Storing Your Personal Information Online
Abstract
This chapter talks about what information you should and shouldn’t be storing online.
Keywords
Facebook; challenge questions and answers; online
Information in This Chapter
• How much information you should share with companies
• Risks of sharing too much information online
This chapter talks about the risks of storing information online and how we can mitigate some of those risks.
Storing your personal information online
In the modern world, we all end up storing information online, even if we don’t know that we are. Every company that you do business with stores information about their customers, including you, in a computer on their network. Every website that you visit on the Internet be it from your desktop computer, laptop computer, cell phone, library computer, and Internet café is storing information about you in some form or another. That computer or system of computers in some cases runs a database that allows the customer service, sales, marketing, etc., staff to find customer information, run reports on purchase history, etc. Even when you do business with companies in person and not via the Internet, you will have information stored about your purchases within their systems.
The perfect example of this is the customer loyalty cards that are given out by grocery stores. These cards are very useful for us the customers because it gives us access to discounts that we wouldn’t normally have access to without having to cut coupons and remember to bring them in. The information that the store gathers via these loyalty programs tells them everything about their customers, their shopping habits, and so on.
Understanding just how much information companies track about their customers, both their online customers and their offline customers, is critical to understanding how you as the customer can protect yourself against data and identity theft. Understanding how the companies collect and use the information about you the customer allows you to make informed decisions about what information to give companies and when. In a lot of situations, you can just give the company false information to get through the process without giving them a way to track you. A perfect example is when asked for your phone number at checkout, give them all zeros, or when asked for your zip code, give them the zip code of the store instead of your home.
The problem with it comes to protecting our own privacy is that we as people by our nature want to be friendly and accommodating. Companies are able to take advantage of this by asking for information that we are usually all too willing to give away, even if we shouldn’t be. Companies may not always make it very obvious that they are collecting this sort of information. Often, they will get you to give the company this information as part of the security questions that are used to later verify that you are you when you forget your password. However, many of the questions that companies use can be easily enough found by simply looking at social networking sites (which we will be talking about in this chapter and Chapter 5).
How much information you share with companies
The companies that we do business with on a daily basis are collecting massive amounts of information about us on a regular basis. As of the writing of this book in the summer of 2013, there are no laws or regulations about how much information a company can collect about their customers.
The reason that companies collect all this information about their customers is for a couple of different reasons. The first, and the most common, is so that they can better target advertising so that there is a better chance of selling their customers additional products at a later date. This reason makes total sense when you think about it: companies make their money by selling us products. If they can figure out what products we want to buy before we know that we want to buy them, they have a better chance of selling us the products than their competitor does.
For example, if Best Buy is able to figure out that I need to buy a new Blu-ray DVD player before Target is able to figure out that I need to buy a new Blu-ray DVD player, and Best Buy is able to get me an ad for their new Blu-ray player that is available in the stores, then odds are that I will end up purchasing the Blu-ray DVD player from Best Buy and not from Target.
The second reason that companies collect information about their customers is much less likeable and enjoyable for their customers. This is when companies collect and store information about their customers so that the information that is collected can be sold to other companies so that the other companies can advertise to us. The easiest example of this practice is Facebook. With Facebook, we willingly give all our information over without any thought about it. Facebook then uses that information to more easily enable advertisers to display us ads on the Facebook website. In this case, we are no longer the customer, we become the product that is being sold.
Risks of sharing too much information online
When companies collect and store large amounts of information about us, that information becomes more at risk of being stolen by other people. The biggest threat to consumers when it comes to identity theft is that the information needed to steal someone’s credit card information or their entire identity can be found in the computers of companies that those consumers do business.
Giving attackers the information that they need
As we share more and more information online about our lives on social networks like Facebook and Twitter, it becomes easier and easier for identity thieves to find out the information that they need to break into our accounts and take over our identities; we will be talking more about social networks in Chapter 5.
When we set up accounts with companies such as our banks, we set up a username and a password. When we do this, we keep these items secret so that no one else knows what these items are. However, there is a weakness with this system that becomes painfully easy to exploit and that is the fact that all of these accounts are set up to go with a specific e-mail address. That e-mail address is your e-mail address and is used to send you information about the bank and your electronic statements and to allow you to gain access to your account in the event that you forget what your password is. By their nature, e-mail addresses are not secret and are known by all our friends and family and may even be published on the Internet so that customers, old friends, and so on can contact us. The e-mail address that is posted online can also be used by attackers as the first step in gaining access to our bank accounts.
Once an attacker has figured out what your e-mail address is, finding out the website where your e-mail can be accessed usually isn’t all that hard. For example, if you have an e-mail address that ends in @earthlink.net, your e-mail can be accessed via the website webmail.earthlink.net. If your e-mail address ends in @gmail.com, then your e-mail can be accessed via the website www.gmail.com. Figuring out the website to access even rare domains is usually very straight forward.
On most public website sites, there is going to be a link that can be used to allow the customer to figure out or reset the password in the event that the password has been lost. Usually, this is done by asking a series of questions that only the owner of the account would know the answer to. When the Internet was first being used and this sort of challenge and response question concept was put together, this worked very well as no one was posting personal information online. However, as time has moved forward and social networking has continued to grow in popularity, the idea of challenge and response questions hasn’t really changed. Now, instead of the information to answer these questions being something that only the account owner would know, it’s a real possibility that the answers to these questions has been shared online on social networking sites.
Telling thieves when to break into your house
While social networks are great for telling our friends and relatives what is going on in our lives, our friends and family aren’t the only people that can view the information that we post on social networking sites. Most social networking sites are wide open by default meaning that anyone who looks at the site can find the information that you post on the site (we will talk more about how to set up security on social networking sites in Chapter 5).
As we post more and more information on social networking sites, we become more and more used to posting everything that we are doing online. However, when it comes to traveling, for business or pleasure, we need to be very careful how much information we post online. Likewise, we need to be very careful about posting our actual home address online. If we have posted where we actually live, and we also post when we are on vacation out of town, we have just told any potential burglars in our home area where our house is and the fact that it’ll be empty. If we post online that we are going to Hawaii for vacation as an example, a potential burglar can assume that the house will be empty for at least 4-5 days if not for a full week.
There are a several location services that have become popular online. The first is Foursquare and the second is Facebook’s location service. When using either one of these services, it is important to not check in at your actual home as this gives away the exact location of your home, your family, and all your stuff. While finding someone’s home address isn’t all that hard if you know where to look online, the goal of masking yourself on social networking just a little bit is to make it a little harder to find out information like where you live and when you aren’t there. If you are a big fan of using these location services, picking a location in the general area of your home is generally safe enough for most people; however, for those people who work in a high security field, they should avoid these sorts of services. This includes people who work in law enforcement, for security companies, banks, and doctors, basically anyone who works with the public or a segment of the public and doesn’t really want to have people.
Knowing how companies protect your information
A big problem when it comes to giving information to companies online is knowing how the company is going to protect the information that you give them. Many companies will post information on their website that will give you basic information about what the company will be doing with your information and how they will protect it. While some basic information may be provided, there won’t be any details such what information is being encrypted or how employees are trained to ensure that personal data aren’t printed and lost that way. The reason that such information isn’t available to the general public is that it gives attackers more information about the company and what sorts of gaps the company has in their data protection policies.
With websites like Facebook and Twitter, these companies while holding lots of personal information, aren’t really holding lots of your confidential information. However, other companies such as insurance companies, doctors’ offices, credit card companies, payroll services, or even your employers’ human resources and payroll departments all hold massive amounts of information about you, much of which you don’t want anyone else to find out about, while some of which is protected information according to many countries' data protection laws, including the United States.
In the United States, all medical data are protected by a federal law called HIPPA or the Health Information Patient Protection Act. This law that was passed and signed into law 1996 requires that all companies that handle medical information (insurance companies, doctors’ offices, medical billing companies, etc.) take precautions to ensure that the medical data that they store either on paper or in a computer system are protected so that only the people who should have access to the information actually have access to them. While this all sounds great in principal, the reality is that it is very easy for the employees at these healthcare companies to lose confidential data in the course of their normal job activities.
For example, a medical auditor could be reviewing medical records at a medical insurance company to ensure that doctors aren’t overbilling the insurance company. While the auditor is reviewing these records, they may end up printing up a copy of the data to make reviewing the information easier. Once that audit is complete, the auditor is supposed to shred the printouts. However, they could end up lost in the person’s desk or dropped on the floor. While lost in the auditors desk isn’t the worst thing, if the papers were dropped on the floor, the cleaning person who comes through at night emptying the trash may throw the papers on the floor away without knowing what they are or that they are supposed to be shredded. This means that there are now medical data on printouts sitting in the trash without being shredded that could be pulled from the trash by anyone who is walking past the trash dumpsters and who knows what they are looking for or who finds the papers when they make their way to the city dump.
Even if in our example, the auditor doesn’t print the information, but instead, they access the information from their company laptop that they then put in their trunk as they head home for the day. On the way home, the auditor heads to the supermarket to pick up dinner for the family. While in the supermarket, the employee's car, with the laptop still in the trunk, is now stolen by a car thief. The car thief now has the employee's laptop as well. The hard drive within the laptop can be easily enough installed in another computer so that the information from the laptop can be downloaded and sifted through. There are data encryption options available that would prevent the data on the hard drive from being read, which are talked about in detail in Chapter 4. If the company policy says that the laptop hard drive is encrypted and that it is actually encrypted using a high security encryption process, then the information can’t be viewed by the car thief. But if the company has no requirement to encrypt the data of the laptop’s hard drive, then it won’t be protected. In any case, the company won’t be posting on their website the kinds of protection that they have in place to protect their customers’ information.
The main reason that companies don’t broadcast this information isn’t to keep their customers in the dark, but to help protect the customers’ information. If the company doesn’t tell people how the data are protected, then attackers don’t know how the data are protected, which means that the attacker doesn’t know how the data are protected, which means that getting access to the data takes longer and is harder. One of the goals of data security is to make breaking through the security so hard and take so long that it isn’t worth the time and the trouble to attempt to break through the data security. While it probably seems like I’m disagreeing with myself in this section, I kind of am. This is one of those times where companies and their customers don’t have the same interests in mind. The companies want to keep their practices secret, while the customers want to know how their data are being protected.
Cookies and websites
Most websites in the modern times of the Internet use cookies to store information about the user and how they use the website on the user’s computer. These cookies can store a variety of information within them, with the user of the website having little if any control over what information is stored within the cookie. Cookies are created per website meaning that different websites cannot read each other’s cookies. As an example, if you were to go to www.google.com and www.yahoo.com, both of these websites would create their own cookies on your computer. This cookie will contain some basic information about you, not necessarily your name or your e-mail address, but there will be at the minimum a specific identifier that is unique to your computer so that these sites can track your interactions with their respective properties. However, Google’s website has not access to Yahoo’s cookie, and likewise, Yahoo has no access to Google’s cookie.
That being said, there are risks to cookies when it comes to online privacy. The first one being that these cookies allow the website to track you as you move around on their website. At first, this doesn’t sound all that bad, but when it comes to the major Internet companies like Google, their website isn’t confined to just their website. This is because Google controls the largest advertising network on the Internet called Google AdWords. This advertising platform is used by the majority of websites to display all manner of advertisements on all manner of websites. As you move from website to website, not only the websites that contain the advertisements will display advertisements on the website that you are viewing but also the advertising system will also track that you visited that website. Then, when you browse other websites using this tracking data, the advertising system would then display advertisements that are similar in nature to the sites that you have visited.
Many people consider this tracking across the Internet to be quite intrusive as it gives one company, specifically a company that you may not be doing business with, access to basically your entire browsing history that they can data mine and use this to serve up advertisements that are reliant to you the user. And frankly, I have to agree with those people. Many people wonder how this sort of Internet tracking is legal. The most basic reason why this sort of thing is allowable is because every website that you visit is going to have some sort of End User License Agreement (EULA) that specifies the terms that you must agree to in order to use the website. Buried somewhere in that user agreement, which it is assumed that you have agreed to by using the website, is something that will give the website and its partner websites, which would include the advertising systems, the right to track you via cookies.
There are a few ways to solve this.
InPrivate Browsing
The first is to enable a feature in most web browsers called “InPrivate Browsing.” In Internet Explorer, this can be enabled by opening Internet Explorer, then clicking on the Tools menu icon (the gear in the upper right-hand corner of modern versions of Internet Explorer), then clicking on the menu that says “Safety,” and then selecting “InPrivate Browsing.” This will open a new Internet Explorer window and this new window will be running in private browsing mode. Any websites that you view when working within the InPrivate Browsing window will not be saving any cookies, temporary Internet files (also known as cache), browsing history, etc.
Turning cookies off in Internet Explorer
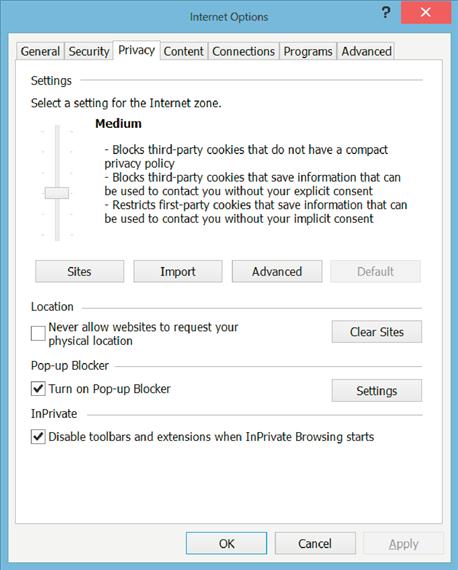
The second method that can be used to prevent cookie tracking by the advertising company is to disable cookies within the web browser. This is a very easy thing to do. In newer versions of Internet Explorer, click on the gear icon in the upper right-hand corner of the Internet Explorer application. In older versions, click on the Tools drop-down menu. In either case, click on the “Internet Options” menu item. On the Privacy tab at the top of the window, there are settings for configuring the cookie usage as shown in Figure 1.1.
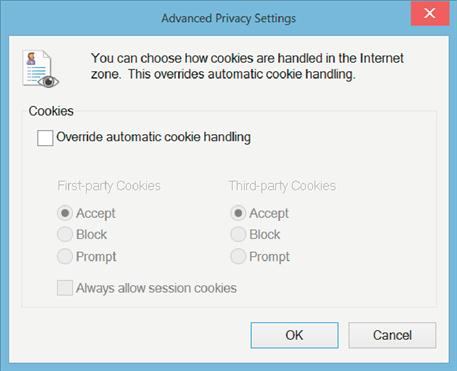
Clicking the Advanced button will allow you to override the default handing of cookies. Checking the checkbox allows the configuring of first-party cookies and third-party cookies as shown in Figure 1.2.
From this screen, you can configure Internet Explorer to Accept, Reject, or Prompt for cookies. The default for Internet Explorer is to accept all cookies. By rejecting cookies, the website would attempt to create the cookies, but the web browser would simply ignore the request to create and save the data to the cookie. By setting the settings to prompt, this would prompt you each time the web browser requested to create, update, or read a cookie. While this will slow down the web using experience by prompting over and over to use the cookie, it will give you the ability to control exactly which cookies are used and which ones aren’t. This can be important as you may wish to store login information for a website and only deny the website the ability to store the advertising cookies.
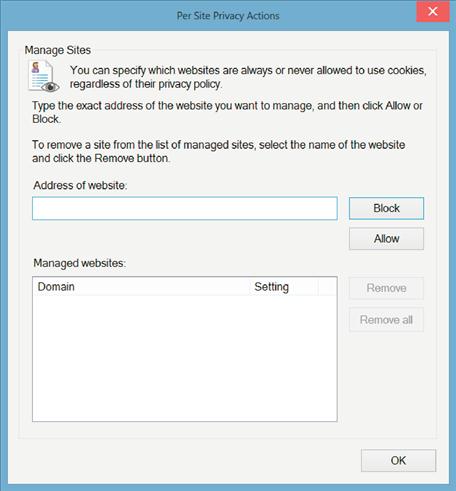
If there are specific websites that you wish to prevent from ever saving a cookie on the system, this can be done through the Privacy tab of the Internet Options window as well. On the top half of the screen, there is a section labeled “Settings,” and within that section, there is a button labeled “Sites.” Clicking on that button will bring up a screen similar to that shown in Figure 1.3.
By adding a site to the screen shown in Figure 1.3, the specific site can be prevented from using cookies at all on the site. For example, to block Google’s AdWords system, enter the URL www.googleadservices.com and then click the block button. Clicking OK all the way out will enable this setting so that the next time you view an advertisement that has been served by the Google advertising system, the Google advertising system will not be able to track the data.
Turning cookies off in Firefox
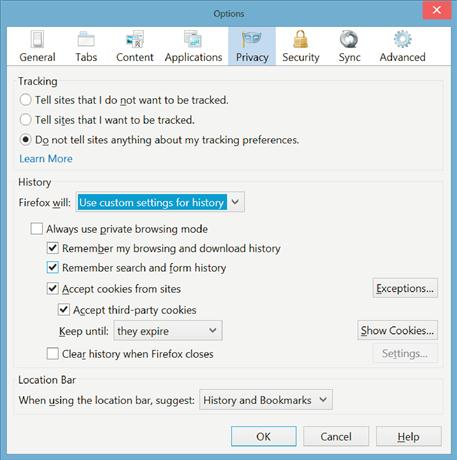
Internet Explorer isn’t the only web browser that allows for turning off cookies, and this can also be done in Mozilla’s Firefox web browser as well. In Firefox, to turn off cookies, click on the Tools drop-down menu at the top of the Firefox application. If you don’t see any of the drop-down menus, click on the key labeled “Alt,” which should make the menus at the top appear. After clicking on the Tools drop-down menu, select from the “Options” menu option. On the Options window that appears, select the “Privacy” page as shown in Figure 1.4. On the “Privacy” page within the “History” section within the “Firefox will” drop-down menu, change the setting from “Remember History,” which is the default to “Use custom settings for history” as shown in the middle of Figure 1.4.
To completely disable all cookies, uncheck the check box next to “Accept cookies from sites.” You can optionally leave cookies enabled but disable cookies, which are created by what are called third parties. Third-party cookies are cookies that are created by one website and are used by another website. An example is the Stack Exchange family of websites such as games.stackexchange.com and programming.stackexchange.com, among other websites within the family. Along with the Stack Exchange websites, there are other sites within the network of websites called Server Fault (www.serverfault.com), Stack Overflow (www.stackoverflow.com), and User “Something” (www.userflow.com). Because the main pages of the website names “stackexchange,” “serverfault,” and “stackoverflow” are all different, they are considered to be different sites; however, they are configured to share a username and password for all the sites, and when you sign into one website, www.serverfault.com, for example, and then view the www.stackoverflow.com website, the second site will know automatically that you are logged in and who you are.
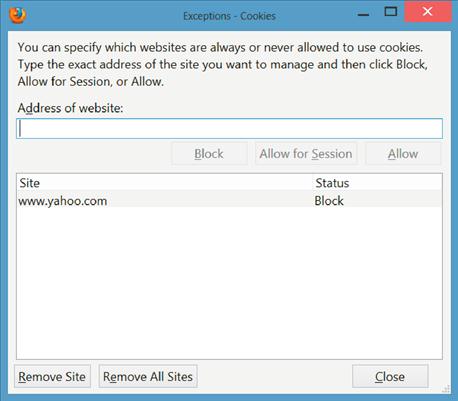
If you wish to configure specific websites to not support cookies within Firefox, this can be easily enough done via the “Privacy” tab shown in Figure 1.4. When the “Privacy” tab is open, clicking the “Exceptions” button will allow you to configure that specific websites will be configured to either allow or block the use of cookies as shown in Figure 1.5.
Within the Exceptions page, simply enter the address of the website as shown such as www.yahoo.com and click either the “Block,” “Allow for Session,” or “Allow” buttons. Using the “Block” button will prevent Firefox from ever accepting a cookie from the specified website. Using the “Allow” button will always allow the website to create and use its cookies. Using the “Allow for Session” button will allow the website to use cookies but only while the web browser is open. When Firefox is closed and reopened, the website will no longer be able to use cookies.
Within the Options window on the “Privacy” tab you can configure how long Firefox should keep the cookies. By default, the cookies will be kept until they expire, typically for 2 weeks or longer depending on how the website has been configured. The other options for how long to keep the cookies are “I close Firefox” and “ask me every time.” By selecting “I close Firefox,” the cookies will be kept until the Firefox web browser is closed, at which time, all the cookie files will be deleted. By selecting the “ask me every time,” the user will be prompted to select how long the cookie should be saved for each time that a new cookie is created.
Turning cookies off in Chrome
Much like the other major web browsers, the Chrome web browser made by Google, Inc., can be configured with various cookie settings. In order to change the cookie settings within Google Chrome, click on the menu button at the upper right of the Chrome web browser as shown in Figure 1.6.
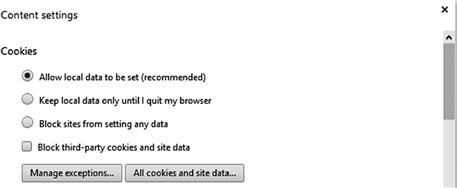
Once the menu has opened setting the “Settings” option from the context menu. Scroll to the bottom of the page that is shown and click the “Show advanced settings…” link that is typically shown in blue. When the additional menu options appear within the “Privacy” section, click the “Content settings…” button. Within the Cookies section, shown in Figure 1.7.
Google Chrome allows for much the same set of settings as Mozilla’s Firefox browser. By default, Google Chrome uses the setting “Allow local data to be set.” This setting allows the Chrome web browser to save cookies to the computer. The setting “Keep local data only until I quit my browser” allows the application to save the cookie but only until Chrome is closed. Once Chrome is closed, it will automatically delete all of the cookies.
The setting “Block sites from setting any data” will prevent Chrome from using any cookies. The check box “Block third-party cookies and site data” will allow sites to use cookies but not third-party cookies.
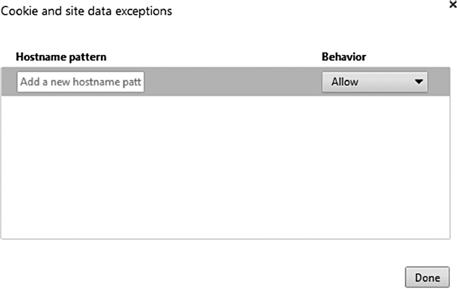
By clicking the Manage Exceptions button, the option to configure exceptions to these rules is set. This screen is shown in Figure 1.8. To add an exception, enter in the site that you wish to set the exception for, and select the kind of exception from the “Behavior” drop-down. When you are done entering the needed exceptions, click the “Done” button to save the settings.
Turning off cookies in Safari
Turning off the cookies in Safari on the Mac operating systems is just as easy as using the Windows web browser, which were discussed previously in this chapter. To make the change, simply open the Safari web browser. Then, click the Safari drop-down menu at the top of the screen and click on Preferences from the drop-down menu as shown in Figure 1.9.
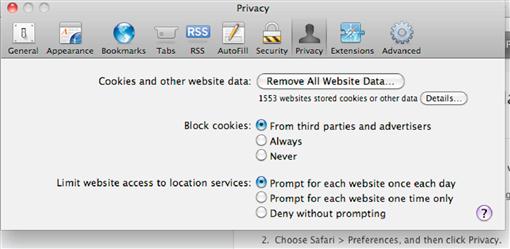
When the Settings window opens, select the Privacy button at the top of the window that will open a window similar to the one shown in Figure 1.10.
From the privacy settings page shown in Figure 1.10, you have the option to block all cookies from third-party websites by selecting the “From third parties and advertisers” option. You can prevent all cookies from being used by selecting to “Always” block cookies, or you can allow the use of cookies by all websites by selecting the “Never” option.
Summary
Protecting your information and your privacy, which really go hand in hand, starts with knowing how much information you should be giving to companies on the Internet. The more information you give to these companies, the more information that will be available for these companies to sell or trade to other companies. As you give away information to companies, you lose control of the information, leaving it up to a company that doesn’t have your best interest at heart to decide what to do with information about you.
When it comes to browsing the web, understanding the technology that drives the web, specifically within the web browsers that we use to browse, the Internet, and the cookies that are used to track us is key in keeping your personal information, personal. Only allowing companies that you trust to use cookies can make your web browsing experience a little less seamless at times, but the trade-off is well worth it in regard to data privacy.