What Is the Scope of Risk Management for an Organization?
The scope of risk management indicates an area of concern, which can also be thought of as an area of control. Some things can be controlled, and others cannot. For example, hurricanes and earthquakes cannot be controlled, but their impact can be reduced by planning how an organization will respond.
FYI
The scope identifies the boundaries of a project. The biggest problem of not identifying the scope is scope creep. Scope creep happens when a project’s goals or deliverables grow without control. For example, personnel could spend time and resources on low-value assets at the expense of high-value assets. If the project scope isn’t controlled, the project can consume more resources, cost more, and take more time than would have been necessary if the scope had been defined. In the case of risk management, the boundaries may grow beyond the resources or time available to manage the risk, which can result in the organization’s not being able to identify or evaluate new risks while evaluated risks go without a response.
When considering risk management scope within the organization, consider the following items:
- Critical business operations
- Customer service delivery
- Mission-critical business systems, applications, and data access
- Seven domains of a typical IT infrastructure
- Information systems security gap
The following sections cover these topics.
Critical Business Operations
An early step in risk management is identifying which business operations are critical. These business operations are the ones that must be functional to ensure the organization stays afloat.
A business impact analysis (BIA) is the key tool used in this step. It helps an organization identify the impact on the business if various risks occur.
One of the key elements of the BIA is the identification of both direct and indirect costs. Direct costs reflect the immediate cost of an outage. For example, if a web server fails and cannot process sales, the sales lost during this period are direct costs. Indirect costs include the loss of customer goodwill and the cost to restore that goodwill.
These costs help identify the priority of the service or function. If the costs of an outage are high, then spending money to prevent outages is justified.
BIAs identify the maximum acceptable outage (MAO). The MAO is the maximum amount of time a system or service can be down before the mission is affected. The MAO is also referred to as maximum tolerable outage (MTO) or maximum tolerable period of disruption (MTPOD).
 TIP
TIP
Risk management must be driven by business needs, which means that the risks that are managed are those that have the potential to affect the business. Costs to manage risks outside this scope are not justified.
The MAO directly affects the required recovery time. As an example, the MAO is 30 minutes for a system, which means that recovery plans must be able to restore the failed system within 30 minutes.
A large part of the BIA is data collection. Data can be collected by going through available reports and interviewing personnel.
When completing a BIA of a specific service or function, the following key questions should be answered:
- How does this service affect the organization’s profitability?
- How does this service affect the organization’s survivability?
- How does this service affect the organization’s image?
- How will an outage affect employees?
- How will an outage affect customers?
- When does this service need to be available?
- What is the MAO of the service?
Customer Service Delivery
Risk management includes an evaluation of services that the organization provides to its customers. In this context, a customer is any entity that receives a service.
Obvious customers are those that purchase the organization’s services. For example, if the organization provides email services to small businesses, these small businesses are the organization’s customers. Instead of managing their own email servers, they outsource the service to the organization.
These customers have an expectation related to this service. They could expect that email will be available 24 hours a day, seven days a week. Alternatively, they may expect access to the email only during their business hours. Either way, identifying their expectations is important.
A service level agreement (SLA) is a document that identifies an expected level of performance, which includes the minimum uptime or the maximum downtime. Organizations use SLAs as a contract between a service provider and a customer. An SLA can identify monetary penalties if the terms aren’t met.
If an organization has SLAs with other organizations, they should be included in the risk management review and special attention paid to any monetary penalties. For example, an SLA could specify a maximum downtime of four hours (i.e., the MAO), after which hourly penalties would start to accrue. Of course, SLAs that promise low levels of downtimes cost more. This extra cost is imposed to pay for the extra controls that are necessary to provide a higher level of service.
A less obvious customer is the internal customer. Any employee or department that receives a service is a customer. Here are some common services provided to internal employees:
- Email services
- Access to the Internet
- Network access
- Server applications, such as database servers
- Access to internal servers, such as file servers
- Desktop computer support
 NOTE
NOTE
Entities within an organization often have agreements that are similar to an SLA but are more informal and don’t include monetary penalties. For example, a remote office may have an agreement with the main office that virtual private network (VPN) services will be provided during business hours.
Employees won’t have SLAs with an IT department, but they will have expectations related to the services. If any of the services fails for too long, the downtime will begin to affect the employees’ ability to perform their jobs, which in turn impacts the organization’s mission. By identifying the time frame when the outage affects the mission, the MAO can be identified.
Just because a service doesn’t have an external customer doesn’t mean it should be ignored. Many services are required for internal customers.
Mission-Critical Business Systems, Applications, and Data Access
Many organizations have mission-critical systems, applications, and data. When any of these critical assets are not available, the mission is affected. Therefore, identifying and reviewing these assets is important when reviewing risk management and risk mitigation plans.
Mission-critical business systems are any systems or processes integral to the organization. A deep understanding of the business is necessary to identify these systems, which can be aided by first identifying the organization’s critical business functions (CBFs) and critical success factors (CSFs).
A CBF is any function considered vital to an organization. If the CBF fails, the organization will lose the ability to perform essential operations, such as sales to customers. If the organization cannot perform the function, it will lose money through either lost revenue or indirect losses.
A CSF is any element necessary to perform the mission of an organization. An organization will have a few elements that must succeed for the organization to succeed. For example, a reliable network infrastructure may be considered a CSF for many companies today. If the network infrastructure fails, communication can stop.
CBFs are supported by several elements. For example, an organization sells products on the Internet. Figures 10-1, 10-2, and 10-3 show the different supporting elements in a complete transaction. By analyzing these elements, the CBFs can be identified.
In FIGURE 10-1, the customer makes the purchase. In this example, the customer is purchasing the product from an Internet web server, and a back-end database server records the transaction.
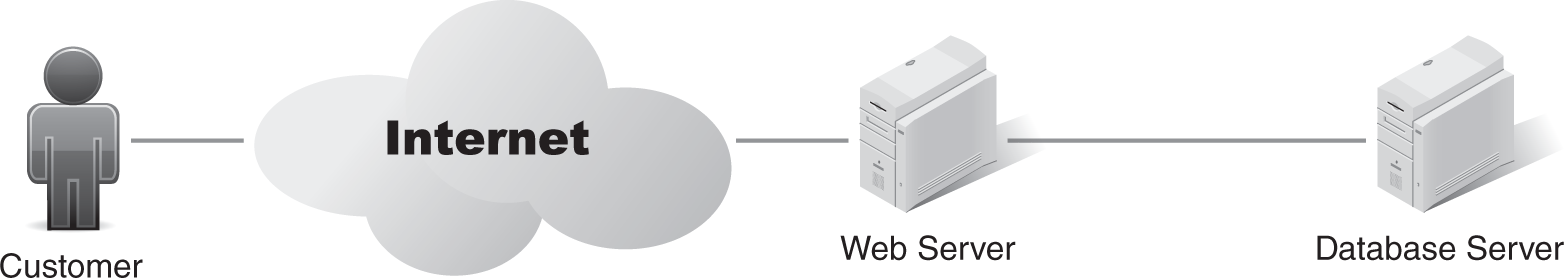
FIGURE 10-1 Critical business functions: making the purchase.
The CBFs here are:
- Internet access—The web server must have reliable Internet access. If Internet access fails, the customer can’t access the web server.
- Web server availability—The web server must be operational, which includes the web server and the web application. If the web server fails, the customer can’t complete the purchase.
- Database server availability—A database server records the transaction, which includes details on the customer, the product purchased, and payment information. If the database server fails, the web application cannot complete the transaction.
FIGURE 10-2 shows how a payment is received. Although payment processing will often occur as part of the transaction, here it’s separated for clarity. Credit card transactions are common on the Internet, and the organization using them must comply with the Payment Card Industry Data Security Standard (PCI DSS) to process them. The web application uses data in the database to identify details for the credit card payment and then sends a request to the appropriate bank for payment.
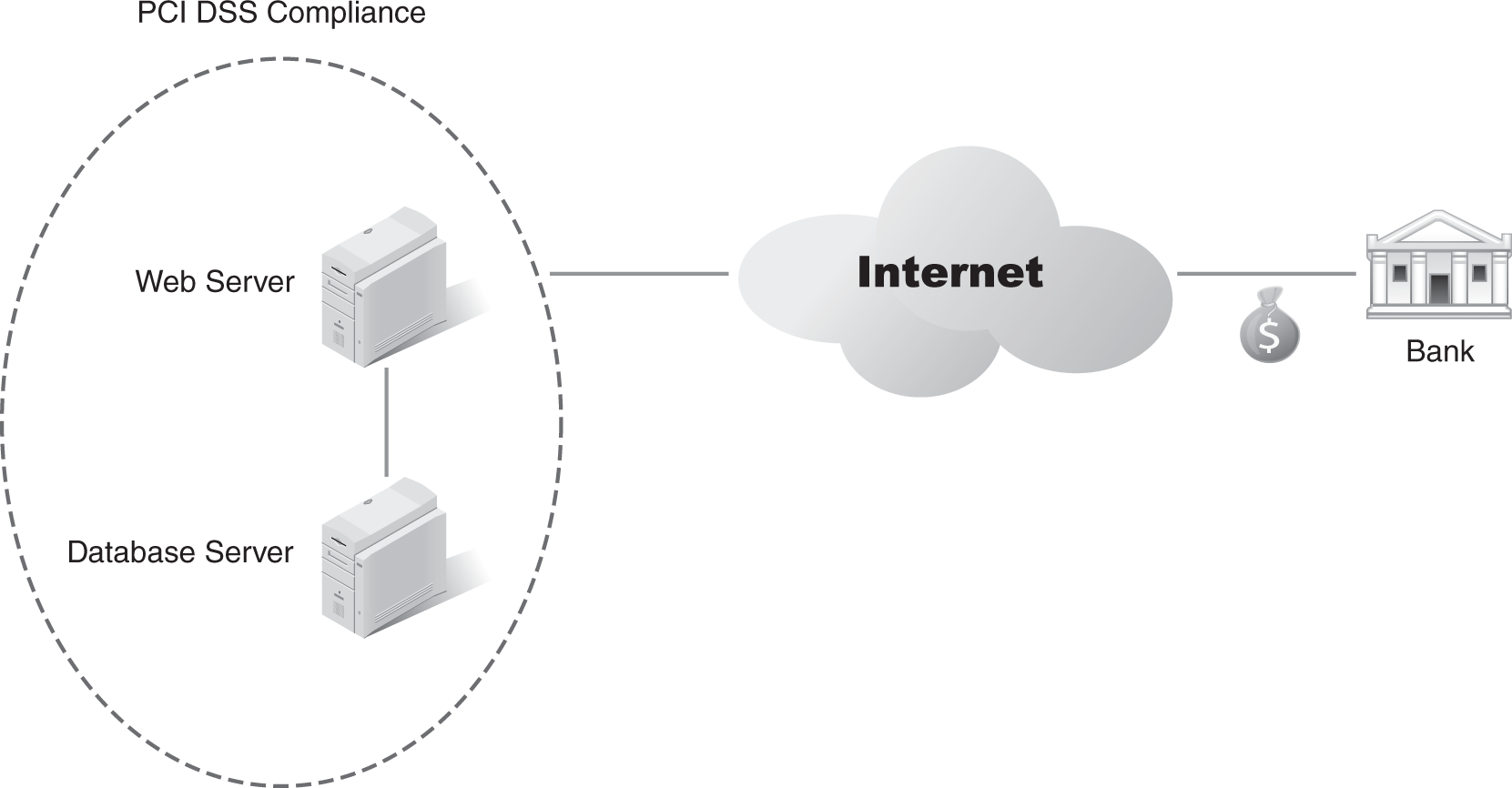
FIGURE 10-2 Critical business functions: receiving funds.
This step requires the same CBFs as the purchase step and one additional element. PCI DSS compliance is required, which ensures the organization is meeting minimum security standards for credit card data. If the organization is not compliant with PCI DSS, it can lose the ability to process credit cards as well as be assessed fines.
 NOTE
NOTE
PCI DSS is discussed later in this chapter in the Legal Requirements, Compliance Laws, Regulations, and Mandates section.
FIGURE 10-3 shows the last step in the process, in which workers use a warehouse application to identify products to ship. This application interacts with a database server, which has details on purchased products, customers, and product locations. The warehouse workers then ship the product to the customer.

FIGURE 10-3 Critical business functions: shipping the product.
This step has several additional CBFs:
- Warehouse application server—This application must be available to the workers and able to interact with the database server. If the application is not available, the workers won’t be able to identify products to ship, and thus shipping will stop.
- Database server—The database server is needed to identify which products to ship and details on where to ship them. If the data from this server is not available, shipping will stop.
- Workers—The workers pack and ship the purchased products. If the workers aren’t available, shipping stops. Even if an organization has been able to automate some of the functions, such as retrieving products, workers are still necessary to finalize the process. Additionally, human interaction is valuable for quality control.
- Warehouse—The products are stored and shipped from the warehouse. If the warehouse is damaged, two things will be affected. First, the inventory may be lost. For example, a fire could destroy some or all of the inventory in the warehouse. Second, shipping may stop or be slowed. If the shipping area is damaged, shipping may stop completely. If products are damaged, shipping will be delayed for these products.
 TIP
TIP
The warehouse database server holds much of the same data as the web database server, but they will probably be separate servers because they have different availability needs. The web application needs to be operational all the time, whereas the warehouse application needs to be available only when workers are shipping goods. Automation techniques would regularly move data from the web database server to the warehouse database server.
With the CBFs identified, focus can now be turned to risk management. Each of these functions can be reviewed to ensure that adequate steps have been taken to protect them.
Notice that some of the functions will require different levels of protection. For example, the web server and the web database server need to be operational all the time, which makes their MAOs short. The servers may require failover clusters to ensure the services continue to run even if a server fails. However, shipping may occur only six days a week during the daytime, which means the warehouse server won’t need the same level of protection as the web server and the web database server. The MAO for this server would be significantly longer.
Seven Domains of a Typical IT Infrastructure
The seven domains of a typical IT infrastructure can also be reviewed to identify risks. By looking at each of these domains, the scope of risk management needed for the organization can be identified. FIGURE 10-4 shows the seven domains of a typical IT infrastructure.
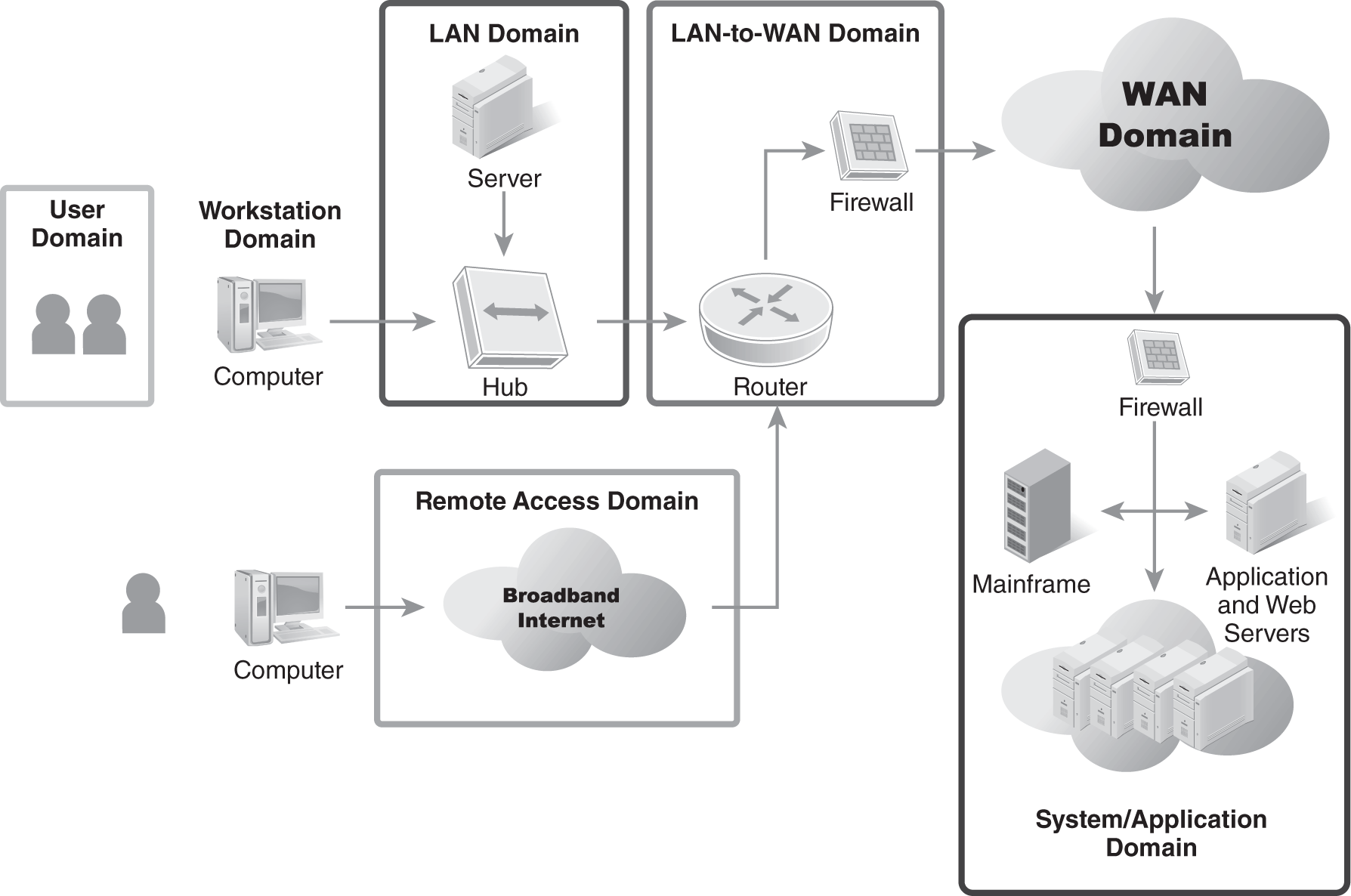
FIGURE 10-4 The seven domains of a typical IT infrastructure.
User Domain
Every organization has users because, even though computers do a lot, they can’t yet do everything. Instead, the computers are used to support the users. Therefore, looking at the risks associated with the User Domain is important. The primary risks associated with users are related to social engineering, which involves a social engineer trying to trick a user into giving up information or performing an unsafe action.
These risks can be mitigated by raising user awareness. Raising user awareness can include instituting an acceptable use policy (AUP), which helps ensure users know what they should and shouldn’t do; using logon banners to remind users of the AUP; sending out occasional emails with security tidbits to keep security awareness on users’ minds; and posting signs in employee areas to help raise awareness.
Workstation Domain
The Workstation Domain comprises the computers that users will use. In some organizations, all employees have computers on their desks, but, in other organizations, desktop computers may be limited. For example, not every user in a warehouse needs a computer.
However, when users do have computers, the computers are at risk. Some of the primary risks associated with workstations are related to malware. Users can bring malware from home on universal serial bus (USB) flash drives, they can accidentally download malware from a website, or they can install malware from malicious emails.
The primary protection for computers is to ensure that antivirus software is installed and antivirus signatures are regularly updated because users can’t be depended on to keep their signatures up to date. Many antivirus software vendors provide tools that automatically install and update the software on workstations.
Operating systems must also be kept up to date. When security patches become available, they should be evaluated and deployed when needed. Many of these security patches remove vulnerabilities; therefore, without the patch, the systems remain vulnerable. Just as tools are available to ensure antivirus software remains updated, tools are also available to keep systems patched.
LAN Domain
The LAN Domain includes the networking components that connect systems on a local area network (LAN). These components include hardware, such as routers and switches, and the wiring and wiring closets used to connect the users to the LAN.
Computers typically access network resources via servers. For example, in a Microsoft environment, clients are connected in a Microsoft domain, which includes at least one server acting as a domain controller. In a Microsoft domain, every user must have an account to log on to the domain, and every computer must have an account on the domain.
The LAN Domain is subject to significant risks. Routers have access control lists (ACLs) used to control what traffic is allowed through them, and switches can be programmed for specific functionality.
Routers and switches are commonly located in a wiring closet or server room, which helps ensure they are protected with physical security. If an attacker has unrestricted access to these devices, the ACLs could be modified, or an attacker could connect a wireless access point to capture and transmit all the traffic going through any of these devices.
Many organizations also practice port security as an added control. Port security ensures that only specific computers are able to attach to the network device, which means that, if an attacker brings in a computer, he or she will not be able to connect the computer to the network.
LAN-to-WAN Domain
The LAN-to-WAN Domain marks the boundary where the private network meets the public network. In this context, the public network is the Internet.
Several types of attacks come from the Internet. The primary protection here is the use of one or more firewalls. Firewalls can examine traffic as it passes through and allow or block traffic based on rules.
Although most organizations have firewalls in place, the major concern here is the management of the firewalls. A common problem is too many firewall rules allowing too much traffic. The firewall should discriminate and allow only certain types of traffic.
Organizations commonly use hardware firewalls that can be very sophisticated. Administrators often need additional training to ensure they know how to manage and maintain them. Trained administrators understand the importance of limiting the number of firewall rules.
WAN Domain
The WAN Domain includes all systems that are accessible over a wide area network (WAN). These systems primarily refer to servers accessible over the Internet.
Servers available on the Internet have public Internet Protocol (IP) addresses. They can be reached from any system on the Internet, which makes them easy targets.
A primary method of protection for systems in the WAN Domain is the use of a demilitarized zone (DMZ). A DMZ uses two firewalls, one of which has direct access to the Internet and the other direct access to the internal network. The area between the two firewalls is called the DMZ.
 NOTE
NOTE
The WAN Domain can also include systems that are accessible over a WAN link, which is semiprivate. For example, an organization can lease lines from a telecommunications company that other customers share. These lines aren’t as public as the Internet, but the organization’s systems are still susceptible to attacks from the other customers leasing the same lines.
Although the DMZ won’t stop an attacker from accessing a server, it can limit the attacker’s access. For example, a web server can be placed in the DMZ to host a website. Both unsecured and secured web servers use the Hypertext Transfer Protocol (HTTP). The well-known ports for HTTP and Hypertext Transfer Protocol Secure (HTTPS) are 80 and 443, respectively. The DMZ can be configured to allow traffic to the web server using only ports 80 and 443 and to block all other traffic.
These servers also need to be kept up to date. When security patches are released, they should be evaluated as soon as possible and then tested to ensure they don’t have any negative impacts, after which they can be deployed to the servers.
 NOTE
NOTE
A DMZ typically uses two firewalls. Public-facing servers are configured in the DMZ between the two firewalls.
Remote Access Domain
The Remote Access Domain allows remote users to access the private network. If the remote access server is a dial-in server, users can dial in. Although dial-in servers aren’t as common, they are still used. A more popular option is a VPN, which allows a user to access the private network over a public network, such as the Internet.
An organization utilizing dial-in remote access servers needs to be aware of the risks associated with the systems being available from any phone, which means an attacker only needs to know the phone number to attack. An organization utilizing a VPN server also needs to be aware of the risks associated with the VPN server having an IP address that is publicly available from anywhere on the Internet, which makes it susceptible to attacks from anywhere in the world.
Several different controls can be used to protect servers in the Remote Access Domain. Automatic callback is one method used with dial-in remote access servers, although this method is rarely used today. For example, Sally works from home. Her account information includes her phone number. When she dials in, she is prompted to log on. As soon as she logs on, the remote server hangs up and calls her home number.
Remote access policies are another control used with remote access. Policies are used to specify several conditions to ensure the connection is secure. For example, a policy could specify that only Layer 2 Tunneling Protocol (L2TP) connections are allowed. Additionally, Internet Protocol Security (IPSec) could be required to encrypt the connection.
 NOTE
NOTE
An older technique of locating remote access servers is war dialing. The attacker dials numbers randomly until a modem answers. Once the modem answers, the attacker attempts to log on.
Remote access monitoring is another control used with remote access. It reports remote user activities, including their status during VPN connections. A monitoring console is used to track client connections, including the quantity and duration of connections across various types of server configurations.
System/Application Domain
The System/Application Domain comprises any server-based applications, including email servers and database servers, and any server or system that has a dedicated application.
For example, Oracle Database hosts databases on a server, Microsoft Exchange is a popular email server, and Apache hosts web applications on web servers. Each of these applications is specialized, and each has its unique risks. They often require specialized knowledge to manage and configure. Moreover, they require attention to detail to keep them secure.
A primary requirement to keep these systems secure is to ensure administrators have adequate training and knowledge. Additionally, configuration and change management practices are helpful. Configuration management ensures the systems are configured using sound security practices, and change management ensures that the configuration is not modified without adequate review.
System applications often have bugs, and vendors release security patches when they have identified the bugs. Administrators of these systems need to stay in tune with the vendor so that they’re aware when patches are released. Unfortunately, some patches cause other problems, such as system crashes; thus, administrators typically test patches to ensure they do not have any negative effects and then apply the patches only after testing. Additionally, they often use software to verify that systems have current patches. When systems are not up to date, the software sends alerts to administrators. In some organizations, network access control (NAC) software isolates unpatched systems. Access to these systems are limited, until the software is up to date.
Information Systems Security Gap
The information systems security gap refers to the difference between the controls that are in place and the controls that are needed. In a perfect world, the in-place controls would address all threats and vulnerabilities. However, threats and vulnerabilities are constantly changing.
A risk assessment provides a point-in-time report. It can be used to compare the existing threats and vulnerabilities against the in-place controls. Even if the last risk assessment was perfect, it wouldn’t be able to address the threats and vulnerabilities that emerged after the risk assessment had been completed.
Gap analysis reports are often used when dealing with legal compliance. For example, a gap analysis report can be used when reviewing compliance with the Health Insurance Portability and Accountability Act (HIPAA) or the Sarbanes-Oxley Act (SOX). The gap analysis report documents the security gap.
The gap analysis report should be combined with a remediation plan, which identifies how the security gap is closed, meaning it provides recommendations on what controls to implement.
