Who’s Watching What You Do?
Abstract
This chapter talks about what information you should and shouldn’t be storing online.
Keywords
Facebook; challenge questions and answers; online
Information in This Chapter
This chapter talks about how others including other people and various governments are able to see what you are doing online. We will also talk about some of the things that you can do to prevent others from watching what you do online and why you may or may not want to do these things.
How can someone watch what I do?
When it comes to what people can see you are doing on the Internet, the amount of what they are watching will totally depend on how secure you have made your online life and how determined they are to see what you are doing. There are two basic tasks that you do on the Internet, sending and receiving e-mail and browsing the web.
Many of the solutions to preventing people from viewing what you are doing online will be rather technical. Throughout this chapter, they will be broken down into the most digestible parts possible. One of the problems with a lot of these sorts of highly technical solutions is that they are made by IT professionals for IT professionals without very much thought being given to how to make these solutions more accessible to the general public at large who doesn’t necessarily have the technical experience or knowledge to configure these solutions. Most if not all of these solutions have documentation, but often, this documentation is written for IT professionals and often makes a lot of assumptions about the technical experience of the reader.
When it comes to monitoring e-mail that someone sends and receives, there are a couple of different methods that someone can use. The easiest is going to be to install something on your computer that tracks all the e-mails that are received by you and sent to you. There are a variety of applications out there that can do this. Some are easy to detect and others are much harder to detect, with some being detected by antivirus software and some not being detectable by antivirus software. While you might consider all of these sorts of applications as viruses, some applications in this category are actually legitimate software packages out there that do the sort of things that are being talked about in this section.
When monitoring software is installed on the computer that they are monitoring, the software works in few different ways. One option is to monitor the network protocol that is used by all e-mail clients to talk to the e-mail servers. In the past, this method would have been mostly useful, but over the past few years, most e-mail servers today require encrypted connections so monitoring the network ports isn’t all that effective.
The second option that is available to the software developer who creates the monitoring software is that he or she can talk to the e-mail software using the application programming interface (API), which has been published by the e-mail software developer. This API would allow the person who is writing the monitoring software to read any e-mails that the software sends or receives. Because the monitoring software is asking the e-mail software for the e-mails after they have been received from the server, any encryption that is used in the communication process between the server and the user's computer would be bypassed.
A third option that would be available to companies such as the Internet backbone providers would be to monitor the network traffic at the e-mail server side. While the network traffic between the e-mail application and the e-mail server is most likely encrypted, odds are the network traffic between the e-mail server that you use and the e-mail server that the person you are e-mailing uses isn’t encrypted as shown in Figure 6.1. While some e-mail servers are configured to communicate with other e-mail servers using an encrypted connection, this is not the default communication method.
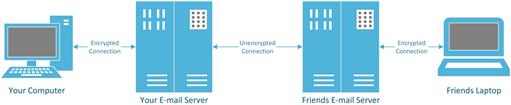
Figure 6.1 Diagram showing which connections are typically encrypted and which connections are not typically encrypted.
Communication between e-mail servers is not encrypted by default. However, it is possible that e-mail servers can be configured to request encrypted connections when transmitting from one e-mail server to another, but since it is not a default setting, this configuration is often skipped. Unfortunately, there is no way as a user of the e-mail server to see if the server is configured to request an encrypted server to server connection.
Another way that e-mails can be viewed is by the Internet service provider that owns the e-mail server that the mail is delivered to. Employees at the Internet service provider such as the technical support department and the systems administration team would have access to view the e-mails within the customers e-mail box. Depending on how the security at the Internet service provider has been configured, these employees may only have access to view the header information of the e-mails that would include who sent the e-mail, who received the e-mail, the subject of the e-mail, and when the e-mail was sent and when it traveled through each of the e-mail servers that handled the e-mail.
In addition to the servers that are used to send the e-mail and the server that receives the e-mail as shown in Figure 6.1, there could be any number of e-mail servers between the two servers that we can see in some sample e-mail headers in Figure 6.2.
The e-mail headers shown in Figure 6.2, which are from an e-mail that I received from a mailing list that I’m subscribed to, are read from bottom to top with each server that receives and processes e-mail starting with “Received:”. In the case of this example, we can see 16 different servers that the e-mail past through from the person who sent the e-mail until it was received by my mailbox. The e-mail headers show that the e-mail passed through a variety of servers each with their own domain name and appearing to be from a few different companies. There are a variety of reasons why different companies handled this e-mail. The sending company could have some of their antivirus services outsourced to another company that would mean that this additional company would need to receive the e-mails, or the third company could be used to help manage outbound e-mail routing, or it could simply be that the company has a very large e-mail sending infrastructure because they have to be able to handle billions of e-mails per day, and so they have configured a large complex system to assist them in the handling of these e-mails.
All these servers that are processing this e-mail as it was moved from the sender to my e-mail box could have been configured to store this e-mail for any period of time, allowing the administrator to view the e-mail without the knowledge of the person that sent the e-mail or from me the receiver of the e-mail.
Web browsing traffic
Viewing the web traffic or someone who is browsing the Internet isn’t quite as easy as viewing their e-mails. The primary reason for this is that e-mails sit on servers and can be viewed at any time that they are sitting on the server so long as the person trying to view them either has the username and password for the e-mail account or has the needed rights to the e-mail server by working for the company that owns the server that the e-mails were received by or the server that they were transmitted through.
With web browsing, the network traffic isn’t being processed through a large number of servers. Network traffic from browsing the Internet also happens in real time. After the webpage has been requested and transmitted from the server to the user's computer, there’s no trace of the specific data that were transmitted between the user and the server.
Intercepting traffic directly on your machine
The easiest way for someone to track the specific webpages that a specific person is looking at online is to install software on the user's computer that tracks the URLs and to capture a full copy of the webpages that the user is looking at. The biggest reason that this is the best solution for tracking a user's online activity is because many websites on the Internet require a secure connection between the user's computer and the web server. This secure connection means that the web server encrypts the network traffic before it is sent to the user's computer, and if it is intercepted before being relayed to the end user, the certificate will not match correctly and the user's web browser will inform them that the certificate does not match the web server correctly.
Like capturing e-mail on a user's computer, there are a wide variety of software packages that are available to capture web browser traffic. Some of these are legitimate software packages that can be used by parents to monitor what websites children are visiting and who they are talking with in forums and on Facebook, etc.
Intercepting traffic on the Internet
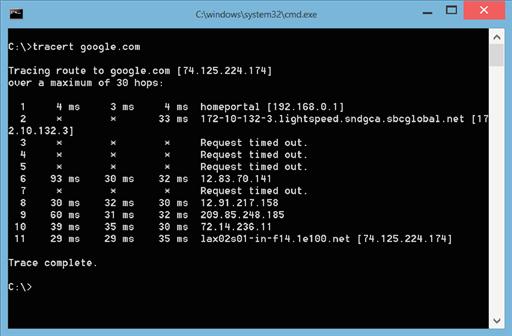
Capturing people's network traffic as it is transferred between the web server and the user's computer is quite a complex task. The reason that this task is so complex is because of the massive amount of data that are transferred across the Internet at any given time and the fact that capturing a user's specific network traffic requires capturing that network traffic on one of the routers between the web server and the user's computer. These routers are very secure and managed by large Internet service providers who specialize in managing these routers. Each website that is accessed by a user has a different set of routers between the user and the website. We can see the list of routers or at least some of them by using the “tracert” command on Windows computers or the “traceroute” command on Linux and Mac OS X computers. The output from the tracert command is shown in Figure 6.3.
Some of the routers between the user and the google.com website are configured to not show themselves. This is why those servers report back a “Request timed out” instead of responding with their name and IP address.
In order to capture the most network traffic possible that was being transmitted to the user's computer, monitoring closer to the user would need to happen. In this case of this sample user shown in Figure 6.3, this would mean capturing the data from the router in the sbcglobal.net datacenter (which is also known as AT&T). Assuming that these data could be captured by someone, much of these data would be encrypted. Websites such as banking websites, shopping websites, and even many social networking websites all secure the data using Secure Socket Layer (SSL) encryption. This means that the data that are captured from the network would be encrypted and unreadable by the person that captured it, unless they were able to break through the encryption that was used.
How can a government watch what I do?
Governments are the biggest threat when it comes to monitoring data on the Internet as a whole. This is because they have massive resources available that they can call upon either by normal monitoring means like monitoring data via network routers as discussed earlier, by inserting rouge code into the operating systems of routers, or by having companies insert backdoors into data encryption code through threats or legal mandate.
The chances of a government putting rouge monitoring code into network routers are a minimal risk. The companies that run the public Internet are very careful when it comes to where they purchase their routers and other networking equipment from. Because the supply chain is ensured, with these companies typically purchasing their equipment directly from the companies that build the hardware, there is very little risk of the equipment being compromised.
In late 2006, the companies that run the public Internet were found to be capturing all of the Internet traffic that passes through their networks for the US government. The most well-known example of this was AT&T's monitoring of their Internet traffic via room 641A in their facility at 611 Folsom Street in San Francisco, CA, which was at the time owned by SBC and rented to AT&T. The existence of this room within this facility and its use were revealed by an AT&T employee and were the subject of a 2006 class action lawsuit against AT&T. Rumors of other rooms such as this one at other facilities exist, but the existence of other capture rooms like this has not been confirmed. Even though a lawsuit was filed, no information about room 641A or the other rooms like it that may exist was ever brought to light. This is because during the course of the legal proceedings between the Electronic Frontier Foundation (EFF) and AT&T, the US Congress granted the Internet service providers that were involved in this wiretapping program retroactive immunity from for their involvement. More details can be read about this room and the resulting law suits at http://basicsofdigitalprivacy.com/go/room_614a.
The data encryption that is used to secure basically everything important that we do on the Internet was not designed by any specific government or government agency. Because the data encryption wasn’t designed or built by any specific government or their agencies, they were not able to directly insert any backdoors into the data encryption process. However, it appears as of the writing of this book in the summer of 2013 that the National Security Agency (NSA) has been able to get some the technology companies that have built a lot of the data encryption that is in use today to install some sort of backdoor into their data encryption technologies.
There are several excellent articles on the Internet. Two of the most accessible that include links to several other articles can be found at http://basicsofdigitalprivacy/go/nsa1 and http://basicsofdigitalprivacy/go/nsa2.
SSL versus the NSA
The NSA has been working hard to break the encryption called SSL, which is used to secure all encrypted Internet traffic. The reason that they want to break the protection that is provided by SSL is so that they can monitor and track those who wish to attack the United States. The side effect of their attempts to break SSL encryption is that they would be able to record and view the web browsing of American citizens, which, as of the writing of this book, is questionably legal at best. By breaking the SSL encryption, not only online shopping but also the secure virtual private networks, which are used to encrypt corporate communications between company offices and for remote workers, are compromised.
According to reports available in the summer of 2013, the NSA has devoted large amounts of money and computing power to the task of breaking SSL encryption algorithms. This is being done by the NSA by building very large and powerful supercomputers which they use to attempt to break the encryption on the data which has been encrypted via the SSL specification.
Through various methods, the NSA has built up a huge collection of encrypted data. Through documents that were released in the summer of 2013, some of which can be read at http://basicsofdigitalprivacy.com/go/nsa3, it has been exposed that starting in 2010, the NSA made breakthroughs in breaking the SSL encryption, allowing them to access “vast amounts” of data that have been collected over the years.
According to documents that have been released around the summer of 2013, the NSA does have some policy data collection. According to these policies, available for viewing at http://basicsofdigitalprivacy.com/go/nsa5, data collected on US citizens can only be kept for up to 5 years or until such time that the communication is found to be not relevant to the original basis of the data collection. This policy however only applies to unencrypted information. Data, which are encrypted, that the NSA has collected can be kept indefinitely until the time that it can be decrypted and analyzed. Depending on how well the NSA has done with breaking the entire SSL encryption standard, this means that encrypted data could be kept on servers operated by the NSA for years or decades.
How can I stop people from watching what I do?
Now that you’ve read about how easy it is for others to monitor your online activities, your next question should be how to prevent people from monitoring Internet activities.
Preventing people from viewing e-mails that you are sending requires a two-phase approach. The first is to properly secure your computer as discussed in Chapter 4 and your home computer network as discussed in Chapter 3. This is your best chance of making sure that no one is able to install anything on your computer that can capture your e-mails. When it comes to the people who receives the e-mails that you send or the people that e-mail you, there’s nothing you can do about their computers.
As for preventing people from intercepting e-mails in transmit, this is something that we can do something about quite easily. When possible, we want to be sure that we are using secure encrypted communications to communicate between the e-mail application and the e-mail server. When using mail services like Gmail or Yahoo! Mail and accessing the e-mail's webmail application, the connection is going to be secured by default using the SSL protocol. If you are using a third-party e-mail client such as Outlook and Eudora, the use of the SSL protocol is required when sending and receiving e-mail. The instructions for setting up e-mail clients securely are fully documented on the Internet and can be found at http://basicsofdigitalprivacy.com/go/yahoo_mail for the Yahoo! Mail instructions and at http://basicsofdigitalprivacy.com/go/gmail for Google's Gmail service. For other services, you’ll need to check with the technical support department of your e-mail service.
Securing the communication between the e-mail client and the e-mail server is only half of the work. We still need to ensure that the e-mails are encrypted as they travel from server to server over the Internet. This is done with an encryption processed called Pretty Good Privacy (PGP). Using PGP in order to secure your e-mails requires both doing some prep work on your computer and giving people that you will be e-mailing some information so that they can read your e-mails.
The first step in setting up PGP is to ensure that your e-mail client supports PGP. In order to do this, you’ll need to check with the manual that comes with your e-mail software or contact their technical support department.
Setting up PGP on Microsoft's Outlook 2013
The first step to getting PGP setup and configured in Microsoft's Outlook 2013 e-mail client is going to be to install some additional software on your computer. You’ll need to download and install two specific pieces of software. The first is the Outlook Privacy Plugin that can be found at http://basicsofdigitalprivacy.com/go/outlook1 and a piece of software called Gpg4win that can be found at http://basicsofdigitalprivacy.com/go/outlook2. Make sure that Outlook is closed when installing these two applications.
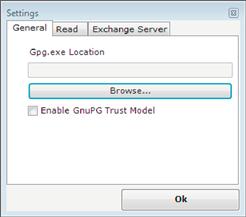
After installing the Outlook Privacy Plugin and Gpg4win open Outlook, you should then be prompted with a dialog box that asks you to locate the gpg.exe application that should be similar to Figure 6.4. By default, the GPG application will be located in C:Program FilesGNUGnuPGpub.
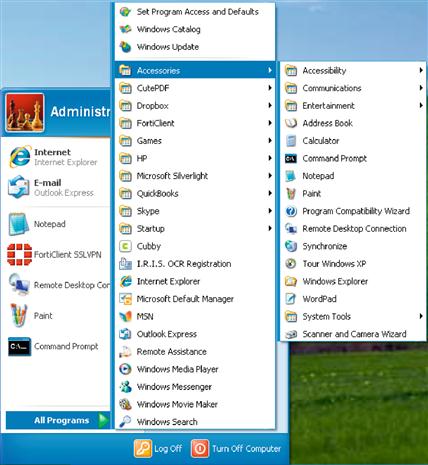
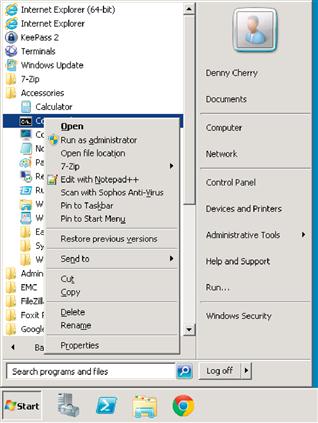
The next step in the process is to include a public and private key pair. These public and private keys are what are used to secure the e-mails. The private key is used by the sender to encrypt the e-mail, while the public key is used by the receiver to decrypt the e-mails. Generating these keys requires that a command line application be used to create these keys. This is done with the GPG application. To do this in Windows XP and Windows 7, click on the Start menu, select “All Programs,” and then select Accessories. If using Windows XP, select the “Command Prompt” option as shown in Figure 6.5. If using Windows 7, right click on the “Command Prompt” option and select “Run as administrator” as shown in Figure 6.6.
If using Windows 8, bring up the Start menu by placing your mouse cursor in the lower right-hand corner until the Start menu button appears as shown in Figure 6.7 then click on the Start button.
If using Windows 8.1, click on the Start button usually located in the lower right-hand corner of the screen, shown in Figure 6.8.
When using Windows 8 or Windows 8.1, the Start menu will have now appeared. At this point, simply type “cmd” and the Command Prompt icon will be shown on the screen that will be similar to Figure 6.9.
With the Command Prompt icon from Figure 6.9 visible, right click on the Command Prompt icon and then select the “Run as administrator” option from the menu that appears at the bottom of the screen as shown in Figure 6.10.
From here, the instructions for Windows XP, Windows 7, Windows 8, and Windows 8.1 are the same.
Within the command line window that has opened change to the directory that has the GPG application. This is done with the CD command as shown in Example 6.1 and pressing the Enter key.
cd "c:program filesgnuGnuPGpub"
After changing into the correct directory, run the gpg command and specify the –gen-key command as shown in Example 6.2. Note that there are two dash marks in front of the gen-key switch.
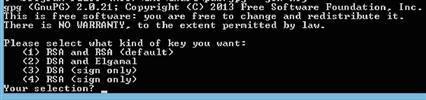
A menu will now appear that gives four different options as shown in Figure 6.11. Option 1 allows you to create RSA keys, which is the recommended option. Select this option by pressing the number 1 and pressing the enter key.
The next step is to enter the key size that you would like to use. The default is a key size of 2048 bits. The higher the number that is used for the key length, the harder it will be for someone to break through the encryption. The trade-off between high levels of encryption is that they require high amounts of CPU power to encrypt and decrypt the data. For maximum protection, a key length of 4096 bits is recommended.
The next step asks how long the key should be valid for. The default is for the key to never expire that requires an input value of 0. To specify expiration of the key in a number of days, enter a number. To specify the key expiration in a number of weeks, enter a number with a “w” after it. To specify the key expiration based on months, enter a number with an “m” after it. To specify the key expiration based on years, enter a number with a “y” after it. If the key is set to expire, that means that e-mails won’t be readable after the key expires. This means that as the key is preparing to expire, a new key would need to be generated so that e-mails could continue to be secured. Each time a new key is created, the people who receive e-mails will need to receive a new copy of the public key.
At this point, in the process, you will be prompted to enter your name and e-mail address. This key will be used with and any comment that you wish to specify. After entering this information and confirming that it is correct, you’ll be prompted to enter a new password for the key twice, and then the key will be generated. As it prompts you on the screen, you’ll want to type on the keyboard and/or move the mouse around randomly in order to help randomize the information that is used to create the key.
Next, we need to export the public key so that we can give it to the people that we will be e-mailing encrypted e-mails to. This is done in the command window again using the gpg program as shown in Example 6.3, replacing the example e-mail address with the e-mail address specified when creating the key.
Gpg –export –a "[email protected]" > public.asc
Within Outlook, you’ll need to tell the Outlook Privacy Plugin to use the key. This is done within Outlook by clicking on the Add-Ins tab and then clicking Settings. This will open a new window from which on the “Compose” tab, you’ll need to select the PGP key that should be used when sending e-mail.
Sending encrypted e-mails
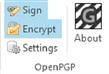
E-mails are not sent as encrypted e-mails by default within Outlook. You have to specifically tell Outlook that you want the e-mail to be signed and encrypted. To do this within the compose e-mail window, select the Sign and Encrypt options within the OpenPGP section of the ribbon at the top of the window as shown in Figure 6.12.Once these options are selected, the e-mail will be encrypted when it is sent, which means that the person receiving the e-mail will need your public key in order to open the e-mail.
Importing a public key from another person
The preferred method of giving out the keys is to give the key to someone on a thumb drive or another secure transfer method. Some people will e-mail out the key, but this means that anyone to intercept the e-mail with the public key would then be able to decrypt the e-mails that are later sent.
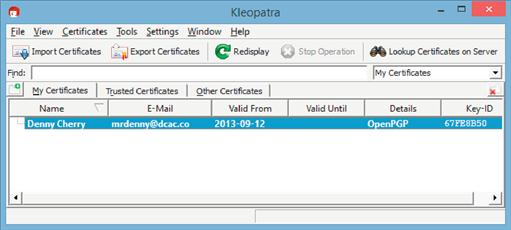
Anyone who is receiving your e-mails will need to import your public key into their computer. Gpg4win includes an application called Kleopatra, which will allow them to import this public key. To find Kleopatra, they will need to first install Gpg4win, which they will need in order to send secure e-mails, as well as any plug-ins, which are required for their e-mail client. After Gpg4win is installed, Kleopatra can be found in Windows XP and Windows 7 by clicking on the Start menu then All Programs, then selecting the Gpg4win program group, and then selecting Kleopatra. In Windows 8 and Windows 8.1, click the Start menu and type in Kleopatra to locate the application. To import a public key, simply click on the “Import Certificates” button in the upper left-hand corner of the application as shown in Figure 6.13.
When you send someone an e-mail, which is encrypted and they have your public key imported into their system, the e-mail will be shown just like it normally would be. If the person receiving the e-mail does not have your public key imported into their system, then the e-mail either will not show or it will show as scrambled text that is totally unreadable. The same applies when someone e-mails you an e-mail that is encrypted with this private key.
Web browsing
One of the ways that web browsing traffic is tied to a specific person or more specifically to an account with an Internet service provider is by tracking the data from an IP address.
One of the ways that we can prevent people from watching what you do on the Internet is to mask the IP address that your network traffic is actually coming from. There are two basic ways of doing this. The first is by using an anonymizer, which makes your network traffic appear to come from a variety of different places throughout the world. A very well-known anonymizer is called Anonymouse and is available from http://anonymouse.org/. By using Anonymouse or one of the other anonymizer services, you simply type in the URL that you wish to browse to, and your web browsing connection is routed through the Anonymouse servers.
The Anonymouse website shows specifically what information they are masking when you use their service. When browsing from an example computer, the information returned by the Anonymouse server is shown in Figure 6.14.
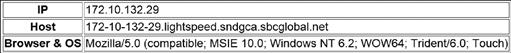
Figure 6.14 Information reported to websites from a sample computer when not using an anonymizer service.
The information shown in Figure 6.14 provides a surprising amount of information when you know how to read it. The IP address is a pretty straightforward piece of information as that is the IP address of the router that the sample computer was connected to. The second line, which is labeled as the host, provides us with some location-based information and tells us who the Internet service provider is. In this case, the Internet service provider is sbcglobal.net, which is one of the domain names that belongs to AT&T. The second thing that we can see is some basic information about where the IP address is used. The part of the hostname, which says sndgca, is a telecommunication industry abbreviation for San Diego, CA. Looking at the third line, which is labeled “Browser & OS,” this gives us a good deal of information about the computer and the web browser that is being used. The web browser that is being used is a Mozilla 5.0 compatible web browser. Specifically, the web browser is MSIE 10.0 or Microsoft Internet Explorer 10.0. The operating system is Windows NT 6.2 or Windows 8. WOW64 tells us that this is a 64-bit operating system running a 32-bit web browser. The “Touch” tells us that this is a touch enabled computer.
The hostname, which is assigned to the IP address, is not something that can be controlled by the end user whose computer the IP address is assigned to. This is assigned by the company that owns the IP address and is configured by them.
When using the Anonymouse service, this information is changed quite a lot as shown in Figure 6.15.
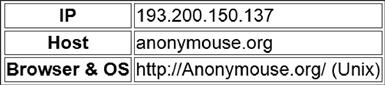
Figure 6.15 Information reported to websites from a sample computer when using the Anonymouse service.
The biggest downside to using the Anonymouse service or really any of the other anonymizer services is the fact that you have to go to the anonymizer's webpage for each new webpage that you want to browse to. For example, instead of being able to go directly to this books website www.basicsofdigitalprivacy.com, you instead have to first browse to www.anonymouse.com and then you put the URL www.basicsofdigitalprivacy.com into the text box on the Anonymouse website, as shown in Figure 6.16. Realistically, this isn’t that big of a problem if the goal is to only browse to some websites anonymously. If however every website that you browse to should be done anonymously, this isn’t the easiest solution to use; this however is where VPN solutions come into play.
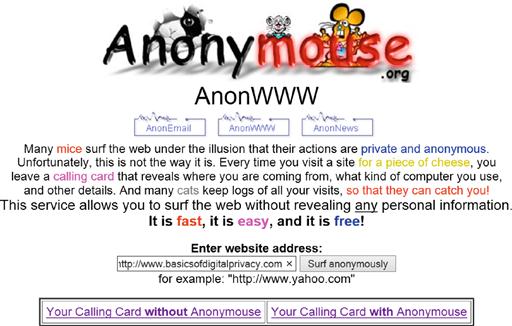
Figure 6.16 The Anonymouse website prepared to browse anonymously to www.basicsofdigitalprivacy.com.
There are a number of VPN solutions that can be used to give yourself a measure of privacy so that websites that you are visiting have no way of knowing your actual home IP address. Where an anonymizer will mask your IP address, hostname as well as the browser and operating system a VPN provider will only mask the IP address and hostname.
VPN services give you a couple of additional perks beyond just changing the IP address that your web browser traffic appears to come from. Depending on the service that you use, this could also change the country that it appears that your web traffic is coming from. This includes not just normal web browsing traffic but also e-mail traffic, online video streaming traffic, and anything else that is done on the Internet.
There are VPN services that are free to use and there are other services that are pay services. Some of the free services include both free and paid services that give you the ability to try the service for free before paying for the higher-end service. In order to keep costs down, many of these services limit the amount of data that you can transfer on a daily or monthly basis. Upon reaching the data transfer limits, these services simply disconnect you from the service until the next month.
How each of these VPN services works depends on the specific service. Some are configured much like a normal corporate VPN connection, while others use a browser plug-in.
The list of available VPN services changes often. As of the writing of this book, some of the VPN services include GPass, which is at http://www.gpass1.com/gpass, which provides free VPN services. Another option is CyberGhost, which is at http://cyberghostvpn.com/. CyberGhost provides a free service that allows for up to two hours of Internet traffic at once before forcing you to disconnect and reconnect. Additionally, CyberGhost offers paid-for services, which include more servers to route the connection through and does not have any limits on how long you can stay connected for. Another free VPN service is called SecurityKISS, which is available at http://www.securitykiss.com. SecurityKISS offers both free and paid-for services. The free service allows for 300 MB of data transfer per day, while the paid-for services include data transfer from 20 GB up to an unlimited amount of data transfer.
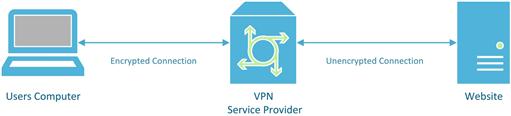
When using these VPN connections to hide or mask your network traffic, keep in mind that the network traffic isn’t going to be completely invisible. Only the network traffic between your computer and the VPN provider isn’t going to be easily visible to anyone who is looking for it. However, any network traffic that isn’t otherwise encrypted would be visible to someone who is watching for the traffic that is coming from the VPN service provider to the web server that is being viewed as shown in Figure 6.17.
Another option available to you is to use a system called Tor. When the Tor protocol was first written, it was designed and deployed as what is called an onion routing project for the US Naval Research Laboratory. However, the project was released to the public and is used today by large numbers of people to communicate securely over the Internet.
According to the Tor website (http://basicsofdigitalprivacy.com/go/tor), “Tor is a network of virtual tunnels that allows people and groups to improve their privacy and security on the Internet. It also enables software developers to create new communication tools with built-in privacy features. Tor provides the foundation for a range of applications that allow organizations and individuals to share information over public networks without compromising their privacy.”
Tor works by bouncing a person's web traffic requests through a variety of servers called nodes. Each node between the client computer and the server only knows about the prior machine in the chain, and the next machine in the chain, meaning that no single machine in the chain, including the person's computer and the server at the end of the chain, has no way to know the entire chain process.
There are a variety of applications that can be configured to use Tor, but not all applications can. While the Tor website does not contain a complete list of applications that can be used with Tor, it does have a variety of settings and instructions for popular applications so that you can use many applications over the Tor network.
Consequences
There are a few consequences when it comes to using an anonymizer service or a VPN solution to mask your actual IP address. The first of these consequences is the ease of use, and the second consequence is increased government scrutiny from various government agencies.
Ease of use
Anytime we add security, we add complexity to the process. In the case of browsing the web using an anonymizer service, we add to complexity of needing to ensure that each new website that we browse to is done via the anonymizer. In some cases, depending on what web browser you are using, there may be plug-ins to help ensure that this is happening. You would need to check with the specific anonymizer, usually in their Frequently Asked Questions or their forum to see what assistance they can provide with regard to getting a plug-in. Typically, these sorts of plug-ins are available for Firefox and/or Chrome web browsers.
Using a VPN connection to ensure that our data are secure while being a little easier to deal with than simply an anonymizer, there are still things that you need to do to ensure that your connection is secure. The first thing that you need to do is make sure that your VPN is connected before opening any applications that are Internet-connected. In the world of applications that check in automatically with the companies that developed them when the computer boots up, this can be quite hard to do to say the least. Depending on the type of VPN connection software that is being used, it may or may not be possible to have the VPN connect before logging into the computer so that by the time that you are logged into the computer and your desktop is visible, the VPN connection has already connected and is routing all of the network traffic across the encrypted connection.
VPN connections can sometimes drop and need to be reconnected. When using a VPN connection to encrypt all network traffic between you and the Internet to ensure that someone isn’t monitoring your network connection, you will need to keep an eye on the status of the network connection to ensure that you are always connected. How you do this will depend on the VPN connection software that you are using. The Cisco AnyConnect VPN software, for example, shown in a disconnected state in Figure 6.18, sits in the system tray and doesn’t provide much of an interface to tell you that it has become disconnected. As the state of the VPN connection changes, there is a small pop-up that appears, but it disappears rather quickly, and if you happened to not be looking at the screen when the connection dropped, then you might not notice that you were in a disconnected state.
The Windows VPN connection can be checked in a couple of different ways. The first is within the “Network Connections” icon with the control panel. If the connection is disconnected, it will be labeled as such, as shown in Figure 6.19.
Another way to verify if the Windows VPN is connected is to simply place your mouse over the network connection icon in the system tray next to the clock. When you place your mouse over the icon, shown in the lower left of Figure 6.20, the status of each network connection being used is shown. In this case, the computer has two different networks configured and the VPN connection that is connected. Upon the VPN being disconnected, the VPN would no longer be visible in the dialog box.
These VPN connections are just a couple of the wide variety of VPN software packages that are available. Check with your VPN provider or the VPN software vendor for specific details if a different VPN software package is being used.
Government scrutiny
Using data encryption techniques such as those shown in this chapter can have some unintended consequences when it comes to government scrutiny. When it comes to programs like the PRISM program within the United States, the specifics of which were leaked to the press and can be read at http://basicsofdigitalprivacy.com/go/nsa4, when you are a person who the government thinks is currently outside of the United States, the NSA, according to Section 1, paragraph 2, of Exhibit A (http://basicsofdigitalprivacy.com/go/nsa_a), can collect your Internet usage information. With many of these services, the specific point is to make it appear like you are outside of the United States, so as far as the PRISM data collection is concerned, you are outside of the United States and therefore they can collect your data, even if you are inside the United States. To make things even worse for encrypting your data, if the NSA isn’t able to figure out where you physically are, the assumption is that you are not within the United States.
Looking at Exhibit B (http://basicsofdigitalprivacy.com/go/nsa_b), Section 5 talks specifically about domestic communications, or communications that the NSA knows to be within the United States. According to this section, “communications identified as a domestic communiation will be prompty destroyed upon recognition unless the Director (or Acting Director) of NSA specifically determines in writing that” “the communication is reasonably believed to contain technical data base information” where technical database information is defined as “Technical data base means information retained for cryptanalytic, traffic analytic or signal exploitation purposes.” What that means in a slightly easier to read version is that if the data are encrypted and the NSA hasn’t broken the encryption when they realize that you are within the United States, the director of the NSA can order that the information be kept so that they can continue to attempt to break the encryption.
A little further down the document in Section 5(3)(a), we see that “In the context of a cryptanalytic effort, maintenance of technical data bases requires retention of all communications that are enciphered or reasonably believed to contain secret meaning, and sufficient duration may consist of any period of time during which encrypted material is subject to, or of use in cryptanalysis.” In other words, if they have captured encrypted data, they can keep these data forever and use it to continue to develop software that attempts to break the encryption.
When using systems like Tor to attempt to protect your network traffic from snooping by groups like the NSA, keep in mind that odds are this will be pushing your network traffic to a node in another country making your now encrypted traffic collectable by the NSA where they are able to keep your network traffic forever.
Summary
As we have seen in this chapter, there are ways of encrypting network traffic so that you can do the best possible job ensuring that the information that you send out over the Internet isn’t visible by data thieves or by government agencies. However, when doing so, this may have the unintended consequence of closer government scrutiny because the government wants to know that you aren’t talking about something that may be of interest to them, and because they don’t technically know for sure where in the world you are at that moment, they make the assumption that it is OK for them to monitor you, potentially storing the captured information for as long as they would like.
There are a variety of ways to encrypt data as it flows over the Internet including PGP, VPN connections, and Tor, among others, which were not discussed here. Each one of these methods has upsides and downsides to them, and the goal when reviewing the various options is to find a solution that works for you, the user of the computer. You want a solution that will provide you with a level of data and privacy protection without being such a cumbersome solution that it isn’t feasible for you to use on a daily basis.