Identifying and Evaluating Relevant Threats
A threat is any potential danger to the data, the hardware, or the systems. A threat assessment is the process of identifying threats.
How threats interact with risks as a whole is important to understand. FIGURE 6-4 shows the relationship between threats, attacks, vulnerabilities, and loss. A threat creates an attack, which exploits a vulnerability. When the threat/vulnerability pair occurs, a loss is incurred.
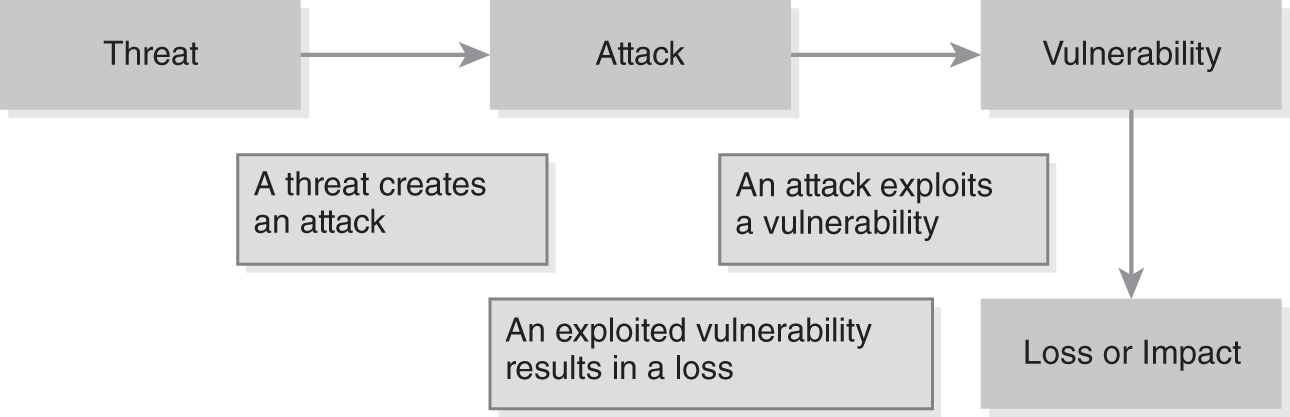
FIGURE 6-4 Threats and vulnerabilities.
In the diagram, an attacker is presented as a threat. However, a threat can be anything that can compromise confidentiality, integrity, or availability. Threats can be external or internal, natural or man-made, or intentional or accidental.
 NOTE
NOTE
This section introduces threats and activities related to risk assessment.
One of two primary methods can be used to identify threats. They are:
- Reviewing historical data
- Performing threat modeling
Reviewing Historical Data
History often repeats itself, and this is true with IT systems. Much time can be saved by reviewing historical data to identify realistic threats.
When reviewing historical data, the following events are important:
- Attacks—If an organization’s website has been attacked before, likely it will be attacked again. The success of the next attack depends on the level of protection that was implemented since then, which is true for any type of event.
- Natural events—If hurricanes have hit a company’s location before, they likely will do so in the future. Most organizations that are in risk zones for natural disasters, such as hurricanes, tornadoes, and earthquakes, have disaster recovery and business continuity plans in place. These plans should be reviewed, if not tested, on a regular basis, such as once a year.
- Accidents—Accidents can be any accidental event that affects confidentiality, integrity, or availability and includes users accidentally deleting data. Accidents can also include user errors or mishaps in the workplace.
- Equipment failures—Equipment failures result in outages, and some systems are more prone to failure than others. Additionally, some failures have a much greater impact on the mission of the business. By analyzing past failures, often, future failures can be predicted. The systems that will benefit from additional redundant hardware should be identified.
Performing Threat Modeling
Threat modeling is a process used to identify possible threats on a system by looking at a system from the attacker’s perspective. The result of threat modeling is a document called a threat model.
The threat model provides information on:
- The system—Background information on the system is also included.
- Threat profile—The threat profile is a list of threats that identifies what the attacker may try to do to the system, including possible goals of the attack. For example, one attack may attempt to take the system down, and another attack may attempt to access data in the system.
- Threat analysis—Each threat in the threat profile is analyzed to determine whether an asset is vulnerable. Threat analysis includes reviewing existing controls to determine their effectiveness against the threat.
Threat modeling allows the prioritization of attacks based on their probability of occurring and their potential harm.
