Usernames and Passwords for Websites
Abstract
This chapter talks about how to select a username and password so that they are easy to remember, yet hard for someone else to figure out.
Keywords
username; password; passphrase
Information in This Chapter
This chapter talks about how to select usernames and passwords that are easy to remember while being hard for someone else to figure out so that people can’t easily get into your accounts.
Picking a username
When getting signed up for a website, you are asked for a variety of information such as your name, address, phone number, e-mail address, and, most importantly, a username and password. Selecting the username and password is very important. This is especially true of the username as often you can’t change the username once you have signed up for the service.
When picking a username, it is important to select a username that is easy to remember but isn’t going to be all that easy for someone to guess. If the username is displayed, on a chat forum website, for example, then this obviously becomes much less important as the username will probably be displayed on the website for all the users to see. At the very least, when selecting usernames for use on Internet websites, you want to have two different usernames, one for casual use websites like Twitter, Facebook, and any other sites that you use and a second username for use on sites that would include your banking websites and any other sort of financial institution’s websites. The reason for this is that while many websites out there take a lot of care in ensuring that their customers' information isn’t going to be compromised, it isn’t worth the risk of using the same username for multiple websites. There have been several data breaches that have happened over the years. One in particular affected people across the widest range of social factors because the data breach happened to users of the website eHarmony.com. You can read more about this data breach at http://basicsofdigitalprivacy.com/go/eharmony. When part of the user list for eHarmony was leaked, this was a wake-up call to a lot of people about how they should be setting up usernames and passwords for websites as anyone who was using the same username and password for their eHarmony account and for their banking information had just had someone else have access to their banking username and password.
Many people like to use their e-mail address for their banking website or credit card company website. Doing this is very convenient as it is very easy to remember your own e-mail address. However, if the attacker is able to figure out your e-mail address, which really isn’t all that hard most of the time, you’ve now given the attacker one of the two pieces of information required to get into your bank account. Because of this, it is recommended that you use a username that is not an e-mail address for all banking and financial websites. This way, if someone was going to attempt to break into your online banking profile, they wouldn’t have access to your username just by knowing what your e-mail address is. If you have multiple e-mail accounts using one for social networking and friends to contact you on and a second e-mail address that is used only for banking information, then using the e-mail address that you only use for banking information should be a fairly safe practice, but only if that e-mail address is never given out to anyone other than the bank.
When selecting the username, make sure that you don’t include any sort of descriptive information in the username. Specific things to avoid include where you live or were born, your birthdate, or any information beyond your name that could be used to identify you other than your name. Beyond these simple rules, your username can be just about anything that you want. The reason that we don’t want to include any sort of additional personal information in the username is that this personal information will probably be used as the answers to the security questions that you would need to answer if you forgot your password. While putting something like the year of your birth into the username, marks1972, for example, will probably make it more likely that the username is available, you’ve just told a potential attacker what one of the answers to the security question is. A perfect example of figuring this information from someone else is shown during a video that was recorded during the Defcon conference in 2010. You can watch this video at http://basicsofdigitalprivacy.com/go/StolenComputer. This video does have some language that one might find offensive, be warned. The presentation starts about 3 minutes into the video, and the part where the presenter talks about using the usernames to figure out the birthdate of the person who stole his computer starts about 13 minutes into the video.
Picking a password
Picking a password requires much more care than picking your username. Passwords should be strong and unique for each website. Passwords that are strong have very specific characteristics. There are four groups of characters on the standard keyboard: lowercase letters, uppercase letters, numbers, and special characters (typically found on the number keys when you hold the shift key down). For passwords to be considered strong, they need to contain at least three of those four types of characters. If you use all four of types of characters, that is even better. In addition to using at least three of the character types, the password should be at least eight characters long. The reason that we want to have passwords to be long is to increase the complexity of the password. The more complex the password is, the harder it will be for someone to brute-force attack the password. This is talked about more in the following section. The end result of a password that is very long is that it takes someone so long to attempt to guess the password by using a brute-force method that they simply give up and move on to another person to attempt to attack.
How passwords are figured out
There are a variety of ways for an attacker to figure out what the password for an account is. The first way is the one that is specifically related to having a long and strong password and is the only method of attack that you, the account owner, can help prevent. This attack method is called a brute-force attack. In this kind of attack, the person who is trying to figure out the password basically tries every password possible starting with just a single character up to a password as long as is needed. This is done with scripts and applications that are specifically designed to try the same username with different passwords over and over very quickly. These applications can try usernames and passwords basically as quickly as the website or the application can try the username and password. Websites that are properly built will have protection for a brute-force attack built into the website. This protection will be to only allow a specific number of failed log-in attempts before the user’s account is locked so that no further attempts can be tried. You may have run into this sort of protection on the website when attempting to log into the website and you can’t remember the password. After a few tries (the specific number of tries is completely up to the website developer), the account is locked and you have to either call their customer support department or go through the forgot password process in order to get the account unlocked.
The longer the password is, the longer it will take for the password to be figured out. Just a few years ago, it could take months or years to figure out a password. While just a few years later, a password can be figured out in just days and for just a few dollars. The reason that this is the case is because of the power of cloud computing. Back in the olden days of technology, also known as the mid-1990s, if someone wanted to break into an account, the person trying would typically only have one or two computers at their disposal. In today’s world of cloud computing, hundreds or thousands of computers can be rented from various cloud computing providers for just a few dollars, and all of these computers can be used all at once to try all the various options of passwords all at once. The economics of the cost to brute force a password are changing very rapidly. However, a great article was put together in October of 2009 by a company called Electronic Alchemy and can be read at http://basicsofdigitalprivacy.com/go/passwordcosts.
Other attack methods involve the attacker breaking into the website through other methods that aren’t anything that we, the end users of the applications, can do anything about. In these attack methods, the attacker downloads the usernames and the encrypted passwords from the website’s database. The attacker then attempts to break the encryption on the passwords. Unfortunately, there is nothing that you as the end user can do to prevent this sort of attack. You as the user of the website need to trust that the website is encrypting the passwords with a strong level of encryption so that if the passwords are attacked, it takes as long as possible to get through the encryption. This leads directly into our next section.
Unique passwords
Every website and application that is used should have a different password setup for it. This makes figuring out which password is used for each application difficult, but it makes the passwords much more secure. The reason that we want to use different passwords for each website is so that if one password is compromised, the attacker doesn’t get access to every website that you use.
When setting up unique passwords, do not include the name of the website as the unique part of the password. Doing so is basically the same as not putting any sort of unique value into the password field as the attacker will easily enough know what the unique value is in your other passwords. For example, if the part of the password that doesn't change was “password” using this format we could put the website name after the password. So if the website that the account was being set up for was www.bestbuy.com, having the password of “passwordbestbuy” would tell the attacker that your password for www.target.com would be “passwordtarget” and the password for www.ebay.com would be “passwordebay,” and so on.
Creating unique passwords
There are a variety of applications that can be used to help you create passwords that should be totally unique for each website. None of these applications are really any better or worse than others. The important thing is that an application is used as they will create passwords that are very random. Different password-generating applications do this in different ways.
One of the password-generating applications is called KeePass. KeePass does a few things for you as the user. The first thing that this application does is create new passwords that are very long and very strong. This allows you to have a truly random and very long password for each unique website that you use. The second thing that the application does is store the passwords in an encrypted database that makes it so that you don’t need to memorize all of these long and strong passwords that are basically impossible to memorize. The passwords within KeePass are stored with usernames as well as the website that the username and password are for, making it very easy for you to copy and paste the information from the KeePass application into the web browser when you need to log into the website.
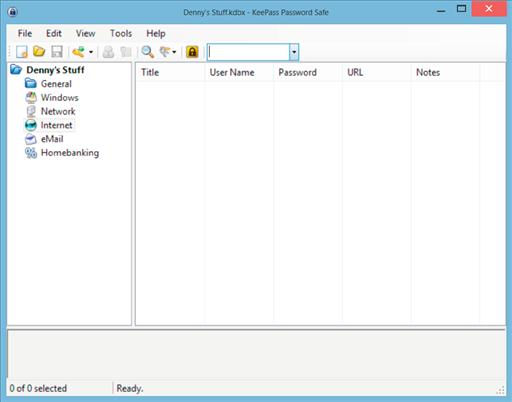
Using KeePass to create these unique passwords and store them is quite easy. After downloading the KeePass application from www.KeePass.org and installing the application, open the application and you should see a screen similar to the one shown in Figure 2.1.
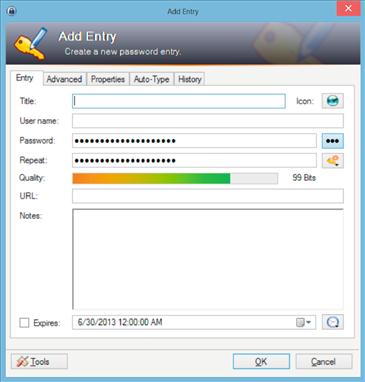
Select the menu item on the left where you want to save usernames and passwords; typically this would be under the Internet option. Right click on the white area on the right-hand side of the screen and select “Add Entry” from the context menu that appears. This will open a window similar to that shown in Figure 2.2.
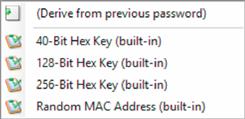
In the title field, enter a title of the entry; typically this would be the URL for the website, for example, www.basicsofdigitalprivacy.com. In the username field, enter the username for the website that you will be using. The password field and the repeat field are already filled out. Clicking the button with three dots on it will show the generated password. If a more secure password is desired, click the button below the button with three dots, then select “Generate Using Profile,” and then select either the 128-bit profile or the 256-bit profile as shown in Figure 2.3.
In the URL field, enter the URL for the website. Clicking the OK button saves the setting into the KeeSave application’s database.
Modern web browsers can all store usernames and passwords in a secure manner so that you don’t have to type in the username or password or to copy and paste from the password application. The passwords are stored within the web browser setting as encrypted values so the risk of the values being stolen from the web browser settings is very low. That being said, most web browsers make it very easy, sometimes too easy, to view the passwords on the screen. Usually, you just need to go into the settings screen for the various web browsers and there will be a button somewhere where you can view the passwords that are saved. This protects your passwords from being downloaded by someone, but not from someone who sits in front of your computer and has access to view the screen.
Passphrases
A great option when picking a new password is to instead use a passphrase. A passphrase is a normal English (or other language) phrase that you use as your password. An example of a great passphrase to use could be a quote from the Beatles song “A Hard Day’s Night” such as “Itsb3enaharddaysn!ght” which takes the phrase “It’s been a hard day’s night” from the song, removes the spaces, and changes a couple of characters from letters to numbers and characters. Normally, passwords which are considered to be strong are very hard to remember because they are long and have numbers and characters placed throughout the password. Normal passwords are often hard to remember while passphrases which are based on songs, TV shows, movies, famous quotes, etc., are very easy to remember.
Two-factor authentication
Another fantastic way to ensuring a unique password for websites is to use a system called two-factor authentication. With two-factor authentication, there are two pieces of information that are required. The first is a code that you as the user know and the website stores in their system. The second piece of information is a randomly generated number that is generated by either a key fob, an application on your phone, an application on your computer, or a text message sent to your cell phone. Both pieces of information are put into the website’s password field when logging into the website.
Two-factor authentication is nice because the passwords can only be used once, and the random values are only valid for a short period of time. For example, if using a key fob, the key fob generates a new value every 60 seconds and if the password isn’t used within the 60-second window, the password becomes invalid and not able to be used.
As of the time of the writing of this book, in the summer of 2013, there were a wide variety of companies who have made two-factor authentication systems. However, most if not all of these applications are specific to just one or two companies with few companies making their two-factor authentication systems available to other websites or applications. This means that when using two-factor authentication via your phone, you may end up having to have several applications installed on your phone.
Using fob-based systems
Fob-based two-factor authentication systems are probably the oldest example and the easiest to use. The fob, shown in Figure 2.4, doesn’t require any user interaction to use other than to enter the information into the website or application when prompted.
These fob-based systems require that you have two pieces of information when using the fob. You need to have the actual device that has the changing number on it as shown in Figure 2.4, but you also need to know a static value that doesn’t change. When logging in with the fob, you take the static value that you know, for example, 1234, and then put the value from the fob after it. Using the value from Figure 2.4, this would mean that the password that would be used to log into the website or application would be “1234497364.”
Using software-based two-factor authentication systems
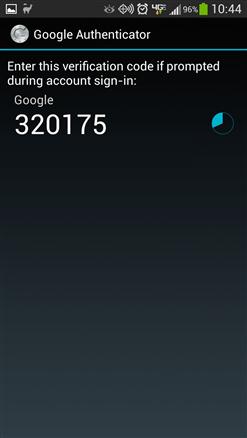
Software-based two-factor authentication systems, shown in Figure 2.5, work in a very similar method to the fob. The big difference between using the fob-based method and using a software application-based method is that instead of needing a fob for each website that you wish to use, you simply use a single application (or two applications if some websites using Apple’s system and others use Google’s system). This also prevents you from having to carry and track these additional physical fobs instead of putting the two-factor authentication within a device that you are already going to carry with you at all times anyway. Whenever you are using two-factor authentication on your cell phone, be sure to secure your cell phone with the most secure method available on the phone. If you don’t and the phone is lost or stolen, then whoever has the phone also has all of your two-factor authentication codes as well.
In order to use either Apple or Google’s system when prompted, simply bring up the application on your mobile device and select the site that you wish to use. Then, enter the number as prompted.
Using a text-messaging-based system
Using a text-messaging-based system is just about as easy as using the other systems that have been discussed in this chapter. When using a text-messaging-based system when beginning the log-in process, the website requests a username and a password. Upon entering the correct username and password, the cell phone that is tied to the account is sent a text message that includes a pin code, which can only be used once to log in. The webpage then prompts you to enter this pin number into the website. Typically, when using these pin-based systems, a wrong pin number can only be used three to five times at which point a new pin number is needed. This prevents someone from simply trying all the possible pin numbers to find the correct one.
These text-message-based systems are considered to be pretty secure. One of the reasons for this security is due to the fact that with text messaging, the text message is only delivered once. Even if someone took a SIM card from one cell phone and inserted it into another cell phone, the old text messages wouldn’t be downloaded again. Even if someone was able to gain access to the older codes that had been texted to someone, those codes shouldn’t be valid codes anymore. While it is up to the company that sends the text message to determine how long the codes are valid for, it is usually a short window of time usually just a few minutes or up to an hour.
These text-message-based two-factor authentication systems work fairly well for most people and are typically very secure as the odds of someone who is attempting to break into your account having physical access to your cell phone is minimal. However, these systems are not perfect. The biggest problem with them is that they typically require that you are physically located in your home country. While this isn’t an issue for many people, for those that travel internationally on business, this prevents those customers from having access to the account while they are outside the country. The reason for this is that most international travelers do not use International Roaming on their cell phones when in other countries. The first reason is the cost as cell phone companies charge incredibly high rates when traveling in other countries. The second is that in a lot of cases, the needed cell phone network simply isn’t available in other countries. The perfect example for this is the CDMA network that Verizon’s cell phones use. As of the writing of this book in the summer of 2013, there was little to no CDMA network in Europe, so if a traveler needed to receive a text message via their cell phone and they were a Verizon customer with their normal cell phone in Europe, there would be no way to receive the text message.
The more important the longer they should be
The usernames and passwords for some websites have become more important than others in recent years. This isn’t because of the information that the website contains but instead because the website grants you access to other websites. This is done through a system called OAUTH (pronounced o-auth) where a website allows its username and password system to be used by other websites. This is good for the website that allows its username and password system to be used via OAUTH because it makes the OAUTH website more important in the global Internet system. This is also good for the websites that are using the OAUTH service on the other website because the website that is using the OAUTH service doesn’t need to store their own username and password.
Due to the fact that the website that has the OAUTH service can be used to sign into many other websites, the password that is used for these websites should be the strongest password possible. There are many different websites out there that can serve as OAUTH providers. This includes websites like openid.com, myopenid.com, Verisign.com, and other sites like google.com and facebook.com. It doesn’t matter which of these sites is used to sign into the various other websites, but whichever one (or ones) is used, the password that is used should always be the strongest possible password. Using the techniques like the ones talked about in the “Picking A Password” section earlier in this chapter will help you to ensure that you have a strong password that is secure and will prevent others from gaining access to all the other websites that you use.
Summary
Having strong and unique passwords is key to protecting yourself in today’s world on the Internet. While we like to think of the Internet as a nice peaceful place where everyone can get along, the reality is that the Internet is more like the Wild West than a peaceful place. There are lots of people out there who want to take your money and your identity and use it for their own purposes, which usually aren’t going to turn out well for you. Protecting yourself proactively is the only way to ensure that you aren’t taken advantage of online.