Chapter 1. The Importance of Threat Data and Intelligence
This chapter covers the following topics related to Objective 1.1 (Explain the importance of threat data and intelligence) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Intelligence sources: Examines open-source intelligence, proprietary/closed-source intelligence, timeliness, relevancy, and accuracy
• Confidence levels: Covers the importance of identifying levels of confidence in data
• Indicator management: Introduces Structured Threat Information eXpression (STIX), Trusted Automated eXchange of Indicator Information (TAXII), and OpenIOC
• Threat classification: Investigates known threats vs. unknown threats, zero-day threats, and advanced persistent threats
• Threat actors: Identifies actors such as nation-state, hacktivist, organized crime, and intentional and unintentional insider threats
• Intelligence cycle: Explains the requirements, collection, analysis, dissemination, and feedback stages
• Commodity malware: Describes the types of malware that commonly infect networks
• Information sharing and analysis communities: Discusses data sharing among members of healthcare, financial, aviation, government, and critical infrastructure communities
When a war is fought, the gathering and processing of intelligence information is critical to the success of a campaign. Likewise, when conducting the daily war that comprises the defense of an enterprise’s security, threat intelligence can be the difference between success and failure. This opening chapter discusses the types of threat intelligence, the sources and characteristics of such data, and common threat classification systems. This chapter also discusses the threat cycle, common malware, and systems of information sharing among enterprises.
“Do I Know This Already?” Quiz
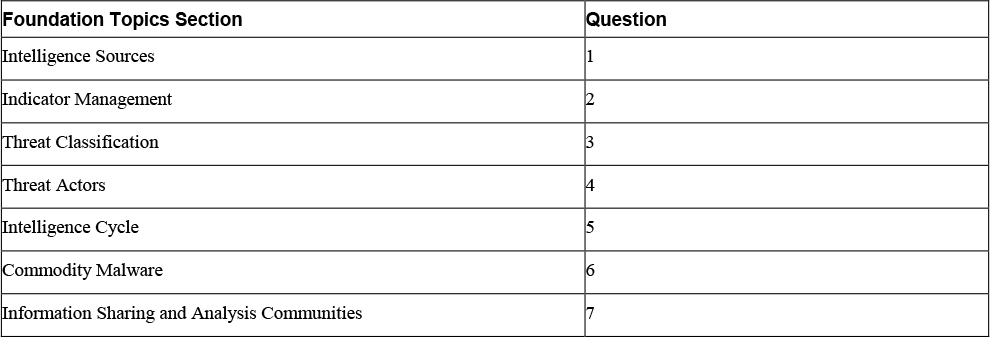
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these seven self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks” section. Table 1-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 1-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Which of the following is an example of closed-source intelligence?
a. Internet blogs and discussion groups
b. Print and online media
c. Unclassified government data
d. Platforms maintained by private organizations
2. Which of the following is an application protocol for exchanging cyber threat information over HTTPS?
a. TAXII
b. STIX
c. OpenIOC
d. OSINT
3. Which of the following are threats discovered in live environments that have no current fix or patch?
a. Known threats
b. Zero-day threats
c. Unknown threats
d. Advanced persistent threats
4. Which of the following threat actors uses attacks as a means to get their message out and affect the businesses that they feel are detrimental to their cause?
a. Organized crime
b. Terrorist group
c. Hacktivist
d. Insider threat
5. In which stage of the intelligence cycle does most of the hard work occur?
a. Requirements
b. Collection
c. Dissemination
d. Analysis
6. Malware that is widely available for either purchase or by free download is called what?
a. Advanced
b. Commodity
c. Bulk
d. Proprietary
7. Which of the following information sharing and analysis communities is driven by the requirements of HIPAA?
a. H-ISAC
b. Financial Services Information Sharing and Analysis Center
c. Aviation Government Coordinating Council
d. ENISA
Foundation Topics
Intelligence Sources
Threat intelligence comes in many forms and can be obtained from a number of different sources. When gathering this critical data, the security professional should always classify the information with respect to its timeliness and relevancy. Let’s look at some types of threat intelligence and the process of attaching a confidence level to the data.

Open-Source Intelligence
Open-source intelligence (OSINT) consists of information that is publicly available to everyone, though not everyone knows that it is available. OSINT comes from public search engines, social media sites, newspapers, magazine articles, or any source that does not limit access to that information. Examples of these sources include the following:
• Print and online media
• Internet blogs and discussion groups
• Unclassified government data
• Academic and professional publications
• Industry group data
• Papers and reports that are unpublished (gray data)

Proprietary/Closed-Source Intelligence
Proprietary/closed-source intelligence sources are those that are not publicly available and usually require a fee to access. Examples of these sources are platforms maintained by private organizations that supply constantly updating intelligence information. In many cases this data is developed from all of the provider’s customers and other sources.
An example of such a platform is offered by CYFIRMA, a market leader in predictive cyber threat visibility and intelligence. CYFIRMA announced the launch of cloud-based Cyber Intelligence Analytics Platform (CAP) v2.0. In 2019, using its proprietary artificial intelligence and machine learning algorithms, CYFIRMA helping organizations unravel cyber risks and threats and enable proactive cyber posture management.
Timeliness
One of the considerations when analyzing intelligence data (of any kind, not just cyber data) is the timeliness of such data. Obviously, if an organization receives threat data that is two weeks old, quite likely it is too late to avoid that threat. One of the attractions of closed-source intelligence is that these platforms typically provide near real-time alerts concerning such threats.
Relevancy
Intelligence data can be quite voluminous. The vast majority of this information is irrelevant to any specific organization. One of the jobs of the security professional is to ascertain which data is relevant and which is not. Again, many proprietary platforms allow for searching and organizing the data to enhance its relevancy.
Confidence Levels
While timeliness and relevancy are key characterizes to evaluate with respect to intelligence, the security professional must also make an assessment as to the confidence level attached to the data. That is, can it be relied on to predict the future or to shed light on the past? On a more basic level, is it true? Or was the data developed to deceive or mislead? Many cyber activities have as their aim to confuse, deceive, and hide activities.
Accuracy
Finally, the security professional must determine whether the intelligence is correct (accuracy). Newspapers are full these days of cases of false intelligence. The most basic example of this is the hoax email containing a false warning of a malware infection on the local device. While the email is false in many cases it motivates the user to follow a link to free software that actually installs malware. Again, many cyber attacks use false information to misdirect network defenses.

Indicator Management
Cybersecurity professionals use indicators of compromise (IOC) to identify potential threats. IOCs are network events that are known to either precede or accompany an attack of some sort. Managing the collection and analysis of these indicators can be a major headache. Indicator management systems have been developed to make this process somewhat easier. These systems also provide insight into indicators present in other networks that may not yet be present in your enterprise, providing somewhat of an early-warning system. Let’s look at some examples of these platforms.
Structured Threat Information eXpression (STIX)
Structured Threat Information eXpression (STIX) is an XML-based programming language that can be used to communicate cybersecurity data among those using the language. It provides a common language for this communication.
STIX was created with several core purposes in mind:
• To identify patterns that could indicate cyber threats
• To help facilitate cyber threat response activities, including prevention, detection, and response
• The sharing of cyber threat information within an organization and with outside partners or communities that benefit from the information
While STIX was originally sponsored by the Office of Cybersecurity and Communications (CS&C) within the U.S. Department of Homeland Security (DHS), it is now under the management of the Organization for the Advancement of Structured Information Standards (OASIS), a nonprofit consortium that seeks to advance the development, convergence, and adoption of open standards for the Internet.
Trusted Automated eXchange of Indicator Information (TAXII)
Trusted Automated eXchange of Indicator Information (TAXII) is an application protocol for exchanging cyber threat information (CTI) over HTTPS. It defines two primary services, Collections and Channels. Figure 1-1 shows the Collection service. A Collection is an interface to a logical repository of CTI objects provided by a TAXII Server that allows a producer to host a set of CTI data that can be requested by consumers: TAXII Clients and Servers exchange information in a request-response model.

Figure 1-1 Collection Service
Figure 1-2 shows a Channel service. Maintained by a TAXII Server, a Channel allows producers to push data to many consumers and allows consumers to receive data from many producers: TAXII Clients exchange information with other TAXII Clients in a publish-subscribe model.

Figure 1-2 Channel Service
These TAXII services can support a variety of common sharing models:
• Hub and spoke: One central clearinghouse
• Source/subscriber: One organization is the single source of information
• Peer-to-peer: Multiple organizations share their information
OpenIOC
OpenIOC (Open Indicators of Compromise) is an open framework designed for sharing threat intelligence information in a machine-readable format. It is a simple framework that is written in XML, which can be used to document and classify forensic artifacts. It comes with a base set of 500 predefined indicators, as provided by Mandiant (a U.S. cybersecurity firm later acquired by FireEye).
Threat Classification
After threat data has been collected though a vulnerability scan or through an alert, it must be correlated to an attack type and classified as to its severity and scope, based on how widespread the incident appears to be and the types of data that have been put at risk. This helps in the prioritization process. Much as in the triage process in a hospital, incidents are not handled in the order in which they are received or detected; rather, the most dangerous issues are addressed first, and prioritization occurs constantly.
When determining vulnerabilities and threats to an asset, considering the threat actors first is often easiest. Threat actors can be grouped into the following six categories:
• Human: Includes both malicious and nonmalicious insiders and outsiders, terrorists, spies, and terminated personnel
• Natural: Includes floods, fires, tornadoes, hurricanes, earthquakes, and other natural disasters or weather events
• Technical: Includes hardware and software failure, malicious code, and new technologies
• Physical: Includes CCTV issues, perimeter measures failure, and biometric failure
• Environmental: Includes power and other utility failure, traffic issues, biological warfare, and hazardous material issues (such as spillage)
• Operational: Includes any process or procedure that can affect confidentiality, integrity, and availability (CIA)
When the vulnerabilities and threats have been identified, the loss potential for each must be determined. This loss potential is determined by using the likelihood of the event combined with the impact that such an event would cause. An event with a high likelihood and a high impact would be given more importance than an event with a low likelihood and a low impact. Different types of risk analysis should be used to ensure that the data that is obtained is maximized. Once an incident has been placed into one of these classifications, options that are available for that classification are considered. The following sections look at three common classifications that are used.
Known Threat vs. Unknown Threat
In the cybersecurity field, known threats are threats that are common knowledge and easily identified through signatures by antivirus and intrusion detection system (IDS) engines or through domain reputation blacklists. Unknown threats, on the other hand, are lurking threats that may have been identified but for which no signatures are available. We are not completely powerless against these threats. Many security products attempt to locate these threats through static and dynamic file analysis. This may occur in a sandboxed environment, which protects the system that is performing the analysis. In some cases, unknown threats are really old threats that have been recycled. Because security products have limited memory with regard to threat signatures, vendors must choose the most current attack signatures to include. Therefore, old attack signatures may be missing in newer products, which effectively allows old known threats to reenter the unknown category.
Zero-day
In many cases, vulnerabilities discovered in live environments have no current fix or patch. Such a vulnerability is referred to as zero-day vulnerability. The best way to prevent zero-day attacks is to write bug-free applications by implementing efficient designing, coding, and testing practices. Having staff discover zero-day vulnerabilities is much better than having those looking to exploit the vulnerabilities find them. Monitoring known hacking community websites can often help you detect attacks early because hackers often share zero-day exploit information.
Honeypots or honeynets can also provide forensic information about hacker methods and tools for zero-day attacks. New zero-day attacks against a broad range of technology systems are announced on a regular basis. A security manager should create an inventory of applications and maintain a list of critical systems to manage the risks of these attack vectors.
Because zero-day attacks occur before a fix or patch has been released, preventing them is difficult. As with many other attacks, keeping all software and firmware up to date with the latest updates and patches is important. Enabling audit logging of network traffic can help reconstruct the path of a zero-day attack. Security professionals can inspect logs to determine the presence of an attack in the network, estimate the damage, and identify corrective actions. Zero-day attacks usually involve activity that is outside “normal” activity, so documenting normal activity baselines is important. Also, routing traffic through a central internal security service can ensure that any fixes affect all the traffic in the most effective manner. Whitelisting can also aid in mitigating attacks by ensuring that only approved entities are able to use certain applications or complete certain tasks. Finally, security professionals should ensure that the organization implements the appropriate backup schemes to ensure that recovery can be achieved, thereby providing remediation from the attack.
Advanced Persistent Threat
An advanced persistent threat (APT) is a hacking process that targets a specific entity and is carried out over a long period of time. In most cases, the victim of an APT is a large corporation or government entity. The attacker is usually an organized, well-funded group of highly skilled individuals, sometimes sponsored by a nation-state. The attackers have a predefined objective. Once the objective is met, the attack is halted. APTs can often be detected by monitoring logs and performance metrics. While no defensive actions are 100% effective, the following actions may help mitigate many APTs:
• Use application whitelisting to help prevent malicious software and unapproved programs from running.
• Patch applications such as Java, PDF viewers, Flash, web browsers, and Microsoft Office products.
• Patch operating system vulnerabilities.
• Restrict administrative privileges to operating systems and applications, based on user duties.

Threat Actors
A threat is carried out by a threat actor. For example, an attacker who takes advantage of an inappropriate or absent access control list (ACL) is a threat actor. Keep in mind, though, that threat actors can discover and/or exploit vulnerabilities. Not all threat actors will actually exploit an identified vulnerability.
The Federal Bureau of Investigation (FBI) has identified three categories of threat actors: nations-state or state sponsors, organized crime, and terrorist groups.
Nation-state
Nation-state or state sponsors are usually foreign governments. They are interested in pilfering data, including intellectual property and research and development data, from major manufacturers, tech companies, government agencies, and defense contractors. They have the most resources and are the best organized of any of the threat actor groups.
Organized Crime
Organized crime groups primarily threaten the financial services sector and are expanding the scope of their attacks. They are well financed and organized.
Terrorist Groups
Terrorist groups want to impact countries by using the Internet and other networks to disrupt or harm the viability of a society by damaging its critical infrastructure.
Hacktivist
While not mentioned by the FBI, hacktivists are activists for a cause, such as animal rights, that use hacking as a means to get their message out and affect the businesses that they feel are detrimental to their cause.
Insider Threat
Insider threats should be one of the biggest concerns for security personnel. Insiders have knowledge of and access to systems that outsiders do not have, giving insiders a much easier avenue for carrying out or participating in an attack. An organization should implement the appropriate event collection and log review policies to provide the means to detect insider threats as they occur. These threats fall into two categories, intentional and unintentional.
Intentional
Intentional insider threats are insiders who have ill intent. These folks typically either are disgruntled over some perceived slight or are working for another organization to perform corporate espionage. They may share sensitive documents with others or they may impart knowledge used to breach a network. This is one of the reasons that users’ permissions and rights must not exceed those necessary to perform their jobs. This helps to limit the damage an insider might inflict.
Unintentional
Sometimes internal users unknowingly increase the likelihood that security breaches will occur. Such unintentional insider threats do not have malicious intent; they simply do not understand how system changes can affect security.
Security awareness and training should include coverage of examples of misconfigurations that can result in security breaches occurring and/or not being detected. For example, a user may temporarily disable antivirus software to perform an administrative task. If the user fails to reenable the antivirus software, he unknowingly leaves the system open to viruses. In such a case, an organization should consider implementing group policies or some other mechanism to periodically ensure that antivirus software is enabled and running. Another solution could be to configure antivirus software to automatically restart after a certain amount of time.
Recording and reviewing user actions via system, audit, and security logs can help security professionals identify misconfigurations so that the appropriate policies and controls can be implemented.
Intelligence Cycle
Intelligence activities of any sort, including cyber intelligence functions, should follow a logical process developed over years by those in the business. The intelligence cycle model specified in exam objective 1.1 contains five stages:
1. Requirements: Before beginning intelligence activities, security professionals must identify what the immediate issue is and define as closely as possible the requirements of the information that needs to be collected and analyzed. This means the types of data to be sought are driven by the types of issues with which we are concerned. The amount of potential information may be so vast that unless we filter it to what is relevant, we may be unable to fully understand what is occurring in the environment.
2. Collection: This is the stage in which most of the hard work occurs. It is also the stage at which recent advances in artificial intelligence (AI) and automation have changed the game. Collection is time-consuming work that involves web searches, interviews, identifying sources, and monitoring, to name a few activities. New tools automate data searching, organizing, and presenting information in easy-to-view dashboards.
3. Analysis: In this stage, data is combed and analyzed to identify pieces of information that have the following characteristics:
• Timely: Can be tied to the issue from a time standpoint
• Actionable: Suggests or leads to a proper mitigation
• Consistent: Reduces uncertainty surrounding an issue
This is the stage in which the skills of the security professional have the most impact, because the ability to correlate data with issues requires keen understanding of vulnerabilities, their symptoms, and solutions.
4. Dissemination: Hopefully analysis leads to a solution or set of solutions designed to prevent issues. These solutions, be they policies, scripts, or configuration changes, must be communicated to the proper personnel for deployment. The security professional acts as the designer and the network team acts as the builder of the solution. In the case of policy changes, the human resources (HR) team acts as the builder.
5. Feedback: Gathering feedback on the intelligence cycle before the next cycle begins is important so that improvements can be defined. What went right? What worked? What didn’t? Was the analysis stage performed correctly? Was the dissemination process clear and timely? Improvements can almost always be identified.
Commodity Malware
Commodity malware is malware that is widely available either for purchase or by free download. It is not customized or tailored to a specific attack. It does not require complete understanding of its processes and is used by a wide range of threat actors with a range of skill levels. Although no clear dividing line exists between commodity malware and what is called advanced malware (and in fact the lines are blurring more all the time), generally we can make a distinction based on the skill level and motives of the threat actors who use the malware. Less-skilled threat actors (script kiddies, etc.) utilize these prepackaged commodity tools, whereas more-skilled threat actors (APTs, etc.) typically customize their attack tools to make them more effective in a specific environment. The motives of those who employ commodity malware tend to be gaining experience in hacking and experimentation.
Information Sharing and Analysis Communities
Over time, security professionals have developed methods and platforms for sharing the cybersecurity information they have developed. Some information sharing and analysis communities focus on specific industries while others simply focus on critical issues common to all:
• Healthcare: In the healthcare community, where protection of patient data is legally required by the Health Insurance Portability and Accountability Act (HIPAA), an example of a sharing platform is the Health Information Sharing and Analysis Center (H-ISAC). It is a global operation focused on sharing timely, actionable, and relevant information among its members, including intelligence on threats, incidents, and vulnerabilities. This sharing of information can be done on a human-to-human or machine-to-machine basis.
• Financial: The financial services sector is under pressure to protect financial records with laws such as the Financial Services Modernization Act of 1999, commonly known as the Gramm-Leach-Bliley Act (GLBA. The Financial Services Information Sharing and Analysis Center (FS-ISAC) is an industry consortium dedicated to reducing cyber risk in the global financial system. It shares among its members and trusted sources critical cyber intelligence, and builds awareness through summits, meetings, webinars, and communities of interest.
• Aviation: In the area of aviation, the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) maintains a number of chartered organizations, among them the Aviation Government Coordinating Council (AGCC). Its charter document reads “The AGCC coordinates strategies, activities, policy and communications across government entities within the Aviation Sub-Sector. The AGCC acts as the government counterpart to the private industry-led ‘Aviation Sector Coordinating Council’ (ASCC).” The Aviation Sector Coordinating Council is an example of a private sector counterpart.
• Government: For government agencies, the aforementioned CISA also shares information with state, local, tribal, and territorial governments and with international partners, as cybersecurity threat actors are not constrained by geographic boundaries. As CISA describes itself on the Department of Homeland Security website, “CISA is the Nation’s risk advisor, working with partners to defend against today’s threats and collaborating to build more secure and resilient infrastructure for the future.”
• Critical infrastructure: All of the previously mentioned platforms and organizations are dedicated to helping organizations protect their critical infrastructure. As an example of international cooperation, the European Union Agency for Network and Information Security (ENISA) is a center of network and information security expertise for the European Union (EU). ENISA describes itself as follows: “ENISA works with these groups to develop advice and recommendations on good practice in information security. It assists Member States in implementing relevant EU legislation and works to improve the resilience of Europe’s critical information infrastructure and networks. ENISA seeks to enhance existing expertise in member states by supporting the development of cross-border communities committed to improving network and information security throughout the EU.” More information about ENISA and its work can be found at https://www.enisa.europa.eu.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 1-2 lists a reference of these key topics and the page number on which each is found.

Table 1-2 Key Topics

Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
proprietary/closed-source intelligence
Structured Threat Information eXpression (STIX)
Trusted Automated eXchange of Indicator Information (TAXII)
Review Questions
1. Give at least two examples of open-source intelligence data.
2. ________________ is an open framework that is designed for sharing threat intelligence information in a machine-readable format.
3. Match the following items with the correct definition.

4. Which threat actor has already performed network penetration?
5. List the common sharing models used in TAXII.
6. ________________are hacking for a cause, such as for animal rights, and use hacking as a means to get their message out and affect the businesses that they feel are detrimental to their cause.
7. Match the following items with their definition.

8. APT attacks are typically sourced from which group of threat actors?
9. What intelligence gathering step is necessary because the amount of potential information may be so vast?
10. The Aviation Government Coordinating Council is chartered by which organization?
