Standards and Guidelines for Compliance
Several standards and guidelines exist that can be used to assess and improve security. Most of these standards are optional. However, some are mandatory for certain sectors. For example, the PCI DSS is required for merchants using specific credit cards.
The standards and guidelines covered in this section include:
- Payment Card Industry Data Security Standard (PCI DSS)
- National Institute of Standards and Technology (NIST)
- Generally Accepted Information Security Principles (GAISP)
- Control Objectives for Information and Related Technology (COBIT)
- International Organization for Standardization (ISO)
- International Electrotechnical Commission (IEC)
- Information Technology Infrastructure Library (ITIL)
- Capability Maturity Model Integration (CMMI)
- General Data Protection Regulation (GDPR)
- Department of Defense Information Assurance Certification and Accreditation Process (DIACAP)
Payment Card Industry Data Security Standard
The Payment Card Industry Data Security Standard (PCI DSS) is an international security standard. The purpose is to enhance security of credit card data. It was created by the PCI Security Standards Council with input from several major credit card companies. These companies include:
- American Express
- Discover Financial Services
- JCB International
- MasterCard Worldwide
- Visa Inc. International
The goal is to thwart theft of credit card data. Fraud can occur if a thief gets certain data. The key pieces of data are:
- Name
- Credit card number
- Expiration date
- Security code
Theft becomes easy if a thief has all of this information.
This data is often transmitted to and from the merchant. It can travel wirelessly from point-of-sale machines and from the merchant’s computer to an approval authority. It can be intercepted any time it’s transmitted and easily read if it is not encrypted.
For example, data from as many as 100 million credit cards was intercepted from a large retail chain between July 2005 and December 2006. Losses on Visa cards alone were close to $83 million. Millions of customers sued and the banks that issued the cards sued the retailer. Other examples include the Equifax data breach of 2017, which affected about 40 percent of Americans and exposed the personal information of 147 million people. A 2019 data breach involving Capital One exposed the records of almost 106 million people. All these problems could have been prevented with basic security.
The PCI DSS is built around six principles. Each of these principles has one or two requirements. The principles and requirements are:
- Build and Maintain a Secure Network
- Requirement 1: Install and maintain a firewall.
- Requirement 2: Do not use defaults, such as default passwords.
- Protect Cardholder Data
- Requirement 3: Protect stored data. Requirement 4: Encrypt transmissions.
- Maintain a Vulnerability Management Program
- Requirement 5: Use and update antivirus software. Requirement 6: Develop and maintain secure systems.
- Implement Strong Access Control Measures
- Requirement 7: Restrict access to data.
- Requirement 8: Use unique logins for each user. Don’t share usernames and passwords.
- Requirement 9: Restrict physical access.
- Regularly Monitor and Test Networks
- Requirement 10: Track and monitor all access to systems and data. Requirement 11: Regularly test security.
- Maintain an Information Security Policy
- Requirement 12: Maintain a security policy.
Merchants using credit cards are required to comply with PCI DSS. Compliance is monitored by the acquirer, which is the company that authenticates the transactions.
Compliance with PCI DSS is a three-step continuous process. This process is shown in FIGURE 3-3:
- Assessing—The merchant inventories IT assets and processes used for credit card data. It identifies existing cardholder data and then analyzes data and processes for vulnerabilities.
- Remediating—The merchant corrects vulnerabilities. It stores data only when necessary.
- Reporting—The merchant submits compliance reports to the acquiring banks.
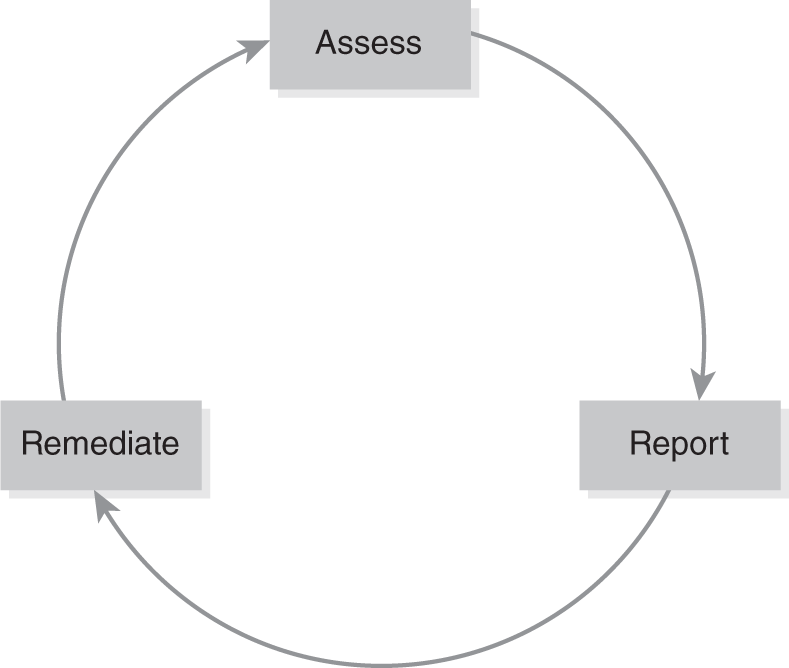
FIGURE 3-3 PCI compliance process.
This process is repeated at different times.
Although PCI DSS compliance helps prevent losses, it isn’t foolproof. For example, attackers stole credit card data on 40 million customers in a major attack against Target Corporation in late 2013. Attackers also stole personal information on up to 70 million more customers in the same attack. In 2019, personal data from over 106 million customers was stolen from Capital One. Target was certified as PCI DSS compliant during the attack. The same attack compromised 1.1 million cards at Neiman Marcus. Michael Kingston, CIO at Neiman Marcus, stated that the company’s security measures exceeded PCI standards.
A PCI DSS investigation might reveal a problem missed by the PCI DSS assessments that certified these companies. In the past, PCI compliance has been retroactively revoked, which allows the certifying agencies to state that “no PCI compliant organization has ever been breached.” However, many security experts suggest that it is time to update PCI DSS.
National Institute of Standards and Technology
The National Institute of Standards and Technology (NIST) is a division of the U.S. Department of Commerce. The mission of NIST is to promote U.S. innovation and competitiveness.
NIST hosts the Information Technology Laboratory (ITL). The ITL develops standards and guidelines related to IT. They are published as special publications whose titles have a prefix of SP. SP 800-30, Guide for Conducting Risk Assessments, is valuable when studying risk management.
SP 800-30 includes three chapters:
- Introduction—This short chapter identifies the objectives and gives some references.
- The Fundamentals—This chapter discusses the importance of risk assessment. It includes definitions for many key risk terms. It also presents models used to assess risk.
- The Process—This chapter describes the process of risk assessments. It includes information on how to prepare for and conduct the assessment. It also provides detailed information on how to perform six key risk assessment tasks. The tasks are:
- Identifying relevant threat sources
- Identifying potential threat events related to the threat sources
- Identifying vulnerabilities threats can exploit
- Determining the likelihood threats will occur and can succeed
- Determining the adverse impact if a threat exploits a vulnerability
- Determining the risk by combining the likelihood and impact
Generally Accepted Information Security Principles
The Generally Accepted Information Security Principles (GAISP) is an older standard that evolved from the Generally Accepted System Security Principles (GASSP), which was created in 1992. GAISP was an update to GASSP.
GAISP version 3 was released in August 2003 and was adopted by the Information Systems Security Association (ISSA). However, GAISP is no longer mentioned on the ISSA website. Additionally, the gaisp.org website is no longer maintained.
GAISP includes two major sections:
- Pervasive principles—These principles provide general guidance. The goal is to establish and maintain information security.
- Broad functional principles—These principles are derived from the pervasive principles. They represent broad goals of information security (IS).
Control Objectives for Information and Related Technology
Control Objectives for Information and Related Technology (COBIT) is a set of practices that apply to IT management and governance. Information technology governance (ITG) refers to the processes that ensure IT resources are enabling the organization to achieve its goals. Further, ITG processes help ensure the effectiveness and efficiency of these resources. COBIT helps link business goals with IT goals.
The IT Governance Institute (ITGI) worked with ISACA to develop COBIT. ISACA was previously known as the Information Systems Audit and Control Association. However, it now uses only the acronym. Many of the free COBIT resources can be accessed from ISACA’s website at https://www.isaca.org/resources/cobit.
ISACA recently published COBIT 2019. COBIT 2019 is a leading framework for the governance and management of IT resources throughout an enterprise.
The five principles are:
- Meeting stakeholder needs—A stakeholder is an entity affected by activity. In this case, stakeholders are typically decision makers who benefit from IT resources.
- Covering the enterprise end to end—All areas of responsibility are included.
- Applying a single integrated framework—COBIT 2019 uses an expanded and robust integrated framework. The integrated framework avoids conflicts when using multiple frameworks.
- Enabling a holistic approach—A holistic approach ensures that the organization is examined as a whole.
- Separating governance from management—Governance includes evaluating, directing, and monitoring. Management includes planning, building, running, and monitoring.
FIGURE 3-4 shows the seven COBIT components. The following bullets describe them:
- Principles, policies, and frameworks—These components translate desired behavior into practical guidance.
- Processes—Processes are the practices and activities performed within the organization. They help an organization reach its IT-related goals.
- Organizational structures—Organizational structures refer to the entities making key decisions. Many organizations define these entities in organization charts.
- Culture, ethics, and behavior—The success of individuals within the organization and the entire organization itself depends on these factors.
- Information—Organizations rely on accurate information, which is true for both operations and governance.
- Services, infrastructure, and applications—Organizations rely on the IT processing and services provided by these elements.
- People, skills, and competencies—Successful completion of activities is dependent on these components.
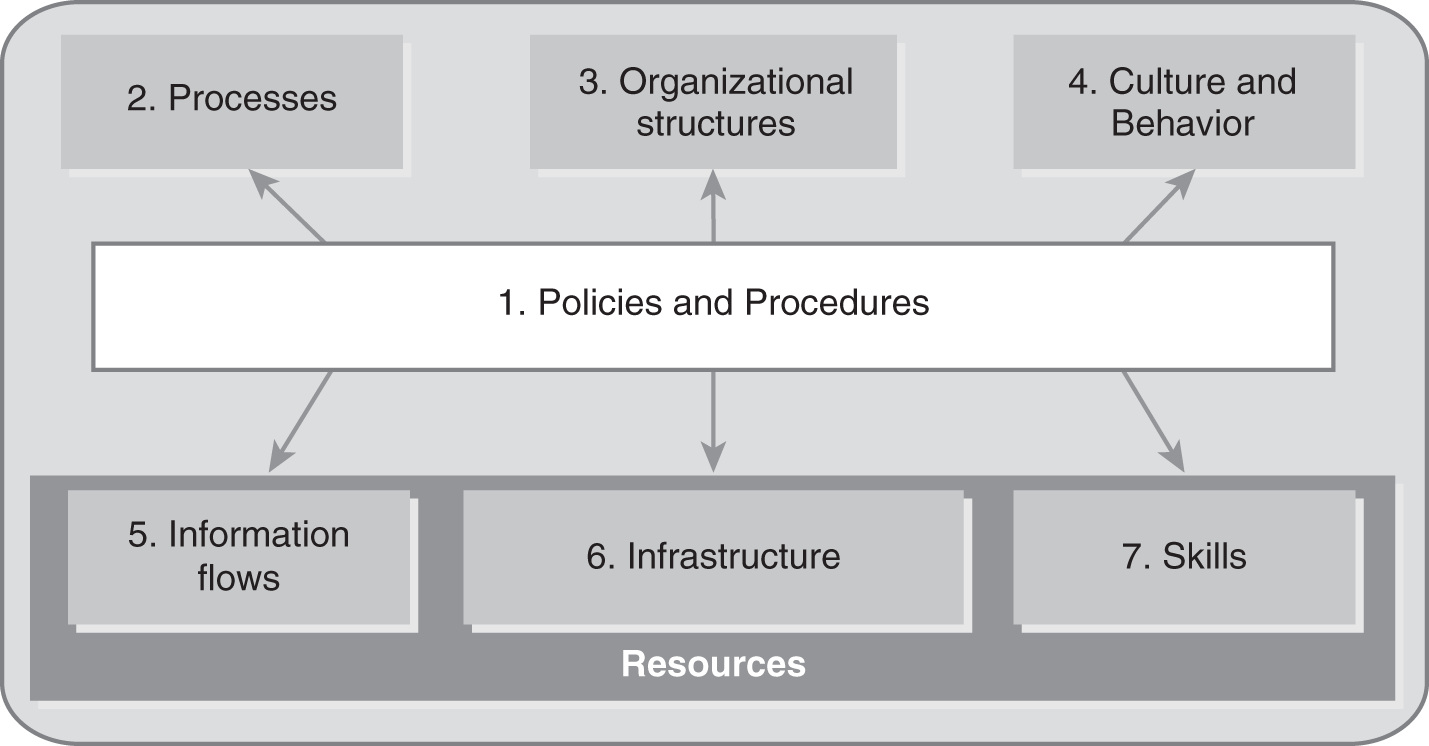
FIGURE 3-4 The seven COBIT components.
COBIT 2019. © 2019 ISACA. All rights reserved. Used with permission.
International Organization for Standardization
The International Organization for Standardization (ISO) develops and publishes standards. Its members are from 164 countries, and its main office is in Geneva, Switzerland.
ISO works with the International Electrotechnical Commission (IEC). Many of the standards are published as ISO/IEC standards; however, commonly, the standards are identified as only ISO. For example, the ISO/IEC 27002 standard is frequently shortened to ISO 27002.
ISO has published many standards that are relevant to risk and IT. Three important standards are:
- ISO 27002 Security Techniques
- ISO 31000 Principles and Guidelines on Implementation
- ISO 73 Risk Management—Vocabulary
Documentation for these standards can be purchased from the ISO website at http://www.iso.org.
ISO 27002 Information Technology Security Techniques
ISO 27002 is a set of guidelines and principles that are used for security management. The current version is ISO 27002:2013. This version was derived from the British Standard (BS) 7799, which is a well-respected standard.
The ISO number for this document has changed over the years. The following list shows the history of these changes:
- ISO/IEC 17799:2000—First ISO version of this document
- ISO/IEC 17799:2005—An update to ISO/IEC 17799:2000
- ISO/IEC 17799:2005/Cor 1:2007—A one-correction document
- ISO/IEC 27002:2005—Includes ISO/IEC 17799:2005 and ISO/IEC 17799:2005/Cor 1:2007. The content is identical to 17799, but the number changed to 27002.
- ISO/IEC 27002:2013—Published as a major update. However, most of the changes just moved and content was renumbered.
An organization can be certified as ISO 27002 compliant. Certification requires a two-step process. First, the organization must implement certain best practices, and, second, an outside source must evaluate the practices.
These best practices are related to:
- Security policy
- Organization of information security
- Asset management
- Human resources security
- Physical and environmental security
- Access control
- Incident management
- Business continuity
- Compliance
ISO 31000 Risk Management Principles and Guidelines
ISO 31000:2009 provides generic guidance on risk management. In other words, it applies to other than IT. An organization can use the principles and guidelines throughout its life and apply them to all types of risk.
No certification process exists for ISO 31000. For comparison, an organization can become ISO 27002 certified but not ISO 31000 certified.
Two supplementary documents associated with ISO 31000 are:
- ISO 73 Risk Management—Vocabulary
- IEC 31010 Risk Management—Risk Assessment Techniques
ISO 73 Risk Management—Vocabulary ISO 73:2009 is a list of terms that are related to risk management. The goal of this list is to provide common definitions for terms used in risk management.
Definitions can be used by:
- Anyone managing risks
- Anyone involved in ISO and IEC activities
- Developers of other risk management standards and guides
ISO 73 refers to ISO 31000:2009 for principles and guidelines on risk management. ISO 73:2009 and ISO 31000:2009 were released at the same time.
 NOTE
NOTE
The ISO 73:2009 standard replaced the ISO/IEC 73:2002 standard.
IEC 31010 Risk Management—Risk Assessment Techniques This generic risk management standard supports ISO 31000 and also guides the selection and application of techniques considered systematic for the assessment of risks
International Electrotechnical Commission
The International Electrotechnical Commission (IEC) is an international standards organization. It prepares and publishes standards for electrical, electronic, and related technologies. The overall objectives of the IEC are to:
- Meet the requirements of the global market
- Ensure maximum use of its standards
- Assess and improve products and services covered by its standards
- Aid in interoperability of systems
- Increase the efficiency of processes
- Aid in improvement of human health and safety
- Aid in protection of the environment
The IEC published IEC 31010 Risk Management—Risk Assessment Techniques, which is a supporting standard for ISO 31000.
Information Technology Infrastructure Library
The Information Technology Infrastructure Library (ITIL) is a group of five books developed by the United Kingdom’s Office of Government Commerce (OGC). ITIL has been around since the 1980s and has improved and matured since then. The OGC released ITIL 2011 in July 2011. It replaces ITIL 2007, which was previously called ITIL v3. The differences between ITIL 2007 and ITIL 2011 are minor. Instead, the books have been updated for clarity.
The UK recognized that some companies that were using IT were succeeding and others using similar technologies were failing. One of the goals of ITIL was to document the differences. Early versions of ITIL identified best practices, which were proven activities or processes that were successful in many organizations.
ITIL later renamed best practice to good practice. A good practice is a proven, generally accepted practice. It isn’t required in every organization. However, good practices are implemented whenever possible. ITIL recommends the use of several frameworks as good practices. Two of the frameworks recommended by ITIL are:
- Control Objectives for Information and Related Technology (COBIT), mentioned earlier in this section
- Capability Maturity Model Integration (CMMI), mentioned later in this section
The five books of the ITIL focus on its life cycle. They are:
- ITIL Service Strategy—This book helps an organization identify the services it should provide.
- ITIL Service Design—This book details how identified services can be implemented.
- ITIL Service Transition—This book focuses on introducing the services and also includes modifying or changing services. Most companies have learned the hard way that, if changes aren’t managed, they can take systems down. Change management has become important for many companies.
- ITIL Service Operation—This book focuses on day-to-day operations.
- ITIL Continual Service Improvement—This book focuses on methodologies used to improve the services.
 NOTE
NOTE
One of the drawbacks to ITIL is the affordability of the books. The five ITIL books together have a retail cost of $300 or more.
FYI
ITIL is centered on services. A service is a means of delivering value to customers, to give customers what they want. Having the service doesn’t require the customer to take ownership of the costs and risks of service delivery. For example, email is a service, and most customers want to be able to send and receive emails. However, most customers don’t want to own and manage the email servers. In this context, email can be provided to employees from the IT department. The employees are the customers, and the IT department is the service provider.
FIGURE 3-5 shows the relationships among the five phases of the ITIL life cycle. Any service implemented and managed within an IT organization will go through several phases, and each phase has its own concerns and requirements.
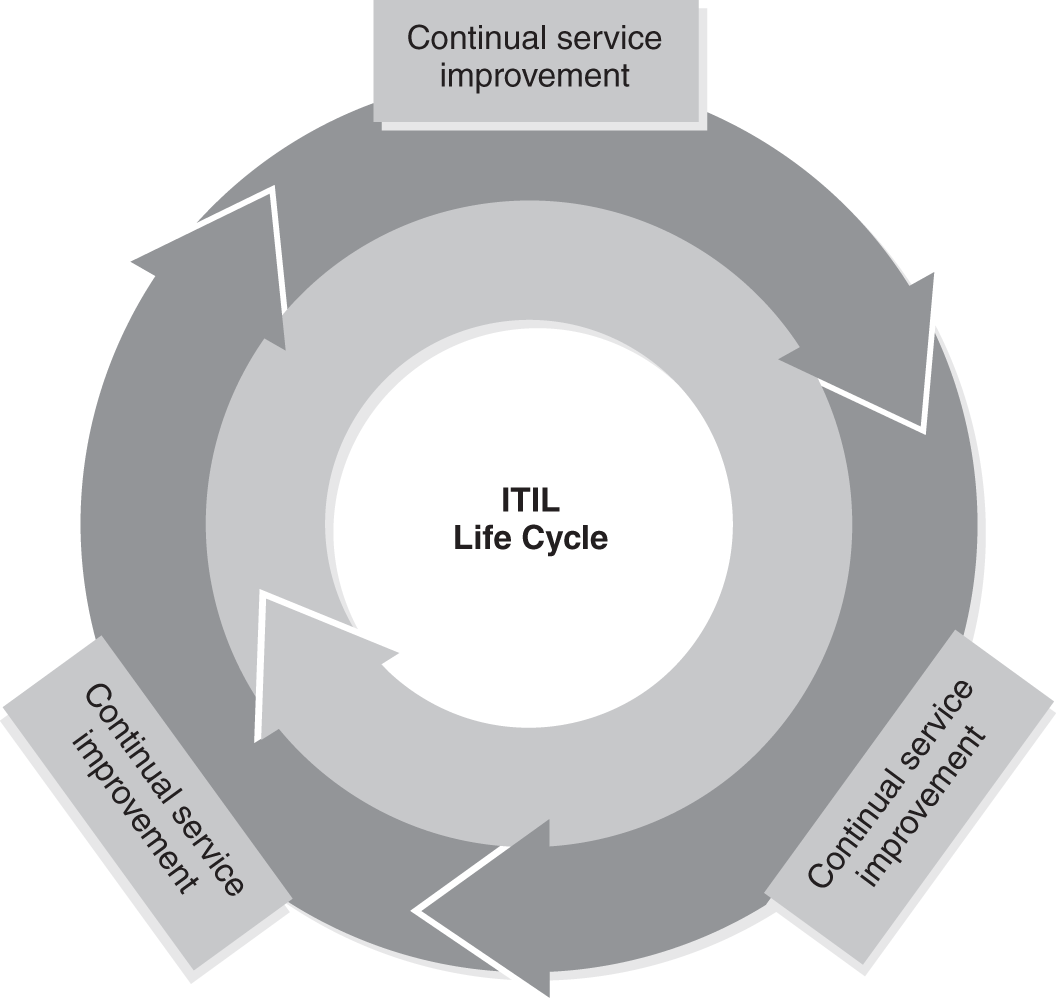
FIGURE 3-5 ITIL life cycle.
For an example of email as a provided service, a company was moving from outsourced email to an internal email server. The company could use the ITIL life cycle for each phase of the implementation:
- Service Strategy phase—Services are evaluated to determine whether they have value to the organization. Email could provide value with improved sales and improved productivity due to better communication. If the determination is made that internal email will provide value, the process continues to the next phase.
- Service Design phase—IT designs services for use within the organization. In this phase, IT would design the company’s email solution. For example, the company’s IT network may be a Microsoft Windows domain, so IT would design a Microsoft Exchange solution. How many servers to add and any changes needed in the network to support the servers would be identified.
- Service Transition phase—This phase includes adding, modifying, and removing obsolete services. A primary goal of this phase is to ensure the transition does not cause an outage. Adding a Microsoft Exchange email solution, for example, would include several elements. The Active Directory schema would need to be modified, and global catalog servers might need to be added. Microsoft Exchange servers would need to be built and applications installed on users’ computers. Everyone from end users to technicians maintaining the new servers would need to be trained.
- Service Operation phase—Daily operations and support of any service are handled at this stage. For email, these services can include regular maintenance and handling incidents that impact the service. They would also include performing backups and test restores. The goal here is to ensure that the end users have access to their email when they expect to have it.
- Continual Service Improvement phase—This phase focuses on measuring and monitoring services and processes. The goal is to determine areas where services can be improved, which can include regular monitoring and performance tuning of the email servers. Analysis can be used to identify problem areas before they become actual problems and provide insight into areas that can be improved.
ITIL resources can be accessed at https://www.itlibrary.org.
Capability Maturity Model Integration
The Capability Maturity Model Integration (CMMI) is a process improvement approach to management. It uses different levels to determine the maturity of a process.
CMMI can be used in three primary areas of interest:
- Product and service development—CMMI is often used with software development to help ensure that the final product meets the original goals and the product is completed within budget and time constraints.
- Service establishment, management, and delivery—CMMI can be used to measure the effectiveness of services, one of which is security. Security helps ensure confidentiality, integrity, and availability of data and systems.
- Product and service acquisition—This area of CMMI can be used to ensure that what is needed is consistently bought and what is paid for is received.
FIGURE 3-6 shows the six levels of the CMMI, which are also referred to as CMMI characteristics. These levels can be used to determine the effectiveness of security within an organization. The following list identifies the levels and how they can be used to evaluate security. Although Level 0 is listed here, sometimes, it is omitted:
- Level 0: Nonexistent—Security controls are not in place. There is no recognition of a need for security.
- Level 1: Initial—Sometimes, this level is referred to as ad hoc, or as needed. Risks are considered after a threat exploits a vulnerability.
- Level 2: Managed—The organization recognizes risks and the need for security. However, it performs controls out of intuition, rather than from detailed plans. Responses are reactive.
- Level 3: Defined—The organization has security policies in place. It has some security awareness, and action is proactive.
- Level 4: Quantitatively Managed—The organization measures and controls security processes. It has formal policies and standards in place and performs regular risk and vulnerability assessments.
- Level 5: Optimized—The organization has formal security processes in place throughout. It monitors security on a continuous basis and focuses on process improvement. This level shows the highest degree of maturity.

FIGURE 3-6 CMMI characteristics.
General Data Protection Regulation
The General Data Protection Regulation (GDPR) is part of European Union (EU) law. The regulation replaced the Data Protection Directive 95/46/ec in 2018 as the primary law regulating how companies protect the personal data of EU citizens. It was designed as a legal framework that sets guidelines to collect and process the personal information of individuals who live in the EU and the European Economic Area (EEA). The regulation applies to all businesses that deal with the personal data of individuals living in the EU or EEA, no matter where the companies are located. All companies, including those that were previously compliant, must comply with the 2018 GDPR directive or otherwise face stiff penalties and fines. Listed below are key changes under the GDPR and how they differ from the previous regulation:
- Increased territorial scope (extraterritorial applicability)—GDPR applies to all companies that process personal data of individuals living in the EU or EEA, no matter where the companies are located. The previous directive did not make this clear; instead, it referred to data processing “in context of an establishment.”
- Penalties—Companies in breach of the GDPR could be fined up to 4 percent of annual global turnover or $22 million, whichever is greater. This amount represents the maximum amount that a company can be liable for, for example, not having adequate customer consent to process data or violating privacy principles.
- Consent—Companies must provide consent in an intelligible and easily accessible form, stating the purpose for data processing attached to that consent. Consent must be clear and distinguishable from other matters and be easy to withdraw in the same way it was given.
- Data subject rights—Individuals whose data is collected and processed have a number of rights governed by the following principles:
- Breach notification
- Right to access
- Right to be forgotten
- Data portability
- Privacy by design
- Data protection officers
Department of Defense Information Assurance Certification and Accreditation Process
The Department of Defense Information Assurance Certification and Accreditation Process (DIACAP) is a risk management process that applies to IT systems used by the U.S. Department of Defense (DoD). It is fully documented in DoD instruction 8510.1.
DIACAP details specific phases that IT systems must go through. The core goal is to ensure that systems are in compliance with requirements. These phases are:
- Phase 1: Initiate and Plan—Register the system with DIACAP. Assign information assurance (IA) controls. Create a DIACAP team. Develop a DIACAP strategy. Begin the IA plan.
- Phase 2: Implement and Validate—Implement the IA plan. Update the IA plan if needed. Perform validation activities to verify compliance of the system. Document validation results.
- Phase 3: Make Certification and Accreditation Decisions—Analyze residual risk. Review documentation to verify certification. A decision is then made whether to accredit the system. Once the system has been accredited, it receives an authorization to operate (ATO).
- Phase 4: Maintain ATO/Review—Maintain the system. The goal is to ensure it stays in compliance with the requirements of the ATO. Periodically review the system for compliance.
- Phase 5: Decommission—Decommission the system. Dispose of DIACAP data.
 NOTE
NOTE
DIACAP replaced DITSCAP in 2007. DITSCAP was an acronym for DoD Information Technology Security Certification and Accreditation Process.
(ISC)2 offers a civilian-based certification that can be used for DoD 8570.1. It is called Certification and Accreditation Professional (CAP). It requires two years’ experience in the certification and accreditation field, and an exam must be passed with a score of at least 700.
 NOTE
NOTE
(ISC)2 sponsors several certifications. One of them is the Systems Security Certified Practitioner (SSCP), and another one is the Certified Information Systems Security Professional (CISSP), which is a higher-level certification than the SSCP.
