Chapter 12. Encryption and Hashing Concepts
This chapter covers the following subjects:
Cryptography Concepts—This section covers the basic terminology of cryptography including encryption, ciphers, and keys. It also discusses private versus public keys, symmetric versus asymmetric encryption, and public key encryption.
Encryption Algorithms—This section delves into the various symmetric algorithms, such as DES and AES, and some of the popular asymmetric algorithms such as RSA and elliptic curve.
Hashing Basics—Here, we investigate the most common way to verify the integrity of files: hashing. We cover basic hashing concepts and cryptographic hash functions, such as MD5, SHA, and NTLM.
This chapter covers the CompTIA Security+ SY0-201 objectives 5.1, 5.2, and 5.3.
Chances are that the majority of you will have limited experience with encryption. Because of this, I have written this chapter, and the following one, in a very to-the-point manner with simple analogous examples. I cover only what you need to know about encryption concepts, methods, and types. Encryption by itself is an entire IT field, but the CompTIA Security+ exam requires that you know only the very basics—the exam objectives only scrape the surface of encryption concepts. Keep all this in mind as you go through this chapter and the next. At the end of this chapter, I have left some links to more advanced encryption books and websites; although, they are not necessary for the exam.
Foundation Topics: Cryptography Concepts
Cryptography is the practice of hiding information. Let’s give a basic example of cryptography. When I was younger, some of the girls I knew would keep a black book with names, phone numbers, and so on. I’m still pretty sure to this day that I wasn’t in any of them! Anyway, a couple of those people did something that fascinated me—they would modify phone numbers according to a code they had developed. This was done to hide the true phone number of a special friend from their parents, or from teachers, and so on. It was a basic form of encryption, although at the time I didn’t realize it. I just referred to it as a “code.”
Essentially, it would work like this:
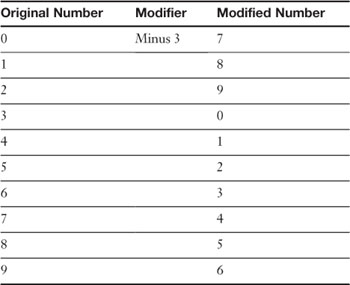
The person with the black book would take a real phone number such as 555-0386. They would then modify the number by stepping each number backward or forward X amount of steps. Let’s say the person decided to step each number between 0 and 9 backward by three steps, the resulting coded phone number would be 222-7053. I’m sure you see how that was done, but let’s break it down so that we can make an analogy to today’s data encryption. Table 12-1 shows the entire code used.
Table 12-1. Black Book Phone Number Encryption
![]()
In this example, each number between 0 and 9 corresponds to a number three digits behind it. BTW, the numbers cycle through: For example, the number 0 goes three steps back, starting at 0, to 9, 8, and then 7 in an “around-the-bend” fashion.
Let’s analogize. Each of the components in the table can be likened to today’s computer-based encryption concepts:
• The original number is like to original file data.
• The modifier is like to an encryption key.
• The modified number is like to encrypted file data.
I call this the “Black Book Example,” but I would guess that others have used similar analogies. Of course, this is a basic example; however, it should serve to help you to associate actual computer-based encryption techniques with this more tangible idea.
Now, for other people to figure out the original phone numbers in the black book, they would have to do the following:
Step 1. Gain access to the black book. This is just like gaining access to data. Depending on how well the black book is secured, this by itself could be difficult.
Step 2. Break the code. This would be known as decrypting the data. Of course, if the owner of the black book was silly enough to put the phone number encryption table in the book, well, then game over; it would be easy to decode. But if the owner were smart enough to memorize the code (and tell it to no one), making it a secret code, it would be much more difficult for another person to crack. Plus, the person could make the code more advanced, for example look at Table 12-2.
Table 12-2. Advanced Black Book Phone Number Encryption
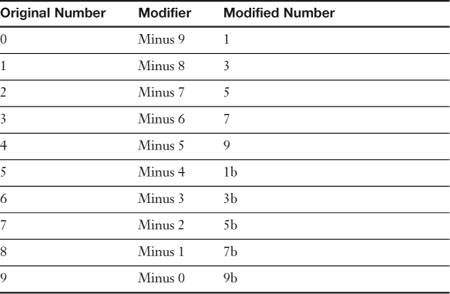
In this example, there is a different modifier (or key) for each original number. Because the modified numbers have duplicates, we place a letter next to each of the various duplicates to differentiate. This is tougher to decrypt due to the increased level of variations; but on the flipside, it is that much harder to memorize. Likewise, computers have a harder time processing more advanced encryption codes, and hackers (or crackers) have a difficult time processing their decryption.
At this point, only one person has legitimate access to the encryption codes. However, what if the person wanted to share phone numbers with another person, but still keep the numbers secret from everyone else? This would be known as a secret key.
We’ll be referring to this basic concept as we go through this chapter and the next.
Now that we have given a basic example, let’s define some terminology in a more technical way. We’ll start with cryptography, encryption, ciphers, and keys. You might want to read through this list twice because each definition builds on the last.
• Cryptography—By definition, cryptography is the practice and study of hiding information. It is used in e-commerce and with passwords. Most commonly, encryption is used to hide information and make it secret.
• Encryption—Encryption is the process of changing information using an algorithm (or cipher) into another form that is unreadable by others—unless, they possess the key to that data. Encryption is used to secure communications, and to protect data as it is transferred from one place to another. The reverse, decryption, can be accomplished in two ways: First by using the proper key to unlock the data, and second, by cracking the original encryption key. Encryption enforces confidentiality of data.
• Cipher—A cipher is an algorithm that can perform encryption or decryption. A basic example would be to take the plaintext word “code” and encrypt it as a ciphertext using a specific algorithm. The end result could be anything depending on the algorithm used, but for example, let’s say the end result was the ciphertext “zlab.” I don’t know about you, but “zlab” looks like gibberish to me. (Although if you Google it, I’m sure you’ll find all kinds of endless fun.) You’ve probably already guessed at my cipher—each letter of the plaintext word “code” was stepped back three letters in the alphabet. Other historical ciphers would use substitution and transposition as well. However, actual algorithms used are much more complex. Algorithms are well-defined instructions that describe computations from their initial state to their final state. IF-THEN statements are examples of computer algorithms. The entire set of instructions is the cipher. We’ll cover the various types of ciphers (again, also known as algorithms) in the section “Encryption Algorithms” later in this chapter.
• Key—The key is the essential piece of information that determines the output of a cipher. It is indispensable; without it there would be no result to the cipher computation. In the previous bullet, the key was the act of stepping back three letters. In the first black book example, the key was stepping back three numbers (a modifier of minus 3). Just like a person can’t unlock a lock without the proper key, a computer can’t decrypt information without the proper key (using normal methods). The only way to provide security is if the key is kept secret—or in the case that there are multiple keys, if one of them is kept secret. The terms key and cipher are sometimes used interchangeably, but you should remember that the key is the vital portion of the cipher that determines its output. The length of the key determines its strength. Shorter, weaker keys are desirable to hackers attempting to access encrypted data.
Keys can be private or public. A private key is only known to a specific user or users who keep the key a secret. A public key is known to all parties involved in encrypted transactions within a given group. An example of a private key would be the usage of an encrypted smart card for authentication. Smart cards and PCMCIA cards (PC Cards) are examples of devices that can store keys. An example of a public key would be when two people want to communicate securely with each other over the Internet; they would require a public key that each of them knows.
Encryption types, such as AES or RSA, are known as ciphers, key algorithms, or simply as algorithms; we refer to them as algorithms during the rest of this chapter and the next. There are basically two classifications of key algorithms: symmetric and asymmetric.
Symmetric Versus Asymmetric Key Algorithms
Some cryptographic systems use symmetric keys only, others use asymmetric, and some use both symmetric and asymmetric. It is important to know the differences between the two, and how they can be used together.
Symmetric Key Algorithms
The symmetric key algorithm is a class of cipher that uses identical or closely related keys for encryption and decryption. The term “symmetric key” is also referred to as the following: secret-key, private-key, single-key and shared-key (and sometimes as “session-key”). Examples of symmetric key algorithms include DES, 3DES, RC, and AES, all of which we discuss later in this chapter. Another example of a technology that uses symmetric keys is Kerberos. By default, Kerberos makes use of a third party known as a key distribution center for the secure transmission of symmetric keys, also referred to as tickets.
Note
Kerberos can optionally use public key cryptography (covered later in this chapter) by making use of asymmetric keys. This is done during specific authentication stages. Kerberos is covered in more depth in Chapter 8, “Physical Security and Authentication Models.”
Following are two types of symmetric key algorithms:
• A stream cipher is a type of algorithm that encrypts each byte in a message one at a time.
• A block cipher is a type of algorithm that encrypts a group of bits collectively as individual units known as blocks. For example, the Advanced Encryption Standard (AES) algorithm uses 128-bit block ciphers.
Symmetric key algorithms require a secure initial exchange of one or more secret keys to both the sender and the receiver. In our black book example, we mentioned that people might possibly want to share their cipher with someone else. To do so, they would need to make sure that they were alone and that no one was eavesdropping. It is also so with computers. The secure initial exchange of secret keys can be difficult depending on the circumstances. It is also possible to encrypt the initial exchange of the secret keys!
Symmetric ciphers can also be used for nonrepudiation purposes by adding a message authentication code, which is a small algorithm that will check the integrity of the cipher and notify the receiver if there were any modifications to the encrypted data. This way, the data cannot be denied (repudiated) when received.
Symmetric encryption is the preferred option when encrypting and sending large amounts of data.
Asymmetric Key Algorithms
Asymmetric key algorithms use a pair of different keys to encrypt and decrypt data. The keys might be related, but they are not identical or even close to it in the way symmetric keys are. The two asymmetric keys are related mathematically. Imagine that you were the night shift security guard for a warehouse that stored CPUs. When your shift is over you are required to lock up. But the warehouse uses a special lock. Your key can only lock the warehouse door, it cannot unlock it. Conversely, the morning watchman has a key that can only unlock the door, but not lock it. There are physical and electronic locks of this manner. This is analogous to asymmetric keys used in encryption. One key is used to encrypt data; the other dissimilar key is used to decrypt the data. Examples of asymmetric key algorithms include RSA, the Diffie-Hellman system, and the elliptic curve cryptography. SSL and TLS protocols use asymmetric key algorithms but generally do so in a public key cryptographic environment.
Public Key Cryptography
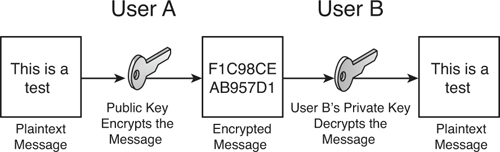
Public key cryptography uses asymmetric keys alone or in addition to symmetric keys. It doesn’t need the secure exchange of secret keys that was mentioned in the symmetric-key section. Instead, the asymmetric key algorithm creates a secret private key and a published public key. The public key is well known, and anyone can use it to encrypt messages. However, only the owner(s) of the paired or corresponding private key can decrypt the message. The security of the system is based on the secrecy of the private key. If the private key is compromised, the entire system will lose its effectiveness. This is illustrated in Figure 12-1.
Figure 12-1. Illustration of Public Key Cryptography
![]()
Public key cryptography can become more intense. In some schemes, the private key is used to sign a message, and anyone can check the signature with the public key. This signing is done with a digital signature. A digital signature authenticates a document through math, letting the recipient know that the document was created and sent by the actual sender, and not someone else. It protects against forgery and tampering. The basic order of functions for the usage of asymmetric keys in this case would be encrypt, sign, decrypt, and verify. In the Diffie-Hellman scheme, each user generates a public/private key pair and distributes their public key to everyone else. After two or more users obtain a copy of the others’ public keys, they can be used to create a shared secret used as the key for a symmetric cipher. Due to the varying methods of public key cryptography, the whole subject can become somewhat confusing. Remember that there will always be a private and public key involved, and that public key cryptography can use asymmetric keys alone, or in addition to symmetric keys.
Internet standards, such as SSL/TLS and PGP, use public-key cryptography. Don’t confuse the term public key cryptography with Public Key Infrastructure (PKI). Although they are related, they are not the same. PKI is an entire system of hardware, software, policies, and so on, that binds public keys with user identities by way of certificates and a certificate authority (server or other such device). A certificate is an electronic document that uses a digital signature to bind the key with the identity. We cover PKI more in Chapter 13, “PKI and Encryption Protocols.”
Key Management
Key management deals with the relationship between users and keys; it’s important to manage the generation, exchange, storage, and usage of those keys. It is crucial technically, and organizationally, because issues can present themselves due to poorly designed key systems and poor management. Keys must be chosen and stored securely. The generation of strong keys is probably the most important concept. Some algorithms have weak keys that make cryptanalysis easy. For example, DES uses a considerably weaker key than AES; the stronger the key, the stronger the key management. We detail several methods for the exchange of keys later in this chapter including encapsulating one key within another, using key indicators, and exchanging symmetric session keys with an asymmetric key algorithm—in effect, ciphering our cipher. Secure storage of keys often depends on users and passwords, or other authentication schemes. Proper storage of keys allows for availability, part of the CIA triad. Finally, keys should be replaced frequently. If a particular user uses a key for too long, it will increase the chances of the key being cracked. Keys, like passwords, should be changed and/or recycled often.
Steganography
Although I have placed steganography within the cryptography section, it actually isn’t cryptography, although it might be used with cryptography. Steganography is the science (and art) of writing hidden messages; it is a form of security through obscurity. The goal is that no one aside from the sender and receiver should even suspect that the hidden message exists. The advantage of steganography is that the clearly visible messages look to be just that, regular old messages, that wouldn’t usually attract attention to themselves. Most people know when they come into contact with an encrypted message, but far fewer people identify when a steganographic message has crossed their path.
Steganography can hide messages within encrypted documents by inserting extra encrypted information. The hidden messages can also be found in sound files, image files, slowed down video files, and in regular Word documents or Excel spreadsheets. Messages can also be concealed within VOIP conversations (known as Lost Audio Packets Steganography, or LACK), and within any streaming service as well. They can also be obscured on a compromised wireless network with the HICCUPS system (Hidden Communication System for Corrupted Networks).
A common example of steganography is when using graphic files to send hidden messages. In this scenario, the least significant bit of each byte is replaced. For example, we could shade the color of a pixel (or triad) just slightly. This slight change would change the binary number associated with the color, enabling us to insert information. The color blue is represented as three bytes of data numbered 0, 0, and 255. We could change the color blue slightly to 1, 0, 255. This would not make the graphic look any different to the naked eye, but the change would be there nonetheless. This would be done in several or more pixels of the graphic to form the message. For this to work, the recipient would first need to have possession of the original file. Then the sender would transmit the modified steganographic file to be compared with the original by the recipient.
Encryption Algorithms
We mentioned previously that ciphers (or algorithms) can encrypt or decrypt data with the help of a key. We also pointed out that algorithms are well-defined instructions that describe computations from their initial state to their final state. In addition, we mentioned that there are symmetric and asymmetric algorithms. Now, let’s talk about some of the actual algorithmic standards within both of those classifications. We’ll start with symmetric types including DES, 3DES, AES, and RC and afterward move on to asymmetric types including RSA, Diffie-Hellman, and the elliptic curve.
DES and 3DES
The Data Encryption Standard (DES) is an older type of block cipher selected by the U. S. federal government back in the 1970s as its encryption standard. But due to its weak key, it is now considered deprecated and has been replaced by other standards. Being a block cipher, it groups 64 bits together into encryption units. Today, a 64-bit cipher is not considered powerful enough; also, and more important, the key size is 56-bit, which can be cracked fairly easily with a brute force or linear cryptanalysis attack. In addition to this, there are some theoretical weaknesses to the cipher itself. DES was replaced by triple DES (3DES) in 1999. The actual algorithm is sometimes referred to as the Data Encryption Algorithm (DEA). The algorithm is based on the Feistel cipher (or Feistel network) that has very similar, if not identical, encryption and decryption processes, reducing the amount of code required.
Triple DES, also known as 3DES or the Triple Data Encryption Algorithm (TDEA), is similar to DES but applies the cipher algorithm three times to each cipher block. The cipher block size is still 64-bit, but the key size can now be as much as 168-bit (three times the size of DES). This was a smart approach to defeating brute force attacks without having to completely redesign the DES protocol. However, both DES and 3DES have been overshadowed by AES, which became the preferred standard in late 2001.
AES
In the late ’90s, the National Institute of Standards and Technology (NIST) started a competition to develop a more advanced type of encryption. There were 15 submissions including Serpent, Twofish, RC6, and others but the selected winner was Rijndael. This submission was then further developed into the Advanced Encryption Standard (AES) and became the U. S. federal government standard in 2002. AES is the successor to DES/3DES and is another symmetric key encryption standard composed of three different versions of block ciphers: AES-128, AES-192, and AES-256. Actually, each of these has the same 128-bit cipher block size, but the key sizes for each are 128-bit, 192-bit, and 256-bit, respectively.
AES is based on the substitution-permutation network, which takes plaintext and the key and applies X amount of rounds to create the ciphertext. These rounds consist of substitution boxes and permutation boxes (usually in groups of 4X4 bytes) that convert the plaintext input bits to ciphertext output bits. AES specifies 10, 12, or 14 rounds for each of the respective versions.
AES is fast, uses minimal resources, and can be used on a variety of platforms. For example, it is the encryption algorithm of choice if you have a wireless network running the WPA2 protocol; the IEEE 802.11i standard specifies the usage of AES with WPA2 and in the process deprecates WEP. In addition, AES is a good choice for transferring encrypted data quickly to a USB flash drive. It is also used in whole disk encryption techniques such as BitLocker. This software can encrypt the entire disk which, after complete, is transparent to the user. However, there are some requirements for this including the following:
• A Trusted Platform Module (TPM)—A chip residing on the motherboard that actually generates and stores the encrypted keys, and defines their use
or
• An external USB key to store the encrypted keys
and
• A hard drive with two volumes
AES is purportedly susceptible to the related-key attack, if the attacker has some information of the mathematical relationship between several different keys. But generally, AES is considered the strongest type of symmetric encryption for many scenarios. Possible future successors to AES include the currently named Anubis and Grand Cru. As of now, AES is used worldwide and has not been outright compromised, nor do some industry experts ever think it will be.
RC
RC stands for different things depending on who you talk to. Officially, it is known as Rivest Cipher but is playfully known as Ron’s Code as well. There are multiple RC versions, most of which are not related aside from the fact that they are all encryption algorithms.
RC4 is a somewhat widely used stream cipher in such protocols such as SSL and WEP. It is known for its speed and simplicity. However, it is avoided when designing newer applications and technologies due to several vulnerabilities; when used with WEP on wireless networks, it can be cracked in under 1 minute with the use of aircrack-ptw. One way to avoid this to a certain extent is to use the Temporal Key Integrity Protocol (TKIP) with WEP. However, it still is recommended that AES and WPA2 be used in wireless networks.
RC5 is a block cipher noted for its simplicity and for its variable size (32, 64, or 128-bit). It was the predecessor to today’s RC6, which is a block cipher entered into the AES competition and was one of the five finalists. Though it was not selected, it is a patented algorithm offered by RSA Security as an alternative to AES. It is similar to AES in block size and key size options but uses different mathematical methods than Rijndael.
Summary of Symmetric Algorithms
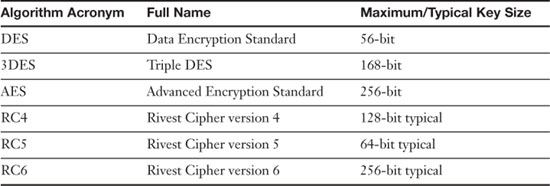
Table 12-3 gives some comparisons of the algorithms up to this point and their key strength.
Table 12-3. Summary of Symmetric Algorithms
![]()
RSA
Let’s talk about some asymmetric key algorithms. The original and very common RSA (which stands for Rivest, Shamir, and Adleman, the creators) is a public key cryptography algorithm. As long as the proper size keys are used, it is considered to be a secure protocol and is used in many e-commerce scenarios. It is slower than symmetric key algorithms but has advantages being suitable for signing and for encryption. It works well with credit card security and SSL. Key lengths for RSA are much longer than in symmetric cryptosystems. For example, 512-bit RSA keys have proven to be breakable over a decade ago; however, 1,024-bit keys are currently considered unbreakable by most known technologies, but RSA still recommends using the longer 2,048-bit key, which should deter even the most powerful super hackers. It is important to note that asymmetric algorithm keys need to be much larger than their symmetric key counterparts to be as effective. For example, a 128-bit symmetric key is equal to a 2,304-bit asymmetric key in strength. The RSA algorithm uses what is known as integer factorization cryptography. It works by first multiplying two distinct prime numbers that cannot be factored, then moving on to some more advanced math, and finally it creates a private and public key pair.
RSA key distribution is vulnerable to man-in-the-middle attacks. However, these attacks are defensible through the usage of digital certificates and other parts of a PKI system that we detail in the next chapter. It is also susceptible to timing attacks that can be defended against through the use of cryptographic blinding: This blind computation provides encryption without knowing actual input or output information. Due to other types of attacks, it is recommended that a secure padding scheme is used. Padding schemes work differently depending on the type of cryptography. In public key cryptography, padding is the adding of random material to a message to be sufficient, and incorporating a proof, making it more difficult to crack. A padding scheme is always involved, and algorithm makers such as RSA are always releasing improved versions.
In 2000, RSA Security released the RSA algorithm to the public. Therefore, no licensing fees are required if an organization decided to use or modify the algorithm.
Diffie-Hellman
The Diffie-Hellman key exchange, invented in the 1970s, was the first practical method for establishing a shared secret key over an unprotected communications channel. This asymmetric algorithm was developed shortly before the original RSA algorithm. It is also known as the Diffie-Hellman-Merkle key exchange due to Merkle’s conceptual involvement.
Diffie-Hellman relies on secure key exchange before data can be transferred. This key exchange establishes a shared secret key that can be used for secret communications, but over a public network. Originally, names were chosen for the “users”: Alice and Bob. Basically, Alice and Bob agree to initial prime and base numbers. Then, each of them selects secret integers and sends an equation based off of those to each other. Each of them computes the other’s equation to complete the shared secret, which then allows for encrypted data to be transmitted. The secret integers are discarded at the end of the session, achieving perfect forward secrecy.
It is considered secure against eavesdroppers due to the difficulty of mathematically solving the Diffie-Hellman problem. However, it is vulnerable to man-in-the-middle attacks. To prevent this, some method of authentication is used such as password authentication. This algorithm is used by the Transport Layer Security (TLS) protocol during encrypted web sessions. This algorithm can also be used within a public key infrastructure, though the RSA algorithm is far more common.
Elliptic Curve
Elliptic curve cryptography (ECC) is a type of public key cryptography based on the structure of an elliptic curve. It is also based on the difficulty of certain mathematical problems. Keys are created by graphing specific points on the curve, which were generated mathematically. All parties involved must agree on the elements that define the curve. This asymmetric algorithm has a compact design and creates keys that are difficult to crack. Other algorithms have been adapted to work with elliptic curves including Diffie-Hellman and the Digital Signature Algorithm (DSA). DSA is a Federal standard public key encryption algorithm used in digital signatures. ECC cryptography is used with smart cards, wireless security, and other communications such as VOIP and IPSec (with DSA).
ECC is susceptible to side channel attacks (SCA), which are attacks based on leaked information gained from the physical implementation (amount and type of curves) of the cryptosystem, and fault attacks (a type of side channel attack). These can be defeated by using an Elliptic Curve scalar multiplication algorithm or fixed pattern windows.
More Encryption Types
We have a couple more encryption types to speak of. They don’t quite fit into the other sections, so I figured I would place them here. The first is the one-time pad and the second is the Pretty Good Privacy (PGP) application and encryption method.
One-Time Pad
A one-time pad is a cipher that encrypts plaintext with a secret random key that is the same length as the plaintext. Unlike other encryption types, it can be computed by hand with a pencil and paper (thus the word “pad” in the name), although today computers will be used to create a one-time pad algorithm for use with technology. It has been proven as impossible to crack if used correctly and is known as being “information-theoretically secure”; it is the only cryptosystem with theoretically perfect secrecy. This means that it provides no information about the original message to a person trying to decrypt it illegitimately. However, issues with this type of encryption have stopped it from being widely used.
One of the issues with a one-time pad is that it requires perfect randomness. The problem with computer numerical random generators is that they are usually not truly random, instead they are pseudorandom generators; high-quality random numbers are quite difficult to generate. Another issue is that the exchange of the one-time pad data must be equal to the length of the message. It also requires proper disposal, which is difficult due to data remanence.
Regardless of these issues, the one-time pad can be useful in scenarios in which two users in a secure environment are required to also communicate with each other from two other separate secure environments. The one-time pad is also used in superencryption (or multiple encryption), which is encrypting an already encrypted message. In addition it is commonly used in quantum cryptography, which uses quantum mechanics to guarantee secure communications. These last two concepts are far beyond the Security+ exam, but they show the actual purpose for this encryption type.
PGP
Pretty Good Privacy (PGP) is an encryption program used primarily for signing, encrypting and decrypting e-mails in an attempt to increase the security of e-mail communications. You might remember that we previously discussed weaknesses of e-mail client programs when sending via POP3 and SMTP servers. PGP uses (actually wrote) the encryption specifications as shown in the OpenPGP standard; other similar programs use this as well. Today, PGP has an entire suite of tools that can encrypt e-mail, accomplish whole disk encryption, and encrypt zip files and instant messages. PGP uses a symmetric session key (also referred to as a preshared key or PSK), and as such, you might hear PGP referred to as a program that uses symmetric encryption, but it also uses the asymmetric RSA for digital signatures and for sending the session key.
When encrypting data, PGP uses key sizes of at least 128-bits. Newer versions allow for RSA or DSA key sizes ranging from 512 bits to 2048 bits. The larger the key, the more secure the encryption is, but the longer it will take to generate the keys; although, this is done only once when establishing a connection with another user. The program uses a combination of hashing, data compression, symmetric key cryptography, and public key cryptography. New versions of the program are not fully compatible with older versions because the older versions cannot decrypt the data that was generated by a newer version. This is one of the issues when using PGP; users must be sure to work with the same version. Newer versions of PGP support OpenPGP and S/MIME, which allows for secure communications with just about everyone.
Because it works with RSA, the security of PGP is based on the key size. It is considered secure and uncrackable as long as a sufficient key size is used. As an example, it has been suggested that a 2,048-bit key should be safe against the strongest of well-funded adversaries with knowledgeable people and the latest in super computers until at least the year 2020; 1024-bit keys are considered strong enough for all but the most sensitive data environments.
Hashing Basics
A hash is a summary of a file or message. Hashes, are used in digital signatures and file and message authentication. A hash is generated through the use of a hash function to verify the integrity of the file or message, most commonly after transit over a network. A hash function is a mathematical procedure that converts a variable-sized amount of data into a smaller block of data. The hash function is designed to take an arbitrary data block from the file or message, use that as an input, and from that block, produce a fixed-length hash value. Basically, the hash is created at the source and is recalculated and compared with the original hash at the destination. Figure 12-2 illustrates this process. Note the hash that was created starting with ce114e and so on. This is the summary, or message digest of the file to be sent. It is an actual representation of an MD5 hash of a plaintext file with the words “This is a test,” as shown in the message portion of Figure 12-2.
Figure 12-2. Illustration of the Hashing Process
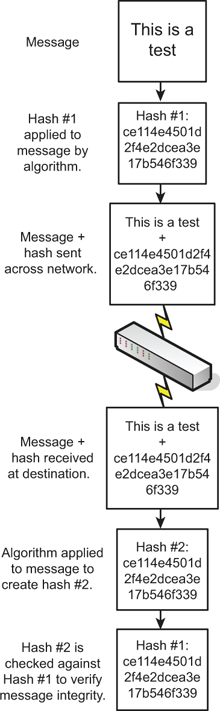
![]()
Because the hash is a condensed version of the file/message, or a portion of it, it is also known as a message digest. It provides integrity to data so that a user knows that the message is intact, hasn’t been modified during transit, and comes from the source the user expects. A hash can fall into the category of a one-way function. This means it is easy to compute when generated but difficult (or impossible) to compute in reverse. In the case of a hash, a condensed version of the message, initial computation is relatively easy (compared to other algorithms), but the original message should not be re-created from the hash. Contrast this concept to encryption methods that indeed can be reversed. A hash can be created without the use of an algorithm, but generally, the ones used in the field require some kind of cryptographic algorithm.
Cryptographic Hash Functions
Cryptographic hash functions are hash functions based on block ciphers. The methods used resemble that of cipher modes used in encryption. Examples of cryptographic hash functions include MD5 and SHA.
MD5
The Message-Digest algorithm 5 (MD5) is the latest in a series of algorithms designed by Ron Rivest. It uses a 128-bit key. This is a widely used hashing algorithm; at some point you have probably seen MD5 hashes when downloading files. This is an example of the attempt at providing integrity. By checking the hash produced by the downloaded file against the original hash, you can verify the file’s integrity with a certain level of certainty. However, MD5 hashes are susceptible to collisions. A collision occurs when two different files end up using the same hash. Due to this low collision resistance, MD5 is considered to be harmful today. MD5 is also vulnerable to threats such as rainbow tables and pre-image attacks. The best solution to protect against these attacks is to use a stronger type of hashing function such as SHA-2 or higher.
SHA
The Secure Hash Algorithm (SHA) is one of a number of hash functions designed by the NSA and published by the NIST. They are used widely in the United States government. SHA-1 is the most commonly used version, which employs a 160-bit hash, which is reasonably secure, but uses a lot of resources on the computer generating the hash. SHA-2 is more secure; it has 256-bit and 512-bit block sizes but uses even more resources and is less widely accepted. SHA-3 is under development but is slated to be the replacement for SHA-1. An NIST hash function competition for SHA-3 (similar to the AES competition) is scheduled for completion in 2012.
It is important that a hashing algorithm be collision-resistant. If it has the capability to avoid the same output from two guessed inputs (by a hacker attempting a collision attack), it is collision-resistant. When it comes to cryptography “perfect hashing” is not possible because usually unknowns are involved, such as the data to be used to create the hash, and what hash values have been created in the past. Though perfect is not possible, it is possible to increase collision resistance by using a more powerful hashing algorithm.
Because MD5 and SHA-1 have vulnerabilities, many government agencies will start using SHA-2 in 2011 (and most likely SHA-3 after 2012).
Happy Birthday!
Not when a birthday attack is involved. A birthday attack is an attack on a hashing system that attempts to send two different messages with the same hash function, causing a collision. It is based on the birthday problem in probability theory (also known as the birthday paradox). This can be summed up simply as the following: A randomly chosen group of people will have a pair of persons with the same calendar date birthday. The probability of this with 365 (or 366) people is 100%, which makes sense. The paradox (thoughtfully and mathematically) comes into play when less people are involved. With only 57 people, there is a 99% probability of a match (a much higher percentage than one would think), and with only 23 people, there is a 50% probability. Imagine that and blow out your candles! And by this, I mean use hashing functions with strong collision resistance. Because if attackers can find any two messages that digest the same way (use the same hash value), they can deceive a user into receiving the wrong message. To protect against a birthday attack, use a secure transmission medium, such as SSH, or encrypt the entire message that has been hashed.
LANMAN, NTLM, and NTLM2
Passwords can also be hashed using algorithms. Some password hashes are more secure than others, whereas older ones have been cracked and are therefore compromised. This section details the LANMAN, NTLM, and NTLM2 hashes starting from the oldest. These three types of authentication are what attempts to make your logon to the computer secure, unless you log in to a domain where Kerberos is used by default.
LANMAN
The LANMAN hash, also known as the LAN Manager hash or simply LM hash, was the original hash used to store Windows passwords. It was used in Windows operating systems before Windows NT but is supported by some versions of Windows as a legacy backward in the attempt to be backward compatible. This backward compatibility can be a security risk because the LM hash has several weaknesses and can be cracked easily.
Its function is based off of the deprecated DES algorithm. Weaknesses also include the fact that the ASCII password is converted to uppercase, essentially removing a large portion of the character set. Brute force attacks can crack alphanumeric LM hashes in a matter of hours.
Due to all these weaknesses, it is highly recommended that it be disabled on operating systems that run it by default. It should also be checked on OSs such as Windows Vista that are supposed to have it disabled by default.
The following step-by-step procedure shows how to disable the storage of LM hashes in Windows Server 2003. It works the same in Windows XP:
Step 1. Access the Local Group Policy.
Step 2. Navigate to Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options.
Step 3. In the right pane, double-click the policy named Network security: Do not store LAN Manager hash value on next password change.
Step 4. Click Enabled and click OK. An example of this is shown in Figure 12-3.
Figure 12-3. LM Hash in the Local Group Policy of a Windows Server 2003
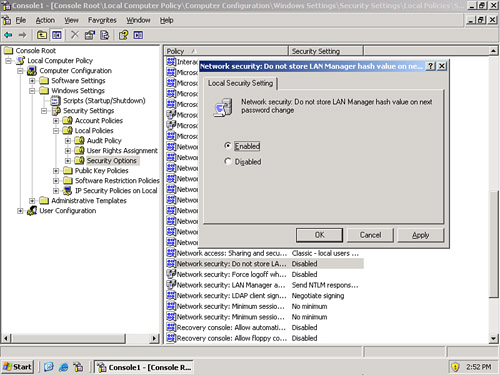
![]()
Note
For Windows Server 2003 domain controllers, you need to access the Group Policy Editor, not Local Group Policy. Generally, this would be done at the default domain policy, but it could also be accomplished at a single OU’s policy, if necessary.
You can also disable the storage of LM hash passwords by modifying the Registry. This process is necessary for Windows 2000 Server and Professional computers. For more information, see the link to Microsoft’s website at the end of this chapter. If, for whatever reason, the storing of LM hashes for passwords cannot be turned off, Microsoft recommends using a 15-character-minimum password. When this is done, an LM hash and a NTLM hash value are stored. In this situation, the LM hash cannot be used solely to authenticate the user; therefore, it cannot be solely cracked; the NTLM hash would have to be cracked as well. Because 15 characters might be beyond some organization’s policies, it is highly recommended that the LM hash policy be disabled.
NTLM and NTLM2
Well, we talked a lot about why the LM hash is insufficient. Let’s get into the replacements. The first is NTLM hash, also known as the NT LAN Manager hash. The NTLM algorithm was first supplied with Windows NT 3.1; it provides Unicode support, and more important to this conversation, the RC4 cipher. Although the RC4 cipher enables a more powerful hash known as NTLM for storing passwords, the systems it ran on were still configured to be backward compatible with the LM hash. So, as long as the LM hash was not disabled, those systems were still at the same risk as older systems that ran the LM hash only. Windows Vista and Windows 2008 operating systems (and higher) disable the older LM hash by default.
The issue with NTLM is that it is based off of the RC4 cipher, which has been compromised. Therefore, the NTLM hash is compromised. You probably remember the NTLM hash we cracked during the Chapter 10 labs. (It was a basic password, but it got the point across.) This was done using Cain & Abel on a Windows Vista computer with SP2, which has the LM hash disabled by default. Due to the weakness of NTLM, we need a stronger hashing algorithm: NTLM 2.
NTLM 2 uses the MD5 hash, making it difficult to crack; it is a 128-bit system. NTLM 2 (also known as NTLMv2) has been available since Windows NT 4.0 SP4 and is used by default on newer Windows operating systems. Older versions of Windows, such as Windows 98, can be upgraded to allow NTLM 2 compatibility by installing Active Directory Client Extensions. Even though NTLM 2 responds to the security issues of the LM hash and NTLM, most Microsoft domains will use Kerberos as the logon authentication scheme because of its level of security when dealing with one computer logging into another, or into an entire network.
Exam Preparation Tasks: Review Key Topics
Review the most important topics in the chapter, noted with the Key Topics icon in the outer margin of the page. Table 12-4 lists a reference of these key topics and the page numbers on which each is found.
![]()
Table 12-4. Key Topics for Chapter 12
Complete Tables and Lists from Memory
Print a copy of Appendix A, “Memory Tables,” (found on the DVD), or at least the section for this chapter, and complete the tables and lists from memory. Appendix B, “Memory Tables Answer Key,” also on the DVD, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
key,
Data Encryption Standard (DES),
Advanced Encryption Standard (AES),
RSA,
elliptic curve cryptography (ECC),
hash,
Message-Digest Algorithm 5 (MD5),
Hands-On Lab
Complete the following written step-by-step scenario. After you finish (or if you do not have adequate equipment to complete the scenario), watch the corresponding video solution on the DVD.
If you have additional questions, feel free to post them at my website: www.davidlprowse.com in the Ask Dave forum. (Free registration is required to post on the website.)
Equipment Needed
• Windows Server 2003
Lab 12-1: Disabling the LM Hash in Windows Server 2003
In this lab, you disable the LANMAN hashing algorithm within the Local Security Policy and within the Registry. The steps are as follows:
Disable the LM hash from a group policy:
Step 1. Access the Windows Server 2003.
Step 2. Access the Local Group Policy.
Step 3. Navigate to Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options.
Step 4. In the right pane, double-click the policy named Network security: Do Not Store LAN Manager Hash Value on Next Password Change.
Step 5. Click Enabled and click OK.
Disable the LM hash from the Registry:
Step 6. Start the Registry Editor by clicking Start > Run and typing regedit.exe.
Step 7. Navigate to the following key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsa
Step 8. Locate the entry named noLMHash. Double-click it and set it to 1 to enable that entry.
If the entry does not exist, create it by right-clicking the white work area in the right window pane, selecting New > Dword. Name the Dword noLMHash, and then set it to 1.
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
View Recommended Resources
Recommended reading:
• Introduction to Modern Cryptography: Principles and Protocols. Katz, Lindell. Chapman and Hall, 2007.
• Cryptography Demystified. Hershey. McGraw-Hill Professional, 2002.
• Practical Cryptography. Ferguson. Wiley, 2003.
• Hiding in Plain Sight: Cole. Wiley, 2003.
• Malicious Cryptography: Exposing Cryptovirology. Young, Yung. Wiley, 2004.
• Privacy on the Line: The Politics of Wiretapping and Encryption. Diffie, Landau. The MIT Press, 2010.
• Schneier on Security. Schneier. 2008 Wiley.
Recommended Internet resources:
• NIST: Data Encryption Standard (DES): http://csrc.nist.gov/publications/fips/fips46-3/fips46-3.pdf
• NIST: Recommendation for the Triple Data Encryption Algorithm (TDEA) Block Cipher: http://csrc.nist.gov/publications/nistpubs/800-67/SP800-67.pdf
• NIST: Advanced Encryption Standard (AES): http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf
• RSA Laboratories: RC6 Block Cipher: www.rsa.com/rsalabs/node.asp?id=2512
• Disabling the storage of LM hashes in Windows: http://support.microsoft.com/kb/299656
• Bruce Schneier Blog: www.schneier.com/
Answer Review Questions
Answer the following review questions. You can find the answers at the end of this chapter.
1. Which of the following is the proper order of functions for asymmetric keys?
A. Decrypt, validate, and code and verify
B. Sign, encrypt, decrypt, and verify
C. Encrypt, sign, decrypt, and verify
D. Decrypt, decipher, and code and encrypt
2. Which type of encryption technology is used with the BitLocker application?
A. Symmetric
B. Asymmetric
C. Hashing
D. WPA2
3. Which of the following will provide an integrity check?
A. Public key
B. Private key
C. WEP
D. Hash
4. Why would a hacker use steganography?
A. To hide information
B. For data integrity
C. To encrypt information
D. For wireless access
5. You need to encrypt and send a large amount of data, which of the following would be the best option?
A. Symmetric encryption
B. Hashing algorithm
C. Asymmetric encryption
D. PKI
6. Imagine that you are a hacker. Which would be most desirable when attempting to compromise encrypted data?
A. A weak key
B. The algorithm used by the encryption protocol
C. Captured traffic
D. A block cipher
7. An SHA algorithm will have how many bits?
A. 64
B. 128
C. 512
D. 1,024
8. What is another term for secret key encryption?
A. PKI
B. Asymmetrical
C. Symmetrical
D. Public key
9. Your boss wants you to set up an authentication scheme in which employees will use smart cards to log into the company network. What kind of key should be used to accomplish this?
A. Private key
B. Public key
C. Cipher key
D. Shared key
10. The IT director wants you to use a cryptographic algorithm that cannot be decoded by being reversed. Which of the following would be the best option?
A. Asymmetric
B. Symmetric
C. PKI
D. One way function
11. Which of the following concepts does that Diffie-Hellman algorithm rely on?
A. Usernames and passwords
B. VPN tunneling
C. Biometrics
D. Key exchange
12. What does steganography replace in graphic files?
A. The least significant bit of each byte
B. The most significant bit of each byte
C. The least significant byte of each bit
D. The most significant byte of each bit
13. What does it mean if a hashing algorithm creates the same hash for two different downloads?
A. A hash is not encrypted.
B. A hashing chain has occurred.
C. A one-way hash has occurred.
D. A collision has occurred.
14. Which of the following methods will best verify that a download from the Internet has not been modified since the manufacturer released it?
A. Compare the final LANMAN hash with the original.
B. Download the patch file over an AES encrypted VPN connection.
C. Download the patch file through a SSL connection.
D. Compare the final MD5 hash with the original.
15. Which of the following encryption methods deals with two distinct, large prime numbers and the inability to factor those prime numbers?
A. SHA-1
B. RSA
C. WPA
D. Symmetric
16. Which of the following is not a symmetric key algorithm?
A. RC4
B. ECC
C. 3DES
D. Rijndael
17. You are attempting to move data to a USB flash drive. Which of the following enables a rapid and secure connection?
A. SHA-1
B. 3DES
C. AES256
D. MD5
18. Which of the following is used by PGP to encrypt data.
A. Asymmetric key distribution system
B. Asymmetric scheme
C. Symmetric key distribution system
D. Symmetric scheme
19. Which of the following encryption algorithms is used to encrypt and decrypt data?
A. SHA-1
B. RC5
C. MD5
D. NTLM
20. Of the following, which statement correctly describes the difference between a secure cipher and a secure hash?
A. A hash produces a variable output for any input size; a cipher does not.
B. A cipher produces the same size output for any input size; a hash does not.
C. A hash can be reversed; a cipher cannot.
D. A cipher can be reversed; a hash cannot.
21. When encrypting credit card data, which would be the most secure algorithm with the least CPU utilization?
A. AES
B. 3DES
C. SHA-1
D. MD5
22. A hash algorithm has the capability to avoid the same output from two guessed inputs. What is this known as?
A. Collision resistance
B. Collision strength
C. Collision cipher
D. Collision metric
23. Which of the following is the weakest encryption type?
A. DES
B. RSA
C. AES
D. SHA
24. Give two examples of hardware devices that can store keys. (Select the two best answers.)
A. Smartcard
B. Network adapter
D. PCMCIA card
25. What type of attack sends two different messages using the same hash function, which end up causing a collision?
A. Birthday attack
B. Blue snarfing
C. Man-in-the-middle attack
D. Logic bomb
26. Why would a hacker use steganography?
A. To hide information
B. For data integrity
C. To encrypt information
D. For wireless access
Answers and Explanations
1. C. The proper order of functions for asymmetric keys is as follows: encrypt, sign, decrypt, and verify. This is the case when a digital signature is used to authenticate an asymmetrically encrypted document.
2. A. BitLocker uses symmetric encryption technology based off of AES. Hashing is the process of summarizing a file for integrity purposes. WPA2 is a wireless encryption protocol.
3. D. A hash provides integrity checks, for example, MD5 hash algorithms. Public and private keys are the element of a cipher that allows for output of encrypted information. WEP (Wired Equivalent Privacy) is a deprecated wireless encryption protocol.
4. A. Steganography is the act of writing hidden messages so that only the intended recipients will know of the existence of the message. This is a form of security through obscurity. Steganographers are not as concerned with data integrity or encryption because the average person shouldn’t even know that a message exists. Although steganography can be accomplished by using compromised wireless networks, it is not used to gain wireless access.
5. A. Symmetric encryption is the best option for sending large amounts of data. It is superior to asymmetric encryption. PKI is considered an asymmetric encryption type, and hashing algorithms don’t play into sending large amounts of data.
6. A. The easiest way for a hacker to get at encrypted data is if that encrypted data has a weak encryption key. The algorithm isn’t of much use to a hacker unless it has been broken, which is a far more difficult process than trying to crack an individual key. Captured traffic, if encrypted, still needs to be decrypted, and a weak key will aid in this process. The block cipher is a type of algorithm.
7. C. SHA-2 algorithm blocks will have 512 bits. SHA-1 is 160-bit. MD5 is 128-bit; 1,024-bit keys are common in asymmetric encryption.
8. C. Symmetric key encryption uses a secret key. The term symmetric key is also referred to as the following: private key, single key, and shared key (and sometimes as session key). PKI and public keys at their core are asymmetrical.
9. A. A private key should be used by users when logging in to the network with their smart card. The key should certainly not be public. A key actually determines the function of a cipher. Shared key is another term for symmetric-key encryption but does not imply privacy.
10. D. In cryptography, the one-way function is one option of an algorithm that cannot be reversed, or is difficult to reverse, in an attempt to decode data. An example of this would be a hash such as SHA-2, which creates only a small hashing number from a portion of the file or message. There are ways to crack asymmetric and symmetric encryptions, which enable complete decryption (decoding) of the file.
11. D. The Diffie-Hellman algorithm relies on key exchange before data can be sent. Usernames and passwords are considered a type of authentication. VPN tunneling is done to connect a remote client to a network. Biometrics is the science of identifying people by one of their physical attributes.
12. A. Steganography replaces the least significant bit of each byte. It would be impossible to replace a byte of each bit, because a byte is larger than a bit; a byte is eight bits.
13. D. If a hashing algorithm generates the same hash for two different messages within two different downloads, a collision has occurred and the implementation of the hashing algorithm should be investigated.
14. D. The purpose of the MD5 hash is to verify the integrity of a download. SHA is another example of a hash that will verify the integrity of downloads. LANMAN hashes are older deprecated hashes used by Microsoft LAN Manager for passwords. Encrypted AES and SSL connections are great for encrypting the data transfer but do not verify integrity.
15. B. The RSA encryption algorithm uses two prime numbers. If used properly they will be large prime numbers that will be difficult or impossible to factor. SHA-1 is an example of a Secure Hash Algorithm. WPA is the Wi-Fi Protected Access protocol, and RSA is an example of an asymmetric method of encryption.
16. B. ECC or elliptic curve cryptography is an example of public key cryptography that uses an asymmetric key algorithm. All the other answers are symmetric key algorithms.
17. C. AES256 enables a quick and secure encrypted connection for use with a USB flash drive. It might even be used with a whole disk encryption technology, such as BitLocker. SHA-1 and MD5 are examples of hashes. 3DES is an example of an encryption algorithm but would not be effective for sending encrypted information in a highly secure manner and quickly to USB flash drive.
18. D. Pretty Good Privacy (PGP) encryption uses a symmetric-key cryptography scheme and a combination of hashing and data compression. Key distribution systems are part of an entire encryption scheme, such as technologies such as Kerberos (key distribution center) or quantum cryptography.
19. B. RC5 (Rivest Cipher version 5) can encrypt and decrypt data. SHA-1 and MD5 are used as hashing algorithms, and NTLM (NT LAN Manager) is used by Microsoft as an authentication protocol and a password hash.
20. D. Ciphers can be reverse engineered but hashes cannot when attempting to re-create a data file. Hashing is not the same as encryption; hashing is the digital fingerprint, so to speak, of a group of data. Hashes are not reversible.
21. A. AES (the Advanced Encryption Standard) is fast and secure; more so than 3DES. SHA-1 and MD5 are hashing algorithms. Not listed is RSA, which is commonly implemented to secure credit card transactions.
22. A. A hash is collision-resistant if it is difficult to guess two inputs that hash to the same output.
23. A. DES or the Data Encryption Standard was developed in the 1970s; its 56-bit key has been superseded by 3DES (max 168-bit key) and AES (max 256-bit key). DES is now considered to be insecure for many applications. RSA is definitely stronger than DES even when you compare its asymmetric strength to a relative symmetric strength. SHA is a hashing algorithm.
24. A and D. Smart cards and PCMCIA cards can be used as devices that carry a token and store keys; this means that they can be used for authentication to systems, quite often in a multifactor authentication scenario. Network adapters and PCI Express cards are internal to a PC and would not make for good key storage devices.
25. A. A birthday attack exploits the mathematics behind the birthday problem in probability theory. It deals with two different messages using the same hash function, generating the same message digest. Blue snarfing deals with Bluetooth devices. The man-in-the-middle attack is when a person or computer intercepts information between a sender and the receiver. A logic bomb is a malicious attack set to go off at a particular time; quite often it is stored on a zombie computer.
26. A. Steganography is the act of writing hidden messages so that only the intended recipients will know of the existence of the message. This is a form of security through obscurity. Data integrity is accomplished through the use of hashing. Steganography is not the same as cryptography in that it doesn’t care if a person sees the original message.
