What Is Risk?
Risk is the likelihood or probability that something unexpected is going to occur. This unexpected result could be either a gain or a loss. In the world of information security, most organizations focus on ways to guard against asset losses. Losses occur when a threat exposes a vulnerability that could harm an asset. Companies employ risk assessment strategies to differentiate severe risks from minor risks. When this is done properly, administrators and managers can make rational decisions about how to handle each risk they’ve identified.
Risk management is the practice of identifying, assessing, controlling, and mitigating risks. In this discussion, the key terms that a person will need to be familiar with are shown in the following list. Each term will be discussed in detail later in the chapter.
 NOTE
NOTE
NIST Special Publication 800-37 Rev. 2 provides a definition of risk: “Risk is a measure of the extent to which an entity is threatened by a potential circumstance or event. Risk is also a function of the adverse impacts that arise if the circumstance or event occurs, and the likelihood of occurrence. Types of risk include program risk; compliance/regulatory risk; financial risk; legal risk; mission/business risk; political risk; security and privacy risk (including supply chain risk); project risk; reputational risk; safety risk; strategic planning risk.”
- Threat—A threat is any activity that represents a possible danger.
- Vulnerability—A vulnerability is a weakness.
- Asset—An asset is a thing of value worth protecting.
- Impact of loss—Impact of loss is a loss resulting in a compromise to business functions or assets.
Risks to a business can result in a loss that negatively affects the business and its core business functions. A business commonly tries to limit, or control, its exposure to risks. The overall goal is to reduce as much as possible the impact of losses that can occur from risk.
 NOTE
NOTE
Threats and vulnerabilities are explored in much more depth later in this chapter.
Compromise of Business Functions
Business functions are the activities a business performs to sell products or services. If any of these functions are negatively affected, the business won’t be able to sell as many products or services. The business will earn less revenue, resulting in an overall loss.
Here are a few examples of business functions and possible compromises:
- Salespeople regularly call or email customers. If the capabilities of either phones or email are reduced, sales are reduced.
- An organization receives several emails that are unrelated to business functions, which temporarily clog up email space and make network resources unavailable. This situation is referred to as a denial of service (DoS) attack. When a DoS attack happens across the organization’s network whereby the network receives emails from multiple sources, it is called a distributed denial of service (DDoS) attack.
- A website sells products on the Internet. If the website is attacked and fails, sales are lost.
- Authors write articles that must be submitted by a deadline to be published. If the author’s computer becomes infected with a virus, the deadline passes, and the article’s value is reduced.
- Analysts compile reports used by management to make decisions. Data is gathered from internal servers and Internet sources. If network connectivity fails, analysts won’t have access to current data. Management could make decisions based on inaccurate information.
- A warehouse application is used for shipping products that have been purchased. It identifies what has been ordered, where the products need to be sent, and where the products are located. If the application fails, products aren’t shipped on time.
- A person calls an organization pretending to have a legitimate purpose and attempts to trick someone in the organization into divulging personal or protected information. This form of impersonation, known as social engineering, can compromise the organization’s business functions and lead to losses.
Because compromises to any of these business functions can result in a loss of revenue, all of them represent a risk. One of the tasks when considering risk is identifying the important functions for a business and ensuring that organizations provide necessary employee training to reduce their weakest links (i.e., people with limited knowledge of technology and security).
The importance of any business function is relative to the business. In other words, the failure of a website for one company may be catastrophic if all products and services are sold through the website. Another company may use its website only to provide hours of operation to its customers; therefore, the website’s failure will have less impact on the business.
Threats, Vulnerabilities, Assets, and Impact
Earlier, key terms related to risk were introduced. Their relationship can now be seen. When a threat exploits a vulnerability to gain access to an asset, the threat could potentially result in a loss if the asset is compromised. The impact of the threat identifies the severity of that loss. It is important to note that not all assets are considered valuable. The greater the value attached to an asset, the greater the severity of the loss will be, making the need to put controls in place to prevent the loss from being greater.
Threats
A threat is any circumstance or event with the potential to cause a loss. A threat can also be thought of as any activity that represents a possible danger. Threats are always present and cannot be eliminated, but they can be controlled. Assets represent anything of value worth protecting.
Threats have independent probabilities of occurring that often are unaffected by an organization’s action. As an example, an attacker may be an expert in attacking web servers hosted on Apache. There is very little a company can do to stop this attacker from trying to attack. However, the company can reduce or eliminate vulnerabilities to reduce the attacker’s chances of success.
Threats can be thought of as attempts to exploit vulnerabilities that result in the loss of confidentiality, integrity, or availability of a business asset. The protection of confidentiality, integrity, and availability is a common security objective for information systems.
FIGURE 1-1 shows these three security objectives as a protective triangle. If any side of the triangle is breached or fails, security fails. In other words, risks to confidentiality, integrity, or availability represent potential loss to an organization. Because of this, a significant amount of risk management is focused on protecting these resources.
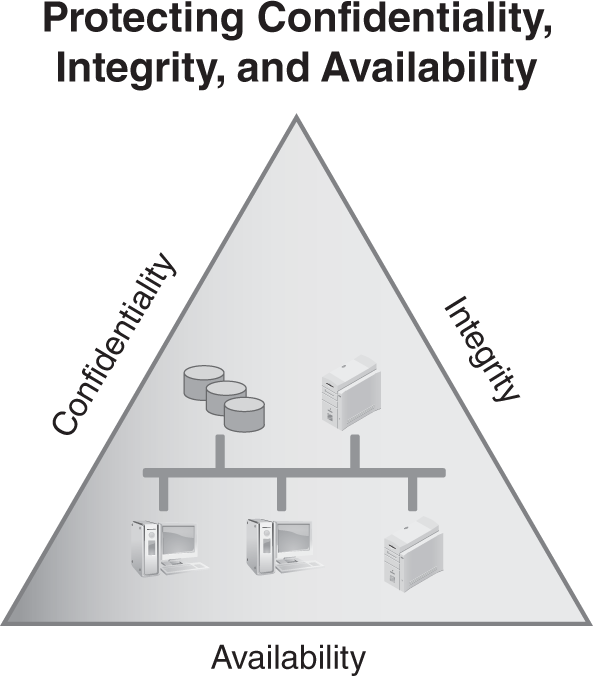
FIGURE 1-1 Security objectives for information and information systems.
- Confidentiality—Preventing unauthorized disclosure of information. Data should be available only to authorized users. Loss of confidentiality occurs when data is accessed by someone who should not have access to it. Data is protected using access controls and encryption technologies.
- Integrity—Ensuring data or an IT system is not modified or destroyed. If data is modified or destroyed, it loses its value to the company. Hashing is often used to ensure integrity.
- Availability—Ensuring data and services are available when needed. IT systems are commonly protected using fault tolerance and redundancy techniques. Backups are used to ensure the data is retained even if an entire building is destroyed.
 NOTE
NOTE
Confidentiality, integrity, and availability are often referred to as the security triad, or the C-I-A triad.
 TIP
TIP
The method used to take advantage of a vulnerability can also be referred to as an exploit.
Vulnerabilities
A vulnerability is a weakness. It could be a procedural, technical, or administrative weakness. It could be a weakness in physical, technical, or operational security. Just as all threats don’t result in a loss, all vulnerabilities don’t result in a loss. A loss to an asset occurs only when an attacker is able to exploit the vulnerability.
Vulnerabilities may exist because they’ve never been corrected. They can also exist if security is weakened either intentionally or unintentionally.
Considering a locked door used to protect a server room, a technician could intentionally unlock it to make it easier to access. If the door doesn’t shut tight on its own, it could accidentally be left open. Either way, the server room and its contents become vulnerable.
Assets
A business asset is anything that has measurable value to a company. If an asset has the potential to lose value, it is at risk. Value is defined as the worth of an asset to a business.
Assets can have both tangible and intangible values. The tangible value is the actual cost of the asset and can be expressed in monetary terms, such as $5,000. The tangible assets of a business include its inventory, furniture, and machinery. Examples of tangible IT assets are:
- Computer systems—Servers, desktop PCs, and mobile computers
- Network components—Routers, switches, firewalls, and any other components necessary to keep the network running
- Software applications—Any application that can be installed on a computer system
- Data—Includes the large-scale databases that are integral to many businesses; also includes the data used and manipulated by each employee or customer
The intangible value is value that cannot be measured by cost, such as client confidence or company reputation. Generally acceptable accounting principles (GAAP) refer to client confidence as goodwill.
For example, a company sells products via a website, and it earns $5,000 an hour in revenue. The web server hosting the website fails and is down for two hours. The cost to repair it totals $1,000. What is the tangible loss?
- Lost revenue—$5,000 times two hours equals $10,000
- Repair costs—$1,000
- Total tangible value—$11,000
The intangible value isn’t as easy to calculate but is still important. For example, a customer with an urgent need tried to make a purchase when the website was down. If the same product is available somewhere else, he or she may choose to purchase the product elsewhere. That experience may damage the organization’s reputation in the eye of that customer, and, if the customer’s experience with the other business is positive, the customer may go directly to the second company the next time he or she wants to purchase this product. The loss of this future business cannot be measured, which makes it intangible.
Intangible value includes:
- Future lost revenue—Any additional purchases customers make with another company are a loss to the company whose website was down.
- Cost of gaining the customer—Large sums of money are invested in attracting customers. A repeat customer is much easier to sell to than acquiring a new customer. If a company loses a customer, the company’s investment is lost.
- Customer influence—Customers have friends, families, and business partners. They commonly share their experience with others, especially if the experience is exceptionally positive or negative.
- Reputation—Customers share their negative experience with others, so one customer’s bad experience could potentially influence other current or potential customers to avoid future business transactions.
One of the early steps in risk management is associated with identifying the assets of a company and the assets’ associated costs. This data is used to prioritize risks for different assets. Once a risk has been prioritized, identifying risk management processes to protect the asset becomes easier.
Impact
The impact is the amount of the loss, which can be expressed in monetary terms, such as $5,000. The value of hardware and software is often easy to determine. If a laptop is stolen, the purchase or replacement value can be used to determine the value of the stolen laptop. However, some losses aren’t easy to determine. If that same laptop held data, the value of the data is hard to estimate.
Descriptive terms, instead of monetary terms, can be used to explain the impact of a loss. For example, losses can be described in relative terms, such as high, medium, or low, which helps an organization quantify the loss by describing the potential harm. The harm might be to operations, such as the inability to perform critical business functions; assets, such as hardware or facilities; individuals, such as loss of personal information, injury, or loss of life; other organizations, resulting in financial losses or damaged relationships; or the nation, affecting government operations or national security.
Published by the National Institute of Standards and Technology, the Guide for Conducting Risk Assessments (NIST SP 800-30) includes the following scale for assessing the impact of threats to the business’s assets:
- Very high—Indicates multiple severe or catastrophic adverse effects. Severe or catastrophic indicates a loss of critical business functions. This loss might result in major financial losses or serious injuries to personnel.
- High—Indicates a severe or catastrophic adverse effect. Note that high indicates one adverse effect. Very high indicates multiple adverse effects.
- Moderate—Indicates a serious adverse effect. Serious indicates critical business functions are significantly degraded. The organization might still be able to operate but not as effectively as normal. The resulting damage can be significant.
- Low—Indicates a limited adverse effect. Limited indicates critical business functions are degraded. The resulting damage is minor.
- Very low—Indicates a negligible adverse effect. Negligible indicates the impact on critical business functions is small and unnoticeable.
