CHAPTER 9
Preparing the Incident Response Toolkit
In this chapter you will learn:
• How digital forensics is related to incident response
• Basic techniques for conducting forensic analyses
• Familiarity with a variety of forensic utilities
• How to assemble a forensics toolkit
Condemnation without investigation is the height of ignorance.
—Albert Einstein
Digital Forensics
Digital forensics is the process of collecting and analyzing data in order to determine whether and how an incident occurred. The word forensics can be defined as an argumentative exercise, so it makes sense that a digital forensic analyst’s job is to build compelling, facts-based arguments that explain an incident. The digital forensic analyst answers the questions what, where, when, and how, but not who or why. These last two questions are answered by the rest of the investigative process of which digital forensics is only a part.
The investigation of a security incident need not end up in a courtroom, but it is almost impossible to predict whether it will. This means that we should treat every digital forensic investigation as if it will ultimately be held to the level of scrutiny of a criminal case. We all know that this is not always possible when trying to bring critical business processes back online or simply based on the required workload. Still, the closer we stay to the principles of legal admissibility in court, the better off we’ll be in the end. The National Institute of Justice identifies the following three principles that should guide every investigation:
• Actions taken to secure and collect digital evidence should not affect the integrity of that evidence.
• Persons conducting an examination of digital evidence should be trained for that purpose.
• Activity relating to the seizure, examination, storage, or transfer of digital evidence should be documented, preserved, and available for review.
Phases of an Investigation
Forensic investigations, like many other standardized processes, can be broken down into phases. In this case, we normally recognize four: seizure, acquisition, analysis, and reporting. Seizure is the process of controlling the crime scene and the state of potential evidentiary items. Acquisition is the preservation of evidence in a legally admissible manner. The analysis takes place in a controlled environment and without unduly tainting the evidence. Finally, the goal is to produce a report that is complete, accurate, and unbiased.
Seizure
The goal of seizure is to ensure that neither the perpetrators nor the investigators make any changes to the evidence. An overly simplistic, but illustrative, example is to put yellow “Crime Scene” tape and guards around the area wherein a murder took place so murderers can’t come back and pick up shell casings with their fingerprints on them. Obviously, the digital crime scene is different in that the perpetrator may continue to invisibly be in the scene making changes even as the investigators are trying to gather evidence.
One of the most important steps you can take is to not power off anything you don’t have to. The one universal exception to this rule is if you are pretty sure that there is a running process that is deliberately destroying evidence. There are many reasons for keeping the devices running, but a key one is that memory forensics (that is, digital forensics on the primary storage units of computing devices) has dramatically evolved over the past few years. Although it is possible for a threat actor to install rootkits that hide processes, connections, or files, it is almost impossible to hide tracks in running memory. Furthermore, an increasing number of malware never touches the file system directly and lives entirely in memory. Shutting down a device without first acquiring the contents of memory could make it impossible to piece together the incident accurately.
Another important, if seemingly mundane, step is to document the entire physical environment around a device. An easy way to do this is to take lots of photos of the scene. Specific shots you typically want to take are listed here. Regardless of whether you take pictures, you should certainly take notes describing not only the environment but also each action your team takes to seize the evidence.
• Computer desktop showing running programs (if the device is unlocked)
• Peripherals connected to the device (for example, thumb drives and external drives)
• Immediate surroundings of the device (for example, physical desktop)
• Proximate surroundings of the device (for example, the room or cubicle)
After you have documented the environment, it is time to start unplugging things and taking them away. It is important to properly tag, label, and inventory everything you seize so there are no questions about what was where later. You also need disassembly and removal tools such as antistatic bands, pliers, and screwdrivers. Finally, you need appropriate packaging such as antistatic bags and evidence bags. You should keep in mind that weather conditions (for example, extreme temperatures, snow, or rain) may also impose additional requirements on your packaging and transportation arrangements.
Chain of Custody A chain of custody is a history that shows how evidence was collected, transported, and preserved at every stage of the process. Because digital evidence can be easily modified, a clearly defined chain of custody demonstrates that the evidence is trustworthy. It is important to follow very strict and organized procedures when collecting and tagging evidence in every single case. Furthermore, the chain of custody should follow evidence through its entire life cycle, beginning with identification and ending with its destruction, permanent archiving, or return to the owner. Figure 9-1 shows a sample form that could be used for this purpose.

Figure 9-1 Evidence container data
Servers Conducting a forensic analysis of a server requires addressing additional issues compared to workstations. For starters, it may not be possible to take the server offline and remove it to a safe analysis room. Instead, you may have no choice but to conduct an abbreviated analysis onsite. Live forensics (or live response) is the conduct of digital forensics on a device that remains operational throughout the investigation. We already touched on a related issue earlier when we described the importance of capturing the contents of volatile memory before shutting off a device. If you cannot remove the server from a production environment, then the next-best thing is to capture its memory contents and files of interest (for example, log files).
Another consideration when dealing with servers is that they typically have significantly more storage (both primary and secondary) than workstations. This is guaranteed to make the process longer, but may also require special tools. For example, if your server uses a redundant array of inexpensive disks (RAID), you will likely need specialized tools to deal with those disks. Apart from the hardware differences, you will also have to consider the particular architectures of the software running on servers. Microsoft Exchange Server has a large number of features that help a forensic investigator, but that person will have to know his or her way around Exchange’s complex architecture. This point also holds for database management systems (DBMS) and in-house web applications.
Mobile Devices It is uncommon for criminal investigations these days not to include mobile device forensics. Though this is somewhat lesser of a case in the corporate world, you should be aware of the unique challenges that mobile devices present. Chief among these is that the device will continue to communicate with the network unless you power it off (which we already said might not be a good idea). This means that a perpetrator can remotely wipe the device or otherwise tamper with it. A solution to this problem is to place the device into a Faraday container that prevents it from communicating over radio waves. Faraday bags have special properties that absorb radio frequency (RF) energy and redistribute it, preventing communication between devices in the container and those outside. Obviously, you will also need a larger Faraday facility in which to analyze the device after you seize it.
Acquisition
Forensic acquisition is the process of extracting the digital contents from seized evidence so that they may be analyzed. This is commonly known as taking a forensic image of a hard drive, but it actually involves more than just that. The main reason you want to extract the contents is that you want to conduct your analysis on a copy of the evidence and not on the original. Throughout the process, preserving the integrity of the original evidence is paramount. To acquire the original digital evidence in a manner that protects and preserves the evidence, the following steps are generally considered best practices:
1. Prepare the destination media. You will need a place to store the digital contents of your seized evidence. This destination may be a removable hard drive or a storage area network (SAN). You must ensure that the destination is free of any content that may taint the evidence. The best way to do this is to securely wipe the media by overwriting it with a fixed pattern of ones and/or zeroes.
2. Prevent changes to the original. The simple act of attaching a device to a computer or duplicator will normally cause its contents to change in small but potentially significant ways. To prevent any changes at all, you must use write-protection mechanisms such as hardware write blockers (described later in this chapter). There are also forensic acquisition software products that enable software-based write protection, but it is almost always better to use physical ones.
3. Hash the original evidence. Before you copy anything, you should take a cryptographic hash of the original evidence. Most products support MD5 and SHA-1 hashes. Though these protocols have been shown to be susceptible to collisions and are no longer recommended for general use, we have seen no pushback from the courts on their admissibility in criminal trials.
4. Copy the evidence. A variety of applications will let you do a forensic copy of digital media, including the venerable dd utility in Linux systems. What these applications all have in common is that they perform complete binary copies of the entire source medium. Copying the files is not enough because you might not acquire relevant data in deleted or unallocated spaces.
5. Verify the acquisition. After the copy is complete, you take a cryptographic hash of the copy and compare it to the original. As long as they match, you will be able to perform analyses of the copy and be assured that it is perfectly identical to the original.
6. Safeguard the original evidence. Because you now have a perfect copy of the evidence, you store the original in a safe place and ensure nobody gains access to it.
Analysis
Analysis is the process of interpreting the extracted data to determine its significance to the case. Some examples of the types of analysis that may be performed include timeframe (that is, what happened when), data hiding (that is, things that have been intentionally concealed), application and file (that is, which applications accessed which files), and ownership and possession (that is, which user accounts accessed which applications and files). Though the specific applications and commands you would use may vary depending on the operating or file systems involved, the key issues are the same.
One of the most important tools to a forensic analyst is the timeline. It establishes a framework for comparing the state of the system at different points in time. For example, you may suspect that a user might have stolen files by copying them to a thumb drive last Friday, but you don’t see that drive registered on the system until Monday. Absent evidence of tampering with the data and time on the system, you can conclude that the exfiltration mechanism was not that particular thumb drive. The timeline is simply an ordered list of actions taken on the system. These actions can be categorized as read, write, modify, and delete operations on an item of interest. Many investigators we know simply keep track of their timelines in a spreadsheet with columns like the ones listed here:
• Data and time
• Time zone
• Source (for example, Windows Registry or syslog)
• Item name (for example, Registry key name or filename)
• Item location (full path)
• Description
At every step of the process, you should be keeping copious notes on each specific action you take, down to the command and parameters you use. If you use a forensic analysis suite such as EnCase or FTK (the Forensic Toolkit), the tool will record your actions for you. Even so, it is a best practice to keep notes on your own throughout the investigation.
Reporting
If you have been taking notes, you have been writing parts of the report as you conducted the investigation. Once you arrive at sound conclusions based on the evidence available, you simply have to put together narrative statements that present your arguments and conclusions in a readable fashion. Like any form of communication, knowing your audience is crucial. If the report is geared toward executive leaders, the document would be different than if you were presenting it in a court of law. All major commercial suites also have a feature that will generate a draft report you can then customize for your own purposes.
Forensic Investigation Suite
Forensic investigations are extremely time-consuming by their very nature. Fortunately, a number of software developers have created suites of tools to facilitate many aspects of the process.
Acquisition Utilities
The acquisition phase of a forensic investigation is perhaps the most critical point in terms of ensuring the admissibility of evidence, analysis, and conclusions. This is where you want to slow down, use a checklist, and ensure you make no mistakes at all because doing so would possibly invalidate all the work that follows.
Forensic Duplicators
Forensic duplicators are systems that copy data from a source to a destination while ensuring that not even a single bit gets altered in the process. What sets them apart from any copying utility is that they do not rely on file system operations, which means they can recover file system artifacts such as the Master File Table (MFT) in Windows systems and the inode table in Linux ones.
dd The venerable workhorse in Linux is the dd utility that comes by default with most systems. Because almost everything in the extended file system (ext) used in Linux is a “file” (even network connections and peripheral devices), dd can duplicate data across files, devices, partitions, and volumes. The following command will do a bit-for-bit copy of hard drive “hda” to a file called case123.img using a block size of 4096 bytes, and it will fill the rest of a block with null symbols if it encounters an error:
dd if=/dev/hda of=case123.img bs=4k conv=noerror,sync
Note that this command does not generate a hash of the output file, which we need for verification. The solution is to simply use the sha1sum command separately.
FTK Imager FTK Imager is a free data preview and imaging tool developed by Access Data. Unlike the dd utility, this imager is a full-featured product that allows you to perform a forensically sound acquisition, verify it by generating MD5 and/or SHA-1 hashes, and even preview the files and folders in a read-only fashion. FTK Imager will also read registry keys from Windows and let you preview them and their values. It also supports compression, encryption, and multiple output formats, including EnCase Evidence File format (E01) and the raw format generated by dd (001).
Password Crackers
It is increasingly common to find encrypted files or drives in everything from mobile devices to back-end servers. If the suspect is unable or unwilling to provide the password, or if there is no suspect to interrogate in the first place, you may have to resort to specialized software that is designed to guess passwords and decrypt the protected resources. A popular commercial solution in this space is called Passware Kit Forensic. It can operate on its own or be integrated with EnCase. Passware Kit Forensic can decrypt over 280 different types of protected files, including BitLocker, FileVault, iCloud, and Dropbox. Additionally, because password cracking can take a very long time, this tool can take advantage of graphics processing units (GPUs) and multiple networked computers to accelerate the process.
Cryptography Tools
It is often the case that we must ensure the confidentiality of an investigation and its evidence. To accomplish this, we can turn to a variety of cryptography tools that are available for multiple platforms. Perhaps the simplest approach to encrypting files is to use the compression utilities found in most operating systems, but you must ensure you provide a password. The advantage is that these applications are ubiquitous and the files are mostly usable across platforms.
If you need something a little more robust, you can try any number of available encryption tools. One of the most popular and recommended open source solutions is VeraCrypt, which is based on the now defunct TrueCrypt. This tool is free and available for Windows, OS X, and Linux systems. VeraCrypt supports multiple cryptosystems, including AES, TwoFish, and Serpent. It also supports the creation of hidden, encrypted volumes within other volumes, as shown in Figure 9-2. Finally, the tool is under constant development, with regular security updates.
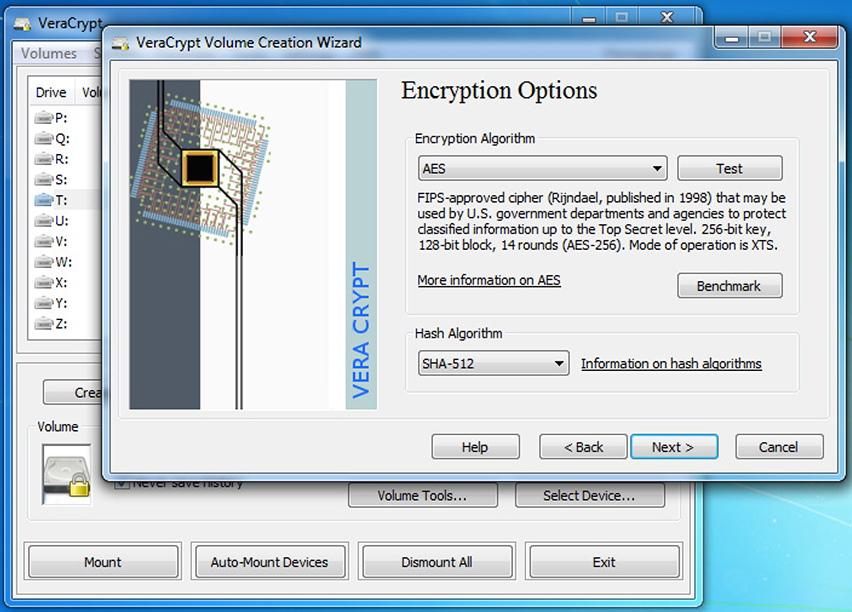
Figure 9-2 VeraCrypt creating an encrypted volume
Hashing Utilities
The most popular hashing algorithms for forensic analysis are MD5 and SHA-1, and they are supported by all the popular tools we discuss in this chapter. If you need a standalone hashing utility, many operating systems include these by default. Mac OS has the md5 tool available from the command line. Linux typically has both the md5 tool as well as sha1sum. Finally, Microsoft provides the File Checksum Integrity Verifier (FCIV) tool as a free but unsupported download. FCIV is able to compute both MD5 and SHA-1 hashes.
Analysis Utilities
The most widely used commercial analysis tools are Guidance Software’s EnCase and Access Data’s Forensic Toolkit (FTK). These tools are not cheap, but there are also a number of free or less-expensive options, including The Sleuth Kit. We describe each of these in turn in this section.
EnCase
EnCase is probably the most widely used analysis tool among law enforcement agencies as well as some of the larger corporations. It is a bit inaccurate to describe it solely as an analysis tool because it can actually perform acquisition (both live and dead), analysis, and reporting. In terms of acquisition, the product offers the option to run agents in all your endpoints and servers that can be used for remote acquisition over the network. This means you don’t need to physically seize the devices in order to acquire their data.
One of EnCase’s contributions to the field was the creation of the proprietary (but widely used) EnCase Evidence File format. Files in this format typically have an .E01 extension, though this is not necessary. What made the format so impactful was its integration of compression, encryption, and metadata all within the same file. If you are developing a raw or bit-for-bit image of an evidence drive, you would end up with multiple files: the copy, the hash value, and the metadata (for example, evidence label and case number). You could very well have other files associated with the copy. Furthermore, if you wanted to save space or ensure the confidentiality of the evidence, you would have to compress and/or encrypt the files separately. EnCase’s format allows all this to be incorporated into one file in an almost transparent manner.
FTK
Another very popular suite is the Forensic Toolkit, which is almost as widely used as EnCase. Users of both systems sometimes point to FTK’s more intuitive user interface, but that is clearly a subjective issue. What truly sets FTK apart from other solutions is its foundational data management model. Because this tool is built on top of a database management system, it is able to process very large volumes of data efficiently. In the latest release, FTK boasts support for ElasticSearch, which is a very popular open source search engine designed to deal with big data sources. The data preprocessing and indexing associated with these features, however, can make the initial case upload take longer than other solutions.
The Sleuth Kit
Rounding out our analysis suites is Brian Carrier’s open source The Sleuth Kit. Whereas EnCase and FTK go to great lengths to present a homogeneous user experience that hides the many tools that are working behind the scenes to support the analyst, The Sleuth Kit is more unabashedly a collection of interoperable tools, many of which use a command-line interface exclusively. However, if you would rather have a graphical user interface (GUI) comparable to the commercial solutions, you can use Autopsy with The Sleuth Kit to get the job done, as shown in Figure 9-3. Collectively, these tools do most of what EnCase and FTK do, but rather than thousands of dollars per license, there is no cost for them.

Figure 9-3 The Autopsy interface for The Sleuth Kit
OS and Process Analysis
An operating system (OS) is a software system that manages and controls all interactions with a computer. Though there are clearly a variety of operating systems in use today, they all perform the same three basic functions:
• Manage all computer resources such as memory, CPU, and disks
• Provide a user interface
• Provide services for running applications
It is the first of these that is of particular interest to a forensic analyst, because every action that occurs on a computer system is mediated by its OS.
If you are investigating a Microsoft Windows system, two of the most important sources of information are the registry and the event log. The registry is the principal data store where Windows stores most system-wide settings. Though all major analysis suites include viewers for this database, you can also examine it directly on any Windows computer by launching the Registry Editor application. There are literally hundreds of interesting artifacts you can find in the registry, including the following:
• Autorun locations This is where programs tell Windows that they should be launched during the boot process. Malware oftentimes uses this for persistence (for example, HKLMSoftwareMicrosoftWindowsCurrentVersionRun).
• Most Recently Used lists Often referred to as MRUs, this is where you’d find the most recently launched applications, recently used or modified documents, and recently changed registry keys. For example, if you wanted to see recently used Word documents, you would look in HKEY_CURRENT_USERSoftwareMicrosoftOffice12.0CommonOpen Find.
• Wireless networks Every time a computer connects to a wireless network, this is recorded in the registry, which you can then examine an as investigator in HKLMSOFTWAREMicrosoftWindows NTCurrentVersionNetworkListProfile.
Another useful source of information is the event logs, which you can access by launching the Event Viewer application in any Windows computer. There is actually a collection of logs, the number of which depends on the specific system. All Windows computers, however, will have an application log in which applications report usage, errors, and other information. There is also a security log in which the OS maintains security-related events such as unsuccessful login attempts. Finally, every Windows system has a system log in which the OS records system-wide events.
Although Linux doesn’t have the convenience of a centralized registry like Windows, it has its own rich set of sources of artifacts for a forensic investigator. For starters, a lot of relevant data can be found in plaintext files, which (unlike Windows) makes it easy to search for strings. Linux also typically includes a number of useful utilities such as dd, sha1sum, and ps, which can help you acquire evidence, hash it, and get a list of running processes (and resources associated with them), respectively. You can do all this in Windows, but need to install additional tools.
The Linux file system starts in the root directory, which is denoted by a slash. As an analyst, you need to be familiar with certain directories with which you should be familiar as an analyst. We highlight a few of these, but you should build up your own list from this start.
• /etc This is the primary system configuration directory, which contains a subdirectory for most installed applications.
• /var/log All well-behaved Linux applications will keep their log files in plaintext files in this directory, making it a gold mine for analysts.
• /home/$USER Here, $USER is a variable name that you should replace with the name of a given user. All user data and configuration data are kept here.
Note that this list is just a start. You should build up your own list from here.
Mobile Device Forensics
While there is some amount of forensic analysis that you can do on a live Windows or Linux system, mobile devices require dedicated forensic tools. The exceptions to this rule are jailbroken iPhones or iPads and rooted Android devices, because both of these expose an operating system that is very similar to Linux and includes some of the same tools and locations. To make things a bit more interesting, many phones require special cables although the migration toward USB-C in recent years is simplifying this as more devices adopt this interface.
Among the challenges involved in mobile forensics is simply getting access to the data. The mobile OS is not designed to support acquisition, which means that the forensic analyst must first get the device to load an alternate OS. This usually requires a custom bootloader, which is an almost essential feature of any mobile forensics toolkit.
Another peculiarity of mobile devices is that much of their data is stored in miniature database management systems such as SQLite. These systems require special tools to properly view their data. The advantage of them, however, is that they almost never delete data when the user asks them to. Instead, they mark the rows in the database table as deleted and keep their entire contents intact until new data overwrites them. Even then, the underlying file system may allow recovery of this deleted information. As with the bootloader, any common analysis suite will include the means to analyze this data.
Log Viewers
Every major OS provides the means to view the contents of its log files. The reason you may need a dedicated log viewer is that the built-in tools are meant for cursory examination and not for detailed analysis, particularly when the logs number in the thousands. Like most other features described so far, this functionality is oftentimes found in the forensic analysis suites. If you need a dedicated log viewer, there is no shortage of options, including many free ones.
A scenario in which a standalone log viewer would make sense is when you are trying to aggregate the various logs from multiple computers in order to develop a holistic timeline of events. You would want a tool that allows you to bring in multiple files (or live systems) and filter their contents in a variety of ways. Some tools that allow you to do this include Splunk, SolarWinds Event Log Consolidator/Manager, and Ipswitch’s WhatsUp.
Building Your Forensic Kit
There is no one-size-fits-all answer for what you should put in your forensic kit. It really depends on your environment and workflow processes. Still, there are some general tool types that almost everyone should have available if their work includes forensic analyses.
Jump Bag
The jump bag is a prepackaged set of tools that is always ready to go on no notice. This is your first line of help when you are asked to drop everything you’re doing and respond to an incident that may involve a forensic examination. Because you want to ensure that the bag is always ready, you’ll probably want to develop a packing list that you can use to inventory the bag after each use to ensure it is ready for the next run. You’ll probably want to include each of the following items in it.
Write Blockers and Drive Adapters
Hardware write blockers prevent modifications to a storage device while you acquire their contents. They come in many flavors and price points, but they all do essentially the same thing. The most important consideration is the type of interfaces they support. You should consult your asset inventory to see how many different types of disk interfaces are in use in your environment. Some tools support SCSI and ATA, but not SATA, and others may not support USB devices. As long as you have an adapter and cable for each type of storage device interface in your organization, you should be in good shape.
Cables
A good part of your jump bag will probably be devoted to cables of various types. A good rule of thumb to follow is that if you’ve ever needed a particular cable before, then you should probably keep it in your jump bag forever. Here are some ideas for the cables you may want to start with:
• Ethernet cables (crossover, straight-through, one-way)
• Serial cables (various flavors of USB and RS-232)
• Power cables
• A small Ethernet hub
• Antistatic wrist straps
Wiped Removable Media
You may not have a few hours to wipe a hard drive before responding to an incident, so it pays to keep a few packed. The type of interface doesn’t much matter (as long as it is supported by your write blocker), but the capacity does. A good rule of thumb is to look into your asset inventory and find the largest workstation or external drive in your organization and pack at least twice that amount of storage in your bag. Servers tend to have significantly larger drives than workstations, so if that is a concern, you may have to invest in a portable RAID solution such as Forensic Computers’ Forensic Data Monster. Solutions like these are portable and designed to facilitate the acquisition of evidence.
A common approach in organizations that deal with fairly frequent investigations is to set up a network-attached storage (NAS) solution specifically for forensic images. As long as you have a fast network connection, you’ll be able to image any workstation or server with ease. An added advantage is that the NAS can serve as an archival mechanism for past investigations that may still be pending in court. In these cases, it is important to abide by your organization’s data-retention policies.
Camera
The camera is an often-overlooked but critical item in your jump bag. It is important to photograph the crime or incident site, but pretty much any digital camera with a flash will do. A useful addition to your camera is a small ruler that you can include in shots whenever you need to capture a sense of distance or scale. Ideally, the ruler should have a matte surface to minimize glare.
Crime Scene Tape
This may sound like overkill, but having some means of notifying others in the area that they should not enter is critical to the seizure process. Crime scene (or other restricted-area-labeled) tape does the job nicely and inexpensively.
Tamper-Proof Seals
When the amount of evidence you collect, or the distance you have to transport it, requires the assistance of others (for example, drivers), you probably want to seal the evidence containers with a tamper-resistant seal. In a pinch, you can use tape and sign your name across it. However, if you can afford them, dedicated lockable containers will be best.
Documentation and Forms
Depending on your organization, many forms and other documents may only exist in digital form. Still, it is a good idea to have hard copies printed and in your jump bag because you never know whether you’ll be able to access your corporate data store in the middle of an incident response. Here are some items most of us would keep in our bags.
Chain of Custody Form Figure 9-1 showed a typical chain-of-custody form, but you should tailor it to your own organization’s requirements if you don’t already have one. The important aspect is to ensure there are enough copies to go with each seized piece of evidence. Ideally, your evidence transport containers have a waterproof pouch on the outside into which you can slide a form for the container (individual items in it may still need their own forms).
Incident Response Plan It is not unusual for an incident response to start off as one thing and turn into something else. Particularly when it comes to issues that may have legal implications (for example, forensic investigations), it is a good idea to have a copy of the plan in your jump bag. This way, even if you are disconnected from your network, you will know what you are expected or required to do in any situation you encounter.
Incident Log Every good investigator takes notes. When you’re performing a complex investigation, as most digital forensics ones are, it is important to document every action you take and every hypothesis you are considering. The most important reason for this level of thoroughness is that your conclusions are only as valid as your processes are repeatable. In other words, any qualified individual with access to the same evidence you have should be able to follow your notes and get the same results that you did. Keeping a notebook and pen in your jump bag ensures you are always ready to write down what you do.
Call/Escalation List If the conditions on the ground are not what you thought they’d be when you started your investigation, you may have to call someone to notify them of an important development or request authorization to perform some action. Though the call/escalation list should really be part of your incident response plan, it bears singling it out as an important item in your jump bag.
Chapter Review
Digital forensics investigations require a very high degree of discipline and fixed adherence to established processes. A haphazard approach to these activities can mean the difference between successful resolution of an incident, or watching a threat actor get away with criminal behavior. The challenge is in striking the right balance between quick responses to incidents that don’t require this level of effort and identifying those cases that do early enough to adjust the team’s approach to them. Because you might not know which events can escalate to forensic investigations, you should always be ready to perform in this manner with no notice.
The CySA+ exam will require you to know the four-step process (seizure, acquisition, analysis, reporting) and which actions you take during each. For example, you may see questions that present you with a scenario in which some part of the process has already been completed and you are asked what’s the next thing you do. This may require familiarity with the way in which you would use some of the most common tools, such as the Linux dd utility. Though you will probably not see a question that requires you to issue a command with arguments, you may have to interpret the output of such a tool and perform some sort of simple analysis of what may have happened.
Questions
1. In the event of a serious incident, which task is not a critical step to take in controlling the crime scene?
A. Record any interactions with digital systems.
B. Verify roles and training for individuals participating in the investigation.
C. Remove power from currently running systems.
D. Carefully document who enters and leaves the scene.
2. What is the practice of controlling how evidence is handled to ensure its integrity during an investigation called?
A. Chain of control
B. Chain of concern
C. Chain of command
D. Chain of custody
3. As part of the forensic analysis process, what critical activity often includes a graphical representation of process and operating system events?
A. Registry editing
B. Timeline analysis
C. Network mapping
D. Write blocking
4. During forensic acquisition, why is a high-level format normally insufficient when preparing the destination media?
A. High-level formatting completely wipes the drive, but may add additional artifacts.
B. High-level formatting only erases the file data, leaving the system structure intact.
C. High-level formatting only erases the file system structure data, leaving the file data intact.
D. High-level formatting removes bad sectors, but leaves file data intact.
5. The practice of modifying or deleting file modification data is referred to as what?
A. Timestomping
B. Timestamping
C. Timelining
D. Timeshifting
Use the following command-line input to answer Questions 6-8:
dd if=/dev/sda of=/dev/sdc bs=2048 conv=noerror,sync status=progress
6. How many bits of data are read and written at a time?
A. 2048
B. 16384
C. 256
D. 512
7. What is the name of the destination image?
A. sda
B. /dev/sda
C. sync
D. sdc
8. What is the purpose of the command?
A. To copy the primary partition to an image file
B. To restore the contents of a hard drive from an image file
C. To copy the entire contents of the hard drive to an image file
D. To delete the entire contents of /dev/sda
Use the following scenario to answer Questions 9–12:
You are called to a scene of a high-profile incident and asked to perform forensic acquisition of digital evidence. The primary objective is a Linux server that runs several services for a small company. The former administrator is suspected of running illicit services using company resources and is refusing to provide passwords for access to the system. Additionally, there are several company-owned mobile phones that appear to be functioning sitting on the desk beside the servers.
9. What is one of the first tasks you undertake in preparing to analyze the server’s hard drive?
A. Hash all storage media and then make a copy of the hard drive.
B. Begin analysis on the target system and perform recurring MD5 hashes.
C. Copy the entire contents to a SAN or external storage and begin analysis.
D. Perform analysis immediately on the server before loss of power.
10. What utility will allow you to make a bit-for-bit copy of the hard drive contents?
A. MFT
B. dd
C. MD5
D. GPU
11. What type of specialized software might you use to recover the credentials required to get system access?
A. Forensic duplicator
B. dd
C. Password cracker
D. MD5
12. You want to take the mobile phones back to your lab for further investigation. Which two tools might you use to maintain device integrity as you transport them?
A. Faraday bag and a tamper-evident seal
B. Write blocker and crime scene tape
C. Thumb drive and crime scene tape
D. Forensic toolkit and tamper-evident seal
Answers
1. C. Removing power should not be done unless it’s to preserve life or limb, or under other exigent circumstances. In many cases, it’s possible to recover evidence residing in running memory.
2. D. A chain of custody is a history that shows how evidence was collected, transported, and preserved at every stage of the investigation process.
3. B. Timeline analysis is the practice of arranging extracted data from a UNIX file system, the Windows registry, or a mobile device in chronological order to better understand the circumstances of a suspected incident.
4. C. The destination media should be free from anything that may contaminate the evidence. Completely removing the data requires overwriting each block of the destination storage medium, which may always be performed if you’re using high-level formatting tools.
5. A. Timestomping is an advanced technique to manipulate file creation or modification data to thwart forensics techniques. It’s often used by malware to make the process of timelining more difficult.
6. B. The bs argument indicates the number of bytes transferring during the process. Because there are 8 bits in a byte, you will multiply the 2048 by 8 to get 16384 bits.
7. D. The of argument indicates the output file of the process.
8. C. The source file is the entire hard drive, indicated by the argument /dev/sda. You should be careful to double-check the spelling of both input and output files to avoid overwriting the incorrect media.
9. A. You want to conduct your analysis on a copy of the evidence and not on the original, but be sure to take a cryptographic hash of the original evidence before you copy anything.
10. B. dd is a common utility found in most Linux-based systems. It can duplicate data across files, devices, partitions, and volumes.
11. C. Password crackers are specialized software designed to guess passwords and decrypt the protected resources. The software can be very resource intensive since cracking usually requires a lot of processing power or storage capacity.
12. A. A Faraday container will prevent the devices from communicating over radio waves by absorbing and redistributing their RF energy. You should secure the bag with a tamper-evident seal to easily identify whether its contents were interfered with.