Securing Your Home Computer
Abstract
This chapter talks about what sort of data encryption you should be using.
Keywords
Facebook; Challenge questions and answers; Online
Information in This Chapter
• Data encryption for the home user
• Why you should be encrypting data
• Native Windows data encryption
• Native Apple data encryption
• Other companies data encryption
While we hope that no one will steal our home computer and that we will never lose our laptop, the reality is that at some point, we will end up losing a computer somehow. A study done by Intel, available at http://basicsofdigitalprivacy.com/go/oneinten, found that 10% of laptops purchased will be lost or stolen within the first year of ownership. Of those laptops stolen, only 3% of those laptops will ever be recovered and returned to their owners. That means that 97% of the laptops that are stolen and the data that they contain remain with the thief or the person that the thief sells the laptop to.
Where laptops are stolen is an interesting set of numbers to review. It is assumed that most laptops are lost or stolen at airports. The reason behind this though is that airports are busy places and the last thing that most people want to worry about at the airport is the location of their laptop at they run from flight to flight. While there are many laptops left at airports every year, the reality is that not that many laptops are actually stolen at airports, due mainly to the fact that there is a high degree of security at the airport compared to everywhere else that we travel. Since not just anyone can walk into an airport and get past the security checkpoint, given that you have to have a valid boarding pass to get past the airport security line, the odds of someone within the airport being there just to steal someone’s laptop is pretty slim. According to the Intel-funded study, available at http://basicsofdigitalprivacy.com/go/oneinten, the places that we consider the safest would be where the most laptops are actually stolen from, with homes and hotel rooms accounting for over 40% of laptop thefts. Additionally, another 33% of laptops, which are lost, are lost while in transit (taxis, trains, subways, airports, etc.). Another 12% of laptops are lost within our workplace, in other words, taken by a coworker or other person who has access to our place of business, with the remaining laptops being taken at an unknown location or a location that couldn’t be identified by the study participants.
Data encryption for the home user
The best way to prevent your personal information from being exposed to someone who has taken or found your computer is to encrypt the information within the computer. This will protect the information in such a way that if someone who doesn’t have the password or key for the encryption system attempts to gain access to the information, they won’t be able to. Within the information technology industry, data encryption is considered to be the gold standard when it comes to protecting information from access by unauthorized people. This trust in data encryption comes from the fact that the strongest levels of data encryption, which are commercially available today, are considered to be virtually unbreakable.
As home users, we need to know how to set up and use the data encryption options within the devices that we use, as these devices can be easily lost or stolen, so that if our device falls into the hands of someone who shouldn’t have them, our data can’t be easily accessed and used by them to steal our identity, blackmail us, or release information, which we wouldn’t want to be released to the public.
Different operating systems such as Microsoft Windows and the Apple operating system have different processes for setting up data encryption on the disks, and different versions of these operating systems have different features and configuration options. Understanding how data encryption can protect your data from being taken, and what sort of threats data encryption protects you against is very important when configuring data encryption.
Native Windows data encryption
When using a computer running the Microsoft Windows operating system, which is running Windows Vista or newer versions (including Windows 7 and Windows 8), there is a feature called BitLocker, which will encrypt the data on the hard drive. When using Microsoft’s BitLocker, there are a few data encryption options available to you and a couple of different options that you need to be aware of. Microsoft’s Windows Vista and Windows 7 support the use of BitLocker for the entire disk only. This means that the entire disk needs to be encrypted, which can take quite awhile to configure. Starting with Microsoft’s Windows 8, the BitLocker application supports encrypting the contents of either the entire hard drive or just a folder within the hard drive.
Encrypting a disk in Windows
Turning on data encryption for an entire disk is very easy to do. The first step is to open the control panel. On Windows Vista and Windows 7, this is done by clicking on the Start menu button on the task bar, typically found at the bottom left of the screen, and then clicking on “Control Panel.” On Windows 8, the Control Panel can be opened by bringing up the Start menu. This is done by putting the mouse in the lower left corner until the Start menu button appears as shown in Figure 4.1. On Windows 8.1, click the Start button, which is typically found in the lower left-hand corner of the screen, and then follow the rest of the instructions below of Windows 8.
Once the Start button shown in Figure 4.1 appears and the button is clicked, the Start menu appears. Once the Start menu appears, type the word “control” and the search menu will appear along with the search results as shown in Figure 4.2. Clicking on the “Control Panel” button will open the “Control Panel.”
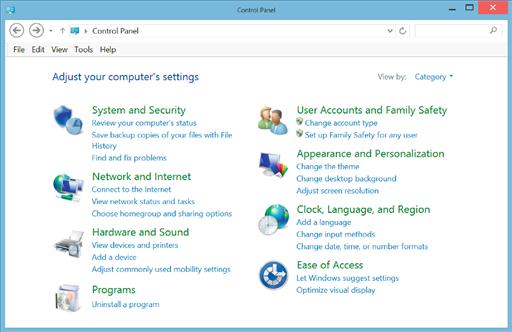
No matter which version of the operating system being used, at this point, the Control Panel should be shown on the screen, similar to that shown in Figure 4.3, which is from Windows 8, but other versions of the Microsoft Windows operating system will look very similar.
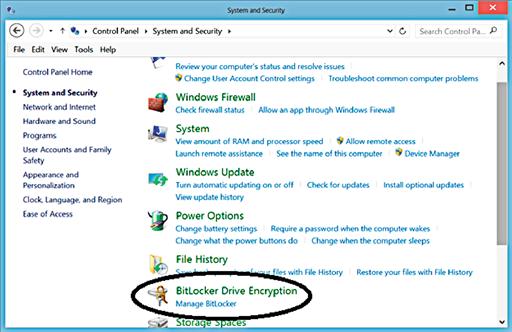
Within the Control Panel, click on the “System and Security” link at the upper left of the Control Panel. This will open the System and Security menu of the Control Panel, which shows a variety of options similar to the options shown in Figure 4.4.
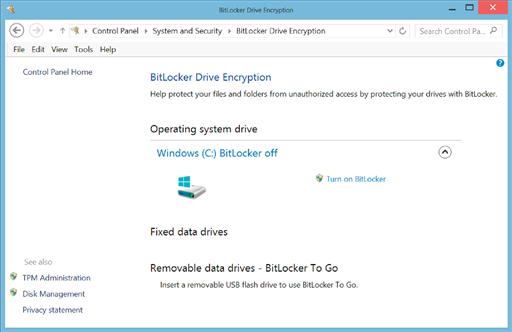
From within the System and Security submenu of the Control Panel, you’ll see the BitLocker Drive Encryption menu option circled in Figure 4.4. Clicking the Manage BitLocker menu link from within the System and security menu of the Control Panel will launch the BitLocker Drive Encryption menu shown in Figure 4.5. From this window, data encryption can be configured for each drive on the system. Each disk can have BitLocker enabled separately from the other drives on the system. This allows you to configure BitLocker on only the drive, which contains your sensitive data, without needing to enable BitLocker on the disks that contain less sensitive data.
As an example, if your personal data was stored within the My Documents folder on the C: drive and your MP3 collection was installed on a different drive such as the D: drive, you would want to encrypt the data on the C: drive but not the data on the D: drive.
To enable BitLocker on the drive, simply click the “Turn on BitLocker,” which can be found on the right-hand side of the window shown in Figure 4.5 in the middle of the window.
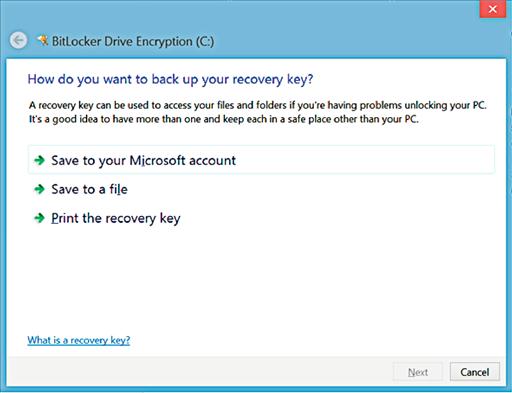
When you turn BitLocker on for one of the drives for the first time, you will be prompted to specify how the recovery key should be saved. The recovery key is used to allow you to access your files in the event that BitLocker has data decryption problems. It also allows you to take the hard drive from this computer and insert it into another Windows computer running the same version of Windows or newer and still be able to access the files on the hard drive. The screen to save the recovery key will look similar to that shown in Figure 4.6. From this screen, shown in Figure 4.6 on a Windows 8 computer, allows you to save the key to your Microsoft account, to a file on your local computer or to print a physical copy of the key on your printer.
Saving the password to your Microsoft account requires that you are using a Windows 8 or newer computer and that you log in to the computer using your Microsoft account (formerly called a Windows Live account). Using this option will upload the key to the Microsoft servers where it will be securely stored. Doing this is only a good idea if your Microsoft account is secured using a strong password (password policies are discussed in Chapter 2). If your Microsoft account is not secured using a strong password and your Microsoft account were to become compromised, then the person who accesses your Microsoft account could gain access to your recovery password.
Saving the recovery password to a file is typically a good idea, provided that the file is then removed from the computer and stored on a CD, DVD, or USB drive, which is then stored in some sort of secure location such as a wall or gun safe or a safe deposit box at your local bank. The same applies if you choose to print the recovery key to your printer in order to store a hard copy of the key. You wouldn’t want to store either the file with the key or the printed copy of the key with or near the computer that the key protects because if someone steals the computer or the computer is lost in some other way, you wouldn’t want the person who has the computer and isn’t supposed to have the computer to have the key to access the data either. When saving the recovery key to a local file, the file must be created on a disk, which isn’t an encrypted disk. If you only have a C: drive like the computer that was used to take the screenshot in Figure 4.6, you will need to have a USB drive to connect to the computer that you can save the key to in order to back up the key.
Without saving the backup of the BitLocker key, you will not be able to continue through the wizard. The next screen of the wizard will be asking you how much of the disk to encrypt. The options are to encrypt only the disk space that has been used or to encrypt all the disk space. The difference between the two is that the latter option will encrypt what is called the white space or the space on the disk that doesn’t have any data written to it yet. The former of the two options will be faster but will leave any files that you have deleted but that still exist on the disk unencrypted. The latter option will encrypt everything even the files that have been deleted.
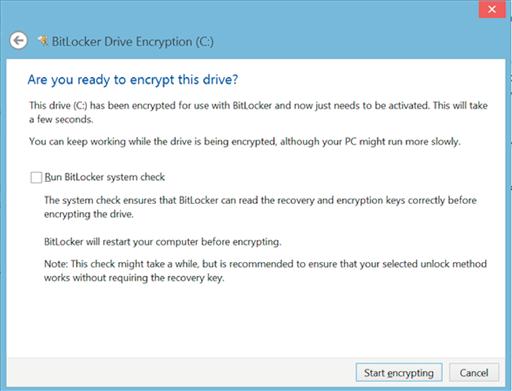
The next screen asks you if you are ready to encrypt the drive and if you want to run the systems check. The system check, which BitLocker runs, will ensure that BitLocker is able to read the recovery keys and the encryption keys, and then, it will begin the process of encrypting the entire hard drive of the computer. At this point, after the “Start Encryption” button, which can be seen in Figure 4.7, is clicked, the computer is rebooted automatically and the BitLocker system will encrypt the hard drive after the reboot is completed.
Encrypting a disk in Mac OSX
Much like the Windows operating system, the Apple OSX operating system also includes a way to encrypt the entire disk. While the Windows operating system has the BitLocker system, the Apple OSX operating system has a software package called FileVault. As Apple talks about in their Knowledge Base article number ht4790, which you can review at http://basicsofdigitalprivacy.com/go/ht4790, you need to be running Apple OS X Lion or Mountain Lion and you’ll need to have “Recovery HD” installed on your startup drive.
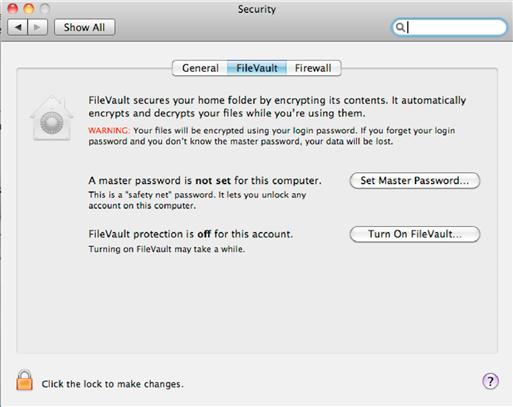
FileVault is enabled and configured from within the System Preferences. Within System Preferences, open “Security & Privacy” and then click the FileVault tab as shown in Figure 4.8. From here, you can set the master password, which allows you to unlock any account on the computer even when it has been encrypted. You can also turn FileVault on by clicking the “Turn On FileVault” button.
After clicking the “Turn On FileVault” button, all the users of the computer will need to enter their password if you want them to be able to turn on the computer. If the users don’t enter their password, they won’t be able to turn on the computer or wake up the computer when it is sleeping or hibernating.
Next, you will be shown your recovery key, which will be different for each computer. Be sure to write down this password and store it in a safe place as this password will be needed if you lose access to your data. The copy of the key that you keep should not be stored on the computer that you are encrypting as if you lose your password, you won’t be able to access the key, so you will have lost everything on the computer. You will at this point be given the option to store the recovery key on Apple’s servers. This protects you from losing the encryption key. Apple will secure the encryption key with a series of questions and answers based on personal information about you. When putting these answers in, make sure that you remember exactly how you put them in because if the answers are even slightly wrong, Apple’s applications won’t be able to decrypt the key and allow you to use it.
At this point, the computer will reboot pretty quickly. When it does, log in to the computer like normal. This will allow the FileVault application to continue encrypting the hard drive. Normally, this initial encryption process takes a few hours to complete.
Additional information about changing your key and decrypting the drive can be found in Apple’s Knowledge Base article ht4790, which you can review at http://basicsofdigitalprivacy.com/go/ht4790.
What do those website security logos mean?
Lots of websites out there have security logos on them. They are there to make you feel better about purchasing products from them or to make you feel better about uploading personal information to them. There are a variety of websites that provide these security logos, and they all mean basically the same thing—nothing. That’s right; these logos that we want to see to ensure that the websites are providing a secure environment for doing business with the company that has the logo doesn’t mean anything at all.
These logos usually mean that the website does meet some very basic security requirements when it comes to browsing the secure website, but they don't actually mean all that much security has been put in place. Just because the website has these logos doesn’t mean that the data is stored in an encrypted format, or that the company is doing any auditing of what data the employees access in the system, or that there aren’t any security patches that haven’t been installed on the web servers or the database servers.
The logos, which I’m talking about, are the ones similar to the ones shown in Figure 4.9, which are available from a variety of companies such as Norton, VeriSign, Trustwave, and McAfee, among others.
The first problem with these sorts of logos is that they are pretty simple to simply copy and paste into your website. The perfect example is this book; this book obviously hasn’t been vetted by VeriSign or Norton as being properly secured, but there is their logo right there as Figure 4.9. I could easily place the graphic, which is this logo, and upload it to my website, and suddenly, the website looks like it is secure but it doesn’t actually have to be.
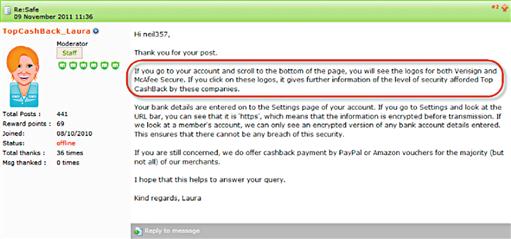
As pointed out by Troy Hunt in his blog post, which you can read at http://basicsofdigitalprivicy.com/go/troypost, websites aren’t secure just because they have logos on them. My favorite piece from Troy’s post is shown in Figure 4.10 where the website “Top Cashback” talks about how secure their website is.
Just because they have these logos doesn’t prove that the website is doing everything possible to secure their information. The reason that this is such a problem is because of the trust that the general public has with these logos. According to the Norton website (as of the writing of this book in the summer of 2013), which is owned by Symantec,
1. 77% of consumers recognize the Norton Secured Seal,
2. 65% of consumers agree that a website displaying the Norton Secured Seal is safe to browse and won’t give them a virus,
3. 55% of consumers agree that a website displaying the Norton Secured Seal means that the website protects their online privacy.
I’ve got issues with every one of these sales points that are listed here and broken down one by one:
#1 People have been taught and trained to think that these logos are important and that it’s all they need to look for.
#2 There is no guarantee that having the Norton Secured Seal shown in Figure 4.9 guarantees that the website won’t give you a virus. Over the years, there have been several occasions where the banner ad services that most of the websites use have served out viruses with the ads either because the banner ad website got a virus or because the person who created the virus was able to sneak an ad into the system, which has a virus as a part of the ad. No matter how the virus gets into the ad network, it’s the website that’ll be serving the ad with the virus in it to the end user.
#3 These logos don’t mean anything about protecting their online privacy. It doesn’t mean that the website is securing your data on their servers. It doesn’t mean that the company is protecting its end users from Internet attacks like cross site scripting errors or that all the communications between the web browser and the server are being done through the most secure possible levels of communication or that the website requires that you use a fully secure password. In fact, having these logos don’t actually mean that the website is even using any encryption between the web browser and the web server as shown in Figure 4.11.

Figure 4.11 rarfile.net with security logos and no data encryption.
You’ll see that the site rarefile.net, as of the summer of 2013, has both the Norton and McAfee logos, but the URL in the URL bar at the top starts with http:// instead of https://, which tells us that the data aren’t being encrypted between the web browser and the web server.
What all this means is that when you see these logos, you need to still be just as careful when using these websites as these logos are basically meaningless when it comes to proving that a website is secure and safe to use.
When Tech Support calls you
There are variety of companies and people out there that want your money. Some of them will buy your identity online for a few dollars, some of them will dig through a company’s trash to find your personal details, and some of them will simply call you and ask you for your money, and a large number of people will simply hand it over.
A popular scam at the time of writing this book in the summer of 2013 is for someone to call you up and tell you that they are from large companies’ technical support department and that they are calling to tell you that you have a virus and that they will help you get the virus off of your computer. They’ll start off helping you for free, usually by having you install some software on your computer. Then, they will tell you that you need to pay them to complete the support. At this point, the software, which they have installed on your computer, probably includes something called a key logger. A key logger is designed to keep track of every keystroke that you enter. The more complex of them will watch for specific strings such as typing in 16 numbers in a row followed by four more numbers and then three more numbers. You’ll probably recognize this pattern as being a credit card number (16 digits, 15 for American Express), the expiration date (4 digits), and the security code on the back of the card (3 digits). They will also watch for things like common tax numbers such as the 9 digits numbers we use here in the United States as Social Security or Tax ID Numbers. When you give them your credit card number, they’ll charge a small amount of money to the card usually a couple of hundred dollars telling you that it is the fee to remove the virus. Sometimes, they will tell you that the fee is to give you a proper license of Windows for your computer because your license was stolen (also called pirated).
No matter how much these people charge you, they aren’t selling anything that is legitimate. The virus removal wasn’t real, and in fact, they probably installed a virus on your computer as a part of the process. If they sold you a Windows license or a Microsoft license (or really a license of any kind), that isn’t real either. They have no way of knowing if your license for Windows is real or not, and they have no ability to sell you a Windows license. The people who are running this scam are very good at it, and this scam is very inexpensive for them to run. With a few Google Voice accounts or using some other forms of free Voice over IP (VoIP) technology, they can call anyone from anywhere and look like they are calling from anywhere that they want to be calling from. If you are in the United States, they will appear to be calling you from the United States. If you are in England, they will call you from an English phone number, the same goes for France, Germany, Australia, etc.
Dealing with these scammers is very simple. As soon as they tell you that they are from Microsoft’s Tech Support and you didn’t call Microsoft’s Tech Support, just hang up the phone. Odds are they will just move on to someone else. If you made the mistake of giving them your credit card number, it is OK; things can be done to fix this. First, call your credit card company and explain what happened and tell them how much they said that they charged you and that you got scammed. The credit card company can simply reverse the charge. This shouldn’t cost you anything as they will simply take the money back from the account that charged your credit card (this may vary depending on your credit card company and your card member agreement as the country or state that you live in). You’ll also want to have the credit card company cancel that card number and issue you a new one. The worst part of all this is that you won’t have access to the credit card for a few days, while you wait for the new card to be e-mailed to you.
A large number of people that are taken by this scam don’t call the credit card company because they don’t want to admit that they got scammed. DO NOT be one of these people. These scammers have been running this scam for a long time, and they are very good at it and very convincing with their sales pitch. By not reporting it, you are putting money directly into their pockets and encouraging them to continue with the scam against other people. If required by your credit card company, contact the police and report the scammer and get a police report. In reality, this probably won’t do anything to the people running the scam as odds are they aren’t in your country or even in a country that your law enforcement could get to them in. The police won’t laugh at you and they won’t embarrass you when you report it. They understand that there are lots of people running these scams and that lots of people get caught up in these scams. Get the police report, get the charges refunded, and get a new card number. No harm, no foul.
Internet games and downloads
Things, which are downloaded or run from the Internet, are one of the many ways that a virus can get on to your computer. There are currently over 100,000 different computer viruses in existence, although most of those aren’t actually found in the wild on the Internet. For the most part, there are about 300 or so viruses that you really need to worry about at any one time; however, each of those base viruses could have dozens of variants, which are all slightly different from each other.
For a computer virus to attack your computer, it needs to have access to your computer. The easiest way for it to get access to your computer is for you to download it either via an application such as a computer game; a flash game, which you play on a website; or an ad, which you view on a webpage. When you install an application, you assume that the application doesn’t have any malicious code within it. An application can be written to do just about anything with your computer that the developer wants to do, and you don’t have to be aware of what the application is doing. As an example, just because you are playing a card game on the screen doesn’t mean that the application isn’t also going through all your files on your computer looking for credit card numbers and e-mailing any that it finds to the application’s creator.
When it comes to downloading games from the Internet or playing games online, only use trusted sources to download the games and applications from. Some places, which are typically safe to download games from, include websites such as msn.com, download.com, FaceBook.com, and games.yahoo.com to name just a few. Random websites, which are publishing just a couple of games for download and aren’t major publishers, should not be taken at their word that they are safe to download from.
Application stores
With the introduction of Windows 8, you now have the Windows Store, which is available through the Store button on the Windows 8 Start menu as shown in Figure 4.12.
The Windows Store is a great place to download applications and games as those games and applications have been reviewed by Microsoft. This review process ensures that the games follow Microsoft’s terms of service and that the application isn’t being published by a computer that Microsoft knows as a scammer. While Microsoft doesn’t inspect every line of code within the applications, they do check to make sure that the application isn’t doing things that the developer says that it shouldn’t be doing by using some automated testing processes during their review process.
This goes right along with the Apple Store on the Apple operating system. Apple does an excellent job making sure that the applications, which are hosted within the Apple Store, are free from viruses and malware and are safe to install on your computer.
In either case, Windows or Apple, this doesn’t mean that you shouldn’t have an antivirus installed on your computer. There are a wide variety of antiviruses out there and many of them do a very good job. Some are better than others and some cost more than others.
Windows antivirus software
For the Windows operating system, Microsoft has an antivirus application called Microsoft Security Essentials, which they have released for free on their website at www.microsoft.com/security_essentials. There are also several other very good products out there such as Sophos (www.sophos.com), McAfee (www.mcafee.com), Norton Security Essentials (www.norton.com), and Trend Micro (www.trendmicro.com). Some of these take less memory than others, while some cost less than others.
Apple computers need antivirus software
There is a long-held belief that because you are using a Mac, you can’t get a virus on your computer. This couldn’t be further from the truth. While it is true that there are less viruses running around the Internet that attack the Apple operating systems, there are plenty of them out there, and without an antivirus installed, you’ll have no idea that one has tried to install itself on your computer.
Back in the day (the day being the late 1990s), there weren’t any viruses for the Mac computer. This wasn’t because the Apple operating systems of the day were more secure than the Windows operating systems of the day. It was purely a numbers game for the virus writers; in the late 1990s, there weren’t enough people using Apple computers compared to the number of people using Windows computers. Back in the late 1990s, Microsoft had well over 90% market share with Apple having between 5% and 8% market share. This means that as a virus writer, if you are going to spend money writing a virus and you want to make the most money possible off of that virus, then you want to target most computers possible, which are Windows computers. Today, the market has changed and Microsoft’s Windows operating system no longer has such a strong market share position with the Windows operating system now having less than 90% market share. This means that it is starting to become profitable for people to make viruses for other operating systems including the Apple operating system.
Cell phones and tablets
Cell phones are the newest attack vector for viruses as there are now cell phone-specific viruses out there. These viruses can be installed just like any normal application on the cell phone, often installed as a part of another application, which looks like another popular application. There are other ways to get a virus on cell phones. There have been flaws out there in some cell phones, which have allowed viruses to spread from phone to phone via text and picture messaging. You can read more about the specifics of the history of these mobile viruses at http://basicsofdigitalprivacy.com/go/mobile_virus. The official application stores such as the Android Market, Apple App Store, and Microsoft Store are the safe places to install applications from. Other application stores such as the Amazon Appstore are usually safe, but there are no guarantees. Other market places out there aren’t considered safe at all. They claim that they are safe, but they aren’t considered safe by the companies who make the phones or the companies who run the antivirus companies.
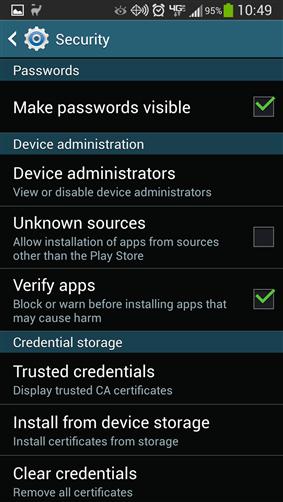
The Windows and Android mobile operating systems both have antivirus applications available for them. These antivirus applications can help ensure that there is nothing running on the phones, which there shouldn’t be. For Android phones, the best way to ensure that there are no viruses installed is to make sure that the phone is configured to only allow installation of applications from the Play Store. Where you configure this will depend on the version of the Android operating system. Typically, it will be found within the Security section of the Settings icon. If the “Unknown sources” check box is unchecked, then the phone will prevent the installation of applications from third-party application stores as shown in Figure 4.13. When this setting is disabled, any application store such as the Amazon Appstore won’t be available.
The recommendation is that if you are using another well-known application store such as the Amazon Appstore that you enable the “Unknown sources” setting each time you plan to install an application, then disable the setting as soon as the application has been installed. It is also recommended that you install an antivirus on the phone to ensure that you are protected from every application that is installed and updated no matter which application store the application is installed from.
With the iOS for the iPhone, there are antivirus applications available but they require that the phone be jail-broken so that the antivirus can be installed. This breaks Apple’s security model for the iOS operating system, which is a pretty locked down operating system. While jailbreaking, the phone is a whole different conversation; if the iPhone (or iPad or iPod) is jail-broken, it is still recommended that an antivirus is installed.
Viruses for cell phones typically do two different things. The first thing they do is monitor your keystrokes and attempt to capture the usernames, passwords, credit card information that you enter for websites like Amazon and eBay, and your application store (or marketplace, etc.) account information. The other thing that these viruses will attempt to do is spread to everyone that you know. This is done via the phone numbers and e-mail addresses in your contact list. Your contacts will all get a text message and/or an e-mail that will have an attachment or a link, which will attempt to install the virus on their devices.
One last thing that these viruses may attempt to do is to dial phone numbers with specific US area codes, which charge you money just for making the phone call with the profits of these numbers being paid to the virus writers. These area codes include 809, 284, or 876 and a few others. The reason that these US area codes can charge high rates per minute is because these aren’t actually in the United States. These numbers are actually based out of the Caribbean Islands so US billing laws don’t apply as the Caribbean Islands aren’t a part of the United States. The charges for these calls simply show up on your cell phone bill.
If you get hit with one of these viruses, contact your cell phone provider if you see calls on your cell phone bill to these area codes that you didn’t make. The cell phone providers will work with the phone company where these numbers are based to attempt to get your charges reversed. This does require that your cell phone company will work with the offshore phone company as the charges are billed from the offshore phone company and your cell phone company can’t refund the charges directly on their own.
Summary
When it comes to protecting the information on your computer from being viewed after a computer theft, data encryption is your best bet. Data encryption will force the person who is trying to read your data to have your password in order to get access to that data. When protecting yourself from a virus, an antivirus product installed on your computer and cell phone is critical in ensuring that the information that you place on the computer or cell phone isn’t going to anyone but the people that are supposed to get the information.