabling tools to increase productivity and flexibility. Increasing productivity can be thought of as extending the leverage of other assets such as property, plants, equipment and human, intellectual, and brand capital. Greater flexibility implies a better ability to sense and respond to internal and external changes that directly affect the organization.
In the context of WLANs, the key question that you need to answer is this: “How can WLANs aid my organization in the value-creation process?”
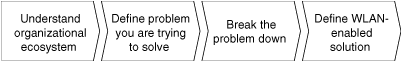
To effectively and successfully answer this question, implement the following top-down approach:
Understand your organizational ecosystem.
Define the problem that you are trying to solve.
Break the problem down.
Define the WLAN-enabled solution.
Figure 2-2 illustrates the discrete steps that need to be taken. The next sections describe each step in detail.
Every organization is subject to forces of change. These forces can come from inside the organization—internal drivers—or from outside the organization—external forces. The combination of the organization, the external constituents that are directly related to your organization, and the internal and external forces makes up the ecosystem in which your organization operates.
Strategy consultants employ a variety of frameworks to structure and facilitate the comprehension of the organizational ecosystem. Example frameworks include the three Cs (Customer, Company, Competition), low-cost versus niche player, and internal-external factors.
When an understanding of internal factors and external considerations has been developed, you are ready to tackle the following step.
Given the dynamics of your specific organization, what value do you expect the WLANs to deliver? Note that this question does not necessarily constrain itself to trivial answers such as “Enhancing communications and connectivity.” Indeed, armed with the knowledge acquired in the first step, your answer can be made not only much more relevant for your organization but also much more specific.
Two examples clearly illustrate this point. In the summer of 2001, Starbucks Corporation, a company known for serving coffee through its worldwide retail outlets, commenced deploying WLANs in its retail outlets. It is arguable that the value proposition for installing WLANs in the retail outlets was to make the baristas more productive.
Starbucks’ management identified the value of providing WLAN-enabled Internet access to its customers in another domain. By providing customers with easy-to-use Internet access, Starbucks hopes to enhance and extend the customer’s experience with the ultimate goal of serving him or her more coffee. As such, the value proposition of WLANs to Starbucks becomes increased revenues through more satisfying (repeat business) and longer (more servings) customer visits. The problem that Starbucks Corporation solved with WLANs is this: “How can Starbucks enhance the experience of customers to increase repeat business and make them consume more Starbucks’ products?”
A second example is that of Lifespan, which is featured in Chapter 10, “Healthcare Case Study.” Wireless networks formed an integral part of Lifespan’s IT infrastructure strategy as early as 1997. The challenge that Lifespan tackled was providing timely information access throughout the healthcare continuum.
The nature of healthcare is such that physicians and nurses cannot be tethered. They must be able to do rounds, go to clinics, and visit libraries. A challenge arises in that hospital staff must be able to access applications for patient information while remaining mobile. As such, the goal becomes finding a solution to get applications closer to the mobile physicians and the point of care of the patient.
The problem that Lifespan solved with WLANs is this: “How can Lifespan provide its physicians and nurses with relevant and timely information at the point of care of patients to increase customer satisfaction through delivery of safer, higher-quality healthcare?” Chapter 10 is dedicated to a case study of WLANs in the healthcare environment and specifically covers the rationale that Lifespan developed for deploying WLANs.
After you accurately define the problem, the next step is to break the complex problem down into simpler, more manageable components.
As you learned in the second step, organizations primarily address two different types of problems with WLANs:
Increasing revenues, as was the case for Starbucks
Increasing productivity and accuracy of staff, as was the case for Lifespan
You could argue that productivity and revenues are directly related and, hence, imply the same goal. The goal might be the same. After all, the majority of organizations strive to increase profitability by increasing revenue and decreasing expenses. The methods for achieving the goal, however, can be very different. This becomes clear when you deconstruct the problem to more specifically identify how your organization benefits from WLANs. Breaking down the problem not only makes the identification of a specific value-proposition easier, but it also reduces the risk of oversight.
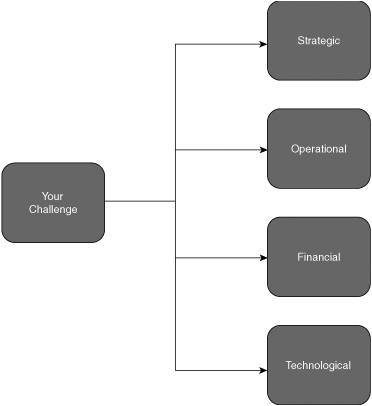
Four different dimensions are relevant when evaluating business challenges: strategic, operational, financial, and technological. Keep in mind that the WLAN’s value-proposition that you are attempting to pinpoint is not necessarily limited to a single dimension. Indeed, it will typically span at least two (strategic and technological) of them. A sample of drivers for WLANs in each of the four dimensions follows.
Strategic drivers include the following:
Provide high-speed mobile access/availability to information.
Increase employee productivity.
Facilitate and enhance collaboration.
Improve response times to stakeholders (customers, coworkers, and suppliers).
Provide richer communications capabilities.
Enhance customer experience.
Increase customer satisfaction.
Increase customer loyalty.
Improve aesthetics (no dangling wires).
Operational drivers include the following:
Simplify management of network infrastructure.
Provide connectivity in temporary locations.
Avoid difficult cabling situations.
Provide scalable connectivity (avoid insufficient data ports).
Financial drivers include the following:
Obviate cabling costs.
Avoid circuit expenses (WLAN inter-building bridges).
Reduce equipment cost for sporadically used spaces (meeting rooms and common areas).
Technological drivers include the following:
Provide communications infrastructure for mobile devices.
Enable mobility for wireless applications.
Interconnect heterogeneous platforms, devices, and applications.
Figure 2-3 illustrates the four dimensions you need to consider when assessing the value proposition of a WLAN.
After you define and understand the problem to be solved, a WLAN solution can be constructed. Chapter 3, “Preparation and Planning,” provides you with a structured approach for doing this. However, prior to launching this phase, you need to understand what the role of WLANs is in your organization as well as how to demonstrate the business value to your stakeholders. This is covered next.
As mentioned earlier in this chapter, the environment in which a company or institution operates can be broken down into interdependent blocks to create a layered model not so different from the OSI model. Each building block can subsequently be broken down into discrete components to further deconstruct and model the corporate and IT ecosystem.
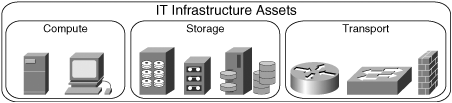
At the infrastructure layer, a simplified distinction can be made between three different classes of IT assets:
Compute assets—. These assets manipulate and transform information. Servers and personal computers (PCs) fall within the compute asset class.
Storage assets—. Storage assets exist to collect and warehouse information. Disk arrays, CDs, DVDs, and tape libraries are all examples of storage assets.
Transport assets—. Transport assets ensure that information can be moved from their point of origin or safekeeping to a point of consumption. Different kinds of communications networks such as the Public Switch Telephone Network (PSTN), WANs, LANs, and the technologies of choice for their implementation such as routers, switches, hubs, and firewalls are all examples of transport assets.
Figure 2-4 illustrates the different asset classes of the IT infrastructure layer.
These asset classes exist regardless of the syntax or semantics of the data—that is, the classes are independent of how the information is represented and what its meaning is. Also note that the classes do not necessarily imply an electronic nature. Indeed, customer data on a paper document can be transformed by a pencil, stored in a filing cabinet, and transported through the postal service. For the purpose of this book, however, we shall ignore analog representations and focus solely on the digital world.
Although the economic value of the information can vary widely—a meeting invitation e-mail is probably much less valuable than a product order or annual budgeting data—its core utility is constant. Information enables companies to sense and respond to changing business environments, thus facilitating the creation and sustenance of a competitive advantage. Similarly, information allows healthcare institutions to provide relevant, accurate, and timely care to patients. Finally, information in educational institutions arms the next-generation work force with the tools necessary to support the economy and drive continued growth through ongoing innovation.
Given the importance of information, it is critical to design an infrastructure that effectively, efficiently, and securely supports the transactional, analytical, and collaborative use of data. As such, the challenge at hand is one of aligning technology solutions—more specifically the IT infrastructure portfolio—with business requirements.
WLANs can be considered a specific subset of the IT transport assets. This type of asset is dedicated to and specialized in the transfer of information from a point of origin to a point of consumption or storage. Note, however, that this transport asset class contains many different communications network solutions. Examples include the GSM or CDMA networks used for cellular communications; data networking solutions such as WLAN, Ethernet, and SNA for local-area networks; and Frame Relay, ATM, and SONET for wide-area networks.
Chapter 1, “Introduction to Wireless LAN Technologies,” introduced the OSI reference model and employed the lower two layers (physical and data link) to provide a means of distinction and classification between the various types of networks. This section focuses on the subset that is relevant to WLANs—that is, local-area networks.
WLANs employ the unshielded, unbounded carrier mechanism of radio waves, as opposed to the unshielded or shielded but bound transport channel of wired networks. Indeed, wired networks use either electrical or photonic signals that are tunneled through a bearer medium. This unbounded versus bounded nature is the key difference between wireless and wired LANs. The organizational pros and cons related to this difference are discussed next.
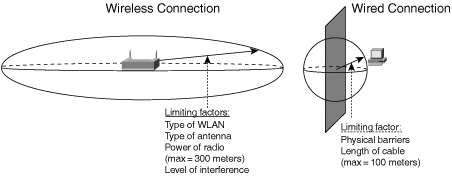
The unbounded nature of WLANs makes them pervasive within the coverage area. As such, you are not forced to locate and remain tethered to a network outlet. Your three-dimensional roaming domain is equal to the WLAN coverage area. In the wired world, your roaming ability is restricted by the tether. It is equal to the volume of the sphere with a radius equal to the length of the cable that connects your NIC to the network drop. That is the very best-case scenario. In practice, physical obstacles such as furniture, doors, and walls will make this reach much smaller.
Contrary to the wired world, the connectivity footprint in the wireless world is not limited to the network outlet. It is equal to the reach of the radio cloud, or more specifically, to the reach of your Basic Service Set (BSS). This untethered character makes WLANs ideal for environments that require fluid, transparent movement of computing assets. The value of mobility thus translates into convenience and reduced downtime, which in turn can translate into increased productivity. Figure 2-5 illustrates the difference in physical reach and mobility between wireless and wired networks.
Mobility is a key benefit in many different environments as it enables individuals to do their work when and where it is convenient for them, thus directly boosting productivity.
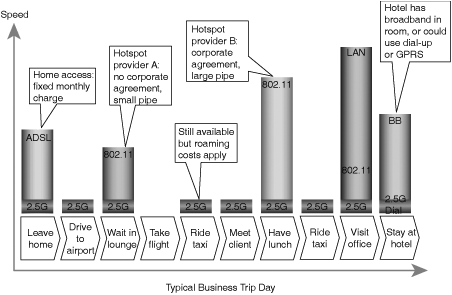
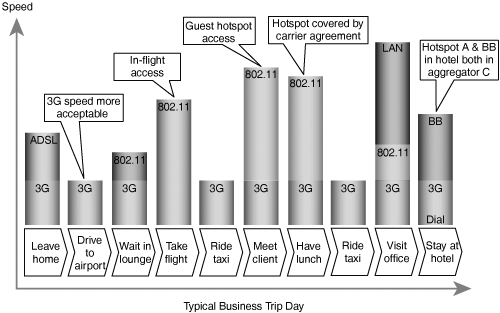
In the knowledge-worker corporate world, the ability to swiftly pick up and move between locations while retaining access to information reduces employee downtime and facilitates collaboration. Note that this concept is not bound to the confines of the corporate offices. WLAN hotspots in airport lounges, coffee shops, and hotels, and airplanes enable road warriors to obtain network access at their convenience throughout the business day. By supplementing WLANs with wide-area wireless cellular networks, the business traveler will soon be able to remain connected continuously throughout his or her journeys. Figure 2-6 and Figure 2-7 illustrate the evolution of connectivity options at various stages of a typical business trip.
Another example is the world of education. Students are highly mobile. They move between dorm rooms, classrooms, study rooms, and libraries. Because many of today’s students are armed with laptops, the value of mobility of the computing asset is vastly increased by complementing it with a transparent, flexible and mobile communications solution. Note that the same is true for teaching staff who roam between their offices, classrooms, and meeting rooms. The ability to remain connected anytime and anywhere vastly increases the ease of use, and hence the productivity, of mobile computing devices.
The hospital environment requires that physicians and nurses have patient information available at the point of care. By their bringing the computing environment to the mobile users, the probability that the healthcare professionals will use the IT tools provided greatly increases. As such, the quality and safety of healthcare is increased through accelerated access to and recording of patient information at the point of care. Refer to Chapter 10 for a case study of WLANs in the healthcare environment.
The source of convenience for WLANs can be found in the shared nature of the communications medium. Indeed, contrary to the fan-out ratio of one user per wired LAN endpoint, the fan-out ratio for access points of WLANs is theoretically unlimited. Many different users can associate with the same access point without running into the situation of insufficient data ports.
In practice, there is an acceptable access point fan-out ratio of approximately 30:1. This is a direct result of the MAC mechanism. When too many stations are attached to the same AP, increasing contention for network access will yield a deadlock situation in which no station can successfully send or receive either because of the inability to obtain airspace access or because of frame collisions.
The upper limit of fan-out aside, WLANs provide a very flexible solution for providing a high number of mobile devices with network access. This is ideal in situations where many different individuals (or devices) require network connectivity. Examples include meeting rooms, classrooms, and public hotspots such as airport lounges and coffee shops.
In addition, by using WLANs, you avoid the aesthetic wiring nightmare of using ad-hoc hubs or switches to increase the fan-out of wired solutions. Finally, you avert the risk of encountering the situation in which you do have a free data port, but you have no cable to plug into it.
WLANs do not offer the same bandwidth that is available in wired networks. Although you encounter port speeds of up to 10 Gbps in today’s wired LANs, WLANs are currently limited to 54 Mbps. The reasons are mainly related to the physical characteristics of the bearer medium—that is, radio instead of electrical or photonic—and the fact that WLANs are typically used in a shared operating mode. As such, it is critical to consider the bandwidth and quality of service (QoS) implications when evaluating WLANs. First, available WLAN bandwidth is orders of magnitude less than what is available with wired networks. Second, WLAN bandwidth is shared among wireless stations. Real available throughput thus becomes a fraction of the WLAN’s nominal throughput. Finally, because WLANs are a best-effort transport solution, additional considerations are required to provide some form of QoS determinism for latency-sensitive applications.
When a device is directly connected to a switch port, the communication medium is dedicated to that device. This dedicated connectivity is only achieved in the WLAN environment if a single device is associated with an AP. As such, bandwidth consideration should always be made with the shared nature in mind.
Note
Strictly speaking, in 802.11—even when the AP has a singular client—the AP and the client share the same medium when communicating with one another. In Ethernet, separate wires enable simultaneous bidirectional or full-duplex communication.
Note that the size of the pipe is not the only important parameter. Determining the amount of time required to get access to the transport medium and the probability for successful transmission (that is, no collisions) are also of key importance. The MAC characteristics of WLANs are such that no guarantees are made in terms of timely delivery.
As such, additional intelligence is required to provide the relatively predictable network throughput, latency, and jitter that is required by real-time and interactive data flows. QoS refers to the ability of a network to provide these higher-priority services and improved loss characteristics to selected network traffic. IP makes use of Layer 3 mechanisms such as IntServ or Diffserv. The IEEE 802.11e working group ratified the mechanism for providing Layer 2 class of service (CoS) mechanisms for WLANs in July 2005.
Note
Class of service (CoS) is part of the portfolio of QoS techniques, which also includes queuing, bandwidth reservation, and traffic engineering strategies. CoS is a way of classifying packets based on application type (voice, video, file transfer, transaction processing, etc.), user type, or any other classification method. The different classes can then be assigned different handling priorities.
802.11e provides the mechanism for injecting more deterministic behavior into the queuing and MAC protocols for WLANs. The goal is to provide a more robust foundation for QoS and increase the support of WLANs for latency- and jitter-sensitive applications such as IP Voice and IP Video.
The bandwidth and QoS limitations should not be taken lightly. As more high-bandwidth and latency-sensitive applications come online, the provisioning of appropriate capacity becomes critical. IP Telephony and high-bandwidth video applications are prime examples.
To perform a relevant cost comparison between wired and WLAN solutions, three distinct deployment scenarios must be considered:
Exclusively wired LANs
Exclusively wireless LANs
The hybrid version in which both wired and wireless connections are provided
Note
WLANs typically employ wired connections to connect APs to the LAN backbone. As such, the distinction between the three LAN environments is based on the connection that is offered to the end user device.
It is critical to realize that all cases are tradeoffs. The cost per end-user connection is lower for WLANs than for their wired counterparts because of the shared nature of the connectivity medium. However, the cost of bandwidth per end user for WLANs is significantly higher than for wired environments. Furthermore, this cost increases approximately linearly as a function of the number of end users that are associated with the AP.
Lastly, an opportunity cost is associated with the inability to connect an end user to a network. The basic premise is that a user requires connectivity to perform a function or task. An opportunity cost is the loss of benefits of a forgone opportunity. For example, if you quit your job to return to school, you incur an opportunity cost of lost income while you pursue your studies.
In the case of WLANs, the task in turn contributes to a particular benefit or contribution of the user. Examples include increasing revenues, lowering unit costs, boosting customer satisfaction, and sharing information. Failure to perform these tasks has a quantitative or qualitative cost, which is referred to as the opportunity cost.
The usable fan-out ratio of APs is approximately 30:1. Hence, the probability that an end station will not be able to obtain basic connectivity, even though throughput might be quite low, is relatively low. The opportunity cost associated with the inability to connect approaches zero. In contrast, wired connectivity has a fan-out ratio of 1:1. If the connection is in use, no other edge station can attach without completely disrupting the first user. The opportunity cost is greater than zero. Depending on the task that is prohibited from being completed, the opportunity cost can be low to very high.
For example, if you want to connect to check whether you received an invitation for a meeting that will take place in two weeks, your opportunity cost of not being able to connect is relatively low. If, however, you are engaged in a timed auction on eBay for a new motorcycle, the opportunity cost associated with not being able to adjust your bid is at least equal to your reservation price—that is, the maximum price you are willing to pay. It could be higher if the motorcycle has a qualitative (for example, emotional) value for you.
With the aforementioned in mind, now take a look at the different deployment scenarios.
The benefit of a wired LAN is that it offers end users high throughput per port. Today, dedicated 100-Mbps connectivity has become the norm for corporate LANs. Throughputs of 1 Gbps are common in the data center environment, with 10 Gbps gaining increased traction.
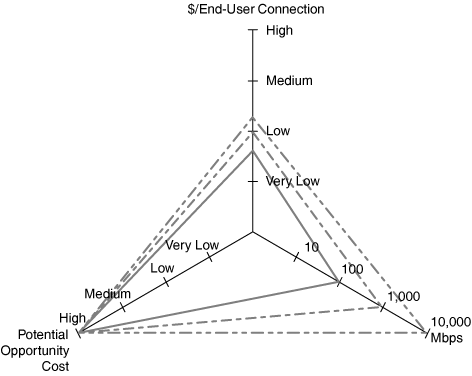
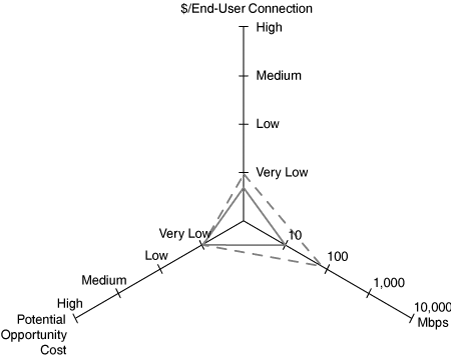
However, the dedicated throughput per port comes at the price of the limited fan-out ratio of the connection. Indeed, in a wired-only environment, the ratio of end-user devices to connections is 1:1. As such, a potentially large opportunity cost is associated with wired-only connectivity if it is deployed in environments where many end users might require simultaneous connectivity. Meeting rooms, lecture halls, and public hotspots are prime examples of such scenarios. Figure 2.8 summarizes these points in a performance scoreboard for 100 Mbps, 1 Gbps and 10 Gbps wired networks. The axes represent throughput, cost per end-user connection, and risk of unavailability of network outlet. Note that the scales of the axis are logarithmic.
The benefits of WLANs are primarily found in the mobility-enabling nature and shared nature of the communication medium. Physical roaming is possible, as long as devices adhere to specific boundary conditions, which are discussed in Chapter 5, “Guidelines for a Successful Architecture and Design,” and a single access, point can provide seamless network access for several end devices ranging from one to multiple dozens.
Because of the shared nature of the communications medium, the opportunity cost of not being able to obtain network access, is minimized. It does not, however, become zero, because the MAC mechanism employed by WLANs precludes an infinite number of stations successfully passing through a single AP. Finally, the shared nature of the AP leads to a relatively low (and variable) cost per end-user connection. Figure 2-9 summarizes these characteristics for 802.11b (11 Mbps) and 802.11g (54 Mbps) WLANs. Note that the $/end-user connection depicted is the worst-case scenario—that is, an AP with a single user—and the bandwidth is the best case (11 Mbps for 802.11b versus 54 Mbps for 802.11a and 802.11g).
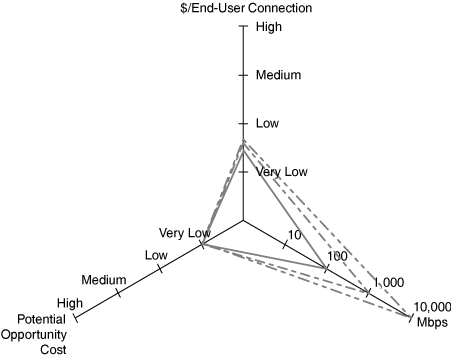
When combining both types of LANs, you arguably create an environment with the best of both worlds. By strategically selecting the locations where wireless network access is provisioned, you enable physical mobility and the ability to transparently share network connectivity among multiple end-user devices. With the latter in mind, the opportunity cost of not being able to gain network connectivity is minimized. Furthermore, if and when higher throughput is required or more stringent demands are placed on the QoS, wired connectivity remains an available option.
When you are considering the cost per end-user connection, the hybrid model spans a range that is a function of the degree of overlay created. If a full overlay model is selected—that is, every point that is provisioned with wired connectivity also has a wireless connection available—the cost per end-user connection will be higher than the wired-only scenario. This is the highest possible cost. Similarly, the lowest possible cost is that in which only wireless is available. Note that in this case, the benefits of wired connectivity are not present. As such, the hybrid model cost per end-user connection falls somewhere in between these two extremes.
Figure 2-10 shows an example of a hybrid connectivity profile.
You should consider security for WLANs to be a superset of the security considerations for traditional wired LANs. In both cases, the following four distinct challenges of securing your communication session are critical:
Network Admission Control—. Gaining access to the communication medium
Authentication—. Ensuring that the communicating parties know whom they are communicating with
Encryption—. Making sure nobody else can read the information that is being sent
Hashing—. Certifying that nobody has tampered with or modified the messages
The wireless nature of WLANs impacts these four considerations in profound ways when compared to their wired counterparts.
Wired LANs are by nature physically bound. They employ shielded or unshielded copper wires or fiber-optic cables. Connecting to an endpoint or tapping onto the wire is a challenge because it requires physical access. Hence, gaining access to a wired LAN can be made as difficult as obtaining access to a facility or somehow acquiring access to subterranean communication lines.
WLANs, however, employ radio signals as the transport medium; therefore, the medium is inherently both unshielded and unbounded. You can thus gain access to the communication medium at any point where you can tune into the radio signal. As such, the burden of securing access to the network cannot be placed on physical barriers but rather must be supported by other mechanisms.
WLANs resolve this challenge by using different kinds of solutions, including admission control mechanisms such as MAC address filters and EAP authentication. These and other mechanisms are discussed in more detail in Chapter 7, “Security and Wireless LANs.”
A challenge that is common to both wired and wireless LANs is authentication of communicating parties. Both parties need to be sure of their counterpart’s identity. This challenge is specifically related to the endpoints of communications and is independent of the transport medium and mechanism. As such, the same degrees of importance and complexity are present in wired and wireless environments.
Note
In a wired network, the user usually be confident that the jack in the wall does not lead out to the parking lot. Conversely, users information about physical location can be inferred from a user attaching to a WLAN. The user can be inside the building or outside in the parking lot.
Various mechanisms exist to support authentication. Examples include using simple keys (symmetric or asymmetric) and more complex digital signatures. Chapter 7 covers these topics in more detail.
Encryption is the process of converting or scrambling a message to something incomprehensible using a locking key so that it can be reconverted only by an authorized recipient holding the unlocking key. Think of the process as putting the message in a safe, locking it with a padlock, and sending the safe to a recipient who is the only other person who can unlock the padlock and open the safe.
Because of the broadcast nature of WLANs, every station that can tune into the signal emitted by another station can “listen in” on the communication session. As such, you should be aware of the consequences and risks of sending information in clear text over WLANs. The risk is more elevated than in wired LANs where tapping is explicit versus implicit in the case of WLANs. However, this implicit/explicit listening capability is the only true difference between the wired and wireless environment.
To avoid unintentional or intentional tapping of the communication sessions, you should use ciphers in your wireless environment to scramble the transmissions in such a way that the information is only meaningful to the sender and receiver of the information. The same considerations should be made for wired environments when selecting encryption algorithms. Consult Chapter 7 for more detailed coverage.
A final risk that exists in communication is that of a third party modifying the message while it is in transit. The broadcast nature of WLANs eases not only the tapping of communication sessions but also the ability to inject bogus messages. To identify messages that have been tampered with, you append a tag to the message. The tag is a mathematical summary of the message. The process of summarization is called hashing. Upon receipt, the receiver reconstructs the tag and compares it to the sender’s tag to determine whether the message has been tampered with.
Note
Hashing is the creation of a one-way mathematical summary of a message such that the hash value cannot (easily) be reconstituted back into the original message, even with knowledge of the hash algorithm.
For identical reasons as mentioned for encryption, the importance of hashing is greater in WLANs than in wired environments. Refer to Chapter 7 for more details on hashing.
Identifying and understanding the qualitative and quantitative benefits of investments are key prerequisites to deciding whether to proceed with those investments. This holds true independent of the investment that is being considered. Indeed, when considering investments in financial instruments such as stocks and bonds, deliberations are made about tangible benefits (quantitative benefits), such as expected returns, in addition to intangible benefits (qualitative benefits), such as familiarity with the markets for the securities, and finally the different risks (capital, market, and operational) associated with the instruments.
The same rationale is applicable for WLANs. When constructing your business case for WLANs, you need to consider three distinct dimensions:
Quantitative benefits—. These financial opportunities (that is, the possibility to monetize the benefits enabled by your WLAN) consist of direct savings through reduced capital and operational expenditures and indirect savings of opportunity costs.
Qualitative benefits—. Examples of qualitative benefits include increased comfort and productivity, improved aesthetics, and strategic aspects such as enabling upstream mobile applications.
Risks—. The risks associated with your WLAN project are related to executing the project (implementation risk), operating the WLAN infrastructure (risk of disruption), and securing the project (risk of loss and theft).
Even though ROI typically refers only to a quantitative analysis, a mutually exclusive and collectively exhaustive (MECE) approach necessitates that not only the quantitative but also the qualitative parameters and the risks of the investment are considered. A choice can then be made about the relative weights or importance attributed to each respective benefit. Indeed, you do not select a portfolio of financial instruments solely on expected returns without, for example, considering your familiarity with the underlying market for the instruments.
In the IT world, ROI typically refers to the financial assessment of an IT project. This assessment would be more correctly denominated as a cost-benefit analysis. The more appropriately named cost-benefit analysis (CBA) is a method of measuring the quantitative yield of an investment in IT assets. To avoid confusion we shall continue to use the terms ROI and cost-benefit analysis interchangeably.
When performing a cost-benefit analysis of an investment, you need to closely examine two distinct areas:
The numerator of the ratio—that is, the costs associated with the investment
The denominator, which quantifies the benefits associated with the investments
Only when both factors have been determined can a decision be made about whether the quantified benefits outweigh the quantified costs. Note the word “quantified” in the previous sentence. As we shall see, there are several costs and benefits that are either very challenging or all but impossible to quantify. An exhaustive consideration requires that these softer parameters are indeed considered in making a business decision. No information about physical location can be inferred from a user attaching to a WLAN. The user can be inside the building, or outside in the parking lot.
The following sections explore the quantitative and qualitative elements of WLANs in more detail. Finally, given the importance of financial metrics in today’s business environment, we take a closer look at decision metrics.
In the context of IT investment, an often-used term is the total cost of ownership (TCO) of the IT asset. This measure reflects all costs associated with the entire lifecycle of the asset.
As you learn in Chapter 3, the WLAN technology lifecycle can be modeled with the preparation, planning, design, implementation, operation, and optimization (PPDIOO) solutions lifecycle. As such, you need to identify the costs related to the PPDIOO lifecycle of your WLAN. The corresponding expenses will include the capital expenditures (CAPX), assuming the WLAN assets will be capitalized; the one-time costs of preparing, planning, designing, and implementing your WLAN and training the WLAN users; and the recurring costs of maintaining and upgrading the WLAN—that is, operation and optimization.
Table 2-1 provides a breakdown of the various WLAN cost components. The table is not intended to be exhaustive and provides a nominal approximation only. The sum of these terms yields the WLAN’s TCO.
Table 2-1. Total Cost of Ownership Components
Stage | Type | Item |
|---|---|---|
CAPX | Hardware | Access points |
LAN switches | ||
Management consoles | ||
WLAN NICs | ||
Power cords | ||
Cabling | ||
Authentication servers | ||
Network administration/security tools | ||
Software | AP software licenses | |
LAN switch OS licenses | ||
Management console licenses | ||
End-user licenses | ||
WLAN management tools | ||
Authentication server software | ||
Finance | Cost of capital | |
Preparation | Program management | WLAN program team resources |
Planning | Program Management | WLAN program team resources Site surveys |
Design | Program management | WLAN program team resources Engineering resources |
Consulting services | Engineering services | |
Implementation | Program management | WLAN program team resources |
Installation | Internal engineering resources | |
External engineering services | ||
Training | Operations staff End users | |
Operation | Support | WLAN management staff Maintenance |
Optimization | Support | WLAN management staff Upgrades |
Currently, the per-user TCO of a WLAN is higher than for a wired LAN. This difference is due to the operational and administrative costs of WLANs, which are typically two to three times higher than for wired LANs. As a result, WLANs should be considered mainly for their mobility and connectivity options and not for enabling savings in IT budgets. Over time, the TCO gap should narrow. Because of this current nominally higher TCO of WLANs, it is critical to identify the types and sizes of benefits that a WLAN can enable.
You need to ask two key questions when attempting to identify the benefits your organization can extract from WLANs:
Where in the organizational ecosystem can WLANs have a positive impact?
How will a WLAN positively influence the identified areas by the first question?
For the purpose of this book, we shall focus on corporate business ecosystems. The same logic can be extended to educational institutions, albeit with slight modifications to the frameworks that will be discussed in the following sections.
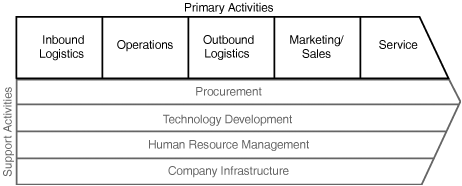
A framework that is highly applicable when determining where a WLAN will have a positive impact in your organizational ecosystem is the Value Chain framework developed by Michael E. Porter, university professor at the Harvard Business School, where he leads the Institute for Strategy and Competitiveness Porter describes the framework in his 1985 book Competitive Advantage: Creating and Sustaining Superior Performance. The framework depicts an organization as an interlinked set of primary and secondary activities that create and build value. Figure 2-11 illustrates Porter’s Value Chain framework.
Consider three different industries: manufacturing, consumer retail, and financial services. This discussion first focuses on the primary activities because this domain exhibits the greatest variability among the selected industries when it comes to the application of WLANs. Note that the distinctions are based on highly simplified views of the respective industries and only serve to illustrate the logic behind the identification of key application areas of WLANs in the respective organizations.
The manufacturing industry is characterized by the necessity for excellence in inbound logistics, operations, and warehousing of finished goods. As goods move through the value chain, the physical attributes of the goods change. The information associated with these goods changes in accordance with the transformations applied. The shop floor thus becomes a prime candidate for being enabled with WLANs. WLANs can help untether logistics and warehousing applications, thus simplifying real-time production updates, wireless asset tracking, quality assessment, and inventory logging.
In the consumer retail industry, the primary focus areas are outbound logistics (warehousing, transportation, distribution, and store operations) and marketing and sales. The consumer retail industry has been a relatively early adopter of wireless solutions because mobile devices help automate the supply chain. Handheld scanners are used to receive inventory into the store, validate shelf-label pricing, perform markups and markdowns, carry out item counts, and do store transfers.
As higher bandwidth becomes available, the wireless applications move up the value chain to sales- and marketing-related functions. Customer-facing activities such as line busting, sales assist activities, and finding product information for the customer can be greatly enhanced by having specific and relevant product information available at the point of sale. Furthermore, store managers can be released from their desks and armed with real-time information to increase their interaction with customers. WLANs thus effectively enable managers to access performance data anywhere in the store at any level of detail.
The third industry that we consider is financial services. The primary activities in the financial services industry of most importance are the marketing, sales, and service activities. As such, it is clear that an area of opportunity for WLANs exists in the financial services industry. WLANs provide the opportunity to mobilize the front office.
A domain where mobility is a key benefit is the bank branch. Roaming staff can handle simple transactions from anywhere in the branch. Service delivery is enhanced through rapid access to customer information, line busting, sales assist activities, and swift accessibility to product information that ultimately enhances the customer’s experience in terms of quality, accuracy, and promptness of service. Furthermore, as the capability to transfer ever-greater volumes of data to mobile devices increases, greater use can be made of multichannel web services delivery efforts.
Given the sensitivity of the information in the financial services industry, several challenges remain. These include security, integrity of data, and system reliability. As WLAN technology continues to mature, these challenges will be resolved, providing financial institutions with a robust and secure alternative to or extension of the traditional wired infrastructures.
The previous section illustrates the differences among industries when it comes to identifying opportune areas of application for WLANs. We first focused solely on the primary activities in the value chain, so it is now time to take a closer look at the secondary activities.
Porter defines the secondary activities as being all activities that support the value-creating primary activities of an organization. The details of the secondary activities are considered to be industry-specific and they include organizational functions such as general management, planning, legal, accounting, finance, human resources, research and development, and purchasing. This is exactly the environment in which the knowledge worker operates.
Given the reliance of today’s knowledge worker on information, it is not surprising that business intelligence and business processes have become highly dependent on IT to increase worker productivity, collaboration, and accuracy. WLANs provide the unprecedented opportunity to inject true mobility into the information supply chain.
The benefits that WLANs offer to secondary activities are many and diverse. Some of the benefits include the following:
Providing mobile data connectivity, thereby enabling workers to transparently roam among different locations without being burdened with the concern of locating a free data port.
Facilitating collaboration by making ad-hoc meetings easier because laptop computers can freely move around the office.
Enabling richer and more accurate communications sessions because information is untethered from the desk (assuming the availability of mobile computing devices).
Provisioning connectivity to temporary locations or intermittently used spaces. Examples of temporary locations include rapidly deployed new sites or disaster recovery facilities. Meeting rooms and boardrooms are examples of sporadically used spaces.
Improving aesthetics of customer-facing locations or executive meeting rooms by precluding dangling wires.
As you can see, the benefits of WLANs for secondary activities are mainly related to boosting productivity and comfort of the knowledge worker by arming him or her with mobile access to rich media content. Additional benefits, albeit of lesser extent, are associated with the ability to reduce capital expenditures on communications equipment for temporary locations and occasionally used areas. Finally, intangible benefits such as improved aesthetics are also enabled by WLANs.
Keeping these benefits in mind will help you identify specific secondary activity areas of your organization where the targeted application of WLANs makes business sense. Note that the application is not limited to a WLAN-only environment—it also includes the hybrid (wired and wireless) LAN. After you have identified the primary and secondary activities of the organization that can most benefit from WLANs, you are ready to tackle the next question.
As you’ve learned in this chapter, the benefits that a WLAN can provide are many and diverse. The variety of benefits is related not only to the place of application in the organization’s value chain but also to the type of benefits.
One potential framework for analyzing the impact of WLANs in a given application area is to consider the strategic, operational, financial, and technological dimensions. Breaking down the problem provides a framework to help define the enabling capabilities of WLANs. However, given that the goal is developing a robust WLAN business case, a different set of lenses is more conducive to structuring and presenting an exhaustive justification for WLANs.
The following sections describe three such lenses—quantitative factors, qualitative factors, and risks—to further analyze the WLAN benefits identified by the previous question.
Quantitative factors are sometimes referred to as hard, tangible, or quantifiable benefits that can be translated relatively easily into a dollar value. The realization of the financial benefits occurs through direct cost reductions, indirect cost avoidance, and increased end-user productivity. Examples include these:
Displacement of equipment costs through replacement of switches by APs
Reduction in cabling expenses
Avoidance of circuit expenditures when utilizing inter-building WLAN bridges
Employee productivity benefits because network access now follows the user, as opposed to the opposite
Ability to connect to public WLAN infrastructure (cafes, hotels, and airports)
As mentioned earlier in the “Total Cost of Ownership” section, the TCO of WLAN-only or hybrid LANs is typically two to three times higher than the wired-only equivalent. However, in situations where connectivity needs to be provided to sporadically used spaces such as meeting rooms or executive boardrooms, temporary locations, or locations where there is a high degree of variance in the number of users requiring connectivity, the cost per end user of provisioning WLANs can be lower than connectivity solutions with more expensive traditional enterprise LAN switches.
Similarly, WLANs provide an opportunity for a reduction in cabling costs. This does not, however, hold true in all situations. Cabling infrastructure is typically depreciated over 10 years. As such, its annual cost contribution tends to be relatively low. However, when temporary sites are required, the cabling cannot be depreciated over such extended periods of time. In these cases, WLANs then provide a cost-effective solution for providing connectivity, even though the expenses associated with the operation and administration of WLANs might be higher. The same argument can be made for environments that provide challenging, and hence costly, cabling situations.
The use of directional antennas enables the construction of inter-building WLAN bridges. This solution can be used as an inexpensive means of interconnecting buildings that are separated by public infrastructure and that would otherwise require the purchase of service provider-provisioned circuits. The installation, subscription, and utilization fees associated with these circuits can thus be avoided.
Staff mobility and productivity enhancements are by far the largest benefits associated with WLANs as increased productivity equates to avoided opportunity costs. The capability to remain connected to the network, independent of one’s physical location, eliminates the opportunity cost of not being able to access online applications and information. Not only does this result in incremental amounts of productive work that users can perform, but it also enables greater responsiveness and speed that these users can bring to business processes.
You can approximate an approximation of the aggregate quantified productivity benefit that is enabled by the WLAN with a two-step approach. First, you identify the total end-user base for which the benefit is applicable. You then establish the monetary benefit for each end user. Multiplying both factors yields the total productivity benefit for the organization.
You can determine the number of users who benefit from WLAN productivity enablement with the following factors:
Total number of employees (total employees)
% of employees using computing devices (percent computing)
% of computing devices that are mobile (mobile computing)
% of mobile devices that will employ WLAN (WLAN mobile)
Multiply these factors to determine the total number of WLAN-enabled users who can benefit from increased productivity:
(Total WLAN beneficiaries) = (total employees) × (percent computing) × (mobile computing) × (WLAN mobile)
Note
The number of total WLAN beneficiaries should be in accordance with the number of users who will effectively be covered by the physical footprint of your WLAN. Indeed, if your WLAN is deployed in site A, but all the potential users are in site B, no productivity benefits will be realized.
The next step is to determine the monetary value of the productivity benefits. This value is determined by considering the fully loaded cost of an average user who uses the WLAN and identifying how much time is converted from unproductive (that is, no network access) to productive (that is, with network access). This calculation, of course, assumes that the unavailability of network access is the reason for the user not being productive.
The rationale for allocating a monetary benefit is based on the following: If we assume that end users require access to online information to perform their tasks, then the time during which this information is unavailable is an entirely sunk cost—that is, during this time, the end user is in effect not contributing to the value-creation process of the organization. However, the loaded cost of the employee continues to accrue and hence there is a direct ongoing expense associated with the person’s time.
A prime example can be found in meetings. Meetings are a part of everyday organizational life. Individuals need to come together to resolve challenges collectively and collaboratively. Participants rarely arrive at the gathering place at the same time, or even on time. Several minutes are thus spent waiting for others before commencing the actual meeting. Even though one can argue that this waiting time is an opportune time for socializing with colleagues, more often than not, some more urgent matter needs attention. The ability to retain network connectivity can thus transform this otherwise idle time into value-creating time. The sunk cost of the organizational resource is now counterbalanced by a positive contribution. Thus, increasing employee productivity translates into reducing or altogether eliminating the sunk cost of idle time.
A similar example can be found in the healthcare industry. By providing physicians with the information that they require at the point of care, the necessity to shuttle between the patient and the information terminal is avoided. The sunk cost of the caretaker’s salary expense is offset by the value creation of taking care of patients.
Ideally, it would be great if you could quantify the exact monetary benefit of the value-creation process. A very accurate picture could then be developed in terms of the net contribution. However, because this quantification is next to impossible to achieve, we approximate the productivity benefit through the conversion of downtime into time spent on the primary and secondary activities of the organization. The productivity benefit enabled by WLANs is thus represented by the total reduction in sunk cost associated with non-value-contributing activities of staff because of unavailability of network access.
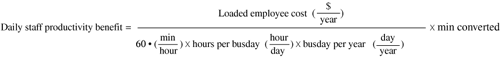
You can determine the monetized productivity benefit per WLAN user with the following factors:
Fully loaded annual cost of WLAN user (loaded employee cost)
Business days per year (busday per year)
Hours per business day (hours per busday)
Minutes per hour (min per hour)
Minutes per day of downtime converted (min converted)
The daily sunk cost per staff member that is avoided by conversion of unproductive time into value-creating time is calculated by multiplication of the these factors:
Note
Note that the first four factors—fully loaded annual cost of WLAN user, business days per year, hours per business day, and minutes per hour—are straightforward to determine. The annual loaded cost of a staff member includes salary, benefits, furniture, and equipment required by the worker, allocated expense, and so on. The Human Resources department should be able to provide an estimate of the loaded cost of a staff member.
Typical values that would be used for the number of business days in a year would be 220 or 240. The variation can be explained by the fact that the number of holidays and vacation days varies from one place to another. Similarly, a typical value for the number of business hours per day would be eight, although local variations do exist.
The number of minutes of downtime per end user that is converted into productive time by the WLAN is also the trickiest factor because it is the factor that can exhibit the highest degree of variance and hence have the biggest influence on the final outcome.
One of the options to quantify this number is to select an arbitrary, albeit conservative, number that will pass the reviewers’ “sniff test.” For example, few people are likely to object to a number such as 5 or 10 minutes a day of useful network connectivity. On the other hand, making the assumption that an end user will benefit from 60 minutes of increased productivity a day is likely to be rejected. If there would be no objection to 60 minutes, something else is seriously awry, and we would suggest that resolving this challenge should take priority over determining the viability of WLANs for your organization.
A second, and more accurate, option for determining the number of incremental productive minutes is through sampling. In statistics, the Law of Large Numbers states that the average of a random sample from a large population is likely to be close to the mean of the whole population. When combined with the Central Limit Theorem, which states that sampling distribution approaches the normal distribution independent of the underlying distribution of random variables, statistical sampling becomes a practical method for determining a robust estimate of the number of minutes that a member of the organization can convert into productive time because of the WLAN.
Fortunately, the Central Limit Theorem converges rather quickly, and a sample size of 30 or more results is a good estimate for the population mean. As such, a simple survey can be constructed in which users are asked for an estimated number of minutes per day they would be online (and hence assumed productive) with availability of a WLAN. Performing the survey on a population sample size of 30 or more will yield a relatively accurate organizational mean.
Note
No information about the skewness of the population distribution around the mean should be extracted from the sample.
After you have determined the number of users whose productivity can benefit from WLANs and the daily productivity benefit captured by these users, the daily organizational productivity benefit is computed by multiplying the two factors, as follows:
Daily WLAN-enabled organizational productivity benefit = (Total WLAN beneficiaries) × (Daily staff productivity benefit)
You can then calculate the annualized benefit by multiplying the daily benefit by the number of business days per annum—that is, by the factor busday per year.
Lastly, an indirect tangible effect of providing WLAN connectivity to the user is that it implicitly creates the capability to connect to public WLAN infrastructures. This can be considered a synergistic effect of deploying WLANs. Public WLANs denote those wireless networks that are made available to the general public. Today, they can be found in cafes, airports, hotels, and even WLAN-enabled airplanes.
Road warriors or staff members who travel frequently can be provided with connectivity to the intranet across this public infrastructure when armed with the necessary remote access tools. Virtual Private Networks (VPN) create the possibility to construct secure tunnels across the Internet. This enables the organization’s private network to be extended in a secure and transparent fashion across public networks, thus effectively providing full access to office applications. E-mail, intranet websites, and the full suite of online applications become accessible.
Note
The IT security implications for providing such remote access are considerable. Chapter 7 covers tools and methodologies for securing such environments.
As such, a similar reasoning is applicable as the one employed for determining the benefit of providing WLANs inside the organizational boundary. Time that would otherwise be spent idle can now be converted into time spent on primary and secondary organizational activities. For example, waiting in an airport lounge can be combined with reviewing and responding to corporate e-mail. Alternatively, time spent at a coffee shop before a client meeting can be used to examine updates on the competition that have been posted to the internal website.
The same algorithm can be employed for quantifying this productivity benefit. The first step is to determine the number of users who have a roaming profile. Subsequently, the benefit per user needs to be determined. We recommend determining the monthly (versus daily) benefit and annualizing it later because it is rather difficult to determine the number of minutes a day that can be converted into productive time by using public WLANs. This difficulty results from the distributed nature of travel requirements. Identifying the number of minutes per month, however, should be easier.
As before, there are two options for determining the average monthly benefit per user. The first option is to select an arbitrary, yet conservative, number that will pass a sniff test. For example, 30 minutes per month saved is likely to be a realistic and conservative estimate. The second option is to perform a survey of 30 or more frequent travelers. The result can then readily be converted into minutes of savings per day as follows:
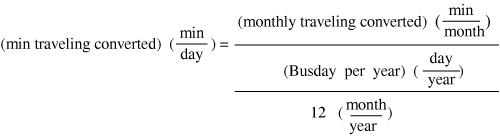
The formulas to be used in the computation are almost identical to those used for calculating the benefit of the nontraveling users. An additional factor is used to determine the number of WLAN users who also travel—that is, traveling WLAN user. This yields the following formula for determining the total number of traveling staff members who can benefit from increased productivity while on the road:
(Total traveling WLAN beneficiaries) = (total employees) × (percent computing) × (mobile computing) × (WLAN mobile) × (traveling WLAN user)
The monetary productivity benefit per traveling WLAN user thus becomes
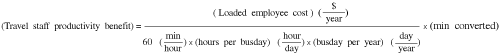
Finally, the total daily organizational benefit of converted traveling idle time is
Daily WLAN-enabled traveling productivity benefit = (Total traveling WLAN beneficiarie)s × (Traveling staff productivity benefit)
After you have determined all the parameters that contribute monetary benefits, simple summation yields the aggregate annualized monetary benefit that can be extracted from the WLAN solution. The total quantifiable benefit thus becomes
Qualitative benefits are often referred to as soft or intangible benefits. Even though these benefits are typically exceedingly hard to convert into a monetary value, they are still valuable to an organization. Indeed, decisions are often made to pursue initiatives based on strategic drivers. Examples of strategic initiatives include programs that intend to increase customer satisfaction, reduce customer churn, or provide the organization with enhanced scaling capabilities to support mergers and acquisitions (M&A)-driven or organic growth.
Earlier in this chapter, we considered the example of Starbucks, which decided to provide WLAN connectivity in its coffee shops. The rationale for this project was to enhance the customer’s experience and hence boost customer satisfaction. This increases customer loyalty, which results in more repeat business. In addition, because customers now have Internet access, the average stay becomes longer and potentially leads to more servings per customer.
The primary goal of the majority of strategic initiatives is to either increase revenues or reduce costs. The linkage between such programs and WLANs is often too complex and too long to permit easy quantification. In the Starbucks example, this translates into determining the effect of WLANs on the creation of repeat business and growing the number of servings per customer.
Even though this value could, in theory, be determined through market studies and surveys, this calculation is rarely done in practice. Stakeholders make a qualitative assessment and rely on sound business judgment to find the balance between risks and rewards.
That said, an exhaustive business case does demand that all dimensions are considered, and it is relatively hard to tell which of the benefits (that is, hard or soft) will have the greatest impact on the organization. Hence, we strongly recommend that the soft benefits be analyzed, documented, and included in the WLAN business case to minimize the risk of oversight and to maximize the business case’s credibility and impact.
Risks are a part of everyday life. They come in all forms, shapes, and sizes. Entire industries revolve around the management, mitigation, and transfer of risk. The insurance industry is built upon the transfer of risk. The financial services industry is rife with instruments whose purpose is the management and transfer of risk.
This section intends to provide a brief overview of the risks associated with WLANs and what can be done to mitigate, reduce, or transfer them. The goal is to arm you with an awareness of the various types of risks so that you can not only proactively address them in your business case but also develop a holistic framework for dealing with them. Chapter 7 is dedicated to one type of risk—the risk of IT security in the WLAN ecosystem, and Chapter 8, “Management Strategies for Wireless LANs,” covers operational risks as well as strategies and tools for managing this type of risk.
Risk is a double-edged sword. Whenever you introduce a new technology into an environment, you lower one set of risks while increasing or introducing another set of risks. In the case of WLANs, examples of risks that are reduced include the unavailability of network connectivity and incapacity to support mobile applications. Examples of risks that are introduced or increased consist of additional equipment that needs to be deployed (execution risk) and managed (operational risk) and additional IT security risk because WLANs provide a new vehicle for disruption, loss, or damage.
Awareness of a problem is the first step toward resolving it. As with any other technology, WLANs carry a diverse set of risks that span the entire lifecycle of the solution. Identification of these risks and what will be done to address them and inclusion of this information in the business justification is paramount to creating a balanced and credible basis for deciding whether to pursue the deployment of WLANs in the organization.
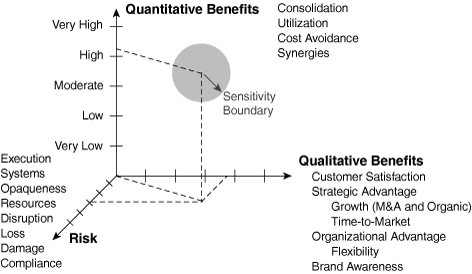
Figure 2-12 illustrates the organization’s vector in the three-dimensional space created by the tangible benefits, the intangible benefits, and the risks. The depiction not only summarizes the relative sizes of the benefits and risks but also creates the possibility to display a sensitivity boundary. Because many of the benefits and risks are based on subjective assessments, variance needs to be included to accommodate the uncertainty surrounding the parameters. As such, the illustration forms a summarizing scorecard for how much the organization can benefit from WLANs.
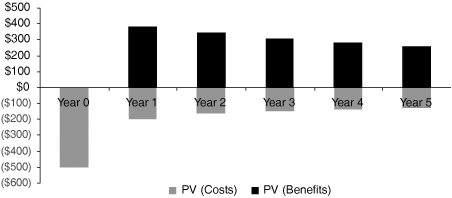
Upon completion of the identification and analysis of the costs, benefits, and risk components, you can tackle the next step of constructing the WLAN cost justification.
When it comes to business decision metrics, everybody is looking for the one tell-all metric. This silver bullet will not only precisely measure the value of your investment but also allow maximization thereof. However, just as there is no single metric for corporate performance or for the state of the economy, there is no single measure to assess IT investments and performance. A collection of measurements and assessments is required to form a relevant and accurate snapshot or projection of the performance of IT investments.
Before delving further into the quantitative ramifications of WLANs, you need to understand the position of WLANs in the IT value chain so that you can place the benefits of WLANs in a more appropriate context.
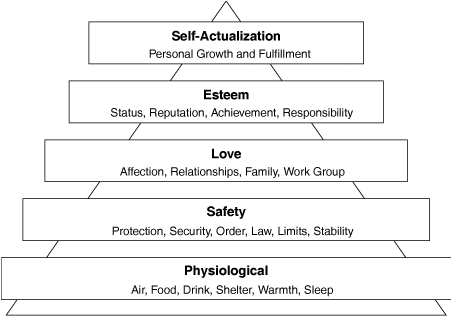
WLANs form an integral part of today’s IT transport portfolio. These assets exist to move information from a point of origin to a point of consumption. The challenge that you face when evaluating the value of such assets is that these types of assets are located at the bottom of the IT hierarchy. You can think of this hierarchy as conceptually similar to the hierarchy of human needs developed by Abraham Maslow, one of the founders of humanistic psychology, in the 1940s. Maslow posited that human beings employ a hierarchy when it comes to fulfilling their needs. The precondition for fulfilling higher-order needs is that lower-order, more basic needs must be met first, as shown in Figure 2-13.
Maslow’s model begins with the fulfillment of physiological needs, such as thirst, hunger, and other basic needs. After physiological needs are met, humans seek to satisfy needs involving physical safety, such as protection from bodily harm. After safety is obtained, Maslow then conjectured that humans act to fulfill their needs for belonging and affection. The next stage in the model is the need for esteem, which includes self-esteem, respect, and recognition. The final phase that humans seek to realize is the need for self-actualization. This includes such things as self-fulfillment and job satisfaction.
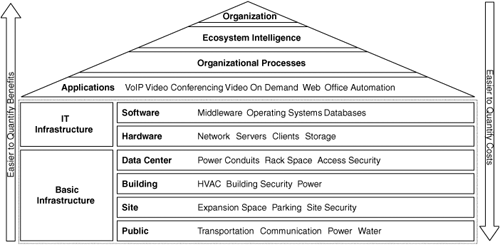
Fulfillment of each level is sequential in nature, suggesting an intrinsic need to satisfy the more basic needs before moving to the next level. Maslow’s hierarchy of needs is a classic model in human behavior. But why is this conceptual model relevant to the IT space? Maslow’s concept can readily be mapped to the corporate or institutional ecosystem. Figure 2-14 illustrates this high-level mapping.
The basic needs to be fulfilled for any organization include the availability of basic infrastructure. This refers to fundamentals such as power, transportation, and water from a public infrastructure point of view; parking space and physical security from a site perspective; power, structural integrity, and air conditioning for buildings; and finally items such as rack space, fire control, and access security for data centers. Figure 2-14 refers to these components as basic infrastructure.
Only after the requirements for basic infrastructure have been met can attention be turned to identifying the necessities in terms of IT infrastructure. This includes both hardware and software. Examples of hardware include the full range of IT transport, compute, and storage assets—that is, network devices, servers, clients, and storage arrays. Software includes middleware, operating systems, and database systems that provide the intelligence to manage the hardware and raw information. No meaning is associated with the information at this level in the hierarchy. That is the responsibility of the next level.
The next stage in the model is the need to provide meaning to the information. This is achieved through applications. As the raw information is moved, transformed, and stored, different applications enable the attribution of semantics. The information now takes on such heterogeneous forms as a phone call, a video session, an e-mail, or a purchase order.
The information presented by the various applications is in turn used by a variety of organizational processes that the organization engages in while performing the primary and secondary activities. The organizational processes provide the ecosystem intelligence that allows the organization to sense and respond to changes in its internal and external environment. Finally, armed with this ecosystem intelligence, the organization can pursue its primary goal, which is the creation of value.
This hierarchy is relevant within the context of developing an ROI or cost justification for wireless networks because of the enabling character of WLANs. That is, the majority of benefits that WLANs create is not on the same level in the organizational hierarchy. The hierarchy enables you to make this intra-level relationship between WLAN costs and organizational benefits explicit.
For some types of assets, there is a direct relationship between the costs associated with the asset and the benefits that can be extracted. Consider, for example, manufacturing equipment. The TCO of this equipment includes all costs associated with the purchase, installation, and operation of the equipment. Examples of benefits could include an increase in production velocity (such as more widgets per minute) or a decrease in cost of goods sold (COGS) as raw materials are used more efficiently. One could postulate that the costs and benefits are at the same level in the hierarchy of organizational needs. The benefits are in essence direct.
Now consider WLANs. The main benefits of WLANs can be derived from their enabling character. They enable mobility of staff and applications, which translates into increased productivity. In some cases, WLANs translate into lower cabling or equipment expenses. However, this is more the exception than the rule because the operational cost is typically higher than for wired LANs. Hence, we find that the costs are at one level of the hierarchy, while the benefits are located at a higher level. The benefits are indirect.
A good analogy can be found in electrical wiring. The cost tied to the acquisition and installation of electrical power is relatively straightforward to determine. However, the quantitative benefit is next to impossible to compute. Indeed, electrical power is an enabler. At home, it permits the use of electrical appliances such as televisions, dishwashers, and vacuum cleaners. In an organization, it allows the use of lighting and computers. As such, electricity has an enabling character because the benefits that it enables are higher up the hierarchy of needs. The same is true for WLANs.
The hierarchy of organizational needs is important for two distinct reasons in the construction of WLAN cost justifications. First, it provides a framework for defining the boundary of what must and what can be included in the analysis. You can include benefits that are higher up the hierarchy either in a quantified form as demonstrated earlier for staff-member productivity or in a qualified form as was the case for increasing customer satisfaction.
Second, the framework explains the linkage between the WLAN and its application points. As one moves higher up the hierarchy, it is implicit that the quantified benefits become more abstract. They are also characterized by an ever-greater degree of subjectivity. However, after the linkage becomes clear, a higher degree of comfort with the benefits included in the cost justification should result.
After you have defined which benefits are to be included in the organizational justification of WLANs, it is time to consolidate the cash flows of the identified costs and benefits into metrics that are meaningful to the decision makers. Because these metrics reflect absolute monetary terms, the benefits included are limited to those that have thus far been quantified.
The following are the standard metrics for evaluating cash flows associated with costs and benefits:
ROI—. The average expected cash flow over the period of the project divided by the initial investment outlay. ROI provides a satisfactory method of evaluating an investment over a short period of time. ROI does not take into account the time value of money.
Payback period—. The period required to recover the initial investment of the project. This method of evaluating an investment does not consider all cash flows and does not discount the cash flow. This method might not be appropriate for evaluating an investment over an extended period of time.
Net Present Value (NPV)—. The Present Value (PV) reflects what a future sum of money is worth today, given a particular rate of return (and inflation). NPV expresses the net value of costs and benefits in today’s monetary terms that is created or destroyed by an investment. It is computed by taking the PV of the expected future cash flow of an investment and subtracting the initial investment cost. Alternatively, the NPV can be determined by subtracting the PV of all cash flows related to costs from the PV of all cash flows from benefits.
Internal Rate of Return (IRR)—. The interest rate that equates the PV of the expected future cash flow to the initial investment outlay, where the NPV is equal to zero.
The next sections take a closer look at each metric by using a numerical example. The sample cash flows shown in Table 2-2 are for illustrative purposes only and are not based on actual WLAN cases.
The ROI is a key indicator of an investment's value. It expresses the relative total gain of the project compared to the total cost. Its computation is very straightforward and is performed by dividing the cumulative expected benefit by the cumulative cost over the analysis period of the WLAN project. The ROI formula is as follows:
ROI = Total cumulative benefit / Total cumulative cost
The formula yields the expected net return on every monetary unit spent. For the cash flow example in Table 2-2, the ROI is this:
ROI = $2000 / $1500 = 133 percent
In other words, for every dollar spent, there is a net return of $1.33.
The simplicity of the ROI calculation is its strength. It generates an easy-to-comprehend ratio. However, it has two considerable drawbacks. First, ROI does not consider the time value of money. The golden rule in finance is that a dollar today is worth more than a dollar tomorrow. This is because cash can accrue interest in a risk-free fashion over time when invested in a risk-free instrument such as U.S. treasury bonds. Additionally, there is the requirement for investing the cash in a risk-free instrument because cash hidden under the mattress does not accrue interest.
Note
This reasoning assumes that the probability of default of the U.S. government is zero. Let us plainly accept that assumption.
Hence, future cash flows should be adjusted in value to reflect their true value today. These future outgoing or incoming cash flows should in effect be discounted. The later section “Net Present Value” delves deeper into this topic. Because ROI does not consider the time value of money, it tends to overestimate the return generated by the investment because the nominal future cash flows are inflated in real terms.
A second drawback is that ROI masks the relative sizes of the cumulative cash flows. An investment of $100,000 that returns $133,000 has an ROI of 133 percent. Compare this to an investment of $100,000,000 that yields a monetary benefit of $133,000,000. Yet again, we find an ROI of 133 percent. It is clear, however, that very different considerations will be made in the latter case. The absolute size of the investment will result in unlike deliberations about risks and will drive very different decision criteria.
Another calculation that is easy to understand is the payback period. The payback period defines the breakeven point of a project and is typically quoted in months. The timer is started at the beginning of the project, and it is stopped when the cumulative benefits exceed the cumulative costs.
For the example mentioned in Table 2-2, the payback period results are shown in Table 2-3.
Figure 2-15 illustrates the breakeven point of costs versus benefits.
Table 2-3 illustrates that the breakeven point should occur at some point after year 2. If you assume a linear distribution of costs and benefits on an annual basis, you can compute the exact point of intersection.
The line section depicting the cumulative costs between year 2 and year 3 goes through the points with coordinates of (year, cost), which in this case is (2, 900) and (3, 1100). As such, the line is represented by the equation:
(X – 2) / (3 – 2) = (Y – 900) / (1100 – 900)
or
Y = 200 × X + 500
Note
The function that describes a line that goes through coordinates (a1,b1) and (a2,b2) is constructed as follows:
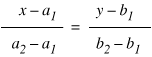
Similarly, the line depicting the cumulative benefits that goes through the coordinates (2, 800) and (3, 1200) is represented by the equation:
(X – 2) / (3 – 2) = (Y – 800) / (1200 – 800)
or
Y = 400 × x
Solving both equations for X results in this:
400 × X = 200 × X + 500
or
X = 2.5 (years)
Multiplying X by 12 results in the number of months for the payback period, which is 30 months for this example.
Payback period is important because it measures the duration to the point that the investment starts generating positive cash flow. The further out in time this breakeven point is, the more risky the project should typically be considered.
Finally, payback period has its drawback in that it communicates nothing about the return size. It only measures the time to a positive return.
The “Return on Investment” section introduced the time value of money concept. This concept is based on the fact that cash that is invested today will increase in value by some future date through the accrual of interest. Because of this accrual of interest—and interest on interest—a cash flow today is worth more than the same cash flow in the future. The idea is that you can invest the cash that you receive today and accrue interest on it. If you receive the same principal amount in the future, you have the opportunity cost of the interest that you miss out on. Hence, cash today is worth more than the same amount of cash tomorrow. The exact amount by which these cash flows differ depends on two parameters:
The interest rate, which shall be further discussed shortly
The number of compounding periods
Interest in its turn accrues interest with time, and hence there is a compounding effect.
The discounting of future cash flows to their PV enables the direct comparison of present and future cash flows. The cash flows have been normalized in time to represent today’s value in monetary terms. NPV refers to the fact that the PV of all outgoing cash flows—that is the PV of the costs—is subtracted from the PV of the incoming cash flows—that is the PV of the benefits. The result is the “net” value today.
To determine the PV of a future cash flow, identify the exact time of the cash flow so that the correct number of compounding periods can be established. Next, select the right discount rate.
One option for selecting the discount rate is to set it equal to the interest rate that could be earned elsewhere by investing the cash. Depending on risk averseness, the cash could be invested in risk-free U.S. government bonds, stocks, or complex instruments such as derivates. Each of these instruments yields a particular interest rate that is related to the degree of risk associated with it. Because the cash spent on the project will not be invested in other instruments, it creates an opportunity cost. The interest rate of this opportunity cost is the basis for the discount rate.
Alternatively, the discount rate can be set to the Weighted Average Cost of Capital (WACC) of the organization. The WACC reflects how much it costs your organization to borrow money over time. It is a function of many different factors, including the risk free rate, the organization’s cost of debt, the cost of equity, the capital structure (debt/equity ratio), and the tax rate. We suggest that you ask your finance department to provide you with the WACC for your organization.
Either the interest rate of the opportunity cost or a risk-adjusted discount rate can be used as the PV discount rate for the future cash flows. Given that higher discount rates result in smaller PVs, the discount rate can be biased upward or downward to modify the project’s risk profile. Higher discount rates should be employed for riskier projects, whereas lower discount rates are more appropriate for less risky initiatives.
The formula to compute the PV of a cash flow that occurs in year m, given a discount rate of r, is this:
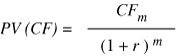
The present value of a series of annual cash flows that start in year 0 and end in year n is computed, assuming the discount rate r, as this:
The formula can be applied to our example to compute the NPV in two different ways. Either the PV of the cash flows of the costs can be subtracted from the PV of the cash flows of the benefits, or the PV of the net annual benefits can be computed. For this example, we assume a discount rate of 10 percent. The calculation of the PV of the net annual benefits is shown in Table 2-4.
Table 2-4. Present Values of Sample 5-Year Cash Flows of WLAN Investment
(In thousands) | Year 0 | Year 1 | Year 2 | Year 3 | Year 4 | Year 5 |
|---|---|---|---|---|---|---|
Total Costs[*] | ($500) | ($200) | ($200) | ($200) | ($200) | ($200) |
PV (Costs) | ($500) | ($182) | ($165) | ($150) | ($137) | ($124) |
Total Benefits | $0 | $400 | $400 | $400 | $400 | $400 |
PV (Benefits) | $0 | $364 | $331 | $301 | $273 | $248 |
Net Benefit | ($500) | $200 | $200 | $200 | $200 | $200 |
PV (Net Benefit) | ($500) | $182 | $165 | $150 | $137 | $124 |
[*] All totals are in thousands | ||||||
Compare the nominal cash flows represented in Figure 2-16 with the PV of these respective cash flows illustrated in Figure 2-17. The impact of compounded discounting can clearly be seen in that it decreases PV of cash flows that are further out in time.
Application of the formula to the net benefits of our example yields the following:
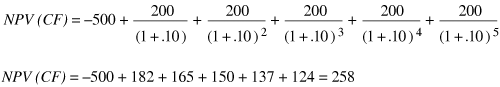
Note
Fortunately, Microsoft Excel provides a built-in function for NPV computation. The function is named NPV and takes the discount rate and cash flows as inputs. It should be noted that the cash flows used in the formula start in year 1, not year 0. Hence, when calculating the NPV, you need to add the cash flow of year 0 to the result of the function. For our example, the Excel formula becomes
Net_Present_Value = –500 + NPV (10%, 200, 200, 200, 200)
The Excel NPV function takes discrete values, cell names, or cell ranges as inputs.
Because the Net Present Value computation increases the effect of current cash flows and decreases the impact of future costs and benefits, the following general conclusions can be drawn:
Projects with low initial expenses and higher initial benefits generate higher NPVs.
Projects with high initial expenses and benefits that increase over time produce lower NPVs.
Determining the NPV of a project is an often-used and accurate method for determining the financial viability of the project. The use of an appropriate discount rate not only ensures that some degree of risk is accounted for but also generates a quantified metric in today’s monetary terms of the net expected gain.
However, NPV is not perfect. One of the pitfalls is that projects that generate enormous savings far in the future—cash flows of benefits look like a hockey stick—will result in NPVs that are substantial. You should remain aware of the simple fact that the further out in time you project, the more uncertainty is associated with the projection. The use of a constant discount rate cannot capture this issue. One potential remedy would be to use variable discount rates with higher discount rates further out in the future to accommodate for the additional uncertainty. Hence, you should consider not only the NPV but also the profile of the cash flows to identify whether a project that is financially attractive in NPV terms is nonetheless too risky.
The IRR calculation looks at the current and future net cash flows from a proposed project and determines an interest rate such that the NPV of the project becomes zero. The rate should be thought of as the interest rate that another investment would have to exceed to become more interesting than the project under consideration.
In mathematical terms, the IRR is the discount rate that makes the NPV equal to zero. The formula becomes
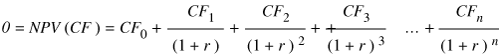
The cash flows are given, and the discount rate r needs to be computed. Given the fact that zeros of fourth and higher-order polynomials cannot be determined algorithmically, they need to be approximated using computer programs that perform iterative approximations. These programs guess values and perform continuous refinements until the equation results in zero or a number very close to zero.
Note
Microsoft Excel has a built-in function for computing IRR. Not surprisingly, the function’s name is IRR, and its parameters are the cash flows starting with year 0. For our example, the Excel formula becomes
IRR = IRR (-500, 200, 200, 200, 200)
The Excel IRR function takes discrete values, cell names, or cell ranges as inputs.
For the sample cash flows, the discount rate (that is, the IRR) that results in an NPV of zero is 20 percent.
As is the case for the other metrics, IRR has its weakness. Similar to ROI, IRR does not provide information on the absolute value in monetary terms of the benefit generated by a project. A project with an NPV of $1,000,000 can have an IRR of 29 percent, as can a project with an NPV of $258.
Today’s environment is characterized by an increased degree of financial scrutiny and accountability. The necessity for a holistic and robust business case is more dominant than ever before. As such, an exhaustive understanding and assessment of all the costs, benefits, and risks associated with WLAN deployments lies on the critical path to successfully using WLANs in your organizational ecosystem.
Business leadership is not limited to cost control. Strategic drivers such as increasing customer satisfaction or decreasing customer churn drive the top line. Increasing or sustaining the top line is at least as important as reductions in operating expenses.
This chapter focused on the strategic, tactical, and financial business considerations when evaluating WLAN solutions for your institution. It introduced you to methodologies and frameworks that facilitate the process of business-technology alignment and the identification of key application areas of WLANs within the organization. The strategic, operational, financial, and technological impact of WLANs on the value-creation process of your organization was touched upon, as were the benefits and constraints of wireless compared to wired solutions.
This chapter also covered the process of performing a thorough cost-justification analysis. Parameters such as TCO and benefits that can readily be quantified were discussed. Furthermore, intangible benefits that are related to the strategic impact of WLANs were revealed. Finally, risks associated with WLANs were clarified to ensure an exhaustive business case.
Finally, this chapter explained the standard methods for consolidating the cash flows of the identified costs and benefits into metrics that are meaningful to decision makers and stakeholders. The construction of the ROI, payback period, NPV, and IRR was further explained as were the pros and cons associated with each metric.
Armed with this knowledge, you are well positioned to tackle the next phase in constructing your WLAN business case. These phases consist of determining the specific WLAN design for your organization and strategies for effectively implementing and operating them. These are the topics of the next chapters.