Asset and Inventory Management Within the Seven Domains of a Typical IT Infrastructure
Approaching an IT management problem from the perspective of the seven domains of a typical IT infrastructure is useful. These IT management problems include asset management and inventory management.
The seven domains of a typical IT infrastructure are:
- User Domain
- Workstation Domain
- LAN Domain
- LAN-to-WAN Domain
- WAN Domain
- Remote Access Domain
- System/Application Domain
FIGURE 7-3 shows the seven domains of a typical IT infrastructure.
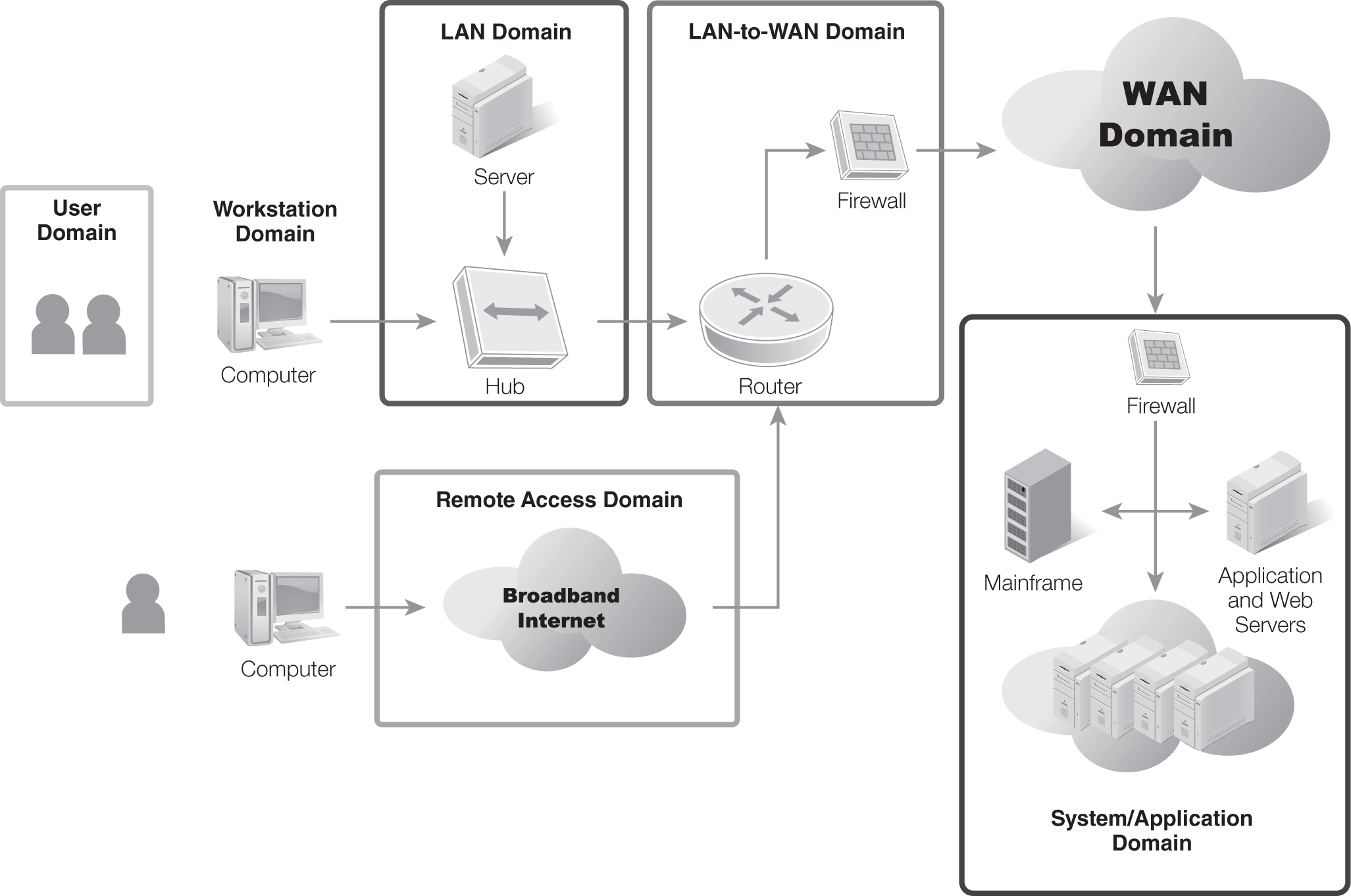
FIGURE 7-3 The seven domains of a typical IT infrastructure.
A difference exists between inventory management and asset management. Basic definitions of the two are:
- Inventory management—Used to manage hardware inventories, which includes only the basic data, such as model and serial numbers. It shows what assets are on hand, where they’re located, and who owns them. Inventory management is valuable to ensure that the inventory isn’t easily lost or stolen.
- Asset management—Used to manage all types of assets. It includes much more detailed data than an inventory management system includes. For example, asset management would cover installed components, hardware peripherals, installed software, update versions, and more.
Organizations may decide to use either or both types of management for different areas. For example, an organization may use inventory management for desktop PCs, which ensures the PCs are tracked and the investment is not lost. However, the same organization can also use automated asset management techniques. Asset management ensures the systems are patched correctly.
For each of the seven domains, company management needs to determine the answers to two basic questions considering the assets the company has:
- Are the assets valuable to the organization?
- Are they included in any type of inventory or asset management system?
If the assets are valuable, they should be included in either an inventory or an asset management system.
User Domain
The User Domain includes people or employees. An HR department maintains records on employees. These records can be manual records, such as folders held in filing cabinets, or files held on servers.
Data on users includes:
- Personal and contact data
- Employee reviews
- Salary and bonus data
- Health care choices
A significant concern with asset management in the User Domain is confidentiality. Data must be protected against unauthorized disclosure. At the very least, the data includes PII that must be protected by law. If any health care data is included, HIPAA mandates its protection. If salary and bonus data is leaked, it often results in morale problems.
Workstation Domain
The Workstation Domain includes the PCs used by employees, which could include typical desktop PCs and mobile computers or laptops. Assets in the Workstation Domain have two risks that need to be addressed:
- Theft—An organization has a significant investment in these systems and can’t afford to allow them to disappear. Inventory management systems include processes whereby each item is manually located on a periodic basis, which verifies the system is still in the organization’s control.
- Updates—As updates, fixes, and patches are released, they need to be applied to the systems. If the systems are not updated, they become vulnerable to new exploits. Automated asset management systems should be used to keep systems up to date. An automated system will often perform three steps: (1) inspect systems for current updates, (2) apply updates, and (3) verify the updates.
LAN Domain
The LAN Domain includes all the elements used to connect systems and servers together. The local area network (LAN) is internal to the organization. The primary hardware components are hubs, switches, and routers.
Having a basic inventory of these devices is important, which includes model number, serial number, and location. Although any network device includes firmware, the more functional network devices, such as routers and switches, have a built-in OS. The version of the OS determines its capabilities, so including the version in the inventory is often useful.
Configuration data should also be included for these devices in an asset management system. For example, scripts can be run to configure routers and switches. These scripts configure the devices to pass or block specific traffic. If a device loses its configuration, the script is run again, which assumes, of course, that the script is available. If the script isn’t available, the configuration data will need to be typed in line by line. If no record of the previous configuration data is available, the device will have to be troubleshot until it is restored to its original configuration.
 NOTE
NOTE
Switches have replaced hubs in most organizations today. A switch is more efficient because it minimizes traffic to only what’s necessary. Moreover, a switch provides an added layer of security by directing network traffic onward to the target system, rather than broadcasting it to all connected systems. An attacker using a protocol analyzer will be able to capture only a limited amount of data when a switch is used in place of a hub.
LAN-to-WAN Domain
The LAN-to-WAN Domain is the area in which the internal LAN connects to the wide area network (WAN). In this context, the WAN is often the Internet. The primary devices to be concerned with here are firewalls. A single firewall or multiple firewalls to create a demilitarized zone (DMZ), or a buffer area, can separate the LAN from the WAN.
Firewalls in the LAN-to-WAN Domain are hardware firewalls. They can be programmed to allow and block specific traffic. The following information should be included in an asset management system:
- Hardware information—Includes basics, such as the model and serial numbers. If the model supports different add-ons, such as additional memory or network interface cards, they should also be included.
- Configuration data—A significant amount of time goes into creating a firewall policy, after which firewall rules and exceptions to implementing the policy should be created. At the very least, all these rules and exceptions need to be documented. Whenever possible, to automate the process, scripts should be created and then backed up.
WAN Domain
The WAN Domain includes servers that have direct access to the Internet. These servers include all those that have public Internet Protocol (IP) addresses and are public facing in the DMZ.
 NOTE
NOTE
Internal computers have access to the Internet but not directly. Most organizations direct client traffic through a proxy server to give clients indirect access to the Internet. The proxy server has connectivity to the WAN with a public IP address and connectivity to internal clients with a private IP address.
Most organizations won’t have many servers in the WAN Domain. However, any servers in the WAN have significantly higher risks. Taking extra precautions to ensure these servers are hardened as much as possible is very important.
Inventory and asset management information for WAN-based servers include:
- Hardware information—Includes basics, such as the model and serial numbers. Documentation is similar to how servers in the LAN-to-WAN Domain would be documented.
- Update information—Servers in the WAN need to be kept up to date, which is an important step to ensure the servers stay secure. As patches, fixes, and updates are released, they need to be evaluated. If the update is needed and testing shows it doesn’t have negative effects, it should be applied. Updating of servers can be manual or automated. Either way, having an accurate record of updates installed on servers is important.
 NOTE
NOTE
Hardening a server makes it more secure from the default installation. The first things to do are remove unneeded services and protocols and enable the local firewall. Additionally, the server should be kept up to date by regularly applying updates after testing them.
Remote Access Domain
Remote access technologies give users access to an internal network via an external location. This process can be done via direct dial-up or a virtual private network (VPN).
When dial-up is used, clients and servers have modems and access to phone lines. When a VPN is used, the VPN server has a public IP address available on the Internet. Clients access the Internet and then use tunneling protocols to access the VPN server.
Inventory and asset management information needed for servers in the Remote Access Domain is similar to that in the WAN Domain. However, for dial-up remote access servers, the dial-up equipment will also need to be included, which includes both modems and phone branch exchange (PBX) equipment:
- Modems—Modems for a remote access server are more sophisticated than a simple modem for a client. They are often configured in banks of several modems and can be programmed to answer calls from more than one line.
- PBX equipment—Phone systems are managed using a PBX. PBXs often come as mini servers with full OSs.
System/Application Domain
The System/Application Domain includes servers used to host server applications. Examples of types of application servers include:
- Email server—Can be a single email server but also a larger email solution, including both front-end and back-end server configurations.
- Database server—Can be an Oracle or Microsoft SQL server as a single server or in a group of servers.
- Web server—A web server hosts websites and serves them to web clients. A single web server can host a single website or hundreds of websites.
- Networking service server—Includes Domain Name System (DNS) servers and Dynamic Host Configuration Protocol (DHCP) servers.
Inventory and asset management systems should include the following information on any servers in the System/Application Domain:
- Hardware information—Includes basics, such as the model and serial numbers, just as a workstation would be inventoried, and an inventory of the hardware components.
- Update information—Servers need to be kept up to date, which is especially true if any servers are public facing, such as web servers and some email servers.
 NOTE
NOTE
A VPN provides access to a private network over a public network, such as the Internet.
